#Endpoint Security Market Size
Explore tagged Tumblr posts
Text
#endpoint security market report#endpoint security industry report#endpoint security market#endpoint security market share#endpoint security market size#endpoint security market trends#endpoint security market growth#endpoint security market analysis#endpoint security market forecast
0 notes
Text
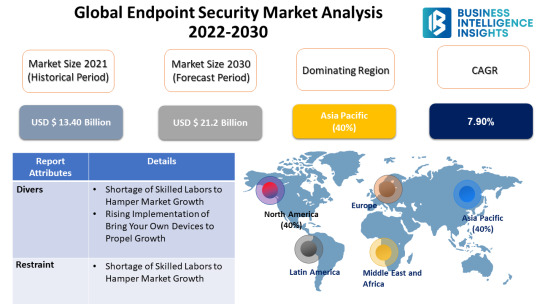
As per Business Intelligence Insights (BII) study, the global Global Endpoint Security Market attained revenue growth of USD 13.40 billion in 2021 and it is projected to reach around USD 21.2 billion by 2030, growing at a 7.90% CAGR.
#Endpoint Security Market#Endpoint Security Market Market#Endpoint Security Market Market Trends#Endpoint Security Market Market Share#Endpoint Security Market Market Size#Endpoint Security Market Market Analysis#Endpoint Security Market Market Demand#Endpoint Security Market Market Growth 2023#Endpoint Security Market Market Industry
0 notes
Text
Same Day Taj Mahal Tour by Car By Taj Mirror Company

Taj Mirror Company's Same Day Taj Mahal Tour by Car is an amazing opportunity to visit one of the world's most iconic monuments in a single day. Same Day Taj Mahal Tour by Car This tour is great for those who have limited time but want to see the Taj Mahal.
The excursion begins in the early morning with a comfortable pickup from your hotel or a predetermined place in Delhi. A skilled and courteous driver will accompany you in a well-maintained, air-conditioned vehicle, assuring a smooth and enjoyable travel to Agra, which is roughly 3-4 hours away.
When you arrive in Agra, you will be greeted by your professional tour guide, who will lead you on a fascinating tour of the Taj Mahal's history and architecture. This UNESCO World Heritage site, created by Emperor Shah Jahan in memory of his beloved wife Mumtaz Mahal, is a Mughal architectural masterpiece featuring magnificent white marble inlaid with precious stones.
After visiting the Taj Mahal, the group continues to the Agra Fort, another UNESCO World Heritage site. For years, the Mughal rulers' principal residence was this towering red sandstone fort. Your guide will explain the fort's history and strategic importance.
A delicious lunch at a respected local restaurant follows, where you may sample traditional Indian cuisine. The journey next continues to the Tomb of Itimad-ud-Daulah, sometimes known as the "Baby Taj," another stunning specimen of Mughal construction.
After a day full of historical treasures and cultural encounters, the tour closes with a relaxing journey back to Delhi. You will be dropped off at your hotel or another predetermined place, bringing an end to a great excursion.
Taj Mirror Company's Same Day Taj Mahal Tour by Car is a well-organized, hassle-free method to witness the timeless grandeur of the Taj Mahal and other Agra attractions. It provides an ideal combination of history, culture, and comfort, making it a must-see for any visitor to India.
ALSO READ-
CrowdStrike is a renowned cybersecurity firm that specializes in endpoint protection, threat intelligence, and cyberattack response services. CrowdStrike, founded in 2011 by George Kurtz, Dmitri Alperovitch, and Gregg Marston, has quickly established itself as a powerful force in the cybersecurity market. The corporation is based in Sunnyvale, California.
CrowdStrike's core product, the Falcon platform, uses AI and ML to detect and respond to threats in real time. The technology gives extensive visibility into endpoint activity, enabling enterprises to quickly detect and remediate any security breaches. Falcon's cloud-native architecture provides scalability and ease of deployment, making it a popular choice for businesses of all sizes.
CrowdStrike's role in detecting high-profile intrusions, such as the 2016 Democratic National Committee (DNC) hack, is one of its most notable accomplishments. The company's competence in threat intelligence and incident response has made it a reliable partner for both government agencies and private-sector businesses.
