#Firewall Security Course In Pune
Explore tagged Tumblr posts
Text
Demystifying AWS Virtual Private Cloud (VPC)
In the ever-evolving world of cloud computing, Amazon Web Services (AWS) has established itself as a leader, offering a wide array of services to meet diverse business needs. Among these services, the Virtual Private Cloud (VPC) is one of the most crucial components for organizations seeking to enhance their security and control over their cloud resources. This blog post provides a comprehensive guide to AWS VPC, exploring its features, benefits, and best practices.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is AWS VPC?
AWS Virtual Private Cloud (VPC) allows users to create a private, isolated section of the AWS cloud where they can launch and manage AWS resources. VPC enables businesses to control their virtual networking environment, including IP address ranges, subnets, routing, and security settings.
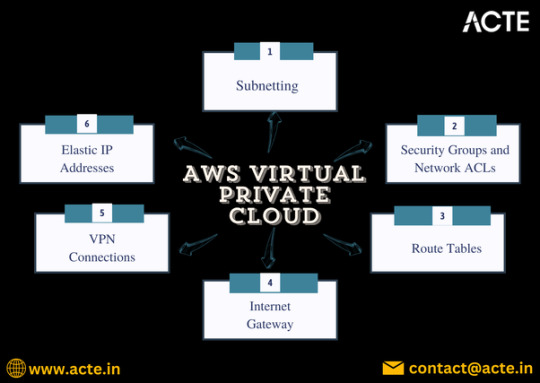
Key Features of AWS VPC
Custom IP Address Range:
When creating a VPC, you can define your own IP address range using Classless Inter-Domain Routing (CIDR) notation. This flexibility allows you to tailor your network architecture to your specific needs.
2. Subnets:
VPCs can be divided into subnets, which are smaller segments within the VPC. You can create public subnets (accessible from the internet) and private subnets (not directly accessible from the internet) to optimize resource security.
3. Security Groups and Network ACLs:
Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic. Network Access Control Lists (ACLs) provide an additional layer of security at the subnet level, enabling more granular traffic management.
4. Route Tables:
Route tables are used to determine where network traffic is directed. You can create custom routing rules to control the flow of traffic between your VPC, subnets, and the internet.
5. Internet Gateway and NAT Gateway:
An Internet Gateway allows communication between instances in your VPC and the internet. A NAT Gateway enables instances in a private subnet to initiate outbound traffic while preventing unsolicited inbound traffic.
6. VPN Connections and AWS Direct Connect:
VPC supports VPN connections, allowing secure communication between your on-premises network and your VPC. AWS Direct Connect provides a dedicated network connection, improving performance and reliability.
7. Elastic IP Addresses:
Elastic IPs are static IP addresses that can be associated with your instances, ensuring consistent public IP addresses even when instances are stopped and restarted.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Benefits of Using AWS VPC
Enhanced Security:
By isolating your resources within a VPC, you gain greater control over your network security. You can implement security measures tailored to your specific needs, enhancing data protection and compliance.
Flexibility:
AWS VPC provides the flexibility to design your network architecture according to your requirements. You can easily adjust your IP address ranges, subnets, and security settings.
Scalability:
VPCs are designed to scale seamlessly. You can add or remove resources as needed, ensuring your infrastructure can adapt to changing workloads without performance degradation.
Cost Efficiency:
With AWS's pay-as-you-go pricing model, you only pay for the resources you use. This makes VPC an economically viable option for organizations of all sizes.
Integration with Other AWS Services:
VPC integrates seamlessly with various AWS services, including Amazon EC2, RDS, and Lambda, allowing you to build comprehensive cloud solutions that meet your business needs.
Conclusion
AWS Virtual Private Cloud (VPC) is a vital service for businesses looking to secure and manage their cloud resources effectively. With its extensive features and benefits, VPC empowers organizations to create a customized and controlled network environment.
By understanding how to leverage VPC and adhering to best practices, businesses can maximize their cloud investment and ensure a robust, secure infrastructure. Whether you're new to AWS or looking to enhance your existing setup, mastering AWS VPC is crucial for success in the cloud.
0 notes
Text
The Ultimate Guide to Different Types of Ethical Hacking
Of all the digital professions out there, few can claim a cooler name than "ethical hacker." As the name implies, ethical hackers are security experts who use their skills to find and fix vulnerabilities within computer systems. These professionals are often hired by companies for various reasons, such as to test their security systems or to ensure compliance with industry regulations.In this post, we'll take a look at some of the most common types of ethical hacking.
Enhancing your career at the Ethical Hacking Course in Pune entails taking a systematic strategy and looking into enrolling in a suitable course that will greatly expand your learning journey while harmonizing with your preferences.

Network Hacking: This type of ethical hacking focuses on identifying vulnerabilities within computer networks. Ethical hackers use various tools and techniques to test the security of network devices, such as routers, switches, firewalls, and servers. By uncovering weaknesses, they help organizations strengthen their network security.
Web Application Hacking: Web applications are a prime target for hackers due to their widespread use and potential vulnerabilities. Ethical hackers specializing in web application hacking analyze websites and web applications to find vulnerabilities that could be exploited by malicious actors. This includes testing for common issues like SQL injection, cross-site scripting (XSS), and insecure direct object references.
Wireless Network Hacking: Wireless networks have become an integral part of our daily lives, but they can also be vulnerable to attacks. Ethical hackers specializing in wireless network hacking focus on identifying weaknesses in Wi-Fi networks, such as weak encryption protocols, default passwords, or misconfigured access points. By doing so, they help organizations secure their wireless infrastructure.
