#Like theres certification classes for programming that someone might be interested in that might go well with streaming but are much more
Explore tagged Tumblr posts
Note
awww
just saw your tags asking what life advice sapnap gave flowtives. he was talking about why he doesn’t want to go to university because it’s expensive and he doesn’t want to be really broke for a degree he isn’t sure he’ll use and sapnap was talking about how if he really wants to he should take a year off to focus on streaming because university will still be there after even if it means graduating a year later. and flow was like I just don’t know how i would explain it to my parents because i’m not super famous or anything. and then sapnap was like if u want we can actually discuss this in depth off stream and i can give you more of my advice and stuff. and flow was like yeah okay i wanna do that later :(
THATS SO SWEET I'LL CRY ;;
#Also there are tech and vocational options if you want some skills but not a full dagree or just freel college isnt going to be your thing.#Like theres certification classes for programming that someone might be interested in that might go well with streaming but are much more#Achievable than a four year dagree both in time and cost#And now you have a skill to use for your goals and possibly to get a job to help uppirt you whole your streaming career gets started#You can also just take a gap year#Many many options
100 notes
·
View notes
Text
Week 7 Notes and Reflection
REFLECTION
Unfortunately I ran out of battery and lost the lectures notes for the second lecture. I had to reconstruct them using the class notes, Richard’s “slides” and what I remember. I’ll especially have to research more about Public Key Infrastructure later, it seems interesting!
Interesting lecture, I like how we found a mistake on the exam! I also liked the way Richard described Man in the middle attacks in Diffie-Hellman. There were lots of “homework” activities so I should do those!
I thought it was pretty insane you can write to memory using %n in printf! I wonder what the designers of printf were thinking?! They were like “o ye lets scan in some stuff using our printing function!!”
The extended lectures were cool - I found it weird that pressing that Command + S key on a Mac gives you root. There are so many interesting practical things with security... bug bounties, CTFs that you don’t really see in other areas of computing such as AI.
NOTES
Mid Term Exam
Question 5 Solution - Can’t brute force it by hand. The answer is F - type I /Type II error tradeoff.
Question 10 - The answer is D - easy to factorise a 64 bit number. Even 512 bit modulus is crackable. However even RSA is wrong for some reason.... All wrong!!
Proof of liveness - Like a replay attack, challenge response. Proof that there is someone there.
Richard expects you to go to all the lectures. Should have known Sun Tzu!
Diffie-Hellman - How do you set that shared secret up?
5^3^7 is the same as 5^7^3. Power raising is associative.
R -> 78125 -> S S-> 125 -> R
We don’t know R or S private key. Only the number they raised (5). Very difficult to solve the discrete log problem, to go backward to the private key.
When both sides receive their key, they both raise the value by their private key. Both becomes the same.
Forward Secrecy - protects the future messages.
Syria Castle - Defence in depth. The castle fell when the sieiging people forged a letter telling the castle people to surrender. Didn’t fall due to the defence of the castle.
CYBER LITERACY - VULNERABILITIES
A vulnerability is a weakness, and an exploit something that takes advantage of that.
Bug - software mistake. Sometimes bugs become vulnerability.
Types
Memory corruption - somehow the bad guy can change something in memory to allow the program to be under the control of the bad guy.
Buffer overflow
Stack and heap - FIFO temporary info about the functions are on the stack. Heap for allocated memory - dynamic memory allocation.
How functions are called in C - when control switches to another function, the function is frozen. Temporary info such as registers stored on stack. COMP1521 stuff.
Integer overflow - If you keep adding, it will go negative. This can cause it to maybe pass some tests.
Format String - Like Bird flu - Everyone has written buffer overflow bad code in the old days! Then people started patching it. Apparently they are coming back. C has crazy way of printing stuff using printf(). In the old days when you wanted to print hello world had to use printf(”%s\n”, “Hello World”). However no ever did that. Everyone just writes printf(”Hello World\n”). However someone might write name <- get user name. Then you want to print the name you write printf(name). E.g. my name is “%s Richard Buckland”. It will try and look lower down in the stack and print that out as the argument. %s will print out the contents of the stack until a null character. You can use %x to print out the next byte and print out hexadecimal versions of the stack. Printf(”%x %x %x %x”). Shows entire contents of stack. Could have passwords, return addresses. %n WRITES TO MEMORY. You can do arbitrary writes to memory.
