#Data Center/Storage-Based DLP
Explore tagged Tumblr posts
Text
Why Azure Cloud Security Services Are Essential for Your Business?
In today’s digital age, enterprises face an ever-growing range of cybersecurity threats, making robust security solutions a necessity. Businesses must ensure that their sensitive data, applications, and networks are well protected against cyberattacks. Azure cloud security services offer a comprehensive suite of security solutions designed to safeguard enterprise infrastructure while enabling seamless cloud operations. From advanced threat protection to data encryption and compliance, Azure provides businesses with the necessary tools to enhance security, maintain regulatory requirements, and ensure uninterrupted business processes. This article explores the critical benefits of using Azure cloud security services for enterprises.
Protect Your Business with Advanced Azure Cloud Security Services
Azure cloud security services provide businesses with industry-leading security capabilities that protect their IT environments from various threats. Microsoft Azure’s security infrastructure is designed to provide a multi-layered approach, ensuring maximum protection across networks, applications, and data storage. With advanced threat detection, artificial intelligence-driven monitoring, and end-to-end encryption, Azure ensures that enterprise data remains secure. Security services like Azure Security Center, Azure Sentinel, and Microsoft Defender for Cloud empower businesses to proactively detect and respond to security threats. By leveraging these advanced security features, enterprises can reduce vulnerabilities, mitigate risks, and ensure business continuity without compromising efficiency.
How Azure Cloud Security Services Safeguard Your Data?
One of the primary concerns for any enterprise is data security. Azure cloud security services provide a robust set of data protection tools, including encryption, access control, and threat intelligence. Azure ensures that all data—whether in transit, at rest, or in use—is encrypted using advanced security protocols. Azure’s Data Loss Prevention (DLP) policies prevent unauthorized access and leakage of sensitive information. Additionally, Azure Active Directory enables multi-factor authentication (MFA) and role-based access control (RBAC), ensuring that only authorized personnel have access to critical business data. Azure’s security framework helps enterprises prevent data breaches while ensuring compliance with global security regulations.
The Role of Azure Cloud Security Services in Cyber Threat Protection
Cyber threats such as ransomware, phishing attacks, and malware pose significant risks to businesses. Azure cloud security services leverage artificial intelligence and machine learning to identify and prevent security threats before they cause damage. Azure Sentinel, Microsoft’s cloud-native SIEM (Security Information and Event Management) system, provides real-time security analytics, threat intelligence, and automated incident responses. Additionally, Azure DDoS Protection safeguards enterprise networks against large-scale denial-of-service attacks. By continuously monitoring and analyzing threat patterns, Azure ensures businesses can effectively respond to potential cyber threats, protecting their assets from security breaches.
Why Businesses Rely on Azure for Secure Cloud Solutions?
Azure’s reputation as a leading cloud service provider is built on its commitment to security, reliability, and innovation. Businesses trust Azure cloud security services because they offer a secure and compliant cloud environment tailored to meet enterprise needs. Microsoft invests heavily in cybersecurity research and innovation, ensuring that Azure’s security measures evolve with emerging threats. Azure also offers compliance certifications such as ISO 27001, GDPR, and HIPAA, making it an ideal choice for businesses in regulated industries. By relying on Azure, enterprises gain access to cutting-edge security technologies, expert support, and a trusted cloud infrastructure that enhances operational security and business resilience.
Strengthen Your Cybersecurity with Azure Cloud Security Services
The increasing complexity of cyber threats demands a proactive approach to security. Azure cloud security services provide businesses with AI-driven threat detection, security automation, and compliance management tools that strengthen cybersecurity measures. Azure Advanced Threat Protection (ATP) identifies and mitigates potential security risks in real time, ensuring a strong defense against cyberattacks. Azure’s Zero Trust security model verifies user identities and enforces strict access policies to minimize security risks. By integrating Azure’s comprehensive security services, businesses can establish a resilient security framework that prevents attacks, safeguards customer data, and ensures regulatory compliance.
Key Benefits of Implementing Azure Cloud Security Services
Adopting Azure cloud security services offers businesses multiple benefits, including enhanced data protection, real-time threat detection, and simplified security management. One of the significant advantages of Azure is its scalability, allowing enterprises to adjust security measures based on their evolving needs. Azure’s integrated security ecosystem enables businesses to manage security policies, monitor threats, and automate incident response from a single platform. Additionally, Azure provides cost-effective security solutions, reducing the need for extensive on-premise security infrastructure. With Azure, enterprises can achieve a higher level of security while optimizing costs and ensuring seamless cloud operations.
Secure Your Cloud Infrastructure with Azure’s Advanced Security Features
Cloud security is a top priority for enterprises migrating to the cloud. Azure cloud security services provide businesses with end-to-end security, covering identity protection, data encryption, and compliance management. Azure’s network security groups (NSGs) and firewalls ensure secure communication between cloud resources, preventing unauthorized access. Microsoft’s Defender for Cloud offers automated security recommendations, enabling businesses to enhance their cloud security posture effectively. Furthermore, Azure’s Security Center continuously assesses security configurations, identifies vulnerabilities, and provides actionable insights to improve enterprise security. These advanced security features make Azure an ideal solution for securing cloud infrastructure while maintaining operational efficiency.
Conclusion
As cyber threats continue to evolve, businesses must prioritize strong security solutions to protect their cloud environments. Azure cloud security services provide enterprises with comprehensive security tools that enhance data protection, prevent cyberattacks, and ensure regulatory compliance. By leveraging Azure’s AI-driven threat detection, automated security responses, and advanced encryption protocols, businesses can establish a secure cloud infrastructure that supports growth and innovation. Investing in Azure’s cloud security solutions ensures not only protection from threats but also long-term business success in an increasingly digital world. Enterprises looking to secure their cloud operations should consider Azure’s industry-leading security services for a robust and future-ready security framework.
0 notes
Text
Email Hosting for Enterprises in UAE: What to Consider Before Choosing a Provider
In today’s digital landscape, enterprises rely heavily on professional email services for seamless communication. Choosing the right email hosting provider in UAE is crucial for ensuring reliability, security, and efficiency in business operations. With multiple options available, businesses must carefully assess their needs and compare various email hosting services UAE before making a decision. This guide will walk you through the key factors to consider before selecting an email hosting UAE provider.

Understanding Email Hosting
What is Email Hosting?
Email hosting is a service that allows businesses to manage their email servers and domains professionally. Unlike free email services, enterprise email hosting provides enhanced security, larger storage, and custom domain names that establish brand credibility.
Types of Email Hosting
Shared Email Hosting – A cost-effective option where multiple users share server resources.
Dedicated Email Hosting – Offers exclusive server resources for businesses with high email traffic.
Cloud-Based Email Hosting – Provides flexibility, scalability, and remote access capabilities.
On-Premise Email Hosting – Best for businesses that require full control over their email infrastructure.
Key Factors to Consider When Choosing an Email Hosting Provider
1. Reliability and Uptime Guarantee
Enterprises need an email hosting service with high uptime guarantees to avoid disruptions in communication. Look for providers offering at least 99.9% uptime backed by Service Level Agreements (SLAs).
2. Security Features
Email security is crucial for protecting sensitive business information. Ensure that the provider offers:
End-to-end encryption to secure data transmission.
Spam and malware protection to prevent malicious attacks.
Multi-factor authentication (MFA) for enhanced security.
Data loss prevention (DLP) to safeguard important emails.
3. Storage and Scalability
Businesses generate a high volume of emails daily, requiring ample storage space. Evaluate:
The amount of storage per user.
Scalability options to accommodate business growth.
