#IoT network protocols (e.g.
Explore tagged Tumblr posts
Text
IoT Network Protocols (e.g., MQTT, CoAP)
Harness robust IoT network protocols, including MQTT and CoAP, for seamless connectivity!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
GTPv2 vs. GTPv1: What Network Engineers Need to Know
Let us understand the importance of selecting the right GPRS Tunneling Protocol (GTP) version for a smooth core network operation. As networks evolved, so too did GTP, from GTPv1, which was used in GPRS and early 3G, to GTPv2, optimized for LTE and 5G. Here is a quick comparison between them for network engineers:
Key Differences · Efficiency: GTPv2 minimizes signaling overhead by combining procedures like session setup and bearer establishment, unlike GTPv1’s multi-step process. · Scalability: Designed to handle millions of connections and high throughput, GTPv2 outperforms GTPv1, which is better suited for smaller networks. · Security: GTPv2 introduces stronger safeguards against replay attacks and spoofing, ensuring robust session integrity. · Interoperability: GTPv2 supports seamless transitions in mixed 3G/4G environments, maintaining backward compatibility with GTPv1. · Advanced Features: GTPv2 enables critical LTE and 5G functionalities like Control and User Plane Separation (CUPS) and Carrier Aggregation.
IPLOOK GTP-Router Highlights IPLOOK's GTP-Router acts as a GTP proxy, managing GTPv1 and GTPv2 control-plane traffic. It dynamically analyzes IMSI and routes traffic to the appropriate Gateway (GGSN/PGW) based on configurable parameters. With its NFV-based virtualized architecture, it supports flexible roaming services, making it an ideal solution for 5G networks.
Use Cases GTPv1: Still relevant in legacy 2G/3G networks and small-scale deployments. GTPv2: Required by LTE and 5G networks, especially by those applications that require low latency and high throughput (e.g., IoT, eMBB).
Takeaway GTPv1 was instrumental in forming early mobile networks, but GTPv2 is essential for fulfilling modern telecom environments
0 notes
Text
The Future of Connectivity: How IoT Testing Ensures Seamless Performance

The Internet of Things (IoT) has revolutionized the way we interact with technology, creating a more connected world than ever before. From smart homes to industrial IoT applications, the possibilities seem endless. However, as more devices become interconnected, ensuring their smooth performance, security, and reliability becomes increasingly complex. This is where IoT testing plays a crucial role. By rigorously testing IoT systems, businesses can guarantee their devices function optimally in a dynamic environment. In this blog, we will explore the significance of IoT testing, the role of test automation services, and how IoT software testing and test automation companies ensure seamless performance in the world of connectivity.
The Growing Need for IoT Testing
As the number of IoT devices continues to increase, so does the complexity of their networks. These devices must work seamlessly with other devices, networks, and cloud systems to deliver real-time data and ensure user satisfaction. IoT testing involves assessing the functionality, performance, security, and reliability of connected devices to ensure they meet quality standards and perform as expected.
Some of the key aspects that IoT testing addresses include:
Interoperability: Ensuring that devices work together within a connected ecosystem, irrespective of manufacturer or platform.
Security: Validating that IoT devices are protected from vulnerabilities and cyberattacks.
Scalability: Verifying that devices can handle increasing numbers of connections and data loads without compromising performance.
Performance: Assessing whether the devices operate efficiently under different conditions and network environments.
The Role of Test Automation in IoT Testing
Testing IoT devices and systems manually is not only time-consuming but can also result in inconsistent results, especially as devices scale and evolve. This is where test automation services come into play. Automating the testing process provides several advantages, particularly in the context of IoT systems:
Speed and Efficiency: Automated tests can run much faster than manual testing, making it easier to identify issues early in the development cycle.
Scalability: As IoT networks grow, automated tests can easily scale to test more devices or more complex network environments.
Reusability: Once automated tests are created, they can be reused multiple times across different IoT projects, ensuring consistency and reducing redundancy.
Continuous Testing: Automation allows for continuous testing, ensuring that every new update or change to an IoT system doesn’t introduce new issues.
By incorporating test automation services, businesses can ensure faster time-to-market for their IoT devices and improve overall product quality.
IoT Software Testing: Ensuring Seamless Connectivity
IoT software testing is critical to ensuring that the applications running on IoT devices perform flawlessly. Whether it's a mobile app interacting with a smart device or the firmware running on the device itself, IoT software testing ensures that every component of the system functions correctly.
Key areas of IoT software testing include:
Device Communication: Testing the communication protocols between devices and their central systems (e.g., Bluetooth, Zigbee, Wi-Fi).
Cloud Integration: Ensuring that data from IoT devices is seamlessly transmitted and integrated with cloud platforms for processing and analysis.
Real-Time Data Processing: Verifying that the device can handle and process data in real time without lag or failure.
With more devices becoming interconnected, software testing becomes even more critical to ensuring that the entire ecosystem operates smoothly and that there are no disruptions in service.
How Test Automation Companies Enhance IoT Testing
The complexity of IoT systems requires expertise in both the technology itself and in testing strategies. This is where test automation companies specialize in delivering end-to-end solutions for IoT testing. These companies focus on creating custom test automation frameworks designed to handle the unique challenges of IoT environments.
Here’s how test automation companies contribute to seamless IoT performance:
Custom Frameworks for IoT Testing: Test automation companies create tailored frameworks that cater to the unique demands of IoT systems, ensuring accurate and comprehensive testing of device behavior, network interactions, and software functionalities.
Expertise in Multiple IoT Protocols: These companies have expertise in testing a wide range of IoT communication protocols, ensuring that devices can communicate effectively across different platforms and networks.
Real-World Scenarios: Test automation companies simulate real-world scenarios to assess the behavior of IoT devices in different environments, such as fluctuating network conditions or high usage volumes, ensuring devices remain reliable in diverse situations.
Security Testing: Given the increased risk of security breaches in IoT networks, these companies conduct in-depth security testing to identify vulnerabilities and mitigate potential threats before devices are deployed.
By working with test automation experts, businesses can ensure that their IoT systems are thoroughly tested for performance, security, and scalability, reducing the risk of issues post-deployment.
The Future of IoT Testing: Preparing for a Connected World
As IoT continues to evolve, so will the requirements for IoT testing. The future will see even more devices interconnected, higher data volumes, and more sophisticated use cases across industries like healthcare, automotive, and manufacturing. This means IoT testing will need to be more efficient, automated, and robust.
AI and Machine Learning: The integration of AI and machine learning in testing will make it possible to predict potential failure points, automatically generate test scenarios, and improve the overall accuracy of tests.
5G and Edge Computing: With the rollout of 5G and the rise of edge computing, IoT devices will experience higher speeds and greater data processing capabilities. Testing will need to evolve to address new challenges in connectivity, data transmission, and real-time processing.
Expanded Automation: As IoT systems grow in complexity, automation will continue to play a central role in managing large-scale test scenarios, allowing businesses to maintain high-quality standards while speeding up the testing process.
Conclusion
The future of connectivity lies in the successful implementation of IoT systems that are secure, reliable, and capable of handling increasingly complex tasks. IoT testing is crucial to achieving this goal, ensuring that devices and software perform seamlessly in real-world environments. By leveraging test automation services, embracing IoT software testing, and partnering with test automation companies, businesses can deliver high-quality IoT solutions that provide value to users and contribute to a more connected world. As the IoT landscape continues to evolve, testing will remain a critical factor in ensuring seamless performance and driving innovation in this rapidly expanding field.
#automation#development#software#devops#futuretech#information technology#applications#projectmanagement#datasecurity#python
0 notes
Text
Why Private 5G is the Future of Outdoor Networks
Why private 5G? In today’s digital age, smooth and reliable wireless network coverage is important for any environment. This gets increasingly difficult as the environment gets larger indoors and/or outdoors. Whether it’s a university, corporate campus, or a large industrial complex, ensuring robust outdoor coverage can be especially challenging, yet also crucial for enhancing communication, productivity, and overall user experience.
Options to effectively provide outdoor wireless coverage are limited in both the number of choices and due to high costs. Public 5G is limited by the availability of public towers in each area. It can also be an expensive proposition with per subscriber pricing. Additionally, it compromises the security and privacy posture of an organization by requiring private traffic to traverse via public cellular networks.