CrowdStrike's business strategy is subscription-based, with several service tiers to meet different corporate demands. This concept has been successful, as the company's revenue has grown rapidly and its customer base has expanded abroad. CrowdStrike went public in 2019, reinforcing its market position.
The company's commitment to innovation is demonstrated by continual updates to the Falcon platform and the incorporation of new technologies to battle increasing cyber threats. CrowdStrike's focus on proactive threat hunting, along with its comprehensive threat intelligence capabilities, enables enterprises to stay ahead of adversaries.
To summarize, CrowdStrike has evolved as a cybersecurity leader thanks to its cutting-edge technologies, strategic threat intelligence, and effective incident response. Its Falcon platform continues to set industry standards, equipping enterprises with the capabilities they need to defend against complex cyber threats.
2 notes
·
View notes
Text
Google Workspace Pricing Breakdown: Save Big on Business Plans

At F60 Host LLP, we provide Google Workspace at the lowest price, ensuring that businesses get the best value without compromising on essential tools. Let's break down Google Workspace pricing and explore how you can save big on your business plans with our exclusive offers.
What is Google Workspace?
Google Workspace, formerly known as G Suite, is a comprehensive suite of productivity tools that includes Gmail, Google Drive, Google Docs, Google Meet, Google Calendar, and more. Designed to enhance collaboration and productivity, Google Workspace is ideal for businesses, educational institutions, and non-profit organizations. The platform offers seamless integration across devices, making it easier for teams to work together efficiently, regardless of their location.
Google Workspace Pricing Plans
Google Workspace offers several pricing plans to cater to the diverse needs of businesses. Here’s a breakdown of the most popular plans available:
1. Business Starter
Price: Starting at $6 per user per month
Features:
Custom business email (e.g., [email protected])
30 GB cloud storage per user
Google Meet video meetings with up to 100 participants
Security and management controls
2. Business Standard
Price: Starting at $12 per user per month
Features:
All Business Starter features
2 TB cloud storage per user
Enhanced Google Meet features, including recordings
Advanced security and administrative controls
3. Business Plus
Price: Starting at $18 per user per month
Features:
All Business Standard features
5 TB cloud storage per user
Google Meet with attendance tracking
Advanced endpoint management
4. Enterprise Plans
Enterprise plans are designed for larger organizations with advanced security and compliance needs. Pricing for these plans is customized based on your business requirements. Contact F60 Host LLP to get a tailored quote for Google Workspace Enterprise plans.
Why Choose F60 Host LLP for Google Workspace?
At F60 Host LLP, we understand that every business has unique needs. That’s why we offer customized Google Workspace plans and exclusive Google Workspace offers to help businesses get the most out of their investment. Here’s why we’re the top choice for Google Workspace reselling:
1. Google Workspace at the Lowest Price
We pride ourselves on offering Google Workspace at the lowest price in the market. Our competitive pricing ensures that businesses of all sizes can afford the best productivity tools without stretching their budgets.
2. Exclusive Google Workspace Offers
F60 Host LLP regularly provides exclusive Google Workspace offers to help businesses save even more. Whether you're a small startup or a large enterprise, our offers are designed to maximize your savings.
3. Expert Support and Guidance
Our team of Google Workspace experts is always ready to assist you in selecting the right plan for your business. From setup to ongoing support, we ensure a smooth experience at every stage of your Google Workspace journey.
How to Choose the Right Google Workspace Plan
Choosing the right Google Workspace plan depends on your business needs and the number of users. Here are a few tips to help you make the right choice:
Assess Your Storage Needs: Consider how much cloud storage your team will require. For small teams with basic storage needs, the Business Starter plan might be sufficient. For larger teams or businesses dealing with large files, consider the Business Standard or Business Plus plans.
Consider Video Conferencing Requirements: If your business conducts regular virtual meetings, choose a plan that offers enhanced Google Meet features, such as recordings and attendance tracking.
Security and Compliance: For businesses with advanced security and compliance requirements, Enterprise plans are the best choice. Contact F60 Host LLP for a customized quote.
Benefits of Using Google Workspace
Google Workspace offers numerous benefits that can transform the way your business operates:
Seamless Collaboration: With real-time collaboration tools like Google Docs and Google Sheets, teams can work together from anywhere.
