#International WhatsApp data extraction
Explore tagged Tumblr posts
Text

WhatsApp contact finder
In an interconnected world, the ability to communicate effectively across borders is more important than ever. For businesses aiming to expand their reach, having access to a diverse range of contacts is essential. This is where a global phone number downloader comes into play, providing a powerful tool to help organizations connect with potential clients and partners worldwide.
What is a Global Phone Number Downloader?
A global phone number downloader is a specialized tool designed to extract and compile phone numbers from various online sources. This can include social media platforms, websites, and databases. By automating the process of gathering contact information, a downloader enables businesses to build extensive and diverse contact lists efficiently.
Why Use a Global Phone Number Downloader?
Expanding Your NetworkOne of the primary advantages of using a global phone number downloader is the ability to expand your network rapidly. Whether you're a startup seeking clients or an established business looking to tap into new markets, having access to a broad range of phone numbers is invaluable. This tool allows you to gather contacts from different regions and demographics, enhancing your outreach potential.
Streamlining Marketing EffortsFor marketers, reaching the right audience is crucial. A global phone number downloader enables you to extract numbers that align with your target market. By having a diverse list of contacts, you can create tailored marketing campaigns that resonate with specific groups, improving engagement and conversion rates.
Cost-Effective SolutionTraditional methods of gathering contact information can be labor-intensive and costly. A downloader simplifies this process, reducing the time and resources spent on manual data collection. This cost-effective approach allows businesses to allocate their resources more strategically.
How to Choose the Right Global Phone Number Downloader
When selecting a global phone number downloader, consider the following factors:
User-Friendly InterfaceLook for a tool that features a straightforward interface. An easy-to-navigate platform ensures that users can extract numbers efficiently without a steep learning curve.
Source VersatilityEnsure that the downloader can extract numbers from a variety of sources relevant to your business needs. This flexibility is crucial for maximizing the effectiveness of your contact-gathering efforts.
Data Privacy and SecuritySince you’ll be handling personal contact information, it’s vital to choose a downloader that prioritizes data privacy and complies with relevant regulations. Protecting your data and maintaining trust with your contacts should be a top priority.
Support and ResourcesA good downloader should offer robust customer support and resources. If you run into issues or need guidance, responsive support can help you navigate challenges and optimize your use of the tool.
Best Practices for Using a Global Phone Number Downloader
Compliance with RegulationsAlways be aware of the legal implications of collecting phone numbers. Ensure that you’re compliant with data protection laws in your target markets to avoid potential legal issues.
Regular UpdatesThe quality of your contact list is paramount. Regularly updating your list using the downloader helps maintain its accuracy and relevance, which is critical for effective outreach.
Organize and Segment Your DataOnce you’ve gathered phone numbers, take the time to organize and segment them based on criteria like geography, demographics, or interests. This organization will enhance your marketing strategies and allow for more personalized communication.
Conclusion
In the quest for effective communication and business growth, a global phone number downloader is an indispensable tool. By automating the process of gathering contact information, it allows businesses to expand their networks, streamline marketing efforts, and operate more efficiently.
Whether you’re a small business looking to reach new clients or a large corporation aiming to penetrate international markets, leveraging a global phone number downloader can transform your outreach strategy. Embrace this powerful tool and unlock new opportunities for engagement and growth in an increasingly globalized world. With the right approach, your business can thrive in the vast landscape of international communication.
#WhatsApp contact extractor#WhatsApp number scraper#Global phone number downloader#Contact harvesting tool#International WhatsApp data extraction#Phone number scraper software#Worldwide contact finder#Global#phone directory scraper#WhatsApp data mining tool#International contact extraction
0 notes
Text
Unveiling the Power of WhatsApp Contact Extractor: Simplify Your Outreach Efforts
In the fast-paced digital era, communication is key, and WhatsApp has become an integral part of our daily interactions. For businesses and individuals looking to streamline their outreach efforts, the WhatsApp Contact Extractor emerges as a powerful tool, revolutionizing the way contacts are managed. In this blog, we will delve into the features, benefits, and practical applications of this tool that is reshaping the landscape of digital communication.

Understanding the WhatsApp Contact Extractor
WhatsApp Contact Extractor is a tool designed to simplify the process of gathering contacts from the popular messaging platform, WhatsApp. Whether you're a business owner, marketer, or an individual managing personal connections, this tool empowers you to extract contact information efficiently and enhance your outreach strategy.
Key Features of WhatsApp Contact Extractor
Efficient Data Extraction:
The primary function of this tool is to extract contact details from your WhatsApp account swiftly. It automates the process, saving you time and effort in manually collecting information.
Versatility in Data Types:
WhatsApp Contact Extractor allows you to extract various types of data, including phone numbers, names, and additional details available on WhatsApp profiles. This comprehensive approach ensures that you have all the necessary information for your outreach campaigns.
User-Friendly Interface:
The tool is designed with simplicity in mind. Its user-friendly interface makes the extraction process accessible to both novices and seasoned users, requiring minimal technical expertise.
Customizable Search Parameters:
Tailor your extractions based on specific criteria such as groups, individual chats, or a combination of both. This level of customization enables you to target your extractions with precision.
Practical Applications of WhatsApp Contact Extractor
Business Marketing Campaigns:
For businesses looking to bolster their marketing efforts, the WhatsApp Contact Extractor proves invaluable. Extract relevant contacts to create targeted campaigns and engage with potential customers directly.
Event Invitations and Announcements:
Organizing an event? Use the tool to extract contacts from relevant groups or chats, ensuring that your invitations or announcements reach the intended audience seamlessly.
Networking and Professional Outreach:
Individuals seeking to expand their professional network can utilize the tool to extract contacts from relevant industry groups or conversations. This facilitates efficient networking and outreach.
Customer Relationship Management (CRM):
Integrate the extracted contacts into your CRM system for streamlined management. This enhances your ability to nurture relationships and provide personalized interactions with clients or customers.
Conclusion
As we navigate the intricacies of digital communication, tools like the WhatsApp Contact Extractor emerge as indispensable assets. Simplify your outreach efforts, whether for personal or professional purposes, by harnessing the efficiency and versatility of this tool. Explore the power of streamlined contact management and take your communication strategy to new heights with WhatsApp Contact Extractor.
#WhatsApp contact extractor#WhatsApp number scraper#Global phone number downloader#Contact harvesting tool#International WhatsApp data extraction#Phone number scraper software#Worldwide contact finder#Global
0 notes
Text
Maximizing Outreach with International WhatsApp Data Extraction
In the modern era of digital marketing, businesses need innovative solutions to reach their target audience effectively. One such powerful tool is international WhatsApp data extraction. This advanced technology enables companies to collect crucial contact information from WhatsApp, making it an essential strategy for expanding customer outreach. A reliable phone number scraper software streamlines this process, ensuring businesses acquire verified contact details effortlessly.
A phone number scraper software is indispensable for businesses aiming to improve their lead generation process. By automating data collection, companies can gather phone numbers efficiently from WhatsApp and other sources, reducing manual work while enhancing accuracy. This tool is particularly beneficial for marketers looking to create highly targeted campaigns that drive engagement and conversions.
Benefits of International WhatsApp Data Extraction
Streamlined Lead Collection A phone number scraper software enables businesses to extract vast amounts of contact details with minimal effort. This ensures that marketing teams have a reliable and up-to-date database to work with.
Time and Cost Efficiency Manual data collection is time-consuming and prone to errors. By leveraging international WhatsApp data extraction, businesses can automate the process, saving both time and resources.
Targeted Marketing Campaigns Access to precise contact information allows businesses to segment their audience effectively. This results in personalized messaging, leading to improved customer engagement and higher conversion rates.
Compliance with Data Privacy Laws A reputable tool ensures that data is collected ethically and complies with global data protection regulations. This helps businesses maintain trust while avoiding legal issues.
Choosing the Right Phone Number Scraper Software
When selecting a software solution for data extraction, businesses should prioritize accuracy, automation features, ease of use, and compliance with privacy laws. Integrating a high-quality scraper with existing CRM systems can further optimize the efficiency of marketing efforts.
By utilizing the right tool, companies can enhance their outreach, build stronger customer relationships, and ultimately drive business growth. Whether you're a startup looking to scale or an established enterprise aiming to refine your lead generation strategy, investing in effective data extraction software can make a significant impact.
0 notes
Text
data correlation
The document you've provided contains extensive details regarding ongoing investigations involving several individuals accused of cybercrimes. Here's a summary of key elements:
Key Investigative Events:
Police Reports & Arrests:
On August 2, 2023, the Los Angeles Police Department (LAPD) raided a residence tied to cybercrime activities. Ronnie Marghiem (34 years old), Kim Rindom Sorensen Joachim (42 years old), and Kathrine Canlas were arrested for wire fraud, computer fraud, conspiracy, and money laundering. A subsequent arrest on August 6 involved Brandy Clegg Williams, who was found to be linked to cybercrime activities and arrested for violating a restraining order.
