#Cloud Computing Users Mailing List
Explore tagged Tumblr posts
Text
Apple Intelligence powers iOS 18, iPadOS 18 & macOS Sequoia
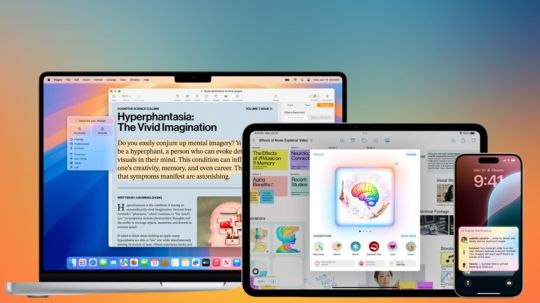
Apple launched Apple Intelligence, the iPhone, iPad, and Mac personal intelligence system that uses generative models and personal context to provide highly valuable and relevant intelligence. Apple Intelligence permeates iOS 18, iPadOS 18, and macOS Sequoia.
It uses Apple hardware to comprehend and create language and graphics, act across apps, and use personal context to simplify and speed up daily chores. With Private Cloud Compute, Apple establishes a new benchmark for AI privacy by flexing and scaling computing power between on-device processing and bigger, server-based models on proprietary Apple silicon servers.
Apple Intelligence New Language Understanding and Creation Skills Apple Intelligence offers new ways to improve writing and communication. Users can rewrite, proofread, and summaries Mail, Notes, Pages, and third-party app content with new systemwide Writing Tools in iOS 18, iPadOS 18, and macOS Sequoia.
Writing Tools boost confidence in writing by organizing class notes, proofreading blog posts, and perfecting emails. Apple Intelligence’s Rewrite feature lets users set a tone for their writing based on audience and task.
From perfecting a cover letter to injecting humour and creativity into a party invitation, Rewrite helps produce the proper words. Proofread evaluates grammar, word choice, and sentence structure and suggests modifications with explanations that users can review or quickly accept. Summaries can summaries text into a paragraph, bulleted points, table, or list.
While writing an email, a user can choose Proofread or Rewrite from the Writing Tools menu. The Summarize feature is selected in the Notes app for holistic health notes. In Mail, managing emails has never been easier. Priority Messages display urgent communications like dinner invitations and boarding passes at the top of the inbox. Instead than previewing the first few lines of each email, users can see summaries without opening them. Users can tap long threads to get relevant details. Smart Reply suggests rapid responses and identifies email questions to assure answers. Deep language understanding extends to notifications. Priority alerts display at the top of the stack to highlight what’s most important, while summaries assist users skim long or stacked alerts to see key facts on the Lock Screen, like ongoing group chats. Reduce Interruptions, a new Focus, highlights only urgent alerts like a nursery pickup SMS to help users stay focused. The Notes and Phone apps may capture, transcribe, and summarize audio. Participants are automatically notified when a call is recorded, and Apple Intelligence creates a summary to help recall key points after the call. The Notes app on iPad Pro can capture and transcribe audio. iPad Pro can summarize audio. Image Playground Enhances Communication and Self-Expression Fun Apple Intelligence enables innovative image creation to help consumers express themselves. Users may create amusing graphics in seconds using Image Playground’s Animation, Illustration, or Sketch styles. Images Playground is simple and embedded into apps like Messages. A separate software lets you experiment with different ideas and designs. Users can play with as many images as they wish because all images are made on device.
Users can choose from themes, costumes, accessories, and locales; provide a description to characterize an image; incorporate someone from their personal photo bank; and pick their favorite style with Image Playground.
Messages’ Image Playground lets users easily create amusing graphics for pals and explore personalized conversation-related themes. If a user messages a group about hiking, they’ll receive suggested concepts relating to their friends, destination, and activity, making image creation faster and more relevant.
iPhone 15 Pro iPhone 15 Pro demonstrates Messages Image Playground Image Playground presents the user’s mum as a superhero in iPhone 15 Pro Messages. In Notes, the new Image Wand in the Apple Pencil tool menu opens Image Playground, making notes more visually appealing. Users can generate beautiful graphics from rough sketches and even empty space utilising information from the surrounding region. Keynote, Freeform, Pages, and third-party apps that use the new Image Playground API also support Image Playground.
Genmojis Create Genmojis for Any Situation
Users can build unique Genmoji to express themselves. Typing a description displays their Genmoji and other options. Photos can be used to create Genmoji of friends and relatives. Genmoji can be used in texts or as stickers or reactions in Tapbacks like emoji. Genmojis are chosen for the prompt “Smiley relaxing wearing cucumbers.” In Messages, users can choose Genmoji Tapbacks.
New Photo Features Increase Control Apple Intelligence makes photo and video searching easier. Use natural language to find photographs like “Maya skateboarding in a tie-dye shirt,” or “Katie with stickers on her face.” Finding certain moments in clips to jump to the relevant segment improves video search. The new Clean Up tool can also remove background distractions without affecting the subject.
Memories lets users create stories by typing a description. Apple Intelligence will use language and picture understanding to select the finest images and videos based on the description, create a plot with chapters based on photo themes, and organize them into a movie with a narrative arc. Apple Music will even suggest songs based on memory. Apple and others do not access user photographs and videos, as with all Apple Intelligence features.
New Era for Siri Siri Siri becomes further integrated into the system using Apple Intelligence. With better English understanding, Siri is more natural, contextually relevant, and personal, simplifying and speeding up daily activities. It can track users’ stammering and preserve context between requests. Users can also type to Siri and switch between speech and text to converse as needed. Siri’s new look includes an exquisite flashing light around the screen while engaged.
Siri can now answer hundreds of iPhone, iPad, and Mac queries and provide device assistance anywhere. Mail app users can learn how to schedule emails and switch from Light to Dark Mode.
Siri will eventually understand and act on user content in more apps with display awareness. A buddy can text a user their new address in Messages and say, “Add this address to his contact card.”
Siri can do hundreds of new activities in Apple and third-party apps using Apple Intelligence. Siri will handle requests like “Bring up that article about cicadas from my Reading List” or “Send the photos from the Saturday barbecue to Malia.”
Siri will provide user-specific and device-specific intelligence. A user can say, “Play that podcast that Jamie recommended,” and Siri can find and play the episode without having to remember if it was mentioned in a text or email. Or they can ask Siri, “When is Mom’s flight landing?” and Siri will retrieve the flight data and compare them to real-time flight monitoring to give an arrival time.
Apple Intelligence must grasp deep personal context and respect user privacy to be helpful. Many Apple Intelligence models operate solely on device, a cornerstone of its processing. Privacy and security of Apple products are extended into the cloud to unlock greater intelligence for sophisticated demands that require more processing power.
Apple Intelligence can increase its computing capability and use larger, server-based models for difficult requests with Private Cloud Compute. Apple servers power these models, ensuring data is never retained or exposed.
Private Cloud Compute cryptographically prevents iPhone, iPad, and Mac from talking to a server unless its software has been publicly logged for scrutiny. Independent experts can analyze Apple silicon server code to verify privacy. Apple Intelligence with Private Cloud Compute redefines AI privacy, enabling trusted AI.
ChatGPT ChatGPT integrates across Apple platforms Apple is adding ChatGPT access to iOS 18, iPadOS 18, and macOS Sequoia, letting users leverage its expertise and image- and document-reading capabilities without switching tools. Siri can use ChatGPT’s knowledge as needed. After receiving inquiries, papers, and photographs from ChatGPT, Siri answers directly. An iPhone 15 Pro user tells Siri, “He have fresh salmon, lemons, tomatoes.” Help me create a 5-course feast with dishes for all tastes.” Siri on iPhone 15 Pro asks, “Do you want me to use ChatGPT to do that?” Siri displays ChatGPT results on iPhone 15 Pro. A bullet describes the first course, tomato and basil bruschetta. Apple’s systemwide Writing Tools will also include ChatGPT to let users write material for any topic. Compose users can use ChatGPT image capabilities to create graphics in many styles to match their content. ChatGPT users’ IP addresses are hidden, and OpenAI won’t store requests. Users who connect to ChatGPT must follow its data-use policies. GPT-4o-powered ChatGPT will launch later this year on iOS 18, iPadOS 18, and macOS Sequoia. Users can access it for free without an account, while ChatGPT subscribers can connect their accounts and enjoy paid features from these experiences.
Read more on Govindhtech.com
2 notes
·
View notes
Text
Mac email backup is very easy now
It has been a topic of discussion for long on how to mac email backup with an easy to use procedure.

Often it has been seen that Mac users complain about incomplete procedure on mac email backup. The foundation of an appropriate data backup always lies on a well instructed procedure. Therefore, it is very important to use a right, more precisely a professional tool for data backup.
While you may come across endless names for data backup tool, we offer the best in class product Mail Backup X. A well-engineered email backup tool for archiving emails from apple mailbox.
Also, the below links on Mac Operating System and Apple mail will make you understand about the subject in detail.
MacOS and Apple mail gives an idea on selection of the right tool considering different aspects of the mail communication tool.
The best way to mac email backup with clear instructions
Downloadthe mac email backup softwareand install on your Macformac email backup. Please follow the link for installation instructions.
Once the installation is completed, launch the tool from the Applications/ Quick Launch Menu.
You can start the fully functional trial run for 15 days or activate it if you have already purchased a license version of the tool.
You may choose to setup a new backup profile from the dashboard by choosing option “setup a new backup” oryou may click my backup profiles on the left side bar in the dashboard and click “set up a new backup profile”.
The next screen shows options to setup back for a list of mail clients. Choose Apple Mail and proceed to next step.
Once you click and choose Apple Mail to setup a backup you are presented with folder structure from Apple Mail accounts. Please select or deselect the folders out of all the mail accounts configured in Apple Mail.
The next step shows Advanced options like setting
* frequency of Mail backup (select automatic as its recommended or you may choose Manual or recurring at particular intervals).
* secure your backup archive by encrypting the data. So, it can only be viewed on this computer.
* you May also activate the USB Auto Snapshot option by assigning a USB drive. So, whenever you connect the USB drive, it automatically makes a snapshot copy of your local mail backup to the USB Drive in the background automatically.
8. You can set the location of backup to local disk drive or Cloud service by authenticating and adding Cloud Space (at Present Google Drive, DropBox and Microsoft One Drive are supported). Click save.
9. Apple Mail Backup Profile is set up and now your emails should have started to back up as per the options and settings you selected during the previous steps.
Demo is the preliminary answer on how to mac email backup on mac
In order to understand the basics of mac email backup, we recommend you to use the demo version of the tool initially.
The demo tool has various advantages before you proceed with the licensed product.
It is completely free and guides in the most systematic way on how to mac email backup. For more information, do visit the official website for a detailed tool on the software www.mailbackupx.com/how-to-backup-apple-mac-mail-mails-on-mac/.
1 note
·
View note
Text
Navigating the Pros and Cons of Fedora Linux 2024: A Comprehensive Overview
In the realm of Linux distributions, Fedora stands out as a versatile and powerful option for both personal and professional use. As we delve into the landscape of operating systems, it's crucial to examine the advantages and drawbacks of Fedora Linux 2024. From its compatibility with Ubuntu Server to considerations for users looking to buy RDP services or install Ubuntu on RDP, let's explore the nuances that define Fedora's appeal and areas for improvement.