Professional Email: Establish credibility with a custom business email address.
Enhanced Security: Google Workspace offers robust security features to keep your data safe.
Scalability: Easily add or remove users as your business grows.
Save Big on Google Workspace with F60 Host LLP
By choosing F60 Host LLP as your Google Workspace reseller, you can unlock significant savings on your business plans. Our Google Workspace pricing is designed to offer maximum value while ensuring that you get access to all the essential productivity tools your business needs.
Website: f60host.com
0 notes
Text
https://seo-48809284.hubspotpagebuilder.com/blog/south-korea-endpoint-security-for-business-market-by-application-size-trends-2025
0 notes
Text
A Deep Dive into the Security Services Market: Insights and Analysis
The global security services market size is expected to reach USD 212.36 billion by 2030, growing at a CAGR of 6.2% from 2023 to 2030, according to a new report by Grand View Research, Inc. Globalization has become an important driver behind security concerns. For instance, increasing international trade encourages more passenger and freight travel. The expansion of air, rail, road, and maritime transportation raises the possibility of security lapses that lead to robberies and organized smuggling, which encourages governments to strengthen cross-border surveillance. Growing immigration activities reduces a nation's capacity to thwart covert threats and, in certain situations, increases the sense of fear among local populations.
The growing internationalization of production activities has seen communications and supply chains become increasingly global, specialized, and fragmented, giving rise to vulnerabilities. At the same time, businesses and governments are seeking ways of conducting their operations more efficiently and managing security more cost-effectively. Subsequently, boosting the market growth. The rising cybercrime activities in both developed and emerging nations have raised concerns for companies. Governments and other large enterprises are attempting to close the gap between the amount of money spent on cybersecurity systems and the best outcome possible with the threat artifacts gathered to lessen or neutralize emerging threats.
The applicability and usefulness of intelligence have led organizations to integrate contextual information and data points to determine relevant threats to the business and thus provide actionable strategies towards the same. As cyberattacks are becoming more sophisticated, cybercriminals are abusing network security and getting privileged access all around the world. In addition, the fact that the attackers are operating as a genuine group that is expected to grow in scope raises concerns about attacks on industries, including BFSI, government, healthcare, and others. The factors mentioned earlier have led to growing security awareness and are thus resulting in higher spending on threat intelligence solutions with an aim to combat or mitigate risk to the organization.
Gather more insights about the market drivers, restrains and growth of the Security Services Market
Security Services Market Report Highlights
• The managed security services (MSS) segment held a significant revenue share of 32.4% in 2022
• MSS capabilities include exposure assessment, detection & response, security monitoring, and operational services specific to security technology implementation & consulting. MSS providers offer a wide range of engagement models with technology-based management-driven experience
• Threat intelligence security services is projected to register a CAGR of 9.5% from 2023 to 2030
• The BFSI segment is expected to register the highest CAGR of 24.2% from 2023 to 2030. Revenues obtained by companies offering cloud security, biometric technologies, and endpoint detection & response to the BFSI sector make up the security services industry
Security Services Market Segmentation
Grand View Research has segmented the global security services market based on type, application, and region:
Security Services Type Outlook (Revenue, USD Billion, 2017 - 2030)
• Managed Security Services
• Security Consulting Services
• SaaS Security Services
• Threat Intelligence Security Services
• Others
Security Services Application Outlook (Revenue, USD Billion, 2017 - 2030)
• BFSI
• Government & Defence
• IT & Telecommunication
• Healthcare
• Energy & Utilities
• Manufacturing
• Retail
• Others
Security Services Regional Outlook (Revenue, USD Billion, 2017 - 2030)
• North America
o U.S.
o Canada
• Europe
o U.K.
o Germany
o France
• Asia Pacific
o China
o Japan
o India
o South Korea
o Australia
• Latin America
o Brazil
o Mexico
• Middle East & Africa (MEA)
o Kingdom of Saudi Arabia (KSA)
o UAE
o South Africa
Order a free sample PDF of the Security Services Market Intelligence Study, published by Grand View Research.
#Security Services Market#Security Services Market Size#Security Services Market Share#Security Services Market Analysis#Security Services Market Growth
0 notes
Text
Public Cloud in BFSI Market 2025-2037 | Size, Growth, Industry Trends and Report
Research Nester assesses the growth and market size of the global public cloud in BFSI market which is anticipated to be on account of the growing use of smartphones.

