#How to Protect Your PC against File-Encrypting Ransomware
Explore tagged Tumblr posts
Text
Critical Windows Update: Apply Patch Now to Prevent Black Basta Ransomware
#Time is running out for Windows users to secure their systems against the notorious Black Basta ransomware. Microsoft has released a critica#as failure to install it could leave your PC vulnerable to sophisticated ransomware threats.#The Critical Windows Update#Microsoft has issued an urgent call to all Windows users to apply a crucial security patch aimed at thwarting the Black Basta ransomware. T#your system remains susceptible to attacks that could encrypt your data and demand a ransom for its release.#Understanding Black Basta Ransomware#Black Basta is a highly dangerous form of ransomware that encrypts files on the victim’s computer#rendering them inaccessible until a ransom is paid. Often#even paying the ransom does not guarantee the recovery of the encrypted files. The threat posed by Black Basta is severe#making it imperative for users to protect their systems immediately.#Why This Update is Crucial#The update released by Microsoft is designed to close a vulnerability that Black Basta exploits to infiltrate systems. Cybersecurity expert#emphasizing the need for users to act quickly. Applying this patch is not just a recommendation—it’s a necessity to safeguard your personal#How to Apply the Update#Applying the Windows update is straightforward:#Open the Settings menu on your Windows PC.#Navigate to Update & Security.#Click on Windows Update.#Select Check for updates.#Once the update appears#click Download and install.#Ensuring your system is up-to-date with the latest security patches is a vital step in protecting against ransomware attacks.#Potential Consequences of Ignoring the Update#Failure to apply this critical update could result in severe consequences. If Black Basta ransomware infiltrates your system#you could lose access to valuable data#suffer financial loss#and face significant disruptions to both personal and business operations. The cost of recovery and the potential damage to your reputation#Real Stories#Real Risks#Think about all the important files on your computer—photos
0 notes
Text
A Deep Dive into Avast's Latest Features: What’s New in Cybersecurity?
In an age where digital threats continue to evolve, the need for advanced cybersecurity solutions cannot be overstated. Avast, a well-known name in the antivirus industry, has consistently delivered top-tier protection for millions of users worldwide. But what’s new in 2024? How is Avast staying ahead of cybercriminals? Let’s explore the latest features of Avast and discover why it remains a leading choice for digital security. Additionally, we’ll uncover how you can save on Avast’s premium offerings using Avast Coupons and Promo Codes and Avast Promo Codes.
Why Is Avast a Top Choice in 2024?
1. Next-Generation Threat Detection
Next-Generation Threat Detection What sets Avast apart in 2024? The answer lies in its next-generation Cyber Threat Protection capabilities. Avast has integrated machine learning and artificial intelligence into its security engine, enabling it to detect and neutralize threats faster than ever before. This new technology allows Avast to identify even the most sophisticated malware, ensuring that your devices remain protected against emerging threats.
2.Enhanced Ransomware Shield Ransomware continues to be a significant threat to both individuals and businesses. In response, Avast has enhanced its Ransomware Shield feature. What makes this update noteworthy? Avast now offers more robust protection by monitoring and securing sensitive files from unauthorized changes. This means that even if ransomware infiltrates your system, your essential data remains safe and untouched.
3.Privacy Protection Like Never Before How does Avast address the growing concern over Online Privacy Protection? In 2024, Avast has introduced several privacy-focused features designed to safeguard your personal information. The Avast Secure Browser now offers enhanced privacy features, helping you secure your digital footprint. Additionally, the Data Shredder ensures that deleted files cannot be recovered, adding an extra layer of protection against data breaches.
4.Avast SecureLine VPN IntegrationWhy should you consider a VPN in 2024? With the increasing risks of data interception and tracking, Avast has made its Avast VPN more integral to its security suite. This VPN offers encrypted connections, keeping your online activities private and secure, even on public Wi-Fi networks. The seamless integration of SecureLine VPN within the Avast dashboard ensures that you’re just a click away from enhanced privacy.
5.User-Friendly Interface What makes Avast appealing to users of all tech levels? Avast’s user-friendly interface is designed for simplicity and efficiency. Whether you’re a tech expert or a beginner, navigating through Avast’s features is intuitive. The dashboard is streamlined, providing easy access to all essential tools, from scanning for threats to activating the VPN.

How to Save on Avast with Coupons and Promo Codes
Where to Find Avast Coupon Codes?
Curious about where to find the best Avast discounts? Dealszo is a top destination for all your coupon needs. This platform offers a wide variety of Avast Coupons and Promo Codes, allowing you to secure your devices without breaking the bank. From Avast Discount Codes and Vouchers to special offers for seasonal events like Black Friday Sales, Dealszo has you covered. It’s a reliable source for discounts across various categories, making it easier to stay protected and save money at the same time.
Exploring Avast’s Comprehensive Security Suite
Avast Premium Security Why choose Avast Premium Security? This all-in-one solution offers comprehensive protection for your PC, Mac, and mobile devices. Avast Premium Security includes features like advanced ransomware protection, a robust firewall, and real-time threat monitoring. The software also provides protection against Phishing Protection attacks, ensuring that your personal and financial information remains secure.
Avast Ultimate: The Complete Package What makes Avast Ultimate the best value for your money? Avast Ultimate combines all of Avast’s top features into one package. It includes Premium Security, SecureLine VPN, Cleanup Premium, and AntiTrack. With Avast Ultimate, you get the best of everything—enhanced security, optimized device performance, and unmatched privacy protection. Plus, using Avast Coupons 2024 can make this premium package even more affordable.
Avast Free Antivirus Is Avast Free Antivirus still a good choice in 2024? Absolutely. Avast Free Antivirus offers essential protection at no cost, making it a great option for those who need basic security without paying a dime. While it lacks some of the advanced features found in the paid versions, it still provides solid protection against viruses, malware, and spyware.
Latest Avast Offers & Discount
Up To 70% Off Avast Discounts & Coupon Codes
Unlock up to 70% off on Avast products with exclusive discounts and coupon codes. Safeguard your devices while saving big. Don’t miss out, grab your deal now!
Up to 60% off Avast Premium Security
Save up to 60% on Avast Premium Security! Enjoy top-notch protection against threats with advanced features at an unbeatable price.
61% Off Avast Premium Security
Enhance your digital security at a steal! Enjoy 61% off on Avast Premium Security. Fortify your devices with advanced protection today.
#DigitalSecurity#CyberSecurity#AntivirusSoftware#CyberProtection#DataPrivacy#OnlineSafety#SecureYourDevices#MalwareProtection#RansomwareProtection#StaySafeOnlineHalloweenDeals#Halloween2024#CouponCodes#PromoCodes#DiscountOffers#SmartShopping#OnlineShopping
0 notes
Text
Protect Your Data with Waredot Anti-Ransomware