Pros:
Cutting-Edge Features: Fedora is renowned for its commitment to embracing the latest advancements in software technology. With each release, users can expect access to bleeding-edge features and enhancements, making it an attractive choice for developers, enthusiasts, and tech-savvy individuals. This dedication to innovation ensures that Fedora remains at the forefront of Linux development, offering users a glimpse into the future of open-source computing.
Community Support and Collaboration: One of the greatest strengths of Fedora is its vibrant and supportive community. Whether you're a newcomer seeking guidance or an experienced user looking to contribute, Fedora's community-driven ethos fosters collaboration and knowledge-sharing. From forums and mailing lists to IRC channels and social media groups, users have access to a wealth of resources to troubleshoot issues, exchange ideas, and participate in the evolution of the Fedora ecosystem.
Seamless Integration with Ubuntu Server: For users who require interoperability with Ubuntu Server environments, Fedora offers seamless compatibility and integration. Whether you're deploying web servers, running virtual machines, or managing cloud-based infrastructure, Fedora's robust networking capabilities and package management system ensure smooth interaction with Ubuntu Server counterparts. This interoperability simplifies cross-platform workflows and empowers users to leverage the strengths of both distributions without encountering compatibility hurdles.
Cons:
Limited Support for Windows RDP: While Fedora excels in many areas, its support for Windows Remote Desktop Protocol (RDP) is relatively limited compared to other operating systems. For users who rely on Windows RDP for remote access and administration, this can present challenges and necessitate alternative solutions or workarounds. While third-party RDP clients may offer partial compatibility, native support for Windows RDP within Fedora remains an area for improvement, especially for enterprise environments where cross-platform compatibility is essential.
Challenges in Buying RDP Services: In the context of purchasing Remote Desktop Protocol (RDP) services, Fedora users may encounter challenges due to the platform's focus on open-source principles and decentralized software distribution. Unlike proprietary operating systems that may offer integrated solutions for buying RDP services, Fedora users may need to explore third-party vendors or alternative platforms to fulfill their remote desktop needs. While this underscores Fedora's commitment to openness and freedom of choice, it also highlights the importance of evaluating compatibility and support options when considering RDP solutions.
Complexity in Installing Ubuntu on RDP: Although Fedora boasts extensive compatibility with Ubuntu Server, users seeking to install Ubuntu on Remote Desktop Protocol (RDP) environments may encounter complexities and dependencies. While it's technically feasible to install Ubuntu on RDP, the process may involve manual configuration, troubleshooting, and potential compatibility issues. As a result, users should carefully assess their requirements and technical expertise before attempting to deploy Ubuntu on RDP within the Fedora ecosystem, considering alternative solutions or seeking assistance from knowledgeable community members if needed.
In conclusion, Fedora Linux 2024 offers a compelling blend of innovation, community support, and interoperability, making it a formidable contender in the realm of open-source operating systems. While its compatibility with Ubuntu Server enhances its appeal for enterprise and development environments, users should be mindful of potential challenges related to Windows RDP support, purchasing RDP services, and installing Ubuntu on RDP. By weighing the pros and cons outlined above, individuals can make informed decisions about whether Fedora aligns with their specific needs and objectives in the ever-evolving landscape of Linux distributions.
0 notes
Text
What is Plesk? A Beginners Guide for 2024
It is necessary to have a control panel in order to efficiently handle the numerous components of your server when you host your website or application on the internet. Your hosting provider, as well as other considerations like cost and user-friendliness, play a significant role in determining which control panel you should choose. You need to make use of a control panel that is not just inexpensive but also simple to operate.
One of the most widely used platforms for administering your internet server is called Plesk. However, what exactly is Plesk, and how does it function? In the event that you are curious about what Plesk is and what it is capable of doing, this article will offer you all the information you require, including its features, pricing, and other relevant details. Let's not waste any more time and get straight down to business!

How does Plesk work?
Providing users with an interface for controlling their website, application, and server, Plesk is a control panel that delivers this functionality. The first development of this platform took place in Russia in the year 2001, and it was sold to Parallel. 2015 marked the year when Plesk became an independent entity. British Oakley Capital Limited completed the acquisition of Plesk in 2017, and the company has since become a part of WebPros.
Virtual Private Servers (VPS) and dedicated servers are managed with this control panel, which is among the most popular and leading control panels in the industry. One of the reasons that Plesk is so popular is because of its user interface (UI), which is both friendly and intuitive. This makes it simple to use even if you do not have a lot of experience managing servers with other software.
What is the Function of Plesk?
When it comes to managing the many features of their server, website, or web application, Plesk gives consumers a user-friendly interface that they can use to handle these aspects. Prior to making use of Plesk, you are required to register with a hosting provider that offers Plesk as one of the control panels that you can use in order to manage your server. Some of the most well-known providers that offer support for Plesk are MyResellerHome, and Dollar2host.
You are able to carry out a variety of operations on your servers by utilizing Plesk. The following is a list of some of the fundamental activities that users are able to perform with the Plesk interface:
Email Accounts: When you sign up for a hosting package, the majority of providers will provide you the choice to register different domain names for your electronic mail accounts. Within Plesk, users have the ability to generate, manage, and organize emails for their own domain names.
Plesk allows you to manage your files by allowing you to create folders, rename your files, transfer them across folders, and delete them totally from your server if you so desire.
Backups: Plesk is also capable of backing up the data on your server or website. When users create backups, Plesk gives them the option to export the backup file to a cloud storage provider during the process.
Plesk gives users the ability to administer databases, including MySQL and PostgreSQL, among other database management systems.
Managing numerous domains from a single location is another feature that consumers may take use of.
Describe what a Plesk Server is.
It is a reference to a system that is either virtual or bare metal and is configured to use Plesk as its control panel. Through the usage of the Plesk server, customers are able to host a website or web application that can be accessed and utilized by other people on the internet. There are a number of major operating systems that Plesk Server is compatible with, including Windows and Linux.
Users have the ability to determine the types of computing resources they require when building a Plesk Server, taking into consideration the type of application they wish to host as well as their financial constraints. Plesk servers are priced differently depending on a number of other aspects in addition to the computational power that they provide. These elements include the number of domains that are to be hosted, the priority of customer support, and access to a number of other tools that one might require in order to run their website or web application.
Features of the WordPress Toolkit offered by Plesk
Through the use of the WordPress Toolkit, customers are able to effortlessly install, manage, and remove WordPress websites from their computer servers. A further feature of the toolkit is that it gives users the ability to develop plugins and theme packs, as well as configure updates. Users are also able to monitor the performance of their websites as well as the security of such websites.
Management of the Server
Through the use of Plesk, administrators are able to monitor the resources and performance of their servers, as well as control the access levels of the various users. Using Plesk's user interface, which is basic and easy to understand, all of this is accomplished. Learn how to add users and assign roles in Plesk by reading this guide, which is intended for those who are new to the Plesk platform.
A vault for applications
You can install programs on your server with only a few clicks using this marketplace, which is a marketplace of applications. A number of popular applications can be found in the Plesk app catalog. These applications include Content Management Systems (CMS) like WordPress, Joomla, and Drupal, e-commerce platforms like Magento, OpenCart, and PrestaShop, and customer relationship management (CRM) software like SugarCRM and vTiger.
In addition, Plesk gives users the ability to block applications that they might not want their clients to utilize. Customers will, therefore, only have access to applications that are pertinent to the service for which they have paid. In the event that a client pays for managed WordPress hosting, for instance, it is possible that you will be required to stop any other applications that are not pertinent to the service.
Migration of people
The ability to move websites or web applications from other web hosting control panels is one of the features offered by Plesk. The migration of websites from one Plesk installation on a virtual private server (VPS) or dedicated server to another is another option for users. Take a look at our detailed guide that will teach you how to migrate from Plesk to Plesk.
Various Safety Measures
Plesk is equipped with a number of security features, such as SSL Certificates, an integrated firewall, virus scanning, data backup, brute force protection, a password policy, and two-factor authentication. In order to ensure the safety of your servers and all of the apps that are installed on them, these characteristics are very necessary.
Functionality of eCommerce
Plesk comes equipped with a number of built-in eCommerce functions, such as the integration of payment gateways, product management, shopping cart setup, and customer order management. Users are able to easily manage and expand their eCommerce websites with the help of these functionality capabilities.
Management of the Customers
Additionally, Plesk provides its users with a customer interface that enables them to get assistance, manage their accounts, and purchase extra services that they might potentially require. The workload of the administrators is reduced as a result of this because clients are able to complete the majority of the chores on their own.
Toolkits for Self-Repair
In recent times, Plesk has introduced a number of new features, and this is one of them. Users are able to use command-line and graphical user interface-based tools to correct faults or any other problems that are affecting their servers.
The Plesk Advisor
Users are able to monitor and optimize the performance of their servers with the assistance of this program. In order to optimize their server for the best speed, stability, and security, users are guided through a variety of activities that can be taken by the Plesk Advisor. Additionally, customers are able to check their ratings for a variety of parameters, which enables them to find areas in which they may improve.
Extensions Plesk offers more than 150 extensions that customers can install on their websites or web applications in order to improve the capabilities and functioning of those websites or applications. There are a variety of helpful apps available in the Plesk extensions shop, such as antivirus software, an SEO toolkit, a backup manager, a server health monitor, a resource consumption meter, interaction with CloudFare, and more. Putting all of these in place requires only a few clicks of the mouse.
Analytical Reports and Reports
Users have the ability to monitor the real-time performance of their website or web application by utilizing Plesk Reports and Analytics, which enables them to make decisions based on accurate information. Within the Reports and Analytics dashboard, customers have the ability to view metrics such as performance, traffic, and resource utilization metrics. Additionally, Plesk displays these indicators in a visual way that is not overly complicated to understand whatsoever.
Administration of Applications
Users are able to successfully install and administer programs on their server with the assistance of this functionality. For instance, users can save time by installing applications like blogs, forums, and e-commerce websites with just a few clicks when they use the internet.
If you are concerned about the performance of your website and the quality of the user experience, it should be a no-brainer for you to choose to Supercharge Your Hosting with Plesk because of all the features and capabilities that it possesses.
Conclusion:
In a nutshell, Plesk is an all-encompassing server control panel that comes equipped with a variety of features and effective tools for the management of your web applications, websites, and servers. The plain and user-friendly interface of this software makes it simple to carry out duties related to website and server management. These tasks include the creation and management of email accounts, the installation of SSL certificates, performance monitoring, and the creation of backups, among other things.
Users are able to secure their websites and applications from a variety of cyber dangers by utilizing Plesk's fundamental security tools, which include an integrated firewall, malware scanning, and a password policy. In addition, we discovered that Plesk provides users with a number of extensions that they may utilize to further increase the capabilities and functionality of their Plesk control panel.
Plesk is an all-in-one solution that website owners, managers, and developers may use to successfully manage their servers and websites. In general, Plesk is a solution that can improve website management. It is also reasonably priced in comparison to other systems that offer capabilities that are comparable.
Plesk is available on Virtual Private Servers (VPS) Hosting, Cloud Dedicated Servers, and Dedicated Servers from Dollar2host. In addition, there are alternatives available for Linux and Windows. To determine which option is best for you, please get in touch with our sales staff.

Mary Thomas
Dollar2host
Dollar2host.com
We provide expert Webhosting services for your desired needs
Facebook Twitter Instagram
0 notes
Text
When stray from Google n Microsoft, what tend happen either:
The amount space can use for free much smaller than Google and Microsoft per account,
Not have all tools or features that Google n Microsoft have, or just 1 specialization.
Need "Self-host" or some other hands-on technical thing
This mean that might have to use multiple these, improvise a combination workflow, and/or invest time n energy into setting up
That in mind though ...
proton.me - Mail (1GB), Calendar (3 versions), Drive (1GB), VPN (1 connection), Password Manager (1 vault).
cozy cloud - Drive (5GB), Password Manager, Office (read), Notes - and some other features
cryptpad - Suite - Documents, Spreadsheets, and such. Drive (1GB) in official instance.
Terabox - Just Drive, but 1TB or 1000GB.
Transfernow - Just file transfers (5GB per transfer file)
fromsmash - Just file transfers ("unlimited" file size, but if file above 12gb it slow down while upload)
syncthing (selfhost but quick) - Just synchronizing files between devices
seafile (selfhost) - File transfer, sharing, and syncing (3 users)
of course there also app alternatives like Libre Office and OnlyOffice (self-host)
and main self-host full suites like filecloud and nextcloud (the pricing on those two website are for if you don't "self-host")
-
Self-hosting mean when you setup an app or service to connect to internet through your server / computer or someone else's.
Usually, the "cost" of if free, depend on what "server" use and how. So there people that try self-host on their own computers
Generally, self-host done on:
1. an old unused computer left running on.
2. a dedicated computer.
3. a cloud with a service with free tiers or cheap for app hosting. (though the ones with generous free tiers tend be big companies - like Amazon and Microsoft)
In other words, it require some technical literacy of that type if go this route...
There are tutorials though, like:
youtube
Self-hosting a whole thing with many options and can be overwhelming ("awesome selfhosted" list)
Also general "switch away from google" playlist (though most videos too broad for topic)
Is kinda complicated at moment.
-
Disclaimer: These not all options available in general, but are ones Magz can remember.
does anyone know a good FREE alternative to google docs, drive etc. i'm trying to systematically remove google from my life (side note: it is very fucking difficult) & i can't afford to buy microsoft 365 or anything
832 notes
·
View notes
Text
A Test For Computer Literacy
Previously on computer literacy: Step Zero
I suspect that the median desktop PC user can accomplish at least two, but no more than five of these. Somebody armed with only a smartphone will probably have a hard time accomplishing only one. How many of these can you do, and how many can your relatives do? Please tell me in the tags!
First Task
Search the web for the recipes of two different dishes (a starter and a main course). Take two recipes from different sites. Copy the text into a document, and remove the original formatting. Then style both recipes with consistent formatting, with a list of ingredients on the left, and the instructions in multiple columns. Both recipes should fit together on one sheet of paper in portrait format, separated by a horizontal line. For readability, format both recipes into two columns (plus the list of ingredients in a box on the left) with consistent column widths for both recipes. This means the text of the first recipe should flow from the left column to the right column on the upper half of the page. The recipes should not be on separate columns that flow from the top to the bottom of the page.
Print out this page, but also save a copy of the document where you can find it.
Second Task
Take the SD card out of your automated wildlife camera, stick it into your PC, and look at the pictures. Consider which image viewer program is appropriate for sorting through 500 pictures (hint: It’s neither GIMP nor Firefox, although both can open .jpg files).
Copy all pictures that contain butterflies into a folder labelled “butterflies“. Copy all pictures that contain pets or family members into another folder. If some butterfly pictures contain faces of family members, you may want to redact their faces by drawing black bars over them, or leave them out, but in any case make sure that the metadata in the pictures (specifically date and time) are intact. If there are any pictures accidentally taken of your neighbour emerging from his sauna, don’t redact them, just delete them. Compress the “butterflies” folder into a .zip file and share that with your entomologist friend. Keep the pictures of pets for yourself on your computer.
When you are done, delete all data off the SD card and put it back in the camera.
Third Task
Take a music CD, rip a track, and cut out a small section. Save that as an mp3 file, or save it as a wav file, and convert it to whatever format your phone expects. Set it as your phone’s main ringtone.
Fourth Task
Create a slide presentation on your laptop in a program of your choice. Try out the presenter mode of your program with an external monitor. Export a version of your presentation in PDF format (or HTML, depending what you think would be more appropriate), in case you cannot connect your laptop to the projector in the seminar room, and save both the “rich“ version and the exported PDF version on a USB thumb drive. Also copy both versions to some kind of “cloud“ data storage, and create a public sharing link that can be opened by a logged-out user.
Extra preparedness extra credit: Print your slides on transparent sheets to use with an overhead projector.
Fifth Task
Find out where a video game stores its saved games. Install the game on another computer, and copy the save file from the first computer to the other one. Continue playing the saved game over there.
Sixth Task
Print a document, sign it, scan or photograph it, and e-mail the signed version back.
Seventh Task
You have a large video file on your 4K film camera. It is a recording of your theatre troupe’s dress rehearsal. It’s too big to e-mail or to upload to a Slack/Discord channel. Find a way to share it with the members of the group that does not require special software or a user account to view the recording.
Eighth Task
Your brother has made a new web site for his business with one of these easy-to-use web site builders you always see advertised on podcasts and YouTube videos. Unfortunately, he made numerous typos, some of the text boxes are hard to read with their white letters on a grey background, and one of the links is hard to click for some reason. Find a way to communicate your ideas for improvement to your brother in a comprehensive and unambiguous document that your brother can open and read at his convenience.
11 notes
·
View notes
Text
TypeKit REVIEWS 2021 — ⚠️SCAM EXPOSED⚠️
what’s the culprit?
THE CULPRIT: Your Website Is NOT Available In The Native Language Of Your Potential Buyers (And Google Translate DOESN’T Fix The Problem)
The culprit may SOUND not very big or harmful, but it is.
Over 80% of your traffic can't navigate or consume your content, let alone BUY from you, because of the language barrier.
And if you don’t believe me, let me prove it:
This Major Traffic Leak Causes More Than 80% Of Visitors To ABANDON Your Site Instantly
(LOWEST PRICE GUARANTEED) Click Here to Buy TypeKit For The Lowest Price Today

