#DEFCON 21
Explore tagged Tumblr posts
Text
An open copyright casebook, featuring AI, Warhol and more

I'm coming to DEFCON! On Aug 9, I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On Aug 10, I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

Few debates invite more uninformed commentary than "IP" – a loosely defined grab bag that regulates an ever-expaning sphere of our daily activities, despite the fact that almost no one, including senior executives in the entertainment industry, understands how it works.
Take reading a book. If the book arrives between two covers in the form of ink sprayed on compressed vegetable pulp, you don't need to understand the first thing about copyright to read it. But if that book arrives as a stream of bits in an app, those bits are just the thinnest scrim of scum atop a terminally polluted ocean of legalese.
At the bottom layer: the license "agreement" for your device itself – thousands of words of nonsense that bind you not to replace its software with another vendor's code, to use the company's own service depots, etc etc. This garbage novella of legalese implicates trademark law, copyright, patent, and "paracopyrights" like the anticircumvention rule defined by Section 1201 of the DMCA:
https://www.eff.org/press/releases/eff-lawsuit-takes-dmca-section-1201-research-and-technology-restrictions-violate
Then there's the store that sold you the ebook: it has its own soporific, cod-legalese nonsense that you must parse; this can be longer than the book itself, and it has been exquisitely designed by the world's best-paid, best-trained lawyer to liquefy the brains of anyone who attempts to read it. Nothing will save you once your brains start leaking out of the corners of your eyes, your nostrils and your ears – not even converting the text to a brilliant graphic novel:
https://memex.craphound.com/2017/03/03/terms-and-conditions-the-bloviating-cruft-of-the-itunes-eula-combined-with-extraordinary-comic-book-mashups/
Even having Bob Dylan sing these terms will not help you grasp them:
https://pluralistic.net/2020/10/25/musical-chairs/#subterranean-termsick-blues
The copyright nonsense that accompanies an ebook transcends mere Newtonian physics – it exists in a state of quantum superposition. For you, the buyer, the copyright nonsense appears as a license, which allows the seller to add terms and conditions that would be invalidated if the transaction were a conventional sale. But for the author who wrote that book, the copyright nonsense insists that what has taken place is a sale (which pays a 25% royalty) and not a license (a 50% revenue-share). Truly, only a being capable of surviving after being smeared across the multiverse can hope to embody these two states of being simultaneously:
https://pluralistic.net/2022/06/21/early-adopters/#heads-i-win
But the challenge isn't over yet. Once you have grasped the permissions and restrictions placed upon you by your device and the app that sold you the ebook, you still must brave the publisher's license terms for the ebook – the final boss that you must overcome with your last hit point and after you've burned all your magical items.
This is by no means unique to reading a book. This bites us on the job, too, at every level. The McDonald's employee who uses a third-party tool to diagnose the problems with the McFlurry machine is using a gadget whose mere existence constitutes a jailable felony:
https://pluralistic.net/2021/04/20/euthanize-rentier-enablers/#cold-war
Meanwhile, every single biotech researcher is secretly violating the patents that cover the entire suite of basic biotech procedures and techniques. Biotechnicians have a folk-belief in "patent fair use," a thing that doesn't exist, because they can't imagine that patent law would be so obnoxious as to make basic science into a legal minefield.
IP is a perfect storm: it touches everything we do, and no one understands it.
Or rather, almost no one understands it. A small coterie of lawyers have a perfectly fine grasp of IP law, but most of those lawyers are (very well!) paid to figure out how to use IP law to screw you over. But not every skilled IP lawyer is the enemy: a handful of brave freedom fighters, mostly working for nonprofits and universities, constitute a resistance against the creep of IP into every corner of our lives.
Two of my favorite IP freedom fighters are Jennifer Jenkins and James Boyle, who run the Duke Center for the Public Domain. They are a dynamic duo, world leading demystifiers of copyright and other esoterica. They are the creators of a pair of stunningly good, belly-achingly funny, and extremely informative graphic novels on the subject, starting with the 2008 Bound By Law, about fair use and film-making:
https://www.dukeupress.edu/Bound-by-Law/
And then the followup, THEFT! A History of Music:
https://web.law.duke.edu/musiccomic/
Both of which are open access – that is to say, free to download and share (you can also get handsome bound print editions made of real ink sprayed on real vegetable pulp!).
Beyond these books, Jenkins and Boyle publish the annual public domain roundups, cataloging the materials entering the public domain each January 1 (during the long interregnum when nothing entered the public domain, thanks to the Sonny Bono Copyright Extension Act, they published annual roundups of all the material that should be entering the public domain):
https://pluralistic.net/2023/12/20/em-oh-you-ess-ee/#sexytimes
This year saw Mickey Mouse entering the public domain, and Jenkins used that happy occasion as a springboard for a masterclass in copyright and trademark:
https://pluralistic.net/2023/12/15/mouse-liberation-front/#free-mickey
But for all that Jenkins and Boyle are law explainers, they are also law professors and as such, they are deeply engaged with minting of new lawyers. This is a hard job: it takes a lot of work to become a lawyer.
It also takes a lot of money to become a lawyer. Not only do law-schools charge nosebleed tuition, but the standard texts set by law-schools are eye-wateringly expensive. Boyle and Jenkins have no say over tuitions, but they have made a serious dent in the cost of those textbooks. A decade ago, the pair launched the first open IP law casebook: a free, superior alternative to the $160 standard text used to train every IP lawyer:
https://web.archive.org/web/20140923104648/https://web.law.duke.edu/cspd/openip/
But IP law is a moving target: it is devouring the world. Accordingly, the pair have produced new editions every couple of years, guaranteeing that their free IP law casebook isn't just the best text on the subject, it's also the most up-to-date. This week, they published the sixth edition:
https://web.law.duke.edu/cspd/openip/
The sixth edition of Intellectual Property: Law & the Information Society – Cases & Materials; An Open Casebook adds sections on the current legal controversies about AI, and analyzes blockbuster (and batshit) recent Supreme Court rulings like Vidal v Elster, Warhol v Goldsmith, and Jack Daniels v VIP Products. I'm also delighted that they chose to incorporate some of my essays on enshittification (did you know that my Pluralistic.net newsletter is licensed CC Attribution, meaning that you can reprint and even sell it without asking me?).
(On the subject of Creative Commons: Boyle helped found Creative Commons!)
Ten years ago, the Boyle/Jenkins open casebook kicked off a revolution in legal education, inspiring many legals scholars to create their own open legal resources. Today, many of the best legal texts are free (as in speech) and free (as in beer). Whether you want to learn about trademark, copyright, patents, information law or more, there's an open casebook for you:
https://pluralistic.net/2021/08/14/angels-and-demons/#owning-culture
The open access textbook movement is a stark contrast with the world of traditional textbooks, where a cartel of academic publishers are subjecting students to the scammiest gambits imaginable, like "inclusive access," which has raised the price of textbooks by 1,000%:
https://pluralistic.net/2021/10/07/markets-in-everything/#textbook-abuses
Meanwhile, Jenkins and Boyle keep working on this essential reference. The next time you're tempted to make a definitive statement about what IP permits – or prohibits – do yourself (and the world) a favor, and look it up. It won't cost you a cent, and I promise you you'll learn something.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/07/30/open-and-shut-casebook/#stop-confusing-the-issue-with-relevant-facts

Image: Cryteria (modified) Jenkins and Boyle https://web.law.duke.edu/musiccomic/
CC BY-NC-SA 4.0 https://creativecommons.org/licenses/by-nc-sa/4.0/
#pluralistic#jennifer jenkins#james boyle#ip#law#law school#publishing#open access#scholarship#casebooks#copyright#copyfight#gen ai#ai#warhol
180 notes
·
View notes
Text
micro
microplastics in our testes which we know is just a dig you said micro just to stress the fact that they are not so big go on mock our packaged plastics give our ego bulbs the squeeze but the situation's drastic some attention if you please we don't want to sound alarmist but DEFCON should be at ten didn't know this stuff could harm us and our little gentlemen but now we know, see how we show environmental regard and all it took was the micro to make its way to our nards rest assured I'm only joking oh no, the plastics are there but the fun that I was poking is pretending that we'd care microplastics in our testes that won't do us any good we don't need polymer plexi we like metaphors of wood go on mock our packaged plastics with these micro tragedies but the situation's drastic some deference if you please we don't want to sound like hippies but our buzz is pretty blown karma hit us in our tipsies and it's left us kinda thrown now we're hopping on the wagon ready to heed all the calls sure there has been some feet draggin' but that was before the balls rest assured I'm only joking oh no, the plastics are there but the fun that I was poking is pretending we now care microplastics in our testes makes us and mother equal we're polluted by our mess we've turned into plastic people (7/21/24)
0 notes
Text