Social Engineering: Social engineering involves manipulating people rather than technology to gain unauthorized access to systems or sensitive information. Ethical hackers use social engineering techniques to test an organization's employee awareness and security protocols. This could include phishing emails, phone calls, or physical attempts to gain access to restricted areas. By enrolling in ethical hacking Online courses, you can gain in-depth knowledge and hands-on experience in these different types of ethical hacking. These courses provide a formal and structured approach to learning, ensuring you acquire the necessary skills to ethically protect organizations from cyber threats. #EthicalHackingCourses #CyberSecurityTraining
Mobile Application Hacking: As mobile devices have become an integral part of our lives, mobile application hacking has gained prominence. Ethical hackers specializing in this area analyze mobile apps for vulnerabilities that could be exploited by attackers. This includes testing for issues like insecure data storage, weak authentication mechanisms, or code tampering.
Physical Security Hacking: Physical security is just as important as digital security. Ethical hackers specializing in physical security hacking assess an organization's physical infrastructure for weaknesses that could lead to unauthorized access. This could involve testing entry points, surveillance systems, or even social engineering attempts to gain physical access to restricted areas.
IoT Hacking: With the rise of the Internet of Things (IoT), ethical hackers are focusing on identifying vulnerabilities within IoT devices and ecosystems. These hackers assess the security of smart devices, such as smart home systems, wearables, or industrial IoT devices, to ensure they cannot be compromised by malicious actors.

In conclusion, ethical hacking is an essential practice for companies that want to ensure the security of their digital infrastructure. By hiring ethical hackers to test their systems, companies can identify and fix potential vulnerabilities before they are exploited by malicious actors. If you're interested in exploring a career in ethical hacking, there are plenty of resources available online to get you started.
0 notes
Text
Unveiling the Expansive Scope of Ethical Hacking in Today’s Cybersecurity Landscape
In an era where data breaches and cyber threats are on the rise, organizations are increasingly turning to ethical hacking as a proactive measure to safeguard their digital assets.

My purpose in being here today is to discuss my exploration of the fascinating realm of hacking. Please fasten your seatbelt and join me as we embark on our hacking journey from the top ethical hacking training institute in pune. We will delve into the expansive scope of ethical hacking and its pivotal role in maintaining robust cybersecurity defenses.
Scope Of Ethical Hacking:
Cybersecurity Assessments: Strengthening the Digital Fortress
One of the primary domains of ethical hacking is conducting comprehensive cybersecurity assessments. Ethical hackers leverage their expertise to perform vulnerability scans, penetration testing, and risk assessments. By identifying weaknesses and vulnerabilities, organizations can fortify their security infrastructure, proactively addressing potential entry points for malicious hackers.
Security Audits: Complying with Standards and Regulations
Ethical hackers play a crucial role in conducting security audits to ensure organizations meet industry standards and regulatory requirements. By assessing security controls, policies, and procedures, ethical hackers help organizations maintain compliance and demonstrate their commitment to data protection. These audits serve as a vital mechanism for maintaining the integrity of systems and protecting sensitive data.
Incident Response and Forensics: Unraveling the Digital Crime Scene

Secure Software Development: Building a Resilient Foundation
Ethical hackers are actively involved in the software development lifecycle, ensuring that security is woven into the fabric of applications. They conduct secure code reviews, assess software architectures, and promote secure coding practices. By actively participating in secure software development, ethical hackers help organizations build robust and resilient systems, reducing the potential for security vulnerabilities.
Cybersecurity Training and Awareness: Empowering the Human Firewall
Ethical hackers contribute to cybersecurity education and awareness initiatives by conducting training sessions, workshops, and awareness programs. Their aim is to educate employees and individuals about recognizing and responding to security threats. By fostering a culture of security, ethical hackers empower organizations and individuals to become the first line of defense against cyber threats.
A peek into my journey from curiosity to aspiring ethical hacker. Hacking is a continuous adventure, and each challenge is a chance to grow.
If you’re keen on ethical hacking, consider enrolling in an Ethical Hacking course in Pune. They often provide certifications, mentorship, and job placement opportunities to support your learning journey.
0 notes
Text
Discover the Benefits of AWS Training Course in Pune for Your Business
Are you looking to take your business to the next level? If so, you may want to consider enrolling in an AWS training course in Pune. AWS, or Amazon Web Services, is a cloud computing platform that offers a wide range of benefits for businesses of all sizes. By enrolling in an AWS training course in Pune, you can gain the knowledge and skills you need to leverage the power of AWS to grow your business.

One of the primary benefits of AWS is its scalability. With AWS, you can easily scale your resources up or down depending on your needs. This means you can quickly respond to changes in demand and avoid overpaying for resources you don't need. Additionally, AWS offers a wide range of tools and services that can help you automate your processes, reduce costs, and improve efficiency.
Another benefit of AWS is its security. AWS offers advanced security features to help protect your data and applications from threats. This includes encryption, firewall protection, and access control. By enrolling in an AWS training course in Pune, you can learn how to implement these security features in your own business to keep your data safe.
Finally, AWS offers a high level of reliability and availability. With AWS, you can ensure that your applications and data are always available to your customers. This is achieved through the use of multiple data centers and redundancy measures. By enrolling in an AWS course in Pune, you can learn how to take advantage of these features to ensure that your business is always up and running.
