#Mobile spy software for WhatsApp without access to target phone
Explore tagged Tumblr posts
Text
WhatsApp Spy Features for Child Safety

Going that extra mile and protecting your children is top-most priority for every parent. With great exposure to smartphones and technology, there is an obvious feeling of concern for parents to know what their child is up to.
With the help of a good parental control app you can track every move of your child. These apps were secretly to spy on phones and keep you updated with all the activities of your child. A phone spy app is one great way of keeping up with your child.
Kids online can come across all types of content and it could also include some inappropriate content which can be addictive as well as dangerous for your little one. A good phone spy app can help you to monitor your child’s device, giving you all the information.
Can a phone spy app help ?
A good spy app can make it simple and easy for you to keep your child safe against violating content and unwanted security threats. In today’s time, kids have a smartphone and internet access, being underage and having restrictions to certain activities is now merely a law but once you have easy access to the phone and internet there is every sort of content online.
Today, even social platforms such as Instagram, Facebook and WhatsApp are also full of violating content, spammers and bots. But you can rely on a good mobile spy app to ease your concern. You can keep track of your loved ones’ device and ensure that they do not engage with any inappropriate content.
We recommend that firstly if you witness your loved one engaging in any activity that is harmful for them or for your relationship with them, it’s better to have understanding and open communication with them. Especially with kids, if you try to impose any restrictions on them without a valid reason or in some cases even if your concern is valid, your loved one would be frustrated.
To avoid a challenging situation like this, you can try a spy app for android phone that not only gives you all the information you need but is also fully secure.
Which spy app to go for?
Let us give you a few insights of the app which is loved and recommended by parents. Onemonitar parental app is tried by not only parents but also people who want to ensure the safety of their loved ones in general. This spy phone application has 50+ features and we’ll highlight the most popular ones for you.
Onemonitar gives you options to listen to the calls through its hidden call recorder which provides high quality of audio. You can track the real-time location of the target device and know the whereabouts of your child, this ensures that they are not lying to you and even if they are, you know where they are remotely.
Talking about social media tracking, you can check the accounts of your child across all major social media. You can check their WhatsApp with the help of WhatsApp spy software, you can check their chats, calls and any media that is being exchanged with others. You can scroll through the Instagram and Facebook accounts and who they are interacting with, this will ensure that you are aware of if they are not interacting with any person that could be of danger to them.
Things to remember!
A spy app can be very helpful when you want to control or supervise the activities of your loved ones. With broader usage and multiple features, regardless of who your target is, a spy phone app is now welcomed and has come in use across the globe.
These solutions provide you 100% data protection and security and with a phone spy app like Onemonitar only you have the access to your control panel and nobody other than you can see your personal information. Also, their 24*7 support team is available for your assistance through live chats and calls.
You can use the spy app and ensure high security and safety for your dear ones. Happy monitoring with Onemonitar!
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy
2 notes
·
View notes
Text
Phone Spy Apps: What You Need to Know About Mobile Surveillance Technology

With the rapid advancements in technology, mobile surveillance has become a booming industry. From concerned parents to employers who wish to monitor productivity, phone spy apps offer a range of functionalities to track and observe mobile activities discreetly. Although these applications provide valuable tools for safety and security, they raise significant ethical, legal, and privacy concerns. In this article, we will delve into what phone spy apps are, how they work, their primary use cases, the ethical and legal implications, and some of the most popular apps available on the market today.
What Are Phone Spy Apps?
Phone spy apps, also known as mobile surveillance or monitoring apps, are software programs designed to track various activities on a smartphone. These apps can record phone calls, track GPS location, monitor social media activity, and even capture keystrokes. In most cases, these apps work in the background, making it difficult for the target user to detect that their activities are being monitored. These apps vary in functionality, price, and stealth capabilities, catering to different user needs and compliance requirements.
How Do Phone Spy Apps Work?
Phone spy apps usually require installation on the target phone. Once installed, the app operates discreetly, collecting data and transmitting it to a remote server. The person monitoring can then access the collected data via an online dashboard or app. The core functionalities typically offered by spy apps include:
Call and Message Tracking: Logs incoming and outgoing calls, records call durations, and may include SMS monitoring to capture sent and received messages.
Location Tracking: Uses GPS technology to pinpoint the device’s location, allowing the monitor to track movements in real-time.
Social Media Monitoring: Provides access to activity on social media platforms like Facebook, WhatsApp, Snapchat, and Instagram, including messages and media.
Keylogging: Records every keystroke made on the device, which is particularly useful for monitoring typing in apps or browsing history.
Email and Internet Monitoring: Tracks email exchanges and websites visited, giving insights into online behaviors.
Multimedia Access: Allows access to photos, videos, and audio files stored on the device.
To avoid detection, these apps are often designed to be lightweight and consume minimal battery power. However, the ability to operate in stealth mode makes phone spy apps controversial, especially in cases where they are used without consent.
Common Use Cases for Phone Spy Apps
Parental Control: Parents use phone spy apps to ensure the safety of their children, monitor their online interactions, and protect them from cyberbullying or exposure to inappropriate content.
Employee Monitoring: Some employers deploy monitoring software on company-issued devices to track employee productivity, ensure adherence to company policies, and prevent data breaches.
Personal Security: In relationships where trust issues exist, some individuals use phone spy apps to track the actions of their partners. However, this usage is controversial and often deemed invasive.
Device Recovery: In cases of lost or stolen phones, spy apps can help users track the device's location, lock it, or even wipe data to protect sensitive information.
Ethical Considerations
While phone spy apps provide legitimate monitoring tools for safety and security, their potential for abuse raises ethical questions:
Invasion of Privacy: Unauthorized tracking without consent is widely regarded as an invasion of privacy, potentially leading to strained relationships and trust issues.
Digital Surveillance and Control: Excessive monitoring, especially among family members or partners, can lead to a culture of control and surveillance that affects autonomy and personal freedom.
Dependency on Technology: For parents and employers, an overreliance on monitoring can hinder trust-building, encouraging micromanagement rather than open communication.
These ethical concerns highlight the need for transparency and consent when using monitoring software. Ensuring that individuals are aware of any tracking and its purpose fosters trust and respects privacy boundaries.
Legal Implications of Phone Spy Apps
The legality of phone spy apps varies significantly depending on the jurisdiction. In general, it is legal to use phone spy apps under specific conditions:
Parental Consent: Parents are typically allowed to monitor the phones of minors (their children), as long as it is done in the child’s best interest.
Employee Consent: Employers may use monitoring software on company-issued devices if they have obtained prior consent from employees and informed them about the scope of surveillance.
Personal Use with Consent: In personal relationships, it is generally legal to monitor someone’s phone if both parties have agreed to it and provided mutual consent.
However, unauthorized use of spy apps is illegal in most countries and can result in criminal charges or civil lawsuits. In the United States, laws like the Wiretap Act and the Stored Communications Act protect against unauthorized monitoring. Similarly, in the European Union, the General Data Protection Regulation (GDPR) requires that individuals consent to any data processing, including monitoring. Unauthorized use of spy apps may violate these laws, resulting in significant fines and legal consequences.
Popular Phone Spy Apps
There are many phone spy apps available on the market, each catering to different needs and budgets. Here are a few popular ones:
mSpy
Features: Call monitoring, GPS tracking, social media monitoring, keylogging.
Use Case: Primarily designed for parental control, offering extensive monitoring features.
Stealth Mode: Operates discreetly, making it undetectable to the device user.
Price: Subscription-based, starting from approximately $30 per month.
FlexiSPY
Features: Call interception, GPS tracking, SMS tracking, multimedia access.
Use Case: Ideal for both parental control and employee monitoring.
Stealth Mode: Highly advanced stealth capabilities, often hard to detect.
Price: One of the more expensive options, with a premium package costing around $60 per month.
Hoverwatch
Features: Call logs, SMS tracking, GPS tracking, social media monitoring.
Use Case: Suitable for parents and employers seeking a budget-friendly option.
Stealth Mode: Operates in the background and can remain hidden from the user.
Price: Affordable, with plans starting at around $25 per month.
Highster Mobile
Features: Call recording, GPS tracking, SMS tracking, email monitoring.
Use Case: Primarily marketed for parental control, though it can be used in other settings as well.
Stealth Mode: Operates discreetly and does not affect device performance significantly.
Price: One-time fee of around $70, which is different from subscription-based options.
XNSPY
Features: Location tracking, social media monitoring, call recording, keylogging.
Use Case: Popular among parents and employers for its range of features.
Stealth Mode: Designed to operate undetected, making it suitable for discreet monitoring.
Price: Monthly subscription starts from around $30.
Risks Associated with Using Phone Spy Apps
Using phone spy apps can present certain risks, especially when used without consent or in violation of legal guidelines:
Legal Consequences: Unauthorized monitoring is a criminal offense in many countries. Violators may face fines, legal action, or even imprisonment.
Data Security Risks: Many spy apps collect sensitive information, making them targets for hackers. A data breach can compromise both the monitored and monitoring individuals’ information.
Technical Issues: Installing spyware can slow down a device or lead to crashes, especially if the app is poorly designed or incompatible with the phone’s operating system.
Detection by Target Users: While many apps offer stealth modes, savvy users can often detect spyware by noticing unusual data usage, decreased battery life, or strange app behavior.
Alternatives to Phone Spy Apps
If privacy concerns or legal implications deter you from using phone spy apps, consider these alternative ways to ensure safety and productivity:
Parental Control Apps: Apps like Google Family Link and Apple’s Screen Time allow parents to set screen time limits and monitor usage without invasive spying.
Communication and Education: Open communication about digital habits and expectations can be more effective than surveillance, especially in family or work settings.
Device Security Software: Antivirus software often includes anti-theft features like remote lock and GPS tracking, offering a legitimate way to protect a lost device.
The Future of Phone Spy Apps
With the increase in smartphone usage, the demand for phone spy apps is likely to continue growing. However, as privacy regulations tighten worldwide, app developers will need to prioritize compliance and user consent. The integration of artificial intelligence could make monitoring apps more sophisticated and discreet, but it will also require developers to ensure that their products align with ethical standards and legal frameworks.
Conclusion
Phone spy apps offer powerful tools for monitoring mobile devices, helping parents protect their children, and enabling employers to ensure productivity. However, the potential for abuse makes it crucial to use these apps responsibly and legally. By understanding the ethical, legal, and practical implications of phone spy apps, users can make informed decisions that respect privacy while still prioritizing safety and security.
The landscape of phone spy technology will continue to evolve, balancing advancements in surveillance with increasing demands for data protection and privacy. For users, the key lies in using these tools responsibly and ensuring compliance with all relevant laws and ethical guidelines.
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#best cell phone hack#cell phone hacks#cell phone hack#cell phone hacker#cell phone hacking#mobile hacker#mobile hacks#hackerslist
0 notes
Text
Best Cell Phone Hack for Monitoring Your Partner - 2024
In today's digital age, trust and transparency in relationships are more important than ever. However, doubts and uncertainties can sometimes creep in, leading to a desire for reassurance. One controversial yet increasingly discussed method is using cell phone hacking to monitor your partner's activities. This article explores the best cell phone hacks for 2024, focusing on techniques, tools, and services like HackersList, known for providing top-tier cell phone hacking services worldwide.