DEFCON 21”
size XXL
—
身幅 63.5cm
着丈 74cm
—
¥7150(tax in)
ラスベガスで毎年開催され、
多くのエンジニアや腕自慢が集まる、
世界最大のハッキングコンテスト
"DEFCON"イベントtee
トライアングルロゴ&3Dグラフィック
0 notes
Text
NoSQLMap: Automated NoSQL Database Enumeration | #Enumeration #NoSQL #NoSQLMap #OffensiveSecurity #Hacking
0 notes
Text
NoSQLMap: Enumeración y Explotación de Bases de Datos NoSQL | #Enumeracion #NoSQL #NoSQLMap #SeguridadOfensiva #Vulnerabilidades #Hacking
0 notes
Text
黑客帝国?论美国Hacker的养成之路
外交部发言人耿爽:事实一再证明,美国才是全球网络空间最大的国家级监听者,是名副其实的“黑客帝国”。“美国中央情报局CIA攻击组织(APT-C-39)��我国进行长达十一年的网络攻击渗透”,平地一声雷,也让吃瓜群众见识了美国黑客帝国的冰山一角。美国“黑客帝国”如何建成?干过什么事?成功地引起了笔者的注意。尽管我们不难看到美国经常性地发布安全报告,论述中国、俄罗斯、伊朗、朝鲜黑客哪家强,以及某某国的黑客又发起了什么行动,但是一到了美国自己,就无辜三连。虽然目前泄露的美国黑客活动并不多,但每一次都在全球网络安全空间投下重磅炸弹,因此,仅凭借以下几件事,称美国为“黑客帝国“也并不为过。
论黑客的养成:Open、free、share,黑客精神虽然逐渐淡化,但依然存在。���国是黑客文化最早诞生的地方,在上世纪50~60年代,第一批黑客就出现在了麻省理工学院。后来,黑客群体逐渐分化,到了90年代,他们开始接受美国政府“招安”,加入美国网安部门。直到2019年,美国依然是最多的黑客聚集地之一。众所周知,软件工程师是个高薪行业,但在美国,黑客的收入是软件工程师的6.4倍。此外,美国黑客的个人特色一般比较强烈,更加推崇自由主义和技术至上。如果说国内的黑客(白帽子)更专注于防护、挖洞等实用型的领域研究。那么美国黑客,就属于什么都搞,什么都涉及:无线电,脑机、甚至连卫星都搞。高薪、技术至上、再加上从小培养的对计算机的兴趣使然,以及青少年更容易满足于炫耀技能带来的巨大快感,低龄化也成为美国黑客的一大时代特点。
黑客的摇篮:罗马不是一日建成的,美国庞大的”黑客“群体从哪里产生?除了自学成才,基本来自国家+教育机构的培养。21世纪开始,各种黑客学校,培训机构在美国迅速涌现。而国家对”黑客“的培养,甚至从小学就开始了。以NSA为例,目前和大学、K-12(美国k-8年级是小学,9-12年级为高中)级别教育机构都有合作机会。���对k-12级的学生,主要是以GenCyber夏令营形式为主,培养他们对网络安全事业的兴趣。甚至,营地会向所有师生参与者免费开放,资金则由NSA和国家科学基金会提供。这也是美国为了解决网络安全专业人才不足的解决方案之一。到了大学,对黑客的培养从原本的夏令营模式发展成专业网络安全课程的学习和实战经验积累,为“就业”做好准备。在1995年6月,美军16名“第一代网络战士”从美国国防大学信息资源管理学院毕业。1999年以来,CAE-CD的高等学校(NSA合作的大学)就为美国输送了第一批网络响应者。此外,NSA还推动了OnRamp II Program项目,通过和大学合作,为学生(必须为美国公民)提供在NSA学习和获得奖学金的机会,同时大学执教人员也可以申请。如果是美国军事学院,美国海军学院,美国空军学院,美国海岸警卫队学院和美国商船学院的军校生,那么还可以参加由NSA组织、美国网络司令部参与活动协同的为期3天的年度网络演习NCX,为成为美国未来的网络安全领导人和网络黑客做准备。2013年,亚利桑那大学陈教授领头的项目组就曾经为国家安全部门培养网络攻防专家,学生的课程里还涵盖了一系列NSA定制的安全课程。通过几年时间的训练,这些学生最终被输送至诸如FBI、CIA和NSA工作。
驱使黑客:逐渐成长的黑客,一部分流入了政府机构,还有很大一部分进入了企业,美国通过几个方式,驱使非“公职”黑客也为其国家网络安全服务。
1、私营合作
黑客成为政府和私营行业进行合作的一个方式。2012年,美国安全局局长Gen. Keith B. Alexander就曾经要求黑客们协助NSA来确保网络安全。
而根据华盛顿邮报的信息,还可以发现情报承包商Booz Allen Hamilton的雇员就曾经为NSA工作工作整整3年,从2012年到2015年。也就是说,国家和私营企业合作,“借用”黑客是现实可能的。
2、投资共生
投资比起“借用”,让美国政府与企业之间的关系更为密切,黑客人才方面的合作也会更加直接与深入。
在美国中情局旗下有一个风险投资部门In- Q-Tel,专为CIA提供风险投资服务。该机构并不��盈利为主要目标,主要任务是对具有重要战略价值的尖端创新技术进行有针对性的投资,并借助这些最新技术强化美国在信息情报方面的搜集和监控能力。因此,其大多数投资交易都服务于美国政府机构,包括中情局、NSA国防情报局、联邦调查局、国土安全部等。
在投资关系网下,网络安全公司FireEye、大数据分析与情报平台Palantir、安全软件厂商ArcSight(已被收购)等接受投资的企业的黑客力量自然可以在一定程度上为美国政府驱使。
3、赛事
每年,美国都会出资举办黑客大赛,让世界各地的黑客对美国的网络软件、武器设备、或者一些重要的程序进行攻击,从而找出漏洞。譬如,在去年8月份举办的Defcon上,美国甚至拿出了F-15喷气式战斗机的数据系统,让黑客进行分析和攻击,最后成功发现了F-15战机的安全漏洞。“国家机器”的运作:如果说全面培养、发展黑客力量是美国黑客帝国的基底,联动民间/私营企业是中坚力量,那么国家体系的运作就是黑客帝国的顶层战略指挥区。
美国有着完整的一套网络黑客运转体系,植根于其网络安全战略之中。
其中,与美国网络空间安全联系较多的部门是国防部(DoD)、美国中央情报局(CIA)、国土安全部(DHS)。
NSA下面有一个专门执行特定目标渗透任务的秘密机构Tailored Access Operations(TAO)。根据前NSA合同工Edward Snowden泄漏的“最高机密”文件,TAO在2010年5月报告成功入侵了墨西哥总统域名的关键电子邮件服务器,访问了总统Felipe Calderon的公开电子邮件帐户。作为NSA的精英黑客部门,TAO每周7天、全天24小时轮班工作,兢兢业业,在上世纪中叶,甚至成功入侵了89个国家的258个目标,主导了279次全球性的入侵行动。
此外,美国的网络黑客有着丰富的作战经验
上世纪90年代起,美国军队开始进行网络战实践,网络黑客被五角大楼列为网络战的主要战士
1995年,一部分高级黑客被五角大楼组织起来,成立信息战红色小组。
1997年,美国的第一批网络战士参加了国家安全局组织的秘密演习。
2005年4月,美军黑客部队正式成军,全称“网络战职能组成司令部”(JFCCNW),”人员或包括美国中央情报局、国家安全局、联邦调查局以及其他部门的专家。在和平时期用来保护美国的信息网络系统安全,在战争时期则负责渗透、监控、摧毁敌网络系统以及窃取情报的任务。
2006年,由美国国土安全部(DHS)主导的演习系列Cyber Storm首次举行,此后约每两年举办一次。
2007年9月,临时网络战司令部成立
2009年10月,网络战司令部正式启动。
可以说,纵观美国黑客的发展离不开国家的一步步引导,这既是一个黑客可以体系化成长、发展的国家,也是一个“每天收集全球各地近50亿条移动电话纪录、窥探德国总理默克尔手机长达十多年之久、每年控制中国境内300多万台电脑主机、向中国境内3600多个网站植入木马的国家。”
黑客本身的力量没有善恶之分,好坏被定义在这种力量如何使用的那一刻。
0 notes
Text
Rsync corrump linkdump

I'm coming to DEFCON! On Aug 9, I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On Aug 10, I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

As per the uje, I've arrived upon a Saturday with a backlog of links that I have not managed to squeeze into the week's newsletters/blogs, so it's time for another linkdump, 22nd in an erratic series. Here's the previous 21:
https://pluralistic.net/tag/linkdump/
Let's start with some seasonal material, and by "seasonal," I of course mean Hallowe'en. Yes, August is the official start of Spooky Season, and yes, I am a monster for insisting on this, but being a monster is the point of Spooky Season (which is what differentiates Spooky Season pushers like me from the creeps who insist that you need to start prepping for Xmas in late September – they're monsters, too, but Yule Monsters are bad) (with the exception of Krampus).
I was a monster kid and now I'm a monster adult. It all started when I was bitten by a radioactive Haunted Mansion at the age of six:
https://memex.craphound.com/2012/10/22/how-a-haunted-mansion-addict-fell-in-love-with-the-greatest-ride-on-earth/
I am a sucker for all things monstrous, and so I was intrigued when I got a book of "creepy-cute" stickers in the mail from a publicist at Simon & Schuster:
https://www.simonandschuster.com/books/The-Creepy-Cute-Sticker-Book/Gaynor-Carradice/Creepy-Cute-Gift-Series/9781507222515
"Creepy-Cute" turns out to be an official designation, embraced by the illustrator GaynorCarradice, who has created several books on these lines, featuring her chibi/monster crossover creations, which do exactly what it says on the tin, by which I mean, there's some genuinely creepy stuff in the mix, along with the cute.