Private 5G cellular coverage avoids the above problems with public 5G and surpasses Wi-Fi and wireless technologies like microwave in outdoor environments needing broad coverage, high data rates, low latency, and robust connectivity. These factors make private cellular the preferred choice for providing outdoor wireless connectivity:
Extended Range: Private 5G requires fewer APs than Wi-Fi to cover large outdoor areas, reducing costs and complexity by utilizing existing power and Ethernet on tall structures.
Robustness: Built for harsh environments, private 5G is more reliable for industrial use and avoids Wi-Fi interference issues, making it ideal for IoT applications.
Smooth Mobility: With superior handoff capabilities, private 5G ensures uninterrupted connectivity for moving devices, perfect for logistics and mobile workforce needs.
Built-In Security: Advanced encryption and security protocols make private 5G more secure than Wi-Fi, which is vulnerable to outdated encryption standards.
Dedicated Spectrum: Operating on licensed or lightly licensed bands, private 5G minimizes interference, ensuring reliable and predictable performance.
Customization: Private 5G can be tailored for specific needs like low latency, high security, and industrial automation, enabling smart manufacturing and critical infrastructure applications.
Planning an outdoor private 5G deployment As with any wireless deployment, coverage planning is required for private 5G to scope the required number of APs and attached antennas to be deployed, including their type, site location, direction, and installation material for each.
These are key deployment considerations for an effective outdoor private 5G networks for your campus:
Define Objectives and Requirements Identify specific use cases (e.g., high-speed internet, IoT, AR, autonomous vehicles) and service locations. Establish KPIs like data rates, latency, coverage, and device density. Estimate traffic volume based on user and device count.
Conduct a Site Survey Evaluate existing infrastructure (Wi-Fi, fiber, cellular coverage), analyze coverage and interference zones, and account for environmental factors like terrain and obstructions.
Network Design and Planning Strategically place macro and small cells to optimize coverage and mobility in high-traffic areas. Select appropriate 5G radios and antennas based on performance needs and site conditions.
Backhaul and Connectivity Use reliable, high-capacity backhaul (fiber or microwave links) with redundancy to ensure uptime and reliability.
By defining clear objectives, surveying sites, and designing robust infrastructure, you can deliver reliable private 5G connectivity tailored to diverse outdoor environments, enhancing performance and user satisfaction.
#private 5g#private 5g deployment#what is private 5g#what is 5g network#private 5g networks#what is a private 5g network
0 notes
Text
IT Sectors jobs in Jobseekerspage.com
JobseekersPage.com offers IT sector job listings across various roles, including software development, cybersecurity, and data analytics. The platform supports advanced search filters for location, experience level, and job type, simplifying the job search process for candidates. Visit JobseekersPage.com to explore current opportunities and apply.
IT (Information Technology) sectors offer a diverse range of jobs, covering everything from software development to cybersecurity. Below is a breakdown of key areas within the IT sector and the types of jobs commonly found in each:
1. Software Development
Roles:
Front-end Developer
Back-end Developer
Full-stack Developer
Mobile App Developer
Game Developer
Skills Required:
Programming languages (e.g., Java, Python, JavaScript, C++)
Frameworks (e.g., React, Angular, Spring)
Version control (e.g., Git)
2. Data Science and Analytics
Roles:
Data Scientist
Data Analyst
Machine Learning Engineer
Business Intelligence Analyst
Skills Required:
Data analysis tools (e.g., Excel, Tableau, Power BI)
Programming languages (e.g., Python, R)
Machine learning frameworks (e.g., TensorFlow, Scikit-learn)
SQL and data visualization
3. Cybersecurity
Roles:
Cybersecurity Analyst
Ethical Hacker/Penetration Tester
Security Architect
Incident Response Analyst
Skills Required:
Network security
Ethical hacking tools (e.g., Metasploit, Wireshark)
Certifications (e.g., CISSP, CEH, CompTIA Security+)
4. Cloud Computing
Roles:
Cloud Engineer
Cloud Architect
DevOps Engineer
Site Reliability Engineer (SRE)
Skills Required:
Cloud platforms (e.g., AWS, Azure, Google Cloud)
Containerization tools (e.g., Docker, Kubernetes)
Automation and CI/CD pipelines
5. Networking
Roles:
Network Engineer
Network Administrator
Wireless Communication Specialist
Skills Required:
Networking protocols (e.g., TCP/IP, DNS)
Hardware configuration
Certifications (e.g., CCNA, CCNP)
6. Artificial Intelligence and Robotics
Roles:
AI Engineer
Robotics Engineer
Natural Language Processing (NLP) Specialist
Skills Required:
AI tools (e.g., OpenAI, IBM Watson)
Robotics programming (e.g., ROS, MATLAB)
Deep learning techniques
7. IT Management and Support
Roles:
IT Project Manager
IT Support Specialist
System Administrator
Database Administrator
Skills Required:
Project management methodologies (e.g., Agile, Scrum)
ITIL and service management
Database tools (e.g., Oracle, MySQL)
8. Web Development
Roles:
Web Developer
Web Designer
SEO Specialist
Skills Required:
HTML, CSS, JavaScript
Content management systems (e.g., WordPress)
SEO and web analytics
9. Emerging Technologies
Roles:
Blockchain Developer
IoT Engineer
Quantum Computing Researcher
Skills Required:
Blockchain frameworks (e.g., Ethereum, Hyperledger)
IoT platforms and sensors
Quantum programming (e.g., Qiskit)
10. Product and UX Design
Roles:
UX/UI Designer
Product Manager
Interaction Designer
Skills Required:
Design tools (e.g., Figma, Adobe XD)
User research and prototyping
Agile product development
11. IT Consulting
Roles:
IT Consultant
Systems Analyst
Technology Strategist
Skills Required:
Business acumen
Systems integration
Technical writing and documentation
0 notes
Text
OTA Software Updates: Ensuring Reliability and Security in Connected Devices
Over-The-Air (OTA) software updates have become indispensable in the realm of connected devices, offering a seamless way to enhance functionality, fix bugs, and improve security without requiring physical intervention. This article explores the critical aspects of OTA updates, their benefits, challenges, and best practices for ensuring reliability and security.
Understanding OTA Software Updates
Definition: OTA software updates enable devices to receive and install firmware, software patches, and configurations remotely, typically over secure wireless networks.
Components:
Client Software: Installed on devices to receive and process updates.
Server Infrastructure: Manages update distribution, ensures authentication, and secures data transfer.
Communication Protocols: Utilizes HTTPS, MQTT, CoAP, etc., for secure and efficient update delivery.
Importance of OTA Updates
Enhanced Security:
Enables prompt deployment of security patches and fixes vulnerabilities, reducing exposure to cyber threats.
Implementation of encryption and authentication protocols ensures updates are tamper-proof and secure.
Operational Efficiency:
Reduces downtime and operational disruptions associated with manual updates.
Facilitates quick rollout of new features and improvements, enhancing device performance and user satisfaction.
Challenges and Considerations
Security Risks: Vulnerabilities in OTA mechanisms can be exploited if not properly secured, necessitating robust security measures and regular audits.
Compatibility and Reliability:
Ensuring updates are compatible with diverse device configurations, software versions, and network environments.
Thorough testing and validation processes are crucial to mitigate risks of unintended consequences or system failures.
Best Practices for OTA Updates
Secure Protocols: Implement strong encryption (e.g., AES-256) and authentication mechanisms (e.g., digital signatures) to protect OTA communications.
Incremental Updates: Deploy incremental updates to minimize data usage and ensure efficient bandwidth management.
User Consent and Transparency: Obtain user consent for updates and provide transparent information about update contents and benefits.
Industry Applications
Automotive Sector: OTA updates enable automakers to remotely improve vehicle performance, safety features, and infotainment systems.
IoT Devices: Smart home devices, industrial sensors, and healthcare equipment benefit from OTA software updates for functionality enhancements and security enhancements.
Future Directions
AI-Enabled Updates: Leveraging AI and machine learning for predictive analytics to anticipate update requirements and optimize deployment strategies.
Blockchain Integration: Exploring blockchain technology to enhance OTA update security and transparency.
Conclusion
OTA software updates play a pivotal role in ensuring the reliability, security, and performance of connected devices across industries. By adopting best practices and leveraging advanced technologies, organizations can effectively manage OTA updates to enhance user experience, mitigate risks, and stay ahead in an increasingly connected world.