In a world where digital threats are constantly evolving, protecting your data is more important than ever. Ransomware attacks can cripple businesses and personal systems alike, leading to data loss and significant financial damage. Waredot Anti-Ransomware offers a robust solution to safeguard your digital assets. In this blog post, we'll explore how Waredot Anti-Ransomware can protect your data and provide peace of mind.
Introduction to Ransomware and its Impact on PC Users
Ransomware - the mere mention of this malicious software is enough to send shivers down the spine of any PC user. Imagine waking up one day to find all your files locked and held for ransom by cybercriminals. Terrifying, right? But fear not! In this blog post, we will introduce you to Waredot Anti-Ransomware, your ultimate shield against these digital extortionists. Stay tuned to learn why every PC user should have Waredot Anti-Ransomware installed for peace of mind and protection in the online world.
What is Waredot Anti-Ransomware?
Ransomware is a type of malicious software that encrypts a user's files and demands payment for their release. Waredot Anti-Ransomware is a powerful tool designed to protect PC users from falling victim to these extortion schemes.
Unlike traditional antivirus programs, Waredot specifically targets ransomware threats, offering an added layer of security against this evolving form of cybercrime. By detecting and blocking ransomware attacks in real-time, Waredot helps safeguard your valuable data and personal information.
With its advanced algorithms and threat intelligence capabilities, Waredot continuously monitors your system for any signs of malicious activity. This proactive approach ensures that your files remain safe from unauthorized encryption attempts.
By incorporating cutting-edge technology and innovative security measures, Waredot Anti-Ransomware provides PC users with peace of mind knowing that their data is protected against the growing threat of ransomware attacks.
How Does Waredot Anti-Ransomware Protect Your PC?
Waredot Anti-Ransomware offers robust protection for your PC against ransomware attacks. By continuously monitoring your system, it can detect suspicious activities and behaviors commonly associated with ransomware.
The software uses advanced algorithms to identify and block malicious files before they have a chance to encrypt your data. It also provides real-time scanning of incoming files and emails to prevent any ransomware threats from infiltrating your computer.
Moreover, Waredot Anti-Ransomware creates secure backups of your important files, ensuring that even if you fall victim to an attack, you can restore your data without having to pay a ransom.
With its proactive approach to cybersecurity, Waredot Anti-Ransomware gives you peace of mind knowing that your PC is constantly defended against the ever-evolving threat landscape of ransomware.
Frequently Asked Questions about Waredot Anti-Ransomware
Have questions about Waredot Anti-Ransomware? You're not alone! Let's address some common queries to help you better understand this essential tool.
One common question is, "Does Waredot Anti-Ransomware slow down my computer?" The answer is no! This software runs efficiently in the background without impacting your PC's performance.
Another frequent query is, "Can Waredot Anti-Ransomware protect against all types of ransomware?" Yes, it uses advanced algorithms to detect and block various ransomware strains effectively.
Users often ask, "Is Waredot Anti-Ransomware easy to install?" Absolutely! With a user-friendly interface and simple installation process, safeguarding your data has never been easier.
"Does Waredot offer customer support?" Yes, their dedicated team is available to assist with any inquiries or issues promptly.
1 note
·
View note
Text
Windows Defender Or Bitdefender: How to Choose the Best?
Windows Defender is the inbuilt antivirus program that you get with Windows 10 and Windows 11 on your PC or laptop. It acts as the first line of defense and does a great job. For most people, it’s more than enough to protect their system. Windows Defender provides decent cloud-based malware detection, but it cannot detect and eliminate all types of threats. Bitdefender is a top-notch security program that is compatible with Windows, macOS, iOS, and Android devices. But the question you must be asking yourself is whether you should stick with the free option or purchase Bitdefender to protect your PC or laptop. Luckily, we are here to provide you with all the information you need to make an informed decision.
Security Features
Previously, Windows Defender had a bad reputation, but over the years, it has made some significant improvements in its threat detection capabilities and features. It doesn’t mean that you can depend solely on it to protect your system without another antivirus program.
Unlike other antivirus suites that you have to download and install, Windows Defender is built into Windows 10 and is mainly focused on securing and protecting your system against threats. So, with Windows, you get what you see; it sticks to the essentials and is more straightforward. However, it still offers some pretty notable features that are hard to ignore.
Windows Defender offers some exclusive features under a single roof that can’t be replaced with any other antivirus protection program, including Windows Hello, Dynamic Lock, and Microsoft account protection options. It also offers some non-antivirus-related functionalities, including Fresh Start, drive encryption, one drive for ransomware recovery, and customer support.
Unlike Windows Defender, Bitdefender needs to be installed on your PC or laptop. It offers third-party products with full-blown features that Windows Defender can’t seem to match. For personal and home use, Bitdefender offers five premium antivirus products. We will start with Bitdefender’s low-end product, Bitdefender Antivirus Plus for Windows. It’s a base product but packs more features than Windows Defender. These features are grouped into three categories: protection, performance, and privacy.
Other than offering on-device and browser security, Bitdefender’s protection features also offer on-device and browser security. These features are:
Privacy features protect and secure your system against online threats. These features are:
Next is Bitdefender Internet Security, which offers more privacy features. These additional features are:
Bitdefender Total Security is one of Bitdefender’s cross-platform products. It's compatible with Windows, macOS, iOS, and Android devices. It packs all the features of the previous products and some additional ones. These additional features are:
Next is Bitdefender Family Pack, which, like Bitdefender Total Security, is compatible with various devices. It has all the features of previous products and is suitable for people with more than 10 devices or large households. It supports a maximum of 15 devices. And lastly, there is Bitdefender Premium Security, which packs all the features of the previous product and offers unlimited VPN traffic.
Malware Protection
Although Windows Defender is a free built-in antivirus suite, it is good enough to compete with premium antivirus suites. Its antivirus engine was able to match the performance of Bitdefender’s antivirus engine. Both antivirus engines do an excellent job of protecting your system against offline and online threats, including viruses, malware, ransomware, spyware, and other threats.
Windows Defender uses its memory-integrity feature to offer protection against file-less threats. It is also equipped with exploit and tamper protection abilities that prevent malicious apps from turning off. It also checks email attachments in Outlook for malicious code on occasion. For comprehensive protection, Windows Defender relies on real-time and cloud-delivered protection. To offer maximum protection, Windows Defender utilizes online analysis and malware signatures. It also compares new threats to its database of known malware.
In contrast, for a comprehensive solution, Bitdefender offers a couple of technology enhancements. Other than its award-winning antivirus engine, Bitdefender products rely on advanced threat defense and network threat prevention. They also get access to Bitdefender’s cyber threat intelligence, which offers protection against suspicious network-level activities and cyber-attacks. Using these advanced security features, Bitdefender analyzes, identifies, and block network threats.
System Performance
Besides protecting your system against all types of threats, a good antivirus should not impact your system’s performance in a negative way. As Windows Defender is an in-built antivirus, in theory, it should have a minimal effect on the system’s performance. But that is not the case when Windows Defender performs background scans. You may notice that your cooling fans are making a lot more noise than usual. Or your computer may start heating up. On the other hand, Bitdefender uses cloud-based technology for heavy scans, so they won’t get in your way. You can rest assured that Bitdefender won't hobble your system’s performance.
User Interface
Windows Defender features a straightforward and user-friendly interface. The home dashboard hosts all seven features, including:
Bitdefender’s layout is very similar to Windows, but with a few modifications. All its products boast a streamlined interface and well-organized features. The main window sports two panels: a left and a right panel. The left panel boasts six features: Dashboard, Privacy, Protection, Utilities, Notifications, and Settings. While the left panel boasts the feature functionalities.
FAQs
Should you replace Windows Defender with a premium antivirus suite that costs money?
Windows Defender is an in-built antivirus that offers decent protection. If you don’t have any sensitive information and you follow the best cybersecurity practices, then Windows Defender is enough to protect your device. But the protection it provides is nowhere near that offered by premium antivirus software, namely Bitdefender.
How is Bitdefender better than Windows Defender?
Bitdefender is a third-party premium antivirus suite that offers the best security solution against offline and online threats and safeguards your privacy. It offers a wide array of features, including an award-winning engine and minimal impact on system performance, and a few of its products are also compatible with other OS such as macOS, iOS, and Android.
Can you run Windows Defender and Bitdefender together on your PC?
Unfortunately, when you install Bitdefender or any other third-party antivirus solution, its real-time protection will automatically turn off Windows Defender. By default, all of Bitdefender’s products come with real-time protection. And if you are using an operating system other than Windows, then Bitdefender Total Security and Bitdefender Family Pack will be ideal choices for you to keep your devices safe and secure.
Visit: Bitdefender Central login Central.bitdefender.com Bitdefender Sign in Bitdefender.com/activate
Source: https://centralbitdefenderdotcom.wordpress.com/2023/04/08/windows-defender-or-bitdefender-how-to-choose-the-best/
#bitdefender central login#central.bitdefender.com#bitdefender login#bitdefender sign in#bitdefender.com/activate
0 notes
Text
Download Avast Antivirus For Windows 10 64 Bit

Avast Antivirus Free Download For Windows 10 64 Bit With Key Offline
Avast Win 10 64 Bit
Avast 64 Bit Free Download
Avast Antivirus Free Download For Windows 7
Avast Free Antivirus Download
Depending on what you do on the web, a secure web browser is often necessary. Enter Avast Secure Browser, with its collection of tools and features that focus on privacy and security.
How to install Avast Antivirus on Windows 10 To start using Avast, just follow these easy steps: 1 Download the installer by clicking here. 2 Right-click the installer and click “run as administrator”. AVG AntiVirus is perfect for Windows 10 AVG AntiVirus FREE gives you essential protection for your Windows 10 PC, stopping viruses, spyware and other malware. Fully loaded and compatible with Windows 10, it's antivirus.
This Chromium-based browser doesn't look too different from a basic Google Chrome installation, but it does include a few tools and plug-ins exclusively from AVAST that can help improve privacy while browsing the web.
The browser implements a few different features for different tasks including banking mode, built-in ad blocking, a video downloader and some anti-phishing and anti-tracking tools. It's also a default setting inside of the program to disguise the browser user-agent to prevent targeted attacks.
A stealth mode included also helps security by performing HTTPS encryption checks so that the security between you and the web site is guaranteed. Avast Secure Browser also has a password manager and support for VPN connections.

All in all, Avast Secure Browser is another Chromium-based browser that's been tweaked by the antivirus creator with a bit more focus on security and privacy.
Features and highlights
Ad Block: A content filter that comes with the EasyList
Bank Mode: A browsing mode that is designed to protect the user against hijacked networks
Passwords: A password manager and form auto-filler
Video Downloader: A plug-in that offers to download videos being watched by the user on selected websites
Anti-tracking and anti-fingerprinting: Prevents the collection of information about the user's computer or browsing history
Anti-Phishing: Analyzes internet traffic for phishing attempts before malicious software is executed
Avast Secure Browser 87.1 on 32-bit and 64-bit PCs
This download is licensed as freeware for the Windows (32-bit and 64-bit) operating system on a laptop or desktop PC from internet browsers without restrictions. Avast Secure Browser 87.1 is available to all software users as a free download for Windows.
Filed under:
Avast Secure Browser Download
Freeware Internet Browsers
Secure Browsing Software
Avast Antivirus 2020 Free Download Latest Version for Windows. It’s a completely online installer standalone setup of a large Antivirus 2020 Free Download for supported version of Windows Mac.
Avast Antivirus 2020 Free Download:
Softwaresfinder this top of the range avast antivirus is not only just like the others because it blocks all webcam-hacking, and stops ransomware before it starts.
It protects your PC, home network, and password again zero-second threat with smart cloud-based detection.
It updates your apps automatically and shreds your data permanently once you say so. That’s why you’ve never seen protection like this before. You’ll also download Avast Antivirus Free Download 2020.
A vast Antivirus 2020 free download latest versions.
Keep spies and snoop off your webcam Can hacker really hijack your webcam. Yes thus far. Webcam Shield makes anything and anyone gets your permission before they’re going to use it so nobody takes a peek UN less you say so. You’ll even disable your camera permanently and enable it against. Go on, do your happy dance nobody watching. You’ll also download Avast Antivirus Free Download 2020.Key
Features of Avast Antivirus 2020 Free Download:
Firewall
Keep hackers on the opposite side of the wall with this essential security feature that monitors and controls what goes in and out of your computer.
Avast Antivirus Free Download For Windows 10 64 Bit With Key Offline
Anti-spam
Avast Win 10 64 Bit
Dodge spam and other malicious content, so you’ll be able to specialize in the e-mail that actually matters.
Real Site
Protect yourself from hackers who plan to hijack your D N S, redirect you to fake sites and steal your banking details.
WiFi Inspector
Avast 64 Bit Free Download
Automatically detect weakness in your home Wi-Fi and strangers piggybacking on your network.
Technical Setup Details for Avast Antivirus 2020:
Software Full Name: Avast Antivirus 2020 Free Download
Download File Name: Avast_free_Antivirus-setup_online .ex
Application Type: Offline Installer / Full Standalone Setup
Download File Size: 228 KB
Compatibility Architecture: 64 Bit (x 64) 32 Bit (x 86)
Developers: Avast Free Download
System Requirements for Avast Antivirus 2020:
Operating System: Windows 10, 8.1, 8, 7, Vista, or X P S P 3*, Mac
Memory: 1 GB RAM
Disk: 2 GB of hard disk space.
Both 32 bit and 64-bit version, excluding Starter and RT edition.
Avast Antivirus Free Download For Windows 7
How to download Avast Antivirus 2020?
Avast Free Antivirus Download
Click the download button below and you will be redirected to the next page. On the next page, you need to wait for 10 seconds to get a download button. Downloads. If you have any software requests, you can post it by Free Download. Enjoy and bookmark our website, visit us daily for the latest and quality Click on the download now button to start your download.