So here’s what happens, on average, over 80% of your traffic that you’ll get on your page is worldwide traffic, many of which are not English speakers or not GOOD English speakers. Plus, many of them just prefer their native language. Hence they abandon the page immediately because it’s in English only, and not relevant to them.
It’ll Only Get Worse As MORE People Around The World Get Online.
And Yes, It Applies To YOU As Well.
Because unless you apply ads to your business where you choose by country, all organic traffic will be worldwide.
And besides, imagine how CHEAP it is to target non-English speaking countries, you can reduce your click cost by thousands of percent just by being available to that audience in their native language.
And It gets worse:
T.O.S (Time spent On Site) Drops, Hurting Your SEO Rankings
One of the CORE rules of SEO (Search Engine Optimization) that drives your rankings up or down, is time spent on your website.
The more time they spend on your site organically, for whatever reason, the higher your rankings will be.
The less, the lower they’ll be.
So you tell me, how’s your site's reputation doing when over 80% of visitors abandon your site immediately?
Very bad, definitely a lot worse than it could.
SO the solution is, offering your website visitors a simple way to translate the page and product without effort or harming the page, and as they do it, you get them as an email lead.
That's where TypeKit comes in...
Amazing benefits of TypeKit Commercial:
Customizable Language Switcher
Add website and generate the embed code to display your Language Switcher with your choice design and layout positioning.
Lead Capture
GDPR compliant Lead capturing of all website visitors.
Visitors Insight
Get instant overview knowledge of who your everyday website visitors are, to allow you know how to offer products or services tailored to their needs.
Edit Translation
Be the master of your locale language with ability to further make any translation edit to perfect the AI more if need be.
Remote AI Edit
Remotely Edit text on your website and still keep the design intact and never pay a developer or designer anymore
>> Click Here to Order TypeKit at a Special Discounted Price Today!

Price & Evaluation:
FE: TypeKit Commercial: $37
There will be an early bird discount price of $37 until 3pm EST and then the price will increase to $39 with a coupon 2off to take it back to the original price, then the price will go up again during the launch and at the end of the launch.

The Upsell:
OTO1: TypeKit Unlimited: $67 OTO2:TypeKit HyperSEO Suite: $67 OTO3: TypeKit ScriptWriter: $47 OTO4: TypeKit DFY Agency OTO5: TypeKit Reseller License
- 250 licenses - $127
- 500 licenses - $197
- Unlimited licenses - $297
Is It Worth to Buy?
Bonus #1 TypeKit Translator Lite Mobile App Companion - All Languages & Voice Translator($97 Value)
Translator Lite is a simple Text and Voice Translator app. Features :
Text translation: Translate between 103 languages.
Speak and translate text.
Listen to translated text.
Easily copy and paste text.
Share translated text with your friends.
Detailed history.
Clear History / Delete History.
Simple and attractive user interface.
Free Translator with speech.
Free Translate different language.
Completely free and faster.
Best word translation app.
Copy and delete text with one click.
Facebook, Admob, Startapp ads.
Clean Code And Well Documented.
Easily reskin app.
Bonus #2 TypeKit Speaker – Page to Speech Plugin for WordPress($67 Value)
Speaker is a WordPress Plugin designed to converts website page content into human-like speech. The plugin uses the latest technology of machine learning and artificial intelligence to play a high-quality human voice and add an audio player with content to the page. The Speaker plugin basis is the Google Cloud Platform, which ensures the plugin’s reliability and speeds anywhere in the world. The Speaker WordPress Plugin converts text into human-like speech in more than 275 voices across 48+ languages and variants. It applies groundbreaking research in speech synthesis (WaveNet) and Google’s robust neural networks to deliver high-fidelity audio. The Speaker is the only WordPress Plugin that supports the Speech Synthesis Markup Language(SSML) standard. SSML allows you to fine-tune speech for each article on your website. You can pause, intonate, read numbers, and telephones in the usual format for humans. Besides, the SSML in the Speaker allows using several voices and languages in a single article. For example, you can voice an article with an interview in several different voices or use this feature for online language courses.
Bonus #3 TypeKit Contacter($67 Value)
Contacter is a WordPress Plugin designed for voice feedback form for any websites. The plugin allows you to go beyond the usual text messages and contact forms and get closer to your users. The plugin adds a voice recording button to any convenient place on the site. This can be useful for reviews, order comments, or any questions. In addition to the voice contact form, the plugin has a simple and powerful editor for creating contact forms. To each form of voice feedback, you can attach a regular contact form containing fields such as e-mail and phone number or messenger.
Bonus #4 TypeKit wappBot - Chat Bot Powered by Artificial Intelligence #1($197 Value)
Are you selling some products and you have too many customers? Don’t you have time to respond quickly to your customers or don’t want to waste time with junk messages? That’s not problem. Take advantage of Talkwai’s unique Artificial Intelligence algorithm and our flawless script to respond to your customers 24/7 from your sites very easily. Share information about your products and do more. Add welcome messages and define the words you want. Prepare questions, create surveys, gather information, generate reports and see data. It all depends on your imagination! This is a Whatsapp autmoation chat bot that offers dozens of features and functionalities. It saves your time by helping you get more done. Even if you’re not on your computer, you could send questions, support or welcome messages easily. Increase your sales.
Bonus #5 TypeKit Convert Pro - The Best Lead Generation Tool($97 Value) #1 Email Opt-In & Lead Generation Plugin
Guaranteed Increase in Subscribers & Conversions!
Buy the offer from my link and send me the screenshots on this email ( [email protected]) and I will send you the bonuses
👉 Click Here to buy

What are the Benefits?
· Instant Higher Rankings thanks to a significant increase in higher time on site, which signals search engines your site is of better quality.
· Instant 500% More Traffic thanks to fixing the leak where 80% of your traffic was wasted, and now all traffic, 100% of it, is flowing in the right direction.
· 5X More Potential Sales thanks to utilizing 5 times more traffic.
· Thousands Of Leads Added To Your List Instantly thanks to our revolutionary “created by marketers for marketers” lead grabbing technology.
· Instant Lower Refund Rates & Higher Customer Satisfaction Rates thanks to the ability to translate the entire process from landing page to product, continuing a smooth flow from point A to point B.
· Finally target non-english speaking countries with ads and get penny clicks
· Higher Brand Trust & Better First Impression thanks to having a well translated and professionally looking page from the get go and throughout your entire marketing process.
>> Click Here to Get TypeKit From Its Official Website <<

Frequently Asked Questions
Q.How many Languages does TypeKit AI supports?
A.So far 116+ languages and more counting
Q.Do I need to pay a developer or designer to integrate TypeKit AI to my website?
A.No, integration of TypeKit AI is as easy as just adding your websites URL, copy and paste a code and it's all done.
Q.What happens to my already translated websites, whenever I choose to stop using TypeKit AI?
A.Your multilingua version of your websites remains intact.
Q.Is TypeKit AI lead capturing GDPR compliant?
A.Yes it is fully compliant with GDPR policies.
Q.Can I use my TypeKit AI account to translate my clients or customers websites?
A.Certainly you can make some extra bucks helping your clients or customersto get their websites translated.
Q.Does TypeKit AI work on any website or app?
A.Yes TypeKit AI supports all kinds of websites, blogs, stores, shopify or just about any app.
Q.Is TypeKit AI Mobile responsive?
A.Yes it is very mobile friendly across all devices
1 note
·
View note
Photo