Profiles of Key Individuals:
Ronnie Marghiem: A hacker and identity thief with expertise in cybercrime tools and techniques. He has been arrested multiple times but never convicted. He has connections to other cybercriminals, including his ex-wife Kim Rindom Sorensen Joachim.
Kim Rindom Sorensen Joachim: Specializes in social engineering and identity theft. She has collaborated with Ronnie Marghiem on several occasions and is now linked to Alex Brandt, another cybercriminal.
Connections & Activities:
Both Marghiem and Sorensen Joachim are implicated in a cybercrime network involving hacking, money laundering, and fraud. Their operations use advanced technologies, including encrypted communications and VPNs, to conceal their activities. Tools used include keyloggers, ransomware, and phishing kits. They have been linked to international crime syndicates, including possible connections to Russian and Chinese intelligence.
Cybercrime Tools & Accessories:
The individuals involved in these crimes use sophisticated tools such as computers with advanced security, external storage devices for stolen data, and cryptocurrency wallets for financial transactions. Additionally, social engineering kits and dark web platforms are used for manipulating victims and exchanging illicit goods.
Current Status:
Ongoing Investigation: The investigation into Marghiem, Sorensen Joachim, and their associates continues. Authorities suspect that their activities span multiple jurisdictions and may be connected to larger international cybercrime operations.
If you need specific data extraction or further details on particular aspects, feel free to ask!
To correlate smartphone data in the context of a cybercrime investigation, several factors need to be considered. This includes information such as the smartphone's usage patterns, communication logs, locations, and the applications installed on the devices. Based on the cybercrime network described in the document, here’s a potential outline for correlating smartphone data with the individuals involved:
Communication Data
Phone Numbers & Call Logs:
Investigators would look for connections between the suspects (Ronnie Marghiem, Kim Rindom Sorensen Joachim, Alex Brandt, Brandy Clegg Williams) through their call logs, including incoming and outgoing calls. Patterns of communication, such as frequent calls to specific numbers or international calls, might indicate collaboration or coordination between these individuals or their associates.
Text Messages & Messaging Apps: Text logs from messaging platforms (SMS, WhatsApp, Signal, Telegram) would provide insight into their coordination for criminal activities, especially encrypted communications to avoid detection. These records might reveal planning for fraudulent activities, or involvement in hacking operations or money laundering schemes.
Geolocation Data
GPS Tracking & Location History:
Smartphones regularly track their location via GPS. By analyzing geolocation data, investigators can map out where suspects have been during certain timeframes. For instance, if Ronnie Marghiem and Kim Rindom Sorensen Joachim were present at the same locations (e.g., a residence used as a hub for cybercrime), it could confirm their involvement in a particular operation.
Cross-referencing location data from their smartphones with physical evidence (such as photos, videos, or police reports) could pinpoint exact times and locations of the criminal activities.
App Usage & Digital Footprint
App Data:
Smartphones often store data related to installed apps. Investigators would look for specific applications that may aid in cybercrime activities. This might include:
VPN apps (for masking IP addresses and online activity),
Dark web browsers (like Tor), which would allow access to illicit marketplaces or forums,
Cryptocurrency wallets, which are used to launder funds,
Encrypted messaging apps (like Signal, Telegram, WhatsApp), used to communicate securely with other members of the cybercrime syndicate.
Social Engineering Tools: If the suspects used any apps or tools specifically for social engineering (e.g., phishing kits or fake identity generators), this data would be invaluable for understanding their methods of operation.
Device Interactions & Network Data
Wi-Fi and Bluetooth Connections:
Smartphone data can also show which Wi-Fi networks and Bluetooth devices a person connected to. Correlating this data with known addresses or individuals involved in the cybercrime operation could link suspects to specific locations or interactions.
Network Activity Logs: Tracking network activity from the smartphones (e.g., IP addresses, MAC addresses) may help identify unauthorized connections to secure systems or websites tied to criminal activities.
Account Data
Social Media & Online Accounts:
Investigators would look into any social media or online accounts linked to the suspects. Smartphones often store login data for platforms like Facebook, Instagram, Twitter, and more. If any criminal activity was discussed or planned via social media, it could provide crucial evidence.
Financial Accounts: Smartphones linked to cryptocurrency wallets, bank apps, or e-commerce sites would reveal financial transactions tied to money laundering or fraud activities. Correlating transaction data with the dates and locations of criminal activities could link the suspects directly to illicit financial operations.
Device Forensics
Data Extraction & Forensic Analysis:
If law enforcement seized smartphones as part of the investigation, forensic tools would be used to extract data from the devices. This could involve recovering deleted text messages, hidden apps, or data wiped using factory resets.
SIM Card Analysis: Examining the SIM card could provide access to call logs, text message histories, and associated phone numbers, linking multiple suspects or individuals tied to the cybercrime network.
Cross-Referencing with Public Records and Investigation Data
Public Records: Investigators could cross-reference smartphone data with other public records, such as addresses, property ownership, or criminal history, to uncover relationships between suspects and their contacts. This is particularly relevant for individuals involved in identity theft, money laundering, or fraud.
Police Reports & Criminal History: By examining existing criminal records and police reports, investigators can compare the timeframes and locations mentioned in smartphone data with prior investigations. For example, if Kim Rindom Sorensen Joachim has a history of using certain aliases, data from her phone (including contact numbers or email addresses) might reveal whether these aliases were used in other fraudulent schemes.
Link Analysis
Correlating Data Points:
By integrating the smartphone data with other pieces of evidence (e.g., financial transactions, physical locations, email addresses, and phone numbers), investigators can create a link analysis map. This would help visualize the relationships between suspects, associates, and other criminal entities.
Phone Number Correlation: If phone numbers from the suspects' smartphones appear in other investigations or databases, this would allow investigators to link them to additional criminal activity or associates in different parts of the world.
Challenges in Smartphone Data Correlation
Encrypted Communication: Many criminals use encrypted apps to prevent law enforcement from accessing their communications. Breaking into these systems often requires legal warrants and specialized tools.
Anonymizing Tools: Criminals often use VPNs and other anonymizing tools that make it difficult to trace their actual location or identity.
Data Deletion & Destruction: Criminals frequently erase data or use apps that automatically delete messages after they are read. However, forensic experts can still sometimes recover deleted information from devices if they have physical access to the phone.
Conclusion
Smartphone data is a crucial part of cybercrime investigations, particularly in cases like this one, where suspects are involved in complex, high-tech criminal activities. By collecting, analyzing, and correlating smartphone data—such as communication logs, geolocation data, app usage, and network interactions—law enforcement can uncover hidden connections between individuals, identify patterns of illegal activity, and gather critical evidence for prosecution.
If you have specific data points or would like to explore particular aspects of smartphone data, let me know! I can help further break down how such data could correlate with the individuals mentioned.
IP Address and IMEI Number Correlation in Cybercrime Investigations
In cybercrime investigations, IP addresses and IMEI numbers (International Mobile Equipment Identity) are vital for tracing and correlating suspect activities. Here’s an expanded overview of how these data points can be used:
IP Address Correlation
An IP address is a unique identifier assigned to a device when it connects to the internet. It allows for the tracing of the device’s online activities, including web traffic, geographical location, and links to specific actions. Here’s how investigators can use IP addresses:
Uses of IP Address in Cybercrime Investigations:
Tracking Online Activities:
Fraudulent Transactions: Cybercriminals often use specific IP addresses when carrying out illegal activities like identity theft, wire fraud, or money laundering. Investigators can trace IP addresses linked to suspicious activity, such as accessing a financial institution’s website, logging into accounts, or making unauthorized transactions.
Accessing Illicit Sites: If the suspects are involved in dark web transactions, IP addresses can be cross-referenced with illicit marketplaces or hacking forums. IP addresses from devices used by suspects (e.g., Ronnie Marghiem or Kim Rindom Sorensen Joachim) can be correlated with the IPs logged on dark web servers.
VPNs and Anonymity: While criminals often use VPNs (Virtual Private Networks) to mask their true location, IP address correlation can still reveal patterns. For example, an IP address originating from a specific country or region might be connected to fraud attempts or hacking activities even if a VPN was used. Multiple VPN nodes may be traced back to a central server, providing further insight into criminal networks.
Geolocation and Location Analysis:
Tracking Suspects’ Locations: IP addresses can provide general geographic locations (e.g., city or country). If law enforcement has multiple logs from the same IP address, it’s possible to trace the physical location of suspects at the time of their illegal activities.
Correlating with Crime Scenes: Geolocation data from IP addresses can be cross-referenced with physical crime scene locations. For example, if Ronnie Marghiem is suspected of accessing a cybercrime hub or making fraudulent transactions from a specific location, the IP address can show if he was connected to the internet from that area.
