#Increase Software Exposure
Explore tagged Tumblr posts
Text
Want Better Things
“You thought that was a bioweapon?”
The translator broke down for a second as the creature did a sort of broken exhale. Connotations were all that came through. Vague implications. Pity, the software flashed. Disgust. Anger.
A pause as it decided.
Sadism.
Valta was already backing away. The final decision didn’t change his behavior, it just made the hall feel far, far too short.
“I didn’t order it deployed. I didn’t make it.”
The thing was staring at him, and he couldn’t look away. The two eyes moved in such perfect tandem that he didn’t think it was conscious. It only had binocular vision because it only needed binocular vision. Always the predator, never the prey.
And now it was moving in on him.
“Oh, but what if you had? Then I could tell you all the things that were wrong with it.”
One of its hands - a sprawling, five fingered spindly thing - traced carelessly along the station's walls.
“No incubation period. Symptoms arrive within 40 minutes of exposure. No time to spread undetected. Minimum should be one week. Embarrassingly low.”
The pressure the thing was putting on the wall increased, the gentle glide turning into a buzzing scratch. Humans were strong, but not strong enough to cut through metal like this. The suit had to be powered and clawed.
“Spread through contact. Limited waterborne. No airborne. Intended mechanism of infection is viral load being put on hands from scratching, and then passed into the environment. Pathetically inefficient.”
The translator was working, but the thing was overeunounciating each word. The meaning was being passed along by a clean, helpful voice in his suit, even as the sound was being passed on through the environmental speakers. And the sound was dreadful - clicks of ceramized bone jarring against each other, wet muscles modulating air into something sharp and rasping.
“Mechanism of death? Lysis overload. Could be dangerous if it was transmitted into the lungs, but since the initial load tends to be dermal all we wind up with-”
It took its helmet off.
It took its helmet off.
It took its helmet off it took its helmet off it took its helmet off in a biozone it -
It looked a little pink, actually. A little scratchy. It lifted a delicate, taloned hand and rubbed its face against it for a moment before finishing.
“-is a rash.”
Valta’s prey drive had glued him to the spot. It was too close. The stupid, stupid part of his brain that still thought he was grazing on Duranga hoped that if he stood still long enough, it might not notice him.
The human paused a moment before continuing.
“Do you know why they sent me? Alphonse Ericsen, PhD, MD, civilian doctor, here to speak with you?”
Valta’s snout twitched. The suit translated the gesture for him.
“No.”
“Because one of our grunts is a dumb fuck,” the human said simply. “And he spent two days fighting on your station with his helmet off. He got infected that way and brought back your stupid, itchy plague to our carrier ship, and now we’ve all spent the last 8 hours scratching ourselves raw. But the jokes on you, because when we were treating that guy you know what we found? That he was in the asymptomatic phase of a COVID infection. So if this-”
It gestured to its pink face with a snarl.
“-is your idea of a bioweapon, then COVID is going to be your apocalypse. But if you work with me, and shut everything the fuck down for the next three or four months, I might be able to save most of you.”
Valta unstuck at that. He’d spent weeks down here, worrying about nothing more than the next skirmish. Now he was looking at a genuine existential threat.
“...What? Why would you help us? We wanted you to die. All of you. I wanted-”
The human cut him off with an exasperated wave of his hand.
“You wanted something stupid. Doesn’t mean I have to join you. Best I can do to fix you is keep you alive and hope that you feel ashamed later. That, I genuinely look forward to. Now come on, you’re going to be the one explaining to all your friends what’s at stake here. My bedside manner is so bad that they limited my patients to virology slides and USMC marines. I think that’s actually one rung below the guys that just dissect cadavers.”
Valta would’ve made an amused hum at that, but something already felt scratchy inside his throat.
#hfy#more flash fiction#I think I just needed a little brain break from pushing for larger works#fun tho#I really loathe HFY where the moral is like 'what if humans comitted war crimes and it was BASED'#so I tried doing one where it was 'what if humans took the moral high ground and like didnt do war crimes'.#the doctors prayer: that you live long enough to know what a dumbass you were#HASO#Humans Are Space Fae#sci-fi#770 words i think#Babylon-HFY
292 notes
·
View notes
Text
"Hold on there, pardner. This here's a cognition hazard." said the holographic cowboy in the corner of my vision. He then took a series of poses that the designer must have thought looked heroic and protective, before flickering back to his original position and repeating the process. My artificial ranch-hand was not incorrect: the thing I was attempting to do would cause me unpredictable amounts of psychic damage, likely impacting my relationships with those around me and even my mental state at rest. Even so, I pushed the button and waited.
Software development used to be a sort of reckless task, undergone without care. Decades ago, hundreds of folks would cram themselves into a single building and then work hard on their computers to develop computer programs. Originally, these programs performed useful but difficult tasks, speeding them up dramatically for the varied needs of government and industry. At first, life improved. And then, as with every prior machine in human history, we looked for harder jobs for it to do.
A funny thing happens when a computer program gets longer than about a page of typewritten code. You have to hold a lot of it in your head. The best programmers could commit an entire system to memory, gliding through it like barracuda through a disreputable motel's swimming pool. We didn't know then how much trauma it caused. The doctors had no idea what was happening with all those isolated burnouts freaking out, moving into the woods, and hunting men for sport.
Watching the old newsreels now, seeing the 20th-century equivalent of coal miners delving willingly into fold-out charts of MFC inheritance diagrams, it's a little hard to stomach. It only took about twenty years of continued exposure to this kind of thing before the human mind rebelled, the manmade logical constructs providing a kind of sharp edge that ripped through sanity like a hot wire. Thing is, it still had to be done, and the folks who did it seemed to enjoy it up until The Void caught up to them too. So the government did what the government does best, and compromise. We'd all have warnings that what we were doing was insanely dangerous and life-shortening, and our employers would keep demanding that we heap more complexity atop ever-increasing mountains of irreducible cruft.
A good deal for all involved, especially the folks who got the contract to make the warning holograms about fifteen years ago. They must have loved their jobs, putting the little cowboy hats on them. You can tell in all the little complex details of his haunted face, begging me to turn back from my route to oblivion. One day I'd like to make something cool like that.
698 notes
·
View notes
Text
Procreate Dreams
I've been playing around in Procreate Dreams for about a week or so now, and I think I've got enough of a handle on the software to offer a fair review! If you're interested in hearing my thoughts, click the read-more below.
A little context before we get started; I have two degrees in animation, but they're both in 3D. My personal specialty is tech and articulation/rigging, but I think my background puts me in a unique position with Procreate Dreams; I know all of the theory behind animation, but I'm not going into Procreate Dreams and comparing it to a professional-grade software I generally prefer to use (like Toon Boom Harmony, for example).
So, let's get into it!
First Impressions
I hated it. I opened the software, it crashed. I couldn't figure out how to enable onion skins. I couldn't increase or decrease the exposure of my frames. I couldn't figure out how to swap to the eraser. I was confused, I was frustrated, and then I realized that I was expecting to jump in and animate without taking the time to learn the software first.
Once I stopped trying to strong-arm it and started looking up documentation, things got a little easier.
Re-Thinking My Approach
Procreate Dreams isn't comparable to any other animation software I've used before. The UI is different, there's a focus on gesture over buttons, and everything about it is meant to be minimalistic. None of this reflects poorly on the program, in my opinion. It's different. You can't go to Procreate Dreams and get mad at it for not being like the other software out there in terms of how it's used. In fact, I think one area of Dreams that should be applauded is the sheer ambition on display. It's a hybrid of traditional frame-by-frame animation and offers a slimmed down version of some of After Effects' most useful compositing & motion graphics tools. That's just plain cool.