In conclusion, if you're looking to take your business to the next level, enrolling in an AWS training course in Pune is a great place to start. By gaining the knowledge and skills you need to leverage the power of AWS, you can improve scalability, security, and reliability in your business. So why wait? Sign up for an AWS course in Pune today and start reaping the benefits for your business!
Website:- https://www.ap2v.com
Email Id:- [email protected]
Customer Care No:- +91 9210333323, +91 8448484213
0 notes
Text
Cyber Education and Training
Cyber education and training will be important not only to employees within a business organization but also to the citizens at large.
Short modules, Training camps, workshops for entrepreneurs, school going and college children, housewives, bureaucracy will have to be rolled out on mission mode as India becomes more digital.
Mere compliance protocols and related penal actions will not work – awareness, sensitization and capability building interventions will be the key to develop the necessary culture, mindset and competencies.
Importance of taking up Courses in Cyber Security :
In a digitized system, humans are the most vulnerable elements and not every employee working in an organization is taught to identify malicious emails and how to properly deal with such emails.
These emails contain links or files that, when opened, compromise the system as it contaminates the computer with malware, which then collects sensitive information from the system and can then spread itself across the entirety of the business organisation’s network.
SIICS has been established to offer in the specialized field of bachelor (BSc) of Science in Cyber Security course in Pune & Digital Science, Open Admission 20-21 for Cyber Security Training & Certification in Pune, India. Get detailed information about Bsc diploma in cybersecurity course, college, training institute in Pune after 12th.

Challenge Of Remote Cyber Forensics :
People are scattered and their machines are not in physical control. So, working on managing cybersecurity operations remotely to build a strategy for how you can remotely do forensics or remotely wipe the data.
So, Remote Forensics or Network Forensics or Online Forensics – i.e. performing computer and digital forensics remotely in an enterprise environment will be in demand.
SIICS is providing certification courses of mobile application security course in Pune, Firewall security courses in Pune, cloud security, Data Protection, Data Privacy. Also, SIICS is the best for BSc information security and digital forensics colleges.

Admissions 2021 at Suryadatta International Institute of Cyber Security (SIICS): SIICS invites applications from eligible candidates for admission to the following academic programmes.
B.Sc. Cyber & Digital Science
Eligibility:
Higher secondary school certificate (10+2) or its equivalent examination with English
Or Three-year Diploma course of Board of Technical Education conducted by the government of Maharashtra or its equivalent OR
Higher secondary school certificate (10+2) Examination with English and the vocational subject of +2 level (MCVC)
How to apply?:
The candidates should apply for the application portal on - https://www.siics.org/
#Cyber Education and Training#Bachelor Of Science In Cyber Security Course#Mobile Application Security Course In Pune#Firewall Security Course In Pune#Bsc Information Security & Digital Forensics Colleges
0 notes
Link
SIICS has been established to offer in the specialized field of bachelor (Bsc) of Cyber Security course in pune & Digital Science. Get detailed information about Bsc diploma in cyber security course college training institute in pune after 12th.
#Firewall security course in pune#web application security course in pune#cloud security course in pune#cloud security certification course in pune
0 notes
Photo

Certified Network Defender (CND) Training Institute & Certification Exam Center
The Certified Network Defender (CND) certification program specializes in growing Network Administrators who're skilled on protecting, detecting and responding to the threats on the community. Network directors are usually acquainted with network components, site visitors, overall performance and utilization, network topology, area of every system, security policy, A CND will get the essential know-how of the proper assemble of statistics transfer, community technology, software technology so that the they apprehend how networks operate, understand what software is automating and how to research the concern In addition, the network defense fundamentals, the application of community network security controls, protocols, perimeter appliances, steady IDS, VPN and firewall configuration, intricacies of community site visitors signature, evaluation and vulnerability scanning also are covered if you want to help the Network Administrator design greater community safety rules and successful incident reaction plans.
Certified Network Defender CND training, Certified Network Defender CND training course,Certified Network Defender CND training institute pune,Certified Network Defender CND training in pune
3 notes
·
View notes
Text
How to choose CCNA certification in Pune? / Benefits of enrollment in CCNA certification in Pune
Do you want to get on a roadmap to success? Do you want to grab the opportunity to excel in networking and IT infrastructure professional? If you really wish to grab the ticket to success, then get enrolled for CCNA certification course offered by GNS Technology in Pune and ensure better career prospects.
CCNA- Cisco Certified Network Associate is a certification course for the management and maintenance of the IT infrastructure, offered by Cisco System. Cisco System offers different computer hardware and networking courses which provides in-depth training in routers and networking, CCNA comes with different specializations like Routing and Switching, Service provider operations, Security, Voices, and Wireless. The CCNA Routing and Switching is the gateway for the entry-level jobs in networking and IT careers.
Kick Start Your Career!
If you wish to kick-start your career in Network Security Domain, then get enrolled for CCNA classes in Pune offered by GNS Technologies. The learning center which offers the CCNA courses would prepare the aspirants for getting involved and performing practical on the real Cisco Switches, Routers, and the Firewalls.
The CCNA methodologies are mainly focused on the practical orientation that ensures high exposure to the real-time network situations. The certified and expert trainers offer proper guidance to the aspirants. The learning centers offering CCNA course in Pune gives full-fledged training and proper guidance to the students that help in scaling up the technical skills.

