#Asynchronous Transfer Mode
Explore tagged Tumblr posts
Text
Subnet Sunday: ATM Networks - High-Speed Data Transfer Made Possible
🌐🚀💨 Welcome to Subnet Sunday, where we unravel the wonders of ATM (Asynchronous Transfer Mode) networks. In this post, we’ll dive into the world of high-speed data transfer, making it easy for non-tech enthusiasts to understand. Think of ATM networks as futuristic pneumatic tubes, where data packets zoom through at lightning speed, delivering information faster than you can blink. So, let’s…

View On WordPress
#Asynchronous Transfer Mode#ATM networks#cell switching#high-speed data transfer#reliability#scalability#speed#virtual circuits
0 notes
Text
Mikrotik Cirebon, IT Solution Cirebon, Jaringan Komputer Cirebon
0 notes
Text
IEEE Transactions on Fuzzy Systems, Volume 32, Issue 12, December 2024
1) A Bayesian Framework for Modelling the Trust Relationships to Group Decision Making Problems
Author(s): Xianchao Dai, Hao Li, Ligang Zhou, Qun Wu, Weiping Ding, Muhammet Deveci
Pages: 6594 - 6606
2) Adaptive Memory Event-Triggered Output Feedback Finite-Time Lane-Keeping Control for Autonomous Heavy Truck With Roll Prevention
Author(s): Fei Ding, Kaicheng Zhu, Jie Liu, Chen Peng, Yafei Wang, Junguo Lu
Pages: 6607 - 6621
3) Adaptive Fuzzy Position and Force Control for Cooperative Multimanipulators With System Uncertainties and Input Dead-Zone Nonlinearities
Author(s): Xing Li, Junxuan Luo, Shaoyu Li, Fujie Wang
Pages: 6622 - 6632
4) VMCFDGS: Variable Multicenter Aggregation Clustering Method Based on Fuzzy Dominating (Dominated)-Granularity Structure
Author(s): Bin Yu, Ruihui Xu
Pages: 6633 - 6645
5) Toward Sensor Fault Detection for Autonomous Underwater Vehicles: A Zonotopic Approach
Author(s): Jitao Li, Yushi Zhang, Zhenhua Wang, Jianbin Qiu, Mingjun Zhang
Pages: 6646 - 6657
6) Mixed Fuzzy Intermittent Control for Nonlinear ODE-PDE Coupled Systems
Author(s): Zi-Peng Wang, Hua-Ran Su, Xi-Dong Shi, Junfei Qiao, Huai-Ning Wu, Tingwen Huang, Xue-Hua Yan
Pages: 6658 - 6670
7) Explain the World—Using Causality to Facilitate Better Rules for Fuzzy Systems
Author(s): Te Zhang, Christian Wagner, Jonathan M. Garibaldi
Pages: 6671 - 6683
8) HPPD-Type Fuzzy State-FDI Estimation and Resilient Control of Cyber-Physical DC Microgrids With Hybrid Attacks
Author(s): Fuyi Yang, Xiangpeng Xie, Yan-Wu Wang, Reinaldo Martínez Palhares
Pages: 6684 - 6694
9) Asynchronously Switched Control With Variable Convergence Rate for Switched Nonlinear Systems: A Persistent Dwell-Time Scheme
Author(s): Han Geng, Huasheng Zhang, Shun-Feng Su
Pages: 6695 - 6707
10) Federated Fuzzy Transfer Learning With Domain and Category Shifts
Author(s): Keqiuyin Li, Jie Lu, Hua Zuo, Guangquan Zhang
Pages: 6708 - 6719
11) Multicontext Fuzzy Clustering: Toward Interpretable Fuzzy Clustering
Author(s): Majed Alateeq, Witold Pedrycz
Pages: 6720 - 6730
12) Predefined-Time Event-Triggered Adaptive Fuzzy Formation Control for Nonholonomic Multirobot Systems
Author(s): Kewen Li, Shijie Dong