Swiss Cheese - holes might line up! Holes overlapping and poke finger through. These sort of bugs are like that! Get lucky.
Stack Canary? Research that.
Shell Code - if you attacking a system, how nice it would be to get a private shell to come up and do whatever you want? Write some machine code that calls OS functions that makes shell pop up. This code is shell code. Put shell code into a buffer and run it.
Nop sleds - You can use buffer overflows to jump back to your buffer to run programs. However sometimes don’t know where in memory where the code is placed. Nice to have a bit of wiggle room. Just put lots of NOP operations - it will be like a slide into your code. Looking for NOP sleds - malware scanners. However whole lots of way to write NOP sleds without NOP.
If you find vulnerabilities, into will go into the National Vulnerability Database and CVN (Common Vulnerabilities and Exposures) and CNA (CVE Naming Authority).
Responsible disclosure - If you find a vulnerability, tell the vendor then CERT(eg CERT Australia). or you can sell it to the bad guys!
OWASP Top 10 list should know for top 10 vulnerabilities. Essentially the same every year!
BUG PUZZLES - Check slides
Example 1 - Integer overflow for the length. Get_user_length is UNSIGNED, but length is signed. Lots of implicit conversions between sign and unsigned. Then read will read the overflowed length value since read() takes in an unsigned length value, which might be bigger than 1024.
Example 2- Optimistic indenting
ASSETS
Security is to protect your assets. Sometimes we protect the wrong assets. Cold war - I wonder if the world will be here tomorrow? The most important asset is to protect mankind.
Door bell on the car - If you placed that in the car it went ding dong in his house. $5 car alarm first step into brilliance. What are you going to do when the ding dong happens? Might run down there and get killed!! The real asset is the window of the car, not the money! Leave the window open! Got wallet stolen, but got AIDS. Easy to protect the wrong thing.
At the uni’s security review was all machines. Uni assets are students, reputation, user data, staff. The trick is, what you should do is the assets - what are you trying to protect? Ask people - junior, senior people. Review the list of assets every year/month. Real weakness is something you don’t see - blind spot. Try and find the things you haven’t seen.
Strategies for Identifying the Assets
Regularly surveying the values of people of the involved in what you are protecting. Multiple pairs of eyes is a good asset.
Develop a sensible plan - well designed to tease this information out of them. Humans are generally poor at regurgitating everything they know, however they are generally very good critics.
Periodically revise current list of assets. Don't set and forget. Values and assets of an organisation can drift.
Examples
Team America
Richard's wallet vs Richard with AIDS
Car doorbell
Leave windows open?
Share registry - no more paper trails, everything is recorded electronically. Land title database was privatised. What are the risks?
Coke formula
Parliament - a collection of people that hold particular importance together.
Valuing the Assets - Defining what is important
Categorising types of assets
Tangible Assets: Those that are easily given a value
A gold chain valued at some relatively static amount
The jewellery in a jewellery store.
Intangible Assets: These cannot be easily and objectively be valued
Company secrets
Availability of services
Employee Morale & Security
Customer information
* Monetary + psychological/emotional costs
* Difficult <> Don't do
Examples:
Company secret - what is at stake?
QOS Guarantees
Strategies for assigning values to assets
Survey what many people think
no single person or group should be solely evaluating the assets;
Examples of the information that should be gathered are as follows:
"How much money would you lose where this data center to go down for 24 hours?".
"How much will you lose if your company is disconnected to the internet for 3 hours?".
Examples
In assessing the value of a park
Picasso
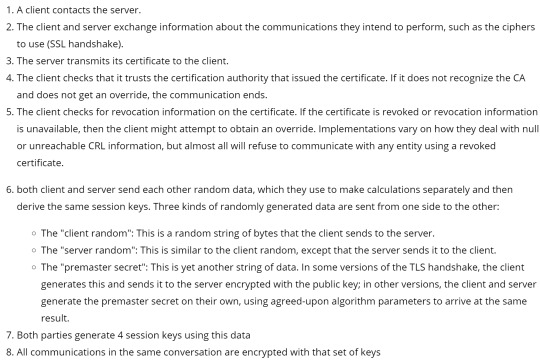
Diffie-Hellman - Only provides confidentiality and integrity? Does not provide authentication.