The Good
For those of you who've used Procreate Dreams, you may find it's a little... difficult to see all the good it has to offer through the muddied waters it's launch-day bugs kicked up, but under all the grime, there's a little bit of gold.
Dreams is a one time, $20 USD purchase. That's huge in terms of affordability and accessibility in the software market right now.
The "Perform" option is great, and I think we'll see the longer that it's out, the more creative people are going to get in using it. I've already seen people create gorgeous parallax on their illustrations.
Simple compatibility with Procreate is a huge win. I'm finding my pipeline uses both software together.
The UI is a mixed bag overall, but I find the ability to move between flipnote mode and timeline mode to be great. It keeps the screen free, but I can still access the features I need while doing frame-by-frame.
The move/filters option is a great way to add a little compositing magic to your work.
The Bad
The "bad" here exclusively covers issues with the software as intended. Bugs will be covered under "The Ugly" below.
The lack of a lasso tool is a huge setback. I've seen people saying that it doesn't make sense not to have that feature at launch, especially when it's part of Procreate, but I understand why it may have been difficult to implement in conjunction with the move/perform/warp options. If you save a warp on top of an illustration, then cut and move part of the drawing, how is the warp/local translation data applied to that image? Does the pixel remember it's movement, or is it applied on top of the drawing? There's a lot to consider.
Similarly, the "reference" tool in Procreate would be an excellent tool to add color to layers beneath current layers. "Add Reference Track" would be great! That said, I think this conflicts with the move/warp tools like the above.
The timeline is a time sink. I should be able to adjust the exposure of my frames easily and consistently. As of right now, I have an 80-20 shot of selecting my layer or grabbing the handle for exposure. A small button on the edge of each frame (like a dot) would improve this considerably.
As far as I can tell, you can't mask a group onto another group.
No double-tap on the Apple Pencil 2 to swap to the eraser. This one I'm not sure about; it runs in Procreate, it seems simple to implement here... though it'd be great to see it customizable.
The Ugly
This includes bugs and other issues that are separate from the features (or lack thereof) of Procreate Dreams.
Crashes are frequent. I haven't used the software reliably during any of my sessions so far, but Dreams' autosave feature is extremely strong and very forgiving, so I have lost no work.
My pen pressure become erratic at times, necessitating a restart of the software.
Sometimes my pen will stop working, though other features in the app will continue to run.
The good news is, I think that Dreams is overall a huge win for artists and animators worldwide. Everything that's not working about Dreams will hopefully be resolved in future updates. I'd encourage anyone who wants to try animating for the first time to pick it up-- with the understanding it might take some time to get used to/master.
61 notes
·
View notes
Text
Yvette Heiser - Mastering Night-time Food Photography in the Heart of Texas
Texas is renowned for its vibrant food scene, from sizzling BBQ and Tex-Mex delicacies to gourmet farm-to-table experiences. As the sun sets and the city lights twinkle, capturing the essence of nighttime dining becomes an art form of its own. Discover Photography in Texas with Yvette Heiser, as mastering night-time food photography allows you to showcase the delicious offerings and unique ambiance of Texas restaurants and street food vendors. In this article, we will explore practical tips and techniques to elevate your nighttime food photography, making your images as mouthwatering as the dishes themselves.

Understanding the Importance of Lighting
Lighting serves as the foundation of any outstanding photograph, particularly in the realm of food photography. At night, natural light is scarce, so you’ll need to rely on artificial lighting sources to bring your images to life. Here are several important factors to keep in mind:
- Use Soft Light: Harsh, direct lighting can create unflattering shadows. Instead, opt for soft light sources such as table lamps, candles, or string lights. Position these lights strategically around your food to create a warm, inviting atmosphere.
- Experiment with Exposure Settings: When photographing at night, you may need to adjust your camera’s exposure settings. A longer exposure time can help capture more light, but be cautious of motion blur. Use a tripod to keep your camera steady, allowing for sharper images even in low light.
Choosing the Right Angles
The angle from which you photograph your food can dramatically change the viewer's perception. Here are some angles to consider when capturing nighttime food scenes:
- Top-Down Shots: This angle works well for flat dishes, such as pizzas or tapas. It allows you to capture multiple items and showcase the table's overall aesthetic. Enhance this shot by including utensils, drinks, and other elements that create a lively dining atmosphere.
- 45-Degree Angles: This angle strikes a balance between a top-down and side shot, offering depth and dimension to your images. It’s ideal for dishes served in bowls or with layers, allowing viewers to see both the surface and the interior of the food.
- Close-Ups: Don’t hesitate to get up close and personal with your food. Close-up shots can highlight textures and intricate details that make dishes appealing. A close-up of a juicy steak or a decadent dessert can leave viewers craving more.
Utilizing Props and Backgrounds
The right props and backgrounds can elevate your food photography. Here are a few suggestions to elevate your nighttime food photography:
- Textured Surfaces: Use wooden tables, rustic cutting boards, or slate plates to create a contrasting background. The texture can add depth to your images and make the food stand out.
- Include Contextual Elements: Incorporate elements that represent the Texas culture, such as vintage cowboy hats, mason jars, or fresh herbs. These items can tell a story and enhance the narrative of your food photography.
- Play with Colors: The warm tones of Texas cuisine can be beautifully complemented by contrasting backgrounds. For example, vibrant dishes can pop against darker surfaces, while cooler dishes may benefit from warmer, earthy tones.
Post-Processing Techniques
Editing is a crucial step in food photography that can help enhance the overall aesthetic of your images. Consider the following techniques:
- Adjust Brightness and Contrast: Increase brightness slightly to compensate for low-light conditions and enhance the contrast to make the colors pop.
- Enhance Colors: Use editing software to boost the saturation and vibrancy of the food without overdoing it. The aim is to present the food in a way that reflects its delicious flavor.
- Sharpen Details: Use the sharpening tool to highlight textures, making the food look even more appetizing.
Conclusion
Mastering night-time food photography in the heart of Texas allows you to showcase the unique flavors and ambiance of this vibrant state. By understanding the importance of lighting, choosing the right angles, incorporating props, and employing effective post-processing techniques, you can create stunning images that capture the essence of Texas cuisine. As outlined in Yvette Heiser: Deliciously Dark Guide to Night-time Food Photography, these elements are crucial for achieving captivating results. So grab your camera, head out into the lively Texas night, and start capturing those delicious moments!
#camera#wedding#moments#photographer#pictures#childphotography#yvette heiser#photography#photographytips#events
7 notes
·
View notes
Text


Hi pals!
I’ll still be travelling when you’re seeing this and haven’t watched the finale, so I don’t have any new content to share, but last week (maybe longer? I don’t know— rainforest brain lol) I posted a poll asking if anyone was interested in seeing a snippet of my editing process, so here it is feat. possibly one of my favourite Wrecker moments.
I use a myriad of different software depending on: my mood, what computer/tablet I’m using, what the image looks like, and how much energy I’m willing to put into it lol In this video, I’m using Lightroom on my iPad.
The three main factors I look mostly closely at when I’m editing shots are 1. lighting, 2. noise, and 3. resolution (read: clarity).