Enrolling for the CCNA security training in Pune does have its own merits! It improves the credential in a resume that supports in leading the career prospects to a high level. Get enrolled at an authentic and registered institute, offering CCNA course and lay a great foundation for your career! For more course details contact us at https://www.gnstechnologies.in
1 note
·
View note
Text
CAREER OPPORTUNITIES AFTER CCNA CERTIFICATION IN NETWORKING
CCNA-Stands for Cisco Certified Networking Associate is a partner level affirmation. Through this confirmation test, you can acquire information to make, oversee and investigate a limited scale organization. There are different tracks in CCNA like CCNA Data Center, CCNA Security, and CCNA Wireless and one can seek after any of this confirmation program to improve their profession amazing open doors.
Recorded underneath are a portion of the top work profiles that are proposed to you after the culmination of the CCNA confirmation test,
Framework Engineers
A System Engineer's significant obligation is to introduce and work the different gadgets in an organization, which includes the different equipment of PCs, switches, switches, and different gadgets. You need to get profound information about the equipment parts of Switches/Routers.
Obligations
The framework architect ought to oversee and screen all the associated framework, and foundation.
Design, introduce, oversee and test working frameworks, framework the executives apparatuses, and application programming.
Proactively secure the most significant levels of frameworks and backing accessibility.
Oversee reinforcement, security, and overt repetitiveness methodologies.
Key abilities:
Cisco Networking.
Network Management Administration.
Windows NT/XP/7 Networking.
Specialized Support Engineer
The primary obligations of the Technical Support Engineer are to tackle client issues through the telephone or by means of remote access.
The IT tech can deal with screens, and keep up with investigating PC frameworks and organizations in an organization.
Obligations
To carry out help and general arrangement of programming.
To finish low-level authority jobs.
Support the testing of inside tasks and applications.
To manage the clients in an in fact productive way.
To give outside client support through email and phone.
Key abilities:
CCNA Course in Pune
Network Support
Microsoft Office
Investigating
Window OS
Network Support Engineer
Network Support Engineer is portrayed as L1 and L2 support engineers. They won't get immediate admittance to switches and switches and furthermore need to help engineers who have direct access.
Obligations:
Oversee tickets, it is signed into the tagging framework by means of Email, Phone or the Web.
Deal with the framework warnings and respond similarly through help tickets.
Support specialized issues are including working frameworks and center business applications.
Fundamental specialized help at the organization level: LAN and WAN, Routers, firewalls, network, and security.
Support Printer and its organizing issues.
The Remote access arrangement can support and carry out VPN.
Work with the merchant for the issues that detailed/noticed.
Key abilities
CCNA Classes in Pune
Window OS
Help Desk
Fundamental Cisco Networking
Framework Troubleshooting
Network Administrator
Systems administration and System Admins are the two different work profiles, however it very well may be similar in certain organizations.
Obligations:
Support and Install, WANs, LANs, Internet, network portions, and intranet frameworks.
Oversee and introduce the organization programming and equipment.
Plan and foster an organization, Perform network address errands.
Allocate type of approval and verification of registry administrations.
Investigating network related issues.
Key Skills:
Essential Linux and Operating System
Windows OS Networking
Cisco CCNA Networking
Network Management and Administration
Network Engineers
It is one of the most well known work profiles in the systems administration field. Network Engineers can function as a piece of the IT Support group in the organization.
Carrying out, keeping up with, planning and dealing with the association's organization and their center liabilities. Abilities with Cisco Networking has a huge impact in this job.
Obligations:
Introduce and arrange the different organization gadgets and administrations, (eg: Switches, firewalls, switches, VPN, load balancers, QoS).
Screen execution and secure accessibility and unwavering quality.
Perform network backing and framework grades including administration patches, packs and security designs.
Screen framework assets use, moving and scope quantification. CCNA Training in Pune
0 notes
Text
Guide to Mastering Ethical Hacking Skills
In an era where cyber threats are rampant, ethical hacking has become an indispensable part of cybersecurity. This blog serves as a comprehensive guide to mastering the essential skills required to become a proficient ethical hacker. Whether you’re a beginner or looking to sharpen your skills, this roadmap will help you navigate your journey.
For individuals seeking to validate their proficiency in Ethical Hacking practices and enhance their career prospects, pursuing the Best Ethical Hacking Course in Pune becomes a strategic imperative. Let’s embark on an exploration into the transformative realm of hacking.

1. Understand the Fundamentals of Cybersecurity
Before diving into ethical hacking, it’s crucial to have a strong grasp of cybersecurity fundamentals. Here’s what you should focus on:
Basic Concepts: Learn about confidentiality, integrity, and availability (CIA triad).
Network Security: Understand firewalls, VPNs, and intrusion detection systems.
Operating Systems: Familiarize yourself with both Windows and Linux environments, as they are commonly used in hacking.
Recommended Resources:
Books: "Cybersecurity Essentials" by Charles J. Brooks.
Online Courses: Look for introductory courses on platforms like Coursera and edX.
2. Learn Networking and Protocols
A solid understanding of networking is essential for ethical hacking. Key areas to study include:
TCP/IP Model: Understand how data is transmitted over networks.
Common Protocols: Get to know HTTP, HTTPS, FTP, and DNS.
Network Devices: Learn about routers, switches, and how they function.
Recommended Resources:
Books: "Networking All-in-One For Dummies" by Doug Lowe.
Online Labs: Try interactive labs on Cisco Networking Academy.
