#DSS Educational Training Program
Explore tagged Tumblr posts
Text
JD Dreams Network ने आयोजित किया हेल्थ प्रोडक्ट्स पर ट्रेनिंग प्रोग्राम
Direct Selling Trending News: JD Dreams Network Pvt. Ltd. ने 24 और 25 नवंबर को आगरा में 2 दिवसीय DSS Educational Training Program का आयोजन किया। इस कार्यक्रम का मुख्य उद्देश्य कंपनी के टॉप लीडर्स को स्वास्थ्य संबंधी JD प्रोडक्ट्स के बारे में विस्तृत जानकारी प्रदान करना था, ताकि वे अपने सहयोगियों को प्रभावी ढंग से प्रशिक्षित कर सकें। JD Dreams Network: DSS Educational Training इस महत्वपूर्ण…
#directsellingnow#NetworkMarkeingAwards#Direct Selling Business#Direct Selling News in Hindi#direct selling now#Direct Selling Now (DSN)#Direct Selling Trending News#DSS Educational Training Program#JD Dreams Network#JD Dreams Network Pvt. Ltd.#JD Dreams Network Pvt. Ltd. director Mr. Sumit Gupta#JD Dreams Network Pvt. Ltd. director Mrs. Priya Gupta#Network Marketing (MLM)#Network Marketing Advice#Success In Direct Selling#Sumit Gupta#डायरेक्ट सेलिंग ताज़ा ख़बरें#नेटवर्क मार्केटिंग समाचार
0 notes
Text
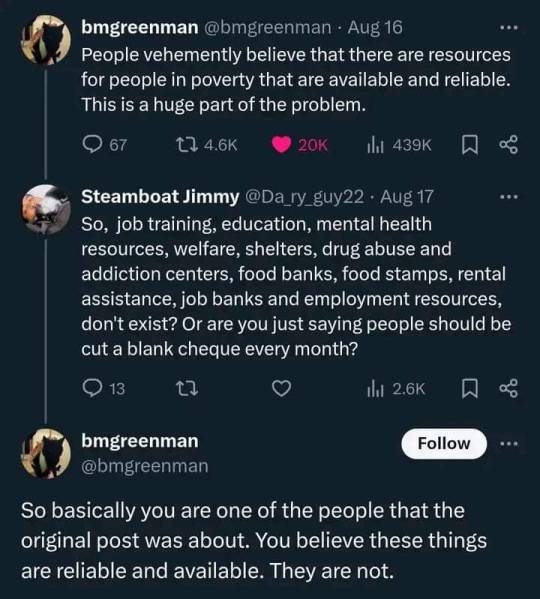
I work at a nonprofit that works with people in these kinds of situations so let's go over what they said here.
Job training does exist, such as through Vocational Rehabilitation, but to get it requires jumping through more hoops than you'd think and the jobs you might get from them are usually at or close to minimum wage. Not enough to get out of poverty by a long shot.
There are better job training services out there such as Project Search, but the program isn't nearly large enough to take on the sheer scale of the people who need it. Funding is limited.
Higher education is usually really expensive unless you get a scholarship, but there's obviously not many of those to go around. Trade schools are a cheaper option and can actually give you the skills and training needed to do a specialized job you could live off of, but you'll be hard pressed to get one even with the right credentials because most places will require experience. You may eventually leave poverty but in the short term you still need some way to not become homeless or die of untreated illness or malnutrition while you're waiting to finish trade school and then finding a scarce entry level trade job.
Welfare and food stamps are kind of in the same bucket in that good luck actually getting it. You may be able to eventually after some appeals but it takes several months to get approved, and there's always the possibility of administrative errors. My consumers have been screwed over by simple errors on the part of the SSA, DSS, and DHHS during crucial vulnerable points of their lives.
They'll send you false bills demanding payback, they'll get your card mailed back to them and not tell you, they'll send false letters of your benefits ending, they'll reject you 90% of the time regardless if you fit their criteria or not. And good luck filling out their forms if you have a disability that hampers your ability to do so. Helping with that aspect is part of what I do.
Shelters are usually at max capacity, simple as that.
Drug abuse and addiction centers may help you get off of your addiction but the problem of no money still remains.
I've never heard of a job bank. I don't think that's a thing in my state. Employment resources are certainly a better option than some of the others on the list but they often run into the same problems as before. Where the jobs offered through them either requiring experience or the job won't pay enough to sustain your bills meaning poverty won't be escaped.
And that's not even getting into the fact that a lot of job postings are ghost positions. They won't actually give you a reply if you apply for them, they just want to seem like they're bringing on new people to give their shortstaffed locations false hope.
So while the things the poster mentioned do exist, and some can be helpful, the ones that genuinely are a lifesaver are also in short supply and underfunded. And everything else is unreliable or extremely hard to get.
57K notes
·
View notes
Text
5 Common Cloud Computing Security Challenges and How to Solve Them
Cloud computing has transformed the way businesses operate by offering scalability, flexibility, and cost-efficiency. However, with the increasing adoption of cloud services, organizations face several cloud computing security challenges. These challenges can expose sensitive data, disrupt operations, and impact customer trust. In this blog, we’ll discuss five common cloud computing security challenges and provide actionable solutions to mitigate them.

1. Data Breaches
The Challenge: Data breaches remain one of the most critical concerns in cloud computing. Unauthorized access to sensitive data can lead to financial losses, legal implications, and reputational damage. Weak access controls, misconfigured storage, or vulnerabilities in the cloud provider’s infrastructure can make your data susceptible to breaches.
The Solution:
Strong Authentication: Implement multi-factor authentication (MFA) to ensure that only authorized users can access the cloud environment.
Data Encryption: Encrypt sensitive data both at rest and in transit to make it unreadable to unauthorized users.
Access Control Policies: Define and enforce strict access control policies, granting permissions based on the principle of least privilege.
Regular Audits: Conduct periodic security audits and penetration testing to identify vulnerabilities and address them promptly.
2. Insider Threats
The Challenge: Employees, contractors, or other insiders with malicious intent or accidental mishandling of cloud resources can pose a significant security risk. Insider threats are often harder to detect because they involve users who already have legitimate access.
The Solution:
User Monitoring: Implement user activity monitoring tools to detect unusual or unauthorized activities.
Role-Based Access Control (RBAC): Assign roles and permissions based on job responsibilities to limit access to critical resources.
Employee Training: Educate employees about security best practices, including recognizing phishing attempts and safeguarding credentials.
Incident Response Plan: Develop and test a robust incident response plan to quickly address any insider-related incidents.
3. Insecure APIs and Interfaces
The Challenge: Application Programming Interfaces (APIs) and user interfaces are essential for interacting with cloud services. However, poorly secured APIs can become a gateway for attackers to exploit cloud resources.
The Solution:
Secure API Design: Use secure API development frameworks and protocols to minimize vulnerabilities.
Authentication and Authorization: Enforce strong authentication mechanisms for API access and implement role-based permissions.
Rate Limiting: Apply rate limiting to prevent API abuse, such as brute-force attacks.
Regular Testing: Conduct regular API vulnerability assessments and patch any identified issues promptly.
4. Compliance and Regulatory Issues
The Challenge: Organizations must adhere to various industry-specific regulations and standards, such as GDPR, HIPAA, or PCI DSS. Non-compliance can result in hefty fines and legal challenges. Managing compliance in a cloud environment can be complex due to the shared responsibility model.
The Solution:
Understand Shared Responsibility: Familiarize yourself with the shared responsibility model to know which security aspects fall under your control versus the cloud provider’s responsibility.
Compliance Management Tools: Use cloud compliance tools to monitor and manage regulatory requirements.
Data Localization: Ensure data is stored and processed in regions compliant with local regulations.
Regular Audits: Partner with your cloud provider to perform regular compliance audits and obtain necessary certifications.