Cloud storage integration for backup and archiving.
4. Custom Domain Support
A professional email address (e.g., [email protected]) enhances credibility. Ensure the provider supports custom domain integration for branding purposes.
5. Compliance and Data Privacy
UAE businesses must comply with data protection laws and industry regulations. Choose a provider that:
Adheres to UAE data privacy laws.
Offers GDPR and ISO 27001 compliance for international standards.
Provides data residency options to store emails in secure UAE-based data centers.
6. Integration with Business Tools
Seamless integration with CRM software, productivity suites, and collaboration tools enhances workflow efficiency. Check if the email hosting service is compatible with:
Microsoft 365 and Google Workspace.
Project management and communication tools.
Third-party applications for automation and analytics.
7. Customer Support and Technical Assistance
Uninterrupted business operations require responsive technical support. Ensure the provider offers:
24/7 customer support via phone, email, and chat.
Localized UAE-based support for quick assistance.
Comprehensive knowledge base and tutorials for troubleshooting.
8. Email Migration Services
If switching from another email host, ensure smooth email migration services are available. The provider should offer:
Seamless data transfer without downtime.
Assistance with domain setup and DNS configuration.
Automated migration tools to streamline the transition.
9. Backup and Disaster Recovery
Data loss can be catastrophic for enterprises. Ensure the provider offers:
Automated daily backups with easy recovery options.
Disaster recovery plans for emergency situations.
Redundant data storage for enhanced reliability.
10. Cost and Pricing Structure
Cost-effectiveness is a key consideration when selecting an email hosting UAE provider. Evaluate:
Subscription models (monthly or annual plans).
The cost of additional features like storage expansion and security enhancements.
Transparent pricing without hidden charges.
Benefits of Enterprise Email Hosting in UAE
Enhanced Professionalism
Using a business email domain enhances brand credibility and professionalism.
Improved Security
Enterprise email hosting provides advanced encryption, anti-spam, and malware protection to safeguard business data.
Increased Productivity
Integration with business tools and collaboration platforms enhances team communication and efficiency.
Better Compliance and Data Control
Email hosting providers ensure compliance with local and international data regulations, providing businesses with peace of mind.
Scalability and Flexibility
Cloud-based email hosting allows enterprises to scale resources as their business grows without significant infrastructure investments.
Conclusion
Selecting the right email hosting providers in UAE requires a thorough evaluation of security, reliability, scalability, and compliance features. Enterprises should prioritize uptime guarantees, integration capabilities, and responsive customer support when making a decision. By considering these factors, businesses can ensure secure, efficient, and seamless communication through a professional email hosting UAE service.
0 notes
Text
What is Data in Motion and Data at Rest ?
BY: Pankaj Bansal, Founder at NewsPatrolling.com
Data in Motion and Data at Rest refer to the state of data in a system and have implications for data security, handling, and processing.
Data in Motion (also called Data in Transit):
This refers to data that is actively moving from one location to another. It could be data being transferred across a network, between devices, or between systems and applications. For example, data traveling over the internet, sent in an email, or transmitted during online transactions.
Security Concerns: Data in motion is vulnerable to interception or attacks (like man-in-the-middle attacks). Therefore, encryption during transmission (e.g., HTTPS, SSL/TLS) is essential to protect it.
Data at Rest:
This refers to data that is stored and not actively moving. It could be stored on physical storage (like hard drives, SSDs) or in cloud storage, databases, or backups. Data at rest includes files, databases, and archived information that is not currently being transmitted or processed.
Security Concerns: While data at rest is less vulnerable than data in motion, it still requires protection from unauthorized access or breaches. Common protection methods include encryption, access controls, and physical security measures.
Both states require distinct security protocols to ensure data integrity and confidentiality.
Read also https://newspatrolling.com/free-movies-download-websites/
And https://www.eduspace360.com
To dive deeper into Data in Motion and Data at Rest, it's essential to understand their broader implications in the fields of security, performance, and compliance.
1. Data in Motion (Data in Transit)
Examples:
Data sent via email.
Online transactions (such as credit card information being processed).
Data being transferred between cloud services.
Streaming data (like live video feeds).
Data moving within an organization’s internal network.
Challenges:
Latency: As data moves across networks, delays may occur, especially with large volumes or over long distances.
Bandwidth Limitations: Data in motion can consume significant network resources, requiring optimization techniques to reduce strain on the network.
Vulnerabilities: Data in motion is susceptible to network attacks, eavesdropping, or interception through methods like packet sniffing or man-in-the-middle attacks.
Security Techniques:
Encryption: Technologies like SSL/TLS (Secure Socket Layer/Transport Layer Security) ensure that even if intercepted, the data remains unreadable.
VPNs (Virtual Private Networks): Create secure tunnels for data to travel through, masking its content from external actors.
Data Loss Prevention (DLP): Helps monitor and prevent unauthorized data transfers or leaks, especially important when dealing with sensitive information in transit.
2. Data at Rest
Examples:
Customer data stored in databases.
Files saved on a computer or external hard drive.
Backup archives in cloud storage.
Data stored in a local data center.
Challenges:
Unauthorized Access: If a malicious actor gains access to storage systems (either physical or virtual), they can compromise data security.
Insider Threats: Employees or individuals with access to systems may misuse or steal data at rest.
Compliance Requirements: Many industries are required to follow strict regulations (such as GDPR, HIPAA) on how data at rest is stored and protected.
Security Techniques:
Encryption at Rest: Encrypting the data so that even if someone gains access to the storage medium, they cannot read the data without the proper decryption keys.
Access Controls: Role-based access control (RBAC) or multi-factor authentication (MFA) ensures that only authorized individuals can access or modify data.
Physical Security: Safeguarding the physical locations of servers, hard drives, and data centers is also important. Measures include surveillance, restricted access, and biometric authentication.
Key Differences Between Data in Motion and Data at Rest
Aspect
Data in Motion
Data at Rest
State
Actively moving across networks
Stationary and stored in databases or storage devices
Security Risk
Higher risk of interception and eavesdropping during transmission
Vulnerable to breaches, theft, or unauthorized access
Encryption
SSL/TLS, VPNs, IPsec for transit security
Disk encryption, database encryption for stored data
Use Cases
Online banking, file transfers, emails
Database storage, cloud backups, file system archives
Protection Focus
Securing transmission channels
Protecting storage devices and access controls
3. Data in Use (Another important category)
Though less discussed, there's a third state of data called Data in Use. This refers to data that is actively being processed or used by applications. For example, data currently in a computer's RAM, or open files being accessed by a user. This state is often where data is most vulnerable because it's decrypted for use, making it susceptible to memory-based attacks.
4. Compliance and Regulations:
Organizations dealing with large volumes of sensitive data are bound by various regulations that outline how they must protect both data at rest and data in motion. Some key regulations include:
GDPR (General Data Protection Regulation): In the EU, mandates encryption of both data in transit and at rest, along with strict consent rules for data handling.
HIPAA (Health Insurance Portability and Accountability Act): In the U.S., mandates the protection of health information through encryption and access controls.
PCI-DSS (Payment Card Industry Data Security Standard): For companies handling credit card data, it requires robust encryption for data in motion and at rest.
5. Zero Trust Model:
A security concept gaining popularity in organizations. It assumes no data, whether in motion or at rest, is inherently safe. Every access request must be verified, authenticated, and continuously monitored, ensuring that all data remains secure.
In summary, both data in motion and data at rest represent critical stages in the lifecycle of data and require tailored security measures. Addressing their respective vulnerabilities is key to building a comprehensive data protection strategy.
