#Entra Cloud Sync
Explore tagged Tumblr posts
Text
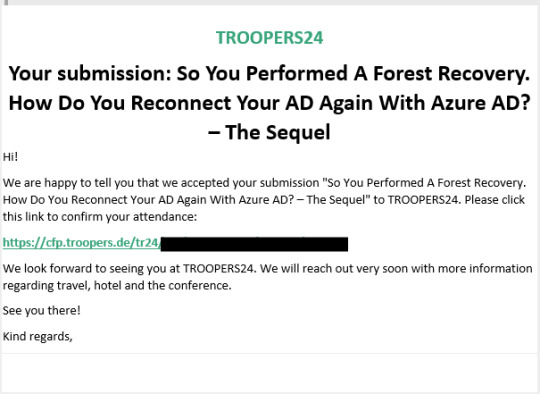
(2024-05-01) Delivering A Demo About Reconnecting AD Back With Entra ID At "Troopers 2024"
Very proud (again!) to have been selected again to present at Troopers 2024! Somewhere in the week of June 24th – 28th, I will be challenging the demo gods for a full hour. Let’s just hope everything goes as planned! Last year at Troopers I presented about the “Best Practices for Resynchronizing AD and Entra ID After Forest Recovery”. This year, I will actually show you how this can be done for…
View On WordPress
#Active Directory#cybersecurity#Disaster Recovery#Entra Cloud Sync#Entra Connect Sync#Fixing Identity Data#GAP Analysis#PowerShell#Ransomware#Security#Tooling/Scripting
0 notes
Text
Entra ID Lateral Movement And Expanding Permission Usage

Abusing Intimate Permissions for Lateral Movement and Privilege Escalation in Entra ID Native Environments: (In)tune to Takeovers
Recently, a client received assistance from the Mandiant Red Team in visualizing the potential consequences of an advanced threat actor breach. In order to compromise the tenant’s installed Entra ID service principals, Mandiant migrated laterally from the customer’s on-premises environment to their Microsoft Entra ID tenant during the evaluation.
Using a popular security architecture that involves Intune-managed Privileged Access Workstations (PAWs), we will discuss in this blog post a new method by which adversaries can move laterally and elevate privileges within Microsoft Entra ID by abusing Intune permissions (DeviceManagementConfiguration.ReadWrite.All) granted to Entra ID service principals. We also offer suggestions and corrective actions to stop and identify this kind of attack.
A pretext
The client had a well-developed security architecture that adhered to the Enterprise Access model suggested by Microsoft, which included:
An Active Directory-based on-premises setting that adheres to the Tiered Model.
A Microsoft Entra Connect Sync-synchronized Entra ID environment that synchronizes on-premises identities and groups with Entra ID. PAWs, which were completely cloud-native and controlled by Intune Mobile Device Management (MDM), were used to administrate this environment. They were not connected to the on-premises Active Directory system. To access these systems, IT managers used a specific, cloud-native (non-synced) administrative account. These cloud-native administrative accounts were the only ones allocated Entra ID roles (Global Administrator, Privileged Role Administrator, etc.).
A robust security barrier was created by separating administrative accounts, devices, and privileges between the Entra ID environment and the on-premises environment:
Because Entra ID privileged roles are associated with unique, cloud-native identities, a compromise of the on-premises Active Directory cannot be utilized to compromise the Entra ID environment. This is an excellent practice for Microsoft.
An “air gap” between the administration planes of the two environments is successfully created by using distinct physical workstations for administrative access to cloud and on-premises resources. Attackers find it very challenging to get through air gaps.
Strong Conditional Access regulations imposed by Privileged Identity Management assigned roles to the administrative accounts in Entra ID, necessitating multi-factor authentication and a managed, compliant device. Additionally, Microsoft recommends these best practices.
Attack Path
One of the objectives of the evaluation was to assign the Mandiant Red Team the task of obtaining Global Administrator access to the Entra ID tenant. Mandiant was able to add credentials to Entra ID service principals (microsoft.directory/servicePrincipals/credentials/update) by using a variety of methods that are outside the purview of this blog post. This gave the Red Team the ability to compromise any preloaded service principal.
There are a number well-known methods for abusing service principal rights to get higher permissions, most notably through the usage of RoleManagement.See AppRoleAssignment and ReadWrite.Directory.Application and ReadWrite.All.ReadWrite.All rights for Microsoft Graph.
However, the Mandiant Red Team had to reconsider their approach because none of these rights were being used in the customer’s environment.
Mandiant found a service principle that was given the DeviceManagementConfiguration after using the superb ROADTools framework to learn more about the customer’s Entra ID system.Go ahead and write.Permission is granted.Image credit to Google Cloud
The service principal is able to “read and write Microsoft Intune device configuration and policies” with this authorization.