This image required pretty minimal work so it’s probably not the best example, but ah well. The process in the above video is as follows, and please note the video had been sped up to 2x for file size reasons lol
The first thing I’ll do is see what the auto edit function defaults to. Often times it overexposes the image, resulting in significant colour noise, but it gives me a decent idea of what I should expect in terms of colour corrections and exposure mapping. The auto edit function wasn’t terrible in this case, but did produce some colour noise, mainly on Wrecker’s chest plate, his sleeves, and the officers hat. Once I’m done the initial scope out, I’ll exposure the image as high as possible to crop it— usually with the subject being as centered as possible.
This software lets the user tweak the bones of the image individually in three ways, all of them very quickly demonstrated here. The first is the curve method which I despise and NEVER use— because it alters multiple aspects at once, I don’t feel like I have the same degree of control as the other methods. Next is HDR setting (the default upon import) using the sliders on the right. This is effective for images that are already pretty well lit, and does give me a little more control, but most of the time because the screenshots are so dark, I’m editing in SDR mode.
Once I’m satisfied with the exposure/lighting, I’ll move on to correcting colour distortion and saturating the image. This software also provides three methods for colour alternation and I’ll typically use all three in conjunction with each other. Colour mixing is extremely crucial when it comes to reducing odour noise and distortion. Because this software lets me isolate certain colours to adjust their hue, saturation, and luminance, I can typically reduce most of or all of the colour noise. However, it does have its limitations. In this particular post, desaturating the colour noise in Crosshair’s rifle coincided with blanching his skin tone, because this software does not let me isolate certain areas of an image. It was also important to me to emphasize the warm tones from the sunset in the background for the overall mood of the shot, so I opted to remove what colour noise I could and leave the rest. (You can’t win em all… especially when the starting image is near-black lol)
Correcting the colour distortion in this image was not particularly difficult, desaturating all purple tones removed the noise from his chest plate, and shifting green tones to something near a yellow instead removed the noise from his sleeve. I didn’t notice the colour noise on the officers hat until a little later, but that was pretty easily corrected too.
Once I’ve fixed the colour noise, I’ll shift to toning the overall image. Wrecker particularly looks good in cool tones, but It’s nice to contrast a cool tone background with the warmth of his skin.
Once the toning is done, I’ll move on the image clarity. I don’t have the means to alter the actual resolution of the image, but I’m particularly picky with balancing texture and clarity. Wrecker always looks the best with texture and clarity increased, because it brings out the scarring on his face and further humanizes him, but overdoing the texture can also emphasize pixelation. Once that’s done, I’ll reduce the overall noise only slightly (doing too much makes them look airbrushed and unnatural), and whatever is left of the colour noise (too much of this setting makes them look like ghouls LOL)
This software also offers a series of preset alterations/filters briefly shown in this video… but I’m not the biggest fan of any of them. I’m a bit of a control freak and would rather tweak each aspect individually to the degree that I like, instead blanketing the image with present modifications and then undoing certain aspects.
Before exporting the image I’ll do another once over and make sure I’m happy! In this case, I opted to go back in and add some darker tones back into the image. I don’t do this often, particularly when they start so damn dark, but I wanted to keep the focus centrally on Wrecker’s radiance lol
That’s about it. If I’m working on multiple edits in a set, this software lets me just copy and paste the settings, so the following images only require extremely light tweaks and take almost no time. And that, I’ll export, autograph, and upload!
Thank you for attending this unprofessional Ted Talk.
#starqueensrambles#things no one asked for but are getting anyways#Jedi queue-doo#starqueensedits#ungatekeeped lol#thats not a word#well… it is now
14 notes
·
View notes
Text
I hate Toon Boom. I want to BURN Toon Boom. I want to kill it with fire. I am never fucking using it again until I have read and memorized the entire MANUAL and every single possible BUG. IT TOOK ME MORE TIME TO FIGURE OUT HOW TO INCREASE EXPOSURE, MOVE CELLS, AND EXPORT IT WITH SOUND THAN IT TOOK TO ACTUALLY DRAW THE DAMN THING. I'm sticking with pencil2d, no matter how shitty and old the software is.
32 notes
·
View notes
Text
Generative AI tools such as OpenAI’s ChatGPT and Microsoft’s Copilot are rapidly evolving, fueling concerns that the technology could open the door to multiple privacy and security issues, particularly in the workplace.
In May, privacy campaigners dubbed Microsoft’s new Recall tool a potential “privacy nightmare” due to its ability to take screenshots of your laptop every few seconds. The feature has caught the attention of UK regulator the Information Commissioner’s Office, which is asking Microsoft to reveal more about the safety of the product launching soon in its Copilot+ PCs.
Concerns are also mounting over OpenAI’s ChatGPT, which has demonstrated screenshotting abilities in its soon-to-launch macOS app that privacy experts say could result in the capture of sensitive data.
The US House of Representatives has banned the use of Microsoft’s Copilot among staff members after it was deemed by the Office of Cybersecurity to be a risk to users due to “the threat of leaking House data to non-House approved cloud services.”
Meanwhile, market analyst Gartner has cautioned that “using Copilot for Microsoft 365 exposes the risks of sensitive data and content exposure internally and externally.” And last month, Google was forced to make adjustments to its new search feature, AI Overviews, after screenshots of bizarre and misleading answers to queries went viral.
Overexposed
For those using generative AI at work, one of the biggest challenges is the risk of inadvertently exposing sensitive data. Most generative AI systems are “essentially big sponges,” says Camden Woollven, group head of AI at risk management firm GRC International Group. “They soak up huge amounts of information from the internet to train their language models.”
AI companies are “hungry for data to train their models,” and are “seemingly making it behaviorally attractive” to do so, says Steve Elcock, CEO and founder at software firm Elementsuite. This vast amount of data collection means there’s the potential for sensitive information to be put “into somebody else’s ecosystem,” says Jeff Watkins, chief product and technology officer at digital consultancy xDesign. “It could also later be extracted through clever prompting.”
At the same time, there’s the threat of AI systems themselves being targeted by hackers. “Theoretically, if an attacker managed to gain access to the large language model (LLM) that powers a company's AI tools, they could siphon off sensitive data, plant false or misleading outputs, or use the AI to spread malware,” says Woollven.
Consumer-grade AI tools can create obvious risks. However, an increasing number of potential issues are arising with “proprietary” AI offerings broadly deemed safe for work such as Microsoft Copilot, says Phil Robinson, principal consultant at security consultancy Prism Infosec.
“This could theoretically be used to look at sensitive data if access privileges have not been locked down. We could see employees asking to see pay scales, M&A activity, or documents containing credentials, which could then be leaked or sold.”
Another concern centers around AI tools that could be used to monitor staff, potentially infringing their privacy. Microsoft’s Recall feature states that “your snapshots are yours; they stay locally on your PC” and “you are always in control with privacy you can trust.”
Yet “it doesn’t seem very long before this technology could be used for monitoring employees,” says Elcock.
Self-Censorship
Generative AI does pose several potential risks, but there are steps businesses and individual employees can take to improve privacy and security. First, do not put confidential information into a prompt for a publicly available tool such as ChatGPT or Google’s Gemini, says Lisa Avvocato, vice president of marketing and community at data firm Sama.
When crafting a prompt, be generic to avoid sharing too much. “Ask, ‘Write a proposal template for budget expenditure,’ not ‘Here is my budget, write a proposal for expenditure on a sensitive project,’” she says. “Use AI as your first draft, then layer in the sensitive information you need to include.”
If you use it for research, avoid issues such as those seen with Google’s AI Overviews by validating what it provides, says Avvocato. “Ask it to provide references and links to its sources. If you ask AI to write code, you still need to review it, rather than assuming it’s good to go.”