Connection to Devices and Accounts:
Linking Multiple Devices: A single IP address can be associated with multiple devices. If the cybercriminals are using the same IP address for various devices (phones, laptops, etc.), investigators can tie their online activities together and determine if multiple suspects are operating in tandem or using shared resources for criminal purposes.
User Login History: IP addresses from social media accounts, online banking, or even email services can help investigators track the login history and correlate it with known criminal activity. For example, if Kim Rindom Sorensen Joachim has accessed a bank account from the same IP address as Ronnie Marghiem, this could indicate that both were involved in a coordinated fraud attempt.
IMEI Number Correlation
An IMEI number is a unique identifier assigned to a mobile phone or device, essential for tracking the physical device, especially in cases of theft or fraud. Here's how investigators can use IMEI numbers:
Uses of IMEI Number in Cybercrime Investigations:
Device Identification and Tracking:
Trace Stolen Devices: If smartphones used in cybercrime activities are seized or tracked, investigators can cross-reference their IMEI numbers to ensure that the devices being used belong to the suspects or are linked to the crime. IMEI numbers help law enforcement link devices to specific suspects.
Preventing SIM Swapping and Identity Theft: If a criminal uses a device for SIM swapping (switching the victim's phone number to another device) to facilitate identity theft, the IMEI number can help authorities trace the exact device used in the crime, distinguishing it from legitimate devices.
Linking Devices to Locations:
Similar to IP address correlation, the IMEI number can be used to track the location of mobile phones via network logs. For example, if Ronnie Marghiem used his smartphone for illicit transactions or to coordinate illegal activities, investigators can pinpoint the time and place where the device was used.
This information can correlate with geolocation data from phone networks (via cell towers) or Wi-Fi connections to map out where a suspect was located during specific cybercrimes.
Cross-referencing with Call Logs and Messaging:
IMEI numbers are logged by telecommunication companies when phones make calls, send messages, or access the internet. Investigators can use these logs to verify which IMEI number was used for certain communications or actions, such as text messages about wire fraud or making calls to accomplices during money laundering schemes.
In cases of social engineering, where criminals manipulate victims into sharing sensitive information, IMEI numbers can provide direct evidence of the devices used to initiate these fraudulent activities. For example, Kim Rindom Sorensen Joachim may have used a specific phone to contact victims or coordinate with other criminals.
Device Forensics:
IMEI data is often included in forensic device investigations, where law enforcement analyzes a suspect’s phone for deleted files, texts, or call history. The IMEI number ensures that the data being analyzed corresponds to a specific phone, and investigators can check its relationship to the suspects and their criminal activities.
SIM card analysis can also link a suspect to a specific IMEI number, showing if a particular phone was used by the suspect in illicit activities, even if they switched SIM cards or tried to hide their identity.
Cross-Correlation of IP Address and IMEI Numbers in Cybercrime Investigations
The integration of IP address and IMEI number data offers a more comprehensive approach to identifying and linking devices, activities, and suspects.
Correlating Mobile Phone Data with Online Actions: By matching IMEI numbers from devices with IP addresses used to access fraudulent websites, social media accounts, or financial platforms, investigators can confirm that a suspect used a specific device to commit the crime.
Tracking Device Movement: Combining IMEI number location tracking with IP address geolocation data helps investigators track both the physical movement of devices (via cell towers) and their digital movement (via the internet). For instance, if Ronnie Marghiem was using a smartphone with a specific IMEI number while making fraudulent transactions from a particular IP address, this data can help law enforcement pinpoint his exact location during the operation.
Uncovering Additional Links: If a suspect uses multiple phones, IMEI numbers can be cross-referenced to link those devices together, even if they’re using different IP addresses to mask their true location. This helps establish a broader network of activity and may lead to discovering additional suspects or accomplices in the crime.
Challenges in IP and IMEI Correlation
Encryption & VPN Usage: Criminals often use encryption tools or VPNs to obscure their IP addresses, making it harder to directly trace their online activities. However, forensic analysis of the device’s physical data and network logs can still provide valuable insight.
Device Spoofing: Cybercriminals may attempt to disguise their IMEI numbers or use devices with cloned IMEI numbers to avoid detection. While these can sometimes be circumvented with forensic techniques, it requires advanced tools and expertise.
Data Privacy: Accessing IMEI number and IP address information requires legal authorization. Authorities must ensure they comply with data privacy laws, such as obtaining warrants for tracking phone data or accessing telecommunication logs.
Conclusion
By correlating IP addresses with IMEI numbers, investigators can track a cybercriminal’s digital and physical presence, uncovering connections between suspects, locations, and criminal activities. This data is particularly valuable when tracing fraudulent transactions, identity theft, or hacking operations. If law enforcement gains access to relevant logs and devices, they can piece together the movements and actions of individuals like Ronnie Marghiem and Kim Rindom Sorensen Joachim, ultimately building a strong case against them.
If you need assistance analyzing or exploring specific IP or IMEI data related to the investigation, let me know!
To retrieve phone numbers from public records, it’s important to understand the different types of records and sources where these phone numbers might be listed. In a cybercrime investigation, public records can sometimes reveal links between suspects, their associates, and the activities they are involved in. Here’s an overview of the types of public records that might include phone numbers:
Voter Registration Records
Description: In some jurisdictions, voter registration records contain personal information about individuals, including their address and sometimes their phone number.
How It’s Useful: If an individual (such as Ronnie Marghiem or Kim Rindom Sorensen Joachim) is registered to vote, this record can potentially include their current contact information, including phone numbers, especially if their registration form was updated with personal details.
Access: These records are typically accessible through local government websites or election boards. However, access to phone numbers might be restricted depending on the location.
Property Records
Description: Property records include details of real estate ownership and transactions, which often contain the owner's name, address, and sometimes a phone number or email address.
How It’s Useful: If any of the suspects own properties (e.g., Ronnie Marghiem or Brandy Clegg Williams), property records can link them to specific addresses and possibly provide contact information.
Access: Property records can usually be accessed via local government websites or real estate databases. The level of detail provided can vary, and phone numbers may or may not be included.
Court and Legal Records
Description: Court documents related to civil or criminal cases often list the contact information for the individuals involved, including their phone numbers.
How It’s Useful: Criminal or civil court records related to prior arrests, cases of fraud, or lawsuits can be useful for finding phone numbers associated with the suspects. These records may list phone numbers of suspects, attorneys, or other involved parties.
Access: Public access to court records is typically available through online portals provided by the local court system or through third-party legal document databases. Some jurisdictions may require a fee to access detailed records.
Business and Professional Licenses
Description: If an individual is involved in running a business or holds a professional license (such as a doctor, lawyer, or contractor), their business or professional license records may contain a phone number.
How It’s Useful: If Kim Rindom Sorensen Joachim or Ronnie Marghiem (or any associated individual) operates a business or holds a professional license, these records can help uncover their contact details.
Access: These records can often be found through state or local regulatory boards and may include personal phone numbers tied to businesses.
Online Directories
Description: Online phone directories such as Whitepages, Spokeo, or TrueCaller allow users to search for phone numbers tied to addresses or names.
How It’s Useful: These services can often provide phone numbers linked to individuals, including cell phones or landlines. By searching the names of suspects or their associates, investigators may uncover personal phone numbers associated with them.
Access: Public access to some information may be free, while other databases may require a paid subscription for detailed or recent information.
Social Media and Online Profiles
Description: Social media profiles often contain contact details, including phone numbers, especially if users have chosen to make that information public.
How It’s Useful: If Ronnie Marghiem or Kim Rindom Sorensen Joachim are active on platforms like Facebook, Instagram, or LinkedIn, investigators could search these platforms for publicly available phone numbers.
Access: Access to this information depends on the privacy settings of the individuals' profiles. Some people may voluntarily list their phone numbers on social media for professional or personal reasons.
Public Utility Records
Description: Utility records (e.g., electricity, water, internet) often include the names and contact details of account holders.
How It’s Useful: If any of the suspects have utility services in their name, these records may provide phone numbers that were provided for the account.
Access: Access to these records is generally restricted due to privacy laws, but they may be obtainable with a legal warrant or during an investigation involving law enforcement.
Government Databases
Description: In some jurisdictions, government agencies maintain databases that include contact information for individuals receiving public services, such as welfare or unemployment benefits.
How It’s Useful: These databases can reveal phone numbers associated with individuals who may not be easily reachable through public records like property or voter registration.
Access: Access to government databases is typically restricted to law enforcement or those with specific permissions, and they may require legal authorization to obtain.
Telephone Companies and Carrier Records
Description: Telecommunication providers store records of customers, including phone numbers, addresses, and service details.
How It’s Useful: If Ronnie Marghiem, Kim Rindom Sorensen Joachim, or their associates have been involved in fraudulent activities like SIM swapping or fraudulent account creation, telco records could reveal the contact numbers linked to these activities.
Access: Law enforcement may obtain these records through a subpoena or warrant, especially if there is suspicion of criminal activity tied to the phone numbers.