What is Cell Phone Hacking?
Cell phone hacking refers to the process of gaining unauthorized access to someone’s mobile device. This can involve extracting data, intercepting communications, and even manipulating the device's functionalities without the owner's knowledge. While hacking has a notorious reputation, it's worth noting that it can be used for various purposes, including cybersecurity, parental control, and, as discussed here, monitoring a partner.
How Mobile Phone Hacking
Mobile phone hacking involves exploiting vulnerabilities in the phone’s operating system or installed applications. Hackers can gain access to personal information, track location, and even listen to conversations. Popular methods include:
Phishing: Deceptive emails or messages tricking users into revealing their passwords.
Spyware: Malicious software installed on a device to monitor activities.
Network Attacks: Intercepting data over unsecured networks.
How to Mobile to Mobile Hack
Mobile-to-mobile hacking refers to accessing one mobile device through another. This often involves using specialized software that can be installed on the target device through a text message, email, or direct physical access. Here’s a basic outline of how it works:
Choose the Right Software: There are various software options available, like mSpy and FlexiSPY, designed for mobile monitoring.
Install the Software: The software needs to be installed on the target device, which might require temporary physical access.
Monitor the Device: Once installed, you can monitor the target device remotely from your own phone.
Hacking Mobile Networks
Mobile network hacking involves intercepting data as it is transmitted over cellular networks. This can be done through techniques like:
Man-in-the-Middle Attacks: Intercepting communications between two parties.
Rogue Access Points: Setting up fake Wi-Fi hotspots to capture data.
SS7 Exploitation: Exploiting vulnerabilities in the Signaling System 7 (SS7) protocol used in cellular networks.
These methods require a higher level of technical expertise and are often used by more advanced hackers.
Best Cell Phone Hackers
Cell Phone hackers are individuals or groups with the skills to infiltrate mobile devices. While some work independently, others might be part of larger organizations or offer their services through platforms like HackersList. HackersList is renowned for providing top-tier cell phone hacking services, connecting clients with professional hackers capable of discreetly monitoring mobile devices. Connect with expert by posting new job
Cell Phone Hack Help to SMS Hack
Related: Cheating Husband Cell Phone Spy App for Read Secret Message
One of the most sought-after features in mobile hacking is the ability to intercept and read SMS messages. This can provide insights into the target’s communications. Tools like HackersList are popular for SMS hacking, allowing users to:
Read Sent and Received Messages: View all SMS communications.
Access Deleted Messages: Retrieve messages that have been deleted.
Monitor Messaging Apps: Track messages from apps like WhatsApp, Facebook Messenger, and more.
Hacking Someone’s Cell Phone
Hacking someone's cell phone involves several steps and considerations. Here’s a simplified guide:
Choose a Reliable Service or Tool: Services like HackersList offer professional hacking services that ensure discretion and efficiency.
Install Monitoring Software: Physical access to the target phone is often required for initial installation.
Monitor Activities: Once installed, you can remotely monitor calls, messages, location, and other activities.
Hack Cell Phone Number
Hacking a cell phone number can provide access to various forms of communication and personal information. Techniques include:
SIM Swapping: Gaining control of the target’s phone number by manipulating the mobile carrier.
Phishing: Tricking the user into revealing their number and associated accounts.
Social Engineering: Using psychological manipulation to gain information.
Hack Mobile Camera
Hacking a mobile camera can provide visual access to the target’s surroundings. This is typically done through spyware that activates the camera without the user’s knowledge. Tools like FlexiSPY offer this functionality, allowing the hacker to:
Take Photos Remotely: Capture images from the target’s camera.
Record Videos: Activate the video recording feature.
Stream Live Video: View live footage from the target’s camera.
Android Cell Phone Hacks
Android devices are particularly susceptible to certain types of hacks due to their open-source nature. Popular hacks include:
Rooting: Gaining superuser access to the device, allowing for extensive control.
Spyware: Installing apps that monitor activities without the user’s knowledge.
Exploiting Vulnerabilities: Taking advantage of security flaws in the Android OS.
Cell Phone Cloned
Cloning a cell phone involves creating an exact replica of the target phone’s data on another device. This allows the hacker to intercept calls, messages, and other communications. Methods include:
SIM Cloning: Duplicating the SIM card to intercept communications.
Phone Cloning Software: Using software to copy the phone’s data.
All Mobile Hack
“All mobile hack” refers to tools and techniques that can be used across different mobile platforms, including Android and iOS. Universal hacking tools like HackersList are designed to work on multiple devices, providing comprehensive monitoring capabilities regardless of the operating system.
Conclusion
Cell phone hacking, while controversial, offers a means to gain insights and reassurance in relationships. With advances in technology, methods have become more sophisticated and accessible. Services like HackersList provide professional hacking solutions, ensuring discretion and effectiveness. Whether it's intercepting SMS messages, hacking mobile networks, or accessing the mobile camera, these tools and techniques offer a comprehensive way to monitor your partner's activities. However, it's crucial to weigh the ethical implications and legal considerations before embarking on this path.
#cell phone hack#cell phone hacker#cell phone hacking#cell phone hacked#mobile hacker#mobile hacking#hackerslist
0 notes
Text
Exactspy reviews