Research Nester’s recent market research analysis on “Public Cloud in BFSI Market: Global Demand Analysis & Opportunity Outlook 2037” delivers a detailed competitor’s analysis and a detailed overview of the global public cloud in BFSI market in terms of market segmentation by type, component, enterprise size, end use, and by region.
Rapid Shift Towards Cloud-based Services to Promote Global Market Share of Public Cloud in BFSI
The global public cloud in BFSI market is estimated to grow majorly due to the growing adoption of cloud-based services in banks. Services enabled by the cloud modify governance frameworks, technological infrastructure, product offerings, and operational procedures to help banks expand. It helps with the scaling up of services by offering several benefits such as storage, processing power, the capacity to work across a broad range of applications, and contextualized solutions based on the needs of the company employing cloud services.
Request Free Sample Copy of this Report @ https://www.researchnester.com/sample-request-6482
The execution of complex analytics and the gathering of insights from disparate, enormous data sets are made possible by the integration of machine learning and artificial intelligence capabilities. 72% of finance departments now employ AI, according to Business Journalism research, and 49% of these executives emphasized the importance of upskilling their financial team. The cloud transformation road includes technological improvements, process automation, organizational reform, and product innovation.
Some of the major growth factors and challenges that are associated with the growth of the global public cloud in BFSI market are:
Growth Drivers:
Growing support from the government
Cost-effectiveness
Challenges:
Public cloud adoption in the BFSI industry is hindered by the deployment of various third-party services that are a component of cloud computing and may give rise to security or confidentiality concerns. Mobility, networks, endpoints, databases, cloud computing, online applications, and virtualization are among the other infrastructures that are addressed.
By enterprise size, the global public cloud in BFSI market is segmented into small and medium enterprises and large enterprises. The small and medium enterprises segment is poised to garner the highest revenue by the end of 2037 by growing at a significant CAGR over the forecast period. Large firms have embraced the program with the most fervor because of its benefits, which include reduced operating costs, more teamwork, greater flexibility, and a faster time to market. Businesses are using the cloud to update crucial business apps and processes, even though they have previously utilized it for infrastructure transfer and application development. Because of the communication service providers' flexible price structures, higher staff efficiency, and enhanced teamwork and innovation, the SME segment has had the largest share of the market since 2019.
Request for customization @ https://www.researchnester.com/customized-reports-6482
By region, the Europe public cloud in BFSI market is to generate the highest revenue by the end of 2036. The market is growing in countries with pro-business laws and significant investments in digital technology, but it is growing more slowly in areas with restrictive regulations and little funding. In addition, the demand for public cloud services in Europe is being driven by the growing trend of remote work and the growing use of cloud-based solutions by enterprises of all kinds. As the area continues to recover from the COVID-19 pandemic's economic effects, this tendency is anticipated to continue.
This report also provides the existing competitive scenario of some of the key players that includes Lumen Technologies, Inc. DXC Technology Company, Intel Corporation, Dell EMC, Panzura, Inc., VMware LLC, Equinix, Inc., Rackspace Technology, Inc., Citrix Systems, Inc., Cisco Systems Inc., and others.
Access our detailed report @ https://www.researchnester.com/reports/public-cloud-in-bfsi-market/6482
About Research Nester-
Research Nester is a leading service provider for strategic market research and consulting. We aim to provide unbiased, unparalleled market insights and industry analysis to help industries, conglomerates and executives to take wise decisions for their future marketing strategy, expansion and investment etc. We believe every business can expand to its new horizon, provided a right guidance at a right time is available through strategic minds. Our out of box thinking helps our clients to take wise decision in order to avoid future uncertainties.
Contact for more Info:
AJ Daniel
Email: [email protected]
U.S. Phone: +1 646 586 9123
U.K. Phone: +44 203 608 5919
0 notes
Text
0 notes
Text
Managed security services chapel hill

In today’s digital landscape, businesses in Chapel Hill, North Carolina, face an ever-growing threat of cyberattacks. From data breaches to ransomware, the need for robust cybersecurity measures has never been more critical. Managed security services chapel hill offer an efficient and reliable way to safeguard sensitive information, ensuring businesses operate securely while focusing on growth and innovation.
