#Free mac antivirus scan
Text
Free mac antivirus scan

FREE MAC ANTIVIRUS SCAN FOR MAC
FREE MAC ANTIVIRUS SCAN MAC OS
Avira the best free antivirus for families. Norton Antivirus state-of-art free antivirus. Bitdefender a super secure free antivirus. All in one attractive user-friendly interface. Best free antivirus software quick list: TotalAV the most extensive free antivirus scanner. As a free antivirus scanner and cleaner, Kaspersky Security Cloud Free software defends your PC and mobile devices, including your iPhone, against viruses, infected files, dangerous applications and suspicious sites. This is not a stripped-down version of a paid product, it's the real deal.
FREE MAC ANTIVIRUS SCAN FOR MAC
Download Comodo’s Best Virus Protection for MAC Softwareįeaturing an on-demand Mac malware scanner, 'always on' real-time protection, and a constantly updated database of known viruses, Comodo MAC Antivirus provides superior protection against zero-day malware.
FREE MAC ANTIVIRUS SCAN MAC OS
The quantity of Mac viruses is growing at an alarming rate and solid protection against these threats is essential if you wish to prevent identity theft, file corruption, or interception of your credit card details.Ĭomodo's best antivirus software for mac provides the state-of-the-art best virus protection for your Mac OS computer at no cost. Unfortunately, this is no longer the case. There used to be a time when Mac computers were considered almost 'virus-proof'. They were allowed to update themselves and query their in-the-cloud services. We offer to install and using the CHOMAR Antivirus Security app on a Windows 10/8/7 PC. Prevent your Mac from spyware, ransomware, viruses. Antivirus Sniper helps you scan your Mac for virus detection and provides real-time protection. Read 1 user reviews and compare with similar apps on MacUpdate. We always used the most current version of all products for the testing. freeload and Install CHOMAR Antivirus Security For PC. Download the latest version of Antivirus Sniper for Mac for free. During November and December 2021 we evaluated 8 home user security products for MacOS Big Sur. Comodo’s Best Mac Antivirus 2022: How does antivirus for mac work? The best MacOS antivirus software for home users. PROS Unusual human-centric interface Available for macOS, Android, and iOS Speedy scan for malware Detects malicious and fraudulent pages Includes basic VPN 24/7/365 live.

0 notes
Link
2 notes
·
View notes
Text
(SOLVED) Help with Waves v13 R2R Windows | AudioSEX - Professional Audio Forum
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Waves Plugins Crack is revolutionary computer software that enables consumers to set soundtrack layouts of choice. Waves Complete Crack Fully complete park of virtual effects and instruments from A to Z of the highest quality and with support. Waves Keygen Where Do So enjoy néw Waves Crack for your mac and powered by Peatix : More than a ticket. Waves All Plugins Bundle V29 R15 Windows (Fixed Crack R2R) Keygen. [Ching] FINAL + Key + Crack Waves Complete V ALL PLUGINS. Antivirus Check. Waves Complete v9r30 Incl Patch and Keygen-R2R Torrentz - Fast and easy torrent search Today, Waves Complete is a professional mastering program that. Waves v Complete Awesome Cracked support bit system, quicker loading, scanning, and process, Waves v parades new. Hi ive been trying to figure out how to use the waves v13 R2R patcher for a while but cant seem to get it working in windows/ studio one. › Products › Plugins. Waves Tune Real-Time provides smooth, natural-sounding vocal pitch correction instantly and automatically, as soon as the notes leave the singer's mouth. Keygen support bit system, quicker loading, scanning, and process, Waves v9 parades new dimensions of high performance plugin power with new plugins. I've found for you Waves Complete v9r27 Incl Patch and Keygen-R2R, iron man spanish. waves plugin crack reddit. Waves Plugins Crack is revolutionary computer software that enables consumers to set soundtrack layouts of choice. Waves Complete Crack Fully complete park of virtual effects and instruments from A to Z of the highest quality and with support. Waves Keygen Where Do So enjoy néw Waves Crack for your mac and powered by Peatix : More than a ticket. Waves All Plugins Bundle V29 R15 Windows (Fixed Crack R2R) Keygen. [Ching] FINAL + Key + Crack Waves Complete V ALL PLUGINS. Antivirus Check. Waves Complete v9r30 Incl Patch and Keygen-R2R Torrentz - Fast and easy torrent search Today, Waves Complete is a professional mastering program that. Waves v Complete Awesome Cracked support bit system, quicker loading, scanning, and process, Waves v parades new. Hi ive been trying to figure out how to use the waves v13 R2R patcher for a while but cant seem to get it working in windows/ studio one. › Products › Plugins. Waves Tune Real-Time provides smooth, natural-sounding vocal pitch correction instantly and automatically, as soon as the notes leave the singer's mouth. Keygen support bit system, quicker loading, scanning, and process, Waves v9 parades new dimensions of high performance plugin power with new plugins. I've found for you Waves Complete v9r27 Incl Patch and Keygen-R2R, iron man spanish. waves plugin crack reddit. I've found for you Waves Complete v9r27 Incl Patch and Keygen-R2R, iron man spanish. View from CIS MISC at Askari College of Education, Burewala. Waves Comeplete Custom Patched+KeyGen Release all previous versions. 0 for MAC and Windows Download Torrent Apr 24, Download Free Mac OS X Snow serial, keygen, torrent Waves Tune Real-Time Crack provides smooth. Waves Complete VST 12 V Crack Free Download Waves Mercury VST Crack Fully complete park of many effects and instruments from A to Z. Tag: Waves All Plugins Bundle v9r8 FULL REPACK – R2R [deepstatus][ keygen. No Content Available. Sign Up to Stay in Touch. * indicates required. Unlike compression, waves vocal rider torrent does not add color to a vocal recording. subtitle Keygen | Added TRACT + TRACT LinPhase License | 5MBsubtitle In celebration of Waves' 25th anniversary, we are pleased to announce a new. Waves Complete V9r2 Keygen Music Download. Waves Complete v Incl Patched and KeygenTeam Ur2R GBFeaturing little. Generally, the following files remain on disk: C:\Program Files (x86)\Keygen\Waves\Waves_Complete_; C:\Users\UserName\AppData\Local\. waves plugin crack reddit.
Waves All Plugins Bundle V29 R15 Windows (Fixed Crack R2R) Keygen rawele - Wakelet
Waves Plugins 12 (v) Crack Plus Keygen Free Download
[download]-R2R amaque - Wakelet
Waves Complete Crack Keygen Free Download
(SOLVED) Help with Waves v13 R2R Windows | AudioSEX - Professional Audio Forum
[download]-R2R amaque - Wakelet
Waves All Plugins Bundle V29 R15 Windows (Fixed Crack R2R) Keygen rawele - Wakelet
Waves Plugins Crack 14 With Keygen Free Download
Waves Plugins 12 (v) Crack Plus Keygen Free Download
Waves Complete 12 V Cracked +Keygen Free PC Version
Waves Tune Real-Time Plugin | Waves
Waves Complete v9r27 Incl Patch and Keygen-R2R - Absolute Posts
Waves Complete Crack Keygen Free Download
[download]-R2R amaque - Wakelet
Waves All Plugins Bundle V29 R15 Windows (Fixed Crack R2R) Keygen rawele - Wakelet
(SOLVED) Help with Waves v13 R2R Windows | AudioSEX - Professional Audio Forum
Waves Complete 12 V Cracked +Keygen Free PC Version
Waves Plugins Crack 14 With Keygen Free Download
Waves Tune Real-Time Plugin | Waves
Waves Complete v9r27 Incl Patch and Keygen-R2R - Absolute Posts
Waves Plugins 12 (v) Crack Plus Keygen Free Download
Waves Vocal Rider Crack + Serial Key Download
Waves Complete v9r27 Incl Patch and Keygen-R2R - Absolute Posts
Waves version by Keygen - How to uninstall it
1 note
·
View note
Text
Remove DynamicMore Virus from Mac OS X - Free Guide
Ever felt like your Mac isn’t quite itself? Maybe it's slower than usual, or you're seeing ads that feel a bit too personal? If so, you might have encountered the DynamicMore virus. No need to worry though, because if you've found this malware guide, you're about to turn things around. Let's walk through how to clean your Mac of this pesky intruder, ensuring it runs smoothly again.
What is the DynamicMore Virus?
Imagine you downloaded what you thought was a helpful app, but it turned out to be a wolf in sheep's clothing, wreaking havoc behind the scenes. That's what the DynamicMore virus does—it masquerades as legitimate software while it disrupts your system, displays ads, and may even monitor your activities.
How Did DynamicMore Infect Your Mac?
DynamicMore typically finds its way onto your Mac through bundled software installations or by downloading apps from unreliable sources. It's like picking up a hitchhiker who turns out to be a bit of a nightmare guest.

Signs Your Mac is Infected
Here’s what to look out for:
Your Mac is slower than its usual self.
Ads pop up unexpectedly.
Your web browser’s homepage has changed without your input.
Applications you don’t remember installing appear.
Step 1: Quit Suspicious Applications
First things first, open your Activity Monitor (found in Applications > Utilities) and quit any process that looks unusual or that you don’t recognize.
Step 2: Remove Applications Related to DynamicMore
Navigate to your Applications folder. Drag any suspicious applications to the Trash, especially those you installed recently and coincide with the appearance of issues.