Let’s take a break from specific fandoms to talk about:
Platform Wars
In 2020, we’re all asking what’s next after Tumblr. This is nothing new. “Is thing X killing thing Y?” is a question fandom has been asking since long before Escapade. But these panels offer comfort and insight into our current fear of change.
They’re also fucking hilarious.
So, without further ado, here are some past Escapade panels on the subject of Change Is Scary:
1997 - Effects of the Internet on Fandom & Slash (On the upside: more fans, more conventions, more excitement and a 24-hour party. On the downside: are the connections more shallow? Are the changes made to "fandom as we knew it" change what we enjoy? Do print fans have something to fear? Or is this simple another wave?)
2000 - Less is More: Gluttony & the Decline of Quality in Fanfic
2004 - Amusing Ourselves to Death (Fannish Discourse in the the Age of the Internet By sheer quantity, has the quality of our conversation declined to predominantly static?)
2004 - LiveJournal, Boon or Bane? (Has the advent of LiveJournal brought about the demise of mailing lists? Has it splintered the venue for discussion to the point where it's impossible to have meaningful conversation? Is the LJ phenomenon just one big egotrip? Come join us to discuss these and other questions.)
2007 - Is F’locked the New Black (Is the flocked post the future of fan communication? Are we returning to the dark ages of closed lists, zines under the table, and "have to know someone"? More and more LJ posts are locked, communities are closed, and groups are invitation only. Is there a way to protect our RL selves (and our fannish selves), yet share our fannish commentary and fic? How does this all look to a newbie? Where is our new comfort zone? And how do we keep track of all of this?)
2008 - The Organization for Transformative Works (The Best Thing Since Ever, or the End Of Days? The OTW is an incorporated nonprofit organization established by fans to serve the interests of fans in multiple ways, including by providing open-source archive software (and an archive), legal assistance, and various efforts to preserve the history of fanworks and fan culture.)
2011 - Delicious - Rumors of Death Greatly Exaggerated? (Delicious, fandom's favorite bookmarking site may be getting shut down (or at least sold out) by The Man. What to do?)
2016 - Fandom Is Fic: from BNF to TL;DR. (From paper through Usenet to Livejournal, text was king. On Tumblr, long text is an imposition—isn’t it? Has fic been dethroned from its place at the top of the heap and fic-writing BNFs along with it? Discuss the dirty little social dynamics of the shifting patterns of fannish value and how we define 'fandom' itself. And what of zines and zine eds?)
2017 - The Kids Are Not the Problem (In recent years, media fandom has grown enormously. It has also scattered, spreading out to new platforms and meeting spaces. You often hear talk about "the kids" vs. "the olds," Tumblr vs. LiveJournal, or the problem of recruiting and retaining new fans. In this panel, let’s try flipping that script. If kids are not the problem, how can we change and grow? What awesome things are other fans doing/trying that people at Escapade should know about? Most importantly, what strategies can we use to leave our fannish bubbles and more fully experience fandom in 2017?)
2019 - The fall of tumblr (Fans have always looked for a good place to build communities on line. Recent events with Tumblr and other platforms like Facebook are restricting our gathering places and even blocking and purging our self-made content. How are people dealing with this? Fandom will survive, but where? Come discuss the problems and options out there.)
And below the cut, a whole bunch more panels on platforms and change:
1991 - Quality Control in Zine Publication/Economics of Fandom (Who is making money in fandom? Should they be? How accountable are fans? Editors? Artists? Have you ever written an LOC?)
1993 - Supply and Demand in Fandom (Can we have too much of a good thing? How many cons or zine is too many? Are we glutting the market?)
1994 - Changing Nature of Fannish Communication (E-mail, and virtual zines, computer video editing and morphing -- all the new toys at our disposal...)
1996 - Internet—Will it eat your brain? Or take you to the poorhouse? (Nearly everyone has or can get access to a computer and thereby the Internet and the World Wide Web. What's out there for fans? What should you look for? What might you want to watch out for? How can you protect your pocketbook at the same time?)
1997 - Net Fiction & Print Fiction (Is the very existence of net fic changing the characteristics or reducing the quantity of print fic? Are there really stylistic and/or content differences? What makes some shows predominantly produce netfic, while others happily generate both? How do the barriers of access to each affect the fan community?)
1997 - History of Fan Socialization (Was fandom really different in the "old days"? Was there a feeling of community that we're missing now? Or is that just nostalgia clouding our memories? In today's net-connected fandom, what is (or should be) different? And what elements of the past should we try and retain?)
1998 - Professionals: Is the Circuit Dead? (Or has it just moved on-line? Is Pros fandom split on the subject of the internet? Many old circuit writers don't want anything to do with the new on-line library. They have objected to having their stories retyped an sent out, even on private e-mail. Has the paper circuit given way to the on-line library?)
1998 - Netfic Formatting A: How to Print It Prettily (An instructional panel, covering the basics of formatting, macros, and other time-saving tips to get the results you want.)
1998 - Privacy and Community: Pseudonyms, Screen Names and Face-to-Face Meetings (As more and more fandom is found online, how are we adapting to the anonymity that comes with it?)
1998 - Netfic Formatting B: From Word to Web, Making Shapely Net Slash (This panel is for everyone who wants to venture into the world of online slash, but gets nervous when faced with the myriad technical difficulties. Relax, it's easier than you think. We look at stylistic conventions, how to make your work newsgroup and e-mail friendly, and the dreaded subject header alphabet soup. We'll also cover some basic info on how to make a www archive site user friendly.)
1998 - Crossing the Line (An instructional panel on how to get what you want (more stories) in a world that may be unfamiliar to you (the web for print fans, and the insular world of zines for net fans).)
1999 - Does Print Fandom Have a Future? (In the age of instant, free net fic, is print fandom a dinosaur on its way to extinction, or a promise of reasonable quality in a sea of mediocrity? What are the key differences between zines and netfic, and what are the advantages and disadvantages of each? Can the two coexist happily? )
2000 - Promoting Critique on Mailing Lists (How to promote critical discussion and attention to the mechanics of writing on email lists?)
2000 - Changing Power Dynamics in Fandom (With the decline of zine editors and growth of the Net, what's changed, and how does it affect us and our fanfic?)
2001 - Website Workshop 2 by the lady of shalott (Setting up and maintaining a fanfic archive, and in particular how to set up the Automated Archive software used by 852 Prospect and the Due South archives.) [NB: Yes, she went through a bunch of name versions before ‘astolat’.]
2002 - How to run a Fiction Archive (and Maintain Your Sanity)
2002 - Nobody Here But Us Sockpuppets (How multiple personality disorder takes on a whole new meaning in the world of mailing lists.)
2003 - Getting slash onto your PalmPilot for computer free reading
2003 - Recs Databases! Creation and Commiseration (Do you run a recs database and want to commiserate? Do you currently have a recs page and want to become database-driven? Want to talk about the relative merits of using PHP, MySQL, or Access to organize smut?)
2003 - How to Set Up and Maintain Fanfiction Archives (If you're thinking of running an archive, or already do and need some help, this is the panel for you. We'll cover everything from choosing a method of archiving, handling fandom growth, dealing with troublemakers, and just how much time, webspace and money are we talking, anyway? Come pick the archivists' brains.)
2003 - Has Escapade Run Its Course (Scuttlebut says: It's not like it used to be. My old friends don't come any more. My new friends can't get in. It's too big. It's too small. Oxnard, for god's sake? I'm getting sick and tired of the same shit year after year. Is Escapade old and tired? Does it need to be retired?)
2004 - HTML and Website Introduction (if you don't have a website and want to create one. where doyoustart'This will cover creating basic HTML pages and common webhosting options, as well as things to think about as you set iin vour first website.)
2005 - Where Have All The Good Conversations Gone? Rise & Fall of the Escapade Panel (Are people still interested in talking about the characters, plots, and themes of their shows? Has in-depth analysis of our fandoms been abandoned in favor of meta and fannish introspection? The forums for analytical discussion are disappearing as self-censorship and over-moderation increase. Can we change this? Do we want to?)
2005 - The Fannish Wiki (So we have the directorium, the directory of All Things Fannish. We visit it and it's just so cool, and we look for our fandom to see what it says... and it's not there! How to add it? What sort of info belongs there? How does a wiki work?)
2005 - I Was So Much Older Then, I'm Younger Than That Now (We've all heard about or lived through the tumultuous era when fandom moved online. But how has slash fandom, particularly slash fandom, changed since then? Are the changes the result of online fandom, or simply of a change in culture?)
2005 - Fanfic Archives (Setting up and administering fanfic archives: concepts, considerations, techniques.)
2006 - Putting your fic on the web (Basic skills for putting your fic on the web, including building your own very basic website, using LJ as a fic-site building tool, various options for labeling adult content, and using the standard upload interfaces for popular self-submit story archive software.)
2006 - Nifty Technology and the Future of Fandom (Fandom is quick to adapt to change and continues to bring fen together and to create fannish product. Fans have thrived regardless of how they communicate; via the post office, mailing lists, message boards, and Livejournal; they've pushed the frontiers of video and audio technology; and have managed to survive changes in copyright, pornography, and other laws. What are the upcoming trends and shiny new technologies on the horizon and how will fen use them to enhance fandom?)
2006 - Intermediate Webmastering (Designing your website for usability, options for restricting access to your website, making your stories easily accessed by mobile devices, and things to consider so fans can easily locale your site.)
2007 - Free Webtools and How to Take Fandom Advantage (Lots of free tools are available on the web to help the needy fan! Tools to edit pictures, make icons, write stories, share recommendations, share stories, and be fannish are becoming more available and more user friendly. Come chat about tools like del.icio.us, google docs, pxn8 audacity, itunes, the gimp, bittorrent, imeem, youtube and lll other things that you come and tell us about!)
2008 - E-book Readers (Sony PRS-505 or Amazon Kindle what's all the fuss about? Introduction to E-Ink and other mobile devices. What are the pros and cons of various devices? Where do you find e- books and fan fiction, and most importantly how do you get fan fiction formatted so you can read it on your ebook reader?)
2008 - If You Build It, Will They Come? (Roundtable on meta fannish infrastructure building strategies. bethbethbeth can talk about some of the specific challenges OTW is facing in its brave new fan territory, while oulangi can talk about why metafandom has flourished while very similar projects have failed, while we'll both discuss some of the challenges of the established meta/fannish structure of new communities, new fans, new technologies—and most of all, how do you keep the meta-fan conversation moving forward?)
2008 - Livejournal: Should Fans Take Their Business Elsewhere? (A discussion of the pros and cons of fannish communication on the various blogging entities.)
2008 - How to Find and Use Free Stuff on the Web (All kinds of free webapps are available for fic, art, icons, communication, and all sort of other fannish stuff. Come share favorite sites—we can bookmark everything we talk about on del.icio.us in real time!)
2009 - The Organization for Transformative Works (Off the ground and starting to soar! Come here about the latest developments in the OTW's projects and discuss where you'd like to see it go next.)
2010 - Is Somebody Taking Notes On This?: A Discussion of the Role of Fannish History (In honor of Escapade's 20th anniversary, let's talk about recording fannish history. What are the challenges? Is it worth doing? Can it be done in a fair way? What are we afraid of happening if we try? Is Fanlore the right vehicle for the project?)
2010 - The OTW in Its Third Year led by Elke Tanzer and Shoshanna (Okay, sure, the Organization for Transformative Works bought its own goddamn servers and hosted an archive (that hosted Yuletide) and published a journal (with a special issue on Supernatural) and saved a bunch of Geocities sites and testified at the DMCA hearings (supporting the FFF's proposed exemptions for vidders and other remix artists) and made a bunch of lolcats—but what have they done for us lately? [5] What do you want them to do?)
2010 - We Are All Naked (On The Internet Now) led by treewishes (Social networking platforms like Facebook and Twitter are conspiring with Google and your ISP to out your slash pseudonym to your RL friends, and to tell all your slash buddies your real name. Is there any way to stop the wave of facial recognition software or your oh-so-helpful friends who type your birthday into the cloud? Or is all this an inevitable consequence of evolving technology? Come on in and let's talk conspiracy theories!)
2011 - Fanlore: Are BNFs Writing Our History?, led by Sandy H (Fanlore has an official policy of 'plural points of view', but is that really happening? Have you ever looked up a kerfluffle you were involved in, and seen how your side of the battle was portrayed.' And on the other side, are we afraid of conflict, to the point that Fanlore is bland and safe?)
2011 - OTW/AO3 Wish List Conversation, led by Sandy H (Do you feel like you don't know how to get your A03 or OTW wishlist through the bureaucracy? A03 is getting better all the time, but there's a ways to go. Let's brainstorm and turn a list over at the end of the panel.)
2011 - The Reccing Crew (Recommending a fanwork is deeply woven into our culture. Are there new social mores at work when we make public recs? How has the move from letters to mailing lists to Livejournal and Delicious affected reccing? Delicious was conceived as a bookmarking site, but often operates as a recs and comments site. If it goes away, what would replace it?)
2012 - Tumblr, Twitter, and Pinboard, Oh My (and GetGlue, too!) (In the past year, the ongoing fannish diaspora has picked up speed, as more fannish activity has moved away from LiveJournal and Dreamwidth, and onto sites like Tumblr and Twitter. And then there was the Delicious implosion. Now there's GetGlue, a social network specifically for entertainment. Let's talk about navigating these sites—their strengths and weaknesses, and how to use them.)
2012 - The Kids These Days (Ever wanted to tell someone to get offa your lawn? Strangle the next person who said that? Revive a dead fandom? Joined a fandom you were 20 years "too old" (or young!) for? Did you go from Usenet to mailing lists? From zines to livejournal? Are you eyeing Tumblr and Twitter with alarm? Let's talk about weathering changes in fandom with grace—or at least a little humor.)
2013 - Privacy, Secrecy, and the Fourth Wall (The fourth wall between fans and The Powers That Be is shrinking day by day. Are the technologies we're using changing fannish etiquette {from invite-only mailing lists, to friends-locked journals, to all public all the time tumblr)? Should we run for the hills or embrace the change? Discuss!)
2013 - The What With the Where Now?! (Every time you turn around fandom is playing on a new site that has new functionality, new ways of interacting and new lingo. Join us in surveying places like tumblr, twitter and getglue.)
2014 - Tumblr: Missing Missing E (So you've just gotten the hang of Livejournal when all of a sudden fandom has jumped shipped to this new "microblogging" platform called Tumblr. What is "microblogging" anyway, and where do you even start? Join us in this tutorial/discussion on creating an account, deciphering the culture, finding fandom, and making Tumblr work for you.)
2014 - Out Of Step With the World (You have no current fandom. You can't even get Tumblr to load. What do you do when you're feeling disconnected and alienated, but you don't want to leave fandom for good? If this sounds like you, come join us to figure out some strategies for rekindling the love, making new friends, and finding your place.)
2014 - Real Fannish Community (Has AO3 ended the era of real fannish community or has it ushered in a new era of increased connectedness? Is Tumblr better or worse than the old days (and were the old days livejournal? yahoo groups? APA snail mail zine groups?)? I'm hoping for equal parts 'get off my lawn' and 'the future's so bright I gotta wear shades' debate here.)
2015 - Tumblr 102: Into Darkness. You’re here, now what? Here we talk about etiquette and xkit and making the most of your fannish tumblr experience.
2017 - Home on the Web (LJ's Russian overlords have removed HTTPS support and are moving the server activity to Russia; some say a shutdown of US services is on the horizon. Yahoo fails to make money with Tumblr. Dreamwidth is slow, and doesn't have media hosting. Email lists are a hassle. Imzy, a startup, places branding aesthetics over design usability. Where's the next place for fandom, or should we reclaim one or more of the platforms from the past?)
2018 - How to Tumblr (Like it or not (often, mostly not), tumblr is where fandom is most active right now. How do you find anything? How do you have conversations? How do you archive the bits you like best? The good news: the answers are not, "you don't; you don't; you don't." Bad news: Those aren't actually good questions for being fannish on tumblr.)
2019 - Social Network of Our Own (SNO3?) (Between FOSTA/SESTA, Article 13, Facebook's new "don't mention that sex exists" policy, and the Tumblrpocalypse, is it time for our own fannish social site? Or are Dreamwidth and Pillowfort enough?)
60 notes
·
View notes
Text
7 Power Laws of the Technological Singularity