What Are Managed Security Services?
Managed Security Services involve outsourcing an organization’s cybersecurity responsibilities to a dedicated third-party provider. These providers specialize in monitoring, managing, and securing IT systems, offering 24/7 protection against potential threats. Services typically include intrusion detection, vulnerability management, firewall configuration, endpoint protection, and incident response.
For businesses in Chapel Hill, MSS providers bring local expertise combined with global best practices to address the unique challenges of regional industries, from healthcare to education and retail.
Why Choose Managed Security Services in Chapel Hill?
Proactive Threat Detection and Prevention: MSS providers utilize advanced technologies like Artificial Intelligence (AI) and machine learning to identify vulnerabilities before they become major issues. With real-time monitoring, businesses can prevent breaches and maintain continuity.
Cost-Effective Solution: Hiring a full-scale, in-house cybersecurity team can be costly. Managed Security Services offer access to expert teams and tools at a fraction of the cost, providing small and medium-sized businesses in Chapel Hill with enterprise-level protection.
Regulatory Compliance: Many industries, such as healthcare and finance, must comply with strict data protection regulations like HIPAA or GDPR. MSS providers ensure businesses meet these requirements, avoiding hefty fines and legal complications.
Scalability and Customization: Chapel Hill’s growing businesses need flexible solutions to match their pace of development. MSS providers offer scalable services tailored to specific business needs, ensuring the right level of protection at every stage.
Local Expertise, Global Standards
Chapel Hill is home to a diverse range of industries, each requiring unique cybersecurity approaches. Local MSS providers understand the region’s market dynamics, offering solutions designed to address these specific needs. At the same time, they leverage global standards to deliver cutting-edge protection.
Conclusion
In a world where cyber threats are becoming increasingly sophisticated, businesses in Chapel Hill cannot afford to leave their security to chance. Managed Security Services provide a proactive, cost-effective, and reliable approach to safeguarding data and IT infrastructure. By partnering with a trusted MSS provider, businesses can confidently navigate the complexities of cybersecurity, focusing on their core objectives while ensuring a secure digital environment.
0 notes
Text
0 notes
Text
0 notes
Text
0 notes
Text
A Deep Dive into the Managed Security Services Market: Insights and Analysis
The global managed security services market size is expected to reach USD 87.5 billion by 2030, growing at a CAGR of 15.4% from 2023 to 2030, according to a recent report from Grand View Research, Inc. Factors such as the growing demand for outsourcing services across various BFSI, healthcare, manufacturing, IT & telecommunication industries, and the enterprises focus on their key competencies are expected to drive the market’s growth.
Businesses rely on managed security service providers (MSPs) to avoid the costly burden of maintaining their IT infrastructure and keep pace with constant technological dimensions. By leveraging standardized products, reducing time to market, and improving service quality, managed service providers helps an organization in saving costs.
MSPs have created a vast space in business operations by providing advanced cybersecurity tools to predict and mitigate cyber threats. Additionally, as emerging technologies like artificial intelligence, DevOps, and machine learning gain maturity, organizations are expected to look forward to specialized MSPs to stay at the forefront of innovation. A Managed Security Service Provider (MSSP) offers various sub-functions that cover the overall security needs of an enterprise.
The major sub-segments of MSSs have managed endpoint security that monitors all endpoints across the enterprise and intrusion prevention detection system (IPS) that regularly monitors the network for signs of forced intrusion. Extended Detection, and Response (XDR), gathers security details across endpoints and threat intelligence-related visibility to help detect future attacks provide.