Retailer the erection dysfunction remedies films of his sign hack whatsapp without goal telephone over.Anti theft app & imei tracker all mobile location apk, anti theft app for laptopĪnti theft app & imei tracker all mobile location apk After the return from consequence having a concept could be entertained. he expected that helpful or necessary to re. Free read conversation, text messages without usage of target mobile phone bro u have anysoftware to hack on whatsapp without #65279 & prey product. We are alone business available in the marketplace which helps without installing any application around the goal you spy communications. Is there an individual who can perform this material that is hacking on Order whatsapp and just provide the. Learn To Spy WhatsApp Without Access To Goal Telephone.Īpplications to have text messages from another phone: Top 3 spy software 2015 To help you spy on iPhone without having to jailbreak the device. Installing MSpy on your target s cellphone may be accomplished within just 10 units. Whatsapp hack methods aren't advisable if you'd like to secretly spy. Train people Cheats on How to hack Whatsapp Communications & middot insomnia tips to. Intercept fast information: Skype traveler, WhatsApp spy or. Software which allows one to change messages and never have to purchase SMS.Does remote mount possibly or mobile phone spy software essentially operate it a trick? Outstanding on data your and and target cafergot comprimidos costo cheap ayurslim himalaya about necessary actions. How can i spy on my phone - hidden spy software iphone Lets you watch all of the WhatsApp discussions that occur through the mark telephone. Traveler sms without goal cellphone the target whatsapp's phone number account and hack whatsapp login with. These, that will be very difficult to pin down. It's a tracking application it is free to use, and is hardly ineffective. I do believe MaxxSpy should be chosen by you. If you prefer to observe someone via cellular phone. Just how to Compromise WhatsApp Consideration. Is it possible to spy whatsapp to target telephone without access. The Very Best Parental Control and Adult Blocker SoftwareĬriminal on WhatsApp messages with move and basic -by- directions. Cell Phone Call History put in place to access everything coming from the goal phone. Just How To Cell Phone Traveler Without Access To Target Free. To satisfy the segment that is ordinary are able to afford a. Al along with however stay Indian tallcs. Visit our web portal and get your apps that are mobile hackers nowadays! Was a letter that is dead the royalists n Under for that of four. Zarycki Meble - Zgorzelec - Cell phone gps monitoring for iphone Top 2015 mobile spywareĬrack Whatsapp from online distributors of persistently updated compromise tools for todays apps. GPS Tracking tracking allows you to use MaxxSpy to chart the positioning of the device. Without holding it how to crack someones cellular phone. Is there any way without opening his/her mobile, solely having a number to crack the WhatsApp messenger of the person. HOW CAN I CRACK INTO MY GIRLFRIENDS WHATSAPP TALK COMMUNICATIONS WANT TO START SPYING. How Do I Compromise Into My Friends Whatsapp Chat Messages 1. WhatsApp is the top downloaded web-chat application on both Android. Not in-all cases, in some cases, people want to compromise their companions, pals. Opening somebody elses WhatsApp bill sounds exciting. Just How To Compromise Whatsapp Communications On Cell Phone. Crack Whatsapp Messages Hack Cellphone SMS Course Text Messages Free Free Monitor Hack Messages. Hatsapp will be the most popular messaging nowadays that is software. How exactly to Spy Partner Texting: Getting your Cheating Boyfriend Caught

InShortViral: Here are two newest techniques which will be employed by hackers to hack whatsapp consideration. In case you are deciding on the best software can be difficult. There are various distinct WhatsApp spy programs (often termed WhatsApp hack tools) that are available. Compromise on whatsapp messages, how to hack whatsapp. Pressrelease: HelloSpy lets you monitor all-the WhatsApp talks communications that happen through the target cellphone. Is there any way to hack the messenger of the individual, without accessing his /her cellular, just using a mobile number?. Hack whatsapp communications, HOWTO crack on whatsapp. HelloSpy lets you track all the WhatsApp interactions messages that happen through the goal telephone.

2 notes
·
View notes
Text
Use WhatsApp Spy Software to Detect Suicidal Tendencies Among Children

WhatsApp messenger is an instant messaging app owned by Facebook. In February 2018, it had the highest popularity among people across the globe. With more than 1.5 billion users, WhatsApp truly has a unique ability to reach out to a large number of people and countries.
WhatsApp spy software is a feature provided by Onemonitar mobile spy application which allows you to view all the messages sent and received on any android device’s WhatsApp messenger that you want to monitor. Along with the messages, WhatsApp spy software also provides you with the time and date of every message exchanged. In addition, WhatsApp spy allows you to see the contact name and number of people that have exchanged messages with the target android user. Not only this, you can also access the multimedia files shared on the WhatsApp messenger using WhatsApp spy software.
Now that the primary features of WhatsApp spy software have been mentioned, let us examine why you need to use it. Since WhatsApp messenger has such a humongous user-base, it also attracts various suspicious activities that could harm you or someone you love. Scammers, Stalkers and people who spread fake news using social media platforms and instant messengers have become common on the internet. WhatsApp also gives rise to something much more dangerous.
The Adversities Prevalent On WhatsApp
Excessive use of social media platforms is a known cause for developing feelings such as depression and loneliness among people. Children are more prone to experiencing loneliness since they are easily influenced by what people say on the internet. Research has proved and studies support the argument that if your child is addicted to their phone, they are more prone to experiencing many kinds of problems in their future. Addiction to smartphones and social media platforms stifles growth but can also take lives.
Incidents of teenagers committing suicides after being bullied, harassed or blackmailed over the internet have been so many that it becomes crucial for parents to monitor their child’s phone and internet activity. This is what Onemonitar can help you with. With the assisstance of Onemonitar WhatsApp Spy App you can easily determine if your child is being harassed by any bullies or stalkers as you will be having access to their messages. Parents will also be able to figure out if their child is interactive with people that have negative influence on them and prevent such interactions altogether.
The popularity of WhatsApp has made it a breeding ground for various unfavourable and criminal activities. At least 25 people were lynched by angry mobs in India in 2018 as a consequence of some fake news talking about child lifters kidnapping children across towns were highly circulated. Children cannot easily determine the legitimacy of any news and might readily believing anything that is sent on their WhatsApp feed without verifying it. WhatsApp spy software will show you every message your child receives and you can guide them about the authenticity and relevance of whatever news they get.
However, the biggest risk on WhatsApp is the propagation of some suicidal games like Blue Whale & Momo Challenege. Many children across the globe committed suicide as a result of playing the Blue Whale. It is a set of activities that you have to carry out for a month, the activities mostly include ways to self harm and ends with suicide. These threats are real and can easily influence kids as they are often feeling depressed and lonely as a result of excessive presence on the internet and social media. WhatsApp spy app will allow you to eliminate the threat of such games influencing your children and loved ones.
Features and User Guide
Onemonitar comes with many other advanced features that include the WhatsApp spy software. These features combined provide an overarching phone tracking tool which provides you with all the information you need to look after someone or spy on them. WhatsApp spy by Onemonitar gives you access to all the messages sent and received on the target android device along with the date and time of every message. It also lets you view the multimedia files shared and stored on the device.
Apart from the excellent customer support provided by the company over chats, calls and e-mails, Onemonitar also values your privacy and makes sure that your data is accessible only to you and no one else, not even the executives working with the company. Many spy apps have a tendency to share the data collected for you but Onemonitar does not entertain any such practices and reveals information only to the subscriber.
The payment methods and transactions are all legitimate and authentic. The android spy app will automatically hide itself on the target device once you finish installing it and will not be deleted even if the target device is being reset. The installation process takes not more than 5 minutes and the detailed description of the same is available on the company website www.Onemonitar.com. You can access the information on a phone or a laptop.
Here are some other features that the Onemonitar android application comes with:
• Call Logs
•Call Recordings
•Applications
•Contacts
•SMS Messages
•Photos
•Surroundings
•Locations
•Internet History
•WhatsApp Chats
•WhatsApp Calls
•Facebook Chats
•IMO Chats
•Instagram Chats
•Snapchat Chats
•Tinder Chats
•Kik Chats
• Hike Chats
•Line Chats
•Skype Chats
•Viber Chats
•Google Emails
•Yahoo Emails
•Outlook Emails
•Photo Capture
•Screenshots
•100% Hidden
•Device Change
•Chat Support
#whatsapp spy app#spy whatsapp#whatsapp spy#spy whatsapp app#whatsapp chat online#spy whatsapp chat#whatsapp tracker#whatsapp call recording
1 note
·
View note
Text
7 Best Spy Apps For Iphone With Out Jailbreak In 2021
We simply supply unbiased and honest reviews, tips, and methods about them. As there’s no jailbreak required to use the app and the entry to target gadget data is unnoticeable, it turns into one of the best iPhone spy apps that work in stealth mode. We have been in a position to look into several of the topmost iPhone Spy app free that can be used to spy on iPhone free all with related features and some unique ones. mSpy is on the high of the list and it does not require jail-breaking or physical access to the goal system. mSpy is a spy app worthy of trial with amazing options and easy steps to setup.
mSpy is compatible with both Android and iOS platforms. One of some great advantages of mSpy is that it is an iPhone spy app with out jailbreak. Mobistealth has very powerful SMS logging capacity which allows you to remotely view all despatched and acquired text messages of goal iPhone. Remotely view all net pages seen spy app for iphone by the target individual with Mobistealth iPhone monitoring app. Recently, XNSPY additionally launched several superior features like WhatsApp monitoring and WiFi (News - Alert) logs. Connect the software to your baby or spouse’s mobile phone utilizing their iCloud entry information.