Pages: 6731 - 6743
13) Unsupervised Deep Embedding for Fuzzy Clustering
Author(s): Runxin Zhang, Yu Duan, Feiping Nie, Rong Wang, Xuelong Li
Pages: 6744 - 6753
14) Consensus Control of Nonlinear Fractional-Order Multiagent Systems With Input Saturation: A T–S Fuzzy Method
Author(s): Yilin Hao, Zhiming Fang, Jinde Cao, Heng Liu
Pages: 6754 - 6766
15) Efficient Monotonicity and Convexity Checks for Randomly Sampled Fuzzy Measures
Author(s): Gleb Beliakov, Simon James, Jian-Zhang Wu
Pages: 6767 - 6774
16) A Fuzzy Neural Network Approach to Adaptive Robust Nonsingular Sliding Mode Control for Predefined-Time Tracking of a Quadrotor
Author(s): Yongjun He, Lin Xiao, Zidong Wang, Qiuyue Zuo, Linju Li
Pages: 6775 - 6788
17) Distributed Prescribed-Time Formation Control of Heterogeneous T–S Fuzzy Multiagent Systems: A Hierarchical Design Approach
Author(s): Yongran Zhi, Lei Liu, Huijin Fan, Bo Wang
Pages: 6789 - 6800
18) A Granular Aggregation of Multifaceted Gaussian Process Models
Author(s): Lan Yang, Xiubin Zhu, Witold Pedrycz, Zhiwu Li, Xingchen Hu
Pages: 6801 - 6810
19) Adaptive Fuzzy Triggered Output Feedback Control of Nonlinear Systems via Compulsory-Event
Author(s): Xu Yuan, Bin Yang, Xudong Zhao
Pages: 6811 - 6821
20) GFS-Node: Graph Fuzzy Systems for Node Prediction
Author(s): Fuping Hu, Zhaohong Deng, Zhenping Xie, Te Zhang, Kup-Sze Choi, Fan Zhang, Shitong Wang
Pages: 6822 - 6834
21) Feature Weighting-Based Deep Fuzzy C-Means for Clustering Incomplete Time Series
Author(s): Yurui Li, Mingjing Du, Wenbin Zhang, Xiang Jiang, Yongquan Dong
Pages: 6835 - 6847
22) Observer-Based Fuzzy PID Control for Nonlinear Systems With Degraded Measurements: Dealing With Randomly Perturbed Sampling Periods
Author(s): Yezheng Wang, Zidong Wang, Lei Zou, Quanbo Ge, Hongli Dong
Pages: 6848 - 6862
23) Boundary Output Tracking of Nonlinear Parabolic Differential Systems via Fuzzy PID Control
Author(s): Jin-Feng Zhang, Jun-Wei Wang, Hak-Keung Lam, Han-Xiong Li
Pages: 6863 - 6877
24) Principal Component Analysis With Fuzzy Elastic Net for Feature Selection
Author(s): Yunlong Gao, Qinting Wu, Zhenghong Xu, Chao Cao, Jinyan Pan, Guifang Shao, Feiping Nie, Qingyuan Zhu
Pages: 6878 - 6890
25) Predefined-Time Composite Adaptive Fuzzy Nonsingular Attitude Control for Multi-UAVs
Author(s): Huanqing Wang, Muxuan Li, Huaguang Zhang, Siwen Liu
Pages: 6891 - 6903
26) Dynamic Event-Triggered Fuzzy Optimal Consensus Control for Stochastic Multiagent Systems Under Switching Topology
Author(s): Ying Xu, Kewen Li, Yongming Li
Pages: 6904 - 6916
27) Intermittent Fixed-Time Fuzzy Consensus of Nonlinear Multiagent Systems With Unknown Control Directions and Event-Based Communication
Author(s): Jian Liu, Zheng Lian, Jinglong Shi, Lu Dong, Changyin Sun
Pages: 6917 - 6928
28) Nash Equilibrium Seeking in Nonzero-Sum Games: A Prescribed-Time Fuzzy Control Approach
Author(s): Yan Zhang, Mohammed Chadli, Zhengrong Xiang
Pages: 6929 - 6938
29) T–S Fuzzy-Based Load Frequency Control of Multiarea Power System With Hybrid Delays: Performance Analysis and Improvement