5. Misconfigurations
The Challenge: Misconfigurations in cloud settings are among the leading causes of security breaches. Examples include improperly configured access controls, unsecured storage buckets, or default credentials left unchanged.
The Solution:
Automated Tools: Use configuration management and monitoring tools to identify and fix misconfigurations in real time.
Security Best Practices: Follow cloud provider guidelines and best practices for configuring resources securely.
Continuous Monitoring: Implement continuous monitoring to detect changes in configurations that may introduce vulnerabilities.
Training: Ensure that IT staff are trained in securely setting up and managing cloud environments.
Conclusion
Cloud computing offers numerous benefits, but it’s essential to address the security challenges that come with it. By implementing strong security practices, leveraging the right tools, and staying informed about potential threats, organizations can protect their cloud environments effectively. Addressing issues such as data breaches, insider threats, insecure APIs, compliance challenges, and misconfigurations will ensure the integrity, confidentiality, and availability of your cloud resources.
Organizations must adopt a proactive approach to cloud computing security to stay ahead of evolving threats and maintain trust with customers and stakeholders. By doing so, they can fully embrace the advantages of cloud technology while safeguarding their critical assets.
0 notes
Text
PCI DSS Certification: Ensuring Secure Payment Systems
In an increasingly digital world, securing payment systems is paramount. The Payment Card Industry Data Security Standard (PCI DSS) plays a critical role in safeguarding cardholder data, protecting businesses and consumers alike from fraud and data breaches. PCI DSS certification is more than a compliance checkbox—it’s a commitment to security and trustworthiness.

What is PCI DSS?
PCI DSS is a set of security standards established by the Payment Card Industry Security Standards Council (PCI SSC). It is designed to ensure that all entities involved in handling cardholder data, including merchants, processors, and service providers, maintain a secure environment. The standard applies to organizations of all sizes that accept, process, store, or transmit credit card information.
Why is PCI DSS Certification Important?
Data Security: PCI DSS ensures that sensitive cardholder data is protected from theft and unauthorized access.
Regulatory Compliance: Many jurisdictions mandate PCI DSS compliance for organizations handling payment data.
Customer Trust: Certification signals to customers that your organization prioritizes their security, building trust and loyalty.
Risk Mitigation: Compliance reduces the risk of costly data breaches and potential legal consequences.
Competitive Edge: Being PCI DSS-certified gives businesses an advantage, especially when partnering with other organizations that prioritize security.
Key Requirements of PCI DSS
PCI DSS outlines 12 core requirements organized into six categories:
Build and Maintain a Secure Network: Install and maintain a firewall configuration to protect cardholder data.
Protect Cardholder Data: Encrypt transmission of cardholder data across public networks and maintain secure storage.
Maintain a Vulnerability Management Program: Regularly update antivirus software and develop secure systems.
Implement Strong Access Control Measures: Restrict access to cardholder data on a need-to-know basis.
Monitor and Test Networks: Regularly test security systems and monitor access to cardholder data.
Maintain an Information Security Policy: Create and enforce policies that address security for employees and contractors.
The Certification Process
Gap Analysis: Assess current compliance against PCI DSS requirements.
Remediation: Address any gaps or vulnerabilities identified during the analysis.
Validation: Engage a Qualified Security Assessor (QSA) or complete a Self-Assessment Questionnaire (SAQ) for smaller entities.
Certification: Upon successful validation, the organization receives PCI DSS certification.
Challenges in Achieving PCI DSS Certification
Complexity: Compliance involves a thorough understanding of technical and procedural requirements.
Resource Allocation: Small and medium-sized businesses often face challenges in allocating resources for compliance.
Evolving Threats: Cybersecurity threats are constantly changing, requiring organizations to stay vigilant and adaptive.
Tips for Successful Certification
Engage Experts: Partner with PCI DSS consultants to navigate the process effectively.
Train Staff: Educate employees on security practices and the importance of compliance.
Adopt Technology: Leverage tools like encryption, tokenization, and intrusion detection systems.
Perform Regular Audits: Continuously monitor and update systems to maintain compliance.
Conclusion
PCI DSS certification is not just a technical requirement but a strategic imperative for any organization handling payment data. Achieving and maintaining compliance demonstrates a commitment to securing customer trust and ensuring operational resilience in a rapidly evolving digital economy. By embracing PCI DSS, businesses not only protect sensitive data but also enhance their reputation and competitiveness in the marketplace.
0 notes
Text
Cybersecurity Training Programs: Building a Resilient Workforce

In a world where cyber threats are constantly evolving, cybersecurity training programs are essential for equipping individuals and organizations with the knowledge and skills to prevent attacks. These programs teach employees, IT professionals, and even the general public how to identify risks, respond to incidents, and protect sensitive information effectively.
This guide explores the importance, key components, and examples of effective cybersecurity training programs.
Why Cybersecurity Training Programs Are Important
1. Reduces Human Error
Most cyber incidents occur due to human mistakes, such as falling for phishing scams or using weak passwords. Training empowers users to make informed decisions.
2. Protects Sensitive Data
Educates employees on safeguarding personal, customer, and business-critical information.
3. Enhances Incident Response
Improves the ability to detect and respond to security threats quickly and effectively.
4. Ensures Compliance
Many regulations, such as GDPR, HIPAA, and PCI DSS, require regular cybersecurity training for employees.
5. Mitigates Financial Loss
Prevents costly breaches, downtime, and reputational damage associated with cyberattacks.
Key Components of Cybersecurity Training Programs
1. Understanding Cyber Threats
Educate participants on common cyber threats and their impact.
Examples: Phishing, ransomware, malware, insider threats, and social engineering.
2. Phishing Awareness
Teach employees how to recognize and avoid phishing attempts.
Key Topics:
Identifying fake emails or messages.
Avoiding suspicious links and attachments.
Reporting phishing attempts.
3. Password Management
Highlight the importance of strong, unique passwords and secure storage.
Best Practices:
Use a password manager.
Avoid reusing passwords across accounts.
Enable multi-factor authentication (2FA).
4. Data Protection
Train participants on how to handle and store sensitive data securely.
Topics to Cover:
Encrypting data at rest and in transit.
Sharing information securely.
Preventing data leaks.
5. Incident Reporting and Response
Teach employees how to report and respond to potential security breaches.
Steps to Include:
Recognizing unusual activity.
Escalating incidents to the IT or security team.
Following the organization’s incident response plan.
6. Safe Use of Devices and Networks
Ensure participants understand best practices for securing devices and network connections.
Key Topics:
Avoiding public Wi-Fi for sensitive transactions.
Keeping software updated.
Disabling unnecessary features like file sharing and Bluetooth.
7. Social Engineering Defense
Train employees to recognize and avoid manipulation tactics used by attackers.
Examples: Impersonation, pretexting, and baiting.
Types of Cybersecurity Training Programs
1. General Awareness Training
Designed for all employees to build a foundational understanding of cybersecurity.
Delivery Methods:
Online courses.
In-person workshops.
Regular email tips and reminders.
2. Role-Specific Training
Customized training for employees based on their job responsibilities.
Examples:
IT staff: Advanced technical skills like penetration testing and threat analysis.
HR staff: Safe handling of employee data.
Executives: Strategies for avoiding business email compromise (BEC).
3. Phishing Simulations
Simulated phishing attacks test employees’ ability to recognize and respond to threats.
Benefits:
Identifies at-risk individuals.
Provides real-time learning opportunities.
4. Advanced Technical Training
Geared toward IT professionals and cybersecurity teams.
Topics:
Network security.
Incident response planning.
Vulnerability assessments.
5. Compliance Training
Focuses on meeting regulatory requirements and industry standards.
Examples: GDPR, HIPAA, ISO 27001, PCI DSS.