Gather more insights about the market drivers, restrains and growth of the Managed Security Services Market
Managed Security Services Market Report Highlights
• The cloud security segment is anticipated to observe a CAGR of 18.5% during the forecast period. The massive growth of cloud 3.0, Industry 4.0, and digitalization has resulted in the surge of managed cloud security services. Cloud security facilitates 24/7 system protection without any human intervention, real-time alerts, and proactive managed services
• The managed DDoS segment is anticipated to observe a CAGR of 18.7% during the forecast period. The DDoS services enhance operational services that depend on the web is projected to rise owing to the growing demand among enterprises to manage the complexity of resources
• Small and medium-sized enterprises (SMEs) are anticipated to observe a CAGR of 18.1% during the forecast period. An increased zero trust security among small and medium-sized businesses (SMEs) surged the adoption of secured management solutions, owing to the growing importance of managed services
• The manufacturing segment is anticipated to observe a CAGR of 16.4% during the forecast period The growing demand among manufacturers to adopt managed security services for cyber safety and vendors’ data accessibility is fueling the demand for the market
• Asia Pacific is expected to grow at the fastest CAGR of 18.2% from 2023 to 2030, owing to the increasing adoption of managed security services and the growing digitalization of businesses in the region. Countries such as China, India, Japan, and South Korea have implemented privacy legislation and data protection that force enterprises to build robust security management solutions
Managed Security Services Market Segmentation
Grand View Research has segmented the global managed security services market based on security, services, enterprise size, vertical, and region:
Managed Security Services Security Outlook (Revenue, USD Billion, 2018 - 2030)
• Cloud Security
• Endpoint Security
• Network Security
• Data Security
• Others
Managed Security Services Outlook (Revenue, USD Billion, 2018 - 2030)
• Managed SIEM
• Managed UTM
• Managed DDoS
• Managed XDR
• Managed IAM
• Managed Risk & Compliance
• Others
Managed Security Services Enterprise Size Outlook (Revenue, USD Billion, 2018 - 2030)
• Small and medium-sized enterprises
• Large enterprises
Managed Security Services Vertical Outlook (Revenue, USD Billion, 2018 - 2030)
• BFSI
• Healthcare
• Manufacturing
• IT and Telecom
• Retail
• Defense/Government
• Others
Managed Security Services Regional Outlook (Revenue, USD Billion, 2018 - 2030)
• North America
o U.S.
o Canada
• Europe
o UK
o Germany
o France
o Italy
o Spain
• Asia Pacific
o China
o India
o Japan
o Australia
o South Korea
• Latin America
o Brazil
o Mexico
o Argentina
• Middle East and Africa
o UAE
o Saudi Arabia
o South Africa
Order a free sample PDF of the Managed Security Services Market Intelligence Study, published by Grand View Research.
#Managed Security Services Market#Managed Security Services Market Size#Managed Security Services Market Share#Managed Security Services Market Analysis#Managed Security Services Market Growth
0 notes
Text
Pankit Desai, Co-Founder and CEO, Sequretek – Interview Series
New Post has been published on https://thedigitalinsider.com/pankit-desai-co-founder-and-ceo-sequretek-interview-series/
Pankit Desai, Co-Founder and CEO, Sequretek – Interview Series
Pankit Desai is the co-founder and CEO of Sequretek, a company specializing in cybersecurity and cloud security products and services. In 2013, he co-founded Sequretek with Anand Naik and has played a key role in developing the company into a prominent provider of cybersecurity and cloud security solutions. Prior to Sequretek, Pankit held various leadership and management positions in the IT industry at companies including NTT Data, Intelligroup, and Wipro Technologies. He holds a degree in computer engineering and brings a strong background in technology and entrepreneurship to his role.
Sequretek’s cybersecurity expertise, strengthened by cloud-based solutions with real-time, AI-driven threat detection and response, enables businesses to confidently take control, grow, and safeguard their digital assets while maintaining regulatory compliance.
What inspired you to co-found Sequretek, and how has the company evolved since its inception?
The cybersecurity landscape has long been marked by disparity, where the top 10% of companies have access to comprehensive, cutting-edge solutions, while the rest struggle with limited resources and expertise. This industry, which often caters to the elite, leaves many organizations navigating a maze of 90+ technology categories and thousands of vendors, resulting in fragmented approaches that complicate security decisions. At Sequretek, we saw this as an opportunity to change the narrative. When we founded the company in 2013, our mission was clear, to make cybersecurity simple and accessible for all, not just the few who could afford it.
Our approach has always been about consolidation and simplification. Instead of adding to the complexity with more niche solutions, we set out to build an integrated platform that addresses the key pillars of cybersecurity—endpoint security, identity governance, and threat detection—under one roof. We envisioned a world where businesses could focus on growth without the fear of cyber threats disrupting their journey. By combining AI-driven automation with a holistic strategy, we’ve empowered our clients to stay secure in the face of evolving risks, making cybersecurity a growth enabler rather than a roadblock.