1 note
·
View note
Text
Serial Key Bitdefender Total Security 2018

Using Bitdefender Total Security 2018 License Key enhanced, and detailed kind of the security collection computers is running Windows Os’s. This program includes antivirus, junk e-mail filter, firewall, combined with the parental control module. Download Bitdefender Total Security 2018 activation key for free and enjoy full protection for whole one year. After getting the Bitdefender Total Security 2018 serial number you have to activate the software with administrator privileges. You will not find best Anti-Malware Protection software in.
Bitdefender Free
Key Bitdefender Total Security 2019
Bitdefender Internet Security 2018

Bitdefender Total Security 2018 Crack + Activation Code Till 2045 Free Download
Bitdefender Total Security 2018 Crack With License Key
Bitdefender Total Security 2018 Crack with Activation Code is an award winning antivirus and Internet security package that is equipped with powerful tools to keep your system safe in every way imaginable. Using a clean and simple interface, Bitdefender Total Security 2018 Serial Key offers high levels of customization or beginners can make use of the AutoPilot feature which automatically adjusts to a balanced protection setting.
Capabilities include antivirus and anti-malware detection and removal engines in real time, phishing protection, a spamguard, a system performance optimizer, file encryption, multiple scan levels, parental controls, two way firewall, identity theft and social networking protection. Bitdefender Total Security 2018 License Key new features include Safepay, a secure virtualized browser (complete with a virtual keyboard and Wi-Fi hotspot protection) which protects your payment data while shopping or banking online, the USB Immunizer which immunizes any flash drives from virus infections when connected to your computer, and Bitdefender Total Security 2018 Activation Code Anti-Theft which protects your personal information on lost or stolen devices by locating, wiping or locking your device remotely.
Bitdefender Total Security 2018 Key Features:
Movies, Work, Games Profiles.
File encryption
Multiple scan levels
Parental controls
Two-way Firewall
Identity theft
Antivirus and anti-malware Detection
Removal engines in real time
Phishing Protection
A spamguard
A system performance optimizer
Social networking security
One Step Payments.
Secure Browsing with Privacy Protection.
Secure Online Storage. Security Report.
Startup Optimizer. Parental Control.
Quick Vulnerability Scanner.
Antivirus and Anti-spyware.
Bitdefender OneClick
Cloud Antispam.
Device Anti-Theft.
OneClick Optimizer. File Encryption.
Safe Online Banking and Shopping.
Two Way Firewall.
What’s New Bitdefender Total Security 2018 Crack?
Bitdefender Free
Advanced Danger protection: Bitdefender Total Security 2018 Crack uses a way this is innovative behavioral detection to display energetic apps vigorously. The instant it acknowledges whatever at all suspicious, required motion this is immediate save you infections.
Webcam protection: shield your privateness and guard against webcam leaks. Webcam protection notifies you each time software program attempts to get entry to your webcam and helps you to block get entry to that is unauthorized.
Secure files: with secure files, you may prevent unauthorized adjustments on your most files which might be vital. You only add folders to the watch listing, and Bitdefender guards the documents kept in all of them in opposition to ransomware and different styles of malware. Handiest applications that we explicitly self-assurance are allowed get right of entry to your very own secure documents.
Bitdefender Total Security 2018 Activation Code:
QZA3WSX
C5DE4SX
W3ZASX4
EDC5RF6
4EDC5RF
6VTG7BY
VTG7BY8
UN9JMNU
H8UNJI9
MN8UHBY
G7TVF6R
System Requirements:
Windows 2000/ XP/ Vista/ 7/ 8/ 8.1/ 10 (32-bit or 64-bit – all editions)
Memory: 1GB
Hard Disk Space: 1.5GB
Processor: Intel Dual Core 1.6 GHz or faster
How to install & Activate Bitdefender Total Security 2018 Crack?
Download Bitdefender Total Security 2018 Crack Free from links shared below.
Extract .rar download file.
Install the program as installed others software.
Now extract the Crack file from download folder after completion of installation process.
Run Bitdefender Total Security 2018 Full Version Free Download as administrator.
Or use Bitdefender Total Security 2018 Activation Code for manual activation.
Enjoy using Bitdefender Total Security 2018 Full Version free for lifetime.
Bitdefender Total Security 2018 Crack
From Links Given Below…
Bitdefender Total Security 2018 Activation Code with Crack
Bitdefender Total Security 2018 Activation Code with Crack is a honor winning antivirus and Internet security bundle that is furnished with capable apparatuses to guard your framework all around possible. Utilizing a perfect and straightforward interface, Bitdefender offers large amounts of customization or apprentices can make utilization of the AutoPilot include which consequently conforms to an adjusted insurance setting.
Bitdefender Total Security 2018 Key Features :
Continuous insurance for Windows, Mac OS and Android
Brought together administration for any PC and cell phones
Wi-Fi Security Advisor: constantly secure in a hurry
Completely recure and continuous execution – no lulls
Single-touch security: finish programmed insurance
Security insurance over any stages far and wide
Parental Advisor: family-arranged assurance
Hostile to robbery and information insurance apparatuses
Exhaustive support, all day, every day.
Bitdefender Total Security 2018.
Bitdefender 2018 key: NN3DLQA (590 DAYS)
KEYGEN: S7DH3BG (356 DAYS)
SERIAL: 2WBCNEL (780 DAYS)
bitdefender key: SLLQZX8 (429 DAYS)
KEYGEN: WZ4RPJQ (201 DAYS)
Key Bitdefender Total Security 2019
LICENSE KEY: Q1NDMLI (897 DAYS)
Bitdefender Total Security Download from Link Given Below :
DOWNLOAD NOW
Download Here!
Bitdefender Internet Security 2018
Related Posts

1 note
·
View note
Text
HOW DO I PROTECT MY OFFICE 365 OR ORGANIZATION MICROSOFT 365 DATA?