Examples of Cybersecurity Training Programs
1. Cybersecurity Awareness Month (NCSAM)
An annual initiative in October to promote cybersecurity education.
Activities: Workshops, webinars, and public awareness campaigns.
2. SANS Security Awareness Training
Offers a wide range of courses, from basic awareness to advanced technical training.
3. KnowBe4 Training
Provides simulated phishing attacks and interactive courses to educate employees on security threats.
4. CompTIA Security+ Certification
A globally recognized certification for IT professionals, covering essential cybersecurity skills.
5. Cisco Networking Academy
Focuses on cybersecurity operations and preparing participants for industry certifications.
Implementing an Effective Cybersecurity Training Program
1. Assess Current Knowledge Levels
Conduct surveys or assessments to identify knowledge gaps and tailor the program accordingly.
2. Use Engaging and Interactive Formats
Combine videos, quizzes, real-world scenarios, and hands-on activities to keep participants engaged.
3. Provide Regular Refreshers
Cybersecurity is an ongoing process. Offer periodic training sessions to reinforce knowledge.
4. Measure Success
Track metrics such as training completion rates, phishing simulation results, and changes in incident reporting behavior.
Best Practices for Cybersecurity Training Programs
Make It Mandatory: Ensure all employees participate.
Focus on Real-Life Scenarios: Use examples that are relatable to the workplace.
Encourage Reporting: Create a culture where employees feel comfortable reporting incidents without fear of repercussions.
Keep It Up-to-Date: Regularly update content to address emerging threats.
Recognize and Reward Compliance: Celebrate employees who demonstrate excellent cybersecurity habits.
Conclusion
Cybersecurity training programs are critical for building a resilient workforce that can identify, prevent, and respond to cyber threats. By tailoring training to the needs of your organization, using interactive formats, and reinforcing knowledge regularly, you can significantly reduce risks and foster a culture of security awareness.
Start investing in cybersecurity training today to protect your organization from evolving threats.
FAQs
1. How often should cybersecurity training be conducted? At least annually, with additional refreshers or updates as new threats emerge.
2. Can small businesses afford effective cybersecurity training? Yes, many free or low-cost resources, like online courses and government programs, are available for small businesses.
3. Is phishing simulation necessary? Yes, it helps employees recognize phishing attempts in real-world scenarios and improves response strategies.
4. What certifications are best for IT professionals? Certifications like CompTIA Security+, CISSP, and CEH are valuable for advancing cybersecurity expertise.
5. How can we measure the success of a training program? Track metrics like phishing click rates, incident reporting, and employee feedback to evaluate effectiveness.
0 notes
Text
Cybersecurity Services: Safeguarding the Digital Landscape
In today’s hyperconnected world, cybersecurity services play a critical role in protecting sensitive data, systems, and digital operations from the escalating threat of cyberattack. From individuals to multinational corporations, everyone faces risks such as phishing scams, ransomware attacks, and data breaches. Cybersecurity services are designed to mitigate these dangers, ensuring that your digital assets remain safe and operational integrity is maintained.
These services offer a broad spectrum of solutions to address varying security needs. Core offerings include network security, which defends against unauthorized access and malware, and endpoint security, designed to protect devices like laptops, desktops, and mobile phones. Cloud security has become indispensable as more data moves to remote servers, ensuring sensitive information stored online remains private and protected. Additionally, advanced services like penetration testing identify vulnerabilities in systems, while incident response teams help recover quickly after an attack, minimizing disruptions and losses.
Managed Security Service Providers (MSSPs) have emerged as a go-to solution for businesses seeking reliable and comprehensive protection. MSSPs monitor networks 24/7, conduct regular vulnerability scans, and ensure compliance with industry standards. This outsourced model is especially beneficial for small and medium-sized businesses (SMBs), which often lack the resources to establish in-house security teams. With MSSPs, even smaller organizations can access cutting-edge security without overstretching their budgets.
Cybersecurity also focuses on reducing human error, a leading cause of breaches. Employee training programs are designed to teach staff how to identify and avoid common threats like phishing emails or fake websites. By fostering awareness and encouraging safe online practices, organizations can create a human firewall that complements their technical defenses.
Compliance with regulations is another area where cybersecurity services excel. Industries like finance, healthcare, and retail must adhere to strict standards such as GDPR, HIPAA, or PCI DSS. Security providers help businesses align with these frameworks by implementing proper protocols and conducting regular audits, ensuring compliance and avoiding costly penalties.
The integration of artificial intelligence (AI) and machine learning is revolutionizing cybersecurity. AI tools analyze patterns to detect anomalies, predict potential attacks, and automate responses, making it easier to stay ahead of evolving threats. These intelligent systems not only enhance detection but also reduce response times, providing a crucial advantage in the fight against cybercrime.
As digital environments continue to grow, the importance of cybersecurity services will only increase. Whether it’s protecting personal information, securing corporate networks, or ensuring regulatory compliance, these services are vital for navigating the modern digital age. Collaborating with trusted providers and staying proactive with updates to security measures ensures a resilient defense against emerging risks.
In conclusion, cybersecurity services are an essential safeguard in the ever-changing digital landscape. By combining innovative technology, expert support, and user education, they provide comprehensive protection for individuals and organizations, enabling confidence in a secure digital future.
0 notes
Text
Top Cybersecurity Trends for 2024 and How Businesses Can Stay Ahead

cybersecurity is more crucial than ever. With the rise of cyber threats and data breaches, businesses of all sizes must prioritize their cybersecurity measures. A cybersecurity company plays a vital role in protecting your organization’s data, systems, and reputation. But with numerous options available, how do you choose the right one? In this blog, we’ll explore what a cybersecurity company does, why you need one, and how to select the best provider for your needs.
What is a Cybersecurity Company?
A cybersecurity company specializes in protecting organizations from cyber threats and vulnerabilities. These companies offer a range of services designed to safeguard information systems, prevent cyberattacks, and ensure regulatory compliance. Their expertise spans various areas of cybersecurity, including threat detection, risk management, and incident response.
Key Services Offered by Cybersecurity Companies
Threat Detection and Response: Identifies potential threats and vulnerabilities within your network and provides solutions to mitigate these risks. This includes monitoring for suspicious activity and responding to security incidents in real-time.
Security Assessments and Audits: Conducts comprehensive evaluations of your current security posture, identifying weaknesses and providing recommendations for improvement. This includes vulnerability assessments, penetration testing, and risk assessments.
Managed Security Services: Offers ongoing management and monitoring of your security infrastructure. This includes managing firewalls, intrusion detection systems, and other security technologies to ensure continuous protection.
Incident Response and Recovery: Provides support and guidance in the event of a cyber incident or breach. This includes investigating the breach, containing the damage, and helping you recover and restore normal operations.
Compliance and Regulatory Support: Assists in ensuring that your organization meets industry-specific regulations and standards, such as GDPR, HIPAA, or PCI-DSS. This involves implementing necessary controls and preparing for audits.
Consulting and Strategy: Offers strategic advice on cybersecurity best practices, risk management, and long-term security planning. This includes developing a comprehensive cybersecurity strategy aligned with your business goals.
Training and Awareness: Provides training programs to educate your staff about cybersecurity threats and best practices. This helps in creating a security-aware culture within your organization.
Why You Need a Cybersecurity Company
Protect Against Evolving Threats: Cyber threats are constantly evolving, and staying ahead of these threats requires specialized knowledge and tools. A cybersecurity company has the expertise to protect your organization from the latest threats and vulnerabilities.
Safeguard Sensitive Data: Protecting your organization’s data is critical to maintaining trust and compliance. A cybersecurity company helps ensure that sensitive information remains secure from unauthorized access and breaches.