Genealogy and Public Record Databases
Description: Genealogy websites such as Ancestry.com or FamilySearch may offer access to historical public records, such as census records or family archives, that sometimes include phone numbers.
How It’s Useful: These databases can be used to gather historical contact details for family members or relatives of suspects, potentially shedding light on further connections.
Access: These services often require a subscription or specific legal permissions to access certain records.
Challenges in Accessing Phone Numbers
Privacy Laws: Privacy protections often limit the availability of personal phone numbers, especially when it comes to government databases or private service providers.
Redaction of Personal Data: Many public records are redacted for privacy reasons, and phone numbers might be omitted or obscured.
Accuracy and Currency: Public records may not always reflect the most current or accurate contact details, as people change their numbers or update their addresses.
Conclusion
Phone numbers from public records can provide critical leads in a cybercrime investigation. Whether through voter registration, court records, property databases, or online directories, these numbers can help correlate suspects, track criminal activity, or identify associates involved in illicit operations. If you are specifically looking to correlate phone numbers with known suspects such as Ronnie Marghiem or Kim Rindom Sorensen Joachim, accessing a combination of the sources above could help uncover relevant contact details.
If you need help searching for specific phone numbers or further details from public records, let me know!
1 note
·
View note
Text
iPhone Data Recovery: Restore Your Lost Data Safely

Losing important data on your iPhone can be frustrating and stressful. Whether due to accidental deletion, software glitches, or hardware issues, regaining access to your photos, messages, and files is essential. Fortunately, professional iPhone data recovery services offer effective solutions to retrieve lost or inaccessible data without causing further damage to your device.
Common Reasons for iPhone Data Loss
Accidental Deletion
Files, messages, or photos might get removed unintentionally.
iOS Software Updates or Bugs
System updates can lead to data loss, especially if backups are not up-to-date.
Device Damage
Water exposure or a cracked phone can make data inaccessible.
Forgotten Password or Lockout
Data becomes unreachable if the phone is locked and you cannot recover the passcode.
Corrupted Backup Files
Backups in iCloud or iTunes might become corrupted and unusable.
How Professional Data Recovery Works
1. Device Diagnosis
Technicians perform an initial analysis to understand the extent of data loss and whether recovery is feasible.
2. Safe Data Extraction
Using specialized tools, experts access the phone's memory to extract recoverable data.
3. Data Preview and Verification
Recovered files are previewed to confirm that the essential data—like photos, messages, or contacts—has been successfully retrieved.
4. Data Restoration to Device or Backup
Once verified, the data can be transferred back to the iPhone or saved to an external backup system, such as iCloud or a computer.
Types of Data That Can Be Recovered
Photos and Videos
Contacts and Call History
Messages and iMessage Conversations
Notes and Calendar Entries
WhatsApp and Social Media Data
App-Specific Files
Benefits of Professional iPhone Data Recovery
High Recovery Success Rate: Experts use advanced tools for maximum data retrieval.
Prevents Data Overwriting: Professional services ensure that no additional data is lost during the process.
Support for All iOS Devices: Works across various iPhone models and iOS versions.
Secure Process: Your data is handled confidentially, protecting your privacy.
Recovery from Physical Damage: Even if your iPhone is damaged, data recovery may still be possible.
DIY Data Recovery: Risks and Limitations
While some software tools promise to recover lost data, they come with risks:
Risk of Overwriting Data: New data written to your phone can make recovery impossible.
Incomplete Recovery: DIY tools might not recover all data or support certain file types.
Potential for Further Damage: Unskilled attempts can damage the phone’s internal storage or worsen existing issues.
Time-Consuming Process: Without professional tools, recovery can be slow and frustrating.
How to Prevent Data Loss in the Future
Regular Backups: Use iCloud or iTunes to back up data frequently.
Enable Auto-Backup: Keep auto-backups enabled to minimize loss in case of device failure.
Use Data Recovery Apps with Caution: Avoid unreliable apps that could corrupt files further.
Update iOS Carefully: Ensure all data is backed up before performing software updates.
Protect Your Device: Use cases and screen protectors to prevent accidental damage.
Why Choose AppleExpert for iPhone Data Recovery
Expert Technicians: Our team specializes in recovering data from all iPhone models.
Advanced Tools and Methods: We use the latest technology to maximize recovery success.
Fast Turnaround Time: Get your essential data back as quickly as possible.
Confidential Service: Your privacy and data security are our top priority.
No Recovery, No Fee Policy: You only pay if we recover your data.
Losing data on your iPhone doesn’t have to be permanent. With professional iPhone data recovery, you can regain access to your photos, messages, and other valuable information. Avoid risky DIY methods and trust the experts for a safe and reliable recovery process. Whether your phone is physically damaged or experiencing software issues, timely recovery efforts can bring your data back and restore peace of mind.
0 notes
Text
RT Table In SAP HR

Understanding the RT Table in SAP HR
In SAP Human Resources (HR), the RT table plays a critical role in storing and managing payroll results. Understanding its function and how to access it is beneficial for HR specialists, payroll administrators, and SAP consultants. Let’s dive in!
What exactly is the RT Table?
The RT table stands for “Results Table.”
It is a dynamic, internal table generated each time payroll is executed in the SAP HR system.
It holds calculated wage types and their corresponding values for each employee in the payroll run.
What Data Does the RT Table Hold?
The RT table houses crucial payroll-related information, including:
Wage Types: Identifiers for different payment components (e.g., basic salary, overtime, bonuses, deductions, etc.)
Amounts: The calculated monetary values for each wage type.
Number/Rate: For wage types based on a quantity or rate (e.g., hours worked, hourly rate).
Period Parameters: Time intervals relevant to the calculation (e.g., start date, end date).
Why is the RT Table Important?
Payroll Reporting and Analysis: The RT table is the source for various payroll reports, which extract wage types, amounts, and other relevant data for analysis and audits.
Integration: Wage type values in the RT table can be transferred to other modules, such as Financial Accounting (FI), to post costs.
Retroactive Payroll Calculations: The RT table serves as a reference point if payroll needs to be rerun with changes from previous periods.
How to Access the RT Table
There are several ways to view the contents of the RT table:
Transaction Codes:
PC_PAYRESULT: General payroll result viewer
PC00_M99_CWTR: Cluster display of results table
Payroll Log: The RT table data is displayed during relevant processing steps within a specific employee’s payroll log.
ABAP Programming: For custom reports or data extractions, ABAP programmers can access the RT table using function modules like:
RP_PROVIDE_FROM_LAST
CU_READ_RGDIR
Important Considerations
The RT table is temporary and is overwritten each time payroll is run.
To retain historical payroll results, essential data from the RT table is transferred to other tables like CRT (Cumulation Results Table).
Being a dynamic internal table, the RT table doesn’t have a fixed database table counterpart.
In Conclusion
The RT table is a central pillar of the SAP HR payroll process. Understanding its purpose, contents, and access methods empowers SAP HR users to manage, analyze, and report on their payroll data effectively.
youtube
You can find more information about SAP HR in this SAP HR Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP HR Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP HR here – SAP HR Blogs
You can check out our Best In Class SAP HR Details here – SAP HR Training
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
1 note
·
View note
Text
SAP GRC Reports and Analytics
SAP GRC Reports and Analytics: The Key to Informed Risk Management
Governance, Risk, and Compliance (GRC) is an essential framework for organizations to ensure they meet regulations, mitigate risks, and operate with integrity. SAP GRC solutions provide a powerful suite of tools to streamline these processes but to get the most value; you need to harness the power of reports and analytics.
Why SAP GRC Reports and Analytics Matter
Data-Driven Insights: Reports and analytics transform GRC data into digestible visualizations and actionable insights. This allows you to see the bigger picture, identify trends, and identify potential risk areas.
Process Improvement: By analyzing key performance indicators (KPIs) and metrics, you can pinpoint bottlenecks, redundancies, and opportunities to optimize GRC processes.
Risk Mitigation: Get proactive about risk management using predictive analytics and pattern recognition in your GRC reports. This allows you to address potential issues before they escalate.
Compliance Verification: Detailed reports help demonstrate compliance with industry regulations and internal standards, simplifying audits and easing the burden on your teams.
Key Features of SAP GRC Reports and Analytics
Centralized Repository: SAP GRC provides a unified reporting workspace where you can access all relevant data across different GRC modules (Access Control, Process Control, Risk Management).
Pre-Built Reports: Choose from a library of standardized reports covering risk analysis, user access, segregation of duties (SoD) conflicts, and more. You can run these immediately, reducing setup time.
Customizable Dashboards: Design visual dashboards tailored to specific roles or needs. Combine charts, graphs, and real-time metrics to get a quick overview of your GRC landscape.
Flexible Data Extraction: Use SAP GRC’s reporting functionalities to export data into formats like Excel or other business intelligence (BI) tools for even deeper custom analysis if needed.