You can protect or secure your office 365 data with top security features recommendation.
The following are the top 10 security features recommendation you can adopt to protect or secure your Office 365 data:
1. Raise the level of protection against malware in mail.
To increase the level of malware protection in email, complete the following steps:
Go to the protection page or portal of Office Online and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
Click Anti-Malware.
Double-click the default policy to edit this company-wide policy.
Click Settings.
Under Common Attachment Types Filter, Click On.
Note: The file types that are blocked are listed in the window directly below this control. You can add or delete file types later, if needed.
Click Save.
2. Protect against ransomware.
You can protect against ransomware by creating one or more mail flow rules to block file extensions that are commonly used for ransomware.
You can also protect against ransomware by warning users who receive these attachments in email.
The following mail flow rules can be created:
Warn users before opening Office file attachments that include macros.
Block file types that could contain ransomware or other malicious code.
To create a mail transport rule, complete the following steps:
Go to the Exchange admin center.
In the mail flow category, click rules.
Click +, and then Create a new rule.
Click **** at the bottom of the dialog box to see the full set of options.
Apply the settings to warn users before opening Office file attachments that include macros and block file types that could contain ransomware or other malicious code.
Click Save.
3. Stop auto-forwarding for email.
If hackers gain access to a user's mailbox, they can exfiltrate mail by configuring the mailbox to automatically forward email and users may not be aware of this change.
To prevent this from happening you can configure a mail flow or transport rule.
Go to the Exchange admin center.
In the mail flow category, click rules.
Click +, and then Create a new rule.
Click More options at the bottom of the dialog box to see the full set of options.
Apply the settings to reject Auto-Forward emails to external domains.
Click Save.
4. Use Office Message Encryption.
Office 365 Message Encryption works with Outlook, Yahoo!, Gmail, and other email services. Email message encryption helps ensure that only intended recipients can view message content.
Office Message Encryption provides two protection options when sending mail:
Do not forward.
Encrypt.
You might have to configure additional options that apply a label to email, such as Confidential.
To send protected email with encryption in Outlook For PC:
In Outlook for PC, click Options tab.
Then click Permissions.
To send protected email with encryption in Outlook account:
In Outlook account, click Protect tab. The default protection is Do not forward.
To change this to encrypt, click Change Permissions.
Click Encrypt.
To receive encrypted email
The recipient with Outlook 2013 or 2016, or 2019 and a Microsoft email account will see an alert about the item's restricted permissions in the Reading pane. After opening the message, the recipient can view the message just like any other.
The recipient using another email client or email account, such as Gmail or Yahoo will see a link that lets them either sign in to read the email message or request a one-time passcode to view the message in a web browser. If users aren't receiving the email, have them check their Spam or Junk folder.
5. Protect your email from phishing attacks.
Anti-phishing protection, a part of Microsoft Defender for Office 365, can help protect your organization from malicious impersonation-based phishing attacks and other phishing attacks. You need this if you've configured one or more custom domains for your Microsoft 365 environment.
To create an anti-phishing policy in Defender for Office 365, complete the following steps:
Go to the protection page or portal of Office Online.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
On the Policy page, click Anti-phishing.
On the Anti-phishing page, click + Create. A wizard launches that guides you through defining your anti-phishing policy.
Specify the name, description, and settings for your policy.
After you have reviewed your settings, click Create this policy or Save.
6. Protect against malicious attachments and files with Safe Attachments.
Microsoft Defender for Office 365 includes Safe Attachment protection, but this protection is not turned on by default. We recommend that you create a new rule to begin using this protection.
To create a Safe attachment policy, complete the following steps:
Go to the protection page or portal of Office Online and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
On the Policy page, click Safe Attachments.
On the Safe attachments page, apply this protection broadly by clicking the Turn on ATP for SharePoint, OneDrive, and Microsoft Teams check box.
Click + to create a new policy.
Apply the settings you want.
After you have reviewed your settings, click Create this policy or Save.
7. Protect against phishing attacks with Safe Links.
Safe Links, part of Microsoft Defender for Office 365, can help protect your organization by providing time-of-click verification of web addresses (URLs) in email messages and Office documents.
To get to Safe Links, complete the following steps:
Go to the protection page or portal of Office Online and sign in with your admin account credentials.
In the Security & Compliance Center, in the left navigation pane, under Threat management, click Policy.
On the Policy page, click Safe Links.
To modify the default policy:
On the Safe links page, under Policies that apply to the entire organization, double-click the Default policy.
Under Settings that apply to content across Office 365, enter a URL to be blocked, such as example.com, and click +.
Under Settings that apply to content except email, click Office 365 applications, Do not track when users click safe links, and Do not let users click through safe links to original URL.
Click Save.
To create a new policy targeted to all recipients in your domain:
On the Safe links page, under Policies that apply to specific recipients, click + to create a new policy.
Apply the settings you want.
Click Save.
8. Set up multi-factor authentication.
Using multi-factor authentication is one of the easiest and most effective ways to increase the security of your organization. It's easier than it sounds - when you log in, multi-factor authentication means you'll type a code from your phone to get access to Microsoft 365. This can prevent hackers from taking over if they know your password. Multi-factor authentication is also called 2-step verification.
To set up multi-factor authentication, you turn on Security defaults. You enable or disable security defaults from the Properties pane for Azure Active Directory (Azure AD) in the Azure portal.
Sign in to the Microsoft 365 admin center with your global admin credentials.
In the left navigation pane, click Show All.
Under Admin centers, click Azure Active Directory.
In the Azure Active Directory admin center, click Azure Active Directory.
Click Properties.
At the bottom of the page, click Manage Security defaults.
Click Yes to enable security defaults or No to disable security defaults.
Then click Save.
After you set up multi-factor authentication for your organization, your users will be required to set up two-step verification on their devices.
Note: You can set up multi-factor authentication in both Microsoft 365 Business Standard and Microsoft 365 Business Premium.
9. Train your users.
Microsoft recommends that you train your users on how to take the following actions:
Using strong passwords.
Protecting devices.
Enabling security features on Windows 10 and Mac PCs
10. Use dedicated admin accounts.
The administrative accounts are valuable targets for hackers and cyber criminals and these accounts include elevated privileges.
Admins should have a separate user account for regular, non-administrative use and only use their administrative account when necessary to complete a task associated with their job function.
They must commit to the following recommendations:
Be sure admin accounts are also set up for multi-factor authentication.
Before using admin accounts, close out all unrelated browser sessions and apps, including personal email accounts.
After completing admin tasks, be sure to log out of the browser session.
Expert advice: To start with, you can check your Microsoft 365 Secure Score in the Microsoft 365 security center. From a centralized dashboard, you can monitor and improve the security for your Microsoft 365 identities, data, apps, devices, and infrastructure. You are given points for configuring recommended security features, performing security-related tasks (such as viewing reports), or addressing recommendations with a third-party application or software.
1 note
·
View note
Text
Bitdefender Total Security 2015 Free License Key

Bitdefender Total Security Free Trial
Bitdefender Total Security 2015 Free License Key Download
Bitdefender Total Security 2015 Free License Key Activation
Go to Bitdefender Central and sign in. If you don’t have an account, choose to create one. Click on the My Subscriptions panel, located on the left side of the window. Click the Activate a service with code button. Input the code from the e-mail received after purchasing Bitdefender. NOTE: The email is received only upon purchase. Bitdefender Total Security 2015 free license key is the ultimate anti-malware software. It builds on technology awarded Best Protection and Best Performance to defend your device with just one click. Lock confidential files in an encrypted vault and use Bitdefender Safebox to securely stores photos and videos online.
Even though there are still a few weeks left before 2015, many software developers and vendors have started launching their 2015 version software. The award-winning security solution provider, BitDefender is also catching the hot wave by rolling out its BitDefender Total Security 2015. Like its other products, BitDefender Antivirus 2015 and BitDefender Internet Security 2015 provide an advanced proactive protection against viruses and spyware in real time without slow down your PC performance.
BitDefender Total Security 2015 is the ultimate anti-malware software that builds from advanced protection technology to defend PC with just one click. Bitdefender Total Security 2015 provides protection anti-virus, anti-malware, anti-spam, tune-up, online banking protection, a 2-way firewall, parental control, online backup and anti-theft provision. In addition, it’s also can lock confidential files in an encrypted vault, Bitdefender Safebox to securely stores photos and videos online, and Device Anti-Theft features helps recover PC in case of loss or theft.
If you would like to have BitDefender Total Security 2015 installed on your PC, now you can get the free 6 months of Bitdefender Total Security 2015.
BitDefender Total Security 2015 normally costs $89.95 for one year license key up to 3 PCs. To grab a free copy of BitDefender Total Security 2015, visit the following URL: http://www.bitdefender.de/media/html/chip2015/
Fill in the email address, and then click the “KOSTENLOSE LIZENZ SICHERN” button.
An email confirmation containing the download link and license key for BitDefender Total Security 2015 will be received.
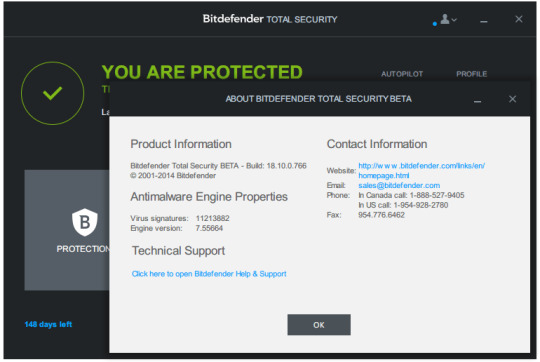
Note: If the e-mail hasn’t arrived within 30 minutes, please check your spam, junk, or promotions mail folder to locate it.
Download BitDefender Total Security 2015 setup installer:
BitDefender Total Security 2015 32 Bit: bitdefender_ts_18_32b.exe
BitDefender Total Security 2015 64 Bit: bitdefender_ts_18_64b.exe
BitDefender Total Security 2015 supports Windows Vista, Windows 7, Windows 8, and Windows 8.1 operating system.
Related Posts
Recent Articles
Tags
BitDefender Total Security 2020 Crack + Activation Code full. free download
BitDefender Total Security Crack provides the best security options to any operating system. The program offers a large number of Security options. It provides a Firewall and best virus protection. Bitdefender total security Crack enables real-time protection for users. It checks the internet security regularly; when you open a web browser, it turns on automatically. It automatically finds errors and fixes them. It stops those sites automatically that have a trojan, viruses, and hacking materials. BitDefender Total Security Keygen allows you to speed up your computer system, operating system, browser, and analyze your hard-disk. When this application is mounted on your computer, it scans your Device automatically, like other antivirus apps.
BitDefender Total Security 2020 Crack provides layered protection to secure your files, images, and videos, including ransomware and malware from all known and emerging threats. You can also test security packages for terminals with Bitdefender Antivirus Total Protection. The privacy of your data is protected by phishing. This also protects your passwords and the number of your bank cards. This offers tools for neighborhood risk management. This app investigates the suspicious behavior of the group. It blocks other attacks as well. The built-in firewall manages the linked network.