It's when the cute pastels rub up against the gore, skulls, eyeballs and other visceral viscera that these illustrations really kick off some heat – I've rounded up a few of my favorites here:
https://craphound.com/images/creepycute.jpg
One of the surefire signs that Spooky Season is upon us is that the (sometimes NSFW) Tumblr account Halloweenlandmotherfucker emerges from dormancy with a stream of images of vintage Hallowe'en cards (these were a thing!), photos of people in costume and other delightful visual novelties:
https://www.tumblr.com/halloweenlandmotherfucker
Monster culture isn't just for Hallowe'en, of course. The ancient and noble tradition of compiling and publishing bestiaries is alive and well, thanks to RPGs. In the beginning, there was the D&D Boxed Set, with its Monsters and Treasure booklet:
https://www.americanroads.us/DandD/ODnD_Monsters_and_Treasure.pdf
Then came the Monster Manual, the first hardcover D&D book, succeeded by the Fiend Folio, which featured Charlie Stross creations like the githzerai and slaad, Indeed, there was a whole, iconic library of hardcovers that fit perfectly in an oversized backpack that I dragged everywhere so that I could obsessively read and re-read them.
Eventually, these gave way to new hardcovers with new rules as well as new corporate owners (Wizards of the Coast, then Hasbro), culminating in the release of the Open Gaming License, an "open content" license that was a) grossly defective; b) largely irrelevant; and c) hugely controversial in 2023, when Hasbro terminated it:
https://pluralistic.net/2023/01/12/beg-forgiveness-ask-permission/#whats-a-copyright-exception
The Open Gaming License purported to license out game elements that weren't copyrightable (rules, tables, etc), as well as material that you could likely use under copyright exceptions like fair use:
https://www.eff.org/deeplinks/2023/01/beware-gifts-dragons-how-dds-open-gaming-license-may-have-become-trap-creators
And worst of all, it was revocable, so games publishers who tooled up to publish supplements and sourcebooks based on the OGL could have the rug yanked out from under them at any time (that time turned out to be early 2023).
Hasbro's OGL rug-pull had three salutary effects:
I. It gave gamers a crash-course in what was – and wasn't – copyrightable in an RPG design;
It encouraged game developers to look beyond D&D's OGL rules and into truly open (and often superior) alternatives; and
It inflicted so much reputational harm on Hasbro that, 20 months later, they announced that they would release a new set of D&D rules under the Creative Commons Attribution Only 4.0 license:
https://www.dicebreaker.com/games/dungeons-and-dragons-5e/news/dungeons-and-dragons-2024-srd-wont-be-another-ogl-fiasco
Now, CC BY 4.0 is a real-ass license. Notably, it corrects a defect in the earlier versions of the CC licenses that gave rise to a class of predatory copyleft trolls like the odious Pixsy:
https://pluralistic.net/2022/01/24/a-bug-in-early-creative-commons-licenses-has-enabled-a-new-breed-of-superpredator/
If Hasbro follows through on their promise, the new CC materials will kick off with the 2025 release of the next edition of the Monster Manual:
https://dungeonsanddragonsfan.com/new-2024-dnd-monster-manual/
It's wild to think that tabletop RPGs are now a cutting-edge way to learn about digital policy, but on the other hand, D&D arrived in my home around the same time as my Apple ][+, which was also around the time I first heard the name Ronald Reagan (rest in piss).
The legacies of the 80s – RPGs, digital technology and Reaganomics – cast a long shadow. Last month, many of us discovered the hard way that Reaganomics – specifically, the embrace of monopolies as "efficient" – has produced a world of unimaginable brittleness. Millions of people around the world found themselves cut off from ATM cash, flights, hospital care, and many other essentials thanks to the Crowdstrike Blue Screen of Death outage. While many of the explainers have focused on how Crowdstrike fatfingered a software update that crashed all those computers, there's been a lot less commentary about how it is that one company had it in its power to do so much harm.
Writing last week for EFF's Deeplinks blog, my colleague Rory Mir tackled that (far more important) issue:
https://www.eff.org/deeplinks/2024/07/crowdstrike-antitrust-and-digital-monoculture
Market concentration – monopoly – is the common thread wound around so many of our daily horribles. Think of the tech billionaires who threw in their lot with Trump last month. How did they get to be billionaires? Monopoly power. Remember back in 2017, that notorious photo of the tech industry meeting at the top of Trump Tower, with Peter Thiel at Trump's left hand?
https://techcrunch.com/2016/12/14/donald-trump-meets-with-tech-leaders/
People were appalled that this group of corporate leaders, who between them controlled virtually all the technology in our lives, would debase themselves by paying fealty to this buffoonish would-be dictator.
But far more consequential was the fact that you could fit everyone who controlled all of our technology around a single table. Once everyone important to an industry can fit around a single table, it's only a matter of time until they find a table to sit around, and that's when it all starts to go wrong. As the Communist firebrand Adam Smith once wrote, "People of the same trade seldom meet together, even for merriment and diversion, but the conversation ends in a conspiracy against the public, or in some contrivance to raise prices."
Enshittification starts with market concentration. This is a subject I'm going to be going very deep on next Saturday, when I give my Defcon keynote, "Disenshittify or die! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification":
https://info.defcon.org/event/?id=54861
When I give that talk – and afterwards at my book signing – I will be wearing an N95 mask, just as I did last year. Why am I wearing a mask? Two reasons: first, Long Covid is a horror. One of the best writers I know – a living legend – recently told me that their book-writing days are likely done because of Long Covid brain fog.
A new Lancet article gets deep into the science of Long Covid:
https://www.sciencedirect.com/science/article/abs/pii/S014067362401136X
The principle author of the Lancet article is Oxford health professor Trish Greenhalgh, who gave an excellent lay summary in her newsletter:
https://independentsage.substack.com/p/long-covid-a-dystopian-game-of-pinball
In particular, Greenhalgh describes why some people don't get Long Covid, and some people do – and, most important, explains why the fact that you didn't get Long Covid last time doesn't mean you won't get it next time:
https://independentsage.substack.com/p/long-covid-a-dystopian-game-of-pinball
So I don't want to get covid, and so I'm gonna wear a mask. Because masks fucking work. A new study reveals just how well they work:
https://www.thelancet.com/journals/ebiom/article/PIIS2352-3964(24)00192-0/fulltext
The study shows that wearing any mask, even without knowing how to fit it well, offers substantial protection against both contracting and transmitting covid. Even better: wearing an N95 (even without paying attention to correct fit) offers "near perfect" protection against covid:
https://today.umd.edu/n95-masks-nearly-perfect-at-blocking-covid-umd-study-shows
I didn't get covid at Defcon last year, and I didn't get it at HOPE, and I didn't get it on our family vacation in July – all events where friends got sick. The difference? I wore a mask. Which works.
OK, I need to go work on my Defcon speech some more, so I'm gonna sign off, but I will leave you with just one more link, the wonderful new public domain image search tool, Public Work, which crawls and indexes the Met, the NYPL, and other sources:
https://public.work/
I rely on public domain, CC and other freely usable clip art to make the collages that accompany this newsletter/blog's stories. While I have very little talent in the visual arts, I'm getting steadily better. I mean, look at this amazing image I womped up for last week's story on Bitcoin bros' election campaign finance fraud:
https://www.flickr.com/photos/doctorow/53893519593/in/album-72177720316719208
You can see a collection of my recent collages in my Flickr gallery for them:
https://www.flickr.com/photos/doctorow/albums/72177720316719208?sd

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/08/03/smorgasbord/#creepy-cute

Image: Anne Lindblom (cropped) https://www.flickr.com/photos/kajsawarg/3600415175
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#linkdump#linkdumps#gift guide#books#stickers#halloween#spooky#creepy cute#Gaynor Carradice#public domain#clip art#collages#antitrust#monopoly#crowdstrike#reslience#ttprgs#rpgs#games#gaming#d and d#open content#covid#pandemics#masks#mask up#public health
67 notes
·
View notes
Text
Berakhot 8b: 11. "The Diesel."

Mashiach according to the Mishnah is like a Defcon, "a defense condition" everyone knows what it means and responds to changes in the Condition all at once. One patch of land cannot be selective as to who gets human rights and who does or Mashiach has not been set.
The mindset, something we call Moses, is the key. Moses means "water of es" or "the knowledge of the special counsel", that which waters the Tree of the Knowledge of Good and Evil.
Prayer will not water the tree or set anyone free, only Moses can free a person from being trapped in an animal's body, a slave to a frame meant for amazing things should "water pressure" make him sentient.
We call a person who ditches the prayer session and walks away even from an audience with the Holiest of Holies a calculator. The Hebrew word for calculator is yehoshabanlev, which is #478 or diesel, which means "knows where the well is, and hangs the bucket."
"Note that the central meaning of these words is "hanging", but most commonly a hanging between a reservoir of plenty and a place of need, whilst transporting some of the plenty to the place of need.
The verb דלל (dalal) means to be low or hang low. In a literal sense it's used to describe someone hanging down a mine shaft (Job 28:4). The prophet Isaiah uses this verb to describe the lowness (dryness) of streams (Isaiah 19:6, and note that a wholly dry river was known as a lying river; see the verb כזב, kazab). Metaphorically, this verb is used to describe a state of depression or humiliation (Judges 6:6).
This verb's derivatives are:
The adjective דל (dal), meaning low, weak, poor or thin (Genesis 41:19, Leviticus 14:21, Job 34:28). Note that this word is identical to the noun meaning door, derived from the next verb.
The feminine noun דלה (dalla), denoting a bundle of hair (Song of Solomon 7:5) or threads of warp hanging in loom (Isaiah 38:12).
The identical feminine noun דלה (dalla), denoting the poor; literally the "hangers" (Jeremiah 40:7, 2 Kings 24:14). Note that this particular word suggests that the poor have a very distinct function, comparable to a bucket that brings water from one place to the dryness in another; see the Lucan story of Lazarus (LUKE 16:24, and also see MATTHEW 26:11). Also note that this noun is spelled and pronounced exactly the same as the previous noun, and both are spelled the same as the following verb.
The verb דלה (dala) is thought to mean to draw (of water out of a well with a bucket) and that for one tremendously daft reason: We moderns call getting water out of a well 'to draw' and that's why everybody else should too. And three of five derivatives of this verb have to do with doors, and doors we draw (shut). So that neatly fits the theory.
Here at Abarim Publications we obviously don't agree with the above, and we are fairly sure that our verb means to hang. In other words: in the vernacular of the ancient Hebrews, one does not draw water from a well; one hangs water from a well (namely in a bucket or leather sack, which in turn hangs from a rope).
Doors were named when people still lived in tents and received their name from being a veiled entrance and not from having a leaf, hinges, a knob and a door bell. The entrance of the tent was generally covered by a hanging length of fabric, which an aspiring visitor would have to lift and swoop aside, and when people began to live in brick houses, their entrances kept being referred to as "hangers".
Our verb is used four times: once in the literal sense of drawing water out of a well (Exodus 2:16-19), once to describe the extraction of a plan out of the watery heart of a man (Proverbs 20:5), and once to describe the extraction of a person out of Sheol (Psalm 30:2). In Proverbs 26:7, however (and BDB Theological Dictionary admits this context is "difficult"), a lame man's legs are performing the action of our verb (דליו), which can hardly be drawing and is certainly hanging.
The derivatives of this verb are:
The masculine noun דל (dal), meaning door, or rather entrance; the "door" of my lips (Psalm 141:3 only). It seems plausible that a hanging entrance veil and later the solid door were known as weak and thin (see above), as the hanging veil did not add to the structural strength of the tent and the door was obviously a lot thinner than the wall it was put in. The link between the door and the bucket sits in the function of both as instruments of transition from general (the water below the earth, or the world at large) to specific (a drinking person, or a person's house).
The feminine noun דלה (dala), also meaning door (Isaiah 26:20 only).
The masculine noun דלי (deli), meaning bucket or literally a "hanger" (Numbers 24:7 and Isaiah 40:15 only).
The feminine noun דלית or rather its plural form דליות (daliyot), denoting floral hangers: olive branches (Jeremiah 11:16), cedar branches (Ezekiel 31:7-12), or boughs of the vine (Ezekiel 17:6-7, 19:11).
The feminine noun דלת (delet), meaning door as the instrument that separates the inside from the outside (to be distinguished from שׁער, sha'ar, which describes the whole formal apparatus of a city gate, or פתח, petah, which accentuates the openness of a doorway).
Our word דלת (delet) may denote the door of a house (Genesis 19:9, Joshua 2:19, Job 31:32), or a room (Judges 3:23, 2 Samuel 13:17), or a city (Deuteronomy 3:5, Joshua 6:26, Nehemiah 3:1).
Figuratively, our word may denote the "door" (or lid) of a chest (2 Kings 12:10), the aperture of one's womb (Job 3:10), or one's lips (Ecclesiastes 12:4), or one's excessive accessibility (as opposed to being a self-respecting wall; Song of Solomon 8:9, also see Ezekiel 26:2: Jerusalem is a "broken door" to the people, for Tyre to plunder; or Zechariah 11:1, "open your door, O Lebanon, that a fire may feed on your cedars"), the jaws of Leviathan (Job 41:6), the "doors" of heaven from whence came Manna (Psalm 78:23), the "doors" of the sea (Job 38:8, 38:10; here at Abarim Publications we guess that the "doors" of the sea is the sea shore; see our article on the word ספה, sapa meaning both sea-shore and lips, and סוף, suph, meaning reeds, which grow on the edge between sea and dry land).
Most spectacularly is the usage of our noun in the sense of the textual columns ("doors") of a scrolled manuscript (Jeremiah 36:23), and keep in mind the transitory essence of our noun, much rather than a superficial resemblance between a door and a text column.
The fourth letter of the Hebrew alphabet is called דלת, or daleth, commonly interpreted as "door".
11.And do not pass through the back of the Synagogue at the hour when the congregation is praying - assisted by Rabbi Yehoshua ben Levi. Rabbi Yehoshua ben Levi said: It is forbidden for a person to pass through the back of the synagogue at an hour when the congregation is praying.
=
And do not pass through the back of the Synagogue at the hour when the congregation is praying - assisted by the calculator in him. The calculator in him said: It is forbidden for a person to pass through the back of the synagogue at an hour when the congregation is praying.
The most effective way to create the mindset and set the Conditions is to ensure basic services are provided to every community on the planet and the benefits are provided free as a right of citizenship. So while we like to pray for the relief of poverty and tyranny, the Gemara says this is not enough. If one knows what the Mishnah says then one needs to carry the water to others and then the community needs to make its move.
The Number is 10217, יבאז, yabaz, "this person will cause trouble."
Although each section of the Mishnah is not subtitled we are working on creating a Gemara of an area called the Divan, or the Dissertation. This frame has me wondering if it isn't fostering the creation of a makeshift Bill of Rights. Certainly persons who advocate for these are not at all welcome by the communities they are trying to help, nor appreciated after their work is done.
0 notes
Note
Hi witches! Just wondering, would you have a list of fics featuring BDE/take-charge patrick? This specific genre of patrick got me on a chokehold and i just can't get enough of it! Thanks in advance!
We respect your desires for more BDE Patrick, so here, have some:
Beware the Ides of March - @asoftplacetoland26
Defcon… Which Is The Worst One Again? - iola17 (@beaiola)
Home, sweet home - Poutini (@cheesecurdsgravyandfries)
No More Waiting - @reginahalliwell
Piledrive my Heart - @lisamc-21
Quiet - @steviestoospooky
solo artist - simplytheworst
Wildly Unprofessional - EggplantSalad you know the way to feel (to keep me satisfied) - railmedaddy (@rmd-writes)
21 notes
·
View notes
Photo