When people talk about the technological singularity they usually do so exclusively in the context of Moore’s Law. But there are several Moore’s Law-like laws at work in the world and each of them is equally baffling. I’m referring to this list of trends as “power laws” because of the nature of their incredible rate of growth and because they independently work as pistons driving the engine of the singularity. A few things to note about these power laws. Firstly they are just observations. There are no, known, deeper physical principles in the universe that would lead us to believe that they must hold true. Secondly, we’ve observed these trends long enough to warren their recognition as power laws and there is no evidence or signs of their stagnating. We’ll start with the most famous and well-known power law and work our way through the others.
1. Moore’s Law
Moore’s Law states that transistors on a chip double about every two years and that the cost of that doubling halves. This is a double-edged sword. It means that the next model computer will be way faster than the previous but it also means that the value of your existing computer is dropping rapidly. The end of Moore’s Law has been proclaimed for a long time but there seems to be no end to its progression.
As we reach the physical limits of transistor sizes, entirely new hardware architectures are developed that sustain the progression. Things like 3D chips, specialized chips, and non-silicon based chips like photonics, spintronics, and neuromorphic chips are being developed and will ensure that this law continues.
“Regular boosts to computing performance that used to come from Moore’s Law will continue, and will instead stem from changes to how chips are designed.” — Mike Muller, CTO at ARM
What this does not mean is that a user’s experience of computer speed will increase. We tend to be more sloppy with application development when it’s cheap to make up for it with hardware horsepower. There is a standing joke that the same amount of computing resources that were used to send astronauts to the moon in the ’60s is now accidentally used by a sluggish browser tab.
2. Kryder’s Law
The second law driving our propulsion into the technological singularity is Kryder’s Law. It states, loosely, that digital storage doubles every year. It specifically has to do with magnetic storage but the principle is applicable to all digital storage as you will see. While you may not see this law exactly played out in the price of external drives in your local Best Buy, you can see it if you consider the price of cloud storage services.
Let’s look at the current top cloud storage providers. Apple offers two terabytes of cloud storage for about $10 a month. Google offers the same space for the same price as well as 10 terabytes for about $100 a month. After that, users can get 20 terabytes for $200 a month, 30 terabytes for $300 a month, and so on. Dropbox offers yet a similar package but with extras like full-text search for $20 a month. Lastly and most competitive is Amazon offering an incredible $0.004 per gigabyte per month through its Glacier storage service. When you take these cloud providers into account and consider that they will only grow via economies of scale, you see that Kryder’s law is in full effect.
Note that this also doesn’t even take into consideration innovations like Filecoin that actually distribute Kryder’s Law by allowing anyone with storage capacity to rent that space out. You could look at it like Uber or Airbnb for digital storage. This highlights the idea that this digital power law, like the others, should not be strictly tied to a hardware implementation. Similar to how Moore’s Law continues but not strictly through cramming more transistors on a chip but through new engineering architectures. The same principle applies.
3. Nielsen’s Law
Thirdly, we have Nielsen’s Law. If the previous laws could be summarized as computation and storage, this one is summarized as throughput. It states that bandwidth grows by 50% a year. More precisely, it states that the bandwidth of high-end users grows by 50% a year. That’s just 10% less annual growth than Moore’s Law.
In practice, we don’t see this linear growth and there are three reasons for it. One, Telecom companies are conservative. It cost billions of dollars to update their sprawling hardware. Two. The immediate impact of the end-user is not a guaranteed faster experience if they do upgrade their infrastructure. You can have the fastest hardware in the world on your street but that doesn’t automatically make the rest of the countries hardware faster. That slow loading web page may only be imperceptible faster after your area’s hardware is upgraded. Lastly, as new people get online, it’s more likely they are using older slower devices so the average expected speed is kept pressed down by these newcomers.
Since 1G was introduced in the 1980s, new wireless technology has been released every ten years. The advent of 1G introduced mobile telephony. Than 2G in the ’90s brought about global roaming and SMS. The 200’s saw 3G and smartphones with data. 2010 introduced 4G and mobile broadband. The year 2020 will be the year of 5G and the realization of the fully ubiquitous cloud. To put this in perspective, let’s say you wanted to download the newest episode of your favorite television show. At 800MB it would have taken 8 hours hrs to download in 1998, 5 hrs in 2001, 45 minutes in 2009, and 1 second with the new wireless protocol.
The impact and roll out of 5G will be enormous. With current networks, it takes about 100 milliseconds for information to travel across a network. With 5G, that latency will be reduced to 1 millisecond. We are talking about downloading full-length 5k movies in less than a second, surgeons controlling surgical robots in real-time from across the country, smart cities, and smart car-to-car communications.
4. Koomey’s Law
Koomey’s law has to do with the efficient use of energy and states that the number of computations per joule of energy dissipated has been doubling approximately every 1.57 years. This trend has been stable since the 1950s and has been faster than Moore’s law. Jonathan Koomey reframed the trend as follows: “at a fixed computing load, the amount of battery you need will fall by a factor of two every year and a half”. You can see the effect of this law in today’s newest generation CPU’s (Apple’s M1 chip) that are pumping out incredible amounts of processing power at significantly reduced levels of energy consumption.
5. Metcalfe’s Law
This power law with its closely associated cousin, the network effect, asserts that the value of a network is proportional to how many users are a part of it and that the addition of a new member adds value to all the existing members. A good example of this power law at work are social media sites like Facebook and YouTube. These sites had no revenue model in the beginning and were very expensive to run but grew to have so many users that the value grew directly from the value of the size of the network itself. Not too many years ago, software products had to packaged on physical media and shipped through the mail to users. Now, the same products can be built and deployed to one of any number of app stores and have a global audience with little to no overhead.
6. Hendy’s Law
Next, consider Hendy’s Law. Hendy’s Law states that the number of pixels per dollar in a digital camera doubles every two years. We can generalize this trend to encompass the idea that our ability to capture images and video of the world is exponentially improving year over year. This improvement opens the door to such high-fidelity VR and lifelogging that our human senses begin to find synthetic media and real-life indistinguishable. This already exists in the form of gigapixel photography where images are used instead of real specimens in biological study where we can’t tell the difference even under a microscope. Imagine being able to photograph a group of people and then zoom in so close later that you can identify properties of their cellular biology.
7. Bell’s Law
Last on our list is Bell’s Law. It says a new class of smaller, cheaper computers comes along about every decade. With each new class, the volume shrinks by two orders of magnitude, and the number of systems per person increases. The law has held from 1960s’ mainframes through the ‘80s’ personal computers, the ‘90s’ notebooks, and the new millennium’s smart phones. This is likely manifesting in the realm of wearable right now with the wild success of smart watched and wireless intelligent earbuds.
To wrap this up and summarize, while there may be temporary or geographically isolated stalls in the progression of these laws, they are still holding steady. You might compare them to walking up a set of stairs. At various points in your travel up the stairs, you rise up very high and then drop low. You do not move at a constant linearly increasing height. You go up and down but the trend is a clear move upwards. Through that up and down, you are converging on a net increase. The same is true of these digital laws. The overarching result is that software is eating the world and eating itself, recursively accelerating the process even further. One doesn’t need to theorize about potential advances in machine intelligence to see that we are accelerating into an unimaginable future. A clear technological singularity.
If none of the above convinces I will leave you with this chart illustrating the grown of the global economy. Assuming the continuation of these power laws, where are we 50–100 years from now?