3. Master Programming and Scripting
Programming skills are vital for automating tasks and understanding vulnerabilities. Focus on the following languages:
Python: Widely used in scripting and automation.
JavaScript: Important for web application security.
Bash/Shell Scripting: Useful for automating tasks in a Linux environment.
Recommended Resources:
Interactive Platforms: Codecademy and freeCodeCamp for hands-on programming.
Books: "Learn Python the Hard Way" for a comprehensive introduction.
4. Get Acquainted with Hacking Tools
There are numerous tools that ethical hackers use to assess and exploit vulnerabilities. Familiarize yourself with:
Nmap: For network scanning and enumeration.
Wireshark: A tool for analyzing network traffic.
Metasploit: A framework for penetration testing.
Burp Suite: Essential for web application testing.
Recommended Resources:
Official Documentation: Explore the manuals and user guides for each tool.
Hands-On Labs: Use platforms like Hack The Box and TryHackMe to practice.

For those looking to excel in Ethical hacking, Ethical Hacking Online Training is highly suggested. Look for classes that align with your preferred programming language and learning approach.
5. Obtain Relevant Certifications
Certifications can significantly enhance your credibility in the field. Consider the following:
CompTIA Security+: A foundational certification for cybersecurity professionals.
Certified Ethical Hacker (CEH): Focuses on the tools and techniques of ethical hacking.
Offensive Security Certified Professional (OSCP): A hands-on certification that emphasizes real-world penetration testing skills.
Recommended Resources:
Certification Websites: Visit the official sites for study materials and exam details.
Study Groups: Join online forums or local meetups to collaborate with others.
6. Gain Practical Experience
Hands-on experience is invaluable in ethical hacking. Here are some ways to build your practical skills:
Capture The Flag (CTF) Competitions: Participate in CTF challenges to practice your skills in a competitive environment.
Internships: Seek internships at cybersecurity firms or IT departments to gain real-world experience.
Home Labs: Create your own lab environment using virtual machines to simulate attacks and defenses safely.
7. Stay Updated on Cybersecurity Trends
The cybersecurity landscape is constantly changing, so staying informed is crucial. Here’s how to keep up:
Follow Industry News: Subscribe to cybersecurity blogs and websites like Krebs on Security and Threatpost.
Join Online Communities: Engage in forums such as Reddit or specialized cybersecurity groups.
Attend Conferences: Participate in events like DEF CON and Black Hat to network and learn about the latest trends.
8. Develop Soft Skills
In addition to technical proficiency, soft skills play a vital role in your success as an ethical hacker:
Problem Solving: Cultivate critical thinking and analytical skills.
Communication: Learn to explain technical concepts clearly to both technical and non-technical audiences.
Team Collaboration: Work effectively with other professionals in multidisciplinary teams.
Conclusion
Mastering ethical hacking skills is a rewarding journey that requires dedication, continuous learning, and practical application. By following this guide, you’ll be well-equipped to navigate the complexities of ethical hacking and contribute to a safer digital world. Start honing your skills today, and take your first step toward becoming an ethical hacking expert!
1 note
·
View note
Text
8 Benefits of Outsourced Accounting Services

Accounts Outsourcing Services have become a great alternative for even the largest of companies these days, but are they really all that great? We're biased, thus we believe so. Here are eight reasons why you may wish to think about employing a virtual accounting team.
#1 - Pre-built Processes
Employing Accounts Outsourcing Services in Pune means you're buying into efficient processes provided that the company you work with is established and has an established history. They are going to have systems in place for reconciliation, invoicing, bill pay, and more. Easy.
#2 - Technology
Online accounting businesses have to be streamlined in order to do their jobs. Without the current technologies, it would not be possible to handle all of the information, bills, and much more. This means that you get access to all of the best tools.
#3 - Expertise
An Accounts Outsourcing Companies in Pune will have many clients in many businesses giving them a view of best practices across multiple disciplines. Implementing that experience to your company is invaluable.
#4 - Privacy
When you hire in-house, you've got someone on the inside that knows all of the payroll data and other information that may cause damage to your business's culture. By utilizing an online bookkeeper, that threat is eliminated entirely.
#5 - Security
If you work with an established team such as Ignite Spot Accounts Outsourcing Services in Navi Mumbai, then you'll get access to a package of safety measures to protect your data. For instance, we use Last Pass to protect all of your passwords and login data. We also have firewall and station-by-station, virus managers. We also implement a separation of responsibilities policy so that no trade runs its whole course via one pair of eyes.
#6 - Rate
Accounting is a method. When you employ a digital accounting group, they are encouraged to get the job done and to do it correctly the first time. Unlike workers who can lounge around, work overtime, and whine about constraints -- your outsourced team has an agenda and an outcome. This is especially true when the business that you choose charges a set monthly fee such as Ignite Spot. We don't bill by the hour. It keeps us motivated and focused.
#7 - The Cost
Everybody knows that outsourced accounting solutions are more reasonably priced than an in-house accounting group but by how much? That all depends on what state you live in and how much service you need. Normally, we see companies save 30% to 40%.
#8 - It's All Under One Roof
Some businesses will be complete support, which means that you can find both tax preparation providers and CFO services out of them too. If that's the case, you just have one telephone number to call for all your accounting needs. That's a potent combination.
Conclusion
Outsourced accounting solutions are a terrific option for companies interested in scaling expansion with a finance team in step. These seven benefits will make a huge difference to your organization and the bottom line.