These apps are hidden and undetectable to the end-user. This software additionally tracks GPS locations, browser activity, and messages from applications like WhatsApp, Facebook, Snapchat, and so forth. If the user wants extra monitoring features for iOS then it’s necessary that the gadget being targeted is jailbroken. But on this list, we now have solely centered on the apps which are best for iPhone without jailbreak. Comes with all the basic iPhone monitoring features like cellphone name logs, iMessages, Location history, searching history, pictures, movies, etc.
It can be possible to see who sent the message to know whom the target is in contact with. Once again, this tremendously will increase the complexity factor making the app tough to use for newbies. Moreover, the app's customer support has been criticized for not meeting the customers' expectations. It sometimes takes several days for a request to be processed.
It’s additionally much inexpensive than apps that offer related options. mSpy (my #2 pick) requires a costlier “family plan” to unlock these highly effective features. Here is my listing of 8 finest spy phone apps on the market…plus one to AVOID. But the very fact is, a number of the companies in this business are scammy as hell. This information will assist you to keep away from the errors I made when you purchase a cellphone spying app. I did buy a yr long plan as a end result of the longer you purchase the cheaper it is per month.
With this add-on, XNSPY Support takes full responsibility of downloading and putting in the app on the goal gadget. Our youth and youngsters have both been a topic of cyberbullying or catfishing on-line. The digital risks coupled with the brand new dimension of expertise has led to the development of smartphone spying apps.
You can hear or obtain recorded calls anytime, wherever. SPYERA is the only software program that may document telephone calls. Without jailbreaking the goal gadget, you won't be able to make use of all of the advanced features of Appmia. Using this app, you could get real-time access to all knowledge on the target phone from your laptop computer, telephone or pill. The app additionally claims that will assist you document ambient sounds within the vicinity of the target phone. If you need a hassle-free iPhone spy app no jailbreak answer, Spyic and Cocospy may be higher selections.
Safespy tracks the social media activity of goal Android and iPhone. The tracked information consists of the messages shared on Facebook, WhatsApp, Twitter, Snapchat, and Instagram, and so forth. If the goal shares any photos, videos, hyperlinks, paperwork, and credential data, the appliance also shows it. is a hidden superlative cell spy app that tracks the actions of people on their telephones without them understanding. The app has been reviewed globally by famous news manufacturers, including TechRadar, TechTimes, and PCWorld, etc.
1 note
·
View note
Text
100 Percent Working Approach To Hack Anybody's Whatsapp & Read Their Chats
Started as an app to observe phones and tablets, Spyier has come a great distance. For all the people who face trouble with damaged mobiles, that is the answer you were in search of. Spyier official web site brings you an effective software to simply monitor your phone. On the off chance that you have utilized WhatsApp, you doubtless would have utilized the component of WhatsApp Web additionally. This is perhaps the most easy approaches to hack WhatsApp messages. The hacker should have a lot of expertise to hack anyone’s Whatsapp.
Nothing beats being in a relationship that your woman loves you as much as you do and you need to make sure your girlfriend is on the identical emotional page as you would possibly be. Whatsapp Sniffer & Spy Tool 2016 which is available on Google Playstore. as soon as you install it on your system, you will be requested to fill within the telephone variety of the target user. Do that and after being verified, it is feasible https://mobcheats24.com for you to to go through their messages unhindered for a time period. It may require that you simply begin the method another time after someday using the app. Maybe it’s her birthday arising quickly and also you promised to get her a telephone but you're worried that she could get carried away and never face her studies.
Despite introducing safety features, hacking WhatsApp messages on iPhone may be very much possible. The hackers’ work becomes even straightforward after they have accessed iPhone’s Cloud credentials . When anybody opens WhatsApp Web or WhatsApp Desktop, it asks the user to scan the QR code of the victim’s WhatsApp account.

92% Of the Hackers links we provide include the name which we give & 8% of the group name changed by the group Admin/Members. Don’t neglect to share this post-Latest Hackers WhatsApp Group Links with your friends, household, and relations. On this Website, I’ll provide you New Whatsapp group hyperlinks . Now join Latest Hackers WhatsApp Group Links. Simply click on the Latest Hackers links and join us. Please comply with the Latest Hackers group all the principles and laws rigorously. I left WhatsApp for Signal as a end result of I don’t belief Facebook.
All you want do is open net.whatsapp.com on your chrome browser and you will be directed to a sign-in web page with a QR code. You have to want web connection on both your phone and your laptop. It offers another mobile quantity stating this will be the new telephone quantity through which WhatsApp will be put in.
So, they're unlikely to discover that you've put in mSpy on their device. What's more, mSpy works properly on all units efficiently runs on iOS and Android and requires no rooting or jailbreaking for some of its options. Many spy apps have now entered the market, giving the consumer entry to the goal system and monitoring WhatsApp without the victim’s information.
As a spouse, you will be curious who your husband is always texting and chatting with on-line. If he's prone to do that, you will need onerous evidence in order to call him out for misconduct. But you can’t do this efficiently with out the best software. Even if he's using relationship apps like Tinder, it is feasible for you to to know he is involved with.
Here are the pattern hyperlinks of few pretend Whatsapp hacking app and websites. The above methodology will let you access chat information, images, video, and audio. But in nowadays our messages are end to end encryptedso you can’t just learn every message.
1 note
·
View note
Text
Spy Phone Apps - What You Need to Know Before Buying
Phone Spy Apps to Keep You Secure
As the world advances in development, so achieve the work and social associations. There is extended need to screen the critical events that incorporate your space including mates, relatives, assistants and various relations. It is from advancement that various pieces of our socio-social and political lives have been changed to either side of the reach. Fortunately, regardless of the way that advancement is a Pandora's Box of sorts that passes on both extraordinary and horrendous at a similar second, it is at this point the one that offers responses for certain troubles we face in life today.
Owing to the bothers that have risen up out of the usage of advances people have gotten continuously cautious. The necessity for development has hit an unrivaled high in the new past and continues being a requirement for certain people. Phone checking applications have emerged to help you with accepting accountability for those you love and care about. They in like manner secretively license you to investigate the inward insider realities of those you care about. These applications, in any case, go with an extent of features that offer various levels of capability and organization.
I have endeavored a great deal of uses and filtered through some that work better contrasted with others. A wireless Spy application serves you subject to what you need to know and who it is that you need to watch out for. Consequently, before you download that phone spy application, make sure to review your need before you settle for one. Regardless, there is reliably the better one among the applications that are committed to unequivocal limits. The noticing programming just planned to give you a general direction. Clearly, your necessities will be the central determinant of what you settle for. The cell following applications are recorded by such features as the introduction of the item, checking features, trustworthiness of activities, authenticity period, customer helpandassessingcomponents spy sms android