0 notes
Text
Unlocking the Future with IoT Testing: Ensuring Seamless Performance and Security in a Connected World
In a world where devices are constantly communicating, IoT (Internet of Things) has emerged as a transformative technology, connecting everything from home appliances to industrial machines. But with this increasing connectivity comes the critical need to test IoT systems rigorously. In this blog, we’ll explore the essentials of IoT testing, its challenges, and best practices to ensure robust performance and security.

Understanding IoT Testing
IoT testing refers to the process of evaluating the performance, functionality, security, and scalability of IoT devices and systems. It’s a unique type of testing because IoT systems are highly complex, involving multiple layers of technology, including hardware, firmware, software, and network infrastructure. Given that IoT devices often operate in unpredictable environments and need to function in real-time, IoT testing must cover various aspects to guarantee seamless interoperability, data security, and reliability.
Why IoT Testing Matters
The IoT ecosystem connects devices from different manufacturers, protocols, and networks. Here’s why rigorous IoT testing is essential:
Ensuring Device Compatibility: Devices must work seamlessly with each other and across various networks.
Security and Privacy: IoT systems are a prime target for cyberattacks, so security testing is crucial to protect data integrity.
Reliability in Real-world Conditions: Testing ensures devices can withstand environmental factors like extreme temperatures, fluctuating connectivity, and battery limitations.
Compliance with Regulations: IoT systems must meet regulatory standards, especially in industries like healthcare, automotive, and finance.
Key Challenges in IoT Testing
Despite its importance, IoT testing comes with unique challenges due to the nature of interconnected systems:
Complexity of Multi-layered Architecture: IoT systems involve a mix of hardware and software components, making it challenging to create comprehensive test cases that cover each layer.
Diverse Communication Protocols: IoT devices communicate using various protocols (e.g., MQTT, HTTP, CoAP), which requires testing for compatibility across these different standards.
Network Variability: IoT devices are often deployed across different networks with varying bandwidths and latencies, impacting performance and reliability.
Data Privacy Concerns: Testing for data security and privacy is complex, as IoT devices collect and transmit sensitive user information, making them attractive targets for hackers.
Types of IoT Testing
To overcome these challenges, IoT testing needs to cover a range of testing methodologies. Here are some essential types:
Functional Testing: Ensures the device functions correctly under various conditions and meets all requirements. For example, a smart thermostat should adjust temperatures based on sensor readings.
Performance Testing: Verifies the system’s response time, scalability, and stability under different network conditions and load scenarios. This helps identify potential bottlenecks.
Security Testing: Focuses on identifying vulnerabilities to prevent data breaches. Testing should cover encryption, authentication, and access control to protect user data.
Compatibility Testing: Ensures IoT devices can communicate effectively with each other, irrespective of the manufacturer or operating system.
Usability Testing: Evaluates the user experience, ensuring the device is easy to set up, configure, and use.
Reliability and Scalability Testing: IoT devices often operate in unpredictable environments. Reliability testing ensures devices function correctly over time, while scalability testing confirms they can handle increased demand as the IoT network expands.
Best Practices for Effective IoT Testing
To maximize IoT testing efficiency and effectiveness, here are some proven best practices:
1. Create Realistic Test Environments
IoT devices interact with real-world objects and network conditions, so it’s vital to simulate these environments in the testing phase. Emulate conditions such as low network bandwidth, high latency, and interference to better understand how devices will perform under varying scenarios.
2. Implement Automation
Automated testing helps address the complexity and volume of testing required for IoT systems. Using automation tools and frameworks can significantly speed up testing and enhance coverage. Automation is particularly useful for regression testing, as it ensures new updates do not impact existing functionality.
3. Prioritize Security Testing
Given the rise in cyber threats, IoT security testing should be a top priority. Conduct penetration testing to identify and mitigate vulnerabilities. Regular security audits and adherence to industry standards (e.g., GDPR, HIPAA) can further strengthen security protocols.
4. Optimize for Power Efficiency
Many IoT devices are battery-operated, so testing for power efficiency is essential. Test the impact of different tasks on battery life, optimizing the device to reduce energy consumption without sacrificing performance.
5. Plan for Scalability
IoT networks tend to grow, adding more devices and expanding functionality over time. Test for scalability to ensure your IoT system can accommodate new devices, increased data load, and extended geographical reach without compromising performance.
6. Monitor in Real-Time
Deploying IoT devices with real-time monitoring tools can help gather insights from actual usage data. Use analytics and logging tools to track performance, errors, and usage patterns. This data is invaluable for identifying issues and improving future iterations.
Future of IoT Testing: Trends to Watch
IoT testing continues to evolve as new advancements emerge. Here are some trends shaping the future of IoT testing:
AI-Driven Testing: Artificial Intelligence (AI) can help identify patterns and predict potential issues, making IoT testing more intelligent and proactive. AI algorithms can be used to create self-healing systems that resolve issues automatically.
5G Connectivity Testing: With the adoption of 5G, IoT devices will have access to faster and more reliable networks, enabling new testing challenges around ultra-low latency and high bandwidth requirements.
Edge Computing: As IoT devices increasingly leverage edge computing, testing must account for how data is processed at the network's edge rather than in a central cloud. This requires additional performance and latency tests.
Blockchain for IoT Security: Blockchain technology has the potential to enhance IoT security by providing a decentralized model for data storage and verification. Testing protocols will need to adapt to validate the reliability of blockchain integrations.
Conclusion
IoT testing is a vital component in the development and deployment of IoT systems. As the IoT landscape continues to expand, robust testing strategies will play a crucial role in ensuring these devices are reliable, secure, and user-friendly. From functional testing to advanced security measures, investing in comprehensive IoT testing can help deliver a safer, more connected experience for users and create a solid foundation for the future of IoT.
By following best practices and staying updated on emerging trends, organizations can build reliable IoT products that inspire trust and innovation, keeping pace with the demands of a connected world.
Are you ready to unlock the potential of IoT? Embrace IoT testing to secure a future of seamless connectivity and reliability.
0 notes
Text
Everything You Need to Know About Leasing an IPv4 Address
In the ever-evolving landscape of the internet, managing IP addresses is a critical task for businesses, data centers, and network administrators. One of the more nuanced aspects of this is the concept of leasing IPv4 addresses. With IPv4 addresses being a limited resource due to the finite number of available addresses (about 4.3 billion), leasing IPv4 addresses has become a valuable option for many organizations. In this article, we will explore what leasing IPv4 addresses is, why it’s important, and how you can go about obtaining them.
What is an IPv4 Address?
To understand why leasing an IPv4 address is important, we first need to understand what IPv4 is. IPv4, or Internet Protocol version 4, is the fourth version of the Internet Protocol (IP) used to identify devices on a network. Each IPv4 address is a 32-bit number, typically written in four octets (for example, 192.168.1.1).
IPv4 addresses are categorized into several types, such as public, private, static, and dynamic, with public IPv4 addresses being used to identify devices on the internet. However, the availability of new IPv4 addresses has been exhausted in many regions, leading to the concept of IP address leasing as a solution.
Why Lease an IPv4 Address?
As demand for IP addresses continues to grow, particularly with the expansion of IoT devices, cloud services, and global internet traffic, the availability of IPv4 addresses has become scarce. This scarcity has led to a thriving market for leasing IPv4 addresses. Let’s dive into some of the primary reasons why leasing an IPv4 address might be the right solution for your business:
1. Cost-Effectiveness
Purchasing IPv4 addresses can be expensive, especially if you need a large block. Leasing provides a more affordable alternative, allowing businesses to pay for only what they need for a specific period. This is ideal for companies that need temporary IP space or are unsure about long-term growth.
2. Immediate Availability
IPv4 addresses are scarce, and acquiring them can be a time-consuming process. Leasing can provide immediate access to the addresses you need, without waiting for a purchase or allocation through other methods (like auctions or waiting lists).
3. Flexibility
Leasing offers flexibility in terms of the length of the lease and the number of addresses. Whether you need addresses for a few months or several years, leasing allows you to tailor the arrangement to suit your needs.
4. Avoid IP Shortages
If your business needs to scale quickly, leasing addresses can ensure that you’re not stuck without enough IPs to accommodate growth, especially when managing web services, cloud infrastructure, or new devices on your network.