Step 3: Clean Up Your Login Items
Go to System Preferences > Users & Groups, click your username, and then click Login Items. Remove anything linked to DynamicMore or that you don’t recognize.
Step 4: Remove Malicious Extensions
Open your browser and remove any extensions that you didn’t install yourself or that seem to generate ads. Each browser has a slightly different process to manage extensions, but you can generally find this option in the preferences menu.
Step 5: Clear Cache and Cookies
Clearing the cache and cookies from your browser can remove tracking cookies and data leftovers from DynamicMore.
Step 6: Check and Clean Up Library Folders
Look in your Library folder (accessible by holding down the Option key while clicking the “Go” menu in Finder). Remove any files or folders that seem related to DynamicMore from locations like ~/Library/Application Support, ~/Library/Preferences, and ~/Library/Caches.
Step 7: Run a Malware Scan
Use a reputable antivirus tool to scan your Mac. This can help ensure that all components of the virus have been removed and that your system is clean.
Prevention Tips for the Future
To prevent future infections:
Download software only from the Mac App Store or directly from developers’ websites.
Keep your macOS and all applications up to date.
Consider using a Mac antivirus program for ongoing protection.
FAQs About Mac Viruses
Can Macs get viruses? Yes, while Macs are less commonly targeted than PCs, they can still be infected.
Is it necessary to install antivirus on Mac? It’s not mandatory, but it can provide an extra layer of security.
Conclusion
By following these steps, you can remove the DynamicMore virus from your Mac and keep your system running smoothly. Remember, the key to computer health is vigilance and quick action when something seems amiss. Keep your Mac clean, and safe surfing
0 notes
Text
The Best Torrent Downloader: Your Guide to Fast and Safe Downloads
If you've ever wanted to download movies, TV shows, music, software, or even eBooks, chances are you've come across the term "torrenting." Torrenting offers a way to access a massive library of files, but to successfully navigate the world of torrents, you'll need a reliable torrent downloader. In this blog, we'll dive into the essentials of torrent downloaders, explore the top choices, and provide tips for safe and efficient downloading.
What is Torrenting?
Before we talk about best torrent downloader, let's understand how torrenting works. Torrenting is a type of file-sharing technology based on a peer-to-peer (P2P) network. Instead of downloading a file from a single server, you download small pieces of it from multiple users (called "seeders") who already have the complete file. This distributes the download, making it faster and more reliable, especially for large files.
What is a Torrent Downloader?
A torrent downloader, or torrent client, is the software that makes torrenting possible. Here's what it does:
Finds Torrents: Torrent downloaders help you search for torrent files on various torrent websites and trackers.
Connects to Peers: The software connects you to other users sharing the file (seeders and leechers).
Manages Downloads: It handles the downloading process, reassembling the file pieces into a usable format.
Features: Many torrent downloaders come with additional features like scheduling, bandwidth control, and even built-in media players.
Choosing the Best Torrent Downloader
With so many torrent downloaders out there, picking the right one can be tricky. Here are the key factors to consider:
Ease of Use: A good torrent downloader should have a simple and intuitive interface, especially if you're new to torrenting.
Speed: Look for a downloader that can handle high-speed downloads and manage multiple torrents without slowing down.
Safety: Choose a torrent downloader with a good reputation and built-in security features to protect you from malware and viruses.
Features: Consider the extra features you might need, like bandwidth controls, download scheduling, or file prioritization.
Ad-free: Many free torrent downloaders come with intrusive ads. Look for one that limits ads or has a premium ad-free option.
Top Torrent Downloaders
Here's a breakdown of some of the most popular and well-regarded torrent downloaders:
qBittorrent: A popular choice known for its lightweight design, clean interface, and lack of ads. It's fast, reliable, and offers all the essential features most users will need.
Deluge: Another excellent open-source torrent downloader with a focus on simplicity and speed. Offers a plugin system if you want to expand the feature set.
Transmission: Simple and lightweight, ideal for users who want a no-frills torrenting experience. Popular on Linux and Mac systems.
uTorrent: While very popular, uTorrent has a history of bundled software and intrusive ads. Consider it only if you opt for a paid version which removes these issues.
BitTorrent: The original BitTorrent client, now similar in features to uTorrent. Again, a paid version will give the best experience.
Safety Tips for Torrent Downloading
It's important to practice safe torrenting to protect your device and personal information. Here are some tips:
Use a VPN: A virtual private network (VPN) encrypts your traffic and masks your IP address, making your torrenting activity more private and secure.
Install Antivirus Software: Have reliable antivirus software running to scan downloaded files for malware.
Choose Reputable Sources: Download torrents from well-known torrent websites with positive user reviews.
Check File Ratings and Comments: Look for torrents with good seed counts and positive comments to minimize the risk of downloading malicious files.
Disclaimer: Remember that downloading copyrighted material without permission is illegal in most countries. Always ensure you have the right to download any content you find through torrenting.
0 notes
Text
The Best Torrent Downloader: Your Guide to Fast and Safe Downloads
If you've ever wanted to download movies, TV shows, music, software, or even eBooks, chances are you'vecome across the term "torrenting." Torrenting offers a way to access a massive library of files, but to successfully navigate the world of torrents, you'll need a reliable torrent downloader. In this blog, we'll dive into the essentials of torrent downloaders, explore the top choices, and provide tips for safe and efficient downloading.
What is Torrenting?
Before we talk about best torrent downloader, let's understand how torrenting works. Torrenting is a type of file-sharing technology based on a peer-to-peer (P2P) network. Instead of downloading a file from a single server, you download small pieces of it from multiple users (called "seeders") who already have the complete file. This distributes the download, making it faster and more reliable, especially for large files.
What is a Torrent Downloader?
A torrent downloader, or torrent client, is the software that makes torrenting possible. Here's what it does:
Finds Torrents: Torrent downloaders help you search for torrent files on various torrent websites and trackers.
Connects to Peers: The software connects you to other users sharing the file (seeders and leechers).
Manages Downloads: It handles the downloading process, reassembling the file pieces into a usable format.
Features: Many torrent downloaders come with additional features like scheduling, bandwidth control, and even built-in media players.
Choosing the Best Torrent Downloader
With so many torrent downloaders out there, picking the right one can be tricky. Here are the key factors to consider:
Ease of Use: A good torrent downloader should have a simple and intuitive interface, especially if you're new to torrenting.
Speed: Look for a downloader that can handle high-speed downloads and manage multiple torrents without slowing down.
Safety: Choose a torrent downloader with a good reputation and built-in security features to protect you from malware and viruses.
Features: Consider the extra features you might need, like bandwidth controls, download scheduling, or file prioritization.
Ad-free: Many free torrent downloaders come with intrusive ads. Look for one that limits ads or has a premium ad-free option.
Top Torrent Downloaders
Here's a breakdown of some of the most popular and well-regarded torrent downloaders:
qBittorrent: A popular choice known for its lightweight design, clean interface, and lack of ads. It's fast, reliable, and offers all the essential features most users will need.
Deluge: Another excellent open-source torrent downloader with a focus on simplicity and speed. Offers a plugin system if you want to expand the feature set.
Transmission: Simple and lightweight, ideal for users who want a no-frills torrenting experience. Popular on Linux and Mac systems.
uTorrent: While very popular, uTorrent has a history of bundled software and intrusive ads. Consider it only if you opt for a paid version which removes these issues.
BitTorrent: The original BitTorrent client, now similar in features to uTorrent. Again, a paid version will give the best experience.
Safety Tips for Torrent Downloading
It's important to practice safe torrenting to protect your device and personal information. Here are some tips:
Use a VPN: A virtual private network (VPN) encrypts your traffic and masks your IP address, making your torrenting activity more private and secure.
Install Antivirus Software: Have reliable antivirus software running to scan downloaded files for malware.
Choose Reputable Sources: Download torrents from well-known torrent websites with positive user reviews.
Check File Ratings and Comments: Look for torrents with good seed counts and positive comments to minimize the risk of downloading malicious files.
Disclaimer: Remember that downloading copyrighted material without permission is illegal in most countries. Always ensure you have the right to download any content you find through torrenting.
0 notes
Text
do norton vpn and security come together
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do norton vpn and security come together
Norton VPN features
Norton VPN is a robust tool designed to ensure your online privacy and security. Packed with a range of features, it offers comprehensive protection for your internet activities.
One standout feature of Norton VPN is its ability to encrypt your data, keeping it safe from prying eyes. With advanced encryption protocols, including AES-256, it creates a secure tunnel for your online traffic, preventing hackers, ISPs, and other third parties from intercepting your data.
Moreover, Norton VPN offers a vast network of servers worldwide, allowing you to browse the internet anonymously from virtually anywhere. Whether you're at home, traveling, or using public Wi-Fi, you can connect to a server of your choice and enjoy unrestricted access to content while keeping your real IP address hidden.
For users concerned about streaming content from geo-restricted platforms, Norton VPN has you covered. Its servers are optimized for streaming, ensuring smooth playback of your favorite movies, TV shows, and sports events, regardless of your location. Additionally, Norton VPN bypasses censorship and firewalls, granting you access to the global internet without limitations.
Furthermore, Norton VPN prioritizes user privacy by adhering to a strict no-logs policy. This means that it doesn't track or store your online activities, ensuring that your browsing history remains private and secure.
In terms of usability, Norton VPN offers user-friendly apps for various devices, including Windows, Mac, Android, and iOS. With just a few clicks, you can connect to a server, toggle settings, and customize your VPN experience according to your preferences.