Jordana LeSesne, formerly known as 1.8.7, is an American musician and producer from Pittsburgh, Pennsylvania.[1] She now produces and performs as Jordana. She became known in the mid-1990s as a drum and bass producer.[2] Vibe magazine called her "one of the most respected Drum ‘n' Bass producers in the US."[3] In 2015, she was named as one of "20 women who shaped the history of dance music" by Mixmag.[4] She is transgender and came out in 1998.[5][2]
She has released over 50 tracks, including four albums, several EPs, and remixes under the alias 1.8.7. The 1997 album When Worlds Collide became known for its "dark pummeling assaults". She has licensed tracks for compilations as well as the Sci Fi Channel. Three of her albums charted in the Top 25 of both the CMJ (College Music Journal) and Mixmag U.S. (later Mixer Magazine, now defunct) for 1997 as well as 1998[6] and 1999. Her third album "The Cities Collection" debuted in the CMJ Top 5 climbed to the #2 position on CMJ Music Monthly's dance chart for June 2000.[7][8][9]
Her works have been reviewed by Billboard,[10] Spin, Rolling Stone, Urb, Mixer, Mixmag, Raygun,[3] as well as Knowledge – the U.K. Drum and Bass magazine. In 1999, she was listed in Raygun's Who's Who of International DJs. She was one of the headlining DJs on Knowledge Magazine's 28 city Kung Fu Knowledge tour in 1999.[11] She also made Out Magazine's OUT100 list for the year 2000.[12]
Contents
1Impact on music
2History
3Hate crime in Ohio
4Additional work in music industry
5Literary mentions
6Personal life
7Vinyl
8CD releases
9Videos
10References
11External links
Impact on music[edit]
Her work has influenced other artists such as well-known dubstep producer Bassnectar, who heavily sampled 5 A.M. Rinse (feat. MC Sphinx), the last song on her first album When Worlds Collide for his song Here We Go of his 2010 EP and single Timestretch.[13] Since the sexual allegations of Bassnectar have become known to her, Jordana has publicly condemned his actions as well as called out the fact that he never delivered contractually promised royalties for the above mentioned work.[14] Additionally, electronic rock act Celldweller sampled "Wake Up" off of her first album as well as "San Francisco" off of her third album "The Cities Collection" in their 2013 song "Uncrowned".[15]
In 1999, Drum & Bass/Hip Hop producer and label owner Hive approached Jordana to remix her song Defcon-1 also off of When Worlds Collide. Hive's remix appears on his 2001 album The Raw Uncut.[16] Jordana collaborated with Lady Sovereign on a song early in Sov's career after the two met through an internet chat room for StrikeFM.co.uk, an online radio station which Jordana had a show, and the now defunct UKGarageWorldwide.com forums. The two would later team up when Jordana under her Lady J alias, had Lady Sovereign MC for her radio show on Flex FM London.[17]
History[edit]
She first came to the attention of the music industry when she was asked to remix Blondie's "Atomic." Her remix appeared along with Armand Van Helden and Diddy’s remixes on the single.[3] A little over a year following that release, Mac McFarlane, the promoter of the well established and legendary New York City club, Konkrete Jungle, contacted her to create a themed song for a CD compilation/mix-CD. Jordana created the song "Konkrete Jungle" for that purpose. Described by CMJ as containing "menacing hardstep attacks",[18] it was released on the Ultra Records compilation, Konkrete Jungle - Maximum Drum & Bass, mixed by BBC Radio 1 Drum'n'Bass show host Jumpin Jack Frost. Following extensive touring throughout North America and abroad as a music producer, Liquid Sky Music, an indie label distributed by Caroline Distribution signed her to a three-album contract in late 1996.
Hate crime in Ohio[edit]
On the night of February 22, 2000 in Kent, Ohio, Jordana was attacked and brutally beaten in a transphobic hate crime by a group of men including Matthew Gostlin.[19] Gostlin and other assailants vaulted her in the parking lot outside of the Robin Hood nightclub where she had just performed on the Cities Collection tour. The attack took place while she was escorted from the event with the event promoter to his car. The group of men attacked suddenly and Jordana lost consciousness almost immediately after being struck in the face. She suffered nerve damage to the lower part of her face from her lower lip down as a result. She was quoted, saying in the May 2000 issue of CMJ New Music Monthly that in the seconds just prior to the attack: "I saw his face. I remember the look on his face. It was this look of utter hate, like 'I'm going to kill you.'"[20] In an interview with the Village Voice, George Meesig, a man from Cleveland, Ohio who defended her during the attack, stated that Gostlin had misgendered her, saying “this is personal”.[21] Other reports noted by the Village Voice on the message board for Breakbeat Science (a Drum'n'Bass record store) mentioned transphobic slurs being shouted during the attack. She subsequently cancelled the tour to recover.[19] Gostlin, while charged, was never arrested nor spent any time in court. Her family was told by the Portage County (Ohio) prosecutor's office that attempts had been made to serve the warrant but Gostlin's whereabouts were unknown. She felt that justice would not be served so she left the United States for England due to concerns about personal safety and well-being.
Additional work in music industry[edit]
In addition to music production, Jordana is a DJ, musician and singer. From 2001 to 2002, she worked at Flex FM in London, England as Lady J, with Lady Sovereign performing for her during her radio show.[22] In 2002, she held a club residency performing UK garage, 2-step garage and house music at the club Trinity in Vauxhall neighborhood.
After returning to the United States, Jordana returned to rock and fronted a goth metal band in Seattle. Prior to that, she was asked to play bass in another band briefly where she met and became close friends with singer/songwriter Shelita Burke. She has toured the world and played many DJ sets. She has been billed alongside Arca for Planet Zolean: Un/Tuck + Hot Mass on the Currents.FM Common Multiverse Initiative.[23] She was featured on the Dekmantel Podcast.[24] She was featured as Mix of the Day for Resident Advisor.[25]
In 2014, Jordana scored the documentary Free CeCe, produced and directed by Jacqueline Gares and Laverne Cox. The documentary details the struggles of CeCe McDonald, an African-American transwoman wrongfully incarcerated for murder for defending herself against a hate attack on her outside a Minneapolis bar.[26][27]
Literary mentions[edit]
She has been featured in several books. Her success in rising from living in a "rust belt" city to being an MTV-featured electronic music artist was mentioned in "The Rise of the Creative Class" by economist Richard Florida. She appears in two books detailing American electronic dance music scene history: Michaelangelo Matos's The Underground is Massive,[28] and Rave Culture, an Insider's Overview by Jimi Fritz and Virginia Smallfry.[29]
An interview with Jordana was featured in multiple books, including a book published in 2012 by rock journalist George Petros.[30] She has spoken on her personal life in interviews for publications such as The Festival Voice,[31] The Brooklyn Rail[32] and href zine.[33]
Personal life[edit]
She currently lives in Seattle, Washington.
Vinyl[edit]
1995 Blondie "Atomic (The Beautiful Drum and Bass Mix)" VV58320 Chrysalis Records/EMI
1996 RockStone Foundation "Dis Soun'" JS007 Jungle Sky
1997 V/A – Nirvana EP "We Are Not Alone" JS114 Jungle Sky
1997 Soul Slinger-Don't Believe "Abducted (1.8.7 Remix) JS118 Jungle Sky
1997 Soul Slinger-Don't Believe "Ethiopia/JungleSky (1.8.7 Megamix)" JS118 Jungle Sky
1997 1.8.7 – When Worlds Collide full-length album EP1 "Defcon 1"/"When Worlds Collide"/"Blueshift"/"Dragonfly" JSK121 Jungle Sky
1997 1.8.7 – When Worlds Collide full-length album EP2 "Wake Up"/"Distant Storm Approaching"/"Ghetto Style"/"Ghetto Style (West Philly Mix)" JSK122 Jungle Sky
1998 Murder 0ne (1.8.7)/T.Farmer "Annihilate"/"Memory" BOOST002 Boosted Records
1998 This is Jungle Sky Vol. 5: Rock N Roll EP Disc 2 "Break In"/"The Return of Shaft"/"Konkrete Jungle" Jungle Sky JSK131
1998 This is Jungle Sky Vol. 5: Rock N Roll EP Disc 3 "Atmosphere Remix"/"The Jam"/Beastie Boys – "Sabotage (1.8.7 JS Remix)" JSK132 Jungle Sky
1998 1.8.7 – Quality Rolls full-length album EP1 "Quality Rolls"/"Relax Your Mind"/"Phobic" JSK136 Jungle Sky
1998 1.8.7 – Quality Rolls full-length album EP2 *"Jerusalem"/"Get Amped" (215 Remix)/"Stigma" JSK 137 Jungle Sky
1998 1.8.7 – Quality Rolls full-length album EP3 "Rock The Party"/"Deep Stealth"/"Cross the Line" JSK138 Jungle Sky
1998 1.8.7 – Quality Rolls full-length album EP3 "United"/"Blue Nile"/"Reboot" JSK139 Jungle Sky
1999 Jordana – "Pure Funk"/Stardust – "Music Sounds Better".. [With Bass] (Jordana JS remix) *whitelabel* JSK149 Jungle Sky
1999 Jordana – Cities Collection 12" 1 "Hollywood (courtesy of Lucasfilm)"/"Los Angeles"/"New York" JSK157 Jungle Sky
1999 Jordana – Cities Collection 12" 2 "Pittsburgh"/"Miami"/"San Francisco" JSK158 Jungle Sky
2000 Loki and Jordana – "Murder" 12" *whitelabel*
2001 Jordana – "Tampa Tantrum"/"In Your Arms" 12" TECO008 Technorganic
2002 Lady J feat. Lady Sovereign – "The Intro Dub" (Flex FM)
2002 Jordana – Full Colour 12" 1 *whitelabel* ConceptAudio
2002 Jordana – Full Colour 12" 2 *whitelabel* ConceptAudio
CD releases[edit]
1994 V/A – Interstellar Outback "Jungleman" ROM01 RomHyperMedia
1995 V/A – Scotto Presents: Drop Beats Vol.1 "Ravestock Anthem" DROP001 Drop Entertainment
1996 V/A – This Is Jungle Sky Vol.2 "Dis Soun" JSK008 Jungle Sky
1997 V/A – This is Jungle Sky Vol.4 "We Are Not Alone" JSK116 Jungle Sky
1997 V/A – Future Groove "We Are Not Alone" ?74321 50089 2 Ariola/BMG
1997 V/A – New York Junglist "We Are Not Alone" AVCD11540 Avex Trax
1997 Soul Slinger-Don't Believe CD "Abducted (187 Remix)" JSK120 Jungle Sky
1997 Soul Slinger-Don't Believe CD "Ethiopia/JungleSky" JSK120 Jungle Sky
1997 1.8.7 – When Worlds Collide CD album JSK124 Jungle Sky
1998 V/A – This is Jungle Sky Vol.5 "The Jam" JSK130 Jungle Sky
1998 V/A – This is Jungle Sky Vol.5 "Atmosphere Remix" JSK130 Jungle Sky
1998 Soul Slinger – Upload: A Continuous Mix CD "Rock the Party" JSK142 Jungle Sky
1998 V/A – Nu Balance: Domesticated Drum & Bass CD "5am Rinse" COA70016-2 City Of Angels
1998 1.8.7 – Quality Rolls CD album JSK135 Jungle Sky
1999 V/A – Sci Fidelity: This is Sci Fi. CD "Deep Stealth" SciFi Channel/Jungle Sky
1999 V/A – This is Jungle Sky Vol.6 CD "Pure Funk" JSK150 Jungle Sky
1999 V/A – This is Jungle Sky Vol.6 CD "Unite Remix" JSK150 Jungle Sky
1999 Jordana presents 1.8.7 – The Cities Collection CD album JSK162 Jungle Sky
1999 V/A – E-Sassin Absolute Friction CD "Worlds Apart" 21C.3007 Quantum Loop
2000 V/A – Digital Empire: DJ Girl "Deep Stealth" 6454-2 Cold Front Records
2001 Hive – The Raw Uncut EP CD "Defcon-1" (Hive Remix) VTXCD-002 Vortex Recordings
2002 Jordana – Full Colour album ConceptAudio Limited Release
2003 V/A – Girls In Space CD "In Your Arms" CD-9213 Urabon Records
2005 Jordana – Jordana EP CD "In Your Arms" TECO CD001 Technorganic Recordings
2005 Jordana – Jordana EP CD "Tampa Tantrum" TECO CD001 Technorganic Recordings
2005 V/A – DJ Psycle-Back From The Future CD "In Your Arms" TECO CD-9213 Technorganic Recordings
2005 V/A – DJ Psycle-Back From The Future CD "In Your Arms" TECO CD-9213 Technorganic Recordings
2008 V/A – What the Bleep & Foi Oi Oi-Feelings For Detroit Vol.3 Yabette – "Babylon (1.8.7 Remix)" EEMIX003 Electronic Enlightenment
Videos[edit]
We Are Not Alone (1998) – directed by MSKW1 aka Michael Whartnaby
Defcon 1 (1998) – directed by MSKW1 aka Michael Whartnaby and DBIDWA aka Dan Bidwa
Worlds Apart (1998) – directed by Gerard Ryan
Atmosphere (1998) – directed by Gerard Ryan
Ring Me Back (2002) – directed by Trevor McKinley
References[edit]
^ "VH1 Biography". Vh1.com. Archived from the original on February 14, 2011. Retrieved September 8, 2010.
^ Jump up to:a b Riedel, Samantha. "This Trans Drum & Bass Musician Was a Pioneer in the 90s. Why Isn't She Getting Her Due?". them. Retrieved September 30, 2020.
^ Jump up to:a b c Vibe Media Group (February 1999). "Vibe". Vibe Vixen. Vibe Media Group: 38–. ISSN 1070-4701.
^ "- - Mixmag". Mixmag.net. Retrieved December 21, 2015.
^ "Roll With the Changes". citypaper.net. Archived from the original on July 7, 2012. Retrieved January 19, 2016.
^ CMJ Network, Inc. (December 1998). "CMJ New Music Monthly". CMJ New Music. CMJ Network, Inc.: 78–. ISSN 1074-6978.
^ CMJ Network, Inc. (March 2000). "CMJ New Music Monthly". CMJ New Music. CMJ Network, Inc.: 48–. ISSN 1074-6978.
^ CMJ Network, Inc. (March 13, 2000). CMJ New Music Report. CMJ Network, Inc. pp. 27–. ISSN 0890-0795.
^ CMJ Network, Inc. (June 2000). "CMJ New Music Monthly". CMJ New Music. CMJ Network, Inc.: 82–. ISSN 1074-6978.
^ CMJ Network, Inc. (June 2000). "CMJ New Music Monthly". CMJ New Music. CMJ Network, Inc.: 95. ISSN 1074-6978.
^ "Kung Fu Knowledge Tour Cities". Bmotion. Archived from the original on October 4, 2013. Retrieved October 3, 2013.
^ Out Magazine (74): 45. January 2000.
^ iphoneunclockseattle. "Bassnectar's Here We Go sample of 1.8.7 feat. MC Sphinx's 5 A.M. Rinse". WhoSampled. Retrieved November 2, 2013.
^ Avery C Kleinman for Vice News. "The Fall of the Bassnectar Empire".
^ jordana. "Celldweller samples Wake Up and San Francisco". WhoSampled. Retrieved May 9, 2014.
^ "Hive – The Raw Uncut EP". Discogs. Retrieved November 2, 2013.
^ "Hot update | Welcome to the FLEX FM NETWORK". FLEX FM Network. May 19, 2002. Archived from the original on June 1, 2002. Retrieved December 21, 2015.
^ CMJ Network, Inc. (October 1998). "CMJ New Music Monthly". CMJ New Music. CMJ Network, Inc.: 62–. ISSN 1074-6978.
^ Jump up to:a b Maximum Rocknroll. Maximum Rock 'n' Roll. 2000.
^ CMJ Network, Inc. (May 2000). "CMJ New Music Monthly". CMJ New Music. CMJ Network, Inc.: 13. ISSN 1074-6978.
^ Bill Werde (February 29, 2000). "Top Jungle Producer Attacked". Villagevoice.com. Archived from the original on January 9, 2019. Retrieved January 8, 2019.
^ Sovereign, Lady (May 18, 2002). "Lock in to FLex FM 2nite". ukmusic.com/. Archived from the original on August 10, 2014. Retrieved May 30, 2013.
^ "Currents.FM Common Stream Multiverse Initiative".
^ "Jordana is one of America's most widely respected drum & bass artists". Dekmantel.
^ "Drum & bass made for the biggest rooms, with plenty of soul, nuance and killer vocal hooks". Resident Advisor.
^ "FREE CeCe! Post-Production Campaign". Retrieved December 21, 2015.
^ "AFROPUNK". Afropunk.com. Archived from the original on December 22, 2015. Retrieved December 21, 2015.
^ Matos, Michaelangelo (April 28, 2015). The Underground Is Massive: How Electronic Dance Music Conquered America. Dey Street Books. p. 154. ISBN 978-0062271785.
^ Jimi Fritz (1999). Rave Culture: An Insider's Overview. SmallFry Press. p. 162. ISBN 978-0-9685721-0-8.
^ Petros, George (2012). Lehman, Deanna (ed.). The New Transsexuals: The Next Step In Human Evolution. Creation Books. pp. 247–274. ISBN 978-0-9855018-1-5. Retrieved December 22, 2015.
^ https://thefestivalvoice.com/black-lives-matter-tfvs-series-on-racial-injustice-jordana/
^ https://brooklynrail.org/2021/05/criticspage/Let-Us-Live/
^ https://href-zine.net/technoid-natures-zine.html
External links[edit]
Jordana discography at Discogs
1.8.7 at Rolldabeats
https://jordanaofficial.bandcamp.com/
https://www.mixcloud.com/jordana/
https://soundcloud.com/jordanaofficial
Jordana at IMDb
#trans history#transgender woman#transgender#trans pride#black transgender woman#postop transwomen#transisbeautiful#trans is not a choice#trans musician#transwomenmatter#transwoman
35 notes
·
View notes
Link
>Slashdot reader ytene writes: As reported by The Intercept, U.S. Customs and Border Protection have just spent $456,063 for a package of technology specifically designed to access smartphone data via a motor vehicle. From the article: "...part of the draw of vacuuming data out of cars is that so many drivers are oblivious to the fact that their cars are generating so much data in the first place, often including extremely sensitive information inadvertently synced from smartphones." This data can include "Recent destinations, favorite locations, call logs, contact lists, SMS messages, emails, pictures, videos, social media feeds, and the navigation history of everywhere the vehicle has been, when and where a vehicle's lights are turned on, and which doors are opened and closed at specific locations" as well as "gear shifts, odometer reads, ignition cycles, speed logs, and more. This car-based surveillance, in other words, goes many miles beyond the car itself." Perhaps the most remarkable claim, however, was, "We had a Ford Explorer we pulled the system out, and we recovered 70 phones that had been connected to it. All of their call logs, their contacts and their SMS." Mohammad Tajsar, an attorney with the American Civil Liberties Union (ACLU), is quoted as saying, "Whenever we have surveillance technology that's deeply invasive, we are disturbed," he said. "When it's in the hands of an agency that's consistently refused any kind of attempt at basic accountability, reform, or oversight, then it's Defcon 1."