5. Compliance with Regulatory Requirements
For some businesses, having a public IP address is essential for regulatory compliance, security measures, or service requirements. Leasing IPv4 addresses ensures you remain compliant without the need for a large upfront investment.
How Does IPv4 Address Leasing Work?
Leasing an IPv4 address involves renting a block of IP addresses from another organization or a leasing service. The process usually follows these key steps:
1. Choose a Leasing Provider
There are various providers, including Internet Service Providers (ISPs), brokers, and specialized companies that facilitate the leasing of IPv4 addresses. When choosing a provider, consider factors like:
The number of addresses you need.
The duration of the lease.
The provider's reputation and history of handling IP address transactions.
2. Lease Agreement
Similar to any lease agreement, this will outline the terms of use, the price, the duration of the lease, and the responsibilities of both parties. Ensure the contract specifies:
The total number of IPv4 addresses being leased.
The time period of the lease (e.g., short-term or long-term).
Payment terms (usually monthly or annually).
Any restrictions on usage.
3. Ensure Proper Documentation
The transfer of IP addresses must be documented with the appropriate Regional Internet Registry (RIR) or the authority that manages IP addresses in your region. This may include updating contact information and demonstrating a legitimate need for the addresses.
4. Pay for the Lease
Once the terms are agreed upon, you will typically need to pay for the lease either upfront or through periodic payments. Prices can vary based on demand and the region of the leased IP addresses.
5. Manage and Use the IP Addresses
Once you have leased the addresses, you can begin using them on your network, just like you would with any purchased IP address. The difference is that these addresses remain under the ownership of the leasing party, meaning they must be returned or renewed when the lease expires.
Risks and Considerations of Leasing IPv4 Addresses
While leasing can be a beneficial option, there are several factors and potential risks to be aware of:
1. Temporary Nature of the Lease
Since the lease is not permanent, you could lose access to the addresses once the term expires. If you’re relying on the IP addresses for critical services, ensure you have a plan for transitioning when the lease ends.
2. Costs Over Time
Leasing may be cheaper upfront, but over a long period, the costs could add up. If you plan to use the IP addresses for an extended duration, it might make sense to purchase them outright.
3. Legal and Compliance Issues
Make sure the leased IP addresses are not involved in any legal disputes or abuse. Some organizations have had issues with previously owned IP addresses being used for spamming, phishing, or other malicious activities.
4. Limited Transferability
Depending on the terms of the lease, you may not be able to transfer the IP addresses to another entity. If your business needs to change IP providers, this could be a constraint.
5. Management Complexity
If you lease a large number of IP addresses, managing them can become cumbersome, especially if they’re used across different services or regions.
Conclusion
Leasing an IPv4 address is an excellent way for businesses to gain immediate access to the IP resources they need without the hefty investment of purchasing them. Whether you need the addresses for a short-term project, expansion, or to avoid running out of space, leasing is a viable option. However, it’s important to carefully consider the terms, risks, and potential costs before committing to an agreement.
As IPv6 adoption slowly progresses, the demand for IPv4 addresses will likely decrease over time. But for the moment, leasing IPv4 addresses remains a practical and flexible solution to navigate the complexities of IP address management.
0 notes
Text
Integration of Smart Pushbutton Switches and Remote Control Technology: Driving Smart Manufacturing in Industry 4.0

With the rapid development of Industry 4.0 and the Internet of Things (IoT), traditional pushbutton switches are evolving towards intelligence. Smart pushbutton switches not only perform basic switching functions but also incorporate advanced technologies such as remote monitoring, automated control, and data communication. These smart pushbutton switches play a critical role in factory automation and smart manufacturing systems, meeting the growing demand for remote control while ensuring compatibility with industrial communication protocols (e.g., Modbus, Profinet), laying the foundation for comprehensive integration in Industry 4.0.
1. Integration Technology of Smart Pushbutton Switches
Smart pushbutton switches are a combination of traditional mechanical buttons and modern electronic technology. In addition to providing physical actuation, they integrate sensors, microprocessors, and communication modules to enable real-time monitoring, data collection, and remote control.
1.1 Internal Integration of Circuits and Sensor Technology Smart pushbutton switches feature built-in microcontrollers (MCUs) and sensors that allow real-time sensing of switch states and transmit data to cloud platforms or local management systems. For example, buttons can integrate pressure sensors, temperature sensors, or vibration sensors to monitor the operational status and environmental conditions of equipment.
Application Example: During an industrial manufacturing process, a pushbutton switch with an integrated temperature sensor can monitor equipment's temperature changes in real time. If the temperature exceeds a set threshold, the switch automatically sends an alert and controls the equipment to stop, preventing damage caused by overheating.
1.2 Data Collection and Communication Module Integration Smart pushbutton switches can also integrate wireless communication modules (e.g., Wi-Fi, Zigbee, or LoRa) to send collected data to remote servers. These switches are not limited to local operation but can be tracked in real-time through remote monitoring platforms, leveraging big data analysis to optimize production processes.
2. Remote Monitoring and Control of Smart Pushbutton Switches
In smart manufacturing environments, remote monitoring and control functions significantly enhance factory management efficiency. Traditional pushbutton switches require manual on-site operation, whereas smart pushbutton switches can achieve remote control via network connectivity, supporting automated management and reducing manual intervention.
2.1 Implementation of Remote Control Through wireless communication technology, smart pushbutton switches can connect with central control systems or mobile devices, enabling operators to remotely control switches through computers or smartphone applications. Smart switches can integrate with factory automation systems (e.g., SCADA systems) to provide real-time remote control and status monitoring of production equipment.
Application Example: In a large factory, smart pushbutton switches are used to remotely control the start and stop of machines. When a fault is detected on a production line, the factory manager can remotely shut down the related equipment from the control center or mobile app, minimizing production accidents and downtime.
2.2 Real-Time Data Feedback and Alarm Functions Smart pushbutton switches are capable not only of remote control but also real-time data feedback and alarm functions. When the switch detects an abnormal condition (e.g., overload, temperature anomaly, or circuit fault), the system immediately sends an alert to notify the management. Through the remote monitoring system, operators can quickly identify and resolve the issue, minimizing the impact of equipment failures.
Application Example: A manufacturing company’s smart pushbutton switch system monitors the electrical current of equipment in real time. If the current exceeds a safe range, the smart switch immediately cuts off the power and sends an alert, preventing potential overheating or burning of equipment.
3. Compatibility Design of Pushbutton Switches with Industrial Communication Protocols
In industrial automation, pushbutton switches play a crucial role as input devices. They must be compatible with various industrial communication protocols to seamlessly integrate into existing industrial control systems, such as PLC (Programmable Logic Controller) networks and Distributed Control Systems (DCS). Modbus, Profinet, and similar protocols are the core standards for industrial communication, and smart pushbutton switches need to be designed for seamless integration with these protocols.
3.1 Modbus Protocol Compatibility Design Modbus is a widely used protocol for communication between industrial devices, typically facilitating data transmission between PLCs and controllers. Smart pushbutton switches with built-in communication modules compatible with Modbus protocol can directly exchange data with PLCs. This allows the switches to perform not only simple switching operations but also bidirectional communication with device management systems, enabling remote status monitoring and parameter adjustments.
Application Example: In a factory, a smart pushbutton switch is connected to a PLC via Modbus, allowing real-time feedback of the switch status. Factory managers can adjust the switch's response parameters through the control system to optimize its sensitivity and operation.
3.2 Profinet Protocol Compatibility Design Profinet is an industrial Ethernet-based standard used for efficient real-time communication, especially in scenarios requiring high response speeds. By supporting the Profinet protocol, smart pushbutton switches can integrate seamlessly with fieldbus and control networks, providing fast and reliable responses.
Application Example: In an automated production line, smart pushbutton switches connect to the robotic control system via Profinet, enabling real-time control and feedback of multiple devices on the production line. Through the Profinet network, switch state changes can be transmitted to the control center within milliseconds, ensuring quick responses during the production process.
4. Application Prospects of Smart Pushbutton Switches in Industry 4.0
The integration and remote control technologies of smart pushbutton switches lay a solid foundation for Industry 4.0’s smart manufacturing. By integrating sensors and communication technology, pushbutton switches can play a more intelligent role in factory automation control.