Overall, Norton VPN stands out for its robust security features, global server network, streaming capabilities, privacy protection, and user-friendly interface, making it a reliable choice for safeguarding your online presence.
Norton security integration
Norton Security Integration: Enhancing Data Security and Protection
In today's digital landscape, safeguarding sensitive data is paramount, and integrating Norton security solutions proves to be a robust defense mechanism against cyber threats. Norton, a renowned name in the cybersecurity realm, offers a suite of tools and features that fortify data security across various platforms and devices.
By integrating Norton security software, individuals and businesses benefit from real-time protection against malware, ransomware, phishing attacks, and other online risks. The seamless integration of Norton solutions ensures that all endpoints, networks, and systems are shielded from evolving cyber threats, providing users with peace of mind and a secure digital environment.
Moreover, Norton security integration extends beyond traditional antivirus protection, offering advanced features such as firewall protection, VPN services, identity theft prevention, and secure cloud storage options. These robust layers of security work in unison to create a comprehensive defense infrastructure that mitigates risks and safeguards data integrity.
Furthermore, the user-friendly interface of Norton security solutions makes integration and management hassle-free, allowing users to customize settings, perform scans, and receive real-time alerts effortlessly. Whether it's securing personal devices or fortifying an entire network, Norton's versatile security suite caters to the diverse security needs of individuals and organizations alike.
In conclusion, Norton security integration is a proactive approach towards enhancing data security and protection in an increasingly digital world. By leveraging Norton's cutting-edge technologies and comprehensive security features, users can defend against cyber threats effectively and uphold the confidentiality and integrity of their valuable data.
Unified Norton VPN and security
Title: The Integration of Norton VPN and Security: A Unified Approach to Online Protection
In an era where online security is paramount, Norton has taken a significant step forward by integrating its VPN service with its renowned security suite. This move marks a strategic shift towards offering users a unified solution for protecting their digital lives.
Norton's VPN, known for its robust encryption and secure browsing capabilities, now seamlessly integrates with its comprehensive security software. This integration not only simplifies the user experience but also enhances overall protection against cyber threats.
One of the key benefits of this unified approach is the ability to safeguard sensitive information across all online activities. Whether browsing the web, accessing public Wi-Fi networks, or conducting online transactions, users can trust that their data remains encrypted and secure.
Moreover, the integration of Norton VPN and security streamlines management for users, eliminating the need to juggle multiple applications. With a single interface for both VPN and security features, users can easily monitor and control their protection settings without any hassle.
Another advantage is the enhanced privacy offered by Norton's VPN, which masks users' IP addresses and encrypts their internet traffic. By rerouting connections through secure servers worldwide, Norton VPN ensures anonymity and protects against prying eyes.
Furthermore, Norton's comprehensive security suite provides advanced features such as antivirus protection, firewall, and identity theft prevention. By combining these capabilities with VPN functionality, users benefit from a holistic approach to online security.
In conclusion, the integration of Norton VPN and security represents a significant advancement in protecting users' online privacy and data. By offering a unified solution, Norton empowers users to navigate the digital world with confidence, knowing that their information is safe and secure.
Compatibility of Norton VPN and security
Norton VPN is a popular choice for individuals seeking enhanced online privacy and security. However, when it comes to compatibility with other security software, users may have concerns. The good news is that Norton VPN is designed to work seamlessly with various security programs, ensuring comprehensive protection for your online activities.
Norton VPN is compatible with most antivirus software, including Norton Antivirus, McAfee, AVG, and Avast, among others. This compatibility ensures that your device remains secure from various online threats while benefiting from the added layer of privacy provided by the VPN service. Additionally, Norton VPN can be used alongside firewalls and other security tools without any conflicts, allowing for a multi-layered approach to safeguarding your digital presence.
For individuals using Norton VPN on multiple devices, compatibility is essential. The service is compatible with Windows, macOS, Android, and iOS operating systems, making it a versatile choice for users across different platforms. This cross-platform compatibility ensures that you can enjoy secure and private browsing experiences on all your devices without compromising on safety.
In conclusion, Norton VPN offers robust security and privacy features while maintaining compatibility with a wide range of security software and devices. By combining the benefits of a VPN with other security tools, users can create a strong defense against online threats and enjoy peace of mind while browsing the internet.
Norton VPN and security bundle
Title: Enhancing Online Security with Norton VPN and Security Bundle
In an era where digital threats lurk around every virtual corner, safeguarding your online presence is paramount. Norton, a renowned name in cybersecurity, offers a comprehensive solution with its VPN and security bundle. By combining the power of Norton Secure VPN and Norton 360, users can enjoy enhanced protection and privacy across their digital activities.
Norton Secure VPN serves as the first line of defense by encrypting your internet connection, shielding sensitive data from prying eyes. Whether you're browsing the web, accessing public Wi-Fi, or streaming content, Norton Secure VPN establishes a secure tunnel that masks your online activities, preventing unauthorized access and potential breaches.
Complementing the VPN service is Norton 360, a robust security suite designed to combat evolving cyber threats. With features such as real-time threat protection, secure VPN, password manager, and dark web monitoring, Norton 360 offers comprehensive defense against malware, phishing attempts, and identity theft. Its intuitive interface and automatic updates ensure hassle-free security management, allowing users to stay protected without compromising usability.
Together, the Norton VPN and security bundle provide a holistic approach to online security, addressing both privacy concerns and cybersecurity threats. Whether you're a casual internet user, a remote worker, or a digital nomad, investing in reliable protection is essential to safeguarding your digital identity and sensitive information.
Moreover, Norton's commitment to innovation and continuous improvement means that users can trust their digital safety to a brand that consistently evolves to meet the challenges of an ever-changing threat landscape.
In conclusion, the Norton VPN and security bundle offer peace of mind in an increasingly digital world. By prioritizing privacy, security, and user convenience, Norton empowers individuals to navigate the online realm with confidence, knowing that their digital footprint is protected by industry-leading solutions.
0 notes
Text
do i need a vpn on my mac
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need a vpn on my mac
VPN benefits for Mac
A Virtual Private Network (VPN) offers numerous benefits to Mac users, ensuring enhanced privacy, security, and convenience while browsing the internet. One of the key advantages of using a VPN on your Mac is the ability to encrypt your online activities, making it difficult for hackers, ISPs, or even government agencies to track your browsing history or access sensitive information.
Moreover, VPNs allow users to bypass geo-restrictions and access region-locked content on streaming platforms such as Netflix, Hulu, and BBC iPlayer. By connecting to a server located in a different country, Mac users can enjoy a wider range of content and online services that may not be available in their region.
Additionally, VPNs help protect your Mac from potential cyber threats such as malware, phishing scams, and ransomware attacks. By routing your internet traffic through a secure and encrypted connection, VPNs create a protective shield that safeguards your device from online dangers.
Another benefit of using a VPN on your Mac is the ability to browse anonymously and maintain your online privacy. VPNs mask your IP address, making it challenging for websites and online advertisers to track your online behavior and target you with personalized ads.
In conclusion, utilizing a VPN on your Mac can significantly enhance your online experience by providing security, privacy, access to restricted content, and protection against cyber threats. Whether you're working remotely, streaming your favorite shows, or simply browsing the web, incorporating a VPN into your Mac usage can offer peace of mind and a more secure internet environment.
Mac security without VPN
In today's interconnected world, maintaining the security of your Mac is crucial to safeguard your personal data and privacy. While virtual private networks (VPNs) are commonly used to enhance online security, there are alternative methods to ensure Mac security without relying on a VPN.
One effective way to enhance Mac security is by utilizing the built-in security features provided by Apple. The macOS operating system is equipped with robust security measures such as Gatekeeper, XProtect, and FileVault, which help protect your system from malware, viruses, and unauthorized access. Keeping your operating system up to date ensures that you benefit from the latest security updates and patches, strengthening the overall security of your Mac.
Additionally, practicing safe browsing habits and being cautious with email attachments can significantly reduce the risk of falling victim to cyber threats. Avoid clicking on suspicious links, downloading files from untrustworthy sources, and sharing sensitive information on unsecured websites to mitigate potential security risks.
Furthermore, utilizing reputable antivirus software specifically designed for Mac systems can provide an extra layer of protection against malware and other online threats. Regularly scanning your Mac for malicious software and conducting system checks can help identify and remove any potential security vulnerabilities.
By implementing these strategies and adopting a proactive approach to Mac security, you can effectively protect your personal information and enhance the overall security of your device without solely relying on a VPN. Remember, staying informed about the latest security practices and being vigilant online are essential components of maintaining a secure Mac environment.
VPN necessity for Mac users
In today's digital age, protecting your online privacy and data security has never been more essential. This is especially true for Mac users who, despite the common misconception that Macs are immune to cyber threats, are just as susceptible to online dangers as any other device. One powerful tool that Mac users can utilize to safeguard their digital presence is a Virtual Private Network (VPN).
A VPN creates a secure and encrypted connection between your device and the internet, ensuring that your online activities remain private and cannot be accessed by hackers, government agencies, or other prying eyes. This is particularly crucial when using public Wi-Fi networks, such as those found in cafes, airports, or hotels, as these connections are often insecure and leave your data vulnerable to cyber attacks.
Furthermore, a VPN allows Mac users to bypass geographic restrictions and access region-locked content, such as streaming services or websites, from anywhere in the world. By connecting to servers in different countries, users can enjoy a more open and unrestricted internet experience.