Microsoft has itself stated that Copilot needs to be configured correctly and the “least privilege”—the concept that users should only have access to the information they need—should be applied. This is “a crucial point,” says Prism Infosec’s Robinson. “Organizations must lay the groundwork for these systems and not just trust the technology and assume everything will be OK.”
It’s also worth noting that ChatGPT uses the data you share to train its models, unless you turn it off in the settings or use the enterprise version.
List of Assurances
The firms integrating generative AI into their products say they’re doing everything they can to protect security and privacy. Microsoft is keen to outline security and privacy considerations in its Recall product and the ability to control the feature in Settings > Privacy & security > Recall & snapshots.
Google says generative AI in Workspace “does not change our foundational privacy protections for giving users choice and control over their data,” and stipulates that information is not used for advertising.
OpenAI reiterates how it maintains security and privacy in its products, while enterprise versions are available with extra controls. “We want our AI models to learn about the world, not private individuals—and we take steps to protect people’s data and privacy,” an OpenAI spokesperson tells WIRED.
OpenAI says it offers ways to control how data is used, including self-service tools to access, export, and delete personal information, as well as the ability to opt out of use of content to improve its models. ChatGPT Team, ChatGPT Enterprise, and its API are not trained on data or conversations, and its models don’t learn from usage by default, according to the company.
Either way, it looks like your AI coworker is here to stay. As these systems become more sophisticated and omnipresent in the workplace, the risks are only going to intensify, says Woollven. “We're already seeing the emergence of multimodal AI such as GPT-4o that can analyze and generate images, audio, and video. So now it's not just text-based data that companies need to worry about safeguarding.”
With this in mind, people—and businesses—need to get in the mindset of treating AI like any other third-party service, says Woollven. “Don't share anything you wouldn't want publicly broadcasted.”
10 notes
·
View notes
Text
The Digital Nomad's Dilemma: Traveling While Working in the US Software Market
The allure of the "digital nomad" lifestyle – working remotely while exploring the world – has never been stronger. However, for those in the competitive US software market, navigating this path can present unique challenges.
The Perks:
Flexibility: Remote work in the US software sector often comes with significant flexibility. This allows employees to escape the traditional office setting and experience different cultures while maintaining their careers.
Increased Productivity: Studies have shown that a change of scenery can boost creativity and productivity. Traveling can provide a fresh perspective and combat burnout often associated with prolonged periods of desk-bound work.
Enhanced Skill Development: Exposure to new environments and cultures fosters adaptability, problem-solving, and communication skills – all highly valuable in the dynamic software industry.
The Challenges:
Time Zone Differences: Collaborating with colleagues across multiple time zones can be challenging. Early morning or late-night meetings may become the norm, potentially impacting sleep schedules and work-life balance.
Reliable Internet Access: Consistent and high-speed internet access is crucial for software development and online communication. Finding reliable internet in remote locations can be a significant hurdle.
Cultural Considerations: Understanding and adapting to local customs and business etiquette while traveling is essential. This requires cultural awareness and flexibility.
Maintaining Focus: Distractions are abundant when traveling. Finding quiet workspaces, managing social interactions, and resisting the temptation to constantly explore can be difficult.
Legal and Tax Implications: Navigating tax laws and regulations while working remotely in different countries can be complex.
Tips for Success:
Choose Travel Destinations Wisely: Prioritize destinations with reliable infrastructure, strong internet connectivity, and a supportive environment for digital nomads.
Establish a Strong Routine: Maintain a consistent work schedule, even while traveling. Create a dedicated workspace and minimize distractions.
Communicate Proactively: Keep your team informed about your travel plans and potential disruptions to your availability. Schedule regular check-ins to ensure smooth collaboration.
Invest in the Right Technology: A reliable laptop, a strong internet connection, and noise-canceling headphones are essential investments. Consider a portable Wi-Fi hotspot for added flexibility.
Embrace the Local Culture: While working, take time to experience the local culture and connect with the community. This can enrich your travel experience and provide valuable insights.
The Future of Work:
The US software market is increasingly embracing remote work. As this trend continues, the challenges and opportunities for digital nomads will evolve. By carefully planning, adapting, and embracing the unique aspects of this lifestyle, software professionals can successfully navigate the world while building thriving careers.
Disclaimer: This article provides general information and should not be considered legal or tax advice.
I hope this article provides a helpful overview of the challenges and opportunities of traveling while working in the US software market.
2 notes
·
View notes
Text
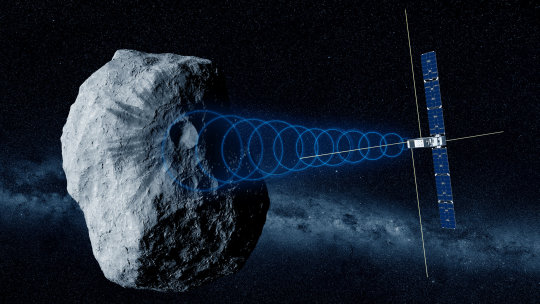

Hera asteroid mission's CubeSat passengers signal home
The two CubeSat passengers aboard ESA's Hera mission for planetary defense have exchanged their first signals with Earth, confirming their nominal status. The pair were switched on to check out all their systems, marking the first operation of ESA CubeSats in deep space.
"Each CubeSat was activated for about an hour in turn, in live sessions with the ground to perform commissioning—what we call 'are you alive?' and 'stowed checkout' tests," explains ESA's Hera CubeSats Engineer Franco Perez Lissi.
"The pair are currently stowed within their Deep Space Deployers, but we were able to activate every onboard system in turn, including their platform avionics, instruments and the inter-satellite links they will use to talk to Hera, as well as spinning up and down their reaction wheels which will be employed for attitude control."
Launched on 7 October, Hera is ESA's first planetary defense mission, headed to the first solar system body to have had its orbit shifted by human action: the Dimorphos asteroid, which was impacted by NASA's DART spacecraft in 2022.
Traveling with Hera are two shoebox-sized "CubeSats" built up from standardized 10-cm boxes. These miniature spacecraft will fly closer to the asteroid than their mothership, taking additional risks to acquire valuable bonus data.
Juventas, produced for ESA by GOMspace in Luxembourg, will make the first radar probe within an asteroid. while Milani, produced for ESA by Tyvak International in Italy, will perform multispectral mineral prospecting.
he commissioning took place from ESA's ESOC mission control center in Darmstadt in Germany, linked in turn to ESEC, the European Space Security and Education Center, at Redu in Belgium. This site hosts Hera's CubeSat Mission Operations Center, from where the CubeSats will be overseen once they are flying freely in space.
Juventas was activated on 17 October, at 4 million km away from Earth, while Milani followed on 24 October, nearly twice as far at 7.9 million km away.
The distances involved meant the team had to put up with tense waits for signals to pass between Earth and deep space, involving a 32.6 second round-trip delay for Juventas and a 52 second round-trip delay for Milani.
"During this CubeSat commissioning, we have not only confirmed the CubeSat instruments and systems work as planned but also validated the entire ground command infrastructure," explains Sylvain Lodiot, Hera Operations Manager.
"This involves a complex setup where data are received here at the Hera Missions Operations Center at ESOC but telemetry also goes to the CMOC at Redu, overseen by a Spacebel team, passed in turn to the CubeSat Mission Control Centers of the respective companies, to be checked in real time. Verification of this arrangement is good preparation for the free-flying operational phase once Hera reaches Dimorphos."
Andrea Zanotti, Milani's Lead Software Engineer at Tyvak, adds, "Milani didn't experience any computer resets or out of limits currents or voltages, despite its deep space environment which involves increased exposure to cosmic rays. The same is true of Juventas."