Maintain Business Continuity: Effective cybersecurity measures help prevent disruptions to your business operations. In the event of a cyber incident, a cybersecurity company provides the necessary support to minimize downtime and recover quickly.
Ensure Compliance: Many industries have strict regulations regarding data protection. A cybersecurity company helps ensure that your organization meets these regulatory requirements, avoiding potential fines and legal issues.
Cost-Effective Security: Investing in a cybersecurity company can be more cost-effective than managing security in-house. It provides access to specialized expertise and advanced technologies without the need for a large internal team.
How to Choose the Right Cybersecurity Company
Assess Your Needs: Determine your specific cybersecurity needs and objectives. This includes understanding the types of threats you face, your compliance requirements, and the level of protection you need.
Evaluate Experience and Expertise: Look for a company with a proven track record and experience in your industry. Check their certifications, client testimonials, and case studies to gauge their expertise.
Review Services Offered: Ensure the company offers the services you require. Some companies may specialize in certain areas, so it’s important to find one that aligns with your specific needs.
Consider Technology and Tools: Evaluate the technologies and tools used by the company. They should use advanced and up-to-date solutions to effectively protect against modern cyber threats.
Check for Customer Support: Choose a company that provides reliable customer support and is responsive to your needs. Effective communication and support are crucial for addressing issues and concerns promptly.
Compare Costs: Obtain quotes and compare pricing among different providers. While cost is important, it should not be the sole factor. Consider the value and quality of the services provided.
Ask for References: Request references from current or past clients to get an understanding of the company’s performance and client satisfaction.
Conclusion
Choosing the right cybersecurity company is a critical decision for safeguarding your organization’s digital assets and ensuring business continuity. By understanding the services offered, evaluating your needs, and carefully selecting a provider, you can enhance your security posture and protect against the ever-evolving cyber threat landscape.
For more information on cybersecurity companies or to find a trusted provider to secure your organization, don’t hesitate to reach out and start your journey towards robust cybersecurity protection.
1 note
·
View note
Text
Navigating Single Parenthood: South Carolina Resources and Support
Single mothers in South Carolina
Single mothers in South Carolina face a range of challenges, from financial strain to finding reliable child care. Fortunately, there are numerous resources available to help ease these burdens and provide support. This article explores various forms of assistance available to single mothers in South Carolina, including financial aid, child care, housing, employment, education, health care, and legal assistance.
>>>>Single mothers in South Carolina<<<<
Financial Assistance Programs
Temporary Assistance for Needy Families (TANF):TANF provides temporary financial support to low-income families with children. Eligible single mothers can receive cash assistance to help cover essential expenses. To qualify, applicants must meet income and family size criteria. Applications can be completed through the South Carolina Department of Social Services (DSS).
Supplemental Nutrition Assistance Program (SNAP):SNAP, formerly known as food stamps, helps low-income families purchase nutritious food. Single mothers can apply for SNAP benefits through DSS. Eligibility is based on income and household size, and benefits are provided via an Electronic Benefit Transfer (EBT) card.
Women, Infants, and Children (WIC):WIC offers nutrition assistance to pregnant women, new mothers, and young children. The program provides vouchers for healthy foods and nutrition education. To qualify, applicants must meet income guidelines and reside in South Carolina. Applications can be made at local WIC clinics.
Child Care Assistance
South Carolina Voucher Program:The South Carolina Voucher Program offers financial assistance to help cover child care costs. Eligible families receive vouchers that can be used at participating child care centers. The program aims to make child care more affordable for working single mothers. Applications can be completed through the South Carolina Department of Social Services.
Head Start and Early Head Start:Head Start and Early Head Start programs provide comprehensive early childhood education and support services. These programs are designed to promote school readiness for children from low-income families. Eligibility is based on income and family size. Interested parents can apply through local Head Start agencies.
Local Nonprofit Child Care Assistance:Several nonprofit organizations in South Carolina offer child care assistance. Organizations such as the United Way of the Midlands and local community groups provide support in the form of subsidies, grants, and free child care services. Contacting these organizations can help single mothers find additional resources.
Housing Assistance
South Carolina Housing Finance and Development Authority (SC Housing):SC Housing offers various programs to assist with affordable housing. These include rental assistance, homebuyer assistance, and foreclosure prevention programs. Single mothers can apply for these programs through SC Housing’s website or local housing authorities.
Section 8 Housing Choice Voucher Program:The Section 8 program provides rental assistance to low-income families. Eligible single mothers can receive vouchers to help cover a portion of their rent. Applications are processed through local public housing agencies, and eligibility is based on income and family size.
Local Housing Authorities and Resources:Local housing authorities in South Carolina offer additional support for affordable housing. These agencies provide information on available rental units, housing subsidies, and other resources. Contacting your local housing authority can provide specific details on available assistance.
Employment and Job Training Programs
South Carolina Department of Employment and Workforce (DEW):DEW offers job search assistance, career counseling, and training programs. Single mothers can access resources to help find employment, enhance skills, and improve job prospects. DEW provides various workshops and services tailored to individual needs.
Local Job Placement Services:Organizations like Goodwill Industries and local community centers offer job placement services and vocational training. These programs assist with resume writing, interview preparation, and job search strategies. Single mothers can benefit from these resources to secure stable employment.
Workforce Investment Act (WIA) Programs:WIA programs provide funding for job training and education. These programs are designed to help individuals gain new skills and find employment. Single mothers can apply for WIA services through local workforce development boards.
Educational Support and Scholarships
South Carolina State Grants and Scholarships:State-funded educational grants and scholarships are available to help cover the costs of college or vocational training. Single mothers can apply for these financial aids through South Carolina’s higher education agencies. Eligibility is based on financial need and academic performance.
Pell Grants and Federal Student Aid:Pell Grants and other federal student aid programs provide financial assistance for education. Single mothers can apply for these grants through the Free Application for Federal Student Aid (FAFSA). Eligibility is determined based on income and financial need.
Local Community Colleges and Universities:Local educational institutions in South Carolina offer support services for single mothers, including childcare on campus, counseling, and academic advising. Exploring these options can help balance education and parenting responsibilities.
Health Care and Medical Assistance
Medicaid and CHIP (Children's Health Insurance Program):Medicaid and CHIP provide health coverage for low-income families and children. Single mothers can apply for Medicaid through DSS, and CHIP offers additional coverage for children in families with higher incomes. Both programs help cover medical expenses and ensure access to necessary care.
Local Health Clinics and Services:South Carolina has several low-cost or free health clinics providing essential medical services. Organizations such as the South Carolina Free Clinic Association offer health care to those without insurance. These clinics provide primary care, dental services, and more.
Mental Health Resources:Mental health services are available through various organizations and clinics in South Carolina. Single mothers can access counseling, therapy, and support groups through local mental health centers and nonprofit organizations.
Legal Assistance and Advocacy
South Carolina Legal Services:South Carolina Legal Services provides free legal assistance to low-income individuals. Single mothers can receive help with issues related to family law, housing, and public benefits. Applications can be made online or through local legal aid offices.
Local Legal Aid Organizations:In addition to South Carolina Legal Services, other local organizations offer legal support. These groups provide advocacy and assistance for single mothers facing legal challenges. Contacting these organizations can help address specific legal needs.
Advocacy Groups and Support Networks:Various advocacy groups support single mothers in South Carolina. These organizations offer resources, support, and community connections. Engaging with these groups can provide additional help and a sense of community.
Practical Tips and Community Resources
Building a Support Network:Connecting with other single mothers and support groups can provide emotional support and practical advice. Online forums, local community groups, and social media platforms can help build a network of peers who understand the unique challenges faced.
Utilizing Community Centers and Services:Community centers often offer programs and services tailored to single mothers. These may include parenting classes, financial workshops, and social events. Engaging with local community centers can provide valuable resources and support.