BitDefender Total Security 2020 Crack + Activation Code
Bitdefender total security Serial Key has immense intelligence performs to stop all kind of threats. It checks your apps regularly and fixes all errors of your apps. Bitdefender Provides both of methods to use it Manually and Automatically. It Gives real protection to your Digital Computer. It would forever be able to keep it updated. Bitdefender Crack Allows to Protect your data for your office and personal use. Besides, It is the most effective technology in the Universe to protects Your information.
BitDefender Total Security Activation Codeoffers award-winning security information and threats to people, businesses, and infrastructure, networks, and cloud services. Today, Bitdefender is also the option provider in more than 38% of global security solutions. Bitdefender is also awarded groundbreaking innovations for what we do best: Secure your digital life with an intuitive and quick device output protection solution. It provides tools for the protection of software, file security, and protection of the Internet. In addition to the network, the program protects your device data. The autopilot mode is available as well if you can use it at Bitdefender.
BitDefender Total Security Key Features:
Fast And Efficient
Bitdefender total security is one of the quickest and Efficient Software compare to others. It scans the whole Pc in a few moments.
Most Securable
Bitdefender is one of the best securable software in the world. It is the best software For Security purpose compared to others
Best security Options
BitDefender Gives us many Security Options like two-step verification, fingerprint security, Pattern, and faces unlock. To protect and analyze your information, it provides the best security options.
User-Friendly Interface
Bitdefender total security crack presents Good User-friendly interface to its users
Protect your Data in one click
Options are so easy. Even a beginner uses it efficiently. The user can easily understand the interface. And perform tasks in just one click
Works with any operating system
Bitdefender Total Security Free Trial
It Can work with any operating System Like Windows XP, Linux, and Vista. Also, Compactable For Android and iOS
Speed up Your Device
With this software, You can Boost your Devices in some seconds
BitDefender Total Security 2020 Activation Code:
Bitdefender Total Security 2015 Free License Key Download
4F5GP-55FFV-KKY65-78T88-GG6HW
4F5G6-H7G56-H7J81-G56H7-FG56C
What’s New in BitDefender Total Security 2020 Crack?
Improved Internet protection on Windows PCs against all attacks.
This tool is intended to protect you in real-time against stubborn threats.
Layered ransomware protection for the safety of your files.
This is the primary weapon for defense from external and internal threats.
It has cloud-based security services that guarantee the cleanliness of your system.
It eliminates new and established risks, malware, trojans, and other hazardous files.
Incredible network threat detection blocking sophisticated attacks.
It also offers security in real-time when browsing the Internet.
It tests URLs and alerts you if the website does not contain anything right.
Besides, It provides Secure and fast VPN.
Internet browsing experience is anonymous and free.
Security of children online with advanced parental control.
Minimum performance effects.
Bug Fixes
Now compatible For Windows 10
Auto Protection
System Requirements:
CPU: Intel Core 2 Duo 2 GHz
RAM: 2 GB.
Hard Disk: 2.8 GB of free space.
OperatingSystem: Windows 7/8.1/8/10
How to Install BitDefender Total Security Crack?
Bitdefender Total Security 2015 Free License Key Activation
Download BitDefender Crack Form bellow Button
After Download Click on install
After Installation put Keys in Key Bar
All Done
Enjoy
Marc
BitDefender Total Security 2020 Crack
5
BitDefender Total Security
Mac & Windows
Security

1 note
·
View note
Text
best buy install trend micro purchased
best buy install trend micro purchased-If you are a home-based user and looking for an ideal www.trendmicro.com/bestbuypc Trend Micro antivirus product then you can select any one of them depending on your need.
How to best buy install trend micro purchased?
First of all, you need to follow my install already purchased TrendMicro security on your new pc: best buy install trend micro purchased-
If you want to install Trend Micro Antivirus on your system then first you will be forced to buy an idea from the official web site.
Your Trend Micro requires completely different types of plans and offers for you, out of which you will be able to make a choice from viewing the services as you wish.
And once you are specifically set up that matches your needs, choose the additional option and click on it which can take you to the Gateway page for on-line payment.
Now on this page, fill all the required information so that you can pay the number shown on the screen.
After that as soon as you pay, antivirus is going to be activated in your name and you will get all the invoices in your mail-id.
And then, just click on download/install and at intervals find trend micro antivirus installed on your computer in minutes.
You are now in your current, your system protected by Trend Micro with the most recent malware and antivirus encryption.
Features for best buy install trend micro purchased :
It provides advanced protection and privacy, therefore, you’ll be able to relish your digital life safely.
It helps to defend you from fraud, additionally to safeguarding against spam, viruses, and malware.
Protect your e-mail from dangerous links in e-mail and instant messages.
Simple control screen choices and clear, easy-to-understand, invariably current security standing reports.
It provides the most recent in anti-ransomware technology, thus your files will not be controlled, hostage.
Fix common issues, and obtain everything running at high speed.
It allows youngsters to explore online safely
1 note
·
View note
Text
What is Cryptojacking
Cryptojacking is the unauthorized use of a computer, tablet, mobile phone, or connected home device by cybercriminals to mine for cryptocurrency. Cryptojacking is an attack where the attacker runs cryptocurrency-mining software on your hardware without your permission. The attacker keeps the cryptocurrency and sells it for a profit, and you get stuck with high CPU usage and a hefty electricity bill.
While Bitcoin is the most widely known cryptocurrency, cryptojacking attacks usually involve mining other cryptocurrencies. Monero is particularly common, as it’s designed so people can mine it on average PCs. Monero also has anonymity features, which means it’s difficult to track where the attacker ultimately sends the Monero they mine on their victims’ hardware. Monero is an “altcoin,” which means a non-Bitcoin cryptocurrency...find out more at - Howtogeek.
Understanding Cryptojacking
Cryptojacking has become an increasingly popular way for bad actors to extract money from targets in the form of cryptocurrency. Widely publicized hacks such as the WannaCry worm, which affected systems on several continents in May 2017, encrypted victims' files and demanded cryptocurrency ransoms – bitcoin, in the case of WannaCry – to decrypt them.
Cryptojacking takes a different approach, harnessing victims' machines to "mine": perform the computations necessary to update cryptocurrencies' blockchains, creating new tokens and generating fees in the process. These new tokens and fees are deposited to wallets owned by the attacker, while the costs of mining – electricity and wear and tear to computers – are borne by the victim...get more to know at - Investopedia.
Why cryptojacking is popular
No one knows for certain how much cryptocurrency is mined through cryptojacking, but there’s no question that the practice is rampant. Browser-based cryptojacking grew fast at first, but seems to be tapering off, likely because of cryptocurrency volatility.
In November 2017, Adguard reported a 31 percent growth rate for in-browser cryptojacking. Its research found 33,000 websites running cryptomining scripts. Adguard estimated that those site had a billion combined monthly visitors.
In February 2018, Bad Packets Report found 34,474 sites running Coinhive, the most popular JavaScript miner that is also used for legitimate cryptomining activity. In July 2018, Check Point Software Technologies reported that four of the top ten malware it has found are crypto miners, including the top two: Coinhive and Cryptoloot.
However, Positive Technology's Cybersecurity Threatscape Q1 2019 report shows that cryptomining now accounts for only 7% of all attacks, down from 23% in early 2018. The report suggests that cybercriminals have shifted more to ransomware, which is seen as more profitable...read more at - Csoonline.
How cryptojacking works
Coin mining on your own can be a long, costly endeavor. Elevated electricity bills and expensive computer equipment are major investments and key challenges to coin mining. The more devices you have working for you, the faster you can “mine” coins. Because of the time and resources that go into coin mining, cryptojacking is attractive to cybercriminals.
There are a few ways cryptojacking can occur. One of the more popular ways is to use malicious emails that can install cryptomining code on a computer. This is done through phishing tactics. The victim receives a seemingly harmless email with a link or an attachment. Upon clicking on the link or downloading the attachment, it runs a code that downloads the cryptomining script on the computer. The script then works in the background without the victim’s knowledge....visit -Norton to know more.
What crypto jacking shows is that someone doesn’t even need to own cryptocurrency to be a victim. Go to -https://duocircle.com/ to protect yourself against these kinds of crypto jacking attacks
1 note
·
View note
Text
How to Protect Yourself Against Ransomware
Ransomware is a type of malicious software, also known as malware. It encrypts a victim’s data until the attacker is paid a predetermined ransom. In this article, we will talk about how to protect yourself against ransomware.
How does ransomware work?
Ransomware identifies the drives on an infected system and begins to encrypt the files within each drive. Ransomware generally adds an extension to the encrypted files, such as .aaa, .micro, .encrypted, .ttt, .xyz, .zzz, .locky, .crypt, .cryptolocker, .vault, or .petya, to show that the files have been encrypted—the file extension used is unique to the ransomware type.
Once the ransomware has completed file encryption, it creates and displays a file or files containing instructions on how the victim can pay the ransom. If the victim pays the ransom, the threat actor may provide a cryptographic key that the victim can use to unlock the files, making them accessible.

How is ransomware delivered?
Ransomware is commonly delivered through phishing emails or via “drive-by downloads.” Phishing emails often appear as though they have been sent from a legitimate organization or someone known to the victim and entice the user to click on a malicious link or open a malicious attachment. A “drive-by download” is a program that is automatically downloaded from the internet without the user’s consent or often without their knowledge. It is possible the malicious code may run after download, without user interaction. After the malicious code has been run, the computer becomes infected with ransomware...get more info at - CISA.
Create backups of your data
In the event that a hacker successfully hijacks your computer, you could rescue yourself with a backup of your data stored somewhere, like on a physical hard drive. That way, if a hacker locked down your computer, you could simply erase all the data from the machine and restore it from the backup.
In general, you should be creating a copy of your data in the first place, in case your computer fails or is lost. To be extra safe from hackers, after backing up your data onto an external drive, unplug the drive from the computer and put it away...to know more, visit - nytimes.

Keep your system up to date
If you are running Windows XP or Vista, you should immediately update your system to Windows 10 or buy a new computer. As we warned back in 2014, Microsoft is no longer supporting these ancient versions of Windows and continuing to use them makes you a prime target for cyber-attacks. And even an entry model $500 computer that will be far more powerful than your current XP one.
For those using Windows 7 and newer, make sure that you have Automatic Updates enabled so new security patches are installed as soon as they are available. These versions of Windows had already been patched by Microsoft to specifically prevent these types of ransomware attacks...get more info at - techlicious.
Scan And Filter Emails Before They Reach Your Users
The easiest way to stop staff clicking on a ransomware link in an email is for the email never to arrive in their inbox. This means using content scanning and email filtering, which ought to take care of many phishing and ransomware scams before they actually reach staff.
Think Very Long And Hard Before You Pay A Ransom
Ransomware crooks have found their way through your defences and now every PC across the business is encrypted. You could restore from backups, but it will take days and the criminals only want a few thousand dollars. Time to pay up?
For some, that may be the obvious conclusion. If the attackers only want a relatively small amount then it might, in the short term, make business sense to pay up because it means the business can be up and running again quickly. However there are reasons why you might not want to pay...visit - ZDNet to know more.
Threat intelligence
While most cybersecurity organizations continue to focus their gaze internally, the only way to move from reactive to proactive is through intelligence. Cybersecurity professionals who understand threat trends and the landscape, which includes adversaries, tactics, techniques, and procedures, are empowered to capitalize on such knowledge to prevent attacks.