0 notes
Text
Power Apps Training | Power Apps Training Hyderabad
Power Apps Data policies
Power Apps is a Microsoft service empowering users to create custom business applications without extensive coding expertise. As part of the Power Platform, it offers a user-friendly environment for app development, enabling seamless integration with various data sources, both on-premises and in the cloud. As of my last knowledge update in January 2022, Power Apps is a Microsoft service that allows users to create custom business applications without the need for extensive coding. It's part of the Power Platform, which also includes Power BI, Power Automate, and Power Virtual Agents.
Power Apps and Power Automate Training

Data Storage and Compliance:
Power Apps may store data in Microsoft Data verse, which provides a secure and compliant data platform.
Ensure compliance with data protection regulations, such as GDPR (General Data Protection Regulation) or any other applicable regional laws.
Connectors and Data Sources:
Power Apps can connect to various data sources, including on-premises data, cloud-based data, and services like SharePoint, SQL Server, and more.
Be aware of the data sources you are connecting to and understand their security and compliance features. Microsoft Power Apps Course
Role-Based Security:
Implement role-based security to control access to data within your Power Apps.
Use Microsoft 365 groups, Azure AD groups, or custom roles to manage access permissions.
Data Encryption:
Ensure that data transmitted between Power Apps and data sources is encrypted.
Microsoft typically employs encryption technologies to secure data in transit and at rest. Power Apps Online Training
Audit and Monitoring:
Leverage built-in audit features to monitor and track user activities within Power Apps.
Use Power Platform's admin connectors and tools for monitoring and managing environments. Power Apps Training Hyderabad
Data Loss Prevention (DLP):
Implement DLP policies to prevent the sharing of sensitive information.
DLP policies can restrict data sharing across environments and between Power Platform and other Microsoft 365 services.
Compliance Center:
Utilize the Microsoft 365 Compliance Center to manage compliance features across Microsoft 365 services, including Power Apps.
Visualpath is the Leading and Best Software Online Training Institute in Ameerpet, Hyderabad. Avail complete job oriented Microsoft Power Platform Online Training by simply enrolling in our institute in Ameerpet, Hyderabad. You will get the best course at an affordable cost.
Attend Free Demo
Call on - +91-9989971070.
Visit: https://visualpath.in/microsoft-powerapps-training.html
#Power Apps and Power Automate Training#Microsoft Power Apps Online Training#Microsoft Power Apps Course#Power Apps Online Training#Power Apps Training#Power Apps Training Hyderabad#Power Apps Training in Ameerpet#Microsoft Power Platform Online Training in ameerpet
0 notes
Text
Cloud Computing Security Issues?

PC LAP Mall is a leading computer and laptop sales and services center in Saravanampatti
Call : 9952274058 | Call / WhatsApp: 8870708883
PC LAP Mall Google Map Location
Cloud computing has become an integral part of modern business operations, offering scalability, flexibility, and cost-effectiveness. However, as with any technology, cloud computing security issues should be carefully considered and addressed to protect sensitive data and maintain business continuity.
Common Cloud Computing Security Issues
Misconfiguration: Improper configuration of cloud resources, such as storage buckets or virtual machines, can expose sensitive data or grant unauthorized access to malicious actors.
Data Breaches: Hackers may target cloud-based systems to steal sensitive information, such as customer data, financial records, or intellectual property.
Insider Threats: Employees with malicious intent or compromised credentials can pose a significant threat to cloud security, as they have access to internal systems and data.
Denial-of-Service (DoS) Attacks: DoS attacks can overwhelm cloud resources, making them unavailable to legitimate users.
Account Hijacking: Attackers may compromise user credentials to gain unauthorized access to cloud accounts and data.
Insecure Interfaces: Vulnerabilities in cloud-based applications or APIs can be exploited by hackers to gain access to sensitive data.
Lack of Visibility and Monitoring: Insufficient visibility into cloud infrastructure and activities can make it difficult to detect and respond to security threats promptly.
Mitigating Cloud Computing Security Risks
Shared Responsibility Model: Understand the shared responsibility model between cloud providers and customers. Cloud providers are responsible for securing the underlying infrastructure, while customers are responsible for securing their data and applications deployed on the cloud.
Identity and Access Management (IAM): Implement strong IAM practices to control user access to cloud resources. Use multi-factor authentication (MFA) and enforce least privilege principles to restrict access to sensitive data.
Encryption: Encrypt sensitive data both at rest and in transit to protect it from unauthorized access.
Data Loss Prevention (DLP): Implement DLP solutions to monitor and prevent unauthorized data transfer or leakage.
Vulnerability Scanning and Patching: Regularly scan cloud resources for vulnerabilities and apply security patches promptly.
Security Awareness Training: Educate employees on cloud security best practices and how to identify and report suspicious activities.
Incident Response Plan: Develop and test an incident response plan to effectively handle security breaches and data loss incidents.
Continuous Monitoring and Logging: Continuously monitor cloud infrastructure and activities for anomalies and suspicious behavior. Implement centralized logging to track user activities and audit access to sensitive data.
By addressing these security concerns and implementing appropriate safeguards, organizations can effectively mitigate risks and protect their valuable data in the cloud computing environment.
BuyComputer.co.in: Your Computer Shopping Destination
We are One of the Best Computer and Laptop Service center in Saravanampatti, Coimbatore
We service all branded laptops and computers. Mainly, HP Laptop Service Center Dell Laptop Service Center Lenovo Laptop Service Center Samsung Laptop Service Center Acer Laptop Service Center India
If you can't find out near a computer service center, Contact
PC LAP Mall, @ Saravanampatti — Call Now: +91 88 70 70 88 83
0 notes
Text
Difference Between the 3 : Microsoft Azure vs AWS vs Google Cloud

The business industry has transformed overall at 360 degrees. With advanced and modern solutions, the processes have turned easier and faster than ever before. Now, mid to large enterprises have redefined the management processes with next-level tools that include effective CMS software and cloud computing.
The high-performance public Cloud computing network has turned into a new trend. It helps to streamline the data processing and allows users to manage it effectively with easy access.
Presently, Cloud has turned into a crucial part and it is also considered as the key success factor of the next business world. In order to leverage all the benefits of Cloud technology, it is important to know all in-depth about this platform.
In this blog, we have discussed Cloud development services, as well as different trending platforms that allow you to streamline several data management processes and ensure you stay ahead in the competitive edge.
How do different Cloud development Services work?
There are three ways that companies can opt for the different public cloud services –
1. Software as a Service (SaaS) –
This model allows business owners to ake the full benefits of Cloud-based applications.
2. Platform as a Service ( Paas) –
This model offers a runtime environment that allows you to build, manage, and test the solutions in an effective manner.
3. Infrastructure as a Service (IaaS) –
infrastructure It refers to the Cloud hosting infrastructure components that physical data centers. Thus, IaaS is also known as the virtual data center.
Due to the high demand, Cloud has turned as the foremost choice of the mid to large enterprises but among them, three platforms are in high trend and always create a buzz with their functionalities update-
Microsoft Azure
AWS
Google Cloud
Let’s know about these three platforms and the major differences among them –
Microsoft Azure

Microsoft Azure is also referred to as Azure. It is a Cloud computing service launched by the reputed worldwide company Microsoft with the motive to build, test, deploy, and manage the different solutions and services. It is launched under open source for client SDKs and this supports different platforms such as Linux, Microsoft Windows, iOS, and Android.
Main features of Azure
Features of Azure
Here are the major features that why you should opt for the Azure –
Highly compatible with Cloud development platform
Azure supports the modern blockchain technologies
Effective in predictive analytics
Comprehensive IoT integration
Allows to leverage the DevOps features that ensures to avoid future failures.