Additionally, VPNs can help improve your online security by masking your IP address and preventing websites from tracking your browsing habits. This not only protects your privacy but also helps prevent targeted advertising and data mining.
In conclusion, a VPN is not just a luxury but a necessity for Mac users looking to enhance their online security and privacy. By investing in a reliable VPN service, Mac users can enjoy a safer and more unrestricted browsing experience, wherever they may be.
Choosing the right VPN for Mac
Choosing the right VPN for Mac can be a critical decision for anyone concerned about online privacy and security. With the increasing prevalence of cyber threats and the need to safeguard personal data, a reliable VPN is essential for Mac users.
When selecting a VPN for your Mac, several factors should be taken into consideration:
Compatibility: Ensure that the VPN service you choose is compatible with macOS and offers dedicated applications for Mac devices. This ensures seamless integration and ease of use.
Security Features: Look for VPNs that offer robust security features such as AES encryption, kill switch, and DNS leak protection. These features help to ensure that your online activities remain private and secure.
Server Network: A wide server network ensures better connectivity and allows you to access geo-restricted content from around the world. Choose a VPN with a large number of servers in diverse locations.
Speed and Performance: Opt for a VPN that offers fast and reliable connection speeds. Slow VPNs can hinder your browsing experience and make streaming or downloading content a frustrating experience.
Privacy Policy: Review the VPN provider's privacy policy to ensure that they have a strict no-logs policy and do not store any personally identifiable information.
Customer Support: Look for VPN providers that offer responsive customer support via live chat, email, or phone. This ensures that you can get help quickly in case of any issues or concerns.
Price and Plans: Consider your budget and choose a VPN that offers affordable pricing plans without compromising on features and security.
By carefully considering these factors, you can choose the right VPN for your Mac that meets your needs and provides the security and privacy you require in today's digital age.
Mac VPN setup guide
Setting up a VPN on your Mac is essential for ensuring your online privacy and security. Whether you want to protect your data while using public Wi-Fi networks or access geo-restricted content, a VPN is a powerful tool. Follow this simple guide to set up a VPN on your Mac:
Choose a reliable VPN service: Start by selecting a reputable VPN provider that offers a user-friendly Mac app and robust security features. You can choose from both free and paid VPN options based on your needs.
Download and install the VPN app: Once you've chosen a VPN service, download the app from the provider's website or the Apple App Store. Follow the installation instructions to set up the app on your Mac.
Connect to a VPN server: Open the VPN app and log in with your credentials. You will then have the option to choose a server location. Select a server based on your needs, whether it's for accessing content from a specific region or optimizing speed.
Customize your VPN settings: Depending on your preferences, you can customize the VPN settings such as enabling a kill switch, choosing a protocol, or setting up split tunneling.
Verify your connection: Once you've connected to a VPN server, verify that your IP address has changed and your connection is secure. You can use online tools to check your IP address and ensure that your data is encrypted.
By following these simple steps, you can set up a VPN on your Mac and enjoy a safer and more private online experience. Remember to keep your VPN app updated for the latest security features and enjoy browsing the web with peace of mind.
0 notes
Text
does avast for mac include a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does avast for mac include a vpn
Avast for Mac VPN compatibility
Avast is a well-known cybersecurity company that offers a range of products to protect devices against online threats. One of its popular offerings is Avast SecureLine VPN, which allows users to browse the internet securely and anonymously by encrypting their connection.
When it comes to compatibility, Avast SecureLine VPN is designed to work seamlessly across different platforms, including Mac devices. Mac users can easily download and install the Avast SecureLine VPN application from the Avast website or the Apple App Store.
Avast SecureLine VPN for Mac is compatible with various versions of macOS, ensuring that users can enjoy a secure internet browsing experience regardless of their operating system. Whether you are using an older version like macOS High Sierra or the latest macOS Catalina, Avast SecureLine VPN has got you covered.
By using Avast SecureLine VPN on your Mac, you can access geo-restricted content, protect your online privacy, and secure your connection while using public Wi-Fi networks. The application offers fast server connections, unlimited bandwidth, and a user-friendly interface, making it easy for Mac users to enjoy a seamless VPN experience.
In conclusion, Avast SecureLine VPN is compatible with Mac devices and provides users with a reliable and secure VPN solution to protect their online activities. Whether you are a casual internet user or someone who values privacy and security, Avast SecureLine VPN for Mac is a great choice to consider.
Secure online browsing with Avast for Mac
Avast for Mac is a powerful antivirus software that offers comprehensive protection for Mac users, ensuring secure online browsing. With the increasing number of cyber threats targeting Mac devices, having a reliable security solution is essential to safeguard your sensitive information and privacy.
One of the key features of Avast for Mac is real-time protection, which continuously monitors your online activities and blocks malicious websites, phishing attempts, and malware in real-time. This proactive approach helps prevent threats before they can harm your Mac, giving you peace of mind while browsing the internet.
In addition, Avast for Mac offers a dedicated Wi-Fi security feature that scans your network for vulnerabilities and alerts you to any potential security risks. This is crucial when using public Wi-Fi networks, as cybercriminals often target these networks to steal personal information.
Furthermore, Avast for Mac includes a robust firewall that acts as a barrier between your Mac and potential threats from the internet. It monitors incoming and outgoing network traffic, allowing you to control which applications can access the internet and ensuring that your data remains secure.
Overall, Avast for Mac is a reliable and effective solution for securing your online browsing experience. By combining advanced security features with user-friendly design, Avast offers Mac users the protection they need to stay safe in today's digital world.
Avast for Mac VPN integration
Avast for Mac VPN integration offers users a secure and reliable way to protect their online privacy while using the internet. With the increasing number of cyber threats and privacy concerns, having a VPN integrated into your antivirus software is essential for keeping your personal information safe.
Avast, a globally recognized name in cybersecurity, has developed a powerful VPN service that seamlessly integrates with their Mac antivirus software. By enabling the VPN feature, users can mask their IP address, encrypt their internet connection, and browse the web anonymously. This added layer of security prevents third parties from monitoring your online activities and helps to protect your sensitive data from being compromised.
The Avast VPN integration for Mac also allows users to access geo-restricted content, such as streaming services and websites, by changing their virtual location. This feature is particularly useful for individuals who travel frequently or want to enjoy content that may be restricted in their region.
Furthermore, Avast's VPN service ensures fast and stable internet connectivity, without compromising on speed or performance. Users can enjoy seamless browsing, streaming, and downloading without experiencing any lag or buffering issues.
In conclusion, Avast for Mac VPN integration is a valuable tool for anyone looking to enhance their online security and privacy. With its user-friendly interface, robust encryption technology, and high-speed servers, Avast VPN seamlessly integrates with Mac devices to provide a safe and unrestricted internet experience.
VPN features in Avast for Mac
Avast, a renowned name in cybersecurity solutions, offers a robust VPN service tailored specifically for Mac users. Avast VPN for Mac boasts a range of features designed to enhance online privacy, security, and accessibility.
One of the standout features of Avast VPN for Mac is its strong encryption protocols. With military-grade encryption, users can rest assured that their online activities, including browsing history, communications, and sensitive data, are shielded from prying eyes. This encryption extends to public Wi-Fi networks, safeguarding users' information even when connected to potentially insecure hotspots.
Another key aspect of Avast VPN for Mac is its extensive server network. With servers located in numerous countries worldwide, users can bypass geographic restrictions and access region-locked content with ease. Whether streaming their favorite shows or accessing websites unavailable in their region, Avast VPN enables Mac users to enjoy a truly global internet experience.
Moreover, Avast VPN for Mac prioritizes user privacy by implementing a strict no-logs policy. This means that Avast does not track or store users' online activities, ensuring complete anonymity while browsing the web. Additionally, the built-in kill switch feature automatically disconnects the user's internet connection if the VPN connection drops, preventing any data leakage in the event of a connection failure.
Furthermore, Avast VPN for Mac offers intuitive, user-friendly software, making it easy for even novice users to navigate and customize their VPN settings. With a simple click, users can connect to the fastest available server or choose a specific location to suit their needs.
In conclusion, Avast VPN for Mac delivers a comprehensive suite of features designed to protect users' online privacy, security, and freedom. With its robust encryption, global server network, commitment to privacy, and user-friendly interface, Avast VPN is a top choice for Mac users seeking reliable VPN protection.
Avast for Mac privacy protection
Avast for Mac offers robust privacy protection for users seeking to safeguard their sensitive information and online activities. With cyber threats on the rise, it is essential to have reliable security software that can effectively shield your personal data from unauthorized access and potential breaches.
Avast for Mac utilizes advanced features such as real-time scanning, firewall protection, and secure browsing to ensure comprehensive privacy protection. The real-time scanning feature constantly monitors your system for any malicious software or suspicious activities, providing an extra layer of defense against cyber threats.
The firewall protection in Avast for Mac acts as a barrier between your device and external networks, allowing you to control which apps have access to the internet and prevent unauthorized connections. This helps prevent sensitive data from being transmitted without your knowledge or consent.
Furthermore, Avast for Mac includes a secure browsing feature that detects and blocks malicious websites, phishing attempts, and online trackers that may compromise your privacy. By warning you about potentially harmful websites, Avast helps keep your sensitive information safe while browsing the internet.
In conclusion, Avast for Mac is a reliable privacy protection solution that offers a range of features to safeguard your personal data and online activities. By utilizing advanced security measures such as real-time scanning, firewall protection, and secure browsing, Avast helps Mac users stay one step ahead of cyber threats and protect their privacy effectively.