Automation
Organizations are overrun with massive amounts of data, information, and intelligence. Considering the skills gap that is still challenging the industry, there is rarely enough time in the day to adequately address all critical or high-level security events, let alone the moderate and low risks. Only through automation, wherein machines capitalize on high-fidelity intelligence to take actions without human intervention, can cyber defenders have the time needed to focus on the biggest-impact security matters...this and more at - Dark Reading.
Final Words
Use these tips to keep your Company’s sensitive information safe and stop a ransomware attack before it starts. Use a good email security service that will keep you from clicking on a phishing link.
1 note
·
View note
Text
McAfee total protection 2020 reviews
McAfee total protection 2020 reviews - McAfee has three consumer security products – but which is best, and how do they compare to rivals.
Where to seek out Mcafee Activation Code?
The Mcafee security package is simple to setup & install at www.mcafee.com/activate. Simply find a 25-character alpha-numeric code that is written on the backside of the retail card. Here may be a sample Product Key to let you understand:
xxxxx-xxxxx-xxxxx-xxxxx-xxxxx
McAfee 2020 Antivirus solutions review:
Installing McAfee Total Protection was a long nightmare during our last review, but this time, fortunately, it was very different. There were no error messages, no delays, no hassles of any kind: the setup tool just downloaded the full Total Protection package, installed it on our hard drive and let us know when it was done. Simple.
The installation did have one unusual aspect. We installed Total Protection on a system already equipped with Kaspersky Security Cloud installed, just to see what it would do. Most antivirus packages will ask you to remove competing for software to avoid conflicts, but McAfee's installer said nothing at all.
Does this matter?
It probably depends on the user. If McAfee might conflict with other security software, enabling newbies to run two antivirus apps side by side is likely to be a bad idea. But if you're an expert, confident you can reconfigure one antivirus to reduce the chance of problems, and sure you can cope with whatever issues arise, you might see this as an advantage.
After the installation was complete, Total Protection prompted us to reboot. We did, and again there were no hassles or unexpected events – no sign of change other than a shiny new McAfee icon in our system tray.
Interface :
The McAfee Total Protection interface grabs far more valuable screen real-estate than most, yet does almost nothing with it.
The expansive opening screen contains a big green tick to show your security status, for instance but has barely any other useful content.
The rest of the console is largely wasted with a button to help you protect other devices, pointless system information ('we are protecting 309 apps/connections/tasks'; is that good, bad? how are you supposed to know?), a button to view a security report, and a large panel recommending that you set up the password manager, or optimize your apps.
These might have some value, but we would much rather have a button to launch a Quick Scan, a line that tells us when our definitions were last updated, or something with real practical value.
Clicking a small icon that comprises three dots reveals a more detailed status report of Total Protection's various features, so, for instance, you can confirm that antivirus, the firewall, and the update system are all working correctly. That's the kind of information which should be visible at a glance, rather than hidden, but at least it's only a click away.
It's not obvious, but this status display also doubles as a menu, and for example, clicking the Virus Scan status loads the Scan dialog.
You can also click various tabs at the top of the screen – PC Security, PC Performance, My Privacy – to view separate panels with their own groups of features. These also waste plenty of space, so, for instance, the PC Performance area includes only three useful elements: a couple of buttons and an on/off status indicator. We've seen more features on desktop widgets.
This approach could have some appeal to casual users who might be overwhelmed by lots of buttons or technical information, but more experienced types might become frustrated.
Antivirus:
McAfee Total Protection keeps its antivirus scanning options to a minimum: just a Quick Scan, a Full System Scan and the ability to scan custom items directly from the Explorer right-click menu.
What you don't get is a specific removable drives scan, a custom scan you can define from the interface, or the ability to set up a new scan type or define how it works. For example, Avast's Windows products can be used to set up a scan that checks specific file types in the folders you need, using the scanning technologies and rules you define, and you can then run that scan whenever you like. There's nothing like that here.
Scan times were a little slower than average, although acceptable.
Scan reports are poor, and short on detail. Our first Quick Scan proudly displayed 'Issues: 0' at the top, while also stating 'All issues fixed', 'We wiped out all the threats on your PC' and listing cryptic names of three threats it had removed.
As Total Protection hadn't asked us if it could remove these 'threats', we clicked on the first, 'JTI/Suspect.19661214ca37a5b9d3b', in the hope of finding out exactly what the program had just deleted.
A browser window opened with a lengthy URL including multiple parameters, presumably intended to display a page with more details. But this immediately redirected to the front page of McAfee's Threat Center, with no more information at all.
A 'View Details' button was also less than helpful, telling us the engine had detected three dangerous files, but not what or where they were.
Eventually, we found the details we needed in the Quarantine section, but it really shouldn't take so much effort to locate such fundamental information.
We noticed another oddity in the Details screen suggesting McAfee's Quick Scan checks files only, ignoring processes, critical system files or boot records. If true, that's disappointing; we think checking running processes should be one of the key elements of a Quick Scan.
Protection:
AV-Comparatives' Real-World Protection Test is an intensive benchmark that pits 16 of the world's biggest antivirus engines against the very latest threats. The company runs 10 tests every year, making it a great way to monitor particular vendors over time.
McAfee's most recent test performance was average, with the July-October summary report placing the company in 8th place with a protection rate of 99.4%.
That's a long way behind the leaders – Avira and Symantec blocked 100% of threats – but it's ahead of some big-name competition, including Avast (99.3%), F-Secure (99.3%) and even Kaspersky (99.1%).
The AV-Test Home Windows report for October 2019 broadly matches this picture, with McAfee not at the top of the list, but performing well enough to earn it one of AV-Test's 'Top Product' awards.
We can't begin to compete with the time and resources the big testing labs put into their work, but what we can do is add to their findings with a small test of our own.
We have created a very, very simple ransomware simulator which spiders through a folder tree, reading and encrypting images, audio files, Office documents and more. By running this on a review system, we're aiming to see whether an antivirus can detect undiscovered ransomware by behavior alone, and discover how many files, if any, might be lost before an attack can be stopped.
The results were disappointing, as McAfee Total Protection left our simulator to run to completion and encrypt thousands of files. Other tools typically do much better, with, for instance, Kaspersky Security Cloud Free 2020 not only detecting and killing the simulator but also recovering the very few files our program had managed to encrypt.
However, this result should be interpreted with care. McAfee may have missed our test program, unlike the best of the competition, but we can't be sure why or what that tells us about the security suite overall. What we do know from the lab tests is that McAfee can detect most real-world malware from behavior alone, and that's the most important result.
Firewall:
Total Protection includes a firewall that automatically makes intelligent choices about which programs on your system can access the internet. This is mostly tucked away within the interface, and most users won't ever have to know of its existence.
Experts get access to a wide range of firewall settings, including the ability to open or close specific ports or define custom rules for individual applications. These options are harder to find than we'd like, though, and it took us some time to begin to figure out what was possible.
Even then, we were often puzzled. The firewall has an Intrusion Detection system, for instance, but it's turned off by default, only has two settings (Basic or High) and even the web knowledgebase has no real information on what it does and the consequences of turning it on (or off).
More features:
Total Protection's spam filter wasn't installed by default in our previous review, but this time it set itself up correctly, added an extension to our Outlook setup and began filtering mail.
The performance was excellent, with the filter detecting most spam and not falsely flagging any legitimate emails. But if this doesn't work for you, a wide range of settings enable customizing the protection to suit your needs.
The True Key Password Manager allows for creating and syncing passwords across up to five devices. It's strong on multifactor authentication methods – email, fingerprint, the second device, Windows Hello, more – but not so good in other areas, with no general form-filling abilities and no secure password sharing.
A Vulnerability Scanner is supposed to check for and install missing application updates, but it did nothing for us. We tried two ways of launching it, and in each case, nothing happened; there was no new dialog box, no error message, nothing at all.
Other apparent features of the program are entirely separate tools which you must download and install separately. Clicking ‘Protect Me On The Web’ opens the website for McAfee WebAdvisor, for instance, a browser extension that defends you against malware, malicious sites and more. It's handy, but it's also available for free, and you don't have to buy Total Protection to use it.
The feature list continues in the PC Performance area, where you'll find a couple of speedup options.
App Boost optimizes CPU and me/O priorities for foreground applications to improve performance. This won't make much difference – sometimes it'll have no noticeable effect at all – but the company suggests you could see an 11-14% speed increase in the targeted apps, which, if true, is worth having.
A Web Boost feature sounds promising, but it's just a separate module that stops videos automatically playing on your choice of many popular websites (YouTube, Netflix, Twitch.tv, Skype.com, ClickMeeting.com and many more). It's a reasonable idea, and may well make web browsing a little less annoying (a worthwhile goal all on its own), but it's probably not going to deliver much of a speed boost.
There are multiple minor tools to explore. A QuickClean option removes tracking cookies and temporary files and can be scheduled to run automatically. A Shredder securely deletes confidential files so they can't be undeleted, and a Network Monitor looks for intruders connecting to your Wi-Fi. Experienced users will probably have more powerful freeware tools already, but these are easy to use and convenient to access and add a little extra value to the suite
Final verdict:
McAfee Total Protection has lots of features, but none are outstanding, and they're not always well implemented (the interface isn't great, the vulnerability scanner simply didn't work). It's hard to see why you would choose this package when others are faster, cheaper, more accurate or easier to use.
MCAFEE TOTAL PROTECTION MULTI-DEVICE: McAfee total protection 2020 reviews-
As you might guess from the name, McAfee Total Protection Multi-Device isn't just another Windows-based security tool; it has apps for Android, iOS, and Mac, too.
The standard license covers five devices, too, up from the miserly one you'll get with Total Security Individual.
Turn on auto-renewal for your subscription and US users also get access to McAfee's ID Theft Protection Essentials service, which monitors the web for signs of trouble and helps you recover from any problems it finds.
That's an unusual feature for a security suite, and it doesn't seem to have bumped up the price. Despite its premium functionality, McAfee Total Protection Multi-Device costs a very reasonable $40 for a five device, one-year license, $100 on renewal. Norton 360 with LifeLock Select, another major suite with identity theft protection, is priced at a relatively chunky $100 for year one, $150 after that.
Multi-platform :
McAfee's Android app is a capable product with all the essential technology you'll find in the Windows version, along with a bunch of more mobile-oriented tools.
The free edition of the app includes on-demand scanning, anti-theft (GPS blocking, remote cleaning, more), and useful reports highlighting which apps are using the most data. Of course, there are ads, too.
The paid version removes the ads and throws in browsing protection, device cleaning, an app locker and related Guest Mode (control the apps a guest can see on your device), a battery booster and extra protection from unsecured Wi-Fi networks. It's a quality set of tools, and the current 4.5-star rating on the Google Play store suggests most users are happy.
McAfee's iOS offering also has a free version with basic functions, including wireless scanning, anti-theft, and a media vault to securely store private photos and videos. The paid edition also blocks malicious links via McAfee's Safe Web and protects you from phishing sites and ARP Spoofing (that's low-level network trickery).
McAfee's Mac edition doesn't have as many extras, but still, more than covers the essentials, with antivirus, firewall, and browsing protection.
Identity Theft Protection:
Total Protection has a more interesting and unusual extra in a separate Identity Theft protection service for its US customers.
Cyber Monitoring is one of the service highlights, regularly checking the dark web for personal details including your social security number, email addresses, phone numbers, banking and credit card details, driver's license, passport and more. If any of your information shows up online in a data breach, you'll be alerted.
Other features include Social Media Monitoring which alerts you to risks with the content you're sharing, and an optional Social Security Number trace and Address Change Monitoring service which could warn you of scammers trying to steal and use your personal details.
This is still a relatively basic product. You won't get to see your credit report, for instance, or be warned when your score changes, and there's no monitoring of loan or credit card applications, court or criminal records.
If you've no plans to buy separate identity theft protection, anyway, this won't matter much. Whatever the McAfee service gives you, it'll be better than what you'd have otherwise.
But if you've very specific ideas on what you need, or maybe you're looking for the best possible protection, it's probably wise to go shopping for it separately. Check out McAfee's standalone Identity Theft Protection plans to get an idea of what's available, and what it might cost.
Overall value:
Thinking of buying McAfee Total Protection Individual? Then stop! Unless you're completely sure you'll only ever want to protect a single PC, signing up for McAfee Total Protection Multi-Device makes a lot more sense. It's only fractionally more expensive than Total Protection Individual ($40 in year one, $100 on renewal, as opposed to $35 and $80 respectively), yet covers up to five devices rather than one, and supports Android, iOS and Mac, as well as Windows.
Whether Total Protection Multi-Device is good enough to make you choose McAfee in the first place – well, that's more open to question. Probably not, although McAfee's identity protection service might just win you over.
MCAFEE TOTAL PROTECTION FAMILY: McAfee total protection 2020 reviews-
McAfee Total Protection Family doubles your device allowance to a generous 10, but the price stays much the same. You'll pay $45 in year one, and $120 on renewal.
The upgrade gets you another major benefit in McAfee's Safe Family, a parental controls package for Windows, Android and iOS (beware, it doesn't work on Mac). That's a big deal because this isn't the usual feeble security suite addition; McAfee sells it as a standalone app for $50 a year.
Safe Family's core features are much as you'd expect. You're able to block websites by content type, restrict access to specific apps, or limit device access to particular times of the day.
The package is easy to configure, too. Safe Family uses default settings based on the age of your child, getting you off to a quick start, then you can tweak them further to suit your needs.
Furthermore, it's flexible. You can add multiple schedules to decide exactly when your kids can and can't use their devices. If the content filter doesn't quite suit your needs, you're able to allow or block your chosen websites. And, unusually, Safe Family recognizes that absolute rules don't always work. If your kids need more screen time or want to access a specific site, a Requests messaging system allows them to ask you, and – if you approve – they can benefit right away.
Safe Family does a good job of keeping you up to date on what your kids are doing. As soon as it's set up, you're able to view the apps and websites they're accessing, along with any attempts to break the rules. You can even check the location of your kids' device on a map.
It's far from perfect – we'd like more content filtering categories, for instance, and there's no built-in protection to prevent anyone uninstalling the Windows edition – but Safe Family tramples all over the parental controls tools in most security suites.
If you need a decent parental controls system, and you have lots of devices to protect, McAfee Total Protection Family might be a sensible choice. Its $45 cost in year one is only $10 more than you'll pay for the basic Total Protection Individual, so there's minimal risk. Check out the trial, see how it works for you.
1 note
·
View note
Text
What to Do if You’re Hit by Ransomware
Ransomware attacks usually hit large companies or government systems to make as much money as possible. Any ransomware can cripple your systems and put a total lockdown on them if you are not careful enough.
In this article, we will give you a few pointers if you are ever hit by a ransomware attack.