#accounts outsourcing services in Pune#accounts outsourcing companies in pune#accounts outsourcing pune#accounting services in navi mumbai#accounting companies in Navi Mumbai#Accounts outsourcing services in Navi Mumbai
0 notes
Text
Unveiling the Expansive Scope of Ethical Hacking in Today’s Cybersecurity Landscape
In an era where data breaches and cyber threats are on the rise, organizations are increasingly turning to ethical hacking as a proactive measure to safeguard their digital assets.

My purpose in being here today is to discuss my exploration of the fascinating realm of hacking. Please fasten your seatbelt and join me as we embark on our hacking journey from the top ethical hacking training institute in pune. We will delve into the expansive scope of ethical hacking and its pivotal role in maintaining robust cybersecurity defenses.
Scope Of Ethical Hacking:
Cybersecurity Assessments: Strengthening the Digital Fortress
One of the primary domains of ethical hacking is conducting comprehensive cybersecurity assessments. Ethical hackers leverage their expertise to perform vulnerability scans, penetration testing, and risk assessments. By identifying weaknesses and vulnerabilities, organizations can fortify their security infrastructure, proactively addressing potential entry points for malicious hackers.
Security Audits: Complying with Standards and Regulations
Ethical hackers play a crucial role in conducting security audits to ensure organizations meet industry standards and regulatory requirements. By assessing security controls, policies, and procedures, ethical hackers help organizations maintain compliance and demonstrate their commitment to data protection. These audits serve as a vital mechanism for maintaining the integrity of systems and protecting sensitive data.
Incident Response and Forensics: Unraveling the Digital Crime Scene

Secure Software Development: Building a Resilient Foundation
Ethical hackers are actively involved in the software development lifecycle, ensuring that security is woven into the fabric of applications. They conduct secure code reviews, assess software architectures, and promote secure coding practices. By actively participating in secure software development, ethical hackers help organizations build robust and resilient systems, reducing the potential for security vulnerabilities.
Cybersecurity Training and Awareness: Empowering the Human Firewall
Ethical hackers contribute to cybersecurity education and awareness initiatives by conducting training sessions, workshops, and awareness programs. Their aim is to educate employees and individuals about recognizing and responding to security threats. By fostering a culture of security, ethical hackers empower organizations and individuals to become the first line of defense against cyber threats.
A peek into my journey from curiosity to aspiring ethical hacker. Hacking is a continuous adventure, and each challenge is a chance to grow.
If you’re keen on ethical hacking, consider enrolling in an Ethical Hacking course in Pune. They often provide certifications, mentorship, and job placement opportunities to support your learning journey.
0 notes
Text
Troubles with solution you may face with AWS
Troubles with solution you may face with AWS
1. Billing Complexity
AWS has a first-rate flaw in its billing device, which can be quite complex and complicated for small non-technical commercial enterprise proprietors.
But, this problem may be mitigated with the aid of working with a reseller who can offer a extra trustworthy and comprehensible invoice or billing.
AWS course in pune
2. Resource obstacles
AWS limits resources via region, that may effect your get right of entry to to resources primarily based on place. As a brand new user, AWS also imposes regulations to prevent excessive resource usage and to guard towards malicious reason.
Although facts regarding resource utilization can be limited, aid increases can be requested if needed.
Three. Cloud troubles
Migrating to cloud computing can bring about issues which include backup safety, hazard of information leakage, privateness troubles, safety, downtime, and constrained manage. However, those problems are not particular to AWS and are common amongst cloud computing corporations.
AWS is aware the significance of securing these issues and has measures to cope with them, ensuring that your business won’t need to address them.
Don’t permit the complexity of AWS intimidate you – Cloudways has got your returned!
Our person-pleasant platform makes it clean to host your website on AWS, with out the need for technical understanding. Say good-bye to confusion and frustration and hey to seamless AWS website hosting with Cloudways.
AWS classes in pune
The simple answer – managed web hosting
The reputedly huge problem of loss of time or knowledge to manage servers has a simple answer – managed Amazon web hosting. Controlled web hosting providers flip barebone infrastructures into the right answer for AWS for beginners.
Managed Amazon website hosting providers build their infrastructure on pinnacle of AWS, leveraging the power and versatility of AWS for all their clients. In almost all instances, these clients experience a controlled revel in that takes away the complexities of the AWS infrastructure while allowing get entry to to the energy of the AWS servers.
These offerings cowl the whole AWS revel in spectrum, from server advent to protection. Whilst the specifics and transport of the offerings fluctuate from vendor to seller, the simple presenting are quite similar.
Some blessings of the use of managed Amazon hosting encompass:
Simplified server setup system thru a person-pleasant one-page form, with provisioning taking only a few minutes.
Get entry to to powerful AWS infrastructure and its features without the want to manipulate its complexities.
A wide range of application options, such as famous picks like WordPress, Magento, and php.
Consumer-pleasant portals with factor-and-click interfaces for coping with servers and deployed packages.
Easy and fast hosting enjoy for users, with selections for adding and doing away with cache subsystems, databases, and related functions.
Safety approaches like firewalls and intruder detection systems (IDS) are managed via the carrier issuer, ensuring a secure hosting environment.
Customers can cognizance on their programs with out worrying about dealing with the underlying infrastructure or losing time on complex server control.
In case you’re a startup, here’s why AWS can be a recreation changer.