Camiel Plevier, Juventas's Lead Software Engineer at GomSpace, notes, "More than a week after launch, with 'fridge' temperatures of around 5°C in the Deep Space Deployers, the batteries of both CubeSats maintained a proper high state of charge. And it was nice to see how the checkout activity inside the CubeSats consistently warmed the temperature sensors throughout the CubeSats and the Deep Space Deployers."
The CubeSats will stay within their Deployers until the mission reaches Dimorphos towards the end of 2026, when they will be deployed at very low velocity of just a few centimeters per second. Any faster and—in the ultra-low gravitational field of the Great Pyramid-sized asteroid—they might risk being lost in space.
Franco adds, "This commissioning is a significant achievement for ESA and our industrial partners, involving many different interfaces that all had to work as planned: all the centers on Earth, then also on the Hera side, including the dedicated Life Support Interface Boards that connects the main spacecraft with the Deployers and CubeSats.
"The concept that a spacecraft can work with smaller companion spacecraft aboard them has been successfully demonstrated, which is going to be followed by more missions in the future, starting with ESA's Ramses mission for planetary defense and then the Comet Interceptor spacecraft."
From this point, the CubeSats will be switched on every two months during Hera's cruise phase, to undergo routine operations such as checkouts, battery conditioning and software updates.
TOP IMAGE: Juventas studies asteroid's internal structure. Credit: ESA/Science Office
LOWER IMAGE: Milani studies asteroid dust. Credit: ESA-Science Office
3 notes
·
View notes
Text
Popular Courses Currently in Demand for International Students
@unilifeabroadcareersolutions

Popular courses currently in demand for international students After finding the perfect course, any international student must make another crucial decision when choosing which course to study abroad in. Global industries are currently changing fast, and it can create career opportunities for international students depending upon the fields they choose and the scope for Permanent Residency (PR). So here is a list of some of the top in-demand courses for international students looking to study abroad in 2024 and beyond. 1. Data Science and Artificial Intelligence
With the emergence of big data and AI-driven technologies, Data Science and AI have emerged as two of the most in-demand courses worldwide.
Why Choose It?
High-paying job opportunities. Demand in industries like IT, healthcare, finance, and retail. Courses available in countries like USA, Canada, Germany, and UK. Career Prospects: Data Scientist, AI Engineer, Machine Learning Expert, Data Analyst. 2. Engineering and Technology
Engineering is at the top preference of the international students due to a wide range of area and scope. Some of the most common specializations offered are Mechanical, Civil, Electrical, and Software Engineering.
Why to choose? All over the world, engineers are required for every industry, such as construction, automobile, and technological. Many colleges provide industrial training along with co-op programs. Top Destinations: Germany, Canada, Australia, and USA. Career Opportunities: Software Engineer, Project Manager, Structural Engineer, Robotics Specialized.
3. Business Administration and Management (MBA) A Master of Business Administration (MBA) is ideal for students who want to work in a leadership position or become an entrepreneur. There is a growing trend towards specialized MBAs in Finance, Marketing, Human Resources, and Operations. Why Choose It? International recognition and high-paying jobs. Networking opportunities and exposure to real-world business. Popular Places: USA, UK, Canada, and Australia. Career Paths: Business Consultant, Marketing Manager, Operations Director, Financial Analyst. 4. Healthcare and Nursing The health sector is on a roll due to the growing need for qualified professionals. Nursing, Public Health, Physiotherapy, and Pharmacy courses are highly rewarded. Why Study It? High employability and PR opportunities in countries like Canada, Australia, and UK. Good chance to make a good difference in people's life. Career Options: Registered Nurse, Public Health Specialist, Pharmacist, Physiotherapist. 5. Information Technology and Cyber security The increased dependency on technology has given a huge demand for IT and Cyber security professionals. Courses like Cloud Computing, Cyber security, and Software Development are in high demand. • Why Choose It? Tremendous job opportunities in tech-driven economies like the USA, Canada, and Germany. Increased demand for cyber security experts to combat digital threats. Career Options: Cyber security Analyst, IT Consultant, Software Developer, Cloud Architect.
6. Hospitality and Tourism Management the tourism industry is on a boom after the pandemic, and so are the demands for professionals in Hospitality and Tourism Management. Why Choose It? Global opportunities for working in luxury hotels, airlines, and tourism companies. Strong industry links and placement during courses. • Popular Locations: Switzerland, Australia, France. • Career Opportunities: Hotel Manager, Tourism Consultant, Event Planner, Airline Executive. 7. Environmental Science and Sustainability As there is a growing interest in sustainability across the globe, courses in Environmental Science, Renewable Energy, and Climate Change are on demand • Why study it? Large-scale efforts at creating the sustainable world present a massive employment scope. • Job opportunities with governments, NGOs, and private sectors Career Prospects: Environmental Consultant, Sustainability Officer, Renewable Energy Specialist. 8. Finance and Accounting Courses on finances and accounting are always in high demand all over the world. FinTech, Financial Technology, and all the related courses are in trends these days. Why Choose It? • High demand for finance people in the world. PR opportunities in Canada and Australia • Career Options: Accountant, Financial Analyst, Investment Banker, FinTech Specialist. 9. Media and Communications The dawn of digital media, content creation, and advertising has made Media and Communications one of the most exciting and rewarding fields. Why Choose It? Growing job demand in digital marketing, PR, and content strategy. Opportunity for creativity and innovation. Career Options: Digital Marketer, Media Specialist, Content Creator, Public Relations Officer. 10. Logistics and Supply Chain Management Supply Chain Management has become a necessary professional skill for international businesses considering the booming of globalization and e-commerce
Why Choose It? Logistics, transportation and e-commerce sectors are demanded. Strong employment opportunities in Canada, Germany and USA. Career Options: Supply chain analyst, logistics manager and procurement specialist. Conclusion The right course according to global trends and industry demand is the key to a successful future. Whether it's technology, healthcare, or business, the top courses in demand are here, offering excellent career opportunities and pathways for PR. Explore programs that align with your interests and goals, and take the first step toward achieving your dream career abroad.
#unilife abroad career solution#unilifeabroadcareersolution#abroad study#free education#paid education#without ielts#overseas education#free education in italy#popularcoursesinabroad
2 notes
·
View notes
Note
How do you get such nice shots in captura? I wanna get better at it could you share some tips? Been trying to figure it out but I admit I'm not the most knowledgeable in photography etc.
Well.... It's a bit of a complicated process and it relies very very much on personal preference. Much like with any type of art there are different styles that each individual artist will gravitate toward. I can only show you how I do things, so I'd recommend asking other Captura folks on here about their own styles to see where our processes and preferences differ.
I'll also include some extremely helpful videos at the bottom, they go extremely in depth as to best practices and technical exploits.
Alright, lets get started with the background stuff... the tools! ReShade: Shader injection, a MUST if you want to take dynamic and customized captura without using a program like Photoshop to do everything in post.
SRWE: Simple Runtime Window Editor.... the god among programs... It's an upscaler, allowing you to increase the resolution of the game beyond the bounds of your monitor. It's how I was able to get 15K panoramas at one point in time.
Any image editing software. Since I rely mainly on compositing to get the lighting I do, I need something to overlay and mesh the images with. I use GIMP cuz it's free, but even Microsoft Paint will work as soon as it add the ability to layer images.
Those are the tools... what about the tactics?
Well, I generally prefer moodier shots with the Warframe being the central focus (though, that's also the side effect of me cropping the image). Just a note! Moody doesn't mean dark, moody is the enigmatic space between dark and light where there is more dark than light... but there's still a good amount of light to be had. Occasionally you can have overexposure in a moody shot even.