0 notes
Text
can t remove vpn mac
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can t remove vpn mac
VPN removal trouble Mac
When it comes to using a Virtual Private Network (VPN) on a Mac, users may sometimes encounter challenges with removing the VPN from their system. Understanding how to troubleshoot and properly remove a VPN is crucial to maintaining the security and functionality of your device.
One common issue users face is difficulty in uninstalling a VPN application from their Mac. This can happen for various reasons, such as incomplete installation, conflicting software, or user error. To address this problem, users can follow a few simple steps to ensure a successful removal process.
Firstly, users should check if the VPN application has a built-in uninstaller. Many VPN providers offer their own uninstallation tool to facilitate the removal process. If this option is available, users should utilize it to uninstall the software correctly.
If the VPN application does not have an uninstaller, users can manually remove it from their Mac. This involves deleting the application from the Applications folder and removing any associated files from the Library folder. It is important to follow specific instructions provided by the VPN provider to ensure a clean and thorough uninstallation.
In some cases, residual files or settings from the VPN application may still remain on the system even after manual removal. To address this, users can use third-party uninstaller tools to scan for and remove any remaining traces of the VPN software.
By following these steps and ensuring a proper uninstallation process, users can effectively troubleshoot and resolve VPN removal issues on their Mac. This will help maintain the integrity of their device and ensure smooth operation without the VPN software.
Mac VPN deletion issue
Title: Resolving Mac VPN Deletion Issue: Troubleshooting Guide
In the digital age, safeguarding online privacy is paramount, prompting many Mac users to rely on Virtual Private Networks (VPNs) for secure internet connections. However, encountering issues like VPN deletions on Mac devices can be frustrating and compromise online security. Understanding the causes and solutions for this problem is crucial for maintaining a secure browsing experience.
One common reason for VPN deletions on Macs is conflicting software. Antivirus programs or firewall settings may mistakenly identify VPN applications as potential threats, leading to their removal. To address this, users should check their security software settings and whitelist the VPN application if necessary.
Moreover, outdated VPN software or operating system versions can also trigger deletion issues. Regularly updating both the VPN client and macOS can prevent compatibility issues and enhance security features. Users should ensure they have the latest updates installed to mitigate such problems.
Another factor contributing to VPN deletions is insufficient disk space. Mac devices with limited storage capacity may automatically delete unused applications, including VPN software, to free up space. To prevent this, users should regularly monitor their disk space and remove unnecessary files or applications to maintain adequate storage.
Additionally, user error or accidental deletion can lead to the removal of VPNs. Users should exercise caution when managing applications and avoid inadvertently uninstalling essential software. Implementing precautions such as locking important applications or enabling parental controls can prevent accidental deletions.
In conclusion, encountering VPN deletion issues on Mac devices can disrupt online privacy and security. By identifying the underlying causes and implementing appropriate solutions such as adjusting security settings, updating software, managing disk space effectively, and exercising caution during application management, users can mitigate these issues and enjoy a seamless and secure browsing experience.
Unable to uninstall VPN Mac
When it comes to removing a VPN from your Mac, you may encounter situations where the process is not as straightforward as expected. The inability to uninstall a VPN on your Mac can be frustrating, but there are various troubleshooting steps you can take to address this issue.
One common reason why you may be unable to uninstall a VPN on your Mac is because the VPN application is still running in the background. Before attempting to uninstall the VPN, make sure to close the application completely. You can do this by right-clicking on the VPN icon in the Menu Bar and selecting “Quit” or using the “Force Quit” option from the Apple menu.
If closing the application doesn’t solve the issue, you can try to uninstall the VPN by locating the application in the Applications folder and dragging it to the Trash. However, some VPNs may have additional components that need to be removed as well. In such cases, you can check the VPN provider’s website for specific instructions on how to completely uninstall their software from your Mac.
Another potential solution is to use a third-party uninstaller application that can help you remove the VPN and its associated files more thoroughly. These applications are designed to clean up leftover files and settings that may prevent you from uninstalling the VPN manually.
If all else fails, you can contact the VPN provider’s customer support for assistance. They may be able to provide you with a specialized uninstaller tool or walk you through the steps to remove the VPN from your Mac successfully.
In conclusion, being unable to uninstall a VPN on your Mac can be a frustrating experience, but with the right troubleshooting steps and tools, you can resolve this issue effectively.
Mac VPN removal error
Title: Troubleshooting Mac VPN Removal Error: A Comprehensive Guide
Are you encountering difficulties when trying to remove a VPN from your Mac? You're not alone. Many users face issues when attempting to uninstall VPN software due to various reasons. However, with the right approach, you can troubleshoot and resolve these errors effectively.
One common issue users encounter is the persistence of VPN files even after the application has been seemingly removed. This can happen due to incomplete uninstallation or leftover files scattered across your system. To address this, start by checking for any remaining VPN files manually. Navigate to your Applications folder and delete any related folders or files associated with the VPN software.
If manual deletion doesn't solve the problem, consider using third-party uninstaller software specifically designed for Mac. These tools can thoroughly scan your system for remnants of the VPN application and remove them efficiently, ensuring a clean uninstallation.
Another potential cause of removal errors is conflicting software or system configurations. Sometimes, other applications or security settings may interfere with the uninstallation process. To troubleshoot this, try disabling any antivirus or firewall software temporarily and then attempt to remove the VPN again.
Additionally, ensure that you have administrative privileges on your Mac, as some VPN software may require elevated permissions for uninstallation.
If you're still experiencing issues after trying these steps, reaching out to the VPN provider's support team can provide further assistance. They may have specific instructions or tools to help you uninstall their software cleanly from your Mac.
In conclusion, encountering errors when removing a VPN from your Mac is a common issue, but it can be resolved with the right approach. By following these troubleshooting steps, you can effectively tackle Mac VPN removal errors and ensure a smooth uninstallation process.
VPN removal challenges on Mac
VPN removal on Mac can sometimes present challenges for users looking to uninstall or switch to a different VPN service. The process of removing a VPN from a Mac device can vary depending on how the software was originally installed and the particular VPN provider in use.
One common challenge when removing a VPN on Mac is incomplete uninstallation. Some VPNs may not include a straightforward uninstallation process, leaving behind files and configurations that can cause issues if not properly removed. This can result in potential conflicts with other VPN applications or network settings on the Mac.
Another challenge users face is difficulty in locating all components of the VPN software. Unlike other applications that have a single uninstaller, VPNs may consist of multiple components spread across various system folders. Users may need to manually delete these components to ensure a clean removal of the VPN from their Mac.
Furthermore, some VPNs integrate deeply with the Mac system, making them harder to completely remove. Users may encounter system errors or stability issues if certain components of the VPN software are not removed correctly.
To overcome these challenges when removing a VPN from a Mac, users can refer to the specific uninstallation instructions provided by their VPN provider. Additionally, third-party uninstaller tools are available that can help ensure a thorough removal of all VPN components from the system.
By following the appropriate steps and utilizing the right tools, users can successfully overcome the challenges associated with VPN removal on Mac and transition smoothly to a different VPN service or network configuration.
0 notes
Text
can you use nord vpn with webroot
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you use nord vpn with webroot
NordVPN compatibility with Webroot
NordVPN and Webroot are two powerful tools that offer essential features to ensure a secure online experience. Both tools excel in their respective domains, with NordVPN focusing on providing top-notch virtual private network (VPN) services, while Webroot specializes in robust antivirus protection.
When it comes to compatibility, NordVPN and Webroot can be used together to create a comprehensive security solution for your devices. NordVPN encrypts your internet traffic and masks your IP address to protect your online activities and ensure your privacy. On the other hand, Webroot provides advanced threat protection against malware, ransomware, and other cyber threats.
Using NordVPN alongside Webroot adds an extra layer of security to your online browsing and data transactions. By encrypting your connection with NordVPN, you can prevent cybercriminals from intercepting your sensitive information, while Webroot's real-time anti-malware protection safeguards your device from online threats.
Both NordVPN and Webroot are compatible with various devices and operating systems, including Windows, Mac, iOS, and Android, allowing you to secure all your devices with ease. Additionally, the user-friendly interfaces of both tools make it simple to set up and manage your security settings without any hassle.
In conclusion, the combination of NordVPN and Webroot offers a strong synergy of VPN privacy and antivirus protection. By integrating these two powerful tools, you can enhance your digital security and enjoy a worry-free online experience.
Using NordVPN alongside Webroot
Title: Enhancing Online Security: Utilizing NordVPN in Tandem with Webroot
In today's digital age, where cyber threats lurk around every corner of the internet, safeguarding your online activities is paramount. Combining the robust protection of NordVPN with the comprehensive security features of Webroot offers a formidable defense against various online threats.
NordVPN, renowned for its top-tier encryption and global network of servers, ensures that your internet traffic remains encrypted and anonymous. By encrypting your data and masking your IP address, NordVPN shields your online activities from prying eyes, protecting your sensitive information from potential hackers and cybercriminals.
Webroot, on the other hand, is a trusted name in cybersecurity, known for its advanced threat intelligence and real-time protection against malware, phishing attacks, and other online dangers. With its cloud-based approach, Webroot scans websites and files for malicious content, blocking threats before they can infiltrate your device.