Best Practices for Getting the Most out of SAP GRC Reporting
Goal Setting: Determine the specific outcomes you want to achieve with your reports. Is it compliance reporting, risk trend analysis, or process efficiency?
KPI Definition: Identify the metrics that truly matter to your organization’s GRC framework. Track metrics that show the effectiveness of your controls, risk exposure, and compliance adherence.
Stakeholder Involvement: Work with relevant business units and GRC specialists to tailor reports to meet the needs of different audiences.
Continuous Review: Update reports as risks, regulations, and business processes evolve. Review your dashboards regularly to ensure KPIs stay relevant.
Taking it Further
Consider integrating SAP GRC data with a dedicated business intelligence (BI) platform for even more sophisticated analysis and visualization. This offers greater flexibility in data modeling and the ability to create highly polished and interactive reports.
Conclusion
SAP GRC Reports and Analytics are a core component of a mature GRC strategy. By embracing these capabilities, you can shift from reactive compliance to proactive risk management, empowering your organization to make informed decisions for greater resilience and long-term success.
youtube
You can find more information about SAP GRC in this SAP GRC Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP GRC Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP GRC here – SAP GRC Blogs
You can check out our Best In Class SAP GRC Details here – SAP GRC Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
#Unogeeks #training #Unogeekstraining
1 note
·
View note
Text
ORACLE APEX 21 DOWNLOAD

Oracle APEX 21: Your Guide to Download and Installation
Oracle Application Express (APEX) is a robust low-code development framework that lets you build sophisticated, data-driven web applications with minimal coding. With the release of APEX 21, you can access an impressive range of new features and enhancements and a sleek new user interface. This blog will guide you through downloading and setting up Oracle APEX 21.
Prerequisites
Before you begin, here’s what you’ll need:
Oracle Database: A supported Oracle Database version (11g Release 2 or later). Check [invalid URL removed] for compatible versions.
Web Listener: Oracle REST Data Services (ORDS) or Oracle HTTP Server (OHS) with mod_plsql.
Installation Steps
Unzip the File: Once the download is complete, extract the contents of the downloaded ZIP file.
Run SQL Script: Navigate to the unzipped ‘apex’ directory and find the apex_installation.sql script. Connect to your Oracle Databa e as the SYS user using SQL*Plus or SQL Developer and execute this script.
Unlock the ANONYMOUS Account: After installation, you must unlock the ANONYMOUS account to enable external access to your database. You can do this using SQL commands or the Oracle Database administration tools.
Install Images: Copy the ‘images’ directory, where you extracted the A EX download, to a location accessible by your web listener. Configure your web listener to serve files from this directory.
Accessing Your APEX Instance
Once installation is complete, you can typically access your APEX instance by entering the f following URL into your web browser and substituting the relevant information:
The APEX login screen will greet you. Use the following default credentials:
Workspace: INTERNAL
Username: ADMIN
Password : (The password you set during installation)
Important Notes:
Oracle APEX is a free feature of the Oracle Database, so you don’t need separate licenses.
Refer to the official Oracle APEX documentation for detailed installation instructions, troubleshooting, and security considerations.
Getting Started with Oracle APEX
So, start building fantastic web applications if you’ve fully downloaded and installed Oracle APEX 21! Oracle provides a wealth of resources – tutorials, a vibrant community, and excellent documentation – to help you navigate this powerful tool.
youtube
You can find more information about Oracle Apex in this Oracle Apex Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for Oracle Apex Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Oracle Apex here – Oarcle Apex Blogs
You can check out our Best In Class Oracle Apex Details here – Oracle Apex Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
0 notes
Text
Ariba VIM

Title: Streamlining Invoice Management with SAP Ariba VIM
Introduction
In today’s fast-paced business environment, invoice management can be cumbersome and error-prone. Paper-bas d invoices, manual data entry, and mismatched information can lead to delayed payments, lost discounts, and strained vendor relationships. SAP Ariba VIM (Vendor nvoice Management) offers a powerful solution to streamline the invoice process, saving businesses time, money, and resources.
What is SAP Ariba VIM?
SAP Ariba VIM is a cloud-based solution that automates and optimizes accounts payable processes. It integrates seamless y with SAP ERP systems and the Ariba Network, enabling businesses to receive, process, and reconcile invoices electronically. Key functionalities i lude:
Invoice Capture: VIM captures invoices from various sources like email, EDI, scans, and the Ariba Network. Its intelligent OCR (O tical Character Recognition) technology extracts high-quality invoice data, reducing manual effort.
Workflow and Approvals: VIM facilitates customizable workflows for invoice review and approval. Rules and automatic routing ensure timely approvals and minimize bottlenecks.
Invoice Matching: VIM automatically matches invoice data with purchase orders and receipts (2-way or 3-way matching) to ensure accuracy and prevent discrepancies.
Exceptions and Disputes: Exception handling mechanisms within VIM enable streamlined management of disputed or incorrect invoices.
Analytics and Reporting: VIM provides robust reporting and dashboards that provide insights into invoice processing performance and identify potential areas for improvement.
Benefits of Using SAP Ariba VIM
Efficiency and Cost Savings: Ariba VIM eliminates manual processes, reducing processing times and minimizing errors. This ultimately leads to significant cost savings.
Improved Compliance: VIM promotes transparency, provides audit trails, and enforces controls, strengthening compliance with internal policies and external regulations.
Faster Payment Cycles: Automated matching and approvals accelerate invoice processing, enabling businesses to take advantage of early payment discounts.
Enhanced Vendor Relationships: Ariba VIM’s transparency and timely payments help strengthen vendor relationships.
Scalability: Ariba VIM’s cloud-based nature makes it flexible to accommodate changing business needs.
Is SAP Ariba VIM Right for Your Business?
SAP Ariba VIM is a precious solution for businesses that:
Process a large volume of invoices regularly
Want to reduce the manual effort involved in accounts payable processes
Desire greater control and visibility over their invoice processing
Wish to improve working capital management and capture more discounts
Aim to strengthen supplier relationships
Implementation and Integration
While SAP Ariba VIM offers many compelling benefits, careful planning is critical for successful implementation. Consider:
Integrations Seamless integration with your existing ERP system is crucial.
Change Management: Effective communication and training help minimize user resistance and maximize adoption.
Customization: Define and configure workflows that match your specific approval processes.
Conclusion
SAP Ariba VIM offers the power to revolutionize invoice management processes. It delivers a tangible return on investment by reducing costs, improving efficiency, and boosting compliance. SAP Ariba VIM is undoubtedly worth exploring if your business is king to streamline accounts payable functions.
youtube
You can find more information about SAP ARIBA in this SAP ARIBA Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP ARIBA here – SAP ARIBA Blogs
You can check out our Best In Class SAP ARIBA Details here – SAP ARIBA Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
1 note
·
View note
Text
Ariba Accounts Payable

Unlocking Efficiency with Ariba Accounts Payable
Accounts payable (AP) departments face the constant pressure of managing invoices, payments, and supplier relationships efficiently. Fortunately, SAP Ariba offers a cloud-based solution to streamline and automate these processes, saving businesses time, money, and headaches.
What is Ariba Accounts Payable?
Ariba Accounts Payable is part of the SAP Ariba suite, a powerful procurement platform. It’s designed to digitize the entire invoice-to-pay process to improve accuracy, visibility, and control. Key features include:
Invoice Capture and Automation: Ariba can receive invoices in various formats (paper, PDF, EDI). It uses intelligent data capture to extract information automatically, reducing manual data entry.
Automated Matching and Approvals: Built-in rules and workflows match invoices to purchase orders and contracts. Approvals are routed through the appropriate hierarchy, speeding up the process.
Collaboration and Visibility: The Ariba Network connects buyers and suppliers, facilitating real-time communication, invoice tracking, and dispute resolution.
Analytics and Reporting: Ariba provides detailed insights into spend, payment cycles, supplier performance, and more, helping optimize cash flow.
Why Choose Ariba Accounts Payable?
Adopting Ariba Accounts Payable brings about numerous benefits:
Reduced Costs: Eliminate paper-based processes, streamline workflows, and reduce errors to cut invoice processing costs significantly.
Improved Efficiency: Automation eliminates manual tasks, allowing AP teams to focus on strategic initiatives and problem resolution.
Enhanced Compliance: Automated matching and built-in controls help ensure compliance with internal policies and external regulations.
Stronger Supplier Relationships: Ariba’s portal provides suppliers with transparent invoice and payment status, strengthening partnerships.
Optimized Cash Flow: Early payment discounts can be captured more consistently through faster processing and better visibility.
Tips for a Smooth Ariba AP Implementation
Clearly Define Goals: Establish the specific pain points you want Ariba to solve and set measurable targets for improvement.
Get Stakeholder Buy-in: Communicate the benefits of Ariba automation to all stakeholders – AP teams, procurement, finance, and suppliers.
Configure Thoroughly: Work closely with an Ariba implementation partner to configure the system to match your unique workflows and requirements.