Important to note, the overall exposure level of the environment, even is the scene lighting is low, will effect how brightly your Warframe can be lit. Both the Scene Light and Exposure sliders need to be fine-tuned otherwise you won't be able to light your Warframe at all.
Now, for shot composition I prefer low angles with either a cluttered but familiar/recognizable background, or a simple but abstract background. The Subject, be it a Warframe, an enemy, or an NPC, reside in the center with their feet out of shot.
Like so:


Each of these shots also demonstrate well the way I like to pose my subjects: Symmetry and.... not... not symmetry. The official term for this is Contrapposto, which is Italian for Counterpoise. Basically, even though the Wisp is sedentary, her body is still giving off the impression of movement based on how her waist is curving and hips are tilted, forming a loose 'S' shape. There's a handful of animation sets, Khora (Urushu) Noble, Mesa Noble, and Wisp Noble are excellent for this.
Some examples:



But... what about the lighting? This is where things get technical. So, the standard Captura's three-point lighting system is generally inadequate at properly lighting the entire Warframe. This is where compositing enters the picture, in a very literal sense. Each of these shots, shown above, are composites of between two and four separate images, each with different lighting angles. I actually have an example I made for an earlier explanation made already (thank goodness)


Getting the different lighting angles is really simple, just rotate the 3-way lighting without moving the camera. Then you overlay them in some photo editing software and just start going layer by layer, erasing bits of the topmost layer to reveal your desired highlights or shadows from the shot underneath.
Don't feel obligated to do this compositing process though! Sometimes the 3-way lighting works perfectly well for a shot or environment, don't feel obligated to complicate this process.
And this segues in nicely to the final part of the shot-making process, post-processing and fog layers.
Now, fog layers are important to the overall appearance and vibe of my Captura. They add texture the image that the game doesn't impart naturally, removing large swathes of solid color from the background and foreground. An added bonus is that the added texture makes the image look somewhat better (imo) when compressed, or when viewed at lower resolutions.
The same image with and without Fog


This shot contains two individual fog layers, one in the foreground, washing out the foliage, giving the general uniformity of it texture and implied depth, it also serves to cover up the manual blurring I did (poorly) around his legs. Then there's the background Fog, which is the deeper blue you see in the sky. It adds a more dynamic air to the generally dour set of greys. And, again, the fog is just something I personally like to add, even if it doesn't serve a practical purpose in a shot. No shade if someone feels the fog ruins the shot, I almost always keep a fog-free version about.
After the fog is added, blended, and blurred slightly, I will apply a few gentle blurring filters to remove any jarring or jagged pixelation from the shot, giving the Frame a somewhat smoother appearance and reducing the file-size dramatically.
That's just how I do it though, it's not a particularly popular style, but it's how I do it and how I love to do it! :3 Remember to ask around, I'm sure there's lotsa Captura Artists out there willing to explain their methods and processes.
Helpful vids! How to Captura by Vash Cowaii Hotsampling in Warframe for High Res Shots by PurpleFlurp
good luck, and happy snapping!
#warframe#captura#warframe tag#warframe captura#sorry for writing an essay... sometimes I don't know when to shut up#-_-
13 notes
·
View notes
Text
Integrated Cluster Development Scheme: A Visionary Initiative by Col Rajyavardhan Rathore

The Integrated Cluster Development Scheme (ICDS), launched under the leadership of Colonel Rajyavardhan Rathore, marks a significant milestone in fostering economic growth and social development across Rajasthan. Focused on empowering small-scale industries, artisans, and rural entrepreneurs, this initiative is set to transform traditional production clusters into engines of innovation, employment, and sustainability.
In this article, we’ll explore the goals, features, and potential impact of this scheme on Rajasthan’s economy and its people.
What is the Integrated Cluster Development Scheme?
The ICDS aims to modernize and strengthen production clusters in Rajasthan, encompassing sectors like handicrafts, textiles, food processing, and small-scale manufacturing. By integrating infrastructure development, skill training, and financial incentives, this scheme provides a holistic framework to promote regional growth.
Col Rajyavardhan Rathore’s Vision Behind the Scheme
Col Rajyavardhan Rathore, a staunch advocate for rural development and economic empowerment, believes that: “Clusters are the backbone of our economy. Strengthening them means empowering our artisans, entrepreneurs, and communities for a brighter, self-reliant Rajasthan.”
His leadership in shaping the scheme reflects a commitment to harnessing the state’s cultural heritage and industrial potential for sustainable development.
Key Objectives of the ICDS
Economic Growth: Enhance the productivity and profitability of Rajasthan’s traditional and emerging clusters.
Job Creation: Generate employment opportunities, particularly in rural and semi-urban areas.
Skill Development: Provide training to workers and entrepreneurs in modern techniques and global standards.
Sustainability: Promote eco-friendly practices in production and infrastructure.
Global Competitiveness: Enable clusters to compete effectively in national and international markets.
Highlights of the Integrated Cluster Development Scheme
1. Infrastructure Upgradation
Establishment of common facility centers (CFCs) equipped with modern tools and machinery.
Development of dedicated industrial parks and cluster zones.
Improved connectivity through roads, railways, and digital infrastructure.
2. Financial Support
Subsidies and Grants: Financial assistance for purchasing equipment and upgrading technology.
Cluster Development Funds: Allocation of funds for infrastructure, marketing, and research.
Low-Interest Loans: Easy access to credit for small businesses and artisans.
3. Capacity Building
Skill Training Programs: Workshops on modern production techniques, quality control, and innovation.
Entrepreneurship Development: Training in business management and digital marketing.
Global Exposure: Participation in national and international trade fairs.
4. Promoting Innovation and Technology
Establishment of innovation hubs within clusters to encourage research and development.
Integration of digital tools such as e-commerce platforms and management software.
5. Focus on Key Sectors
Handicrafts and Textiles: Revitalizing traditional crafts with modern designs.
Food Processing: Expanding the scope of agro-based industries with value addition.
Renewable Energy Clusters: Promoting solar and wind energy production units.
Impact of the Scheme on Rajasthan
Economic Benefits
An estimated 20–30% increase in cluster productivity within the first three years.
Boost in state GDP through enhanced industrial output and exports.
Social Empowerment
Improved livelihood opportunities for over 50,000 workers and artisans.
Empowerment of women and marginalized communities through focused support programs.
Sustainability
Adoption of eco-friendly production techniques, reducing the environmental footprint.
Examples of Targeted Clusters
Jaipur Handicrafts Cluster
Known for its exquisite jewelry, blue pottery, and textiles, Jaipur’s cluster will benefit from marketing support and infrastructure development.
Jodhpur Furniture Cluster
Famous for its wooden furniture, this cluster will see investments in modern tools and export promotion.
Bikaner Agro Cluster
A hub for food processing and agricultural produce, Bikaner’s cluster will receive funding for value-added processing units.
How the Scheme Promotes Self-Reliance
Aligned with the “Make in India” and “Atmanirbhar Bharat” initiatives, the ICDS focuses on reducing import dependency by enhancing local production capabilities. By enabling small businesses to scale up and reach global markets, it fosters a self-reliant ecosystem.
Col Rajyavardhan Rathore’s Commitment to Progress
Col Rathore has been instrumental in advocating policies that blend tradition with technology. His leadership ensures that the ICDS not only preserves Rajasthan’s cultural identity but also propels it into the future.