AWS

AWS is known as the Amazon Web Services. It offers a huge number of the toolset, that allows expanding AWS capabilities and has also turned into an important part of many industries and large-scale businesses. Majorly, AWS focuses on the public Cloud structure.
It helps in managing services for –
Web Application Firewall (WAF)
AWS Inspector
AWS Shield for DDoS protection
GuardDuty for threat detection
AWS Config and CloudTrail for inventory auditing and policy management
For data security, AWS provides:
KMS and CloudHSM services for key management
Encryption at Rest for most storage services
Macie – an AI-driven data loss prevention (DLP) service
Google Cloud Platform

This platform is also called the GCP, it was introduced in the market lastly and has a different enterprise focus. This platform is funded in the best way and experts have in-depth technical knowledge about it. The best reason to opt for this technology is its focuses on modern technologies that include AR, VR, and many more that allow users to leverage the next generation experience.
Reasons to Choose GCP
It is based on the comprehensive container-based model
Hyperscale networking environment
Supports in Developing and deploying cloud-based apps and software
Companies have already this technology for their digital migration and that results in a cost-efficient and greener tech solution
AWS vs Azure vs Google Cloud Customers
AWS is the oldest in the market, and also has huge community support. It has market leaders based customers such as Samsung, Netflix, BMW Airbnb, and Unilever.
Azure is also known for its services and 80% of companies have opted for it. The top brand companies also include in the list such as Johnson Controls, Polycom, Apple, Honeywell, and many more.
Google Cloud is the latest but it has also marked an immense presence in the market and companies have opted such as PayPal, Bloomberg, 20th Century Fox, Dominos, HSBC Bank, and others.
Conclusion
Microsoft Azure, AWS, and Google Cloud are the most trending and popular platforms. Many times companies get confused to opt for which platform, but in order to leverage all the benefits of the tech world, it is important to know all about the three technologies and the functionalities they offer. As these three are very different from each other, but you should the major differences between them and choose your platform as per your project requirements.
#helpdesk#networking#it solutions#managed it services#cloud managed services#it consulting#cloud migration
1 note
·
View note
Text
Data Center Fabric Market to reach USD 151.52 billion by 2028 | Market analyzed by Size, Trends, Analysis, Future Scope, and Demand Forecast
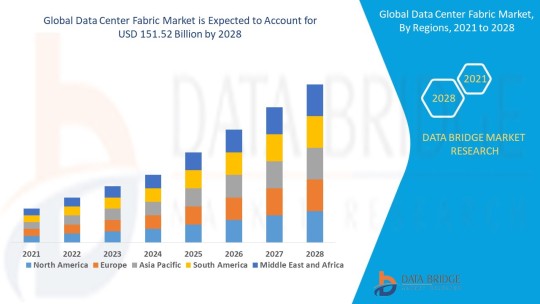
Industry Analysis
Data Bridge Market Research analyses that the Data Center Fabric market will exhibit a CAGR of 22.17% for the forecast period of 2021-2028. Therefore, the data center fabric market value will rocket up to USD 151.52 billion by 2028.
Additionally, the credible Data Center Fabric Market report helps the manufacturer in finding out the effectiveness of the existing channels of distribution, advertising programs, or media, selling methods and the best way of distributing the goods to the eventual consumers. Taking up such market research report is all the time beneficial for any company whether it is a small scale or large scale, for marketing of products or services. It makes effortless for Semiconductors and Electronics industry to visualize what is already available in the market, what market anticipates, the competitive environment, and what should be done to surpass the competitor.
Get a Free Sample of The Report: https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-data-center-fabric-market
Market Insights and Scope
Data center fabric is an integrated system of multiple switches and servers. This integrated system allows and facilitates smooth communication between server and switch nodes. The major aim between the application of data center fabric is to improve the network performance and optimize communication.
Rising focus of the manufacturers on technological advancements will emerge as the major market growth driving factor. Growing infrastructural development especially in the emerging economies like India and China, surging utilization of high-speed data transfer technology and rising research and development proficiencies in regards to complex interactive applications will further aggravate the market value. Growing volume of organizational data and growth and expansion of semiconductors industry especially in the emerging economies will further carve the way for the growth of the market.
The Data Center Fabric Market report encompasses various segments linked to Semiconductors and Electronics industry and market with comprehensive research and analysis. These comprise industry outlook with respect to critical success factors (CSFs), industry dynamics that mainly covers drivers and restraints, market segmentation & value chain analysis, key opportunities, application and technology outlook, regional or geographical insight, country-level analysis, key company profiles, competitive landscape, and company market share analysis. All the data, figures and information are backed up by well recognized analysis tools which include SWOT analysis and Porter’s Five Forces analysis. So, take business to the peak level of growth with the all-inclusive Data Bridge Market research report.
Get full access to the report: https://www.databridgemarketresearch.com/reports/global-data-center-fabric-market
Industry Segmentation and Size
Data center fabric market is segmented on the basis of solutions, process technology, user environment and vertical. The growth amongst the different segments helps you in attaining the knowledge related to the different growth factors expected to be prevalent throughout the market and formulate different strategies to help identify core application areas and the difference in your target market.
The data center fabric market on the basis of solutions has been segmented into switching, routers, controllers, storage area network (SAN), network security equipment and management software.
Based on process technology, the data center fabric market has been segmented into stereo-lithography apparatus (SLA) and digital light processing (DLP), fused Filament fabrication (FFF) processes, jet printing, powder bed fusion (PBF) processes and others.
On the basis of user environment, the data center fabric market has been segmented into enterprises, telecommunications and cloud providers.
On the basis of vertical, the data center fabric market is segmented into high-tech, banking, financial services, and insurance (BFSI), government, healthcare, retail, education, media and entertainment and others.
Market Country Level Analysis
The countries covered in the data center fabric market report are
U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, Israel, Egypt, South Africa, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America.
A reliable Data Center Fabric Market marketing report proves to be the finest and excellent market research report as it is formulated with the following critical factors. These consist of primary research, benchmarking studies, secondary research, company profiles, competitive intelligence & reporting, syndicated research, data collection, data processing and analysis, survey design, and survey programming. The report performs market study and analysis to provide market data by considering new product development from beginning to launch. The Semiconductors and Electronics business report also provides evaluations based on the market type, organization size, availability on-premises, end-users’ organization type, and the availability in areas such as North America, South America, Europe, Asia-Pacific and Middle East & Africa.
Industry Share Analysis
The major players covered in the data center fabric market report are
Cisco Systems, Inc., Hewlett Packard Enterprise Development LP, Broadcom., Huawei Technologies Co., Ltd., NVIDIA Corporation, Arista Networks, Inc., Juniper Networks, Inc., Intel Corporation, Dell., FUJITSU, Microsemi, Lenovo, Vcinity, Apeiron Data Systems, Argo Technology East, American Megatrends International, LLC., Fortinet, Inc., Allied Telesis Holdings K.K., D-Link Corporation and New H3C Technologies Co., Ltd., among other domestic and global players. Market share data is available for global, North America, Europe, Asia-Pacific (APAC), Middle East and Africa (MEA) and South America separately.