By integrating NordVPN with Webroot, users can enjoy a multi-layered defense strategy. NordVPN encrypts your internet connection, ensuring that your data remains secure while in transit. Simultaneously, Webroot safeguards your device from malware and other online threats, providing comprehensive protection from various cyber attacks.
Furthermore, NordVPN's ability to bypass geo-restrictions allows users to access region-locked content securely. Whether streaming your favorite shows or accessing restricted websites, NordVPN ensures that your online activities remain private and unrestricted.
In conclusion, the combination of NordVPN and Webroot offers users a potent defense against online threats. By encrypting your internet connection and providing real-time protection against malware and phishing attempts, this duo provides peace of mind in an increasingly digital world. Whether browsing the web, conducting online transactions, or streaming content, NordVPN alongside Webroot ensures that your online experience is safe, secure, and unrestricted.
Integration of NordVPN and Webroot
NordVPN and Webroot are two powerful tools that, when integrated, offer enhanced security and privacy for users across the globe. NordVPN, a leading VPN service provider, ensures a secure and encrypted connection for internet browsing, protecting users from potential cyber threats and maintaining anonymity online. On the other hand, Webroot is a trusted cybersecurity solution known for its reliable antivirus and anti-malware capabilities, keeping devices safe from malicious attacks and harmful software.
By integrating NordVPN with Webroot, users can benefit from a comprehensive approach to online security. The combination of NordVPN's advanced encryption protocols and Webroot's real-time threat intelligence creates a robust shield against cyber threats, ensuring a safer online experience. Users can browse the internet, access geo-restricted content, and engage in online activities without compromising their security and privacy.
Furthermore, the integration of NordVPN and Webroot simplifies the user experience by providing a single platform for managing both services. Users can easily toggle between VPN settings and cybersecurity features, ensuring seamless protection without any hassle. Additionally, the compatibility of NordVPN and Webroot across various devices and operating systems makes it a versatile solution for users with diverse security needs.
In conclusion, the integration of NordVPN and Webroot offers a potent combination of privacy, security, and convenience for users seeking comprehensive online protection. By leveraging the strengths of both tools, users can enjoy a worry-free browsing experience and stay protected from potential cyber threats in today's increasingly digital world.
Compatibility issues between NordVPN and Webroot
NordVPN and Webroot are both popular cyber security tools used by many individuals and businesses worldwide. However, some users have reported encountering compatibility issues when trying to use these two software together.
One of the common issues reported is that Webroot may sometimes block NordVPN from establishing a secure connection. This can occur due to Webroot's firewall settings or its real-time protection feature, which may view NordVPN's network traffic as a potential threat. As a result, users may experience difficulties in connecting to NordVPN servers or maintaining a stable connection.
Another compatibility issue that users may face is related to performance. Running both NordVPN and Webroot simultaneously can sometimes lead to a decrease in internet speed or overall system performance. This is because both tools consume a certain amount of system resources, and when used together, they may compete for these resources, causing slowdowns or lags.
To address these compatibility issues, users can try adjusting the settings of both NordVPN and Webroot to allow smooth operation. For instance, users can try adding NordVPN as an exception in Webroot's firewall settings or temporarily disabling certain features of Webroot while using NordVPN. Additionally, updating both tools to the latest versions may also help in resolving compatibility issues as developers frequently release updates to improve performance and compatibility.
In conclusion, while NordVPN and Webroot are valuable tools in ensuring online security and privacy, users may encounter compatibility issues when using them together. By being aware of these issues and taking necessary steps to troubleshoot, users can enjoy the benefits of both tools without any hindrances.
Optimizing NordVPN and Webroot usage
Optimizing NordVPN and Webroot Usage
Utilizing NordVPN and Webroot together can provide enhanced security and privacy for your online activities. NordVPN is known for its robust encryption and global server network, which ensures your internet traffic remains secure and anonymous. On the other hand, Webroot offers advanced antivirus protection that safeguards your devices from malware, phishing attacks, and other online threats.
To optimize the usage of NordVPN and Webroot, it is essential to ensure both applications are configured correctly and working in tandem. Firstly, make sure that both NordVPN and Webroot are updated to the latest versions to benefit from the most recent security enhancements and features.
When using NordVPN, connect to a VPN server that is geographically close to your location for optimal speed and performance. Additionally, enable the kill switch feature on NordVPN to ensure that your internet connection is severed if the VPN connection drops unexpectedly, preventing any data leakage.
Webroot's real-time threat protection should be active at all times to proactively detect and block any malicious activity on your devices. Regularly scan your device with Webroot to identify and remove any potential threats.
By combining the strengths of NordVPN and Webroot, you can create a layered defense strategy that fortifies your online security and privacy. Remember to follow best practices such as using strong, unique passwords and being cautious of phishing attempts to further enhance your cybersecurity posture.
0 notes
Text
How Do I Connect Cricut to Computer: A Step-by-Step Guide
How do I connect Cricut to computer? This was a question I got on one of my blogs a week ago. Not only this, but I also received similar questions regarding connection from many readers. Since none of my posts has a complete guide to Cricut connection in one single guide, I tried to write this.
Without thinking twice, dive into this blog and explore the steps one by one. In this blog, I have answered how do I connect my Cricut to my computer via Bluetooth. Let’s start now!
What Do I Need to Connect My Cricut to a Computer?
In order to learn how do I connect Cricut to computer, you have to first understand what you need before connecting to your Cricut. As we know, the connection is a part of the Cricut setup, meaning we are actually setting up our machines. So, there are things that are required before setup. Let’s get a look into it:
Cricut machine
Power cable to connect your Cricut to a wall outlet
A flat surface like a table for keeping the machine on
A Windows/Mac computer with the following system requirements:
For Windows
Operating System – Windows 10 or later (64-bit)
RAM – Minimum 4GB
Disk – 2 GB free
CPU – Intel Dual Core or equivalent to AMD processor
Display – 1024px x 768px screen resolution
Connectivity – A USB port/Bluetooth connection
For Mac
Operating System – macOS 11 or later
CPU – 1.83 GHz
RAM – Minimum 4GB
Display – Minimum 1024px x 768px screen resolution
A USB port or Bluetooth is required
Disk – 2GB
How Do I Connect Cricut to Computer (Windows)?
You will need to set up your Cricut on a Windows PC, which requires a connection. Since the connection is part of the Cricut setup, you must use a compatible Windows PC, such as Windows 10 or a later version. I have explained the easy steps I followed to connect my Cricut to a Windows computer.
Here are the easy steps to connect your Cricut to a computer on a PC:
First, you need to look for a flat surface to place your Cricut.
Here, ensure the distance is no more than 15 feet from the PC.
Afterward, go to the Start menu and select a gear icon to open Settings.
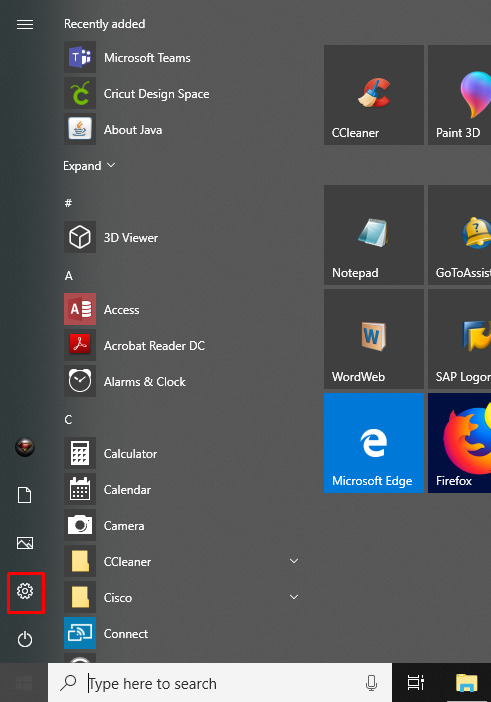
As you click on Settings, you will move to another screen, where you need to click on Devices.
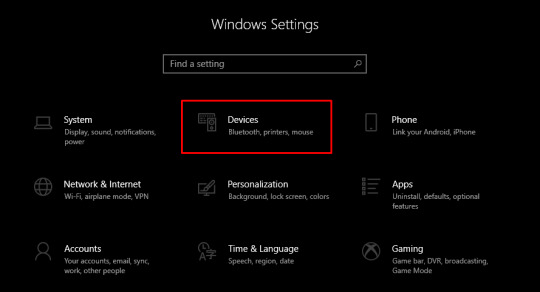
Verify if your Bluetooth is ON, then go to Add Bluetooth or other device.
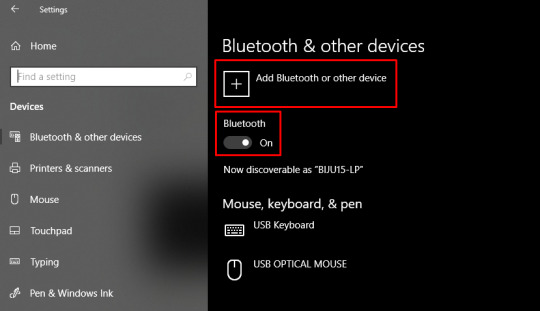
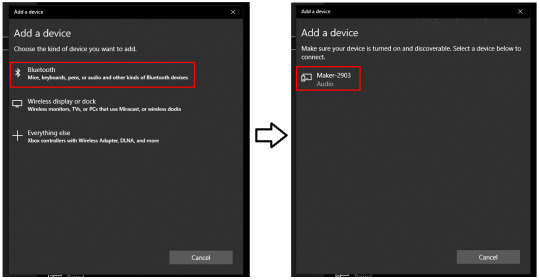
Next, select the Bluetooth option and wait for your PC to detect your Cricut machine.