Disconnect from the Network Immediately
The first step after discovering a computer that is infected by ransomware is isolating it from other systems and getting it off the network to reduce the potential damage.
“Disconnect infected computers from all cables and Wi-Fi,” says Ed Cabrera, chief security officer at enterprise security firm Trend Micro. “Begin the mitigation process as soon as possible.”
This won’t save the infected computer, but it could possibly keep other systems from also getting the infection.
Determine the Scope of the Attack
After getting help, assessing the damage that has been done and understanding the attack is the next priority.
“Determine the scope of the incident, what systems were impacted, the initial attack vector, and whether there are active backdoors deployed,” advises Charles Carmakal, chief technology officer for security firm FireEye Mandiant. “What is the scope of the incident? How many systems have been impacted?”...get more info at - Toolbox.

Find out what kind of ransomware you have
First, you'll need to determine whether you've been hit by encrypting ransomware, screen-locking ransomware or something that's just pretending to be ransomware. See whether you can access files or folders, such as the items on the desktop or in the My Documents folder.
If you can't get past the ransom note you see on your screen, you're likely infected by screen-locking ransomware, which is not so bad. If you see a notice claiming to be from the police, the FBI or the IRS that says you've been caught looking at pornography or filing false taxes and must pay a "fine," that's usually screen-locking ransomware, too.
If you can browse through directories or apps but you can't open your regular office files, movies, photographs or emails, then you have encrypting ransomware, which is far worse.
If you can both navigate the system and read most files, then you're probably seeing something fake that's just trying to scare you into paying. You can ignore the ransom note. Try closing your web browser. If you can't, then hit the Control, Shift and Esc keys at the same time to open Task Manager, choose the Application tab, right click the browser application and select End Task...visit - tom’s guide for more info.

UNDERSTAND WHAT'S CONNECTED TO YOUR NETWORK
PCs and servers might be where your data resides, but they aren't the only devices you have to worry about. Thanks to the office wi-fi, the Internet of Things and working from home, there's now a wide variety of devices connecting to the company network, many of which will lack the kind of built-in security you'd expect from a corporate device. The more devices, the greater the risk that one will offer hackers a backdoor into your network, and then use that access to move through your systems to more lucrative targets than a badly secured printer or a smart vending machine. Also, think about who else has access to your systems: are your suppliers aware of the potential risk of ransomware and other malware?
CHANGE DEFAULT PASSWORDS ACROSS ALL ACCESS POINTS
Clicking on a bad link in an email is probably the best known way of getting infected with malware, but it's far from the only way. Nearly a third of ransomware was distributed via brute force and remote desktop protocol (RDP) attacks, according to research by F-Secure. Brute force attacks are attempts by hackers to access servers and other devices by trying as many passwords as possible, usually with the aid of bots, in the hopes of hitting the jackpot...read more at - zdnet.com

Should you pay the ransom?
Of course, though, ransomware attacks have not dropped to zero. If you’re ever hit with a ransomware attack, you need to consider every possible avenue, one of which being — should you pay the ransom? The majority of companies say they would never consider paying a ransom (66 percent). However, in reality, about 65 percent do end up pay the requested amount.
The current advice is, understandably, to not pay the ransom. This simply creates more of a market for ransomware, encouraging attackers to continue. However, the hackers often ask for a sizable ransom but one that is still much lower than losing the data. They also often offer discounts for quick payment so companies pay without having time to consider all options...get more info at - Techgenix.