Browse Related Reports@
Global Whiskey Market
South Africa Battery Market
Global Plant-Based Egg Market
Global Nutritional Beverages market
MENA Tahini market
Global Dental Membrane and Bone Graft Substitute Market
About Us: Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with an unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market
Contact: Data Bridge Market Research Tel: +1-888-387-2818 Email: [email protected]
#Data Center Fabric Market Growing Popularity#Data Center Fabric Market Global Leading Brands#Data Center Fabric Market drivers-advantages#Data Center Fabric Market Segmentation-CAGR rate#Data Center Fabric Market Demands-Size-Share-Top Trends#Data Center Fabric Market Industry-Competitors#Data Center Fabric Market Growth-Competition#Data Center Fabric Market 2028 by Types-Application#Data Center Fabric Market Semiconductors and Electronics Industry
1 note
·
View note
Text
Cybersecurity Market Size 2022, Industry Trends, Regional Analysis, Segments, Key Players Profile, Statistics and Growth to 2027
The latest study from Astute Analytica examines the global Cybersecurity Market for the forecast period from 2022 to 2027. The report offers an in-depth analysis of top industry trends, market dynamics, and competitive dynamics. Astute Analytica delivers business insight and consulting services to help its clients achieve sustainable growth. The analysis reports are useful for retrieving information and making business decisions.
Request Sample Report for Cybersecurity Market: https://www.astuteanalytica.com/request-sample/cybersecurity-market
The global Cybersecurity Market size was US$ 149.7 billion in 2021. The global Cybersecurity Market size is forecast to reach US$ 346.0 billion by 2027, growing at a compound annual growth rate (CAGR) of 13.40% during the forecast period from 2022 to 2027.
The Cybersecurity Market research report analyzes industry trends, growth patterns, and research methodologies. It also analyzes the factors that influence market growth, including manufacturing strategies, product optimization, and customer retention.
Among the significant factors analyzed in the study are capacity, costs, production, revenue, production rate, consumption, import/export, supply/demand, gross, market share, CAGR, capacity utilization rate, and gross margin.
Impact Analysis of COVID-19:
The impact of the COVID-19 pandemic outbreak appeared to slow global revenue growth. It is evident that life, businesses, and economies have transformed in the past year--a process reflected in revenue increases and decreases. A disruption in production and a slowing demand was evident as workers went home, travel restrictions took place, and delay in raw materials supply. The effects of the pandemic on supply have been most visible. During the early days of the pandemic, companies in the worst-hit countries or companies dependent on supply chains in those countries suffered severely.
Regional Insights:
The report highlights key factors such as R&D, new product launches, M&A, agreements, partnerships, joint ventures, collaborations, and growth of key industry participants from a regional and global perspective. The report covers the regions of North America, Asia Pacific, Europe, Middle East & Africa, and South America. Additionally, the report offers country-level estimates for 25+ countries, including the US, Germany, UK, Japan, China, India, the UAE, South Korea, South Africa, and the Middle East. The regional analysis presents information at the regional and country-level about the market, including the market dynamics based on the segments covered in the report.
Customization of the Report:
This report can be customized to meet the client's requirements. Please connect with our sales team ([email protected]), who will ensure that you get a report that suits your needs. You can also get in touch with our executives on +18884296757 to share your research requirements.
Request Sample Report for Cybersecurity Market: https://www.astuteanalytica.com/request-sample/cybersecurity-market
Leading Competitors:
The leading prominent companies profiled in the global Cybersecurity Market are:
AWS, Intel Corporation, Check Point Software Technologies, McAfee, Oracle, Symantec Corporation, HP Enterprise, IBM Corporation, Cisco Systems, Inc., Rapid7, Inc., EMC RSA, FireEye, Inc., Trend Micro, Inc., Sophos Ltd., SecureWorks, Inc., Imperva, BAE Systems, Carbon Black, Inc., and Other.
Scope of the Report
The global Cybersecurity Market segmentation focuses on By Component, By Security, By Deployment, By Application, By Enterprise Size.
By Component
Identity and Access Management
Security and Vulnerability Management
Risk and Compliance Management
Others
Network DLP
Storage/ Data Center DLP
Endpoint DLP
Design and Integration
Risk and Threat Assessment
Consulting
Training and Education
Support and Maintenance
By Security
Network Security
Endpoint Security
Application Security
Cloud Security
Others
By Deployment
Cloud-based
On-premises
By Application
BFSI
Government
Retail
Healthcare
IT and Telecommunication
Manufacturing
Others
By Enterprise Size
Small and Medium-sized Enterprises
Large Enterprises
The Outline of the Report:
While developing the Cybersecurity Market report, the market segmentation focuses on segments By Component, By Security, By Deployment, By Application, By Enterprise Size, the region. The segmentation provided the basis for identifying companies and analyzing their financial positions, product ranges, and growth prospects. The next step involved studying the core competencies and market shares of leading players in order to predict the degree of competition. The overall size of the market was determined using a bottom-up approach.
About Astute Analytica:
Astute Analytica is a global analytics and advisory company that has built a solid reputation in a short period, thanks to the tangible outcomes we have delivered to our clients. We pride ourselves in generating unparalleled, in-depth, and uncannily accurate estimates and projections for our very demanding clients spread across different verticals. We have a long list of satisfied and repeat clients from a wide spectrum including technology, healthcare, chemicals, semiconductors, FMCG, and many more. These happy customers come to us from all across the globe.
They are able to make well-calibrated decisions and leverage highly lucrative opportunities while surmounting the fierce challenges all because we analyze for them the complex business environment, segment-wise existing and emerging possibilities, technology formations, growth estimates, and even the strategic choices available. In short, a complete package. All this is possible because we have a highly qualified, competent, and experienced team of professionals comprising business analysts, economists, consultants, and technology experts. In our list of priorities, you-our patron-come at the top. You can be sure of the best cost-effective, value-added package from us, should you decide to engage with us.
Get in touch with us:
Phone number: +18884296757
Email: [email protected]
Visit our website: https://www.astuteanalytica.com/
Content source: https://www.astuteanalytica.com/industry-report/cybersecurity-market
Address: BSI Business Park, Sector-63, Noida UP- 201301, India
SOURCE Astute Analytica
0 notes
Text
Enterprise Data Loss Prevention Software Market Research, Global Applications, Recent Trends, Size, Segments, Emerging Technologies and Industry Growth by Forecast to 2027
Market Overview
In its research report, Market Research Future (MRFR), emphasizes that the global enterprise data loss prevention software market 2020 is expected to grow exponentially over the review period, securing a substantial market valuation of USD 2.1 Billion by 2023, and a healthy 21% CAGR over the review period.
Drivers and Restraints
The program for the prevention of corporate data loss helps track and secure sensitive business information and properties. The market for enterprise data loss prevention software is gaining traction as it can reduce the distribution of confidential data through client data centers, identify broken business processes that transfer confidential data, track and secure sensitive material communications to public websites, and others. Information security and storage next-generation are driving the development of the software industry for data loss prevention. One of the major factors that allowed the Data Loss Prevention market to expand is organizations’ growing emphasis on meeting regulatory and enforcement requirements, as well as data saved in the public and private cloud. Factors such as increased data breaches and cyber-attacks are also driving demand for DLP solutions. Such factors have significantly contributed to consumer growth and have emerged as the main drivers of business development.
Segmental Analysis
The global enterprise data loss prevention software market is analyzed on the basis of components, applications, deployment type, and region.
The components are segmented into solution, service, and others.
The deployment type is segmented into on cloud, on-premises, and others.
The applications are segmented IT and telecom, government, healthcare, manufacturing, BFSI, and others.
Regional Analysis
The geographical overview of the global market has been conducted in four major regions, including the sia Pacific, North America, Europe, and the rest of the world.
North America is one of the leading regions across the world based on themarket share in enterprise data loss prevention software market as it has massive demand in many industries, including banking, healthcare, and other sectors. In the North America region, the enterprise data loss prevention software demand is growing with huge demand among various verticals such as manufacturing, retail, healthcare, and others. The prominent companies such as Symantec Corporation (U.S.), and McAfee Inc. (U.S.), are providing enterprise data loss prevention software solutions that can enhance the performance at a reduced cost.