Author(s): Zhe-Li Yuan, Chuan-Ke Zhang, Xing-Chen Shangguan, Yu-Long Fan, Yong He
Pages: 6939 - 6950
30) Toward Embedding Ambiguity-Sensitive Graph Neural Network Explainability
Author(s): Xiaofeng Liu, Yinglong Ma, Degang Chen, Ling Liu
Pages: 6951 - 6964
31) Multiview Fuzzy Concept-Cognitive Learning With High-Order Information Fusion of Fuzzy Attributes
Author(s): Jinbo Wang, Weihua Xu, Weiping Ding, Yuhua Qian
Pages: 6965 - 6978
32) Bipartite Synchronization of Fractional-Order T–S Fuzzy Signed Networks via Event-Triggered Intermittent Control
Author(s): Yao Xu, Zhuozhen Jiang, Xiangpeng Xie, Wenxue Li, Yongbao Wu, Reinaldo Martínez Palhares
Pages: 6979 - 6989
33) A Predefined Time Fuzzy Neural Solution With Event-Triggered Mechanism to Kinematic Planning of Manipulator With Physical Constraints
Author(s): Ying Kong, Xuxiang Zeng, Yunliang Jiang, Danfeng Sun
Pages: 6990 - 7001
34) Weakly Supervised Causal Discovery Based on Fuzzy Knowledge and Complex Data Complementarity
Author(s): Wenrui Li, Wei Zhang, Qinghao Zhang, Xuegong Zhang, Xiaowo Wang
Pages: 7002 - 7014
35) Adversarial Attack Detection via Fuzzy Predictions
Author(s): Yi Li, Plamen Angelov, Neeraj Suri
Pages: 7015 - 7024
36) Averaging Functions on Triangular Fuzzy Numbers and an Application in Graphs
Author(s): Nicolás Zumelzu, Roberto Díaz, Aldryn Aparcana, José Canumán, Álvaro Mella, Edmundo Mansilla, Diego Soto, Benjamín Bedregal
Pages: 7025 - 7036
37) Design Trend Fuzzy Granulation-Based Three-Layer Fuzzy Cognitive Map for Long-Term Forecasting of Multivariate Time Series
Author(s): Fei Yang, Fusheng Yu, Chenxi Ouyang, Yuqing Tang
Pages: 7037 - 7049
38) Adaptive Fuzzy Safety Control of Hypersonic Flight Vehicles Pursuing Adaptable Prescribed Behaviors: A Sensing and Adjustment Mechanism
Author(s): Xiangwei Bu, Ruining Luo, Maolong Lv, Humin Lei
Pages: 7050 - 7062
39) Dynamic Guaranteed Cost Event-Triggered-Based Anti-Disturbance Control of T-S Fuzzy Wind-Turbine Systems Subject to External Disturbances
Author(s): Yang Gu, Mouquan Shen, Ju H. Park, Qing-Guo Wang, Zheng Hong Zhu
Pages: 7063 - 7072
40) Fuzzy Adaptive Bipartite Consensus of Stochastic Multiagent Systems: A Singularity-Free Prescribed Performance Control Approach
Author(s): Lei Chen, Hongjing Liang, Yuhua Cheng, Tingwen Huang
Pages: 7073 - 7085
41) A New Family of Metrics in Interval Space and Their Applications to Multicriteria Decision-Making Theory
Author(s): Y. Chalco-Cano, T. M. Costa, Benjamín Bedregal, Ademir G. Chalco Cano
Pages: 7086 - 7095
42) FGRBC: A Novel Fuzzy Granular Rule-Based Classifier Using the Justifiable Granularity Principle and a Fusion Strategy
Author(s): Xiao Zhang, Yijing Liu, Jinhai Li, Changlin Mei
Pages: 7096 - 7108
43) Observer-Based Sliding Mode Control for Stochastic Sampling Fuzzy Systems With Stochastic Communication Protocol
Author(s): Junhui Wu, Jun Cheng, Huaicheng Yan, Leszek Rutkowski, Jinde Cao
Pages: 7109 - 7117