Clients running Windows 10 and later can execute the unique PowerShell scripts used by Intune for device management. Administrators have an alternative to configuring devices with settings not accessible through the configuration policies or the apps section of Intune by using the ability to run scripts on local devices. When the device boots up, management scripts with administrator rights (NT AUTHORITY\SYSTEM) are run.
The configuration of Device Management.Go ahead and write.To list, read, create, and update management scripts via the Microsoft Graph API, all permissions are required.
The Microsoft Graph API makes it simple to write or edit the management script. An example HTTP request to alter an existing script is displayed in the accompanying figure.PATCH https://graph.microsoft.com/beta/deviceManagement/ deviceManagementScripts/<script id> { "@odata.type": "#microsoft.graph.deviceManagementScript", "displayName": "<display name>", "description": "<description>", "scriptContent": "<PowerShell script in base64 encoding>", "runAsAccount": "system", "enforceSignatureCheck": false, "fileName": "<filename>", "roleScopeTagIds": [ "<existing role scope tags>" ], "runAs32Bit": false }
The caller can provide a display name, file name, and description in addition to the Base64-encoded value of the PowerShell script content using the Graph API. Depending on which principle the script should be run as, the runAsAccount parameter can be set to either user or system. RoleScopeTagIds references Intune’s Scope Tags, which associate people and devices. The DeviceManagementConfiguration can likewise be used to construct and manage them.Go ahead and write. Permission is granted.
The configuration of Device Management.Go ahead and write.By changing an existing device management script to run a PowerShell script under Mandiant’s control, Mandiant was able to go laterally to the PAWs used for Entra ID administration with full authorization. The malicious script is run by the Intune management script when the device reboots as part of the user’s regular workday.
By implanting a command-and-control device, Mandiant could give the PAWs any instructions. The Red Team obtained privileged access to Entra ID by waiting for the victim to activate their privileged role through Azure Privileged Identity Management and then impersonating the privileged account (for example, by stealing cookies or tokens). By taking these actions, Mandiant was able to fulfill the assessment’s goal and gain Global Administrator rights in Entra ID.
Remediation and Recommendations
To avoid the attack scenario, Mandiant suggests the following hardening measures:
Review your organization’s security principals for the DeviceManagementConfiguration.ReadWrite.All permission: DeviceManagementConfiguration should be handled by organizations that use Microsoft Intune for device management.Go ahead and write.Since it grants the trustee authority over the Intune-managed devices and, consequently, any identities connected to the devices, all permissions are considered sensitive.
Mandiant advises businesses to routinely check the authorizations given to Azure service principals, with a focus on the DeviceManagementConfiguration.Along with other sensitive permissions (like RoleManagement), there is the ReadWrite.All permission.See AppRoleAssignment and ReadWrite.Directory.Application and ReadWrite.All.ReadWrite.All.
Businesses that manage PAWs with Intune should exercise extra caution when assigning Intune privileges (either via DeviceManagementConfiguration).Use Entra roles like Intune Role Administrator or ReadWrite.All.
Enable Intune’s multiple admin approval: Intune allows you to use Access Policies to demand a second administrator’s approval before applying any changes. By doing this, an attacker would be unable to use a single compromised account to create or alter management scripts.
Think about turning on activity logs for the Microsoft Graph API: Graph API Activity logs, which provide comprehensive details about Graph API HTTP requests made to Microsoft Graph resources, can be enabled to aid in detection and response efforts.
Make use of the features that Workload ID Premium licenses offer: With a Workload-ID Premium license, Mandiant suggests using these features to:
Limit the use of privileged service principals to known, reliable places only. By guaranteeing that only trustworthy places are used, this reduces the possibility of unwanted access and improves security.
Enable risk detections in Microsoft Identity Protection to improve service principal security. When risk factors or questionable activity are found, this can proactively prohibit access.
Keep an eye on service principal sign-ins proactively: Monitoring service principal sign-ins proactively can aid in identifying irregularities and possible dangers. Incorporate this information into security procedures to set off notifications and facilitate quick action in the event of unwanted access attempts.
Mandiant has a thorough grasp of the various ways attackers may compromise their target’s cloud estate with some hostile emulation engagements, Red Team Assessments, and Purple Team Assessments.
Read more on Govindhtech.com
#EntraID#EntraIDLateral#Lateral#Mandiant#MicrosoftEntraID#RedTeam#Windows10#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
3 notes
·
View notes
Text
TIM Beta suspende novas adesões em Santa Catarina; Claro e TIM mudam planos
Usuários do TIM Beta nos DDDs 47, 48 e 49 foram informados via SMS que não receberão convites nesta rodada, e o site oficial informa que o plano não está disponível para adesão nos DDDs de Santa Catarina. O motivo é a lei 17.691/2019, que entra em vigor nesta segunda-feira (15) e impede que operadoras incluam assinatura de serviços dentro da mensalidade. Outros planos da TIM e Claro também foram modificados no estado devido à legislação.