3 notes
·
View notes
Text
How to establish taxi reserving application
Practically each and every smartphone person provides a taxi scheduling application downloaded on their own gadget. The market for on-demand companies apps has actually been proliferating and now represents an incredible selection of options and designs.
We chose to compose this post to get rid of some gentle on what it's going to take to construct a clone of Among the most famous As well as in some ways controversial apps of recent occasions. Looking to contend with Uber’s world dominance is a daunting problem, but launching an identical company at the nationwide or regional levels looks really promising.
At Japanese Peak Now we have effectively implemented various identical tasks together with Gett, a world taxi provider, #1 for on-demand from customers corporate transportation driving 50 percent the Fortune five hundred.
To create a taxi scheduling application like Uber we must know how it really works and define its basic building blocks.
Common overview
On-need experience companies (also referred to as journey-hailing or ridesourcing products and services) like Uber are marketplaces where individuals (riders) and service companies (drivers) can link with one another.
Drivers for these providers are usually not necessarily certified professionals but are personal people who use their own autos and need to make some more money. This simplistic approach which captures a standard consumer desire is exactly what tends to make these expert services accessible Just about all over the place – something not achievable by regular taxi corporations.
A person who calls for transportation solutions simply just needs to create a request to the application. Once the ask for has been created, a notification with all the mandatory information, like The placement and level of vacation spot, is distributed to the closest driver. The driving force both accepts or rejects it.
In the case that a rejection is built, the request is allocated to the nearest driver etc. If the driver accepts the request, they travel to The client’s place to choose them up. Later on, the two the passenger and the driver get an option to level each other.
How it works underneath the hood
Launching applications of this sort of complexity entail equally consumer and server-aspect growth. They need a central server to handle interactions involving a number of people (in our circumstance passengers and drivers), to execute advanced computations (matching, cost calculation, ETA, Fee subtraction, and so forth), and organization logic and information storage capabilities. Uber maintains various geographically dispersed servers to enhance response occasions, remove failures and supply continual support availability.
Uber’s backend program is prepared making use of these types of systems as Node.js, Python, Go, Redis, MongoDB and MySQL. Moreover, it takes advantage of its possess facts center community even though also relying on third-party PaaS/IaaS vendors for example Amazon Web Solutions for many functions.
Trip-hailing products and services of this kind of magnitude as Uber are unable to do without having its individual massive computing infrastructure. Nonetheless, It will likely be sufficient to guidance your complete backend in the Preliminary levels within your undertaking working with cloud support suppliers like Amazon Website Services, Microsoft Azure, Google App Motor or Parse.
On-demand experience companies also depend seriously on diverse frameworks and APIs for navigation, on the internet payment and conversation. Uber employs Google Maps to point out the surrounding place, Core Place and Google Spot Expert services API to ascertain the user’s spot, MapKit and Google Maps Instructions API for route configuration, Braintree for payments, Twilio for SMS notifications, Apple Force Notifications Services and Firebase Cloud Messaging for drive notifications, and SendGrid for sending transactional e-mails.
The client-side of a taxi booking application like Uber consists of two interactive cellular applications – a single for demand from customers (travellers) and one particular for supply (drivers), Every with its possess list of features. There’s also will need for the online-based mostly admin dashboard which will provide the function of centralized backend-Workplace, to observe all the process and also to complete administrative steps. Shopper aspect cell apps may be developed as native applications making use of platform-unique programming languages (Java for Android or Goal-C/Swift/C++ for iOS) or cross-platform/hybrid apps applying HTML5,CSS & JavaScript. While in the context of taxi reserving application development, utilizing a local strategy is considered much more preferable.
Let’s now discover shopper-facet apps in better element, outline The essential attributes they ought to have and how to implement them.
Needs to have features for the two Driver and Passenger apps:
1. Registration and Authentication
Uber like applications must present social websites and electronic mail/password signup and login performance. Creating a profile, past increasing buyer retention, is required for companies that entail mobile payments. As yet another necessity for drivers, profiles must be verified and accredited via the support administration.
2. Profile modifying
Travellers and motorists should be capable of effortlessly edit their own profiles: identify, Image, cell phone number, email, etcetera. The motive force app must also include the driving force’s license and information about the vehicle (manufacturer and calendar year of creation, car or truck class, shade, license plate amount) and its Image. Both of those the driving force and also the passenger need to have the ability to view each other’s profile. With this data, they might understand one another within the pickup site. This will help minimize anxiety and offers a sense of security.
three. Matching
Matching permits a passenger to routinely connect with the closest out there driver. It’s a fancy algorithm which will take into account a number of components: places of your passenger and nearby drivers (Uber displays approximately eight motorists), motorists’ standing and their rating, vehicle versions, and so on. The driver has a couple of seconds to just accept the request (Uber offers fifteen seconds) just before it goes to the following driver.
Some taxi scheduling providers allow for travellers to choose the driver manually. At present Uber doesn’t make it possible for this selection.
You could also include an option to customise the matching algorithm. One example is, a driver could set a spot filter and be matched only with Those people riders who are interested in traveling in precisely the same route.
four. Navigation
At the center of a place-primarily based application like Uber is the technology of GPS tracking, all over which all the things else is built on. It makes it possible for to discover latest spots of passengers and motorists, draw paths between them, established pickup and drop-off destinations, track the motion of autos and in some cases compute the cost of the ride along with the ETA (estimated time of arrival). These details sets are sent to the server for even more processing and broadcasting to other customers in that exact place.
A lot of geolocation, https://androiddevelopers.co/united-states/california/sandiego orientation, and mapping APIs will also be used when constructing apps with navigation options.
5. Notifications
Now most experience-hailing apps use a few options to notify consumers about critical occasions: SMS, press notifications and e-mail. Thrust notifications is often implemented making use of absolutely free utilities furnished by platform suppliers: Apple Push Notification Provider for iOS and Firebase Cloud Messaging for Android, or third-occasion cross-platform utilities like OneSignal.
To put into practice SMS notifications Uber utilizes Twilio but there’re a number of other equivalent services companies: Plivo, Nexmo or Sinch.
For sending advertising and transactional e-mails Uber employs SendGrid.
six. Analyzing and exhibiting the expense of a trip
The two the driver as well as the passenger must know the estimated fare beforehand. As we talked about previously, calculating the actual fare with the trip will likely be performed within the server-facet. It could entail the subsequent parameters and elements: the distance between pickup and fall-off areas, cost of fuel, probable reductions, auto class, traffic and weather conditions, peak several hours and many others.
Uber makes use of the so-named ‘surge pricing’ approach and improves its regular fares when demand from customers for rides exceeds supply, which happens to be currently a really controversial aspect and Lots of people have already been complaining about it due to the fact its introduction. We don’t recommend implementing this feature, no less than originally, mainly because it could repel buyers.
seven. Creating payments
This really is how it works inside of Uber’s application:
Uber has partnered with Braintree to securely acknowledge payments throughout the app. All payments are cashless, so once the ride has done, payment is withdrawn mechanically with the payment gateway. There are plenty of other on-line payment providers like Stripe, Worldpay or Adyen. They provide sturdy APIs, that can certainly be built-in into cellular applications. All of these are optimized for World-wide-web, cellular and in-app purchases. They assist significant bank cards like Visa, MasterCard, American Categorical and digital wallets like Apple Shell out, Walmart Shell out, Android Pay back and plenty of Some others.
Uber makes income by charging drivers a twenty% Fee on all rides booked by means of it. Payments are transferred to the driver’s account every week.
Regular cash payments really should not be fully eradicated. Paying out in income continue to remains the dominant payment technique in a few international locations, in rural spots or for some classes with the inhabitants like senior citizens and teenagers.
8. Ranking and responses
Travellers and drivers ought to have the capacity to price each other after the journey is around. This feature aids keep a large standard of service. Drivers with small scores will at some point not be capable to use the support. If a passenger features a lower ranking, it might be more durable for him to get a journey. Travellers must also have the ability to offer suggestions on their own working experience through the vacation. This suggestions will probably be shown in the motive force’s profile for Other people to view.
Analyzing the ranking of equally the need (passengers) and the provision (motorists) can help you discover strengths and weaknesses in the assistance and make enhancements where by wanted.
nine. Reserving and payments historical past
Both motorists and passengers need to be able to check out comprehensive data about previous visits from their profiles: date, time, Value, driver/passenger name, automobile design, pickup and drop-off locations, score etcetera.
10. Reserving cancellation
Motorists and passengers should have the ability to terminate a experience. In the situation of the cancellation, a rate can be charged.
Ought to-have capabilities for the Passenger App:
Tracking close by motorists
Capacity to set the pickup site around the map without having typing an tackle
Capacity to see pertinent facts about the driver: name, Image, contact facts, rating, car kind, and ETA (approximated time of arrival)
Notification upon taxi arrival
Choosing automobile typeRiders needs to be ready to choose between different classes of motor vehicles (In the situation of Uber you'll find UberX, UberXL, UberSelect and Uber BLACK). Needless to say, the fares will differ depending on the form of motor vehicle
Sharing rides with other passengersA rider must manage to share a reserving with One more rider who’s heading in a similar path and break up the price
Most loved addresses for handy long term bookings
Should-have characteristics for the Driver Application:
Finding passenger on map
Power to see appropriate facts regarding the passenger: title, photo (optional), Get hold of data, rating, number of travellers;
Power to settle for or deny requests
Placing position (Go Online / Go offline)The “Log on” standing permits passengers to find out motorists about the map and have interaction them. The “Go offline” standing will temporarily cover the driving force from remaining tracked.
Admin panel
The admin panel will likely be an internet-based mostly interface that can help take care of your entire assistance: handle back-end settings, handle drivers, passengers, requests, transactions, look at passengers and motorists’ routines, figures, and produce reports.
Website-based buying portal
As an extra choice for passengers you could Establish an on-line Net portal that can duplicate the features of the Passenger cellular app and permit them to create requests ideal in the browser without the require for any mobile app.
MVP
You don’t have to fill the product with all the above mentioned-described Innovative features when releasing it to the market. We suggest getting started with a Least Practical Product (MVP) – the initial Edition with the item that will include things like both equally Passenger and Driver applications along with the Admin Panel Using the most basic and indispensable features simply to ‘check the waters’ of the marketplace.
How long will it take to acquire an MVP for an application like Uber
Below’s an approximate list of features for a taxi booking app MVP and our rough estimate of the amount advancement time it will acquire:
Functional technical specs and layout
Making a in-depth useful specification to the conclusion product and UI/UX style and design – one hundred twenty-150+ several hours
Superior-amount design and style: Database schema, third party integrations, know-how stack, etc. – fifty+ hrs
Acquiring an application for only one platform
Making an application for iOS and Android can take 2 times as while.
Registration (in-app or by means of social networking sites) – 32-40 hours
Consumer profile – 16-24 hours
Driver profile – sixteen-24 hrs
Putting an buy (customer) – 80-ninety six hrs
Booking (driver) – 48-fifty six hours
Pickup area and route – 32-forty hours
Booking heritage (shopper)- sixteen-24 hrs
Reserving background (driver)- sixteen-24 several hours
Payment (include a card, integrating payment API, computerized payment after the purchase is entire) – forty-forty eight hours
Backend development
Database schema – 24 hours
Organization logic – 240 hrs
Admin dashboard – a hundred and sixty several hours
Technique general performance report – a hundred and sixty hours
Top quality Assurance
QA commonly provides about 30% additional to the event time.
You should Notice, that this is really an approximate estimate based upon our preceding undertaking in taxi scheduling app development. The development time of similar task may possibly vary with regards to the UI/UX complexity, challenge specifics and enterprise logic complexity.
Increasing the performance
One example is, there’s no have to have to include rating and opinions functionalities, Price tag splitting or preferred addresses to the MVP or develop the world wide web-primarily based purchasing portal. These capabilities offer added worth, but you can save Preliminary fees and depart it for afterwards date. Working with only thrust notifications to establish a link in between motorists and travellers will likely be adequate. Here’s a list of other attributes which could be extra later:
scheduled rides
discount rates and free rides
power to choose drivers (presently Uber doesn’t provide this selection)
desired destination filter for motorists
paid waiting around time for drivers
dynamic pricing (surge pricing)
in-application chat
voice-pushed Guidance
in-app suggestion element
insurance coverage
multi-language aid
promo codes
gamification
In addition to the most simple and indispensable characteristics we’ve protected in this post, an MVP could also contain Unique advertising functions to aid get initial shoppers (each motorists and riders) and market your application in these techniques
signup bonuses
tipping motorists to stay on the web even if there’s no demand
free of charge rides for new travellers in the expense on the services
no commission For brand spanking new motorists for the first three months
The way to get going?
The products discovery section is the greatest initial step you might take to put a good foundation for the event of the app. It features a functional specification, UX/UI structure, and a visible prototype that provides you with a clear eyesight of the tip merchandise. On typical, this phase can take 4-6 months.
The item discovery phase will help you:
define a full scope of work and acquire a roadmap for the challenge set a realistic spending plan for the MVP and strategy your sources, examination the waters together with your audience applying a visual prototype, craft a convincing expenditure pitch, get to learn your workforce
2 notes
·
View notes
Text
Henry Payton | Cyber Security Tips for Small and Medium Business
Henry Payton – Keeping business data safe is the number one concern of business nowadays. Due to the rising security breaches on several companies, data security against unwanted intrusion is on everyone’s mind. No matter big or small, IT security is the biggest challenges organizations face. When it comes to small or medium enterprise the impact of security threat is even more severe. Cyber criminals love to target small business largely due to the fact that SMBs cannot afford to implement strong security protocols. Nothing can be hundred percentage safe, but at the same time SMEs can advance the protection environment by acquiring a strong understanding of their external web presence and ensuring it is secure by undertaking penetration testing and minimizing exposure by taking action such as regularly updating security patches.