AWS training in pune
Summary
Amazon’s AWS cloud computing provider is comfortable, and it's far right here to help you in decreasing your commercial enterprise statistics infrastructure costs. Consequently, opting for AWS cloud offerings will gain your company and assist you to exponentially scale your enterprise on a leading cloud infrastructure platform.
With a bit of luck, you learned a excellent deal from our AWS for beginners guide. Let us realize in case you overlooked anything well worth sharing inside the comments section underneath.
SEVENMENTOR
0 notes
Text
Best Career Opportunity for an Engineering Students
Pune is the second largest city in the Indian state of Maharashtra and the seventh most populous city in the country. Pune is a city of knowledge and often known as the Oxford of the east. In Marathi, it is known as “vidyeche maherghar” which means, the hometown of education. In Pune, there are lots of engineering colleges so that it’s difficult to choose for students. I want to improve knowledge of students who take an admission for an engineering after 12th.
List of Engineering Departments:
1. Electronics & Telecommunication Department:
The program of the department is an undergraduate course in Electronics and Telecommunications. Department also offers Post Graduate course (M.E.) in Electronics and Telecommunications with specialization as Communication Network. Most of the faculties are doing research work on the latest area such as Image Processing, Cognitive radio and Wireless Communication, Network Security etc.
The department has six laboratories equipped with latest software and hardware. All the computers are connected to LAN. Internet leased line of 6 Mbps is available. The department has the latest software such as MATLAB Software with Simulink, Signal Processing, DSP block, Image Processing, the Lab view professional development system for windows, MultiSim, Triton, Xilinx, Proteus and Quick Heal Admin Console 4.2 ver. Berkley wireless LCD projector, Toshiba LCD projector and ASK C2 Compact Onida LCD Projector. The department has high-performance computing facility such as IBM X3650 server, firewall, routers, etc.
2. Computer Engineering Department:
Department also offers Post Graduate course (M.E.) in Computer Engineering and Ph. D. in Computer Engineering under the ambit of University of Pune. The department has 10 laboratories equipped with the latest software such as Oracle 10G, Microsoft School Campus, IDASM, Rational Software Architecture, and hardware. All the computers are connected on LAN with high Bandwidth Internet leased line facility. The department has high-performance computing facility such as IBM X3400 servers, firewall, routers, etc.
3. Instrumentation Engineering Department:
The Department has been accredited thrice by National Board of Accreditation (NBA). Department has highly qualified and devoted staff. The Department is associated with research work and has received the Research Project grant from the University of Pune as well as grand in aid from AICTE under MODROB Scheme. The Department emphasizes on augmenting technical skills of students through practical implementation of ideas. The department has successfully conducted National Conference on Signal Processing and Automation (NCSPA) for academic excellence.
4. Mechanical Engineering Department:
The department is also offering M.E. (Design engineering) and Ph.D. The department is of vital importance, being located in a cluster of mechanical engineering based industries. The department has a team of well qualified, experienced, energetic and result oriented faculty having wide exposure to the industry as well as academics. Many faculty members have research experience in fields like Design, Thermodynamics, Hydraulics, Production Technology and Metallurgy.
5. Civil Engineering Department:
Civil engineering is the oldest engineering discipline. This department is endowed with a high caliber, dedicated, well qualified and experienced team of professionally inclined faculty. Currently, various laboratories are being developed with the state of art technology to impart the advanced knowledge to our students. To sustain global competition, innovative techniques will be utilized to expose the students to the latest trends and practices in the construction industry through various activities like site visits, seminars by experts from fields and technical projects.
6. Electrical Engineering Department:
The department is committed to the advancement of the frontiers of knowledge in Electrical Engineering and to provide the students with a stimulating and rewarding learning experience. The Department of Electrical Engineering has the excellent team of highly qualified and experienced faculty and non-teaching staff. The department has fully equipped laboratories with the latest technology and has excellent computational facilities. World class software like MATLAB, Simulink, PSCAD, ETAP, MULTISIM, PSIM, Lab view is available in the department to work on top-of-the-line projects in various areas of electrical engineering. The Department has strong Industry interaction and has been involved in the development of state-of-art products for Industry. It has extensive fabrication, calibration and testing facilities for carrying out industry-sponsored research and consultancy projects.
Infrastructure:
The college is located at Pimpri in the heart of Pimpri-Chinchwad industrial belt. The campus has well ventilated, spacious classrooms, seminar rooms, laboratories, library, administrative block and conference hall. The campus provides the in-house Xeroxing facility, bank, student's consumer Co-operative Society, cafeteria etc.
The central computer center has structured networking and server with an adequate number of terminals. All the software required for academic purposes and day to day work are available. The peripherals like printer, scanner, speakers, CD-ROM drive, and webcam also available. The Institute has 24-hour leased line facility for all the students and staff. The internet workstation is centrally connected with the structured network having a state-of-the-art server, printing facility and Wi-Fi. Separate hostel accommodation is available for the boys and girls in close vicinity of the college. Rooms are well furnished. The hostel has a canteen, mess, STD facility, TV room, medical facility and even an ATM. 24 hours medical facilities are available at Dr. D. Y. Patil Medical College, Hospital in a vicinity of the campus. Bank of Maharashtra with ATM facility is available in vicinity of the campus
Dr. D. Y. Patil Institute of Technology, Pune is the best engineering college in Pune, located in Sant Tukaram Nagar, Pimpri. All branches are affiliated to Savitribai Phule Pune University.