Read more of this story at Slashdot.
via: https://ift.tt/2QWqreH
28 notes
·
View notes
Text
September 2, 2021 - The Wisdom of my Wife
Today is the day when an imaginary version of my wife sat on my shoulder and repeated whispered sage advice in my ear. While I might once have considered it subconscious nagging, I have to ask: Is it really nagging when she is almost always right and it usually prevents me from making huge mistakes?
If you have been following the blog, you are aware the Deutsche Bahn (the national railway) went on strike at midnight and will not return to work until next Wednesday. While I had done my best to make alternate arrangements, this is the kind of thing that usually raises my stress level to Defcon 4, with collateral damage to all around me. However, when I got up this morning I just kept hearing Lu-Anne’s voice in my head, “slow down for a minute and take a deep breath, it will all work out somehow.” She was right as usual. I managed to make it to Frankfurt where I exchanged my second DB ticket for one on a private railway that was not on strike. While it would not take me to Bingen, it would let me gaze longingly across the Rhine from the Rudesheim Bahnhof and I understood there was likely a ferry somewhere nearby. On arrival, my GPS informed me that the “personenfahre” was right below the station at riverside (20m). After waiting half an hour for a ferry that likely never came, I realized that the “autofahre” was crossing every 10 minutes only 200m further down the riverbank. After dragging my suitcase a little over 2km on both sides of the river, I walked into Cafe Hotel Koppel with a smile on my face. To make a long story short, throughout this I remained uncharacteristically calm and relaxed thanks to my wife’s ethereal advice.