44) Dynamic Event-Based Hierarchical Fuzzy Prescribed Performance Control for Underactuated Systems With Uncertain Dead Zone
Author(s): Yi Shui, Lu Dong, Ya Zhang, Changyin Sun
Pages: 7118 - 7128
45) Long-Term Interpretable Air Quality Trend Forecasting via Directed Interval Fuzzy Cognitive Maps
Author(s): Xiaoqian Liu, Yingjun Zhang, Hui Wang, Sipei Qin, Zhenhua Zhang, Yanyan Yang, Jingping Wang
Pages: 7129 - 7142
46) Higher Order Fuzzy Membership in Motif Modularity Optimization
Author(s): Jing Xiao, Ya-Wei Wei, Jing Cao, Xiao-Ke Xu
Pages: 7143 - 7156
47) Membership Function-Dependent H∞ Control for Set-Described T-S Fuzzy System via Improved Dynamic Memory Event-Triggered Mechanism
Author(s): Qinghua Hou, Jiuxiang Dong
Pages: 7157 - 7167
48) A Cross-Field Deep Learning-Based Fuzzy Spamming Detection Approach via Collaboration of Behavior Modeling and Sentiment Analysis
Author(s): Keping Yu, Xiaogang Zhu, Zhiwei Guo, Amr Tolba, Joel J. P. C. Rodrigues, Victor C.M. Leung
Pages: 7168 - 7182
49) Adaptive Type-2 Fuzzy Filter With Kernel Density Estimation for Impulse Noise Removal
Author(s): Vikas Singh, Alankrita, Vipin Chandra Pal, Avadh Pati
Pages: 7183 - 7189
50) Fuzzy Formation Control for Nonlinear Multiagent Systems With Two Time Scales: A Reinforcement Learning Scheme
Author(s): Qing Yang, Jing Wang, Hao Shen, Ju H. Park
Pages: 7190 - 7195
51) A Novel Unsupervised Capacity Identification Approach to Deal With Redundant Criteria in Multicriteria Decision Making Problems
Author(s): Guilherme Dean Pelegrina, Leonardo Tomazeli Duarte
Pages: 7196 - 7201
0 notes
Text
DAC0832 Digital-to-Analog Converter
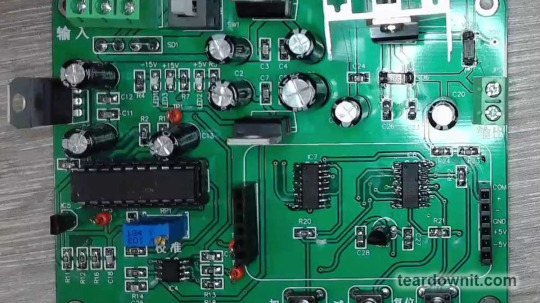
Digital-to-analog converters (DACs) are often built into microcontrollers but tend to be slow, noisy, and lack resolution. So, we frequently use specialized DAC chips.
Today's example is a digitally controlled voltage regulator module that could be used in a lab power supply. The workhorse here is the LM317T chip, which has the DAC0832 digital-to-analog converter at its core.
The DAC0832 is a pretty advanced chip, with not one but two latches arranged in sequence. This setup allows it to store digital data from the microprocessor bus and convert it to an analog value at just the right moment.
In the post about the 74HC374 latch, we used it to freeze the readings on seven-segment displays for a second while counting input pulses.
After a second, the data from the counters was sent out to the display decoders, showing the frequency of the input signal measured a second earlier. Meanwhile, the next count of pulses was happening. This made for a good frequency counter.
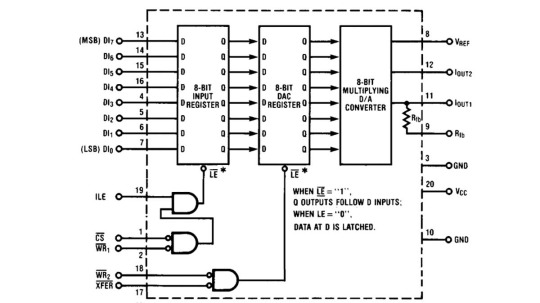
Each of the two latches in the DAC0832 can be made transparent, meaning asynchronous. In this mode, data from the input instantly appears in the output.

A logic high on the ¬LE (¬LATCH ENABLE) pin is needed to set the input latch to transparent asynchronous mode. You could call it LATCH DISABLE without the ¬ sign.
¬LE = ILE & (¬¬CS & ¬¬WR1) = ILE & ¬(¬CS | ¬WR1).