#Engineering College#Engineering College in Pune#Engineering College in Pimpri-Chinchwad#Best Engineering College in Pimpri-Chinchwad#Best Engineering College in Pune#Best Engineering College in Maharashtra#Best Engineering College in India#Top Engineering College in Pune#Top Engineering College in Maharashtra#Top Engineering College in India
0 notes
Text
Security Testing: A Critical Part of Software Testing
April 4, 2017
Software Testing
,
software testing course in pune
,
software testing in pune
,
software testing institute in pune
,
Software Testing Jobs
,
Software Testing Trends
,
Types Of Testing
,
understanding the benefits and risk of independent test
best software testing institute
,
best software testing training institute in pune
,
Security testing:
,
Software Testing
,
software testing course
,
software testing institute in pune
,
software testing job in pune
,
testing classes in pune
Edit
Security testing is an important part of software testing and is included in the curriculum of most of the software testing courses in Pune. Look out for a software testing course in Pune with placement. This would help you in getting a job in this field.
Now,
Let’s get into the various aspects related to security testing.
Security testing fundamentally refers to a type of software testing that is done to check whether the application or the software is secured or not. It verifies whether the application is powerless against attacks, in the event that anybody hacks the framework or login to the application with no prior approval or authority.
It basically is a type of non-functional testing.
Security testing characteristics:
The six basic parameters that need to be covered under security testing are as follows:
– Integrity- The application and related data is authentic.
– Authentication- Data is genuine or not and the application origin.
– Availability- As the name suggests, this tests the accessibility of the software application i.e. it is dependably up and running, data and administrations are accessible at whatever point required. Likewise, this incorporates the bckup records which are promptly accessible of any disappointment happens.
– Confidentiality- Data or information is protected from theft.
– Authorization- Certain users should have access to authorized functions only.
– Non-repudiation- Assurance that the receiver and sender of information can’t deny the fact of having sent or received the data.
It is a process to discover that a information framework protects information and keeps up functionality as proposed.
Software security is about making software carry on in the sight of a malicious attack.
The security testing is carried out to check whether there is any data spillage in the sense by encrypting the application or utilizing extensive variety of softwares and hardwares and firewall and so forth.
For a software testing job in Pune, search on the various job portals.
Security testing is a huge subject. Each technology that you utilize, regardless of whether it’s a programming language like .NET or PHP or an element like input validation or authentication, presents another arrangement of security vulnerabilities. Today, we are occupied with giving you a fundamental idea of what security testing is and how it is performed.
Security testing must begin at an early stage to limit defects and cost of quality. It is a decent practice to begin security testing at the time of prerequisite assembling, this guarantees quality of the finished product will be high.
There is no standard approach to test the security of an application, it absolutely relies upon the reason it serves and what are the security hazards present in it. Each time begin security testing by testing the UIs, this is the primary spot of entry for hackers and unlawful users. At that point think what a hacker would likely do in the event that he gets the access or entry into the system, regardless of whether he will steal the credit card data or get access to some personal files and so forth begin some destructive testing i.e. to test what application or system can’t do and after that focus on the error messages you get. When you are finished with every one of these sorts of testing, attempt and burrow further and see what could be the escape clauses with regards to security at the coding level. With some experience, you will have the capacity to perform security testing in a better manner.
Security testing happens to be an important part of software testing and cannot be ignored at any cost. Testing classes in Pune can give you a detailed insight into security testing.
#software testing institute in Pune#software testing course#software testing in pune#software testing jobs#best software tetsing institute in pune#software testing institute
0 notes
Text
Red Hat Linux Certifications that must perform
Linux classes in pune
Following would be the Red Hat Linux Certifications that must perform
Red Hat Certified System Administrator (RHCSA), is an entrance certification course that covers Linux demands (RH124), Linux direction (RH134) that centers on actual efficiencies in system administration, including installation and configuration of a Red Hat Enterprise Linux application and attach it into a live program operating system solutions.RHCE is a midsize array to advanced-level certification course that covers Linux community and safety (RH254) that builds on topics covered in the RHCSA certification to include more complex topics such as installing and safety shared venture media (IP) services.
Intro To Linux, Getting the management line, Manage Documents in the command line, Get Help at a Red hat Enterprise LinuxCreating, Viewing and editing the text files. Administer Groups and Clients Controlling Access files with Linux file system permissions
Installing and upgrading software PackagesAccessing Linux file systems. Managing Temporary Files and Managing Priority of Linux ProcessesControlling Access to Records together with Access Control Lists (ACLs). Managing SELinux SecurityLinking into Network-defined Users and Groups.
Review for this course Boost command line Controls using innovative features of the bash shell scripts, and utilities, and economically provided by Red Hat Enterprise Linux.
Schedule prospective jobs Schedule controls to function in the near or on a program.
Linux Training in pune
Tune system performance Boost system performance by adjusting the scheduling priority of processes and setting tuning parameters. Control access to files with ACLsInterpret and set access control lists (ACLs) on files to look after situations requiring complex user and group access permissions. Manage SELinux security
Protect and manage the protection of a server utilizing SELinux.Maintain basic storageCreate and manage storage devices, partitions, file systems, and change spaces at the management line. Handle logical volumesProduce and handle volumes containing swap spaces and document systems. Storage features advanced Manage storage using the Stratis storage management system that's neighborhood and use VDO volumes to optimize storage space. Control the boot Procedure Manage services to be controlled with the boot process and to mend and fix problems. Manage network security
Control network connections to suppliers using SELinux rules along with also the machine firewall.
Linux courses in pune
0 notes