Train Thoroughly: Ensure your AP team, approvers, and suppliers thoroughly understand the system’s features and how to use it effectively.
Start Small, Iterate, and Scale: Begin with a pilot group or a select group of suppliers and then gradually expand Ariba’s use across your organization.
The Future of Accounts Payable
Ariba Accounts Payable offers a glimpse into the future of AP processes. As automation and AI technology evolve, we can expect even higher levels of efficiency, accuracy, and strategic decision-making power. By embracing solutions like Ariba, businesses can stay ahead of the curve, gain a competitive advantage, and thrive in a rapidly changing business environment.
youtube
You can find more information about SAP ARIBA in this SAP ARIBA Link
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on SAP ARIBA here – SAP ARIBA Blogs
You can check out our Best In Class SAP ARIBA Details here – SAP ARIBA Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeek
1 note
·
View note
Text

WhatsApp user data scraper
In today’s fast-paced digital landscape, effective communication is paramount, especially for businesses aiming to connect with customers and clients. With over two billion users, WhatsApp has emerged as a vital tool for both personal and professional communication. However, managing contacts efficiently can be a daunting task. This is where a WhatsApp contact extractor comes into play, offering a streamlined solution for businesses and individuals alike.
What is a WhatsApp Contact Extractor?
A WhatsApp contact extractor is a tool designed to gather and organize contacts from WhatsApp chats and groups. This can be particularly beneficial for marketers, sales teams, and anyone who needs to maintain an extensive network. Instead of manually saving contacts one by one, an extractor automates the process, saving valuable time and effort.
Why Use a WhatsApp Contact Extractor?
Efficiency and Time-SavingThe primary advantage of using a WhatsApp contact extractor is the efficiency it brings. For businesses with large groups or active chat threads, manually compiling contact information can be tedious and time-consuming. With an extractor, you can quickly compile a list of contacts in just a few clicks.
Enhanced Marketing StrategiesIn the realm of marketing, targeted outreach is crucial. A WhatsApp contact extractor allows businesses to gather contacts for segmentation and personalized messaging. By having a comprehensive list of contacts, companies can tailor their marketing strategies, ensuring that messages resonate with the right audience.
Improved NetworkingNetworking is essential in today’s business environment. A contact extractor helps professionals expand their network effortlessly. By consolidating contacts from various chats and groups, users can easily reach out and establish connections, fostering potential collaborations and partnerships.
How to Choose the Right WhatsApp Contact Extractor
When selecting a WhatsApp contact extractor, consider the following factors:
User-Friendly InterfaceOpt for a tool that is easy to navigate, even for those who may not be tech-savvy. A straightforward interface ensures that users can extract contacts without hassle.
CompatibilityEnsure that the extractor is compatible with your device and WhatsApp version. Some tools may work better on specific platforms, so it’s crucial to do your research beforehand.
Privacy and SecuritySince contact information is sensitive, prioritize extractors that adhere to strict privacy policies. Look for tools that provide secure data handling and storage to protect your information.
Customer SupportReliable customer support can make a significant difference, especially if you encounter issues or have questions. Choose a tool with responsive support to assist you whenever needed.
Tips for Using a WhatsApp Contact Extractor Effectively
Regular UpdatesTo ensure your contact list remains current, consider using the extractor regularly. Regular updates will help you maintain an accurate database, which is crucial for effective communication.
Data OrganizationOnce you’ve extracted contacts, take the time to organize them into categories. This can be based on customer interests, demographics, or any other relevant criteria. An organized contact list will enhance your outreach efforts.
Respect PrivacyAlways remember to respect the privacy of the contacts you gather. Use the extracted information responsibly and ensure that you have permission before reaching out, especially for marketing purposes.
Conclusion
In a world where communication is key, a WhatsApp contact extractor is an invaluable tool for anyone looking to optimize their networking and outreach efforts. By automating the process of collecting and organizing contacts, users can focus on what truly matters: building relationships and growing their business. With the right extractor in hand, you’ll not only save time but also enhance your communication strategies, paving the way for success in your personal and professional endeavors.
Whether you’re a small business owner or a marketing professional, leveraging a WhatsApp contact extractor can significantly impact how you connect with your audience. So, take the plunge and experience the efficiency that comes with streamlined contact management today!
#WhatsApp contact extractor#WhatsApp number scraper#Global phone number downloader#Contact harvesting tool#International WhatsApp data extraction#Phone number scraper software#Worldwide contact finder#Global#phone directory scraper#WhatsApp data mining tool#International contact extraction
0 notes
Text

Unveiling the Power of WhatsApp Contact Extractor: Simplify Your Outreach Efforts
In the fast-paced digital era, communication is key, and WhatsApp has become an integral part of our daily interactions. For businesses and individuals looking to streamline their outreach efforts, the WhatsApp Contact Extractor emerges as a powerful tool, revolutionizing the way contacts are managed. In this blog, we will delve into the features, benefits, and practical applications of this tool that is reshaping the landscape of digital communication.
Understanding the WhatsApp Contact Extractor
WhatsApp Contact Extractor is a tool designed to simplify the process of gathering contacts from the popular messaging platform, WhatsApp. Whether you're a business owner, marketer, or an individual managing personal connections, this tool empowers you to extract contact information efficiently and enhance your outreach strategy.
Key Features of WhatsApp Contact Extractor
Efficient Data Extraction:
The primary function of this tool is to extract contact details from your WhatsApp account swiftly. It automates the process, saving you time and effort in manually collecting information.
Versatility in Data Types:
WhatsApp Contact Extractor allows you to extract various types of data, including phone numbers, names, and additional details available on WhatsApp profiles. This comprehensive approach ensures that you have all the necessary information for your outreach campaigns.
User-Friendly Interface:
The tool is designed with simplicity in mind. Its user-friendly interface makes the extraction process accessible to both novices and seasoned users, requiring minimal technical expertise.
Customizable Search Parameters:
Tailor your extractions based on specific criteria such as groups, individual chats, or a combination of both. This level of customization enables you to target your extractions with precision.
Practical Applications of WhatsApp Contact Extractor
Business Marketing Campaigns:
For businesses looking to bolster their marketing efforts, the WhatsApp Contact Extractor proves invaluable. Extract relevant contacts to create targeted campaigns and engage with potential customers directly.
Event Invitations and Announcements:
Organizing an event? Use the tool to extract contacts from relevant groups or chats, ensuring that your invitations or announcements reach the intended audience seamlessly.
Networking and Professional Outreach:
Individuals seeking to expand their professional network can utilize the tool to extract contacts from relevant industry groups or conversations. This facilitates efficient networking and outreach.
Customer Relationship Management (CRM):
Integrate the extracted contacts into your CRM system for streamlined management. This enhances your ability to nurture relationships and provide personalized interactions with clients or customers.
ConclusionAs we navigate the intricacies of digital communication, tools like the WhatsApp Contact Extractor emerge as indispensable assets. Simplify your outreach efforts, whether for personal or professional purposes, by harnessing the efficiency and versatility of this tool. Explore the power of streamlined contact management and take your communication strategy to new heights with WhatsApp Contact Extractor.
#WhatsApp contact extractor#WhatsApp number scraper#Global phone number downloader#Contact harvesting tool#International WhatsApp data extraction#Phone number scraper software#Worldwide contact finder#Global#phone directory scraper#WhatsApp data mining tool#International contact extraction
0 notes
Text
Unlock the Power of International WhatsApp Data Extraction with Advanced Software
In today’s digital landscape, businesses and marketers rely heavily onInternational WhatsApp data extraction to streamline their communication and outreach strategies. Whether you need to build customer databases or enhance your marketing campaigns, using a reliable phone number scraper software can be a game-changer. With the right tools, extracting valuable contact information from WhatsApp becomes effortless and efficient.
Why Use International WhatsApp Data Extraction?
WhatsApp has become one of the most popular messaging platforms globally, making it a goldmine for businesses looking to connect with potential customers. Here’s why businesses opt for WhatsApp data extraction:
Targeted Outreach – Extract relevant phone numbers from WhatsApp groups, chats, and databases for precise marketing campaigns.
Time-Saving Automation – Instead of manually collecting contacts, a specialized tool automates the process and increases efficiency.
Improved Lead Generation – Gather phone numbers from various sources to build a strong customer database.
Cost-Effective Solution – Reduce marketing costs by directly reaching potential clients through WhatsApp messaging.
Benefits of Using a Phone Number Scraper Software
A powerful phone number scraper software provides a range of benefits to users, including:
Accuracy and Reliability – Extracts genuine and verified numbers from WhatsApp databases.
Speed and Efficiency – Quickly collects a large volume of contacts without manual effort.
User-Friendly Interface – Designed for ease of use, even for non-technical users.
Compliance and Security – Ensures data protection and follows ethical extraction methods.
How to Choose the Right Software?
When selecting a phone number scraper, consider the following factors:
Compatibility – Ensure the tool works well with your system and WhatsApp version.