Web of Trust (PgP) - Research this
Public Key Infrastructure (PKI)
SSL/TLS
Read Bruce Schneier's paper https://www.schneier.com/academic/paperfiles/paper-pki.pdf
passports (links photo with name, certified by office)
x509 certificates (links public key with domain (and maybe some other info))
padlock in your browser
look at some certs
CAs, root certificates, RAs, pay money to browser manufacturer??!! (check out your web browser)
conflicts of interest
most google search pages on SSL written by vendors
it was the blockchain of the 2000s
self signed, domain verification, organisational verification, extended verification. (ha!)
what if anything are the risks of self-signed?
safety vs identity
the green bar
session keys - the TLS handshake (4 keys)
why use session keys rather than using RSA for all?
wildcards
3 main certificate authorities: Symantec, Comodo, GoDaddy
homework : find examples of (serious) fraudulant certificates being issued
Certificates don’t protect against gooooogle.com
TLS handshake example
BUG BOUNTIES (From notes, I lost mine)
Crowd-Sourced Bug Bounty Websites
Public: Hackerone, bugcrowd
Private: Synack
Often have criteria of whats in/out of scope, as well as what kind of bugs they won’t accept. For example websites that they don’t want you touch
Tips
Learn web apps
Usea a wide scope → bigger net = more bugs
Look for software updates, or assets that have recently changed
Look for publicly disclosed reports → Can see prior bugs that have been found/exposed. If a bug has occurred once, theres a chance it will occur again
Pentesting (From notes, I lost mine)
Fuzzing
Automate process - a program that continually adds input
Some fuzzers are aware of input structure, and some even are away of program structure
Fuzzers aren't precise, but can test a large amount of inputs
Fuzzing software - afl (the way to go apparently)
Mutation strategies - bit flips, byte flips, arithmetic, havoc (combination
Use fuzzing to test your own software
Homework: Do the fuzzing tutorial
0 notes
Text
Your Career Is a Multimillion-Dollar Investment, So Manage It Wisely
Over the course of a 40-year career, the average American with a bachelors degree can expect to earn about $1.8 million. When viewed by gender, the cumulative earnings shift somewhat, with women taking home $1.4 million over four decades compared to an average of $2.1 million for men, according to estimates by theIndiana Business Research Center at Indiana Universitys Kelley School of Business, The substantial gender pay gap aside, when viewed in this way, it becomes far more obvious just how valuable ones career can be. And those figures are just the averages. For those who manage a career as actively and shrewdly as they might an investment portfolio, aggressively working to maximize its potential as a financial asset all along the way, a careers worth of earnings could be worth far, far more. The most important part of thinking of your job as an investment is actually pretty basic: realizing that you dont just have to make an investment, you have to manage it as well, says from Emmet Savage, chief investor at MyWallSt, a learning and investing app. What does that mean exactly? Here are some ways to help make the most of your career arc and the amount of financial gain, growth, and opportunity you realize over the course of a lifetime. Change Your Mindset In many ways, treating your career as a multimillion-dollar investment begins with altering the way you view work in general. For most people, a job is just that. Something they do as a must to pay bills without really thinking about their end goal or ideal outcomes, says 35-year-old Greg Dorban, chief marketing officer for Ledger Bennett. Dorban, however, never viewed work on such simplistic terms. In the space of just five years, he progressed from intern to co-owner of a multinational marketing agency that generates eight-figure revenues, a meteoric rise he attributes to starting out with a much broader view of work than merely making ends meet. Early on Dorban established a North Star for himself the goal of owning a business in short order. This shining beacon guided his subsequent steps, inspiring him to take actions to rise above the day to day hustle of earning a living, including consistently investing in himself and in the training needed to maximize his professional potential. Building the right skills will be the best investment you can make as the payoff positively impacts so many areas of your life, not just your wallet, says Dorban. The underlying message of his story, Dorban adds, is that when considering your career, allow yourself to think bigger than simply bringing home a paycheck to cover the next rent or mortgage payment. Then identify the training, new skills, or specific experiences and growth opportunities needed to reach that higher goal. Maximize the Benefits of Everything You Do The idea of always being on and bringing your professional A-game wherever you go can be off-putting to some, but theres something to be said for recognizing the potential of all situations, including the most ordinary of moments. Erica McCurdy, a certified master coach and managing member of McCurdy Solutions Group, calls this utilizing and maximizing the benefits of everything you do, which she says can accelerate the power of your time and efforts with regard to your career. This includes making sure to introduce yourself to everyone at a meeting and at every place you pause on the way to and from the meeting, says McCurdy. It also means collecting business cards, connecting with each person on LinkedIn, including a personal message, and scheduling coffee meetings with those people who pique your interest. Never forget to send thank you notes to those who helped make the day possible, adds McCurdy. Finish up the day