Budgeting and Financial Planning:Effective budgeting and financial planning can help manage expenses and reduce stress. Single mothers can benefit from financial education resources and tools to better manage their finances and plan for the future.
Conclusion
Single mothers in South Carolina have access to a range of resources designed to support their financial, educational, and personal needs. By exploring the available programs and services, single mothers can find the assistance they need to navigate their challenges and build a stable, successful life for themselves and their children.
FAQs
1. How do I apply for TANF in South Carolina?
You can apply for TANF through the South Carolina Department of Social Services (DSS). Applications can be completed online via the DSS website or in person at a local DSS office.
2. What is the eligibility criteria for SNAP benefits?
Eligibility for SNAP benefits is based on income, household size, and other factors. You can check the specific requirements and apply online through the DSS website.
3. How can I find affordable child care options?
To find affordable child care, you can explore the South Carolina Voucher Program, Head Start, and local nonprofit organizations. Contact these programs for information on eligibility and application processes.
4. Where can I find housing assistance in South Carolina?
Housing assistance can be accessed through SC Housing, Section 8 programs, and local housing authorities. Visit the SC Housing website or contact your local housing authority for more information.
5. What job training programs are available for single mothers?
Single mothers can access job training programs through the South Carolina Department of Employment and Workforce (DEW), local job placement services, and Workforce Investment Act (WIA) programs.
6. How do I apply for educational grants and scholarships in South Carolina?
You can apply for state grants and scholarships through South Carolina’s higher education agencies and for federal aid through the Free Application for Federal Student Aid (FAFSA).
7. Where can I find low-cost health care services?
Low-cost health care services are available through local health clinics and organizations such as the South Carolina Free Clinic Association. Check with these organizations for information on available services.
8. What legal assistance is available for single mothers?
Single mothers can receive legal assistance from South Carolina Legal Services and other local legal aid organizations. These groups offer help with family law, housing issues, and public benefits.
0 notes
Text
Cyber Security Consulting Companies In The USA
Introduction
In today's digital era, cyber security has become a critical concern for businesses of all sizes. With the increasing frequency of cyber threats, the need for specialized expertise in protecting sensitive information has never been greater. This is where Cyber Security Consulting Companies in the USA come into play, offering a range of services to help organizations safeguard their digital assets. One notable player in this field is Tech Workflow, a company renowned for its comprehensive cyber security solutions.
The Importance of Cyber Security Consulting
Cyber security consulting companies provide businesses with the necessary tools and strategies to defend against cyber threats. These companies specialize in identifying vulnerabilities, implementing robust security measures, and ensuring compliance with regulatory standards. By partnering with cyber security consultants, businesses can focus on their core operations while leaving the complex task of security management to the experts.
Key Services Offered by Cyber Security Consulting Companies
Risk Assessment and Management Cyber security consulting companies conduct thorough risk assessments to identify potential threats and vulnerabilities within an organization's IT infrastructure. They then develop and implement risk management strategies to mitigate these threats, ensuring that businesses are well-prepared to handle any security breaches.
Security Audits and Compliance Regular security audits are essential to ensure that an organization's security measures are effective and up to date. Cyber security consultants perform detailed audits and help businesses comply with industry standards and regulations, such as GDPR, HIPAA, and PCI-DSS.
Incident Response and Recovery In the event of a cyber attack, quick and effective response is crucial to minimize damage. Cyber security consulting companies provide incident response services, helping businesses to quickly identify, contain, and recover from security breaches.
Security Training and Awareness Human error is a significant factor in many cyber attacks. To address this, cyber security consultants offer training programs to educate employees about best practices in cyber security, helping to create a culture of security awareness within the organization.
Tech Workflow
A leading Cyber Security Consulting Company Among the numerous Cyber Security Consulting Companies in the USA, Tech Workflow stands out for its exceptional service and innovative solutions. Based in the USA, Tech Workflow has a proven track record of helping businesses protect their digital assets from a wide range of cyber threats.
Comprehensive Cyber Security Solutions
Tech Workflow offers a comprehensive suite of cyber security services tailored to meet the unique needs of each client. Their approach includes detailed risk assessments, proactive security measures, and robust incident response strategies. By leveraging the latest technologies and industry best practices, Tech Workflow ensures that their clients are well-protected against evolving cyber threats.
Expertise and Experience
With years of experience in the cyber security field, Tech Workflow's team of experts possesses deep knowledge and expertise. They stay abreast of the latest trends and developments in cyber security, enabling them to provide cutting-edge solutions to their clients. Whether it's safeguarding sensitive data, ensuring compliance, or responding to security incidents, Tech Workflow's consultants are equipped to handle the most complex challenges.
Client-Centric Approach
Tech Workflow prides itself on its client-centric approach. They understand that each business has unique security needs and challenges. Therefore, they work closely with their clients to develop customized solutions that align with their specific requirements and goals. This personalized approach has earned Tech Workflow a reputation for excellence and reliability in the cyber security consulting industry.
Conclusion
In an increasingly digital world, the role of Cyber Security Consulting Companies in the USA is more crucial than ever. These companies provide essential services that help businesses protect their digital assets and maintain the trust of their customers. Tech Workflow, with its comprehensive solutions, expertise, and client-centric approach, exemplifies the excellence that can be found in this industry. By partnering with a reputable cyber security consulting company like Tech Workflow, businesses can confidently navigate the complex landscape of cyber threats and safeguard their digital frontiers.
0 notes
Text
API Security Best Practices Checklist
Introduction
In the realm of modern web applications, APIs (Application Programming Interfaces) play a crucial role in connecting various systems and enabling seamless data exchange. However, the convenience of APIs comes with significant security challenges. Securing APIs is paramount to safeguarding sensitive data and maintaining the integrity of systems. In this article, we delve into API security best practices to ensure your applications are fortified against potential threats.

Authentication and Authorization
Implement Strong Authentication Mechanisms
Authentication is the cornerstone of API security. Utilize robust authentication methods such as OAuth 2.0 or JWT (JSON Web Tokens) to verify the identity of clients accessing your APIs. Ensure credentials are transmitted securely over HTTPS to prevent interception by malicious actors.
Role-Based Access Control (RBAC)
Authorization defines what authenticated users are permitted to do within your API ecosystem. Implement RBAC to enforce least privilege access, granting permissions based on roles and responsibilities. Regularly review and update access control policies to reflect organizational changes and minimize security risks.
Secure Communication
Transport Layer Security (TLS)
Secure data transmission between clients and servers using TLS (Transport Layer Security). TLS encrypts data in transit, preventing eavesdropping and tampering. Always enforce the use of HTTPS for API endpoints to protect sensitive information from interception.
API Gateway
Deploy an API gateway to centralize control and security policies across API services. A gateway acts as a single entry point for client requests, enabling functionalities such as rate limiting, logging, and request validation. Configure your API gateway to authenticate clients and validate incoming requests before forwarding them to backend services.
Input Validation and Output Encoding
Input Validation
Validate and sanitize all input parameters to mitigate SQL injection, cross-site scripting (XSS), and other injection attacks. Implement strict input validation routines on both client and server sides to ensure only expected data formats are processed by your APIs.
Output Encoding
Encode output data to prevent malicious scripts from executing on client browsers. Use encoding mechanisms such as HTML entity encoding or JavaScript escaping to neutralize potential XSS payloads embedded in API responses.
Logging and Monitoring
Comprehensive Logging
Maintain detailed logs of API activities, including request parameters, user identities, and response statuses. Logging helps in auditing and forensic analysis during security incidents. Ensure log entries are securely stored and accessible only to authorized personnel.
Real-time Monitoring
Implement real-time monitoring to detect suspicious activities or anomalies in API traffic. Leverage SIEM (Security Information and Event Management) solutions to correlate events across your infrastructure and trigger alerts for potential security breaches.