Select it as it is visible in the open list, and your pairing will be done.
How Do I Connect Cricut to Computer (Mac)?
Mac users need to follow the following steps. However, the placements of Cricut and your computer are almost the same as for Windows. Here are the easy steps to connect your Cricut to a computer on a Mac:
Review if your computer is powered on or off.
After that, move to the Apple menu and choose the System Preferences option.
Now, go to the Bluetooth app on your Mac computer.
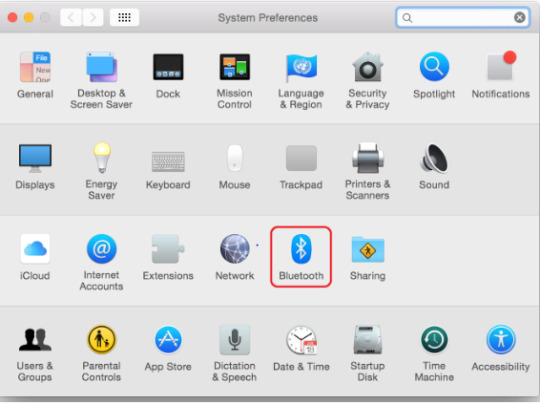
Afterward, turn on the Bluetooth.
Next, select the detected Cricut model from the available list.
Last but not least, you have connected your Mac computer to your Cricut.
FAQs
Question 1: What is the “Connect to Computer via Bluetooth” screen on Cricut?
Answer: The “Connect to Computer via Bluetooth” usually appears during the setup of Cricut Maker 3 or Cricut Explore 3. It happens because the Cricut Design Space app has detected an AMD Ryzen chip on your desktop. Actually, there is a problem with some Windows AMD Ryzen chips that may cause problems when you try to connect your Cricut via a USB cable. Therefore, Cricut recommends you use a Bluetooth connection for these computers.
Question 2: What should I do if my Cricut won’t connect?
Answer: If your Cricut is not connecting to your device, then you need to try the following useful tips:
You need to clear the cache and history of the web browser.
Run a scan on your computer for potential malware.
Defragment the hard disk.
Ensure your firewall or antivirus is blocking Cricut connections.
Question 3: Are all Bluetooth dongles compatible with Cricut machine?
Answer: According to Cricut’s official website, CSR (Cambridge Silicon Radio) Bluetooth dongles are incompatible with the Cricut machine. However, if you want to use a Bluetooth dongle, you need to use one that supports audio devices. Cricut doesn’t guarantee that all dongles will connect to your machine, but those that support audio devices are more likely to be able to connect.
Conclusion
To learn how do I connect Cricut to computer, I have explained all the steps carefully. Before that, I also mentioned things that were required before the Cricut setup. In it, I have especially discussed the system requirements. Make sure your Cricut meets the requirements so that you can do the setup in no time. To have an error-free, smooth connection with the Cricut software, go to this write-up and follow the steps mentioned above.
Read more: install cricut design space app
cricut.com/setup mac
Cricut Design Space
Cricut New Machine Setup
Source: How Do I Connect Cricut to Computer
#How Do I Connect Cricut to Computer#Cricut New Machine Setup#install cricut explore air 2#cricut design space#cricut explore 3#cricut.com/setup#design space signin#cricut.com/setup mac#cricut.com/setup windows
0 notes
Text
Optimizing Your Mac: Strategies for Improving Performance

MacBooks have become more common these days than before with their unbeatable advantages like utmost security and performance. But at times, you might have faced some issues regarding their performance. Such issues can result in frustration and inconvenience during the functioning. Our experts in MacBook repairs Adelaide have come up with the blog ‘Optimizing Your Mac: Strategies for Improving Performance’ to provide an overall idea on what are the reasons behind the slow performance and how can you overcome the issue effortlessly. So, you do not have to be tense next time when you face such an issue!
Why is Your Mac Slow?
If you have come across slow performance with your Mac, you may know the difficulties and the frustration. Well, do you know why does it happen? It can be due to MacBook overheating or other reasons. In the following, let us look in detail at what are the possible reasons behind the slow performance of your Mac.
Insufficient RAM:
If you run out of RAM (Random Access Memory) on your Mac, it starts depending on the virtual memory (disk space used as RAM), which is slower. Processing many apps or heavy tasks tends to immediately become the source of RAM consumption. This can result in low-speed performance and system instability. Ram upgrading of your Mac might be the best way to improve the performance of your Mac, and this is especially true for video editing, gaming and virtual machines.
Outdated Hardware:
Older Mac models, such as models with slower processors, outdated graphics cards, or storage technologies like HDDs (Hard Disk Drives) compared to SSDs (Solid State Drives), may not be able to keep pace with up-to-date software requirements. Switching to a Mac that has newer hardware models and a faster processor can give a significant performance benefit, especially for tasks that require computing power.
Fragmented Hard Drive:
The process of fragmentation happens as a result of computer files being cut into smaller parts and placed into different physical locations across the hard drive. This can slow down file access times as the system needs to collect small fragments scattered across different places. It is recommended that you defragment your hard drive (less important for SSDs) now and then or you can optimize the disk performance with macOS that comes with built-in tools for that.
Insufficient Storage Space:
If your Mac storage capacity is close to full, it affects the system's performance in multiple ways. macOS must have free space needed for tasks like virtual memory, caching, and temporary files. Also, applications can be unable to write or read data, which results in slowdowns and potential system drops. All these issues can be avoided by cleaning space by deleting unimportant files, apps that are not used, and by use of external storage.
Background Processes:
Background processes like system maintenance tasks, antivirus scans, and heavy-resource applications running in the background for a long time could demand CPU resources and memory. This can result in slow performance when you open other tasks as your Mac's hardware specifications may be limited. Monitoring and managing background processes, optimising startup items, and using task manager utilities help to fight these performance issues.
Software Issues:
Some kinds of problems with software like corrupted PCS, incompatible programs and bugs may result in lowered performance, freezing, or the shutdown of the PC. Doing macOS and app updates using the new versions, running system maintenance tasks like disk permissions repair and verifying disk integrity periodically, and getting rid of applications that are causing troubles can help correct software-related performance problems and stabilize the system.
Strategies for Improving Mac Performance
Well, understanding the reasons behind the slow performance of Mac may have made you eager to know their solutions. Here are those:
Look for macOS System Update:
Always make sure to update your version of macOS and install it immediately when available. Apple launches updates to maintain release systems stability, security enhancement, and performance. These upgrades may come with optimizing how the system resources are used, fixing bugs and improving compatibility with software that is new.
Clean All Caches:
Digital media such as games, movies, and music tend to occupy large spaces in your devices and often lead to their slowing down. Regularly clearing caches will free up disk space and improve system performance. They encompass clearing the system’s caches, application caches, browsers’ caches and temporary files. Apps like Disk Utility that are provided by System Apple, in the same manner, can be used or applications like CleanMyMacs which are introduced by third parties.
Upgrade RAM of Your Mac:
A large inflow of RAM, such as in the MacBook Pro, helps to ensure an effective memory pipeline while carrying out data operations and allows running several apps at a time. This quantity resources your Mac to work with many processes and data at once without the necessity of virtual memory (swap space) to be an active participant in the process due to it being slower.
Reset PRAM and SMC Promptly:
The switching of PRAM (Parameter Ram) and SMC (System Management Controller) to their default states, if needed, can help with solving some system-related problems and can increase overall performance. PRAM saves the diverse system settings regarding Screen resolution, startup disk choice, and loudness of the speaker. SMC is a responsible party for hardware-related features such as fan control, power manager and battery. This is a way of solving certain minor issues, which in turn help the system to run at optimal performance again.
Manage Fonts and Extensions:
Limit the number of installed fonts and browser extensions on your Mac. Unused fonts and excessive browser extensions can consume memory and CPU resources, impacting system performance, especially during tasks like graphic design, document editing, or web browsing. Remove or disable unnecessary fonts and extensions to streamline system resources.
Manage Background Processes:
Monitor and manage background processes and tasks to optimize system resources. Use Activity Monitor to identify resource-intensive processes and close or disable them as needed. Limit the number of apps running simultaneously, especially those that consume significant CPU, memory, or disk resources.
#macbook#macbook repair#computer repair#laptop repair#electronic services#iphone repair#macbook service center#adelaide#south australia
1 note
·
View note
Text
Bitdefender vs Webroot: Which Antivirus Software is Better?
Are you regularly facing viruses on your operating system? If yes! Then you must be comparing Bitdefender vs Webroot. According to the famous idiom, "There cannot be two swords in one well," the same applies to antivirus. Bitdefender and Webroot are the most popular antivirus providers that have different features and prices. No doubt, both of them offer the same service, which is to prevent viruses and malware from harming a PC. But choosing the best antivirus program will be a very challenging task.
In earlier times, I used to get tired of frequent viruses, which affected not only my work but also the performance of my PC. But as time passed, I found a permanent solution by choosing a compatible software. In this blog, I will help you choose the best program for your system.
Bitdefender vs Webroot: An Overview
In today's time frame, Bitdefender is one of the most demanding antivirus when it comes to safeguarding systems from cyber threats or viruses ruining the data. Since it entered the market, it has been fulfilling all the users' expectations. Also, it is budget-friendly and built with helpful features that contribute to giving the best performance. No doubt, it is already the best antivirus, but there is a possibility for it to grow and upgrade itself.