by updating your career and contact log so you dont lose any valuable information. There are countless points along the way where you might come into contact with someone who can open a new door for you or somehow play a pivotal role in moving your career to the next level, so keep your eyes open to the possibilities. Dont Pass Up Free Money Maximizing your earnings over the course of a career also means taking some very practical steps as well with the financial opportunities your career presents. This includes being sure to enroll in an employer sponsored 401(k) plan, particularly if the employer matches your contributions, as that match is free money and can add up over the course of a lifetime. The first and best advice I give to new hires is to contribute the maximum to their 401(k), says careers analyst Laura Handrick of FitSmallBusiness.com. Many dont understand the concept of compound interest, so as an HR professional, its important to educate employees. Handrick also suggests that if your company offers financial planning workshops, be sure to attend. This is another opportunity to expand your financial skills at no cost to you. But 401(k) matches are merely one example of the financial opportunities available through your workplace. Take Advantage of Tuition Reimbursement Many companies offer tuition reimbursement programs to help cover the costs of continuing education for employees who want to go back to school and obtain degrees or certifications. Brent Michaels, a registered nurse and creator of the website Debt & Cupcakes, says these offers have financial value on multiple levels. I graduated from nursing school with minimal student loan debt and have been able to work toward my Bachelor of Science in nursing and other certifications without spending a dime, he explained. In addition, as I complete classes, I grow professionally and personally, and the knowledge from these courses helped me secure promotions and business opportunities that would not have been available to me otherwise. Even just earning certifications, says Michaels, allows him to stand out as a motivated employee, which pays off in spades over the long run. and On the Job Training Obtaining an advanced degree or certification isnt the only way to distinguish yourself and maximize career earning potential. Many employers offer on the job training related to specific tasks the organization deems important, said Michaels. Dont pass up this opportunity, either. You may also want to actively search out such opportunities if theyre not openly available. I knew that project management was needed for a promotion I was hoping to obtain in the future, but I had no experience. I intentionally volunteered to work on projects so that I could network with the project managers, he explained. I developed relationships and obtained free project management training. This cost nothing more than my time, and allowed me to secure a promotion a few years later that increased my salary by over 25 percent. Networking Your network is everything; use it to maximize your ROI. Lets face it, you can have the best resume, you can be the best employee out there, but having people of trust who can vouch for you is irreplaceable. Nothing can beat that, begins Peter Koch, creator of the site Seller at Heart, which is focused on how to save and make extra money. Koch is obviously on to something: As many as 85% of jobs are filled via networking,according to a LinkedIn survey. This means that when youre searching for new career opportunities to boost your pay, it really is who you know, continues Koch. If youre able to make good impressions on others in your field and provide value to them, theyll be happy to recommend you next time their company has an opening you could fill. Employers want to build a team of people they trust, and a personal recommendation from a colleague will always carry more weight than an unknown applicant emailing their resume. Need an added reason why networking is so important? Switching jobs is often a better way to increase your salary more significantly, as opposed to waiting for a raise at your current company. In fact, those who leave their employers to take a new job are realizing pay raises that are about one-third larger than those who stay put. As of this past July, wages for job hoppers grew 3.8% from a year earlier, compared with 2.9% for those who opted to stay with their current employer, according to data from the Federal Reserve Bank of Atlanta. Lean Out All of these tips and tactics really lead to what career coach Denise Riebman refers to as leaning out with your career.Ribeman recently gave a keynote speech about building your career capital heres what that means. Its really about doing a skill and knowledge gap analysis and asking where you do you want to go to in your career and investing in yourself to get there, she explains. See who is a couple chapters ahead of you and identify the gaps to get there. And like Koch, Riebman says a critical part of leaning out means actively expanding that professional network, or having what she calls an open network, which will ultimately help you to be more successful professionally and financially over the long term. Traditionally people like to stay in our tribes, among people we know, people we went to school with, said Riebman. The problem is that those people have same ideas and same information as you. Having an open network is about building your career capital. Mia Tayloris an award-winning journalist with more than two decades of experience. She has worked for some of the nations best-known news organizations, including the Atlanta Journal-Constitution and the San Diego Union-Tribune. Read more: https://www.thesimpledollar.com/your-career-is-a-multi-million-dollar-investment/
0 notes