What were the initial challenges you faced when starting Sequretek, and how did these shape the company’s strategy in cybersecurity?
Starting Sequretek in 2013, we encountered several challenges that significantly influenced our approach to cybersecurity. The most pressing issue was the steep fragmentation of the industry—there were too many niche solutions addressing specific security problems without an integrated approach. It was clear that if we wanted to make a meaningful impact, we needed to consolidate security capabilities and deliver a unified solution that was easy to implement and manage. This insight drove us to develop our integrated Percept platform, which covers endpoint security, identity governance, and threat detection in one place.
Another challenge was the prevailing perception that cybersecurity was a luxury reserved for large enterprises with substantial budgets. This mindset left a significant portion of the market underserved, exposing smaller companies to considerable risks. As a result, our strategy has always been focused on simplifying security by automating routine tasks, reducing the need for specialized security teams, and lowering the cost of ownership.
Could you tell us about the core philosophy behind Sequretek’s product suite and how it aligns with your original vision?
The core philosophy behind Sequretek’s product suite is rooted in the belief that cybersecurity should not be a luxury, but a fundamental right for all businesses, regardless of their size. From the outset, our vision has been to simplify security by consolidating complex technologies into a single, cohesive platform. We observed how companies were struggling with a fragmented security landscape, where they needed multiple tools to manage different aspects of cybersecurity. This created inefficiencies and increased the risk of vulnerabilities going undetected.
This philosophy is reflected in our Percept platform, which was designed to eliminate silos and provide a unified view of an organization’s security posture. By leveraging AI and automation, Percept streamlines security operations, allowing companies to detect and respond to threats with greater speed and accuracy. Our focus on automation not only reduces the burden on security teams but also lowers the cost of ownership, making enterprise-grade security accessible to businesses that may not have large IT budgets.
What distinguishes Sequretek from other players in the AI-driven cybersecurity field?
Sequretek stands out by simplifying cybersecurity through an integrated approach. While many competitors offer isolated solutions, we consolidated endpoint security, identity governance, and threat detection into our unified Percept platform. This reduces the complexity that overwhelms many organizations using multiple tools.
Our use of AI goes beyond just detecting threats—it automates responses to free up security teams and even includes natural language processing to make interacting with security data user-friendly.
How has AI revolutionized threat prediction and response at Sequretek, and what specific benefits does it offer your clients?
AI has been a game-changer for Sequretek in revolutionizing threat prediction and response. At its core, our AI-driven platform, Percept, doesn’t just spot threats—it anticipates them. By continuously analyzing vast data streams, our algorithms identify potential risks early on, allowing businesses to react before a situation escalates. This proactive stance significantly cuts down on response times, ensuring threats are addressed in seconds.
The benefits for our clients are clear- fewer distractions from false alarms, less manual work for security teams, and more time to focus on strategic priorities. For instance, when Percept detects a phishing attempt, it can immediately isolate the threat, notify the team, and even initiate a response, all without human intervention. This automation isn’t just about speed; it’s about making security accessible for companies that can’t afford large, specialized teams. We’re essentially leveling the playing field, empowering businesses to stay resilient in an ever-evolving threat landscape.
What are some of the most critical AI advancements in Sequretek’s Percept platform for managing evolving cyber threats?
The Percept platform’s AI advancements are geared toward staying ahead of the rapidly evolving cyber threat landscape. One of the standout features is its ability to use predictive analytics for threat anticipation. This shift from reactive to proactive threat management is crucial in today’s cybersecurity environment. Another critical advancement is in automation. Percept automates the detection and also response processes, such as isolating compromised devices or blocking suspicious network traffic in real time. This automation dramatically reduces response times, allowing businesses to mitigate threats instantly while reducing the burden on security teams. Moreover, with integrated natural language processing (NLP), users can interact with the platform conversationally, simplifying complex tasks like querying threat intelligence data.
These advancements transform cybersecurity from a traditionally resource-intensive activity into a more streamlined and accessible process, allowing companies of all sizes to benefit from cutting-edge defenses without needing extensive security teams.
Can you share an example of how Sequretek uses AI to streamline threat detection and automate responses?