Conclusion
Malware and Ransomware are not going away soon and are here to stay. To make sure that your data is safe against these attacks, you will need good malware and ransomware protection service as the last line of defense to protect against phishing. User education is also very important. Always make sure that you look at links and avoid suspicious emails and websites.
1 note
·
View note
Text
4 Strategies to Prevent Ransomware Attacks on PC
Ransomware is a type of malicious software that blocks access to the computer system that it infects and demands a ransom paid to the creator of the malware in order to decrypt the data and remove the lock. Ransomware attacks are becoming increasingly common. In fact, according to the FBI’s Internet Crime Complaint Center, ransomware attacks were up over 100% in 2016 compared with 2015. To get protective measures against cyber ransomware, Check out here.
Ransomware attacks are on the rise and they're one of the biggest concerns for security. If you haven't heard of ransomware before it is a type of malware that restricts access to your files until you pay a ransom. In today's post, I will give you 4 strategies that you can use to prevent ransomware attacks from infecting your PC.
Define the threat.
Ransomware is a type of malicious software (also known as malware) that can be installed on your device without you knowing. Once it's there, ransomware typically uses sophisticated encryption to lock all of the files on your computer and then demand payment in order to decrypt them.
The best way to avoid ransomware is by not downloading software from websites or emails that you don't trust. This is because many times the software has been modified so it will install the ransomware when you run the file. If you think you've been infected, contact a professional immediately!
Establish a baseline and monitor for change.
This strategy is the most time-consuming and complex, but it's also one of the most effective. Establishing a baseline means creating a record of how your computer is normally used. You can do that by recording:
Which files are accessed regularly
When those files are accessed and for how long
What programs are run at specific times
After establishing this baseline, you'll be able to detect any changes that occur on your system as an indicator of potential malware infections or suspicious activity. For example, if new programs start running when they weren't previously being used—a sign that ransomware might be at work—you'll be able to identify them right away instead of being taken by surprise when it happens again later on down the road."
Build a strong cybersecurity culture.
Having a strong cybersecurity culture is more than just having a mission statement or policy. A cybersecurity culture refers to the way you interact with your employees, vendors and customers across all levels of the organization. For example, if you have employees who aren't aware of how important it is for them to do their part in protecting the company from cyberattacks, they may click on malicious links in emails or download infected files that could lead to ransomware attacks.
To create a cybersecurity culture within your company:
Train everyone—from executives down through every level of your business—on what ransomware is and why it's important to keep information secure
Give everyone access to essential software applications so they can safely do their jobs without compromising security
Keep your systems secure and up-to-date.
There are many ways to protect your system from getting infected by ransomware. You can prevent the attack by keeping your system secure and up-to-date.
Think about your backups.
You can also protect yourself from ransomware by backing up your files. This is an essential part of any cybersecurity strategy, but it's especially important for ransomware prevention.
In case of a ransomware attack, backups allow you to restore files without having to pay the ransom. Even if you decide to pay the ransom, backups are still helpful—they'll let you restore files quickly if the hackers refuse to provide the key after receiving payment or release their malware after receiving payment.
Backing up your data isn't just applicable in cases where malicious software has taken over; it's also necessary for preventing other types of cyberattacks and data loss. For example:
You could be attacked through social engineering techniques like phishing emails that ask for sensitive information like passwords or credit card numbers (in this case, backups will help prevent identity theft).
Don't pay ransoms.
Once you realize that you have been hit with a ransomware attack, do not pay the ransom. Ransomware attackers are criminals who want to earn money from unsuspecting victims. Paying a ransomware payment will only make it more likely that you’ll be attacked again in the future.
Ransomware attacks are on the rise and they can be devastating to businesses and individuals alike. The best way to protect yourself against these attacks is to use anti-virus software like Norton Security Premium or ESET Smart Security Premium and create regular backups of your data so that if an attack does occur, your files will be safe and sound regardless of whether or not you paid off the hackers.
Ransomware is a very serious threat, and you should take steps to secure your system against it.
Ransomware is a very serious threat, and you should take steps to secure your system against it.
According to a report by Kaspersky Lab, the number of ransomware attacks increased by 250% in 2017 compared with 2016. This year is likely to see even more ransomware attacks as well—the FBI has said that ransomware attacks are likely to become more common over time. It's not just businesses that need to worry about this cyber threat; anyone who uses a computer can be affected by malware like CryptoLocker or SamSam Ransomware.
So what can you do? The first step is being aware of the risks and vulnerabilities associated with ransomware infections on PCs, as well as knowing how cybercriminals use these tools in their operations.
Conclusion
After reading this article, you should have a better understanding of how to prevent ransomware attacks on your PC. If you're still unsure about any of these steps, then we recommend contacting us for help! Our team will be more than happy to answer any questions and provide assistance with implementing our recommendations here at the office or remotely at your home or workplace.
1 note
·
View note
Text
Trend micro internet security review

#Trend micro internet security review software
#Trend micro internet security review Pc
This differs from the anti-ransomware tool used by Bitdefender, which pre-emptively locks the files designated by the user so they are unable to undergo encryption.ģ.
#Trend micro internet security review software
The software also attempts to halt the encryption process if the software appears to be suspicious. To defend users against encrypting ransomware, Trend Micro’s software monitors your device for encryption attempts, and then backs up the file or files that are being targeted prior to encryption occurring. Once the program bypasses the locking mechanism, you will be able to access your files and use your computer as normal, and the maker of the ransomware will not be able to access anything on your computer, maintaining your security. This way, if you are caught up in one of these dangerous and frustrating schemes, you can trust that the software is there in place as a backup measure to protect you.
#Trend micro internet security review Pc
Trend Micro Maximum offers tools that can bypass the locking mechanism even in cases where rebooting the PC in Safe Mode doesn’t remedy the problem. The types of things that ransomware or malware generally does include locking up the screen of your computer, encrypting the files on a computer, and demanding a ransom to allow the user to regain their access to their device. Don’t get caught up with harmful viruses on your computer or leaving yourself vulnerable to cyber-attackers eager to steal your information for their less than benevolent purposes. It’s unfathomable how many amazing things you can do with only a few clicks of the buttons on your keyboard-however, if you are not careful, the internet can be just as dangerous as it is astonishing. The age of the internet is an incredible time to be alive. The purpose of the software is to provide you with multi-device protection on up to 6 devices with the latest and greatest in anti-ransomware technology, block you from accessing dangerous web content, shielding your social media privacy, protecting your children while they browse the web, and safely managing your online passwords. Trend Micro Maximum Security is a protection program for your internet accessible devices that allows you to go digital, safely. While this opens so many doors and opportunities in life for great things, it also leaves us vulnerable to dangerous attacks and people who wish to do us harm will stop at nearly nothing to access your personal and private information.ĭon’t leave yourself unprotected against such threats. In fact, for most of us, we have some sort of internet-accessible device in our pockets always. Today, we use the Internet in the things that we do daily.

0 notes
Text
Norton antivirus plus

NORTON ANTIVIRUS PLUS SOFTWARE
NORTON ANTIVIRUS PLUS PC
NORTON ANTIVIRUS PLUS PLUS
Parental controls and covers multiple devices.
If you were considering getting a VPN separately too, then Norton 360 Standard might be worth considering though, as it’ll work out cheaper than two separate subscriptions but ultimately you’re still only getting cover for a single device.
NORTON ANTIVIRUS PLUS PLUS
So is Norton 360 worth double the cost of Norton Antivirus Plus? That depends on your needs, but for most users we think that Norton Antivirus Plus will be sufficient.
NORTON ANTIVIRUS PLUS PC
There’s also PC Safecam, which specifically blocks unauthorized access to your webcam and dark web monitoring, which will periodically scan the dark web for your email address and notify you if it comes up. If you’re looking for more info on VPNs, check out our best VPN services (opens in new tab) guide, and our explainer on what a VPN is and why you need one (opens in new tab). This is especially useful if you often use public or unsecured WiFi networks, where you can’t always be sure who is watching. This will probably be enough data for an average user, though again people with extensive media libraries that need protecting might need more space.Īlong with the extra storage space, you also get access to a secure VPN, which encrypts your online activity data, making sure you stay anonymous and safe when you’re online. Well to start with your cloud storage data limit is increased to 10GB, which means you’ll be able to securely store and protect a lot more data. But what do you get for that extra money? Norton 360 Standard costs $39.99 for the first year and then $79.99 annually after that. Again, it covers one device (either a PC, Mac, smartphone, or tablet) and contains everything that you’ll find in Norton Antivirus Plus, along with some extra features to help keep you even more secure online. Norton 360 Standard is the next step up from the antivirus and offers a more complete security package. A guarantee to replace your device would be much better, but it’s something at least. This is… fine, but if you get a virus that Norton can’t remove, you’ll also likely be out the cost of your PC or laptop (opens in new tab). 2GB is enough to safeguard work documents easily enough, but this might not be enough if you have an extensive photo or video library on your hard drive.įinally, there is Norton’s Virus Protection Promise, which states that they will refund you the cost of your subscription if your computer gets a virus that it can’t remove. You also get 2GB of cloud storage to backup your laptop or computer’s hard drive to keep your files safe should a virus actually make it through onto your computer and destroy your local copies. This is all backed up with online threat protection, which is designed to keep your personal information safe when you’re browsing the web. This includes the essentials like antivirus and firewall, but also protection against spyware, ransomware, and malware.
NORTON ANTIVIRUS PLUS SOFTWARE
For that you get a comprehensive suite of online protection software for a single device (PC, laptop or Mac). It’s also the cheapest of Norton’s offerings, costing $19.99 for the first year and then $59.99 annually after that. This is Norton’s basic antivirus program without all the bells and whistles that you find in its more complete security systems. Norton AntiVirus Plus for $19.99 per year (opens in new tab).Norton AntiVirus Plus subscription options: So strap in as we take you through the six different security packages that Norton offers and explain which one is right for you. And just how good is Norton’s antivirus program when it comes to keeping your devices safe from online threats and malicious software? But which is the right package for you? Do you go for the basic antivirus setup, or splash the cash and go for the Ultimate Plus edition in an attempt to have a home more secure than the Pentagon? Well that all depends on who you are, how many people you’re looking to cover and just how valuable the data you’re looking to protect is.

0 notes