Competitive Landscape
The prominent market players operating in the global market as identified by MRFR are Hewlett-Packard Company (U.S.), Symantec Corporation (U.S.), McAfee Inc. (U.S.), Cisco Systems Inc. (U.S.), Dell EMC (U.S.), Digital Guardian (U.S.), Somansa Technologies Inc. (U.S.) Forcepoint LLC (U.S.), Fidelis Cybersecurity (U.S.), GTB Technologies Inc. (U.S.), and among others.
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions.
Contact:
Market Research Future
+1 646 845 9312
Email: [email protected]
0 notes
Text
Enterprise Software Market Report to Raise Moderately over Global Forecast to 2023
Market Research Future has published a Half-Cooked Research Report on the Global Enterprise Data Loss Prevention Software Market.
Market Overview
In its research report, Market Research Future (MRFR), emphasizes that the global enterprise data loss prevention software market 2020 is expected to grow exponentially over the review period, securing a substantial market valuation of USD 2.1 Billion by 2023, and a healthy 21% CAGR over the review period.
Get Free Sample Report:
https://www.marketresearchfuture.com/sample_request/4273
Drivers and Restraints
The program for the prevention of corporate data loss helps track and secure sensitive business information and properties. The market for enterprise data loss prevention software is gaining traction as it can reduce the distribution of confidential data through client data centers, identify broken business processes that transfer confidential data, track and secure sensitive material communications to public websites, and others. Information security and storage next-generation are driving the development of the software industry for data loss prevention. One of the major factors that allowed the Data Loss Prevention market to expand is organizations' growing emphasis on meeting regulatory and enforcement requirements, as well as data saved in the public and private cloud. Factors such as increased data breaches and cyber-attacks are also driving demand for DLP solutions. Such factors have significantly contributed to consumer growth and have emerged as the main drivers of business development. The that demand for enterprise data loss prevention software is due to the cloud-based Web protection service and protection broker for cloud access will ensure a secure web interface and protect organizational data. The companies are now gaining flexibility in the secure handling of sensitive data. This platform is highly scalable, challenges automated blocks, offers excellent coverage of the cloud, prioritizes sensitive data, compliant with forensic analysis, and others. Adopting cloud storage, and rising mid-market penetration, avoidance of data loss can be provided as a managed service.
Segmental Analysis
The global enterprise data loss prevention software market is analyzed on the basis of components, applications, deployment type, and region.
The components are segmented into solution, service, and others.
The deployment type is segmented into on cloud, on-premises, and others.
The applications are segmented IT and telecom, government, healthcare, manufacturing, BFSI, and others.
Regional Analysis
The geographical overview of the global market has been conducted in four major regions, including the sia Pacific, North America, Europe, and the rest of the world.
North America is one of the leading regions across the world based on themarket share in enterprise data loss prevention software market as it has massive demand in many industries, including banking, healthcare, and other sectors. In the North America region, the enterprise data loss prevention software demand is growing with huge demand among various verticals such as manufacturing, retail, healthcare, and others. The prominent companies such as Symantec Corporation (U.S.), and McAfee Inc. (U.S.), are providing enterprise data loss prevention software solutions that can enhance the performance at a reduced cost.
The enterprise data loss prevention software market in the European region is expected to witness rapid growth in the forthcoming period. Over the past years, most of the large organizations in this region, including oil and gas, healthcare, utilities, and banks, have strengthened their data security capabilities.
Meanwhile, Asia-Pacific countries like China, Japan, and India is an emerging market for enterprise data loss prevention software market and poised to record the fastest CAGR in the forthcoming years.
For More Details:
https://www.marketresearchfuture.com/reports/enterprise-data-loss-prevention-software-market-4273
Competitive Landscape
The prominent market players operating in the global market as identified by MRFR are Hewlett-Packard Company (U.S.), Symantec Corporation (U.S.), McAfee Inc. (U.S.), Cisco Systems Inc. (U.S.), Dell EMC (U.S.), Digital Guardian (U.S.), Somansa Technologies Inc. (U.S.) Forcepoint LLC (U.S.), Fidelis Cybersecurity (U.S.), GTB Technologies Inc. (U.S.), and among others.
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
0 notes
Text
5 Qualities of a Good Cloud Solution Provider in Mississauga
If you want everything to be done properly, then you should do it properly as they say. In the DIY logic when it comes to storage, you can do it yourself, but having cloud services can give you more options. Especially when it comes to cost control, flexibility, speed, security, access, and recovery from disasters. Having a cloud solution provider in Mississauga will safeguard client data and will stay relevant to the trends. To help you identify the good ones, we’ll show you the traits you need to look out for.

What to look for in a cloud provider
1. A strong and confident client base.
Technology is as good as the people behind it, that’s why you need to know that the company behind your cloud is worth its salt. You can dig into their client base and make sure their company is well-regarded, having served organizations like yours before, there haven’t been any major security incidents, and that they are generally a trustworthy bunch.
2. A robust data center.
If you decide to rely on your provider’s servers in their datacenter, then you need to know that the data center has the physical and environmental controls monitoring and alerting, redundancies, security traps, and staffing to keep your environment secure and running. A tour may not be necessary, but details on safeguard are.
3. Full disaster recovery capabilities.
Backups are important but can be insufficient on their own. Your cloud needs to have automatic failovers in the event of internet, power, and hardware failures. Your data should be live-replicated to a secondary location so that your environment is protected even if the main data center is destroyed. You need to ask the provider “what if” and see how they will respond.
4. Written data security policies.
Your cloud service provider should have documentation of their permissions, malware protection, patching policies and procedures, incident response policy and reporting, and other security policies that are currently in place. They regulate the way that network requests are handled, which in turn can obviate the need for human intervention. This is always a great way to keep things moving quickly and efficiently, without delay. They should be able to share this documentation with you too.
5. A roadmap for future security initiatives.
Contentment when it comes to technology is a dangerous thing according to VBS IT Services. Hackers don't stop advancing their methods, that’s why your provider is obligated to do the same. Whether the roadmap involves migrating to a better datacenter, implementing data loss prevention or DLP, implementing two-factor authentication, or researching access-based enumeration or ABE, there needs to be a methodical forward movement. If you are evaluating providers, ask if they can give you a high-level explanation of their plan.

These should be considered as the minimum requirements when selecting a cloud provider. If they cannot satisfy themselves won’t satisfy your needs, and they won’t last long anyhow. Check this out to find a professional cloud service provider that will help you and your business. After all, it’s better to be prepared than to lose all your precious data.
0 notes
Text
Data Center Market 2028 by Growing Popularity and Growing Traffic Research Report

Industry Analysis
Data Bridge Market Research analyses that the data center fabric market will exhibit a CAGR of 22.17% for the forecast period of 2021-2028. Therefore, the data center fabric market value will rocket up to USD 151.52 billion by 2028.
Additionally, the credible Data Center Market report helps the manufacturer in finding out the effectiveness of the existing channels of distribution, advertising programs, or media, selling methods and the best way of distributing the goods to the eventual consumers. Taking up such market research report is all the time beneficial for any company whether it is a small scale or large scale, for marketing of products or services. It makes effortless for Semiconductors and Electronics industry to visualize what is already available in the market, what market anticipates, the competitive environment, and what should be done to surpass the competitor.