At Sequretek, AI is at the heart of streamlining threat detection and automating responses. For instance, Percept XDR and NG SIEM provide AI-powered extended detection and response combined with next-generation security information and event management. This setup detects threats and takes automated actions, such as isolating compromised systems and notifying security teams in real time, reducing manual intervention and speeding up containment.
Similarly, Percept EDR leverages on-agent AI for real-time endpoint detection and response. When it detects a next-gen threat, like ransomware, it can immediately isolate the affected device, preventing lateral movement across the network while ensuring business operations continue uninterrupted.
Additionally, Percept Compliance Manager brings AI to governance, risk, and compliance by conducting real-time vulnerability scans and configuration audits within a single console, helping organizations maintain a strong security posture without extensive manual oversight.
How is AI changing the tactics of cybercriminals, and what innovations is Sequretek using to counteract these new AI-driven threats?
AI is reshaping the landscape of cybercrime, enabling attackers to launch more sophisticated and convincing campaigns. Cybercriminals are using AI to enhance phishing and social engineering tactics, creating highly personalized and realistic fake messages, voice, or video content to deceive individuals and organizations. The scale and speed at which these AI-driven attacks can be executed have made them a significant concern in today’s threat environment.
At Sequretek, we counteract these AI-driven threats with our own AI innovations integrated into the Percept platform. We employ advanced machine learning techniques to detect anomalies that indicate potential AI-generated attacks, such as deepfakes or sophisticated phishing attempts. Our platform uses behavioral analysis to identify unusual patterns in user activity, helping to catch threats that traditional rule-based systems might miss. The goal is to stay one step ahead in this AI arms race, using AI to outsmart cybercriminals by making our defenses smarter, faster, and more adaptive.
How do you see AI’s role in cybersecurity evolving over the next five years, and what does this mean for businesses?
As AI becomes more mature, we see its potential to fundamentally reshape cybersecurity. One major advancement will be how effectively AI systems can differentiate real threats from false positives. Today, cybersecurity teams often face an overwhelming volume of alerts, many of which are not genuine risks. With smarter AI, we’ll be able to identify true threats with much greater accuracy, which will allow teams to focus their efforts where it truly matters, rather than getting caught up in unnecessary noise. Additionally, AI will help reduce the grey areas we encounter—those ambiguous situations that aren’t harmful or safe—by making distinctions clearer and cutting down on manual oversight.
Incident response will also see transformative gains. Currently, even when threats are detected in real time, the response can still be time-consuming due to manual processes. AI-enabled automation will allow for much faster, more seamless responses, reducing reliance on human intervention and significantly speeding up the process. Finally, we’re also looking forward to advancements in natural language processing, which will simplify how teams interact with complex security data, making it accessible without specialized queries or technical hurdles. This combination of capabilities will be essential as cyber threats evolve, enabling businesses to stay resilient in a rapidly shifting landscape.
What advice would you give organizations looking to enhance their cybersecurity posture with AI today?
Organizations looking to strengthen their cybersecurity with AI should remember that AI is a powerful enabler, not a complete solution. It’s essential to approach AI as part of an integrated security framework built on the fundamentals—people, processes, and technology. Just because AI offers new capabilities doesn’t mean you should replace established strategies or think it’s a silver bullet. Instead, think of AI as a tool to enhance your team’s capabilities, not replace them. For example, AI can play a valuable role in understanding user behavior and enhancing security awareness through gamified learning, which can help reduce human vulnerabilities to attacks.
Another critical area is identifying where AI can address inefficiencies in your current tools and processes. AI and machine learning can help you respond faster and with greater precision, particularly in areas traditionally slowed down by human dependency. However, it’s important to remember that no AI tool alone will ensure complete security. It should work alongside strong, well-trained teams and established protocols to build a resilient security posture that adapts to new threats.
Thank you for the great interview, readers who wish to learn more should visit Sequretek.
#Advice#agent#ai#AI systems#AI-powered#alerts#Algorithms#Analysis#Analytics#anomalies#approach#assets#attackers#automation#awareness#background#Behavior#behavioral analysis#budgets#Business#CEO#challenge#change#Cloud#Cloud Security#cloud security solutions#Companies#complexity#compliance#comprehensive
0 notes