After checking in and getting organized I went back along the River for lunch at about 15:00. I stopped at a ridiculously expensive restaurant with loads of character on the riverbank. I decided to treat myself and once again my wife’s wisdom echoed in my one good ear. “Too many $10,000 vacations have been ruined by spending all your time trying to save $20.” (Or words to that effect). While I recognize that, even on a public service pension, one needs to be careful and not waste money, my wife has taught me that $20 here and there can literally shove thousands of dollars of enjoyment down the toilet.

I perused the menu and spotted something called a flame cake. I saw one go by and it seemed to be a pizza. When my waiter came I asked him what it was. He said it was hard to describe, but it was kinda like a pide (Turkish pizza) but with no cheese of tomato sauce. I asked “is it good”. His response was “some people like it” all the while shaking his head from side to side. I asked if he liked it and his response was “I always have something else”. My wife’s advice again kicked in “always ask your waiter and always listen to (his/her/their) advice”. Cheeseburger and fries were ordered ($21) and he broke into a huge smile, “you will like that a lot”. I did, and, after all, Hamburg is in Germany so this is still local food😊.
One caution though, I have had three hamburgers in Germany and all three have been about a 1/2 a pound on a 5” bun. Germans seem to love their meat. My schnitzel last night (with large salad) was roughly the size of a frisbee, but nonetheless I somehow managed to choke it down. At lunch yesterday on the market square in Wurzburg, I joined a line to a kiosk that stretched about 150 m around the square uncertain of what they were selling, only convinced that it was likely very good. When I eventually got to the front, it was only for a “simple” bratwurst on a bun with mustard. Nonetheless, when I finished that one, I would have two more (as many did) if I had had time to brave the lineup again.
Oh yes, I should also probably mention the wine. In Canada a standard glass is 5 ounces or about 150 ml. Here, a standard glass is 200 ml and almost everyone that I have had has been closer to 250ml (glasses are marked) or about a third of a bottle. Depending on the situation I have switched between everyday Silvaner ($5.50 a glass) and some lovely Rieslings (up to $8 a glass). Basically 2/3 the price we are use to paying for a glass in Edmonton restaurants for 30-60% more wine. Little wonder I spent another two hours after my meal savouring a couple of glasses while I watched the barges and tour boats pass by while a huge statue of Germanic looked down from across the river.

Will take another walk down by the river, but will make it an early night as I walk to Kalb tomorrow 20+ km and 2,000+ ft gross vertical climb. The good news is the breakfast should be good as many Europeans serve sweet baked goods with breakfast, and my hotel is also a cafe/pastry shop👍🏻.



2 notes
·
View notes
Link
In a previous article I discussed the possibilities of increasing your safety online by using measures such as encryption, VPN and Tor. Nonetheless I did not cover all possibilities and most importantly it was a practical discussion rather than a theoretical one. This article will be a theoretical dissection of online anonymity tools and their weaknesses.
Why do people get caught despite using Tor? Can anyone be truly anonymous online ?
This article will be a summary of the work of Tom Ritter, presented at DEFCON 21, the annual hacker conference. His video presentation can be viewed here and the printed version of his article here.
While doing a great Job, Tom’s work is heavy on tech jargon and might confuse laymen. So I will summarize his work and explain the strengths and weaknesses of modern anonymity tools. His work was published in 2013, but remains relevant today as well.
In his work Tom talks about 4 anonymity technologies : SSL, Tor, Remailers and Shared Mailboxes. Let’s discuss them one by one.
SSL

SSL stands for Secure Socket Layer and is a common online security standard used by the likes of Facebook and other major websites. The way SSL works is that it creates an encrypted tunnel of communication between 2 parties so that third parties cannot read the messages they are sending to each other. Despite being secure on paper, it can be circumvented rather easily. To understand how, first we must talk about metadata.
Metadata
Metadata is data that describes other data. For example, library cards which hold the name of the book, its publishing date and its location in the library is a form of metadata. Metadata is also used in IT.
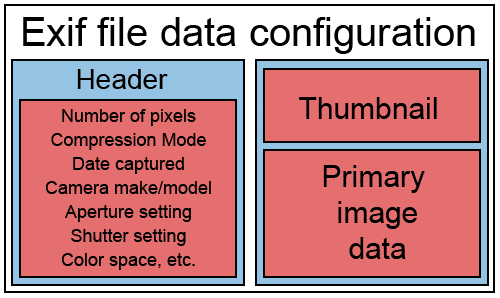
An example of metadata is the EXIF file in photos. When you take a photo with a camera you not only register the photo, but usually your device also adds extra info such as the date the photo was taken, the GPS location, phone brand, etc. and stores it in the photo file.
Other form of metadata is not registered but can be inferred. For example, someone created a program that can discover which parts of Google maps you are looking at based on the size of map tiles you are downloading.