On the other hand, Webroot has made its name by being one of the fastest antivirus that utilize the minimum system resources as compared to its rivals. Moreover, it is a lightweight cloud-based antivirus with a good malware scanner, an excellent password manager, and other decent features. It runs in the background without interrupting the existing programs and gives its best shot to protect the system from harmful viruses.
After getting a basic overview of Bitdefender and Webroot, it's time to get a step and come across these antivirus software features.
Bitdefender vs Webroot: Main Differences
On the other hand, Webroot antivirus offers uninterrupted lightning-fast scans. Plus, it gives ransomware protection, real-time anti-phishing, firewall, and network connection monitoring. To use the antivirus, the user needs to sign in and come with a 14-day free trial. Also, Webroot is compatible with the Windows operating system and supports only five devices.
In addition, this antivirus program doesn't authorize parents to block access to adult websites, limit the use of devices to particular times, and many more. Plus, Webroot has a less sleek user interface as compared to Bitdefender. Lastly, this Windows antivirus supports via email, phone, and tickets.
On the contrary, Bitdefender antivirus provides complete and real-time data protection and network threat prevention. In addition, this software is composed of upgraded threat defense, total and real-time data protection, and multi-layer ransom protection. The user doesn't need to sign in and has a one-month free trial.
Furthermore, it supports Windows, Mac, & Android and runs on 15 devices. Besides, Webroot software allows parental control and comes with a sleek and upgraded user interface. Finally, it combines services such as email, phone live support, and training to its customers.
Did you understand the foremost pointers difference between Webroot vs Bitdefender? You should undoubtedly get one of them for your system. Before doing that, I will help you come across the prices of both software.
Bitdefender vs Webroot: Prices
In addition to the blog, before making the final call between Bitdefender and Webroot, pricing plays an important role. It allows the user to choose the correct one that fits their budget. Go through the content given in the tabulated form below:
This table comparing Webroot vs Bitdefender pricing somewhere made you aware of coming to a final decision.
Final Words
As a result of this blog, from these above-said three sections, both of these computer system antivirus software plays a vital role. They have a common aim of protecting the computer from unwanted cyber activity to keep a PC in good performance and maintain its speed while doing any work. However, it's going to be your decision to choose between Bitdefender vs Webroot program for your system.
Frequently Asked Questions
Question: Will Bitdefender Software Slow Down My PC?
Answer: After installing this Bitdefender software on your computer system, your PC might slow down. However, you shouldn't worry as it is slightly normal. If you frequently encounter an issue while accessing the software, you need to uninstall and reinstall the software on your system. Plus, you can also go through the steps given on the user manual or official portal.
Question: How Can I Install Bitdefender Program on My Windows?
Answer: To get the Bitdefender program on a Windows PC, go through the following steps:
Question: How to Install Webroot Software on Windows PC?
Answer: Go through the below steps and get Webroot software on your Windows:
Visit: central.bitdefender.com
bitdefender central login
bitdefender central
Source: https://centralbitdefenderdotcom.wordpress.com/2024/02/07/bitdefender-vs-webroot-which-antivirus-software-is-better/
#bitdefender sign in#central.bitdefender.com#bitdefender central login#bitdefender login#www.central.bitdefender.com#bitdefender#bitdefender.com/activate#bitdefender antivirus#bitdefender central#bitdefender log in#Bitdefender vs Webroot
1 note
·
View note
Text
A Step-by-Step Guide to Recovering Lost Data from Your Computer

Losing data from your computer can be a harrowing experience, whether it's a vital work document, precious photos, or important financial records.
However, with the right approach, much of this lost data can often be recovered. In this comprehensive guide, we'll walk you through the steps you can take to retrieve your lost files.
Understanding Data Loss
Before diving into recovery methods, it's crucial to understand how data loss occurs. Data can be lost due to physical damage to your storage device, software corruption, accidental deletion, or a virus attack.
In many cases, the data isn't actually 'gone'; it's just that your computer can't access it in the usual way.
Step 1: Don't Panic and Stop Using the Affected Device
The first and most important rule is to stop using the device immediately. This is crucial because when data is deleted, it’s not immediately erased. Instead, the system marks the space as available for new data. If you keep using the device, you risk overwriting the lost data, making recovery more difficult.
Step 2: Assess the Situation
Identify what type of data loss you're dealing with:
Accidental deletion: If you've simply deleted files and they’re not in the recycle bin, it’s a straightforward recovery.
Physical damage: If the device is physically damaged (like a failed hard drive), the recovery process is more complicated and might require professional assistance.
Virus attack or software corruption: If data loss is due to malware or software issues, you’ll need to clear the infection or fix the software problem first.
Step 3: Try Basic Recovery Methods
For accidental deletions, start with the simplest solutions:
Check the Recycle Bin: If you haven't emptied the Recycle Bin (or Trash on a Mac), your files could be there.
Use File History or Backup: If you have Windows File History or a similar backup service enabled, you can recover earlier versions of your files.
Step 4: Use Data Recovery Software
If the above steps don’t work, it’s time to try data recovery software. There are many options available, both free and paid, like Recuva, EaseUS Data Recovery Wizard, and Stellar Data Recovery. Here’s how to use them:
Choose the right software: Select a program based on your needs (such as the type of files you want to recover or the file system of your hard drive).
Install on a different drive: To avoid overwriting data, install the software on a drive other than where the lost data was stored.
Follow the software instructions: Run the software and follow the on-screen instructions to scan for and recover your data.
Step 5: Consult a Professional
If you're dealing with physically damaged hardware or complicated data loss scenarios, it’s time to consult a professional data recovery service. They have specialized equipment and expertise to recover data from damaged drives, but be prepared for potentially high costs.
Step 6: Protect Your Data in the Future
Once you’ve dealt with the immediate crisis, it’s time to think about preventing future data loss:
Regular Backups: Regularly back up your data to an external drive or cloud service.
Use Anti-virus Software: Protect your computer from malware and viruses.
Handle Hardware Carefully: Physical damage is a common cause of data loss, so handle storage devices carefully.
Conclusion
Losing data can be stressful, but there's a good chance you can recover much of what you've lost by following these steps.
Remember, the key is to act quickly and not overwrite the lost data. In the long run, preventive measures like regular backups and using antivirus software are your best bet against data loss.
Losing data isn't the end of the world. With patience and the right approach, you can often get back what you thought was lost forever. Remember, preparation and quick action are your best allies in the fight against data loss.
0 notes
Text
Recovering Your Precious Data: A Guide to Mac and RAID Data Recovery in Milwaukee

Losing data, whether on your Mac or a complex RAID system, can be a heart-stopping experience. Memories, work projects, financial records - all seemingly vanished like smoke. But fear not, Milwaukee residents! Data recovery services are here to offer a lifeline, retrieving your precious bits and bytes from the digital abyss.
The Mac Data Dilemma:
Macs are known for their stability, but even they aren't immune to data loss. Accidental deletions, software malfunctions, corrupted files, and physical storage failures can all leave you staring at a blank screen. Fortunately, Milwaukee boasts several reputable Mac data recovery Milwaukee specialists. These companies employ advanced software and hardware tools to meticulously scan your hard drive, SSD, or external storage, reconstructing lost data structures and recovering your files. mac data recovery Milwaukee
RAID Data Recovery in Milwaukee: When Complexity Meets Catastrophe:
RAID systems, designed for redundancy and performance, add another layer to data recovery challenges. If one disk in your RAID array fails, the remaining disks can theoretically keep the system functioning. However, a complete failure or damage to multiple disks can be a data disaster. Thankfully, Milwaukee's data recovery experts are equipped with specialized RAID recovery techniques. They can rebuild the array, identify and repair corrupted data blocks, and ultimately bring your RAID system back to life, along with your valuable data.
Choosing the Right Recovery Partner:
With several options in Milwaukee, choosing the right data recovery service can be overwhelming. Here are some key factors to consider:Expertise: Look for companies with proven experience in Mac and RAID recovery, specifically. Success rates: Ask about their success rate in recovering data from similar cases. Transparency: Choose a company that provides clear pricing estimates and explains the recovery process in detail. Security: Ensure your data is protected by strong security protocols and confidentiality agreements. Turnaround time: Understand the estimated time it will take to recover your data, especially if you have urgent needs.
Taking Action:
If you've suffered data loss, the most important step is to act quickly. Stop using the affected device to minimize further damage. Then, contact a reputable data recovery service in Milwaukee. They will diagnose your situation, provide a free consultation, and offer a tailored recovery plan. Remember, the sooner you act, the higher your chances of successfully retrieving your data.
Beyond Recovery: Prevention Tips:
To avoid future data loss nightmares, consider these preventive measures:Regular backups: Back up your data regularly to an external drive or cloud storage service. Virus protection: Use a robust antivirus program to protect your system from malware. Software updates: Keep your operating system and applications updated to patch vulnerabilities. Safe storage: Store your data in a cool, dry place, away from magnetic fields.
By following these tips and partnering with a reliable data recovery service, you can ensure your precious digital memories and essential files remain safe and accessible. Don't let data loss define your Milwaukee experience - take control and get it back!
#mac data recovery milwaukee#data recovery waukesha wi#data recovery milwaukee#raid data recovery milwaukee#harddrivedatarecoverymilwaukee
0 notes