4.1 Data-Driven Intelligent Decision-Making Smart pushbutton switches are not just operational interfaces but also sources of valuable data for smart manufacturing. These data can be used for production forecasting, equipment maintenance, and energy efficiency optimization. For example, data collected by smart pushbutton switches allow companies to analyze the status of equipment, predict potential failures, and conduct maintenance in advance, reducing unplanned downtime.
Application Example: A factory monitors real-time data from pushbutton switches to accurately predict maintenance times for production line equipment, preventing interruptions caused by equipment failure and improving overall operational efficiency.
4.2 Integration with Cloud Computing and Big Data Combining smart pushbutton switches with cloud computing and big data platforms enables broader remote management and optimization. Through cloud platforms, operators can not only monitor equipment status remotely but also use data analytics to identify potential issues and improvement opportunities.
Application Example: In a globalized production network, smart pushbutton switches connected to a cloud platform allow for remote management across different regions. Factory managers can monitor equipment operation in real-time across various facilities and make adjustments remotely.
5. Future Development Trends of Smart Pushbutton Switches
As IoT and smart manufacturing continue to spread, smart pushbutton switches will become even more intelligent and multifunctional. The following are key trends in the future development of smart pushbutton switches:
5.1 Application of Artificial Intelligence (AI) Technology By introducing AI algorithms into smart pushbutton switches, devices will be able to learn and optimize their operations autonomously. For example, smart switches may adjust their sensitivity based on usage habits or automatically modify control strategies by analyzing environmental data.
5.2 Introduction of Edge Computing Technology Future smart pushbutton switches will leverage edge computing technology to process more data locally, reducing reliance on remote servers. This will enhance system response speed and improve the autonomous decision-making capabilities of pushbutton switches.
Conclusion
The integration and remote control technologies of smart pushbutton switches are revolutionizing industrial manufacturing. Through compatibility with industrial communication protocols, smart pushbutton switches can seamlessly integrate into industrial automation systems, enabling real-time control and remote monitoring. In the future, with the introduction of artificial intelligence and edge computing technologies, smart pushbutton switches will play an even more crucial role in Industry 4.0, driving manufacturing towards greater intelligence and automation.
en.dghongju.com
0 notes
Text
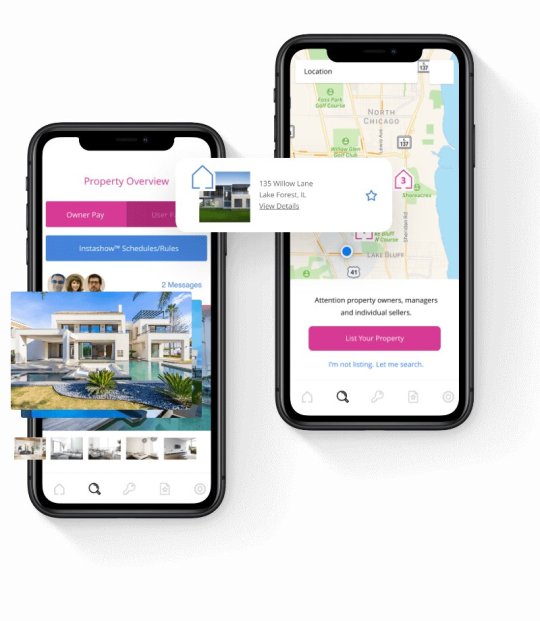
IoT Device Selection
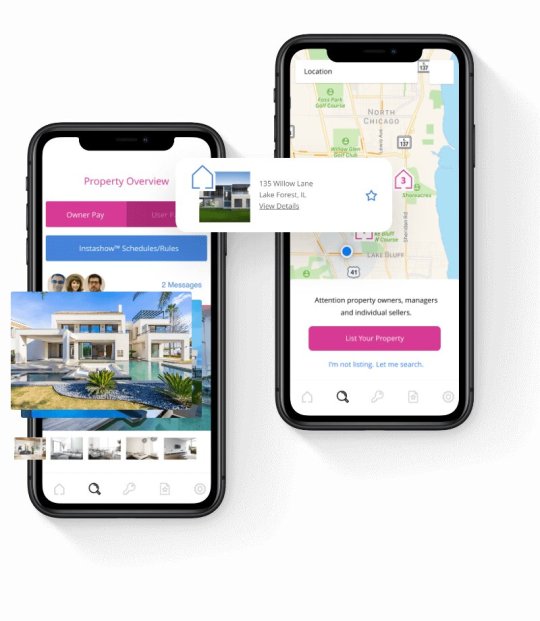
IoT App Development Company: Everything You Need To Know
Get a balance between quality, cost, and time with superior IoT Services for dealing with your business challenges in the best possible manner. We serve global clients with boastful services on a varied scale, with end-to-end network vs. device integration services with the most innovative solutions. Optimize your IoT strategy with meticulous IoT device selection tailored to your goals.
Benefits of IoT Development
The Internet of Things (IoT) is the technology that allows businesses to integrate their service via secondary devices. With IoT, you can build user-friendly apps compatible with various devices, operating systems, and screen resolutions. You can also integrate your smart apps with third-party apps using secure APIs and collect vital user data and behavior on the mobile application to personalize the experience even further.
How to choose a reliable partner for IoT Development?
While analyzing an IoT vendor partner, you should prioritize secure organizations that behold strong web security and development. You must also adopt Full-stack organizations and companies that can establish an ‘all-in-one’ solution that manages a single project’s hardware, mobile interface, and web interface. Opting for a vendor offering these development capabilities and improvements is a much safer bet.
Why TechAhead for IoT App Development?
With over 13+ years of experience delivering cutting-edge digital transformation and mobility solutions, TechAhead has been a major digital partner for globally established companies like Disney, Audi, and American Express. Clutch has ranked us among the top IT IoT development services companies and the top multicultural companies with a strong-willed presence across Los Angeles and Noida.
Who is the top IoT development company?
TechAhead, of course! We have been accelerating business agility and stimulating digital transformation since 2009. Our company was recognized last year as the top IT service provider by Leaders Matrix, an industry-recognized, unbiased ranking entity.
We disrupt the traditional outsourcing model of other IoT companies. We ensure long-term and sustainable success for our customers and the mobile and digital ecosystem. Our relationships with our customers go beyond transactional. Our software development services give entrepreneurial ideas life. We infuse existing mobile and digital platforms with innovation and creativity.
What are the top IoT Apps developed by TechAhead?
We are a world-class digital transformation and mobility solution company and have delivered over 2,000+ project developments on Android, iOS, and cross-platform compatible apps for global brands. We recently announced the launch of “The Healthy Mummy” fitness app, which was recently ranked the world’s #1 Mum’s fitness app, attracting over 2M+ users and adding to many of our success stories.
What about Data security and integrity of IoT Apps?
All TechaAhead development practices are highly efficient and secure thanks to meticulous adherence to security practices and data governance at every step. Our development process considers the devices connected, cloud computing requirements, IoT platforms, and security while developing IoT mobile applications. We ensure that our IoT apps follow all the guidelines and protocols for the highest security.
How to get IoT app maintenance help and post-launch support?
Our role remains strong after the go-live. TechAhead takes full responsibility for the smooth functioning of IoT solutions in your company. With platform support services, maintenance, and the support of process management, our team will monitor your app’s success, it’s adaptability and remove any bugs/errors as per our client’s business needs and user reviews.
In conclusion, the world of IoT app development is a realm of boundless possibilities. Through TechAhead's expertise and commitment, businesses can harness the power of IoT to create user-friendly apps, ensure data security, and drive innovation. TechAhead's track record of success, recognition, and dedication to post-launch support make it a reliable partner in the journey of IoT app development. With a focus on disruptive innovation and holistic relationships, TechAhead is poised to continue shaping the landscape of IoT solutions, delivering transformative results for businesses worldwide!
#IoT software development services#embedded software development services#IoT device selection#IoT strategy consultation#IoT data visualization tools#edge computing for IoT#IoT network protocols (e.g.#MQTT#CoAP)#IoT user experience design#AI in IoT solutions#IoT and blockchain integration#IoT app design services#IoT app development#IoT device integration#IoT data analytics services#IoT security solutions#custom IoT application development#enterprise IoT services#industrial IoT solutions#IoT firmware development#IoT cloud integration#IoT connectivity solutions#mobile app development#software development#TechAhead Corp#TechAheadCorp#techaheadcorp.com
0 notes
Text
Introduction to Data Centers: What They Are and How They Work

In today’s digital age, data centers are the backbone of the internet, supporting everything from personal email to massive corporate databases. These complex facilities are critical for the storage, management, and dissemination of data. This blog provides a comprehensive introduction to data centers, explaining what they are, how they function, and why they are essential in our increasingly connected world.