Get a Free Sample of The Report: https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-data-center-fabric-market
Market Insights and Scope
Data center fabric is an integrated system of multiple switches and servers. This integrated system allows and facilitates smooth communication between server and switch nodes. The major aim between the application of data center fabric is to improve the network performance and optimize communication.
The wide-ranging Data Bridge market report covers an array of aspects of the market analysis which today’s businesses call for. This market document also defines a chapter on the global market and allied companies with their profiles, which provides important data pertaining to their insights in terms of finances, product portfolios, investment plans, and marketing and business strategies. This market research report is generated with a nice blend of industry insight, talent solutions, practical solutions and use of technology to advance user experience. An outstanding Data Bridge market report puts light on many aspects related to Semiconductors and Electronics industry and market.
Get full access to the report: https://www.databridgemarketresearch.com/reports/global-data-center-fabric-market
Industry Segmentation
The data center fabric market on the basis of solutions has been segmented into switching, routers, controllers, storage area network (SAN), network security equipment and management software.
Based on process technology, the data center fabric market has been segmented into stereo-lithography apparatus (SLA) and digital light processing (DLP), fused Filament fabrication (FFF) processes, jet printing, powder bed fusion (PBF) processes and others.
On the basis of user environment, the data center fabric market has been segmented into enterprises, telecommunications and cloud providers.
On the basis of vertical, the data center fabric market is segmented into high-tech, banking, financial services, and insurance (BFSI), government, healthcare, retail, education, media and entertainment and others.
An influential Data Center Market research report displays an absolute outline of the market that considers various aspects such as product definition, customary vendor landscape, and market segmentation. Currently, businesses are relying on the diverse segments covered in the market research report to a great extent which gives them better insights to drive the business on the right track. The competitive analysis brings into light a clear insight about the market share analysis and actions of the key industry players. With this info, businesses can successfully make decisions about business strategies to accomplish maximum return on investment (ROI).
Industry Share Analysis
The major players covered in the data center fabric market report are
Market Country Level Analysis
The countries covered in the data center fabric market report are
U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, Israel, Egypt, South Africa, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America.
Get TOC Details: https://www.databridgemarketresearch.com/toc/?dbmr=global-data-center-fabric-market
Browse Related Reports@
Global Nutritional Beverages market
Global Oral Care/Oral Hygiene Products Market
Global Warehouse Management Logistics Market
Global Carpets & Rugs Market
Global 1, 4-Cyclohexanedimethanol Dibenzoate Market
U.S. Tahini Market
Europe Customer Journey Analytics Market
West Africa Shisha Tobacco Market
About Us:Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with an unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market
Contact: Data Bridge Market Research Tel: +1-888-387-2818 Email: [email protected]
#Data Center Market Growing Popularity and Traffic#Data Center Market Global Leading Brands and Businesses#Data Center Market drivers-advantages-restraints and challenges#Data Center Market Value-Segmentation-CAGR rate-Future Trends to 2028#Data Center Market Demands-Size-Share-Top Trends#Data Center Market Industry Insights-Country-Competitors Research#Data Center Market Growth-Competition-Scenario-Outlook#Data Center Market Global Opportunity Analysis#Data Center Market 2028 by Product-Types-Procedure-Application-End User#Data Center Market Semiconductors and Electronics Industry
0 notes
Text
Enterprise Data Loss Prevention Software Market Data Analysis, Trends and Opportunities forecast year 2025 (SARS-CoV-2, Covid-19 Analysis)
Enterprise Data Loss Prevention Software Market Data
A new market study, titled “Enterprise Data Loss Prevention Software Market Data ” has been featured on Market Research Future.
The enterprise data loss prevention software aids in the monitoring and protection of valuable business information and assets. The next generation of data protection and storage is anticipated to boost the growth of the data loss prevention software (EDLP) market. It aids in the provision of data transmissions in real-time. The study, conducted by Market Research Future (MRFR), and presented in the format of a report, reveals that the enterprise data loss prevention software is gaining momentum in terms of growth due to the rising adoption of cloud-delivered web-security service and cloud access security broker for ensuring a safe web experience for the protection of sensitive organizational data. Owing to this the global enterprise data loss prevention software market size is anticipated to expand at a robust CAGR of 21% during the forecast period.
FREE PDF@
Read on marketresearchfuture.com
The world enterprise data loss prevention software market is estimated to garner a market revenue valuation of USD 2.1 billion by the end of the forecast period. This can be because organizations are gaining flexibility of safe handling of sensitive data. These software are highly scalable, provide impressive cloud coverage, block threat, prioritize sensitive data, and are compatible with the forensic analysis, among other features. Further, the adoption of cloud computing and a rise in the mid-market penetration, the global data loss prevention software is also deployed as a managed service.
Market Segmentation
The global EDLPS market is studied for a detailed segmentation that is based on deployment type, components, applications, and region. Based on components, the global enterprise data loss prevention software market is segmented into service and solution. The solution market is further sub-segmented into endpoint DLP, storage/ data center DLP, and network DLP. The sub-segments of the services segment, as studied in the report include consulting , managed security services, and system integration and installation.
Based on deployment type, the global EDLP software market is segmented into on cloud, and on premise. The EDLP software market is segmented into BFSI, IT and telecommunication, healthcare, government, and manufacturing.
Detailed Regional Analysis
The global market for enterprise data loss prevention software is analyzed into the regions of North America, South America, Asia Pacific, Europe, and the Middle East & Africa. The report has stated that the enterprise data loss prevention software market share is mainly held by North America over the forecast period. The market for enterprise data loss prevention software in the region is witnessing huge demand in several sectors including banking healthcare and banking.
The (EDLP) enterprise data loss prevention software market in Europe is anticipated to expect rapid growth in the forthcoming years. Europe’s market is likely to garner the second position in the global enterprise data loss prevention software market over the forecast period. This can be accredited to the huge deployment noted in this regional market for proactive web communications, applications, and email, prevention of personal identifiable information and intellectual property from being leaked through cloud-based applications.
On the other hand, Asia Pacific is anticipated to gain maximum growth in the global enterprise data loss prevention software market. China, Japan, and India are observed to emerge as prominent growth pockets in the global market for enterprise data loss prevention software. This can be causative to the rising adoption of cloud-computing services in major organizations, especially in developing nations.
Key Players
Some prominent players in the global enterprise data loss prevention software market, as profiled in the latest report include Dell EMC (U.S.), Hewlett-Packard Company (U.S.), McAfee Inc. (U.S.), Symantec Corporation (U.S.), Cisco Systems Inc. (U.S.), Digital Guardian (U.S.), Somansa Technologies Inc. (U.S.) Fidelis Cybersecurity (U.S.), Forcepoint LLC (U.S.), and GTB Technologies Inc. (U.S.).
More Information@

Enterprise Data Loss Prevention Software Market Research Report | MRFR
Enterprise Data Loss Prevention Software Market is growing rapidly over 21% of CAGR | Enterprise���
Read on marketresearchfuture.com
About Market Research Future:At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Reports (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research and Consulting Services.Contact:Market Research Future+1 646 845 9312Email: [email protected]
#Enterprise Data Loss Prevention Software Market Data#Enterprise Data Loss Prevention Software Market
0 notes
Text
8 Tips to Stay Ahead of Data Protection Trends
What could be the best ways for Data Protection? In a world where businesses are increasingly feeling the heat and pressure to go digital, data protection is growing more contentious than ever! Data protection today is made up of three vital domains (Data Loss Preventions, storage system recovery, and data security) that have all been reinvented over the past year or so thanks to some very tech trends around. Well, it is becoming pretty hard to keep up the pace with these trends but this article will take you through some of the tips to keep you on top of your game in terms of maximizing your data protection investment.