Henry Payton | What is Data breach and how it happens?
Data breach is an incident in which sensitive, protected or confidential data has potentially been viewed, stolen or used by an individual unauthorized to do so. The most common concept of a data breach is an attacker hacking into a network to steal sensitive data. A number of industry guidelines and government compliance regulations mandate strict governance of sensitive or personal data to avoid data breaches. It is a scenario where your company or organizations’ data is stolen. When we check into the company folder and find all information is gone, client files, logs, billing information have all been compromised. Then it is clear that your business is becoming a victim of a data breach cyber-attack.
Most common causes of data breaches
Protecting sensitive data is critical to the lifeline of an enterprise. What can be the most common causes of data breaches?
• Physical loss or theft of devices is one of the most common causes of data breaches: This is arguably the most straightforward of the common causes of data breaches. However, there are many different ways that this can occur. It could be that anyone of your laptop, external hard drive, or flash drive has been damaged, stolen, or misplaced.
• Internal threats like accidental breach (employee error) or intentional breach (employee misuse): This can occur when employees handling delicate data not clearly understanding security protocols and procedures. Data breach can also occur from a mental error, when an employee sends documents to a wrong recipient.
• Weak security controls are often top concerns for protecting an organization’s data: Incorrectly managing access to applications and different types of data can result in employees being able to view and transport information they don’t need to do their jobs. Weak or stolen password has been yet another main concern. When devices such as laptops, tablets, cell phones, computers and email systems are protected with weak passwords, hackers can easily break into the system. This exposes subscription information, personal and financial information, as well as sensitive business data.
• Operating system and application vulnerabilities: Having outdated software or web browsers is a serious security concern.
Tips to prevent Cyber threat | Henry Payton
Amid the chaos and the hype, it can be difficult to get clear, accurate information about what’s really going on when a data breach occurs. While data breaches are certainly a complex issue, equipping yourself with basic knowledge of them can help you to navigate the news, to handle the aftermath, and to secure your data as best as you can. The increasing frequency and magnitude of data breaches is a clear sign that organizations need to prioritize the security of personal data.
Latest developments like embracing cloud, deploying BYOD etc. enhances the risk of cyber threat. Employee ignorance is also one of the major concerns. Hackers are well aware of these vulnerabilities and are organizing themselves to exploit. There is no need to panic, especially if you are a small business, but it is imperative to take a decision. Make yourself difficult to target and keep your business secure with these top 5 tips.
Here are the top 5 tips to prevent the cyber threat.
1. Encrypt your data: Data encryption is a great preventive control mechanism. If you encrypt a database or a file, you can’t decrypt it unless you have or guess the right keys, and guessing the right keys can take a long time. Managing encryption keys requires the same effort as managing other preventive controls in the digital world, like access control lists, for example. Someone needs to regularly review who has access to what data, and revoke access for those who no longer require it.
2. Choose a security that fits your business: Cracking even the most secure companies with elaborate schemes is now far greater than ever. So adopt a managed security service provider that can deliver a flexible solution cost effectively and provide a seamless upgrade path.
3. Educate employees: Educate employees about appropriate handling and protection of sensitive data. Keep employees informed about threats through brief e-mails or at periodic meetings led by IT expert.
4. Deploy security management strategy: Nowadays cyber-attacks are highly organized so organizations need to establish a strategic approach so that your entire environment works as an integrated defense, detecting, preventing and responding to attacks seamlessly and instantly.
5. Install anti-virus software: Anti-virus software can secure your systems from attacks. Anti-virus protection scans your computer and your incoming email for viruses, and then deletes them. You must keep your anti-virus software updated to cope with the latest “bugs” circulating the Internet. Most anti-virus software includes a feature to download updates automatically when you are online. In addition, make sure that the software is continually running and checking your system for viruses, especially if you are downloading files from the Web or checking your email.
Actions or measures that can be taken if any, malicious attack suspected in your network
• If when an unknown file is downloaded, the first step is to delete the file. Disconnect the computer from the network and have IT run a complete system sweep to ensure no traces are left.
• Whenever a key logger is detected on a computer, IT should immediately reset password on all related accounts.
• Businesses should have central administration capabilities on their local and cloud server. Controlling which users have access to what files/folders on the server ensures that essential business data is only accessible by authorized individuals.
• Have all business files backed up in a remote cloud server. If disaster recovery is necessary, all files backed up in the cloud can be imported back to the local server to prevent complete data loss.
Perfect Cyber Security involves:
• Determining what assets need to be secured • Identifying the threats and risks that could affect those assets or the whole business • Identifying what safeguards need to be in place to deal with threats and secure assets • Monitoring safeguards and assets to prevent or manage security breaches • Responding to cyber security issues as they occur • Updating and adjusting to safeguards as needed
Every day businesses are under attack on multiple fronts, and realizing that data breaches can stem from several different source allows for a more comprehensive protection and response plan. Never assume that your data is safe because you have the best electronic protection, or because you don’t use POS terminals. Criminals want your data, and they will try anything to get it.
1 note
·
View note
Text
Windows 10 evaluation : hands on with Windows 10 – the constructive return of the Start Menu and different Desktop UI options
Windows 10 overview: what’s Windows 10?
Microsoft in late 2014 took the wraps off the Technical Preview of its subsequent Windows working system, and in doing so it took everybody abruptly. We anticipated the following era of Windows: we simply did not anticipate it to be referred to as Windows 10. None the much less right here is Windows 10: the following Windows OS for PCs and laptops, smartphones and tablets . And, certainly, an OS for servers and all factors inbetween.
Microsoft execs said that Windows 10 would be built from the ground up for a world in which mobile- and cloud computing are key. They also told us that Microsoft was committed to making Windows 10 friendly for the enterprise, ideal for keyboard and mouse users, but also optimised for touch. Oh, and Windows 10 will put the same interface on devices with displays ranging in size from 4in to 80in. ‘One product family, one platform, one store,’ says Microsoft.
Given the lukewarm reaction to compromised Windows 8, these seem like bold claims. They are probably necessary.
Also necessary is Microsoft’s decision to make Windows 10 the most beta-tested product it has ever released. Windows 10 Technical Preview will be available to everyone who wants to test it from today – October 1 2014. Given that we don’t expect it to launch until the middle of next year, that is a longer test period than we have previously seen. And the version of Windows that Microsoft is sharing is very far from the final code. Microsoft tells us to expect the Charms to change, for instance.
Critically the Start Menu contains standard Windows software and Windows Apps. Modern UI apps. So you can use those apps from within the Desktop area. Hopefully this removes some of the pointless division in Windows on X86 systems. It should also help Microsoft make good on its claim that Windows 10 will feel familiar to Windows 7 users. But we are a long way from that just now.
All of which means that this article is very far from a final Windows 10 review. More of a flavour of what to expect. As yet there is no music, IE or video to be found. We’re guessing that won’t be the case come launch in 2015. We brought you live coverage of the Windows 10 launch event, and our colleague Mark Hachman – he works for our sister title PCWorld.com – spent some time getting hands on with Windows 10 Technical Preview, and gave us detailed thoughts on some of the new features. We share some of them here with you in no particular order. You can get all the hard facts on Windows 10 in our article: Windows 10 release date, price, features. The next version of Windows will run on everything: smartphones, tablets, laptops and PCs.
Windows 10 review: search improvements
Personally I think that universal search in Windows 8 is a much-undervalued feature. Searching to load up apps and files is much more efficient than navigating via apps and file systems. And going by the Technical Preview Microsoft has made strides in this area.
Because, quite simply, Windows 10 sees a search button added to the taskbar. This in one important move one of the few important aspects of the Windows 8 Start page is pulled into the Desktop. Microsoft officials tell us that Search and File Explorer now displays your recent files and frequently visited folders. This should make finding files you’ve worked on faster and easier. It’s difficult to test this on a demo machine, but we look forward to trying it out on the Technical Preview just as soon as we can get it installed.
Windows 10 review: Snap Assist and windowed apps
With Snap Assist every app in Windows 10 can be dynamically resized in a window. And unlike in Windows 8 – where a snapped app takes up half the screen – with Windows 10 up to four apps can be snapped per screen. This has the potential to be a killer productivity app – true multitasking in a single window.
Even better, Snap a document to one side of the screen, and Snap Assist will suggest others that you may wish to open. Snap an app and Windows 10 suggests another, similar app that you might want to snap next to it. Mark was impressed with his brief test: “The feature is intended to save you the hassle of hunting about through menus to actually construct a virtual desktop. Time will tell whether these suggestions will prove useful, but it’s a good start.
“You can see, however, that a number of different features – Snap Assist, windowed apps, virtual desktops – all flow somewhat organically into one another. I’m honestly interested to see what difference they make in my own daily workflow.”
Windows 10 review: the all-new Start Menu
Now we get on to the big stuff. The Start Menu is back, back, back baby. But this time it is improved, and it may even make Windows apps useful. Look to the left and you’ll see a list of frequently used apps and shortcuts to PC settings. Here you will also find documents and pictures folders. At the bottom we see an ‘All apps’ shortcut.
And Microsoft has retained the functionality of the Windows 8 Start screen over on the right, with resizeable Live Tiles so that you can immediately check unread mail or Calender appointments. The Start Menu is customisable – you can resize it, and rearrange the tabs, You can also revert to the Windows 8 Start page, should you wish to. Who will wish to?
Mark wasn’t impressed with the Windows 10 Start Menu’s looks, but he can see the beauty within: “Aesthetically, it looks like someone surgically conjoined the Windows 7 and Windows 8 experience. Move past that inelegance, however, and it’s darn useful.”
Windows 10 review: Task View, virtual desktops, ALT-TAB
Another useful and visual productivity enhancer is the way that Task View allows you to create a kind of multi-monitor setup within a single monitor. As with previous versions of Windows you can use ALT-TAB to quickly shuffle between windows. The killer difference here is the new Task View button. Third from the left in the Windows Taskbar is the Task View button. Press it – or hit Windows TAB – and you will see an array of ‘virtual desktops’, virtual displays into which you can snap multiple apps. So you could keep your email and web browser on one Desktop that you hide away when you are working on an Excel spreadsheet.
Potentially a very useful feature.
Buying Advice
It is clearly much too early to give a verdict on Windows 10. We applaud Microsoft’s commitment to user-driven testing of Windows 10, and are excited about the possibility of fixing some of the problems with Windows 8 – particularly on the Desktop. We are a long way from being able to praise Windows 10, but the start is good. And, yes, that is in part because the Start Menu is good. You ca get an amazing discount for windows 10 product key at DigitBrew.com.
1 note
·
View note
Text
What is the best nvidia driver for gaming
Caesars Casino Gaming Weblog
On the web Gambling Web pages covers the whole business of gaming over the Net. Scump is experienced American Call of Duty player. He is a two time MLG X Games gold medalist and is sponsored by various gaming hardware providers, including Turtle Beach and Scuf Gaming. He is also sponsored by Loot Crate, Gymshark, and Brisk Mate. As of September 2016, Scump has won $262,293, of which almost $100,000 was won in Get in touch with of Duty: Advanced Warfare.
As you can see, gaming studios require to find their personal way to operate consumer service into the gaming knowledge. It indicates completely understanding their players, and that suggests understanding how to communicate player help in the most perfect fashion. Rovio, Nexon, and Riot are all great examples, but even when giving optimal player support is not so apparent, studios can do proper by their audience by staying rapid with their client service. The sooner the player gets the assist they will need, the more quickly they can get back into the game.
You have played thousands of unique board games, yes that is proper not hundreds, but thousands. You are a member of numerous gaming groups, and you've come to realise that diverse groups have various personalities and one of a kind dynamics. You recognize what style of games you take pleasure in and precise mechanics that you do and never like in a game. You don't actively preach or inform people about board games, but when asked you are an ambassador for the genre and with your vast expertise you can always add thoughtful discussion and predictions regarding games you are yet to play. Your collection is the great variety of games that you like. It is not simple for a new game to make it into your collection, and you have a defined a rigorous trial of fire that any game will have to meet to make it successfully into your collection.
Currently is the day! I will be progressively releasing the names of the major ten gaming blogs of 2014. Searching more than this list, I am positively blown away. So numerous great posts this year! If you have been disappointed by the Ennies… if you consider that the real deep thinkers in gaming commentary never get the consideration they deserve… nicely, folks, we are going to repair that.
Irrespective of whether you will need a thing to cool you down on a hot summer day or you merely want to assistance your gaming console cool down and preventing overheating your gear, the SIMBR Transportable USB Mini Desk Fan can be a very handy gift. Very first, its six-inch fan blades are drastically larger than other types of USB mini fans. Second, its highly effective motor is surprisingly quiet, generating less than 30 decibels of noise. Its one of a kind design enables the SIMBR to be rotated a complete 360 degrees, making sure you get optimum airflows wherever you point the desk fan to. The triangular base and metal frame are welcome attributes.
Operating as the evaluation editor for Destructoid and functioning as a gaming writer for Destructoid, Jim Sterling also runs a weekly video game series on Youtube. Sterling discusses quite a few of the unethical organization practices in gaming like gender inequality and early access games. The primary gameplay series that you will come across from Sterling is titled, Jimpressions,” and he covers subjects like new-release video games and covers the gameplay with his pre-recorded sessions.
The wonderful thing about the gaming niche is that video games are a hobby. This suggests that individuals will constantly devote additional cash to fund this hobby, no matter whether it be by way of new games, new gear, or both. You can capitalize on this by constructing an e-mail list, which will preserve these buyers acquiring from you again, expanding your income consistently. When one particular game gets old, merely send them out an e-mail and get started advertising the next one particular to them. When the subsequent fantastic headset comes out, send out an e mail. New CPA platform? Promote it! With an e-mail list, you can get these purchasers coming back to commit their income more than and over Mobile gaming blog again.
Gaming was when regarded a solitary past time, but this assumption is now a thing of the previous. These days, gamers share their hobby digitally with others from all around the globe. This requires spot through live Web sessions on Twitch and even the most well-liked of social media platforms nowadays. On social networking sites like YouTube, blogs and Instagram, influencer video game content dominates. There are now actually thousands of gaming influencers making content for social media platforms like YouTube and blogs. And the greatest and brightest of these influencers have huge followings. In truth, several of the top rated YouTubers in the world had been initially gaming influencers.
Like gaming? With the assist of a screen capture device (or a video camera) you can pass on your knowledge on a particular game (or level) and entertain persons at the same time. Video games as a spectator sport is a somewhat new phenomenon, but immensely preferred. Take Twitch, exactly where millions of gamers gather each month. Some gamers have even grow to be celebrities as a result.
PenNews is a modern day and clever responsive WordPress multiconcept news & magazine web-site theme. It is a potent platform for webmasters across the spectrum. Regardless of market or niche, PenNews has the demos and templates to make your life a lot easier. You do not will need to know any coding to function the WP Bakery like a pro. Awesome post types fit different stories, to usually deliver the message appropriate. Gaming magazines and news blogs are a great match for PenNews.
The Best Way To GAMING
A bustling neighborhood of excellent-minded folks, the game web page is greatest identified for producing original & fresh content related to newly & preferred gaming gears such as headsets, keyboards, laptops, mice, controllers, computers and a lot more. The game internet site is loaded with distinct sections that contain specialist reviews, previews, game trailers, cheat codes, discussion forums & video game news. One of the most popular game web-sites ever, VideoGamer has an intuitive interface & they also run their personal podcast as well.
With years of market-top QA practical experience behind us along with a team of gaming and domain specialists, we are properly-placed to serve the end-to-end and cross-platform gaming QA needs, which we meet through a complete service portfolio that consists of functional testing, localization testing, compatibility testing, and certification testing.
So you want to start off a gaming weblog? Very good for you! Gaming is a wonderful subject to write a weblog about, with a lot of men and women out there interested in this niche. No matter if you want to commence a weblog as a hobby or you're looking to make a bit of revenue from blogging, the following suggestions can assist you get started.
And this is exactly where cloud gaming has fallen down historically. In the previous, bandwidth just wasn't high sufficient to deliver responsive gameplay - but now, we're beginning to see web speeds that make cloud gaming a viable solution. 5G broadband is seen as a essential enabler, with a somewhat high quantity of users now in a position to take complete benefit of remotely hosted gaming solutions. That said, it's significant to note that higher-speed internet is far from widespread even in developed markets like the US, exactly where poor connectivity and bandwidth caps are still challenges for a lot of users.
If you are in the market for less costly or more very affordable games, make certain that you check the Hot Deals section of the internet site. Green Man Gaming consists of a link to that web page on all its pages. You can look at the Deal of the Day or at existing specials that let you save up to 75% off the MSRP on well-liked games. The Hot Deals section also consists of some VIP specials chosen by major games from around the globe.
1 note
·
View note
Text
What computer monitor is best for gaming
Why You Really should Start Your Gaming Blog On GameSkinny (Alternatively Of WordPress)
Enthusiast Gaming is a media and technologies organization building the biggest neighborhood of authentic gamers. Travel into a virtual world with a VR headset , exactly where all of your senses will be treated to a barrage of stimulus from numerous sources. With the Oculus Rift + Touch Virtual Reality Method , you'd have to prepare oneself for extra intense gameplays, more immersive action, and a completely new and exhilarating gaming present experience as the package currently comes with 6 VR games that will maintain your heart pumping by means of your chest. The Oculus Touch controllers are ingeniously developed for optimum and unparalleled interaction with the many components in the virtual globe. You will will need to meet certain system specifications on your laptop, though. This also makes a perfect gift for nerds in your life.
As you can see, gaming studios have to have to discover their own way to perform client service into the gaming expertise. It means fully understanding their players, and that means understanding how to communicate player help in the most perfect style. Rovio, Nexon, and Riot are all wonderful examples, but even when providing optimal player support is not so apparent, studios can do proper by their audience by staying quickly with their customer service. The sooner the player gets the support they require, the more quickly they can get back into the game.
You have played thousands of unique board games, yes that is ideal not hundreds, but thousands. You are a member of several gaming groups, and you have come to realise that distinct groups have unique personalities and unique dynamics. You realize what style of games you get pleasure from and precise mechanics that you do and don't like in a game. You never actively preach or tell persons about board games, but when asked you are an ambassador for the genre and with your vast expertise you can usually add thoughtful discussion and predictions with regards to games you are but to play. Your collection is the great variety of games that you like. It is not simple for a new game to make it into your collection, and you have a defined a rigorous trial of fire that any game must meet to make it successfully into your collection.
Nowadays is the day! I will be steadily releasing the names of the top rated ten gaming blogs of 2014. Searching more than this list, I am positively blown away. So quite a few amazing posts this year! If you had been disappointed by the Ennies… if you feel that the real deep thinkers in gaming commentary don't get the focus they deserve… well, folks, we are going to fix that.
When it comes to graphical intensity there actually is no comparison in between mobile gaming and Pc and console gaming. Even though handheld devices such as the Nintendo Switch offer a mobile alternative , it nevertheless doesn't pack enough punch to truly compete on an even field with the Computer and console market — and the average smartphone possesses even much less graphical energy. Although there have been massive advancements in mobile technologies, with new devices coming equipped with extra potent processors and RAM than ever just before, only Computer and consoles are in a position to deliver the power required for 4K imaging, the hottest new issue in gaming.
Operating as the assessment editor for Destructoid and working as a gaming writer for Destructoid, Jim Sterling also runs a weekly video game http://frantik.online series on Youtube. Sterling discusses lots of of the unethical organization practices in gaming like gender inequality and early access games. The main gameplay series that you will locate from Sterling is titled, Jimpressions,” and he covers topics like new-release video games and covers the gameplay with his pre-recorded sessions.
The wonderful factor about the gaming niche is that video games are a hobby. This indicates that folks will continuously spend extra cash to fund this hobby, irrespective of whether it be via new games, new equipment, or both. You can capitalize on this by building an e-mail list, which will keep these buyers purchasing from you once more, increasing your income regularly. When one particular game gets old, basically send them out an e mail and get started promoting the next a single to them. When the next fantastic headset comes out, send out an email. New CPA platform? Promote it! With an email list, you can get these purchasers coming back to commit their revenue more than and over once more.
The gaming labor marketplace is evolving like lots of industries impacted by the development of technologies. Jobs for game developer might be declining, but jobs in other gaming-associated fields are developing. This is reflective of the altering nature of video games and the gaming sector. The definition of video game and video game creator is totally distinctive. And the labor industry reflects this.
It is very crucial to have your own information hub no matter if you are an indie developer who tends to make the games or beginning a new eSports gaming league. It helps your fans and shoppers to find out much more about your group or enterprise perfectly. These days gaming is expanding day by day which has become the most profitable industries in the globe these days. A easy YouTube channel is sufficient for you to earn millions of dollars by merely streaming gaming videos. But having a web site will assist you to market and sell your official merchandise as nicely as be extra discoverable on the net.
Gaming consists of diverse genres and systems, and it is critical to know what type of gaming web site you would want to be. Gaming web pages consist of on the web magazines that focus on gaming-related articles, gaming portals, on the net retail and distribution, and gaming blogs. Gamers are specific with what content material they want to access, which means that defining what your web page is would make certain you get the appropriate audience.
To People That Need to Jump GAMING But Are Affraid To Get Started
A bustling community of great-minded persons, the game website is very best recognized for producing original & fresh content associated to newly & well known gaming gears such as headsets, keyboards, laptops, mice, controllers, computers and extra. The game web-site is loaded with different sections that include professional evaluations, previews, game trailers, cheat codes, discussion forums & video game news. A single of the most common game websites ever, VideoGamer has an intuitive interface & they also run their own podcast as effectively.
These historical cloud gaming services, while revolutionary, had been often somewhat niche. But will cloud gaming go mainstream any time quickly? Both Microsoft and Google have recently announced forays into the sector, with trials of Project xCloud” and Project Stream” respectively. Even Nintendo, a far much more standard gaming brand, has established some key cloud inroads on its platforms. Streamed versions of demanding games like Assassin's Creed Odyssey and Resident Evil 7 - originally developed for Xbox, PlayStation and Computer - are becoming accessible on the comparatively weak Nintendo Switch hardware. If the actions of the main players are anything to go by, gaming on demand could achieve critical traction more than the next decade.
So you want to commence a gaming weblog? Very good for you! Gaming is a terrific topic to write a blog about, with a lot of people out there interested in this niche. Whether you want to start out a blog as a hobby or you're hunting to make a bit of dollars from blogging, the following suggestions can support you get began.
And this is where cloud gaming has fallen down historically. In the past, bandwidth just wasn't higher enough to provide responsive gameplay - but now, we're starting to see web speeds that make cloud gaming a viable option. 5G broadband is noticed as a crucial enabler, with a reasonably higher quantity of users now in a position to take complete benefit of remotely hosted gaming solutions. That mentioned, it's essential to note that high-speed internet is far from widespread even in created markets like the US, exactly where poor connectivity and bandwidth caps are still problems for a lot of customers.
Alia Lia” Shelesh, far better identified as Sssniperwolf is the very first female gaming influencer on our list. She started her YouTube profession by playing first-individual shooter games like Get in touch with of Duty, Halo, and Far Cry. Her account today consists of vlogs and various video games that she plays and has far more than 7 million subscriptions.
1 note
·
View note
Text
Mac Os Mavericks App Store