What is a Data Center?
A data center is a specialized facility designed to house computer systems and associated components, such as telecommunications and storage systems. It provides a centralized location for critical IT operations and equipment, ensuring data is secure, accessible, and available. Data centers are equipped with redundant power supplies, data communication connections, environmental controls (e.g., air conditioning, fire suppression), and various security devices.
Key Components of a Data Center
Servers
Servers are the heart of a data center. They are powerful computers that store, process, and manage data. Servers can vary in size and capacity, from small blade servers to large, rack-mounted units. They run applications and provide services to users over a network.
Storage Systems
Data centers use various types of storage systems, such as hard drives (HDDs), solid-state drives (SSDs), and storage area networks (SANs). These systems store the vast amounts of data that organizations generate and use.
Networking Equipment
Networking equipment, including routers, switches, and firewalls, ensures data can be transferred within the data center and to external users. This equipment manages data traffic and maintains security protocols to protect sensitive information.
Power Supply
A reliable power supply is crucial for data center operations. Data centers often have multiple power sources, including generators and uninterruptible power supplies (UPS), to ensure continuous operation even during power outages.
Cooling Systems
Servers generate significant heat, requiring effective cooling systems to maintain optimal operating temperatures. Data centers use air conditioning units, liquid cooling, and other technologies to dissipate heat and prevent equipment from overheating.
Security Systems
Security is a top priority in data centers. Physical security measures include surveillance cameras, access control systems, and security personnel. Cybersecurity measures involve firewalls, encryption, and intrusion detection systems to protect data from unauthorized access and cyber threats.
Types of Data Centers

Data centers come in various forms, tailored to different needs and scales. Here are some common types:
Enterprise Data Centers
These are built and operated by individual companies for their exclusive use. They support internal IT operations and business applications, ensuring data control and customization.
Colocation Data Centers
Colocation facilities, or “colos,” lease space, power, and cooling to multiple customers. Companies rent space within these data centers, reducing the cost and complexity of building and maintaining their own facilities.
Cloud Data Centers
Operated by cloud service providers like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud, these data centers offer scalable computing resources and services over the internet. They allow businesses to access computing power and storage on-demand without the need to invest in physical infrastructure.
Edge Data Centers
Edge data centers are smaller facilities located closer to end-users and devices. They reduce latency and improve performance for applications that require real-time processing, such as IoT and autonomous vehicles.
How Data Centers Work
The operation of a data center involves several interconnected processes and technologies. Here’s a step-by-step look at how data centers work:
Data Collection and Storage
Data centers collect data from various sources, including user inputs, sensors, and applications. This data is then stored in servers and storage systems within the facility.
Data Processing and Management
Once stored, data is processed by servers, which perform computations, run applications, and manage databases. Data management involves organizing, securing, and maintaining data integrity.
Data Transmission
Networking equipment ensures data is transmitted efficiently within the data center and to external networks. This involves routing data packets, managing bandwidth, and maintaining network security.
Data Access and Delivery
Users access data and applications hosted in data centers through the internet or private networks. Data centers use content delivery networks (CDNs) to distribute data across multiple locations, reducing latency and ensuring fast access.
The Importance of Data Centers
Data centers are crucial for several reasons:
Business Continuity
Data centers ensure business continuity by providing reliable and secure access to data and applications. They offer disaster recovery solutions, minimizing downtime and data loss during emergencies.
Scalability
Data centers enable businesses to scale their IT resources up or down based on demand. This flexibility allows companies to adapt to changing needs without significant investments in physical infrastructure.
Data Security
Data centers implement robust security measures to protect sensitive information. They offer physical and cybersecurity solutions to safeguard data from unauthorized access, cyberattacks, and natural disasters.
Efficiency and Cost Savings
By centralizing IT operations, data centers improve efficiency and reduce costs. They allow organizations to consolidate hardware, optimize energy use, and benefit from economies of scale.
Challenges Facing Data Centers
Despite their importance, data centers face several challenges:
Energy Consumption
Data centers consume significant amounts of energy to power and cool servers. As the demand for data services grows, so does the need for sustainable energy solutions to minimize environmental impact.
Security Threats
Cybersecurity threats are a constant concern for data centers. Operators must stay vigilant and implement advanced security measures to protect against data breaches and cyberattacks.
Data Privacy Regulations
Data centers must comply with data privacy regulations, such as the GDPR and CCPA. Ensuring compliance involves implementing strict data protection policies and maintaining transparency with users.
Infrastructure Management
Managing the physical infrastructure of data centers, including hardware maintenance and upgrades, is complex and resource-intensive. Operators need skilled personnel and advanced tools to ensure smooth operations.
The Future of Data Centers

Green Data Centers
Sustainability is becoming a priority for data centers. Green data centers use renewable energy sources, energy-efficient technologies, and innovative cooling solutions to reduce their carbon footprint.
Edge Computing
As IoT devices proliferate, the demand for edge computing is rising. Edge data centers, located closer to end-users, will play a critical role in processing data locally and reducing latency.
Artificial Intelligence (AI)
AI is transforming data center operations. AI-driven tools can optimize energy use, predict hardware failures, and enhance security through advanced threat detection.
Quantum Computing
Quantum computing holds the promise of revolutionizing data processing. While still in its early stages, quantum computers could perform complex calculations at unprecedented speeds, driving innovation in data centers.
Conclusion
Data centers are indispensable in the modern digital landscape, providing the infrastructure needed to store, process, and deliver data. Understanding their components, operations, and challenges is crucial for appreciating their role in our connected world. As technology advances and data demands grow, data centers will continue to evolve, embracing new innovations and sustainability practices to meet the needs of the future.
0 notes
Text
Integrating AI Video Surveillance with IoT and Edge Computing in Construction
In the fast-paced world of construction, ensuring safety, optimizing operations, and maintaining efficiency are pivotal to project success. Modern advancements in technology, particularly AI Video Surveillance, IoT (Internet of Things), and Edge Computing, offer unprecedented opportunities to transform how construction sites are monitored and managed. This blog delves into the seamless integration of these technologies, exploring their synergies and benefits in real-time monitoring and proactive decision-making.

Video Surveillance Systems powered by AI
AI Video Surveillance Systemsrepresent a significant leap forward in construction site management. By harnessing the power of artificial intelligence, these systems analyze video feeds in real time, detecting anomalies, monitoring worker activities, and identifying potential safety hazards. This proactive approach not only enhances site security but also streamlines operations by providing actionable insights for better decision-making.
Exploring IoT in Construction
IoT has revolutionized construction by interconnecting devices, sensors, and equipment, creating a network that gathers and exchanges valuable data. In construction, IoT applications range from environmental monitoring (temperature, humidity) and equipment tracking to worker safety enhancements (wearable sensors, biometric data). This data-driven approach improves visibility into site conditions and operational performance, enabling proactive management and optimized resource allocation.
The Role of Edge Computing
Edge Computing complements AI Video Surveillance and IoT by processing data closer to its source—on-site or near-site devices. In construction, edge devices analyze data from IoT sensors and AI Video Surveillance systems locally, enabling immediate responses to critical events and ensuring continuous operation even in bandwidth-constrained environments.
Synergies Between AI Video Surveillance, IoT, and Edge Computing
The integration of AI Video Surveillance with IoT and Edge Computing unlocks synergistic benefits that go beyond individual capabilities:
● Enhanced Safety Monitoring: AI algorithms analyze data from IoT sensors to detect safety hazards in real-time, triggering immediate alerts and preventive actions.
● Optimized Operational Efficiency: Real-time insights from AI Video Surveillance and IoT enable proactive maintenance, efficient resource allocation, and streamlined workflows.
● Cost Savings: Predictive analytics and AI-driven optimizations reduce downtime, minimize equipment wear and tear, and optimize labor productivity, resulting in significant cost savings over time.