When you are using SSL you are unwillingly lending third parties metadata which can lead to your discovery, particularly the time the message was sent and the size of your messages.
This allows for attackers to do something called a correlation attack.
Correlation attacks are primarily of 2 types : Time-based attacks and Size-based attacks
Time-based attack
In order to perform a time-based attack a party sends a message in an encrypted stream, then it looks at who receives the message. Since SSL communication is instantaneous, you can easily infer who is behind the SSL stream. The third party sends a message at 15:59 and whoever happens to get the message right afterwards must be the person they are looking for.
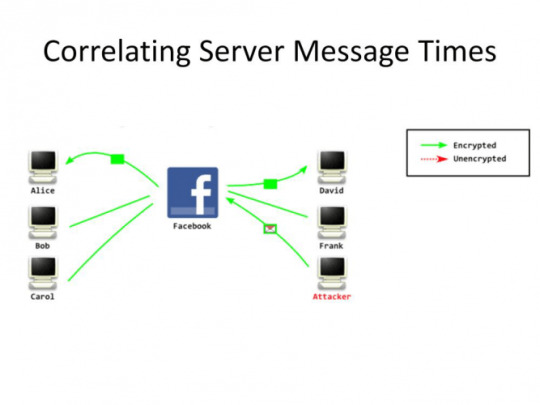
This type of attack was used against the person who dumped Stratfor mailpools. The way it worked is that government analyzed the time he was logging in on the internet and noticed it coincided with the time the person they suspected logged on to a secret chat through Tor. Not only that, rumor has it the government cut electricity to his house at a certain hour and noticed that the user of the secret chat logged out at the same time. The coincidences were too much, so he got caught.
Size-based attack
In order to perform a size-based attack, the third party sends a file of an unusual size, and then whoever receives the file must be the person they are looking for. Since most people on Facebook send small messages to each other, one only needs to send a very large message and see who happens to receive a message of that size afterwards.
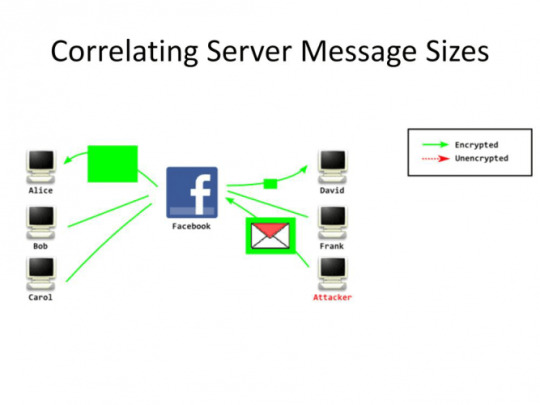
As you can see correlation attacks render you vulnerable if you use SSL as your only line of defense. The reason is because the Third Party can not see WHAT you are sending, but they know that you ARE sending something, WHEN you do it and HOW BIG is the file.
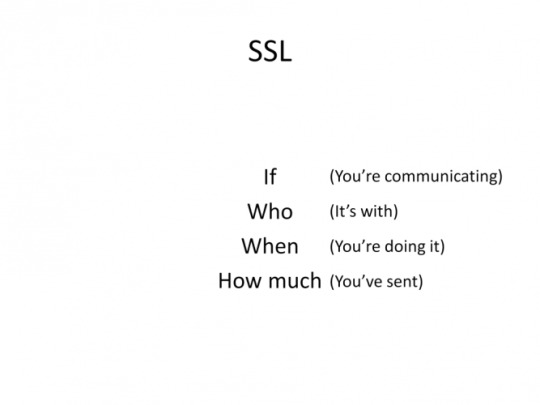
Ideally they should not even know you are communicating with anything at all. So, let’s see what other technologies have to offer.
Tor
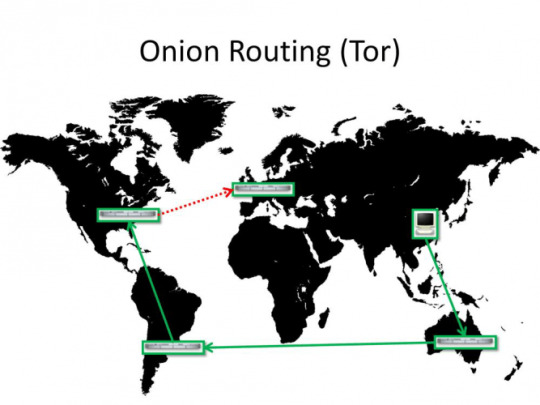
Tor is a custom browser based on Firefox with extensions that works on the principle of connecting to a few nodes so that when you look at a website the only thing the website can see is the last node you traveled through and on the opposite side your ISP (Internet Service Provider ) can only see your first node, not the whole route.
This is already getting better. However it does not add that much anonymity since now third parties do not know WHO is communicating, but they can still see that it DOES happen, WHEN it happens and HOW BIG the size of messages are.

Not only that, but there are known vulnerabilities, particularly of 3 types.
You are viewing a website in the country you are in.
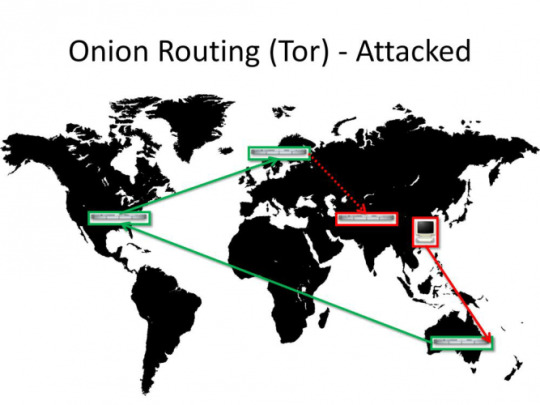
This allows advanced opponents calculate that it was YOU who was using Tor. It is difficult, but not impossible. This is bad news since a lot of people from US view websites stored in US. And so do dissidents from China or Iran.
Every single node you pass through is compromised
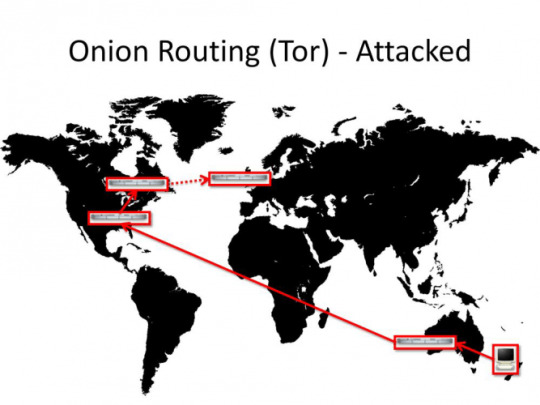
In my previous article I mentioned that the government can set up Tor nodes that they monitor. But to successfully pull an attack they would have to monitor EVERY node you go through.
This requires NWO level trickery, but again, we already have examples of this happening already with VPN agreements. Countries in the Anglosphere have an agreement to give away information regarding VPN usage by suspects from respective countries. This agreements is called Five Eyes. I wouldn’t be surprised if a similar thing is organized regarding Tor nodes.
Passive traffic analysis
Although not mentioned by Ritter in his presentation, it is common knowledge that an opponent with a lot of resources, mostly governments, could analyze the whole network and correlate patterns to discover who is viewing a certain website or communicating with someone.
To give an analogy, it would be like the police heavily patrolling every single street in a city and every single car , so that even if your car had fake plates they could notice patterns and discover its owner.
The problem is, this approach can create false positives, with a 10% chance of error, which is why these analyses are not accepted in court as proof. But you can rest sure if such an analysis points to you, you will be put under further investigation and it only gets worse from there.
So what can be used to further aid us ?
Remailers
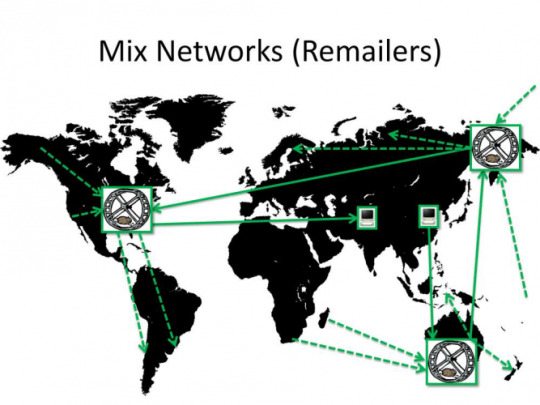
Remailers are an interesting concept. The way they work is that people pool their mail messages on a server, after which some time passes and all mails are sent simultaneously at the same time.
This is supposed to protect from Time and Size based correlation attacks.
The problem here is that it still allows third parties to see that you ARE sending a message, WHEN you sent it and HOW BIG it was. But they can’t see the other end. For the receiver, he has the same problem. Third parties can’t know WHO he got the message from, but they can still see WHEN he receives it from the remailer and HOW BIG it is.

On top of that, for Remailers to work lots of people have to use them at the same time. Otherwise if there are few users, an enemy can still use size-based correlation attacks.
It’s hard to use size-based attacks when thousands of people are sending messages of various sizes, but if only three people at one time are using a Remailer, then it is very easy to do a size-based attack.
Shared mailbox
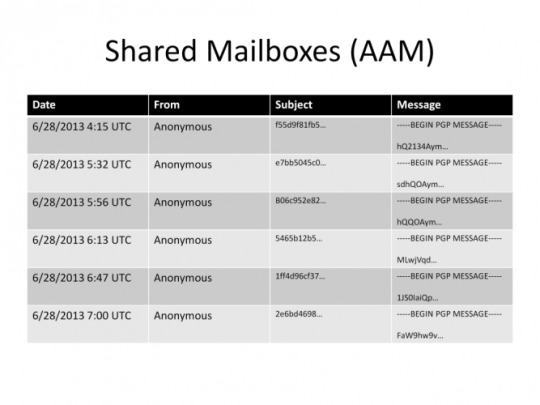
Shared mailboxes are the most out-of-the-box anonymous solution.
The way a shared mailbox works is that users share a mailbox. They cannot delete messages from it, but can only add encrypted messages to it. And when they want to check if they received a message they download all messages and use their key and try to decrypt the header of all of them and see if any of the messages belong to him.
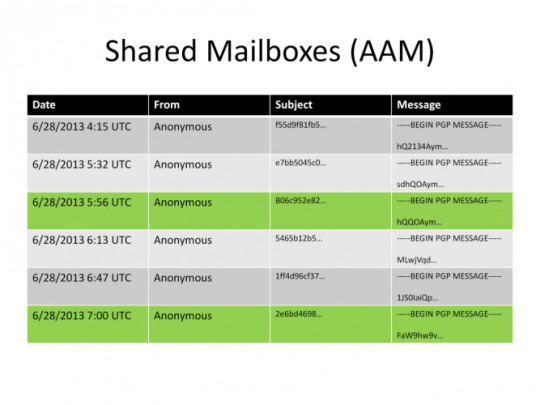
It is a resource-tedious process, but it offers a great payoff. For the receiver this is great because when he downloads the whole mailbox third parties can’t know if he received a message, maybe he did, or maybe he didn’t. For the sender however, the equation stays the same as before.