Features – Look for advanced filtering options, bulk extraction capabilities, and data export functions.
Support and Updates – Opt for software that offers regular updates and customer support.
Affordability – Compare pricing to find a cost-effective solution that meets your needs.
Final Thoughts
For businesses looking to enhance their marketing and lead generation efforts, International WhatsApp data extraction combined with a robust phone number scraper software is a must-have solution. By automating contact collection, businesses can save time, improve targeting, and maximize their outreach efforts. Choosing the right software ensures seamless data extraction, allowing businesses to stay ahead in the competitive digital landscape.
0 notes
Text
Know how machine learning is used in healthcare at the #14IHNPUCG2024

The healthcare sector is one that is continually changing. It can be challenging for healthcare workers to keep up with the constant development of new technologies and therapies. Machine learning in healthcare has emerged as one of the hottest buzzwords in recent years. However, what precisely is machine learning in healthcare? Why is machine learning for patient data so crucial? And what are a few advantages of machine learning in the medical field?
For Healthcare professionals, continual education is crucial, as we are aware. Our conference has been carefully planned and created to offer you worthwhile educational opportunities that adhere to the strictest CME and CPD accreditation requirements. Join us at Dubai, UAE & Virtual for the 14th International Healthcare, Hospital Management, Nursing, and Patient Safety Conference from July 25–27, 2024.
WhatsApp: https://wa.me/442033222718 Register here: https://nursing-healthcare.universeconferences.com/registration/ Register through zoom: https://us06web.zoom.us/meeting/register/tZMlceqrrzspGNTUrFCqaxRoDwNwZaw1h0D2
How does machine learning work?
A specific form of artificial intelligence called machine learning enables systems to learn from data and identify patterns with little to no human involvement. Computers that employ machine learning are presented patterns and data rather of being told what to do, allowing them to draw their own conclusions.
Machine learning algorithms perform a wide range of tasks, including email filtering, object recognition in photos, and the analysis of enormous amounts of steadily more complicated data sets. Machine learning systems are used by computers to automatically scan emails for spam, identify objects in photographs, and handle large amounts of data.
There are numerous possible uses for machine learning in healthcare, which is a growing area of research in precision medicine. Healthcare practitioners and health systems will increasingly rely on machine learning to extract meaning from medical data as patient data becomes more easily available.
Why are Healthcare Organisations Using Machine Learning?
Machine learning algorithms are particularly useful for the healthcare sector because they may assist in making sense of the enormous amounts of healthcare data that are created daily within electronic health records. We can discover patterns and insights in medical data using machine learning techniques, such as machine learning algorithms, that would be impossible to identify manually.
Healthcare providers have the chance to adopt a more predictive approach to precision medicine as machine learning in healthcare achieves wider use. This will result in a more unified system with enhanced treatment delivery, better patient outcomes, and more efficient patient-based operations.
The automation of medical billing, clinical decision support, and the creation of clinical practise guidelines within health systems are the three most prevalent applications of machine learning in healthcare among healthcare professionals. In science and medicine, there are numerous high-level applications of machine learning and healthcare principles. Data scientists at MD Anderson have created the first deep learning system for healthcare to anticipate acute toxicities in patients undergoing radiation therapy for head and neck tumours. Deep learning in healthcare can uncover complicated patterns automatically in clinical workflows and provide primary care providers with clinical decision support at the point of care within the electronic health record.
What Advantages Do Healthcare Professionals and Patient Data Have? As you can see, machine learning technologies have a wide range of possible applications in healthcare, ranging from better patient data, medical research, diagnosis, and treatment, to lowering costs and improving patient safety. Here is a short overview of some of the advantages machine learning applications in healthcare can offer healthcare professionals: better diagnosis Medical experts can apply machine learning in healthcare to create better diagnostic tools for examining medical pictures. For instance, a machine learning algorithm can be used in medical imaging (such X-rays or MRI scans) to seek for patterns that suggest a specific condition using pattern recognition.
Registration is now OPEN for the Exhibitor/Sponsors and you are only a few easy clicks away to exhibit/sponsor CME/CPD accredited 14th International Healthcare, Hospital Management, Nursing, and Patient Safety Conference, which will take place on July 25-27, 2024 in Dubai, UAE & Virtual. This is the best ways to network with fellow professionals, earn educational credits.
Register Today: https://nursing-healthcare.universeconferences.com/exhibit-with-us/
Better diagnosis
Medical experts can apply machine learning in healthcare to create better diagnostic tools for examining medical pictures. For instance, a machine learning algorithm can be used in medical imaging (such X-rays or MRI scans) to seek for patterns that suggest a specific condition using pattern recognition. A faster, more precise diagnosis made by a clinician using this kind of machine learning system could lead to better patient outcomes.
Clinical trials, medication discovery, and the development of new therapies
Healthcare institutions and pharmaceutical firms can utilise a deep learning model to find pertinent information in data that could result in the discovery of new pharmaceuticals, the creation of new drugs by pharmaceutical firms, and novel methods of treating diseases. To uncover previously unidentified drug adverse effects, machine learning in healthcare could be used to analyse data and medical research from clinical trials. Clinical trials using this kind of machine learning in healthcare could benefit patient care, medication discovery, and the security and efficacy of medical procedures.
Lowering expenses
Healthcare organisations can employ machine learning technology to increase the effectiveness of the industry, which could result in cost savings. For instance, machine learning in healthcare could be utilised to create better scheduling or patient record management algorithms. The amount of time and resources wasted on repetitive tasks in the healthcare system might be decreased with the use of this kind of machine learning.
Enhancing care
Medical personnel can apply machine learning in healthcare to enhance the standard of patient care. For instance, the healthcare sector may utilise deep learning algorithms to create systems that proactively monitor patients and send alarms to medical devices or electronic health records when their status changes. Making use of machine learning for data collecting could help to guarantee that patients receive the proper care at the appropriate time. The promise of machine learning to give care is still being realised, but machine learning applications in healthcare are already having a positive impact. Machine learning in healthcare will be more crucial in the future as we try to make sense of clinical data sets that are constantly expanding.
Track 16: Machine Learning for Digital Healthcare Innovation
Machine learning is a branch of computer science and artificial intelligence (AI) that focuses on using data and algorithms to replicate how people learn, gradually improving the system's accuracy.
The abstract submission at 14th International Healthcare, Hospital Management, Nursing, and Patient Safety Conference aims to explore the vital role of healthcare professionals in delivering compassionate care and the various factors that contribute to its cultivation and sustenance. Submit now and join us in Holiday Inn Dubai, UAE & Virtual, on July 25-27, 2024.
Submit the abstract here: https://nursing-healthcare.universeconferences.com/submit-abstract/ To register, visit here: https://nursing-healthcare.universeconferences.com/registration/ WhatsApp: https://wa.me/442033222718
Healthcare Quality Improvement | Interprofessional Collaboration | Healthcare Policy | Global Health Nursing | Telehealth and Telemedicine | Nursing Simulation | Cultural Competence in Nursing | Nursing Research Symposium | Nurse Career Fair | Nursing Expo | Nursing Simulation | Nursing Workforce Development | Cultural Competence in Nursing | Nursing Continuing Education
0 notes
Text
Facebook algorithm boosts pro-Facebook news

Facebook is a rotten company, rotten from the top down, its founder, board and top execs are sociopaths and monsters, committers of non-hyperbolic, no-fooling crimes against humanity. They lie, they cheat, they steal. They are some of history’s greatest villains. Because Facebook is a terrible company run by terrible people, it periodically erupts in ghastly scandal. Sometimes whistleblowers or reporters reveal historic crimes, including (but not limited to) deliberately helping to foment genocide.
Sometimes, the scandals are contemporary: either Facebook blithely announces it’s going to do something terrible, or we learn of some terrible thing underway from leaks or investigations.
Thanks to a history of anticompetitive mergers — Whatsapp, Instagram, Onavo and more — based on fraudulent promises to antitrust regulators, Facebook has grown to nearly three billion users — except FB doesn’t have users, really — it has hostages.
https://www.eff.org/deeplinks/2020/07/dont-believe-proven-liars-absolute-minimum-standard-prudence-merger-scrutiny
As Facebook’s own internal memos show, the company doesn’t just buy up competitors so users have nowhere to flee to, it also engineers in high “switching costs” to make it more painful to leave the system.
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
For example, Facebook’s internal memos show that the manager for its photo products set out to seduce users into entrusting FB with their family photos, because that way quitting Facebook would mean abandoning your memories of your kids, departed grandparents, etc.
Everybody hates Facebook, especially FB users. The point of high switching costs, after all, is to increase the pain of leaving so that FB can dole out more abuse to its users without fearing that they’ll quit the whole enterprise.
FB’s mission is to increase the size of the shit-sandwich they can force you to eat before you walk away. But they’re not mere sadists: shit-sandwiches have a business model: the more hostages they take, the more they can extract from advertisers — their true customers.