The initial Mac App Store version of Mavericks will boot only those Macs released prior to Mavericks’s debut; Macs released after Mavericks’s debut ship with a newer version of OS X 10.9. Nov 01, 2013.
Mac Os Mavericks Download
Mac Os Mavericks Iso
5/5(52 votes )
If you looking on the internet a Niresh Mac OS X Mavericks DVD ISO So, you come to the right place now a day shares with you an amazing powerful features application Niresh Mavericks Mac OS Operating System to added 200 more cool features to improve the security and compatibility these features just like Gmail enhancements, Smart Mailboxes, VoiceOver features it’s really cool am personally enjoy this feature and finally you can send them to iPhone for recognition of your voice. Download Niresh Mac OSX Mavericks 10.9 DVD ISO free standalone offline setup for AMD and Intel Computers.
This Mac OS X release also offers better security features and numerous improvements to improve the operating system’s usability and compatibility. The iCloud keychain maintains passwords and credit card information and encrypts information to enhance security. Finder tabs, improved notifications and much more are available to make it a better system. The new version of the program is available for Windows download on Niresh Mac OS X Mavericks 10.9.0 DVD ISO online. This is a complete, stand-alone package for the 32-bit and 64-bit operating system from Niresh Mac OS X Mavericks 10.9.0 DVD ISO. This is a good software platform that provides the consumer with the best experience.
Niresh Mac OSX Mavericks 10.9 OverView:
In this version of the Calendar app, you can manage your time very easily with a new look and a few very impressive features. It has a brand new event inspector that has made the creation of an event easier. The travel time can be calculated easily and the weather forecast can display. You can start the iBooks app from your Mac in this version. iBooks have over 2 million books under your fingertips now. The iCloud Keychain, which can remember and save your passwords, is another impressive feature. Besides storing passwords, you can also automatically enter your username and password by selecting it.
Mavericks Zone offers a stable and reliable system with Mac OS X Mavericks 10.9 updates with several corrections and improvements. It includes improved stability and compatibility to improve operating system performance. The users can have complete control over the operating system with a simple and familiar user interface. It is also a very lightweight operating system that offers improved safety and the highest performance levels.
This powerful OS also offers Gmail in OS X Mail, various corrections with Gmail settings, search improvements for mailboxes and contact fixes in the mail. In addition, this operating system also provides VoiceOver solutions to prevent emoji phrases from being spoken. Shared Links upgrades are automatically made a stable and better operating system by numerous other potent features. In brief, Niresh Mac OSX Mavericks 10.9 has been released in a stable way with numerous improvements and new features. you can also check out the Samsung Smart Switch for Mac.
Features Of Niresh Mac OSX Mavericks 10.9
Take the whole world on your desktop.
It can be installed on any AMD and Intel
Can look up for different directions easily.
Improved calendar application.
Got Event inspector to create an event easily.
Can easily create your travel time.
Can launch iBooks app from your Mac.
iCloud Keychain included for remembering your passwords.
Can make and receive FacTime audio calls.
AMD Processor Support
Protect user’s password through cloud keychain.
A user-friendly app is simple to use.
This app is compatible with Intel and AMD.
The user can navigate or search options through finder tab.
Have updated and latest calendar.
A lightweight tool for the system.
It can manage events and set a reminder.
This also helps to make audio calls.
A highly customizable app so the user can manage easily.
Provide a feature of iBook app so give access to millions of books.
It also supports shared links simply.
An app with cool and intuitive interface
A quick and fast app to operate the system.
The user can hide or show the taskbar.
Also, provide a wonderful feature of voiceover fixing.
A stable and reliable tool with high performance.
Now user can control their device easily.
Easy to install and straight forward app.
Provide updates with new features.
Standalone Installer
MBR Patch
Trim Patch
RTC Patch
Auto-Install Audio Kexts
Auto-Install Network Kexts
Standalone Installer Can be used with MacBook, iMac, and MacPro.
Many Intel HD Graphics Support (choose SMBIOS of MacBook Pro)
Powerful Mac OS X release with different security enhancements
VoiceOver, Smart Mailboxes, Shared Links and different other improvements
Supports multiple displays and the users can connect and use multiple screens
iCloud Keychain protects the passwords and the credit cards information protected
Notifications, Finder Tab, and different other enhancements
Much More…………/
Niresh Mac OS X Mavericks Technical Setup Details
Software Full Name: Niresh Mavericks
Setup File Name: OSX_Mavericks.iso
Full Setup Size: 5 GB
Setup Type: Offline Installer / Full Standalone Setup
Latest Version Release Added On: 28th Mar 2019
System Requirements For Niresh Mac OS X Mavericks
Operating System: Mac OS X 10.9 or later.
Machine: Apple Macbook
Memory (RAM): 1 GB of RAM required.
Hard Disk Space: 3 GB of free space required.
Processor: Intel Dual Core processor or later.
Download Free Niresh Mavericks 10.9.0 Mac OS X DVD ISO
Check out the best Mac OS X Mavericks apps including the best productivity, game, life, finance, and music apps providing best Mac experience.
Mac Os Mavericks Download
Apple Mac OS X Mavericks is here making the Mac experience even better and bigger. With Mavericks update you can bring apps right on your desktop and add features that you love the most.

Best Mac OS X Mavericks Apps
There are hundreds and thousands of apps available at App Store and OS X owners can easily get confused which is the best among those. For that reasons, we have come up with list of 101 best Mac OS X Mavericks apps. We have listed out the best productivity apps for Mavericks OS, best Mavericks OS games and best Mavericks Finance or music apps.
Best Mac OS X Mavericks Productivity Apps
For those who are looking to gain productivity outputs on Mac OS laptops, here are the best Mac OS X Maverick Productivity Apps –
Wunderlist: Allows you to manage your to do list across all the Apple products.
Scrivener: Save your text, copy or document as it happens, no matter how long or short it is.
Cobook Contacts: Keep your Apple iPhone, iPad contacts updated and organised using Cobook Contacts.
Things:Things Apps for Mavericks OS allows you to keep a track on things to do easily.
OmiFocus: Stay on top of things that you do in your life.
AutoCad WS Allows you to share DWG and DXG documents easily real time.
Evernote: Taking notes on your laptop is never easy and sync to cloud.
Best Mac OS X Mavericks Lifestyle Apps
JCPenney
Bling My Screen
Best Mac OS X Mavericks Games
Gaming is the best way to timepass and have fun. Here are the best Mac OS X Mavericks Games that you can play in your free time –
Temple Run OZ
Monopoly
Civilization V
Grid

Best Mac OS X Mavericks Entertainment Apps
Netflix
Bitstrips
LIE DETECTOR… FREE!
Best Mac OS X Mavericks Finance Apps
Looking for Finance tips right on your Macbook and other Mac OS laptops, here are the best Mac OS X Mavericks Finance Apps –
Yahoo! Finance
Best Mac OS X Mavericks Music Apps
Find your choice of best Mac Mavericks music app –
YStream – Youtube edition
Mac Os Mavericks Iso
This post was last modified on April 2, 2018 6:21 PM

1 note
·
View note