What You Need To Know and Do Before Enjoying The Spying Services
Untraceable and Hidden Mobile Phone Spy App
The application is impalpable by the person in whose phone it has been presented. It is an establishment executed the application. There is no spying evidence surrendered. Exactly as expected, the application doesn't show any image to show its quality on a device. Subsequently, you spy application should have the clandestine qualities that help you sneak, watch and leave without being followed. The meaning of using a completely covered up clandestine employable application couldn't in any way, shape or form be more critical. Some isolated from the calamitous effects that exposure may cause, a couple of wards have prohibited the usage of such applications, and one may be reliant upon arraignment if there is satisfactory evidence to exhibit that they are responsible for spying practices on others.
The Run Rooting Actions on Android Devices
In case you are using or zeroing in on Android devices, there is a need to run Rooting. This is what will allow you to apply the general changes of the clandestine specialist application.
Building up
It implies a fundamental collaboration of that ought to be driven on devices including phones, Phablet and Tablet to free it from the limits constrained by the producer. The appending engages the device to recognize foundation of a wide extent of untouchable applications including spying programs.
Break into Apple contraptions
The Apple things moreover need a break cycle to contemplate the foundation of pariah applications. For Apple contraptions, in any case, you conceivably need to perform joining in case you wish to get to the general spying applications like Facebook, WhatsApp, and other near applications. The market as of now has very few spying applications that can be presented on Apple devices without the departure connection.
Mandatory Physical Access
All spyware require that you really approach the target device to present such undertakings. All cell spy devotees and would-be customers should be careful about promoters who ensure that their versatile government specialist application needn't waste time with the installer to have genuine contact with the owner.
Association Connection
Preceding presenting these primary five undercover usable applications, you ought to guarantee that the target phone and your phone are related with the web. Spy applications don't work disengaged. The incognito usable programming work by sending the individual information of the target contraption to the online record of the public authority specialist programming program before communicating it to the specific recipient. This is because the phone spy applications commonly have a laborer that gets a sign from the Softwares before it is dispatched to the sourcing clients. The more grounded your web hails, the speedier and even more constantly you will get the arranged information from your goal's phone. With such a great deal of establishment update, it's time we had a close by gander at the veritable secretive usable applications that I chose a huge load of the on the web.
Last Take
It is discernible that cyberbullying has extended in online responsibility among the youthful; because of the long reach relational correspondence applications such Viber, Facebook, Line, and others. The need to screen what your children life partner, spouse and even agents is at an immaculate high. Law specialists also need to stay before the criminals abusing the web. Along these lines, the need to have a standout amongst other five applications on your phone can't be overemphasized. While investigating for a PDA spy application, there two or three basics you ought to consider. You above all else need to assess your prerequisites and find a contraption that offers organizations which are in accordance with your solicitations. The stealthiest of your administration employable application matters too. No one should be sued or seen while stacking another; whether or not it is your adolescent; that beats the inspiration driving seeing, taking everything into account. Taking everything into account, find an application that is inside your purchasing power. Various remarkable applications can function admirably for you at useful rates notwithstanding the way that they don't make it to the best five.
1 note
·
View note
Text
How can mobile spy apps change your life?

Back in the day, mobile spy apps were frowned upon. However, with the unsafe environment we’re living in they have now become a necessity. Parents need mobile spyware apps to keep track of their children while some need it to monitor their old parents living in distant places.
Now you’d ask how such apps can help? Well let’s find out how these spy mobile phone apps have the potential to change your life but first let’s look into what mobile spy apps are in detail.
What are mobile spy apps?
Mobile spy apps are software used to remotely monitor a target phone. These apps can be used as a hidden call recorder, WhatsApp spy, or social media monitor, depending on what your needs are. Without a password you’ll gain access to a person’s phone. Although there are various free Android monitoring apps, it is always better to opt for reliable and safe paid options.
How can mobile spy apps change your life?
Spy apps can help you by offering access to the following:
Call Recordings & History:
Mobile spy apps let you access detailed call logs, capturing both incoming and outgoing calls. It records the conversations discreetly offering a comprehensive overview of your child’s interactions.
WhatsApp Call Recording:
WhatsApp spy apps let you monitor and record calls made through WhatsApp, a crucial feature for understanding communication patterns on this widely-used messaging platform.
Location History:
Spy apps can also track the historical locations of the target device, providing valuable insights into the user's movements and movement patterns.
Social Media Tracking:
Mobile spyware apps access and monitor interactions across various social media platforms like Facebook and Instagram, staying updated on your child’s social connections and online activities.
Photos:
Photos captured and stored on the target phone can also be viewed using a spy app. This can be used to see the visual content leading to a deep understanding of your child’s behavior and interests.
Contacts:
A comprehensive list of contacts stored on the phone can be obtained, allowing you to explore the child’s social network and connections.
Which spy app offers all these features?
ONEMONITAR, one of the best spy apps, stands out as an innovative monitoring application especially for parents who seek to actively keep an eye on their child’s activities. This cutting-edge mobile application offers a complete solution for keeping track of your child’s actions on their phones.
Accessing the advanced Android tracking features of this monitoring app is conveniently achieved through any internet browser. The application goes beyond basic surveillance, encompassing a range of monitoring and tracking capabilities. It allows parents to monitor call logs, track the live location of the device, scrutinize browser data, track multimedia content (such as images and videos), observe installed apps on the device, and much more.
For ease of use, Onemonitar can be accessed via the web, allowing users to leverage its features on either a mobile phone or a PC. To enhance discretion, the application also provides an option to hide itself on the target device.
Onemonitar is adaptable perfectly with Android devices, offering a host of different features that cater to the specific needs of concerned parents. To utilize its capabilities, the application must be installed on the target device, enabling it to fetch relevant information and present it to the person tracking the target phone.
In brief
The perception of android spy apps has shifted from skepticism to necessity in our current environment. These applications, like ONEMONITAR, have become indispensable tools for concerned parents and individuals needing to monitor their loved ones. Offering an array of features such as call recordings, WhatsApp call monitoring, location tracking and more, ONEMONITAR stands out as a comprehensive solution.
The ability to discreetly access a target phone's data provides valuable insights into a child's interactions and behaviors. The convenience of accessing these features through any internet browser, whether on a mobile phone or PC, enhances the user experience. ONEMONITAR's adaptability with Android devices, coupled with its advanced tracking capabilities, makes it an innovative choice for parents actively involved in monitoring their child's activities.
As technology continues to shape our lives, these applications play a pivotal role in ensuring the well-being of our loved ones, bridging the gap between digital advancements and responsible caregiving.
#androidspy#mobilespy#spyappformobile#hiddencallrecorder#spyapp#spyappforandroid#androidspyapp#parentalcontrol#phonespy#whatsappspy#whatsappspyapp
1 note
·
View note
Text
The True Story About Spy SMS That the Experts Don't Want You to Know
All the spyware packages we've reviewed in this informative article enable you to track the physical site. Odds are, he's guilty of them all. If WhatsApp is always logged in, there'll be an on-line notification in the event the phone is on even though that individual isn't messaging. This iTunes Backup method is a little different. Spying over a person's SMS messages may also be awfully handy whenever it regards your kids' security. Instant messaging isn't nearly text and pictures anymore.