Benefits of Integrated Systems in Construction The convergence of AI Video Surveillance, IoT, and Edge Computing delivers comprehensive benefits tailored to construction site requirements:
● Improved Safety Protocols: AI-powered surveillance enhances safety protocols by detecting unauthorized access, identifying potential hazards (like slip/trip/fall risks), and ensuring compliance with safety regulations.
● Enhanced Operational Visibility: Real-time data insights enable construction managers to monitor progress, track equipment usage, and optimize workflows, leading to enhanced project management and timely decision-making.
● Scalability and Flexibility: Integrated systems scale with project requirements, supporting diverse applications such as construction progress monitoring, equipment management, and environmental compliance monitoring.
Challenges and Considerations While integrated systems offer substantial advantages, their deployment poses challenges that need careful consideration:
● Data Security and Privacy: Protecting sensitive data from breaches and ensuring compliance with data privacy regulations (e.g., GDPR) are critical concerns.
● Infrastructure Compatibility: Ensuring seamless integration across different hardware, software, and communication protocols requires robust planning and execution.
● Regulatory Compliance: Adhering to industry standards and regulations governing surveillance, data handling, and safety protocols is essential for legal and operational compliance.
Future Trends and Innovations The future of construction site management is poised for further innovation and advancement:
● AI-driven Predictive Maintenance: Anticipating equipment failures before they occur, optimizing maintenance schedules, and extending equipment lifespan.
● Autonomous Construction Equipment: Integrating AI and robotics for autonomous operations, enhancing efficiency, and reducing human intervention.
● Smart Site Management: Leveraging AI insights for predictive analytics, resource optimization, and proactive risk management.
In conclusion, the integration of AI Video Surveillance with IoT and Edge Computing represents a transformative approach to construction site monitoring and management. viAct is committed to pioneering these technologies, empowering construction companies with advanced tools to enhance safety, optimize operations, and drive project success. Contact viAct today to discover how our integrated solutions can revolutionize your construction projects and propel your business into the future.
Explore viAct's AI Video Surveillance System and integrated IoT solutions to revolutionize your construction site management. Request a demo today and experience the future of construction safety and efficiency.
Visit Our Social Media Links :-
Facebook - viactai Twitter - aiviact Instagram - viactai/ Youtube - @viactai Linkedin - viactai
Blog URL -
Top 5 Computer Vision Use Cases in Manufacturing How Computer Vision in Manufacturing can help Prevent Anomalies?
0 notes
Text
Smart Blind Rivets Enable IoT and Sensor Integration
In an everchanging landscape of technology advances the lowly blind rivet has not been neglected. The inclusion of Internet of Things (IoT) and sensor technology in blind rivets is transforming the way fastening and assembly processes are approached with industries. This enables them to offer a range of features almost like never before, ranging from real-time monitoring and inspection to predictive maintenance - features that are often highly desired in modern manufacturing and building. In this blog, we describe the evolution, applications, and transformation that smart blind rivets are creating within specialized industries.
What Are Smart Blind Rivets?
These are state-of-the-art blind rivets having sensors inside and equipped with Internet of Things capabilities, they can be referred to as smart blind rivets. Traditional blind rivets are merely used to hold two materials together, whereas the smart blind rivets of the invention further serve to collect and transmit data with respect to their environment e.g., condition. Information harvested can be applied for the continuous monitoring of structural integrity, potential problem areas, and maintenance scheduling optimization.
Key Features:
Embedded Sensors- Measure other factors such as stress, tension, vibration, temperature.
IoT Connectivity: Send data to central systems in real-time for monitoring & analytics.
Predictive Maintenance: Utilize the data you have collected to predict impending failures and perform maintenance in a timely manner.
How Smart Blind Rivets Work
To understand just how smart blind rivets work, we must first take a closer look at their operations:
1. Sensors: These sensors monitor different parameters, e.g. pressure, temperature or load from within the rivet itself.
2. Micro controllers (process sensor data and control the communication protocols)
3. Wireless Transmitters: Send all the processed data to a central monitoring system through IoT networks.
4. Data Analytics Software (Pending/Coming Soon): Looks at incoming data and provide relevant insights, alerts and proactive maintenance schedules
Installation Process:
However, it can still be done with a conventional blind rivet tool in the case of smart blind rivets. As the sensors and IoT components are standardized, installation procedures can be operated identically to existing workflows.
Smart Blind Rivets Application
Aerospace Industry
Aerospace has an importance of each single part integrity. It specializes in the development of blind fastening devices and components with built-in sensors for aerospace applications, such as smart blind rivets that can alert MRO crews to looming problems in aircraft structures before they become mission-critical.
Structural Health Monitoring: Real time evaluation of the aircraft fuselage and wings.
Safety Improvements: Detect dangers and warning the maintenance team before impending failure
Life cycle Management: to extend the life of aircraft components by pro-active maintenance.
Automotive Industry
To conclude, the automotive industry is able to receive a range of benefits from using smart blind rivets in both the manufacturing and maintenance processes.
Assembly Line Optimization: Real-time quality inspection for riveted joints to guarantee the quality of work and reduce rework costs.
- Vehicle Health Reporting’s: Integrate with Vehicle diagnostics for in-depth vehicle health report generation.
1- Crash Safety: Improve the durability of safety-critical components such as airbags and seatbelt anchors.
Construction Industry
Smart blind rivets also have applications in construction, such as keeping buildings and infrastructure together.
Structural Monitoring: Monitor critical joints in bridges, sky scrapers and other structures.
Maintenance Scheduling: Leverage data for proactive scheduling of maintenance which minimizes downtime and cost.
Safety Compliance: Monitor that the regulations are configured in the building so that it complies with safety standards throughout the time.
Renewable Energy
Smart blind rivets also have applications in installation of renewable energy installations such as wind turbines and solar farms.
Turbine Health Monitoring MPI Turbine health monitoring The structural integrity of wind turbines is critical to avoid very expensive failures - escalators have 3 years life and replacing a failed unit is complicated, costly and inconvenient.
Solar Panel Maintenance -- Check the condition of solar panel mounts and brackets.
They will allow this by - Environmental Adaptation: They can use the data from their rivets to adjust maintenance schedules based on environmental circumstances.
Key Advantages of Smart Blind Rivets
Real-Time Monitoring
It offers intelligent sensors and monitors the condition of the structures in which it is placed, in real time. As a result, it comes with different big advantages, such as the early issue detection which lowers the possibility of some failures happening without any warn.
Predictive Maintenance
The data taken from smart blind rivets can be analysed for maintenance to be planned Predictively. By following this method downtimes can be prevented and component lifespans can be extended hence saving a fortune.
Enhanced Safety
One of the main objectives in the sense of safety applied to different structures (as in aircraft, vehicles, buildings or renewable environments) is continuous monitoring and early detection of problems.
Improved Efficiency
Data from smart blind rivets can be used to improve production processes, guaranteeing that every single one of them is installed the right way and does the job they were supposed.
Future Challenges and Directions
Despite the advantages of smart blind rivets, there are also a number of hurdles to practically realizing their benefits:
Higher Cost: The basic technology of smart blind rivets is accompanied by a higher price than traditional rivets.
Data Management - large data produced needs only to be appropriately managed and analysed.
- Implementation: Incorporating smart rivets with the existing system and the infrastructure are complex.
Future Developments
Due to the advancement of technology, smart blind rivets are slated for a price drop as it becomes cheaper. IoT and sensor technology will also continue to improve which will further empower their capabilities, providing more granular and precise data. Also, by integrating AI and ML your predictive maintenance can be even better which would potentially improve in operational efficiency greatly.
Conclusion
In a broader perspective, smart blind rivets are a major development in fastening technology that have benefits which extend beyond just assembly. Incorporating IoT and sensor technologies, these advanced fasteners enable real-time monitoring, predictive maintenance, as well as safety improvement across industries from aerospace to construction. It is only a matter of time and as these challenges are met and technology advances, smart blind rivets will become a part of standard modern manufacturing with prospects towards a smarter more connected world.
1 note
·
View note
Text
Unlocking Seamless Connectivity: The Importance of Wireless Access Points
In our increasingly connected world, where the demand for reliable internet access continues to rise, the role of Wireless Access Points (WAPs) has become indispensable. Whether you're at home, in the office, or at a public venue, WAPs play a crucial role in providing seamless connectivity to the internet and other network resources. Let's delve into why these devices are so vital and how they enhance our digital experiences.