The polite term for what FB has is a “two-sided market” (selling advertisers to users and users to advertisers). The technical term is “a monopoly and a monoposony” (a monopsony is a market with a single buyer).
The colloquial term?
“A racket.”
A scam. A bezzle. A blight.
Facebook gouges advertisers on rate cards, then lies about the reach of its ads (like when it lied about the popularity of video, evincing a media-wide “pivot to video” that bankrupted dozens of news- and entertainment-sites).
Facebook didn’t set out to destroy journalism by price-fixing ads, lying to advertisers and media outlets.
FB set out to acquire a monopoly and extract monopoly rents from advertisers and publishers, with a pathological indifference to how these frauds would harm others.
Having shown a willingness to destroy journalists and media outlets to extract a few more billions for its shareholders, Facebook has attracted a lot of enemies in the media.
If you’re a whistleblower with a story to tell, there’s a journalist whose editor will allocate the resources to report your story out in depth. The combination of a rotten company and a lot of pissed off journalists produces a lot of bad ink for the company.
But the fact remains that FB has a vast pool of hostages, billions of them, and it gets to decide what they see, when and how. I used to joke with my human rights activist friends that the best use for Facebook was showing people why and how to leave Facebook.
FB’s response was predictable. As Ryan Mac and Sheera Frenkel write in the New York Times, FB’s Project Amplify is a Zuckerberg-led initiative to systematically promote positive coverage of FB and its founder — including articles that originate with FB itself.
https://www.nytimes.com/2021/09/21/technology/zuckerberg-facebook-project-amplify.html
That is, FB staffers are charged with writing puff pieces about how great the company is, and FB’s algorithm will push these ahead of reporting by actual journalists who present detailed, factual, multi-sourced accounts of the company’s fraudulent and depraved conduct.
Project Amplify marks a pivot from FB’s longstanding policy of issuing insincere apologies for its scandals. Company sources told the reporters that everyone figured out these don’t convince anyone, so the company turned to pushing happy-talk quackspeak instead.
One of the leaders of this project is Alex Schultz, “a 14-year company veteran who was named chief marketing officer last year,” but the major impetus comes from Zuck himself, one of the most hated men on the planet.
Amplify is just one of FB’s strategies for distorting the discourse about itself. In July, it neutered Crowdtangle, an widely used analytics tool that showed that FB’s top posts were unhinged far-right disinformation and conspiracies.
https://pluralistic.net/2021/07/15/three-wise-zucks-in-a-trenchcoat/#inconvenient-truth
And Facebook has declared all-out legal warfare (accompanied by a disinformation campaign) to kill Adobserver, an NYU project that tracks paid political disinformation on the platform.
https://pluralistic.net/2021/08/05/comprehensive-sex-ed/#quis-custodiet-ipsos-zuck
By shutting down Crowdtangle and Adobserver, FB hopes to control the academic findings about the company’s role in disinformation, hate, and harassment. The company runs its own research portal where academics are expected to access data about the platform.
But as with the journalists who report on it, FB has heaped abuse on the academics who research it.
Its portal data was bad, leaving PhD and masters’ theses are at risk of retraction. Mid-dissertation researchers have been set back to square one.
https://www.nytimes.com/live/2020/2020-election-misinformation-distortions#facebook-sent-flawed-data-to-misinformation-researchers
In retrospect, Facebook’s decision to game its own algorithm to push pro-company quackspeak seems inevitable. It’s not just that no one believes the company’s apologies anymore (if they ever did) — it’s that the company seems incapable of hiring competent spin doctors.
Take the WSJ’s blockbuster “Facebook Files,” a series of reports detailing the company’s willingness to harm children, commit fraud, and allow millions of favored, powerful people to violate its rules with impunity.
https://www.bloomberg.com/news/newsletters/2021-09-16/facebook-s-promised-to-gain-the-public-s-trust
FB’s response was genuinely pathetic. In a perfunctory blog post, its top flack — the widely despised British politician Nick Clegg, paid millions to front FB on the global stage — vilified the WSJ’s reporting without producing any factual rebuttals.
https://about.fb.com/news/2021/09/what-the-wall-street-journal-got-wrong/
It’s the kind of ham-fisted policy advocacy that Facebook is (in)famous for. Who can forget the absolute shitshow in India over its Internet Basics program, when it bribed telcos to exempt FB and the services it hand-picked from their data-caps?
https://www.theguardian.com/technology/2016/may/12/facebook-free-basics-india-zuckerberg
This Net-Neutracidal maneuver, falsely billed as a way to bring the internet to poor people (something is absolutely does not do), was the subject of a consultation by India’s telco regulators.
FB pushed deceptive alerts to millions of its Indian users, tricking them into sending a flood of form-letters to the regulator urging it to leave Internet Basics intact.
But whoever drafted the form letter didn’t bother to check whether it addressed any of the questions the regulator was consulting on. That made these millions of letters non-responsive to the consultation, so the regulator ignored them.
FB lost! It’s almost as though people who are good at fighting policy battles don’t want to work for Facebook, and the only talent they can attract are the kinds of opportunistic blunderers that no one takes seriously and everyone hates.
Weird, that.
111 notes
·
View notes
Text
Free Itunes Backup Extractor Key

Summary
Free Iphone Backup Extractor
Free Itunes Photo Extractor
1st iTunes Backup Extractor: Dr.Fone - Data Recovery (iOS) Dr.Fone - Data Recovery (iOS) is the world's first tool to extract backup data from iTunes, and supports the extraction of all kinds of video, music, app, contact, call history, message data. You can preview what data was stored in iTunes and then choose to extract. Free iTunes Backup Extractor Syncios iTunes Backup Extractor finds all iPhone, iPod Touch and iPad backups on your computer and lets you extract data from iTunes backup onto your computer with ease.

Download free iPhone backup extractor crack full keygen to free recover lost and deleted data files like contacts, calendar events, WhatsApp messages, notes and app data from iPhone & iPad devices, iTunes backup or iCloud backup easily.
Don't trust iPhone backup extractor crack full keygen
An iPhone backup extractor is very helpful in case of lost or deleted files on iOS devices. It helps recover various data files (contacts, calendar events, WhatsApp messages, notes and app data) once people's phones broke, factory reset, water damaged, etc. Since many of the iPhone backup solution & data recovery tools are not free to use, instead, they charge some money which allows people to use its full version to recover unlimited amount of data, many people tend to search iPhone data recovery software crack or iPhone backup extractor keygen on the internet, thinking they might work in the same way as the genuine software does. However, it's not true.
iPhone data recovery technology is not what a cracker or user can copy, that's why some iPhone backup extractor failed to pull up the lost data while scanning the device, iTunes or iCloud backup file. Usually, fake iPhone backup extractor will crash many times while working on searching lost data. What's worse, the lost data will take a second time damage from the pirate software, and gets corrupted, until then even the genuine iPhone data recovery software could not help.
Download safe alternative - EaseUS MobiSaver, the most powerful & cheap iPhone backup extractor
It's time to step aside any iPhone backup extractor crack download keygen, your lost data and backup files won't stand a further damage. EaseUS MobiSaver, a top-notch iPhone data recovery and iPhone data backup program, provides straightforward way to restore contacts, photos, SMS and everything from iTunes backup, iCloud backup as well as iPhone internal memory.
For Windows users: Click 30% discount for EaseUS MobiSaver - the best iPhone backup extractor; For Mac users: Click 30% discount for EaseUS MobiSaver - the best iPhone backup extractor;
Free Iphone Backup Extractor
How to extract iPhone data from iTunes/iCloud backup with EaseUS MobiSaver?
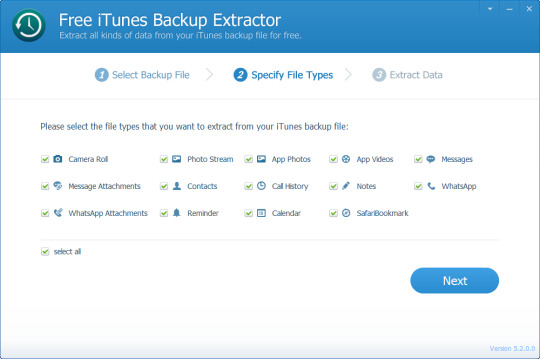
Step 1. Launch EaseUS MobiSaver. There are 3 recovery modes available: recover from iOS device, recover from iTunes backup and recover from iCloud backup. Choose either ' Recover from iTunes Backup' mode or 'Recover from iCloud Backup' mode. Click 'Scan' button.
Free Itunes Photo Extractor
Step 2. After a quick and complete scanning, you can see the iPhone backup extractor has found all the data in the iPhone backup file and has listed them in clear categories on the left side of the window. You can click any type to preview the detailed contents and select out the files you want to get. Finally click 'Recover' button to selectively extract data from iPhone backup and export them to your computer.

1 note
·
View note