Security Testing and Continuous Integration
Automated Testing
Integrate security testing into your CI/CD pipelines to identify vulnerabilities early in the development lifecycle. Conduct regular penetration testing and vulnerability assessments to evaluate the resilience of your APIs against evolving threats.
Secure Development Lifecycle (SDLC)
Adopt a secure SDLC approach by integrating security practices from design through deployment. Educate developers on secure coding practices and conduct regular security training sessions to foster a security-aware culture within your organization.
Compliance and Governance
Regulatory Compliance
Adhere to industry-specific compliance requirements such as GDPR, HIPAA, or PCI DSS when handling sensitive data through APIs. Implement controls to protect data privacy and ensure lawful processing of user information.
Security Governance
Establish robust security governance frameworks to define policies, procedures, and controls governing API security. Conduct periodic security assessments and audits to validate compliance with internal policies and external regulations.
Incident Response and Recovery
Incident Response Plan
Develop and maintain an incident response plan outlining procedures to address security breaches affecting your APIs. Define roles and responsibilities for incident responders and establish communication protocols for notifying stakeholders.
Disaster Recovery
Implement disaster recovery measures to restore API services in the event of a security incident or infrastructure failure. Maintain backups of critical data and configurations to facilitate rapid recovery and minimize downtime.
Conclusion
Effective API security requires a proactive approach encompassing authentication, authorization, secure communication, input validation, monitoring, and compliance. By adhering to these best practices, organizations can mitigate risks associated with API vulnerabilities and uphold the trust of users and stakeholders.
For more information on securing your APIs, consult with our team of security experts who specialize in safeguarding digital assets against emerging threats.
0 notes
Text
The Ultimate Cybersecurity Partner: Bantech Cyber’s Comprehensive Services
In a world where cyber threats are becoming increasingly sophisticated, finding the right cybersecurity partner is paramount. Bantech Cyber offers a suite of comprehensive services that positions us as the ultimate choice for organizations seeking robust, proactive, and tailored cybersecurity solutions. Our approach goes beyond traditional security measures, delivering an integrated strategy that ensures the highest level of protection for your business.

Why Bantech Cyber is Your Ideal Cybersecurity Partner
Cybersecurity is not just about preventing attacks; it's about creating a resilient defense system that evolves with the threat landscape. Bantech Cyber excels in providing a holistic cybersecurity strategy that encompasses every aspect of digital security. Our services are designed to address current challenges while anticipating future risks, ensuring that your organization remains secure and operational at all times.
Bantech Cyber’s Comprehensive Service Offerings
1. Advanced Threat Detection and Prevention
Our Advanced Threat Detection and Prevention solutions leverage cutting-edge technologies to identify and neutralize threats before they can impact your operations. We utilize AI-powered analytics and machine learning algorithms to detect unusual activities and potential threats in real-time. Our system's ability to predict and prevent attacks ensures that your business is always one step ahead of cybercriminals.
2. Comprehensive Vulnerability Management
Vulnerabilities in your system can be a gateway for cyberattacks. Bantech Cyber’s Comprehensive Vulnerability Management service focuses on identifying, assessing, and mitigating potential weaknesses in your infrastructure. Our process includes regular vulnerability scans, penetration testing, and patch management to ensure that any potential security gaps are promptly addressed.
3. Tailored Incident Response and Recovery
In the event of a cyber incident, swift and effective response is crucial. Bantech Cyber’s Tailored Incident Response and Recovery service provides a structured approach to managing and mitigating incidents. Our incident response team is equipped with the expertise and tools to handle breaches efficiently, conduct forensic analysis, and implement remediation strategies. We work to minimize downtime and restore normal operations as quickly as possible.
4. Continuous Security Monitoring
Our Continuous Security Monitoring service ensures that your systems are under constant surveillance. We operate a 24/7 Security Operations Center (SOC) that monitors and analyzes security events in real-time. This continuous oversight allows us to detect potential threats and vulnerabilities immediately, providing proactive defense and instant response to any security issues.
5. Security Compliance and Risk Management
Navigating the complex world of security compliance and risk management can be daunting. Bantech Cyber offers expert guidance to help your organization adhere to regulatory requirements such as GDPR, HIPAA, and PCI-DSS. Our services include risk assessments, compliance audits, and policy development, ensuring that your security practices align with industry standards and regulations.
6. Data Protection and Privacy
Protecting sensitive data is critical for maintaining customer trust and business integrity. Bantech Cyber’s Data Protection and Privacy services include encryption, data loss prevention (DLP), and secure backup solutions. Our comprehensive approach ensures that your data is safeguarded both in transit and at rest, and that you have robust mechanisms in place to recover data in the event of a breach or loss.
7. Customized Security Training and Awareness
Human error is often a weak link in the cybersecurity chain. Bantech Cyber’s Customized Security Training and Awareness programs are designed to educate your employees about potential threats and best practices. Our training modules cover phishing prevention, secure password policies, and incident reporting procedures, empowering your team to be an active part of your defense strategy.
8. Integrated Security Solutions
In addition to individual services, Bantech Cyber offers Integrated Security Solutions that combine multiple elements into a cohesive security strategy. We work with you to develop a unified security framework that addresses all aspects of your cybersecurity needs, providing seamless protection across your entire digital environment.
The Bantech Cyber Difference
Bantech Cyber’s commitment to excellence is reflected in our approach to cybersecurity. We don’t just provide services; we partner with you to develop a security strategy that fits your unique needs and goals.
Expertise and Experience
Our team of cybersecurity professionals brings years of experience and a deep understanding of the latest technologies and threats. We leverage this expertise to deliver solutions that are both effective and innovative, ensuring that your security measures are always up-to-date and optimized.
Customer-Centric Approach
We prioritize your needs and work closely with you to understand your specific challenges and objectives. Our customer-centric approach means that we tailor our services to meet your unique requirements, providing solutions that align with your business goals and offer the highest level of protection.
Innovative Technology
Bantech Cyber invests in the latest technologies and tools to stay ahead of emerging threats. Our use of advanced technologies such as AI-driven analytics, next-generation firewalls, and cloud security solutions ensures that we deliver cutting-edge protection for your organization.
Proactive Defense
We take a proactive approach to cybersecurity, focusing on prevention and early detection rather than merely reacting to incidents. Our proactive defense strategies are designed to anticipate potential threats and address them before they can impact your business.
Conclusion
Choosing Bantech Cyber as your cybersecurity partner means entrusting your security to a leader in the field. Our comprehensive suite of services, combined with our commitment to innovation and customer satisfaction, positions us as the ultimate choice for businesses seeking unparalleled protection in today’s complex digital landscape. Contact Bantech Cyber today to discover how our tailored solutions can help you achieve a secure and resilient future.
0 notes
Text
Strengthen Your Cyber Defense with Sify's Managed Security Services
In an era where cyber threats are constantly evolving, ensuring robust security for your organization is more critical than ever. Sify’s Managed Security Services (MSS) provide comprehensive, proactive, and scalable security solutions designed to protect your business from the ever-growing landscape of cyber threats.
What are Managed Security Services?
Managed Security Services involve the outsourcing of an organization’s cybersecurity functions to a third-party provider. These services include monitoring, managing, and maintaining security systems and practices, allowing businesses to focus on their core operations while ensuring robust protection against cyber threats.
Key Features of Sify’s Managed Security Services
24/7 Threat Monitoring and Response: Sify’s Security Operations Center (SOC) operates around the clock to monitor network traffic, identify potential threats, and respond to incidents in real-time. This continuous vigilance ensures that threats are detected and mitigated before they can cause significant harm.
Advanced Threat Intelligence: Leveraging global threat intelligence and sophisticated analytics, Sify’s MSS can anticipate and defend against emerging threats. This proactive approach helps in staying one step ahead of cyber adversaries.