A Wireless Access Point often abbreviated as WAP or simply AP, is a hardware device that allows wireless devices (such as laptops, smartphones, tablets, and IoT devices) to connect to a wired network using Wi-Fi. Essentially, it bridges the gap between the wired and wireless networks, enabling users to access the internet and other network resources without the constraints of physical cables.
2. Enhancing Connectivity and Mobility
One of the primary benefits of WAPs is their ability to enhance connectivity and mobility. Instead of being tethered to a specific location by cables, users can move freely within the range of the WAP while maintaining seamless access to the network. This freedom is particularly valuable in environments like offices, schools, and public spaces where mobility and flexibility are key.
3. Scalability and Coverage
Modern WAPs are designed to provide extensive coverage and can be scaled to accommodate larger areas or more users. This scalability is crucial in environments with high user density, such as stadiums, conference centers, and shopping malls. Advanced WAPs can support hundreds or even thousands of concurrent connections, ensuring that everyone can stay connected without experiencing slowdowns or interruptions.
4. Security and Management
Security is another critical aspect of WAPs. They often include features like encryption protocols (e.g., WPA2, WPA3) to protect data transmitted over the wireless network from unauthorized access. Additionally, WAPs can be centrally managed, allowing administrators to monitor and control network usage, enforce security policies, and troubleshoot issues remotely. This centralized management simplifies network administration and enhances overall security.
5. Evolving Technologies and Future Trends
As technology continues to evolve, so do WAPs. The advent of Wi-Fi 6 (802.11ax) and beyond promises faster speeds, lower latency, and improved efficiency, further enhancing the user experience. Moreover, advancements in mesh networking are making it easier to extend wireless coverage over large areas with minimal signal degradation.
In conclusion, Wireless Access Points are indispensable components of modern networking infrastructure. From enhancing connectivity and mobility to ensuring security and scalability, WAPs play a crucial role in keeping us connected in today's digital age. As technology continues to evolve, so too will the capabilities of WAPs, promising even better performance and reliability in the years to come.
Whether you're setting up a new network or upgrading an existing one, investing in quality WAPs can significantly improve the connectivity experience for users, making it easier to stay connected anytime, anywhere.
0 notes
Text
OTA Software Updates: Ensuring Reliability and Security in Connected Devices
Over-The-Air (OTA) software updates have become indispensable in the realm of connected devices, offering a seamless way to enhance functionality, fix bugs, and improve security without requiring physical intervention. This article explores the critical aspects of OTA updates, their benefits, challenges, and best practices for ensuring reliability and security.
Understanding OTA Software Updates
Definition: OTA software updates enable devices to receive and install firmware, software patches, and configurations remotely, typically over secure wireless networks.
Components:
Client Software: Installed on devices to receive and process updates.
Server Infrastructure: Manages update distribution, ensures authentication, and secures data transfer.
Communication Protocols: Utilizes HTTPS, MQTT, CoAP, etc., for secure and efficient update delivery.
Importance of OTA Updates
Enhanced Security:
Enables prompt deployment of security patches and fixes vulnerabilities, reducing exposure to cyber threats.
Implementation of encryption and authentication protocols ensures updates are tamper-proof and secure.
Operational Efficiency:
Reduces downtime and operational disruptions associated with manual updates.
Facilitates quick rollout of new features and improvements, enhancing device performance and user satisfaction.
Challenges and Considerations
Security Risks: Vulnerabilities in OTA mechanisms can be exploited if not properly secured, necessitating robust security measures and regular audits.
Compatibility and Reliability:
Ensuring updates are compatible with diverse device configurations, software versions, and network environments.
Thorough testing and validation processes are crucial to mitigate risks of unintended consequences or system failures.
Best Practices for OTA Updates
Secure Protocols: Implement strong encryption (e.g., AES-256) and authentication mechanisms (e.g., digital signatures) to protect OTA communications.
Incremental Updates: Deploy incremental updates to minimize data usage and ensure efficient bandwidth management.
User Consent and Transparency: Obtain user consent for updates and provide transparent information about update contents and benefits.
Industry Applications
Automotive Sector: OTA updates enable automakers to remotely improve vehicle performance, safety features, and infotainment systems.
IoT Devices: Smart home devices, industrial sensors, and healthcare equipment benefit from OTA software updates for functionality enhancements and security enhancements.
Future Directions
AI-Enabled Updates: Leveraging AI and machine learning for predictive analytics to anticipate update requirements and optimize deployment strategies.
Blockchain Integration: Exploring blockchain technology to enhance OTA update security and transparency.
Conclusion
OTA software updates play a pivotal role in ensuring the reliability, security, and performance of connected devices across industries. By adopting best practices and leveraging advanced technologies, organizations can effectively manage OTA updates to enhance user experience, mitigate risks, and stay ahead in an increasingly connected world.
0 notes
Text
The Role of Technology in Modern Shared Offices in kochi
Introduction
In the dynamic landscape of modern workspaces, technology has become the backbone of efficiency, productivity, and collaboration. Shared offices, also known as coworking spaces, have particularly benefited from technological advancements, making them hubs of innovation and flexibility. This article explores the various ways technology is transforming modern shared offices.
1. High-Speed Internet and Connectivity
Reliable high-speed internet is the lifeline of any shared office. With businesses increasingly relying on cloud services and online collaboration tools, uninterrupted connectivity is essential. Shared offices often invest in robust IT infrastructure, including multiple internet service providers (ISPs) to ensure redundancy and uptime. This setup supports diverse tenant needs, from startups to established enterprises.
2. Cloud Computing and Storage
Cloud technology has revolutionized how businesses operate, particularly in shared office environments. With cloud computing, companies can access files and applications from anywhere, facilitating remote work and flexible office hours. Shared office spaces offer secure cloud storage solutions, ensuring data is accessible yet protected. This flexibility allows teams to collaborate seamlessly, irrespective of their physical location.
3. Smart Office Automation
Smart office technology enhances the efficiency and user experience of shared workspaces. Features like automated lighting, climate control, and smart access systems not only create a comfortable working environment but also contribute to energy savings. IoT (Internet of Things) devices play a pivotal role here, allowing for real-time adjustments based on occupancy and usage patterns.
4. Collaboration Tools and Software
Effective collaboration is a cornerstone of shared office spaces. Technologies such as video conferencing tools (e.g., Zoom, Microsoft Teams), project management software (e.g., Trello, Asana), and instant messaging platforms (e.g., Slack) are integral to modern coworking spaces. These tools enable seamless communication and project tracking, fostering a collaborative community even among disparate teams.
5. Security and Data Protection
With multiple businesses operating under one roof, security is a paramount concern in shared offices. Advanced security measures, including biometric access, surveillance cameras, and cybersecurity protocols, ensure that both physical and digital assets are protected. Shared offices invest in encryption and secure network practices to safeguard sensitive data from breaches.
6. Virtual Office Services
For freelancers and remote workers, virtual office services provided by shared spaces are invaluable. These services include a professional business address, mail handling, and reception services. Technology facilitates these virtual offerings, allowing individuals to maintain a professional presence without a permanent physical office.
7. Networking and Community Platforms
Technology also plays a crucial role in building and maintaining the community within shared offices. Internal social networks and community apps help members connect, collaborate, and share resources. These platforms often include event calendars, discussion forums, and member directories, enhancing the overall coworking experience.
8. Flexible Workspace Management
Shared offices utilize advanced workspace management software to optimize space utilization and member satisfaction. These systems enable online booking of meeting rooms, hot desks, and other facilities, streamlining operations. They also provide analytics on space usage, helping managers make informed decisions about space allocation and amenities.
9. Enhancing Member Experience with AR/VR
Augmented Reality (AR) and Virtual Reality (VR) are emerging technologies that can enhance the coworking experience. Virtual tours of the workspace, AR-assisted navigation within the office, and VR meeting rooms are innovative applications that add value to shared offices. These technologies create immersive experiences that attract tech-savvy professionals.
Conclusion
The integration of technology in modern shared offices is not just a trend but a necessity. As the demand for flexible and efficient workspaces grows, technology will continue to shape the future of coworking. By embracing these advancements, shared offices can offer enhanced productivity, security, and community, ensuring they remain relevant in the ever-evolving business landscape.
0 notes