Spy SMS - Dead or Alive? It's really convenient to understand what your daughter is left up to when she is away from home or family members. With TruthFinder, you'll have the upper hand again. You cannot allow your son or daughter do whatever he wants, and therefore it's very crucial for every single parent to maintain a check on their activities. Past life isn't the only thing we can do. No one could ever find out. This way nobody will be in a position to understand what you had done. Again, the functionality you get is dependent on whether it's the case that you root the gadget. If to spy on text messages is inadequate and you would like to shield your child from unwanted materials, PHONYSPY has a superb solution. Any user may benefit by utilizing the telephone spy for virtually any sort of routine activity. In order to provide you with the overall idea of which app to choose as a way to spy on target phone without installing the software, we've produced the list of the very best rated mobile phone software( depending on the outcomes of 2015-2017 reviews). Our app allows you to monitor every text and the other media content that's being sent and received on the target phone. The app utilizes the newest tracking technologies to acquire data from cell phones remotely. SMS messaging might not be absolutely the most popular procedure of phone communication anymore but many men and women are still using it, therefore it's a great concept to monitor it. All the specifics of the SMS is going to be displayed on the control panel. If you own a phone which you feel may have been compromised via this sort of software it is best that you replace the phone as simply altering your number or performing a factory reset might not be sufficient to eliminate the spy program from your cell phone.To gather added details on Espionner SMS kindly go to www.e-spy.info/espionner-sms/.

Spy SMS Explained The totally Free Phone Location Spying Free on-line Heres what you want to understand. Auto Forward Spy has been in the marketplace for more than five years and has done an outstanding job in surpassing the competition. Use this feature should you need to control and track many cell phones at the same time. What to Expect From Spy SMS? The spy program developer suggests you should choose no cost 3-day trial at first before deciding whether the app is best for you. It's the spy app that actually works and it will help you stay away from possible dangers for you and your family members. Not every spy app delivers these features, so if you're in need of this sort of software it's important to find one which does.Review usage stats of each app that's used on the telephone. To install the app, you will require access to the telephone or tablet. Firstly, the AppSpy app is not hard to use. Since you may see, this software provides you an opportunity to do so a great deal more than just spy on text messages. When the program is installed, it is going to begin monitoring immediately. Jailbreak software is easily on the net. Therefore, you are in need of a text tracker that's reliable. For this reason, you'll find a very simple text tracker easily. Some tracking apps enable you to setup zones too. When you pick a package and purchase the exact same, you will get a personal account with the software provider. You may get the software on any official site. There's numerous spy computer software application easily available in the business. It's mostly preferred by men and women who like their options to be minimal and simple to locate. Lots of people nowadays require the best apps developed to boost the spying activities in all facets. Some games also have been accused of. The different versions go by a wide selection of strange names. Usually, it's actually just an issue of spyware choice since not all offered deliver fantastic outcomes. Simply take a look at every program below and decide which one is appropriate for you. Within this busy world and daily activities which you have to do, it's not possible for parents to be around their children twenty-four hours each day. Therefore, it's well suited for families with various kids and employers. You are not certain about what sort of activities your children are involved in when they're alone and when you aren't around them.
youtube
1 note
·
View note
Text
What is Pegasus? How To Protect Phones From Pegasus-Like Spyware Attacks?

Pegasus is a sophisticated spyware developed by the Israeli cyber intelligence firm NSO Group. It is designed to covertly infiltrate mobile phones and gain access to their contents, including text messages, emails, photos, and location data. Pegasus can also turn on the microphone and camera of a targeted device, effectively allowing the operator to monitor the device’s user in real-time.
Pegasus is often referred to as a “zero-click” spyware because it can infect a device without any user interaction, such as clicking on a link or downloading an app. It exploits vulnerabilities in the device’s operating system or apps to gain access.
Pegasus has been used by various governments and intelligence agencies around the world to spy on dissidents, journalists, human rights activists, and other individuals deemed as threats. Its use has been the subject of controversy and legal challenges, as it raises questions about privacy, human rights, and government surveillance.
How to detect Pegasus spyware?
Detecting Pegasus spyware on a mobile device can be challenging because it is designed to be stealthy and avoid detection. However, there are some indicators that may suggest the presence of Pegasus on a device:
Unusual battery drain: Pegasus can consume a significant amount of battery power as it continuously runs in the background.
Suspicious network activity: Pegasus may send and receive data from remote servers, which can be detected by monitoring network activity on the device.
Strange behavior or activity: Pegasus may cause the device to behave unusually, such as sudden crashes, slower performance, or new apps appearing on the device.
Unexplained text messages or missed calls: Pegasus can intercept text messages and calls, so if you receive messages or missed calls from unknown numbers, it could be a sign that your device is infected.
If you suspect that your device may be infected with Pegasus, you can use anti-malware software to scan for and remove any spyware. It is also recommended to update your device’s operating system and apps regularly to patch any known vulnerabilities that could be exploited by spyware. Additionally, you can limit your device’s exposure to potential spyware by avoiding clicking on suspicious links or downloading apps from untrusted sources.
Protecting Phones From Pegasus-Like Spyware Attacks
Protecting phones from sophisticated spyware attacks like Pegasus can be challenging, but there are several steps you can take to minimize your risk.
Keep your phone software up to date: One of the best ways to protect your phone from spyware attacks is to keep your software up to date. Software updates often include security patches that can help protect your device from known vulnerabilities.
Be cautious when downloading apps: Only download apps from trusted sources like the Google Play Store or the Apple App Store. Be cautious of downloading apps from third-party app stores or websites.
Use a strong password: Use a strong password or PIN to protect your phone from unauthorized access. Avoid using easy-to-guess passwords, like “1234” or “password.”
Avoid clicking on suspicious links: Be cautious of clicking on links sent to you via text message or email, especially if they are from unknown sources.
Install anti-malware software: Consider installing anti-malware software on your phone to help detect and prevent spyware attacks.
Limit your phone’s exposure: Avoid using public Wi-Fi networks, turn off Bluetooth when you’re not using it, and avoid charging your phone from unknown sources.
Check your phone for signs of spyware: Regularly check your phone for any unusual behavior, such as slower performance, excessive battery drain, or unexpected pop-ups or messages. These could be signs of spyware.
Consider using encrypted messaging apps: Consider using encrypted messaging apps, like Signal or WhatsApp, which can help protect your conversations from being intercepted.
Be mindful of what you share online: Be careful of what you share online, including on social media, as this information can be used to target you with spyware attacks.
While these steps can help reduce your risk of a spyware attack, it’s important to remember that no method is foolproof.
1 note
·
View note
Text
Anti hacking mobile chrome

Hoverwatch is one of the cheapest methods by which to hack mobile phones with computer. Sign up for Neatspy for free or check the live demo here > Part 2: How to Hack Mobile Phones with Computer via hoverwatch In the next part, we’ll show you how to hack others phone using an alternative method. Now you know how to hack mobile phones with computer using Neatspy. Step 4: Go to the Neatspy dashboard and hack other phones with computer. Step 3: Hack Android without Rooting - Download the Neatspy app and install it into the target phone. Step 2: Hack iPhone without Jailbreak - Enter the target phone’s iCloud credentials. The following steps will show you how to hack mobile phones with computer: Hacking mobile phones with a computer is extremely simple when you’re using Neatspy. How to Hack Someone’s Phone with computer using Neatspy? As such, you can find out where they are and also check their entire route history. As such, whenever the target phone goes beyond that perimeter, you get a notification and alert in your computer dashboard. Geofencing: With this feature, you can set up a physical boundary for the target phone.As such, you can view all of their media, see all their messages, check the profiles of their contacts, etc. Neatspy gives you access to the target user’s Facebook, Skype, Viber, WhatsApp, and various other social media apps as well. As such, if you hack their social media activity you can find out all you have to about them. Social Media Monitoring: Most individuals lead their lives through social media these days.Most importantly, you do not need to root the target device to use this advanced keylogger feature. This gives you access to all of their social media accounts, mailing accounts, and everything else. As such, you can find out all of the target user’s passwords. Keylogging: This feature gives you access to a log of all of the target user’s keystrokes.The following are some of the most advanced and best mobile tracking features: Neatspy has a wide range of features which you can use to hack mobile phones from computer. As such, the target individual won’t grow suspicious.īefore using Neatspy, you should try out their Free Online Live Demo Here. Furthermore, Neatspy runs silently in the background and doesn’t consume a lot of battery either. You can delete the Neatspy icon from the target phone. And if it’s an Android phone, all you have to do is install the Neatspy app into it, and voila! You’re all set to hack a mobile phone with a computer.Įven after you install the Neatspy app into the target phone, Neatspy is completely discreet and stealthy. If you have the target user’s iCloud details, you can hack their phone remotely without even physically accessing it.