Comprehensive Risk Assessment: Sify conducts thorough risk assessments to identify vulnerabilities within your IT infrastructure. This includes regular security audits, penetration testing, and vulnerability scanning to ensure your defenses are always up to date.
Robust Security Architecture: Sify designs and implements a multi-layered security architecture tailored to your business needs. This includes firewalls, intrusion detection/prevention systems (IDS/IPS), secure web gateways, and more, ensuring a strong defensive posture.
Compliance and Regulatory Support: Navigating the complex landscape of regulatory requirements can be challenging. Sify’s MSS ensures that your security practices comply with industry standards and regulations such as GDPR, HIPAA, and PCI-DSS, reducing the risk of non-compliance penalties.
Incident Response and Management: In the event of a security breach, Sify provides expert incident response services to quickly contain and remediate the threat. This includes detailed forensic analysis, root cause identification, and strategic recommendations to prevent future incidents.
Security Awareness Training: Human error is a significant factor in many security breaches. Sify offers comprehensive security awareness training programs to educate your employees about the latest threats and best practices, fostering a culture of security within your organization.
Real-World Impact
Organizations across various sectors have significantly strengthened their cybersecurity posture with Sify’s Managed Security Services. For instance, a major financial institution reduced its incident response time by 50% and achieved full compliance with regulatory standards, thanks to Sify’s continuous monitoring and expert guidance. Similarly, a healthcare provider successfully thwarted multiple cyber attacks, safeguarding sensitive patient data and maintaining trust with their clients.
Why Choose Sify?
Expertise: With decades of experience in cybersecurity, Sify has the knowledge and resources to provide top-tier managed security services tailored to your unique needs.
Innovation: Sify stays at the forefront of cybersecurity advancements, continuously updating its services to incorporate the latest technologies and threat intelligence.
Customization: Sify understands that every business is different. Our managed security services are designed to be flexible and scalable, ensuring they fit seamlessly with your specific requirements.
Comprehensive Support: From initial risk assessments to ongoing threat monitoring and incident response, Sify provides end-to-end security solutions backed by dedicated support teams.
In a world where cyber threats are becoming increasingly sophisticated, having a reliable security partner is essential. Sify’s Managed Security Services offer a robust, proactive, and scalable approach to protecting your business, allowing you to focus on growth and innovation with peace of mind.
Discover how Sify’s Managed Security Services can enhance your cybersecurity posture by visiting our website or contacting our sales team today. Partner with Sify and fortify your defenses against the ever-evolving cyber threats.
0 notes
Text
What are the security measures in place to protect sensitive customer data in inbound call center software?
With the increasing prevalence of cyber threats and regulatory requirements such as GDPR and CCPA, inbound call center software providers have implemented robust security measures to ensure the confidentiality, integrity, and availability of customer information. In this article, we'll explore the security measures in place to safeguard sensitive customer data in inbound call center software.
Encryption of Data Transmission:
Inbound call center software employs encryption protocols such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL) to encrypt data transmitted between the caller's device and the call center's servers. Encryption ensures that sensitive information, including personal identifiable information (PII), is protected from interception by unauthorized parties during transmission over the internet.
Secure Access Controls:
Access controls are implemented to restrict access to sensitive customer data only to authorized personnel. Inbound call center software utilizes role-based access control (RBAC) mechanisms, multi-factor authentication (MFA), and strong password policies to ensure that only authenticated users with the appropriate permissions can access and manipulate customer information.
Data Masking and Redaction:
To prevent unauthorized access to sensitive customer data during call recordings or screen captures, inbound call center software may employ data masking and redaction techniques. Personally identifiable information such as credit card numbers, social security numbers, or account passwords are automatically masked or redacted to protect customer privacy and comply with regulatory requirements.
Secure Storage and Encryption at Rest:
Customer data stored within inbound call center software is encrypted at rest to prevent unauthorized access in the event of a data breach or unauthorized access to storage devices. Encryption keys are managed securely, and encryption algorithms such as Advanced Encryption Standard (AES) are used to encrypt customer data stored in databases or cloud storage solutions.
Regular Security Audits and Compliance:
Inbound call center software providers conduct regular security audits and assessments to identify potential vulnerabilities and ensure compliance with industry standards and regulations. This includes conducting penetration testing, vulnerability scanning, and security assessments to identify and remediate security weaknesses proactively.
Compliance with Data Privacy Regulations:
Inbound call center software adheres to data privacy regulations such as GDPR, CCPA, HIPAA, and PCI DSS to protect sensitive customer data and ensure compliance with legal requirements. Software providers implement features such as consent management, data access controls, and data retention policies to uphold privacy rights and protect customer information.
Employee Training and Awareness:
Inbound call center software providers invest in employee training and awareness programs to educate staff on best practices for handling sensitive customer data, recognizing potential security threats, and adhering to security policies and procedures. Regular training sessions and security awareness campaigns help instill a culture of security consciousness among call center personnel.
Conclusion:
Inbound call center software is equipped with a comprehensive suite of security measures to protect sensitive customer data from unauthorized access, interception, and exploitation. By employing encryption of data transmission, secure access controls, data masking and redaction, secure storage and encryption at rest, regular security audits and compliance checks, adherence to data privacy regulations, and employee training and awareness initiatives, inbound call center software providers ensure the confidentiality, integrity, and availability of customer information. These security measures are essential for instilling trust and confidence among customers and safeguarding their privacy in an increasingly connected and digital world.
0 notes
Text
What are the security measures in place to protect sensitive customer data in inbound call center software?
With the increasing prevalence of cyber threats and regulatory requirements such as GDPR and CCPA, inbound call center software providers have implemented robust security measures to ensure the confidentiality, integrity, and availability of customer information. In this article, we'll explore the security measures in place to safeguard sensitive customer data in inbound call center software.
Encryption of Data Transmission:
Inbound call center software employs encryption protocols such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL) to encrypt data transmitted between the caller's device and the call center's servers. Encryption ensures that sensitive information, including personal identifiable information (PII), is protected from interception by unauthorized parties during transmission over the internet.
Secure Access Controls:
Access controls are implemented to restrict access to sensitive customer data only to authorized personnel. Inbound call center software utilizes role-based access control (RBAC) mechanisms, multi-factor authentication (MFA), and strong password policies to ensure that only authenticated users with the appropriate permissions can access and manipulate customer information.
Data Masking and Redaction:
To prevent unauthorized access to sensitive customer data during call recordings or screen captures, inbound call center software may employ data masking and redaction techniques. Personally identifiable information such as credit card numbers, social security numbers, or account passwords are automatically masked or redacted to protect customer privacy and comply with regulatory requirements.
Secure Storage and Encryption at Rest:
Customer data stored within inbound call center software is encrypted at rest to prevent unauthorized access in the event of a data breach or unauthorized access to storage devices. Encryption keys are managed securely, and encryption algorithms such as Advanced Encryption Standard (AES) are used to encrypt customer data stored in databases or cloud storage solutions.
Regular Security Audits and Compliance:
Inbound call center software providers conduct regular security audits and assessments to identify potential vulnerabilities and ensure compliance with industry standards and regulations. This includes conducting penetration testing, vulnerability scanning, and security assessments to identify and remediate security weaknesses proactively.
Compliance with Data Privacy Regulations:
Inbound call center software adheres to data privacy regulations such as GDPR, CCPA, HIPAA, and PCI DSS to protect sensitive customer data and ensure compliance with legal requirements. Software providers implement features such as consent management, data access controls, and data retention policies to uphold privacy rights and protect customer information.
Employee Training and Awareness:
Inbound call center software providers invest in employee training and awareness programs to educate staff on best practices for handling sensitive customer data, recognizing potential security threats, and adhering to security policies and procedures. Regular training sessions and security awareness campaigns help instill a culture of security consciousness among call center personnel.