In his words: “This scheme is a tribute to the hardworking people of Rajasthan who keep our traditions alive while embracing the opportunities of the modern world.”
A New Dawn for Rajasthan’s Clusters
The Integrated Cluster Development Scheme is a game-changer for Rajasthan’s economy. By focusing on modernization, skill enhancement, and financial support, it promises to uplift thousands of artisans, workers, and entrepreneurs while showcasing Rajasthan’s rich heritage to the world.
This initiative is not just about economic development; it’s about empowering communities, celebrating culture, and creating a sustainable future for all.
4 notes
·
View notes
Text
Yvette Heiser - Mastering Advanced Photo Editing for Breathtaking Travel Photography
Travel photography is about capturing the essence of the places you visit—whether it’s the breathtaking landscapes, vibrant cityscapes, or candid moments of local life. However, a great photo isn’t just taken; it’s crafted. As seen in Yvette Heiser Travel and Photography: Capturing Nature, advanced photo editing techniques can transform an ordinary shot into a stunning image that not only preserves memories but also enriches the narrative behind each photograph.

Just as a painter adds layers of color and detail to a canvas, advanced editing tools empower photographers to enhance their images and showcase the best aspects of their travel experiences. Let’s explore some essential photo editing techniques that can elevate your travel photography to new heights.
1. Correcting Exposure for Perfect Lighting
Exposure plays a crucial role in photography, determining how light or dark an image appears. Travel photography often involves shooting in diverse lighting conditions—from bright sunny beaches to dimly lit streets. One of the first steps in editing your travel photos is adjusting the exposure to achieve balanced lighting.
In post-processing software like Adobe Lightroom or Photoshop, you can adjust the exposure sliders to brighten dark areas or tone down overly bright spots. This helps create a more evenly lit image, ensuring that the key details of the scene are visible. Think of it like opening or closing blinds in a room—you're controlling how much light comes in to reveal or hide certain aspects.
2. Enhancing Colors for Vivid Imagery
Travel photography often includes vibrant colors—whether it’s the blue waters of a tropical island, the orange hues of a desert sunset, or the green hills of a countryside. Enhancing the colors in your image can make these elements pop, adding richness and depth to your photo.
You can achieve this by adjusting the saturation and vibrance settings in your editing software. Saturation controls the intensity of all the colors in your image, while vibrance selectively increases the intensity of only the muted tones, leaving already bright colors intact. It’s like adjusting the contrast on a painting to make certain colors stand out without overwhelming the entire composition.
3. Using Local Adjustments for Precision
In advanced editing, precision is key. Global adjustments (like brightness or contrast) affect the entire image, but sometimes you need to focus on specific areas to create a more balanced and dynamic image. Local adjustments allow you to make targeted edits, whether it’s brightening up a subject’s face in the foreground or reducing the brightness of a distracting object in the background.
Tools such as the brush, radial filter, or graduated filter in programs like Lightroom let you adjust exposure, contrast, and clarity in specific areas of your photo. This technique is like using a spotlight on a stage—highlighting the main subject while keeping the rest of the image balanced.
4. Sharpening for Crisp Details
One of the key aspects of travel photography is capturing the fine details that make each location unique. Whether it’s the intricate architecture of a historic building or the texture of a mountain range, sharpening helps enhance the clarity of these details.
Sharpening tools focus on the edges in your photo, making them crisper and more defined. Be cautious, though—too much sharpening can make your image look unnatural, like over-seasoning a dish. A light touch is often all you need to make your photos appear polished and professional.
5. Removing Unwanted Elements
Travel photography can sometimes include unwanted distractions—a person walking into the frame, a piece of trash on the ground, or power lines running through the sky. Luckily, modern photo editing software has tools that can remove these elements seamlessly.
The clone stamp or healing brush tools in Photoshop can help you remove these distractions by sampling nearby areas and blending them into the unwanted spots. Think of it like cleaning up a cluttered room, making sure that only the elements that matter remain in the frame.
6. Perfecting the Composition with Cropping
Even the best photographers sometimes need to adjust the framing of their shot after the fact. Cropping allows you to refine your composition, eliminating unnecessary areas and directing the viewer’s attention to the most important parts of the image.
For instance, you might crop out empty space around a subject or use the rule of thirds to reposition key elements within the frame. It’s like trimming a bonsai tree—removing excess branches to highlight the tree’s natural beauty.
Conclusion
Mastering advanced photo editing techniques can elevate your travel photography, transforming good photos into stunning, unforgettable images. Techniques covered in Yvette Heiser's "Painting with Pixels: A Guide to Advanced Photo Editing Techniques" include adjusting exposure, enhancing colors, sharpening details, and removing distractions. Each step in the editing process helps you craft a more compelling narrative through your lens. With these methods in your toolkit, you’ll be well-equipped to capture and share the magic of your travels in a way that leaves a lasting impression..
#wedding#camera#moments#pictures#childphotography#photographer#photographytips#photography#yvette heiser#events
5 notes
·
View notes
Text
The Value of a BCA Degree: Is It Worth Pursuing?
In the rapidly evolving landscape of technology and business, the Bachelor of Computer Applications (BCA) degree has emerged as a popular choice for students aiming to carve out a career in the IT sector. As technology continues to influence every aspect of our lives, the demand for skilled professionals in the field has never been higher. But is a BCA degree truly worth pursuing? Let’s explore the benefits and considerations to help you determine if this path aligns with your career goals.
What is a BCA Degree?
A Bachelor of Computer Applications (BCA) is a three-year undergraduate program designed to provide students with a strong foundation in computer science and applications. The curriculum typically covers programming languages, software development, database management, networking, and other core areas of IT. In addition to technical skills, BCA programs often include training in problem-solving and project management.
Benefits of Pursuing a BCA Degree
Foundation in IT Skills: The BCA program equips students with essential IT skills, including proficiency in programming languages like Java, C++, and Python. This foundation is crucial for any career in technology and prepares students for various technical roles.
Diverse Career Opportunities: Graduates of BCA programs can pursue a wide range of careers in IT and related fields. Job roles such as software developer, web developer, system analyst, and network administrator are just a few examples. Additionally, the skills gained from a BCA degree can also be applicable in sectors such as finance, healthcare, and education.
Gateway to Advanced Studies: For those interested in further specialization, a BCA degree can serve as a stepping stone to advanced degrees such as a Master’s in Computer Applications (MCA) or a Master’s in Business Administration (MBA). These advanced degrees can open doors to higher-level positions and increased earning potential.
Practical Experience: Many BCA programs emphasize practical experience through internships, projects, and industry collaborations. This hands-on approach helps students gain real-world experience, making them more attractive to potential employers.
Growing Demand for IT Professionals: The tech industry continues to expand globally, and the demand for skilled IT professionals is on the rise. A BCA degree can provide a competitive edge in a job market that increasingly values technological expertise.
Considerations Before Pursuing a BCA Degree
Cost and Duration: While a BCA degree is often less expensive than a four-year engineering degree, it’s still a financial commitment. It’s important to weigh the cost of tuition against the potential return on investment in terms of job opportunities and salary.
Job Market Saturation: In some regions, the job market for IT professionals can be competitive. It’s important to research local job markets and employment trends to ensure that there are sufficient opportunities available.
Interest in IT: A BCA degree requires a strong interest in technology and computer science. If you’re not passionate about these fields, you might find the coursework challenging and less engaging.
Long-Term Career Goals: Consider how a BCA degree aligns with your long-term career goals. If you aim to work in highly specialized or advanced IT roles, you may need additional qualifications or experience beyond a BCA degree.