TIM Beta reformula Blablablâmetro e redes sociais deixam de contar pontos
Anatel exigirá mais que CPF no cadastro de linhas celulares para evitar fraudes
Parece drástico retirar o plano apenas de uma única região enquanto poderiam criar uma versão sem os serviços de valor agregado (SVAs), mas a TIM optou pela primeira opção.
O Tecnoblog questionou a operadora sobre o motivo da remoção dos convites, mas ela apenas informou que “os convites para entrada de novos clientes nas ofertas do TIM Beta não serão distribuídos nesta rodada em Santa Catarina, em razão do cumprimento da Lei 17.691/2019, que começou a vigorar hoje (15/4) no Estado”.
E essa agora do Tim Beta? Cc @Tecnoblog pic.twitter.com/6mFnNyV1LG
— #ETC (@epictimechat) April 13, 2019
A lei foi baseada no projeto 296/2018 do deputado estadual Marcos Vieira (PSDB). A justificativa que o projeto irá proteger o consumidor da venda casada. O parlamentar também aponta que, na prática, o governo deixa de arrecadar com impostos que possuem “função social… para a satisfação dos interesses coletivos”.
Um recurso foi apresentado pela Abrafix (Associação Brasileira de Concessionárias de Serviço Telefone Fixo Comutado) e pela Acel (Associação Nacional das Operadoras Celulares), que questionam a constitucionalidade da lei. No entanto, o processo ainda aguarda julgamento no STF.
No passado, o Sinditelebrasil — sindicato que representa as operadoras — se posicionou de forma contrária à lei aprovada: “a Constituição Federal define que é prerrogativa exclusiva da União, e não dos Estados, legislar sobre telecomunicações”.
“De acordo com a Lei 17.691/2019, novos clientes dos DDDs 47, 48 e 49 não estão elegíveis ao plano TIM BETA”
Outros planos da TIM sofreram alterações
A TIM também alterou os outros planos para o estado de Santa Catarina. No pós-pago TIM Black, além de remover os serviços de valor agregado, a operadora diminuiu a franquia de internet; deixou de incluir a franquia exclusiva para serviços de vídeo; e retirou o zero-rating de redes sociais, deixando apenas o WhatsApp sem descontar do pacote de dados.
Este é o TIM Black em Santa Catarina…
… e as opções de pós-pago em São Paulo:
O TIM Controle deixou de incluir SVAs e redes sociais, mas a opção de R$ 64,99 ainda inclui Messenger, Telegram, Waze, Easy Táxi e WhatsApp sem descontar da franquia.
O TIM Pré Top e Pré Top Mais também deixaram de incluir redes sociais e SVAs. Estes são os planos de SC:
E estes são os planos atualmente em vigor em SP:
Claro também remove assinaturas de apps
Os planos da Claro para Santa Catarina também deixam de incluir assinaturas de serviços de valor agregado. No entanto, eles continuam com as redes sociais ilimitadas e franquia dedicada para vídeos.
No seu site, a operadora informa que “as ofertas conjuntas de serviços de telecomunicações e outros serviços estão temporariamente suspensas para comercialização no estado em razão da lei estadual n. 17.691 de 14/01/2019”.
Oi e Vivo continuam anunciando SVAs
No momento da publicação dessa notícia, o site da Oi continua anunciando planos com serviços embutidos. Na opção com 50 GB de internet por R$ 99, a operadora destaca que estão incluídos Fox+, HBO Go, WatchESPN, Discovery Kids On, Noggin e Coleção Oi.
O mesmo acontece com o plano da Vivo: o pós-pago puro de entrada é anunciado com os apps Vivo Cloud Sync, Vivo Família Online, Vivo Educa, Vivo Play Kids, NFL e NBA incluídos na assinatura, enquanto o plano controle básico inclui NBA, GoRead e Vivo Cloud Sync.
TIM Beta suspende novas adesões em Santa Catarina; Claro e TIM mudam planos
O post TIM Beta suspende novas adesões em Santa Catarina; Claro e TIM mudam planos apareceu primeiro em Folha de Feira.
source https://folhadefeira.com/tim-beta-suspende-novas-adesoes-em-santa-catarina-claro-e-tim-mudam-planos/
0 notes
Text
(2024-05-01) Presenting A Session At "European Identity and Cloud Conference 2024"
On Friday, June 7th, I will be presenting a session at “European Identity and Cloud Conference 2024”. Very honored to be selected as a speaker and to contribute to helping others. For more information about the conference, please see: https://www.kuppingercole.com/events/eic2024 For more information about my session, please see: https://www.kuppingercole.com/sessions/5699/1 On Thursday, June…

View On WordPress
#Active Directory#cybersecurity#Disaster Recovery#Entra Cloud Sync#Entra Connect Sync#Ransomware#Security
0 notes