Conclusion:
Inbound call center software is equipped with a comprehensive suite of security measures to protect sensitive customer data from unauthorized access, interception, and exploitation. By employing encryption of data transmission, secure access controls, data masking and redaction, secure storage and encryption at rest, regular security audits and compliance checks, adherence to data privacy regulations, and employee training and awareness initiatives, inbound call center software providers ensure the confidentiality, integrity, and availability of customer information. These security measures are essential for instilling trust and confidence among customers and safeguarding their privacy in an increasingly connected and digital world.
0 notes
Text
Multifactor Authentication: Strengthening Identity Security in the Digital Age

In today’s interconnected world, safeguarding digital identities has become paramount. Cyber threats are constantly evolving, posing significant risks to individuals and organizations alike. In this blog, we delve into the importance of multifactor authentication (MFA) as a robust solution for strengthening identity security and mitigating cyber risks.
Understanding Multifactor Authentication (MFA):
Multifactor authentication is a security measure that requires users to provide two or more verification factors to access a system or application. These factors typically include something the user knows (e.g., password), something the user has (e.g., smartphone or hardware token), and something the user is (e.g., biometric data like fingerprint or facial recognition).
The Importance of MFA in Identity Security:
Enhanced Security: MFA adds an extra layer of protection beyond passwords, reducing the risk of unauthorized access due to compromised credentials.
Mitigation of Credential Theft: With MFA in place, even if a password is compromised, additional factors are required for authentication, minimizing the impact of credential theft.
Compliance Requirements: Many regulatory standards and data protection laws, such as GDPR and PCI DSS, mandate the use of MFA to ensure secure access to sensitive information.
User Convenience: Modern MFA solutions offer seamless and user-friendly authentication methods, balancing security with convenience for users.
Types of Multifactor Authentication:
Passwords + One-Time Passcodes (OTPs): Users combine their passwords with unique, time-sensitive OTPs generated via SMS, email, or authenticator apps.
Biometric Authentication: Utilizes unique biological traits such as fingerprints, facial features, or iris scans for identity verification.
Hardware Tokens: Physical devices that generate OTPs or cryptographic keys, providing an additional layer of security.
Mobile-Based Authentication: Leveraging smartphones for authentication via push notifications, biometrics, or mobile authenticator apps.
Benefits of MFA for Businesses:
Reduced Risk of Data Breaches: MFA significantly reduces the risk of unauthorized access and data breaches, protecting sensitive information.
Compliance Adherence: Organizations can meet regulatory requirements and industry standards by implementing MFA as part of their security policies.
Increased Trust and Customer Satisfaction: MFA reassures customers and stakeholders about the security measures in place, enhancing trust and satisfaction.
Protection Against Phishing and Social Engineering: MFA adds a barrier against phishing attacks, as even if credentials are phished, additional factors are needed for authentication.
Best Practices for Implementing MFA:
Choose the Right Authentication Factors: Select authentication factors based on security requirements, user convenience, and regulatory compliance.
Educate Users: Provide training and awareness programs to educate users about the importance of MFA and secure authentication practices.
Implement Risk-Based Authentication: Utilize risk-based authentication to dynamically adjust MFA requirements based on risk levels and threat detection.
Integrate MFA with Identity Governance: Integrate MFA solutions with identity governance and administration (IGA) platforms for centralized management and policy enforcement.
Conclusion
Multifactor authentication is a crucial component of modern identity security strategies, offering robust protection against cyber threats and unauthorized access. By implementing MFA solutions tailored to their needs, organizations can strengthen security, enhance compliance, and build trust with stakeholders in an increasingly digital and interconnected landscape. Embracing MFA as a proactive security measure is essential for safeguarding digital identities and mitigating cyber risks effectively.
0 notes
Text
Steps to Achieving PCI DSS Compliance in Botswana

PCI DSS Certification in Botswana - As digital transactions continue to rise in Botswana, ensuring the security of payment card data has become paramount for businesses operating in the financial sector. The Payment Card Industry Data Security Standard (PCI DSS) is a set of comprehensive requirements designed to enhance the security of credit and debit card transactions and protect cardholders against fraud and data breaches. For businesses in Botswana, achieving PCI DSS certification not only enhances customer trust but also ensures compliance with global security standards, thereby facilitating smoother international business operations.
In Botswana, the adoption of PCI DSS certification is gaining momentum as more companies recognize the importance of safeguarding sensitive payment information. This certification involves a series of rigorous steps, including the implementation of robust security measures, regular monitoring, and periodic audits to ensure ongoing compliance. By adhering to PCI DSS standards, businesses can significantly reduce the risk of data breaches and associated financial losses.
PCI DSS Implementation in Botswana
Conducting a Gap Analysis: PCI DSS Implementation in Eswatini - A gap analysis helps identify the areas where a business’s current security practices fall short of PCI DSS standards. This initial assessment is crucial for developing a roadmap to achieve compliance. It involves reviewing existing policies, procedures, and technical measures against the PCI DSS requirements.
Building a Compliance Team: Successful PCI DSS implementation requires a dedicated team. This team should include members from IT, security, compliance, and management. Their role is to oversee the entire implementation process, from planning to execution and ongoing maintenance.
Training and Awareness: Educating employees about PCI DSS and the importance of data security is vital. Regular training sessions should be conducted to ensure that all staff members understand their roles and responsibilities in maintaining compliance.
Regular Monitoring and Testing: Continuous monitoring and testing of security systems and processes are essential to maintain PCI DSS compliance. This includes regular vulnerability scans, penetration testing, and monitoring network traffic for suspicious activity.
PCI DSS Services in Botswana
Consulting Services: PCI DSS consulting services provide expert guidance on achieving and maintaining compliance. Consultants assess the current security posture of an organization, identify gaps, and develop a roadmap for compliance. They offer tailored advice based on the specific needs and challenges of the business.
Gap Analysis and Risk Assessment: PCI DSS Services in Pune - Gap analysis services involve a thorough review of an organization’s existing security measures compared to PCI DSS requirements. This helps identify areas of non-compliance and potential vulnerabilities. Risk assessment services evaluate the risks associated with cardholder data environments and recommend mitigation strategies.
Implementation Services: These services assist businesses in implementing the necessary security controls and processes to meet PCI DSS standards. This includes network security, data encryption, access control measures, and more. Implementation services ensure that all technical and procedural controls are correctly put in place.
Training and Awareness Programs: Training services educate employees about PCI DSS requirements and best practices for data security. These programs are crucial for ensuring that all staff members understand their roles in maintaining compliance and protecting cardholder data.
PCI DSS Audit in Botswana
Engaging a Qualified Security Assessor (QSA): For most businesses, especially those processing large volumes of transactions, engaging a QSA is crucial. QSAs are certified by the PCI Security Standards Council to conduct official PCI DSS assessments. They bring expertise and an unbiased perspective to the audit process.
Submission to Acquiring Bank and Card Brands: The ROC and AOC are submitted to the business’s acquiring bank and relevant card brands. This formalizes the compliance status and ensures that the business is recognized as PCI DSS compliant.
How can I get PCI DSS Certification in Botswana?
B2Bcert Consultants could be a great option when looking for PCI DSS Certification Consultants in Botswana to make sure that international laws are followed and corporate procedures are improved. For the reasons outlined below, choosing B2Bcert as your PCI DSS Certification Consultants in Botswana makes sense. Being able to offer our clients top-notch service at a reasonable cost makes us very proud. For many, one of the primary sources of conflict is the work budget. In contrast to its competitors, B2Bcert provides solutions at reasonable prices without sacrificing the quality of its advisory services.
#PCI DSS Implementation in Botswana#PCI DSS Services in Botswana#PCI DSS Certification Services in Botswana
0 notes