Data Protection Trends
1. Speed Up Your Digital Transformation
The first thing you will need to do is to fasten your enterprise’s digital transformation in a bid to tackle a wide array of challenges facing enterprise IT today. As a matter of fact, stats show that the coming years will see a massive growth in infrastructure related to digital technology. Well, the key is to find a way to tap into existing investments dealt into your infrastructure. One such investment is your data protection solution that has to be properly crafted in a bid to streamline backup and recovery over virtual and physical workloads. The beauty with this sort of approach is that you will not have to worry about the disparity in data location and you will find it very easy to leverage the power of converged data protection.
2. Jump Ahead of Escalating data
The amount of data is exponentially growing every passing day. Back in 2014, IDC predicted that the amounts of data will double every two years not to mention that by the year 2020, the amount would have increased by 10 fold! That is exactly why you need to stay ahead of the game! One way to manage your data growth is to make use of integrated deduplication from the source to the unified backup appliance. This will save you a great deal of backup time while also ensuring that the storage footprint and the network loads are reduced. This approach will also help you optimize repetitions that will soften the landing spot in case your enterprise experiences a data-related disaster.
The other thing you can do is to look for solutions to help you put your data under the microscope, perhaps through maps and visual presentations. This way, you can manage your data well and reduce your enterprise’s risk levels.
3. Embrace the Hybrid Cloud
A Hybrid cloud is an integrated cloud-computing environment where the private cloud and the public cloud are utilized within an organization. Most organizations are now evolving into the hybrid cloud model and the trend is bound to roll into the coming years. This will even include scaling on-premise data centers to public and private clouds. Just keep in mind that data security is vital when using the cloud thus you should always opt for cheapest SSL certificates that allow you to protect your enterprise data during the online transition.
4. Optimize Existing Solutions
According to the IDC, by the year 2020, all x86 servers will be located outside traditional data centers as enterprises continue to adopt cloud computing, mobility, analytics, etc. The workloads remaining on the data centers will be used in undertaking colossal services e.g. Oracle databases meaning that there will be no room for faults. Therefore, look into finding a solution that delivers fast backup and recovery metrics coupled with self-service capabilities.
5. Cut on Cost and Complexities
Many organizations are finding it very cumbersome to build servers from scratch in that the task tends to consume many resources. Talk of loading operating systems, installing apps among other things that can peg back deployment cycles. It has been predicted that most enterprises will seek to purchase storage as a physical appliance over the next couple of years. In other words, IT teams in enterprises are encouraged to work towards delivering policy-based services across hybrid architectures instead of focussing on maintaining components.
6. Streamline Multi-Vendor Virtualization
There is no denying that virtualization has gained a lot of ground over the past few years but the real debate has to be in the pros and cons of deploying multiple hypervisor environments. Still, analysts seem to agree on one thing; it is wise to go for a data protection and management solution that supports multi-hypervisors. In other words, the solution must support cloud and on-premise virtual machines.
7. Integrate and Simplify Global Snapshot Management
The need to manage tight backup and recovery Service Level Agreements (SLA) has seen a rise in two key components of data protection strategy: Snapshot and replication. Snapshots are actually effective in backup and recovery but they then end being another incongruent system in IT scenery. To manage them, it is advisable to go for an enterprise-class data protection solution together with an integration strategy that ensures snapshot management is easy to replicate, initiate and automate. It is also smart to make sure that you can be able to do granular recovery up to the file level out of any snapshot image replicated.
8. Make Strides Towards “IT AS SERVICE” Model
Adopting IT AS Service sort of model shifts some tasks that are usually seen to be in the domain of backup admins to other business users. For instance, if an IT admin or data scientist is given policy-based access to self-service backup, this will not only devolve IT resources but also improve agility and productivity. This means that enterprises should opt for a single solution that can provide such a capability whilst also support data protection needs. After all, every company out there is craving for on-demand services and technologies that increase business value.
Conclusion
It is always important to keep in mind that no data protection solution is perfect. Nevertheless, you can always strive to deliver a data protection strategy that will strike a balance between products and services from multiple domains. So, why not audit your enterprise to see if you have the right blend of best practices/trends in DLP, storage system protection, and cybersecurity.
0 notes
Text
Enterprise Data Loss Prevention Software Industry Share, Synopsis and Highlights, Key Findings, Major Companies Analysis and Forecast to 2027
Market Overview
In its research report, Market Research Future (MRFR), emphasizes that the global enterprise data loss prevention software market 2020 is expected to grow exponentially over the review period, securing a substantial market valuation of USD 2.1 Billion by 2023, and a healthy 21% CAGR over the review period.
Drivers and Restraints
The program for the prevention of corporate data loss helps track and secure sensitive business information and properties. The market for enterprise data loss prevention software is gaining traction as it can reduce the distribution of confidential data through client data centers, identify broken business processes that transfer confidential data, track and secure sensitive material communications to public websites, and others. Information security and storage next-generation are driving the development of the software industry for data loss prevention. One of the major factors that allowed the Data Loss Prevention market to expand is organizations’ growing emphasis on meeting regulatory and enforcement requirements, as well as data saved in the public and private cloud. Factors such as increased data breaches and cyber-attacks are also driving demand for DLP solutions. Such factors have significantly contributed to consumer growth and have emerged as the main drivers of business development. The that demand for enterprise data loss prevention software is due to the cloud-based Web protection service and protection broker for cloud access will ensure a secure web interface and protect organizational data. The companies are now gaining flexibility in the secure handling of sensitive data. This platform is highly scalable, challenges automated blocks, offers excellent coverage of the cloud, prioritizes sensitive data, compliant with forensic analysis, and others. Adopting cloud storage, and rising mid-market penetration, avoidance of data loss can be provided as a managed service.
Segmental Analysis
The global enterprise data loss prevention software market is analyzed on the basis of components, applications, deployment type, and region.
The components are segmented into solution, service, and others.
The deployment type is segmented into on cloud, on-premises, and others.
The applications are segmented IT and telecom, government, healthcare, manufacturing, BFSI, and others.
Regional Analysis
The geographical overview of the global market has been conducted in four major regions, including the sia Pacific, North America, Europe, and the rest of the world.
North America is one of the leading regions across the world based on themarket share in enterprise data loss prevention software market as it has massive demand in many industries, including banking, healthcare, and other sectors. In the North America region, the enterprise data loss prevention software demand is growing with huge demand among various verticals such as manufacturing, retail, healthcare, and others. The prominent companies such as Symantec Corporation (U.S.), and McAfee Inc. (U.S.), are providing enterprise data loss prevention software solutions that can enhance the performance at a reduced cost.
The enterprise data loss prevention software market in the European region is expected to witness rapid growth in the forthcoming period. Over the past years, most of the large organizations in this region, including oil and gas, healthcare, utilities, and banks, have strengthened their data security capabilities.
Meanwhile, Asia-Pacific countries like China, Japan, and India is an emerging market for enterprise data loss prevention software market and poised to record the fastest CAGR in the forthcoming years.
Competitive Landscape
The prominent market players operating in the global market as identified by MRFR are Hewlett-Packard Company (U.S.), Symantec Corporation (U.S.), McAfee Inc. (U.S.), Cisco Systems Inc. (U.S.), Dell EMC (U.S.), Digital Guardian (U.S.), Somansa Technologies Inc. (U.S.) Forcepoint LLC (U.S.), Fidelis Cybersecurity (U.S.), GTB Technologies Inc. (U.S.), and among others.
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions.
Contact:
Market Research Future
+1 646 845 9312
Email: [email protected]
0 notes