This is for the moment the most powerful anonymity solution out there. However it has a few issues. In order to use alt.anonymous.message (the shared inbox) you need to have some degree of technical skill, and user inexperience leads to issues.
In order to be easier to use alt.anonymous.message allows the use of nymservers. Nymservers act as regular mail addresses, which when sent to, automatically post them to alt.anonymous.message .
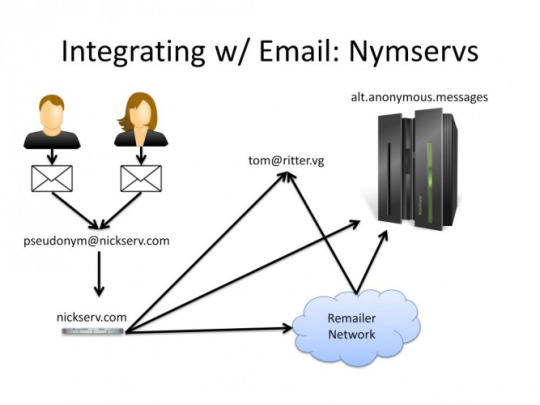
There are however issues with AAM and Nymservers.
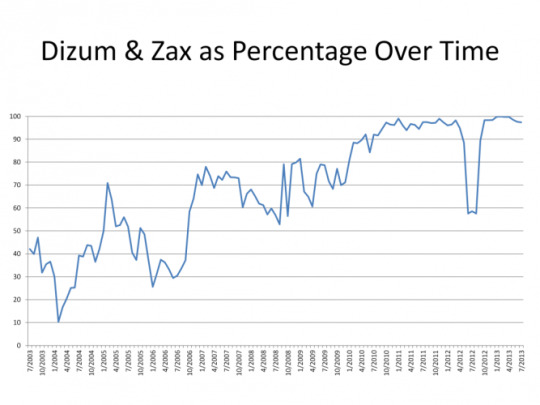
1. Poor network diversity
The number one issue is there are currently two main node operators: Zax and Dizzum, which are responsible for the trafficking of messages to alt.anonymous.message. If both were to retire or be arrested it would the death of alt.anonymous.message. As you can see, network diversity is horrible.
2. Poor encryption used on messages
Another issue is the type of encryption used. Some messages used the outdated MD5 encryption standard which is easy to crack.

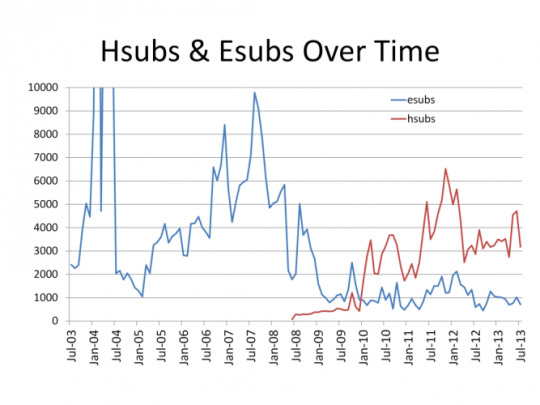
Also, the title of messages are encrypted less strongly in order to be able to determine quickly which belong to you and which don’t. Subjects can be encrypted using either hsubs or esubs. Esubs is an older and stronger standard, but hsubs have grown in popularity in recent years.

3. Pattern analysis due to use of same subject line and same remailers
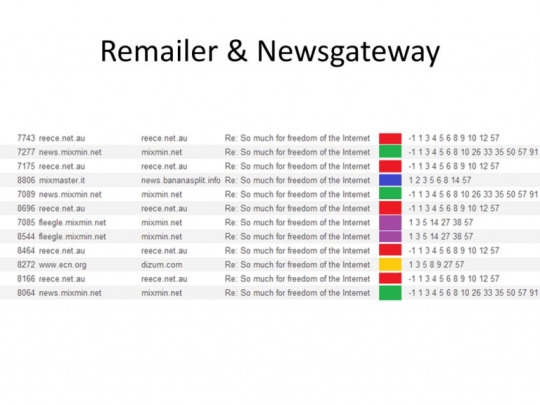
A lot of messages use the same subject over and over, people tend to reply to a particular subject. On top of that most people also usually use the same remailer over and over, you can start noticing communication patterns :
4. Custom Remailer command errors
There are different type of remailers. The old school one was called Type 1 and lives on in the protocol of Mixmaster. It allows a lot of customizing options for the header. The users often screwed up the name of the command, which ended in the title of a message.
For example if you write “X-No-Archive Hello Friend” it would turn into “Hello Friend” and the X-No-archive would be interpreted as a command to not archive. But if you wrote “no-archive-x Hello Friend” you messed up so the title would become “no-archive-x Hello Friend”. If you do this multiple times, you would be identified as a unique user since your titles would all contain “no-archive-x” or uncapitalized “x-no-archive” or whatever other combination of mispelled commands you use.
Since most people used the same commands over and over and did the same mistakes they became quickly identifiable as unique users.
5. Imperfect Remailers
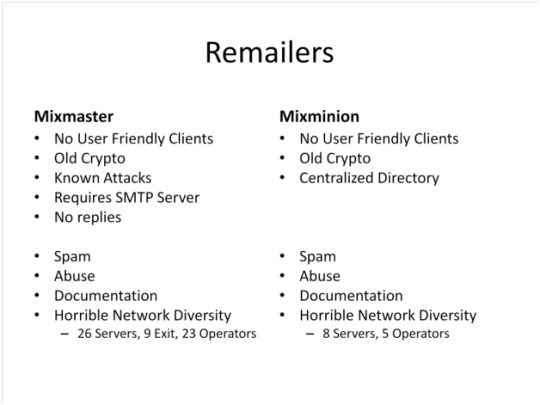
There are different types of remailers. Currently there are two types of remailers in use, MixMaster and MixMinion. MixMinion has certain advantages over MixMaster. But both suffer from certain problems.
6. Nymservers which do not protect from size-based correlation attacks
Nymservers themselves have problems. Zax’s Nymserver is instantaneous which allows for size-based correlation attacks. However even Type 1 Nymservers (older ones) which are not always instantaneous still allow for size-based correlation attacks given a bit of perspicacity.
Therefore we identified main issues with AAM (alt.anonymous.message):
1) Giving users options allows for segregation and profiling 2) Some encryption is weak 3) It can be complicated to use and allows for beginner mistakes 4) Weak network diversity
Nonetheless, Ritter identified the most secure way of using AAM :
1) Use a strong passphrase and hsub 2) Use Type 3 PGP packet (Key Stretching) 3) Use Remailers 4) Do not use extra headers or options
The issue here is that if you do it properly you will still be part of a small community of people doing so (around 500 – 1500 people), which will make you looks suspicious and will cause the government to look closer into you and maybe add you to a database.
Solutions of the future
Pynchon gate
Pynchon Gate is a project meant to replace shared mailboxes. It uses Private Information Retrieval. It exposes less meta-data, scales better and resists flooding and size-based attacks. However it is currently work in progress

Improved Remailers
MixMinion is currently the best remailer protocol and as such should be used as a basis for future improvement. Planned improvements include things such as improving TLS settings and moving to a new packet format.

What is currently lacking
As of right now, what is lacking is some tech that could be used to anonymously share large files. AAM and such are low bandwidth, which means it can only be used to share small files like text messages.
A new service needs to be created to cover this niche. In the words of Tom Ritter :
But what I keep coming back to is the fact that we have no anonymity network that is high bandwidth, high latency. We have no anonymity network that would have let someone securely share the Collateral Murder video, without Wikileaks being their proxy. You can’t take a video of corruption or police brutality, and post it anonymously.
Now I hear you arguing with me in your heads: Use Tor and upload it to Youtube. No, youtube will take it down. Use Tor and upload it to MEGA, or some site that will fight fradulent takedown notices. Okay, but now you’re relying on the good graces of some third party. A third party that is known to host the video, and can be sued. Wikileaks was the last organization that was willing to take on that legal fight, and now they are no longer in the business of hosting content for normal people.
And you can say Hidden Service and I’ll point to size-based traffic analysis and confirmation attacks that come with a low-latency network, never mind Ralf-Phillip Weinmen’s amazing work the other month that really killed Hidden Services. We can go on and on like this, but I hope you’ll at least concede the point that what you are coming up with are work-arounds for a problem that we lack a good solution to.
Conclusions
As we can see true anonymity online is non-existent. At the very least, third parties can collect meta-data on you and use correlation attacks, when ideally they shouldn’t even know you are communicating at all. Moreover, even strong anonymity tools like Tor have shown to have known vulnerabilities.
However, what matters is not whether something is vulnerable in theory, but rather does it keep you safe in practice? And so far, the tools we have at our disposal are pretty powerful.
As I have mentioned in my previous article, using TailsOS off a flash stick in a public wi-fi area with no cameras + VPN/Tor seems to be the best solution for now.
The testament to the power of anonymity tools is that pedophile rings and drug dealers have managed to escape persecution by multiple world governments to this day using them.
And that’s what I will talk about in my next article. We will analyze the electronic operational security of pedophile rings and how one infamous one managed to escape unscathed after years of being searched. Stay tuned.
Read More: 12 Ways To Increase Your Anonymity And Security Online
3 notes
·
View notes
Text
"Danvers," the voice on the other end answered.
"Were you freaking out this much when Astrid went to school?" Kara asked without preamble or greeting.
"That depends," her sister answered without pause. "Are you using super-hearing to listen in on El right now?"
Kara exhaled deeply. "Maybe."
"Then, yeah, probably the same," Alex admitted. "I was at DEFCON 2 for most of the first week."
"Week?!" Kara exclaimed. "It hasn't been a half hour!"
"You know your daughter is smart, charming, and extremely resilient," Alex said. "Thanks in large part to her amazing mothers, and equally talented aunt?"
#fanfic#ao3#supergirl#supercorp#lena luthor#fanfiction#kara danvers#kara x lena#lena x kara#kara zor el
1 note
·
View note
Text
21 questions
i was tagged by @parasitebestpicture ily and miss youuuu
nickname: Emcon
real name: Emily
zodiac: Leo Sun, Capricorn Moon, Virgo rising
height: 5’8″
what time is it? 10:12 pm
favorite band/group: sleeping at last, queen, bastille
favorite sports team: the new england patriots and boston red sox
other blogs: @emcon-imagines @emcon-ocs
do I get asks? sometimes? on my other ones i do!
lucky ☘️ number: 8
what am I wearing right now? periodic table joke shirt, flannel, yoga pants
how many blogs do I follow: 155
dream vacation: iceland or antarctica
dream car: a van like the ones the kids had in MA-- but less creepy looking
favorite food: spaghetti with a ton of cheese
drinks of choice: a glass of lukewarm tap water
instrument: flute, piano, uke
language: english and spanish
celebrity crushes: oh god here we go: jodie comer, sandra oh, janelle monae, amy adams, zendaya, jessica chastain, tessa thompson, jennifer lopez (she was my first crush after i saw her like age 10 as a judge on american idol don’t @ me), anna torv, mariska hargitay, rhea seehorn, cate blanchett i’ll just stop here there’s too many
random fact: my cryptography team came in first yesterday on the 1o57 DEFCON forum puzzle!
i’m tagging @anti-solidcoffee @annatorv (I’m SO glad you finally secured that url) @dewysbride and @autumnofdawn98
2 notes
·
View notes