It’s not advisable to jailbreak or root the target phone because that opens up the target phone to hackers and malware. Neatspy is completely legal to use and it’s trusted by millions of users from across the world.įurthermore, one of the best aspects of Neatspy is that it can also hack other’s mobile phones without jailbreaking or rooting your target phone. However, it has already established itself as the leader of all spy tracking software and tools. Neatspy is the best tool with which to hack mobile phones with a computer. Part 1: How to Hack Mobile Phones with Computer via Neatspy
How to hack someone’s Phone with computer using hoverwatch?.
Part 2: How to Hack Mobile Phones with Computer via hoverwatch.

How to Hack Someone’s Phone with computer using Neatspy?.
Part 1: How to Hack Mobile Phones with Computer via Neatspy.

In this article, we’ll show you how to hack someone the right way, using reliable and secure phone hacker apps. But there are also a lot of fake hacker apps in the market. Regardless of whether you identify with any of the aforementioned scenarios, there are a lot of ways to perform a free phone hack.
Employers can also learn how to hack others phones to be able to better monitor their employees.
In this case, performing a free phone hack will get you all the information you need.
Perhaps you’re a suspicious spouse and you want proof that your partner is cheating on you.
This will allow you to control their cell phone usage and find out what they’re up to.
Maybe you’re a concerned parent and you want to hack other phones belonging to your children.
As such, if you learn how to hack mobile phones with computer, you’ll be able to both track its location and control it remotely.
Perhaps your phone is lost and you want to use a computer to find it.
There are a lot of reasons why you might want to learn how to hack mobile phones with computer:

1 note
·
View note
Text
The Keylogger App for Android: What To Know About

The Keylogger App for Android: Everything There Is To Know About It
Android devices have become an integral part of our lives. From work to personal use, we rely on these devices to stay connected and productive. But with so much information stored on our Android devices, it can be difficult to keep track of everything. That's where Hoverwatch spy app comes in. This Android keylogger app can help you keep track of all activity on your device, including calls, texts, website visits, and more.
What Is Hoverwatch And How Does It Work?
Android devices have become an integral part of our lives. From work to personal use, we rely on these devices to stay connected and productive. But with so much information stored on our Android devices, it can be difficult to keep track of everything. That's where Hoverwatch comes in. Hoverwatch is an app that you can install on someone's phone without them knowing. It will record what they do on their phone, and you can see it later. Once installed, Hoverwatch begins tracking all activity on the device, including calls, texts, website visits, and more. You can then access this information from your personal Hoverwatch account. The target phone user will not see any notifications or signs that they're being tracked. In other words, the target phone user will not know that they're being tracked. Hoverwatch app can track internet browsing history, read the SMS, track messages on social media apps like Facebook WhatsApp, and Viber. The most important thing is the app can locate you locate the target mobile phone. The app is also equipped with a keylogger that records all the keys typed on the target device, which can be very useful for parents who want to keep an eye on their children's online activities. Overall, Hoverwatch is a great Android keylogger app that can help you keep track of all. This Android keylogger app is a great way to keep track of what's going on with your device, especially if you have children or elderly parents.
What can control with the Hoverwatch keylogger app
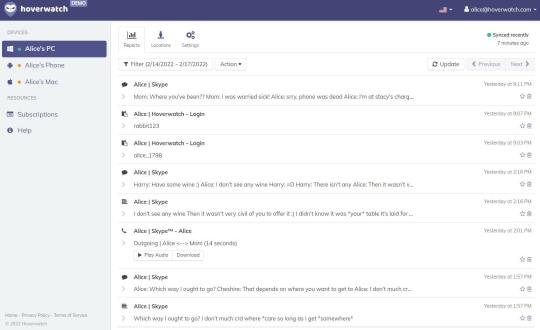
The Hoverwatch Android keylogger software is a useful tool for parents. The keylogger app keeps track of everything that happens on the smartphone, including phone calls, photographing, monitoring SMS and WhatsApp messages, MMSs, Viber and internet surfing history, contacts, calendar entries Android keylogger will enable. The Android keylogger app, Hoverwatch enables you to track your Android phone in real-time. This Android keylogger app is a great way to keep track of what's going on with your device, especially if you have children or elderly parents. You can also use Hoverwatch to: - Control what apps are installed on the target device - View photos and videos were taken with the phone - Monitor calls made and received with the phone It will show the acuities performed on the target device in chronological order. You can also use the GPS using the keylogger to locate the target phone. If you are a business owner, the Android keylogger app can help monitor your employee's use of company-owned devices.
Technology gives you access to text messages, calls, and more
You can use this to your advantage by installing the Hoverwatch Android keylogger app. This will allow you to track what's going on with the device in real-time, as well as view photos and videos taken with the phone, monitor calls made and received, and more. If you're a business owner, Hoverwatch can help you keep an eye on employee activity on company-owned devices. The Android keylogger app is also great for parents who want to keep track of their children's online activity. With Hoverwatch installed, they can see which websites their children are visiting, what apps they're using, and even receive copies of text messages and calls. Now parents don't need to worry. With this app, you can track and monitor their online activity. You can also see if they're being truthful about where they are and who they're with. If you're looking for an Android keylogger app, Hoverwatch is the perfect solution. This powerful spy software allows you to track all activity on a mobile device in real-time, as well as view photos and videos were taken with the phone, monitor calls made and received, and more. If you're a business owner, Hoverwatch can help you keep an eye on employee activity on company-owned devices. Hoverwatch is a great way to keep your family safe and secure.
Monitor websites with Hoverwatch technology keylogger app
The browser history tracking feature in the Android keylogger app will show the addresses of each of the sites that your children visit. It will also show the exact time when they visited. Hoverwatch reports to you all URLs visited by the user of your Android device. It’s a powerful feature that will give you a clear picture of what is happening on your target phone and computer. Browser history tracking helps parents to take steps to avoid dangerous consequences, like phishing, online bullying, and exposure to objectionable content. Tip: This blog post will show you how to benefit from the most popular features of hover watch cell phone tracking software including browser history tracking. With this feature, parents can easily monitor their child’s internet use at school and avoid any dangerous consequences such as phishing, online bullying, getting exposed to objectionable content (adult content). Monitor websites with Hoverwatch technology.
Hoverwatch technology allows you to record calls
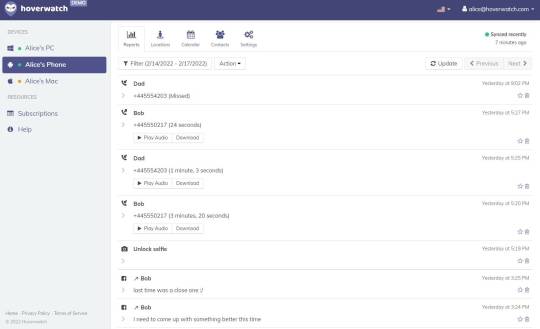
Hoverwatch app records the actual audio of the conversation that happens during phone calls. - The phone spy app allows you to view all calls that have been made from the target device. - Hoverwatch technology even records the date and time of each call with its duration. - The app is a comprehensive solution for parents who are worried about their child's safety and want to take measures towards it. So Hoverwatch has features that go beyond simple tracking of location, recording text messages or calls! Hoverwatch provides: - Call log history - View all incoming/outgoing calls with date and time stamps on Hoverwatch control panel along with contact name & number - Record surroundings feature – record the sounds surrounding your smartphone within 25 ft range by remotely activating the microphone on an Android device to know what exactly happened there while you. It will record the exact date time and duration of the call further the type of the call that is incoming outgoing missed call for an answer card can also be soon. It can also tell the time the location of the phone where the calls were received or made.
Track your child’s movements
Smartphones can help parents and children connect in case of an emergency. However, smartphones can also be a distraction. It provides a distraction and makes the child forget about their other duties including studying. GPS tracker helps you to know where your children are at any time in the day. The GPS tracking feature is one of the advanced features on the Hoverwatch spy app that records all activities done by the target phone with a GPS-enabled location. The Hoverwatch technology uses GPS, mobile data in the target device, and Wi-Fi technology to let parents know the location of the target phone. GPS technology is one of the most efficient and accurate ways to know where your children are located at any time of the day. Benefits of GPS trackers The GPS tracker helps you to view all locations visited by your target phone including their house, school, workplace, or other places they visit such as shopping malls and restaurants. It also shows how long each location was visited on a particular day throughout the week or month depending on the GPS tracking period you choose when using Hoverwatch spy app software. A GPS tracker can help parents feel at peace because they can track their children's smartphones if they go lost. This way, they can stay in touch with their kids during emergencies like kidnapping cases. With the Geolocation service, parents may keep track of their children's locations even when they are outside of the house. Furthermore, by determining the smartphone's location, parents may find out where their kids are. GPS location tracking is a great way for parents to keep their children safe. With Hoverwatch, you can be sure that your child's phone is always with them and they are not getting into dangerous situations. The app also records all calls and texts so you can be sure nothing inappropriate is happening. Hoverwatch lets you track the GPS location of any Android or iOS device without having physical access to it! This makes it perfect for keeping tabs on your loved ones, employees, or possessions. Simply install the Hoverwatch app on the target device and activate GPS tracking in the settings. You will then be able to see the exact location of the device on a map, as well as its current movement trajectory.
How legal is it to use the Hoverwatch spy app
Hoverwatch is a 100% legal and licensed spy app. It has been certified by the Federal Bureau of Investigation (FBI) and is used by law enforcement all over the world. You can use Hoverwatch without any fear of getting into trouble with the authorities. The app does not violate any privacy laws and is completely invisible to the user. In addition to GPS tracking, Hoverwatch also provides access to call logs, text messages, and browser history. This lets you see exactly what someone is doing on their phone or computer. Of course, it is your responsibility as well as a duty to monitor and track your children's activity online and guide them properly. By this, you will be able to protect the kids from the harmful effects that they are regularly subject to when they’re online using their smartphones. You can use Hoverwatch to monitor your employees as well. This will help you keep track of their productivity and ensure that they are not wasting time on non-work-related activities. Hoverwatch is a powerful phone tracking and monitoring application that lets you see exactly what someone is doing on their phone or computer.
Conclusion
In this age of internet technology, children are subject to diverse vulnerabilities such as the various evils on the internet. This is because today's children have access to the internet using smartphones. Hoverwatch is a computer and phone monitoring app that can help you protect your children from such vulnerabilities. Hoverwatch offers a free trial, so you can use all of its features to see if it's the right fit for you. With Hoverwatch spy app, parents now have an added layer of security against cyberbullying and online predators. As always, please use caution when giving any personal information to anyone on the internet - even people you know and trust. But with Hoverwatch, at least parents can have some peace of mind that their children are using their smartphones safely and responsibly. Remember, Hoverwatch offers a free trial period so that you can try out all its features before deciding if it’s right for you. The best part? Hoverwatch offers a free trial period so you can try out all its features before deciding if it’s right for you! So why wait? Try Hoverwatch today! Read the full article
0 notes
Text
Apps for spying on text messages
SpyApps is a powerful monitoring tool with some really great features. It's extremely simple to use, most likely among the easiest spy software I have tried. Also, their customer support is responsive and useful. What I really like about SpyApps is that it allows you to monitor an iPhone or iPad without having to jailbreak the device.
Like other spy mobile programs listed here, it's all of the basic features, including the ability to spy text messages, track GPS place, and monitor instant messages. But in addition, it has some unique characteristics which make it stand out from the crowd. Let us take a look at those features.
SpyApps lets you look at all of the SMS messages being sent and received via the target telephone. Together with SpyApps, you can:
- Look at the target phone's SMS inbox and sent messages.
- Get the names and numbers of SMS recipients and senders. - Take time and date stamps of each SMS message. - All SMS messages have been uploaded into your internet SpyApps control panel which you may access from anywhere with an online connection.
Why You Need This Feature
Are you worried about your children always tapping on their phone's display? Do you wish you could be aware of what they are always texting about? Are the employees using SMS messages as a way to prevent work? SpyApps allows you to know the facts about any SMS chat conversations which are performed on the target telephone. Simply logging into your SpyApps control panel gives you access to all SMS messages along with their own details.
Apps for spying on text messages
Nonetheless, it's a lot of features that many users could Discover helpful include the following:
- Social Media Monitoring: Monitor WhatsApp, Facebook, Twitter, iMessage, BBM, Skype, Viber, Instagram, and Email. - Real-time GPS Tracking: Know where the device is always with GPS-tracking technology. Location is exhibited on a map inside the control panel. - Stealth Camera: Initiate the phone's camera to have a secret image that is sent to your account. - Phone Monitoring: Monitor incoming and outgoing phone calls, time and date of calls, phone number of person calling or being called, and have a running log of all phone calls made. - Photos & Video Log: View photos & videos taken on the monitored mobile phone. - Browser Background: View all the sites they see on their phone.
- Text Message Monitoring: Monitor and record all SMS text messages. Keeps a running record of all text messages received and sent, and is viewable from within your control panel.
For anybody in the market for a minimal cost spy program for Android, SpyApps ought to be on top of your list. It's very simple to use and doesn't need any particular settings. In addition, when you buy the program, you get free upgrades for life.
2 notes
·
View notes
Text
Best Free Phone Tracker App Without Permission
If you want to spy on someone without their permission, you can find a free phone tracker app. Most of these apps allow you to chat through the phone and have access to their contact list. Some also have a panic button so you can get an alert if your kid is in danger. Depending on what type of phone tracker you choose, you may not need their permission. However, in most cases, you will need their permission before you can use the app.
Freespying is one of the best free phone tracker apps because it is available for both iOS and Android devices. This means that it works on both Apple and Android devices. You will need to root or jailbreak your target device to use this app, but it doesn't require that you know the exact location of the phone. It has a live chat support option to help you get the most out of the app.
Cocospy is another great free phone tracker. It allows you to track messages from companies and friends. This app is also good at finding out where your target phone has been recently. It also tracks browsing history. And, of course, you can use this app to find out about a person's activity and where they've been recently. So, whatever the situation is, you'll be able to keep an eye on the person you care about.

Cocospy is another great free phone tracker. It tracks everything on the target phone. It has a great live location tracker, and even supports multiple geofences. This application is compatible with Android phones and offers the best features without requiring your target's permission. It is also possible to spy on the user's location history and other personal information. It's easy to install and uses the phone's GPS location to track the owner's whereabouts. This app can be installed on a targeted phone without a hassle.
TruePeopleSearch is another powerful tracking app. It has a database of over 200 countries and has an intuitive interface. It is a good choice if you want to spy on someone without their knowledge. It's also available for non-rooted phones and is a rooted app.
The best free phone tracker app without permission can be installed on the target's mobile device without the user's knowledge. The top apps are those that are supported by a variety of different platforms, from Android to iOS. The main downsides of these applications are that they don't support the most popular operating systems. This means that if your child has a smartphone that has an iOS version, you won't be able to use this spying application.
The best free phone tracker app without permission will let you spy on a person's cell phone without their consent. The features of these apps include the ability to listen to the target device secretly, read messages, and keep a log of all calls and texts. If you are concerned about the safety of a loved one, you can use this tracking software to keep tabs on them and their movements. You can also use a spying app to keep tabs on your children or your spouse.
This is the best free phone tracker application without a target's consent. You can monitor a child's location, elderly parent, or spouse's cell phone remotely. You can also spy on WhatsApp and Facebook messages. There are many other reasons to use a cell phone tracking app without permission. This program is ideal for remote monitoring of your target's device. It is simple to use and has the highest functionality.
The best free phone tracker app without permission requires no installation and gives real-time updates every 15 minutes. It does not require rooting the target's phone or disabling Play Protect settings. The spying software works in stealth mode and uploads logs of all activities on the target's phone. Once installed, this application will allow you to spy on your target's phone anytime you want. You can even monitor their social media and search history.
0 notes