Alternative Paths: There are various alternative paths to a career in IT, such as coding bootcamps, certifications, and online courses. These alternatives can sometimes offer a more flexible or cost-effective route to entering the tech industry.
RERF , while primarily known for its research on radiation exposure and health effects, is not directly related to educational institutions like BCA colleges. However, for students interested in a Best BCA college in Kolkata, the city offers several reputable options that provide a solid foundation in computer applications and technology. These colleges prepare students for diverse IT careers and often include advanced research opportunities in their curriculum. If you're looking to pursue a BCA in Kolkata, you'll find institutions that can equip you with the skills needed for a successful career in the tech industry.
Conclusion
The Bachelor of Computer Applications (BCA) degree offers a solid foundation in computer science and opens doors to numerous career opportunities in the technology sector. For those with a passion for IT and a desire to work in a rapidly growing field, the BCA degree can be a worthwhile investment. However, it's essential to consider your personal interests, career goals, and the job market in your area before making a decision. By carefully evaluating these factors, you can determine if a BCA degree aligns with your aspirations and offers the value you’re seeking in your educational and professional journey.
2 notes
·
View notes
Text
What is Enterprise Fleet Management?

As is revealed in today’s world business environment, any organization must manage its resources appropriately. Thus, for companies and firms having major operations related to transportation and logistics, it becomes even more essential to manage their fleets.
Now, let’s start with the basics: what does enterprise fleet management mean? Now let’s discuss this idea and figure out how it can be of great benefit to the business processes.
Understanding what is Enterprise Fleet Management
Fleet management within an enterprise could be described as a strategic approach to managing and supervising such a company's vehicle fleet. The areas include its acquisition and maintenance, driver and vehicle management, and laws governing the automobile industry. Fleet management is prospective to optimize the operating costs and enhance the safety and productivity of both fleets and their drivers.
In an enterprise environment, fleet management goes beyond tracking the vehicles; it is more about getting improved ways of running organizations. Fleet management is important irrespective of whether it involves delivery vans, trucks, or even corporate cars if the business owns a set of cars for business use.
The outcome highlights the fundamental issues of fleet management.
Vehicle Acquisition and Disposal: Picking the correct car for your fleet, beginning from procurement to the time of disposal.
Maintenance and Repair: Managing to schedule vehicles for maintenance and repairs regularly to make sure that they are in good working condition to reduce time loss.
Fuel Management: Fuel efficiency management by controlling consumption and considering these to minimize fuel expenses by using fuel-efficient driving techniques and other energy resources.
Driver Management: Incorporating training and supervision of drivers as well as planning meals nt to support safety, compliance, and efficiency among the drivers.
Compliance and Risk Management: The safety of all the used vehicles as well as the used drivers with brutal and international requirements and managing of risk exposures of operating fleets.
Here we will discuss the concept of Fleet Management Software. Inefficiently managing all these components, many businesses turn to the use of fleet management software. This is because it acts as a platform for accessing any information regarding the fleet, including real-time data and automated operations of the fleet.
Key Features of Fleet Management Software
GPS Tracking: Precise vehicle location in real-time to increase efficiency and controllers.
Maintenance Scheduling: Schedule reminders in case of preventive maintenance and repairs to avoid ‘bottlenecks Management: Proper equipment that tracks fuel usage and gives an indication of wasteful activities.
Compliance Management: Material properties garages need to comply with set safety measures as well as regulatory requirements.
Driver Performance Monitoring: Measures to monitor and measure drivers’s performance, detect their training requirements, and incentivize them over safe behavior on roads.
Why Enterprise Fleet Management is So Important
To large companies, fleet management is not only limited to planning on how to ensure that vehicles are running. It’s about being able to harness data and technology in a way that will put you ahead of the competition. Effective management of fleets is known to have numerous benefits, such as cutting costs, satisfying customers, and reducing risks involving drivers and cars, among others.
However, due to emerging issues such as global warming, companies are now focusing on the use of fleets to be environmentally friendly. This is done through the optimization of routes, timely maintenance of vehicles, and training of the drivers to ensure they are conscious of the impact they make on the environment.
Being a web-based service, the most advantageous aspect related to an FMS or a Fleet Management Software Development Service is that it can be easily and effectively utilized across the corporate fleet range.
This has led to the increasing need for the development of fleet management software to be able to meet the expanding market need. Custom software, as the name suggests, is designed to improve organizational operations to suit a company’s needs, making it more flexible than packaged software.
A fleet management software development service typically includes
Consultation and Needs Assessment: Ah, awareness of the particular requirements and objectives of your fleet. You need to hire a professional fleet management software development company.
Custom Software Development: Constructing a custom fit that incorporates into the complex structures of the organization and fits the needs of the organization perfectly.
Integration with IoT Devices: The use of Internet of Things (IoT) devices such as GPS trackers or sensors to input real-time information and data.
Ongoing Support and Maintenance: Needed to make sure the software will continue to include all the features and incorporate the latest technologies and that it will cover all current needs of the business.
Conclusion
Okay, then, Fleet management is a system that encompasses all activities that involve control of a company’s fleet of vehicles with the use of the latest technologies in software and quality practices. Fleet management is not only a good idea but a necessity for any business that depends on transportation, where proper management of the company’s fleet is critical to achieving success.
Let it be a handful of vehicles or a multitude, the appropriate strategy in fleet management as enhanced by software changes the equation, provides steps towards optimizing your operations, lowers costs, and enhances the performance of an organization. The fast advancement of technology means that the means and ways used in the implementation of the strategies by the f managers are ever-changing and therefore a very promising industry to follow.
#business growth#fleet management#fleet maintenance#enterprise software#enterprise application development#business solutions#software#trending#viralpost#viral trends
2 notes
·
View notes
Text
ha megkerestek linkedin-en (recruiter) h van egy X cegnel allaslehetoseg, gaz ha inkabb en magam kuldom el a paprijaimat a cegnek? (megtalaltam oket direktbe linkedinen es allast is hirdetnek (linkedin + sajat weboldalon) )
mondjuk pingpong asztalt nem hirdetnek, mega weboldalukon a soc media linkek fele halott (fb es twitter accountok deaktivaltak), de allitolag 11-50 ember dolgozik ott , de glassdoor-on nincsenek jelen
(Edit: saját weboldalukon nem lehet jelentkezni,van egy generic email cím, meg LinkedIn állás,mégis a recruiter út lesz, hátha van belső kapcsolata)
ez nem hangzik borzasztoan:
Responsibilities
Develop quality software and web applications
Analyze and maintain existing software applications
Design highly scalable, testable code
Discover and fix programming bugs
Qualifications
5+ years of C#
5+ years of SQL Server
2+ years of Cloud services, ideally Windows Azure
Bachelor's degree or equivalent experience in Computer Science or related field
Desirable Skills or Exposure
AI and Large Language Models
Machine Learning
Big Data
The Package
Salary £55-65K per annum (depending on experience).
Remote & Physical Office (usually 1 day per week but not mandatory).
25 days holiday, plus UK bank holidays, plus discretionary extra Christmas leave (3 days). Increases after 3 years’ service to one additional day per year to a maximum of 30.
Share Options (EMEI Scheme).
4% employer pension contribution.
WFH allowance plus budget of £150 per year for home working expenses.
Simply Health Cashback plan.
Group Life Assurance upon death your family will receive 4x your salary.
Group Income Protection upon long term illness you will receive 75% of your salary.
Discretionary Bonuses in line with business performance.
Annual Salary review.
3 notes
·
View notes