In simpler terms, you need a logic high on the ILE (INPUT LATCH ENABLE) input and a logic low on at least one of the two inputs, ¬CS (¬CHIP SELECT) or ¬WR1 (¬WRITE1). The ¬WRITE1 and ¬WRITE2 inputs are used for strobe signals.
For the 8-bit DAC latch register, the logic for ¬LATCH ENABLE is more straightforward:
¬LE = ¬¬XFER & ¬¬WR2 = ¬(¬XFER | ¬WR2).
So, you need a low logic level on at least one of the inputs: ¬XFER (¬TRANSFER) or ¬WR2 (¬WRITE2).
The heart of the DAC0832 is the analog-to-digital converter. This analog multiplexer switches precision silicon-chromium resistors deposited on a silicon chip.
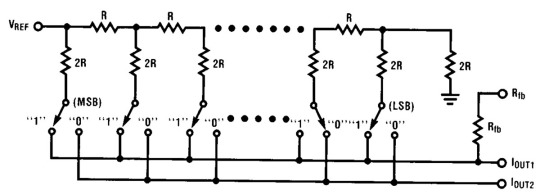
This manufacturing technique ensures high accuracy and temperature stability, which is why we use DAC chips in our favorite high-fidelity audio gear.
Plus, a multiplexer can work much faster than pulse-width modulation (PWM) analog-to-digital conversion, which we often use in Arduino DIY projects.
Also, PWM produces square pulses with different duty cycles with a broad frequency spectrum. The frequencies might be inaudible, but their interference with other frequencies in the device can create audible noises, which can be pretty unpleasant.
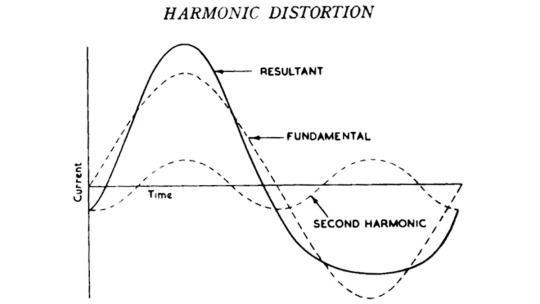
The homemade tube amplifier article mentioned that asymmetrical and softly clipped waveforms sound pleasant and musical to human ears because they're full of even harmonics.

But a square, symmetrical waveform has many odd harmonics, which aren't so nice to listen to, especially when they create dissonance with the overtones of other sounds played at the same time.
The DAC0832 needs an external operational amplifier to convert the current through switched precision resistors into an output voltage.
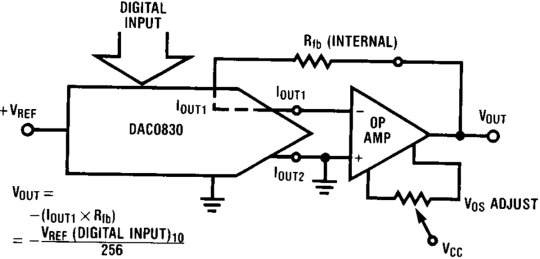
We'd probably go with the NE5532 for audio output, which we used for a simple, affordable, and high-quality headphone amp.

But the good old LM358 will do fine for a power supply. Here, op-amp IC4A converts the output current of the DAC0832 into voltage, and IC4B amplifies the resulting signal by six times.
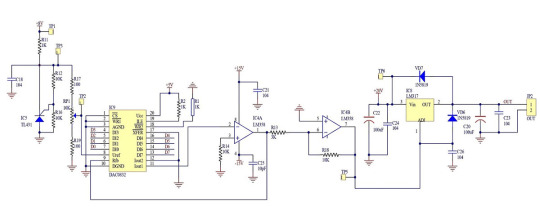
The TL431 chip generates the DAC0832's reference voltage, which is adjusted with the potentiometer RP1. The voltage ranges from 5×1100/1200=0.42V to 4.58V.
The output of IC4B is connected to the adjustment input of the LM317. Therefore, this chip's output voltage, and therefore our homemade power supply's, will be 1.25 volts higher than IC4B's.
So, the output voltage formula is:
Vout = 1.25 + 6 * Vref * DIGITAL INPUT / 256 = 1.25 + 0.024 * Vref * DIGITAL INPUT.
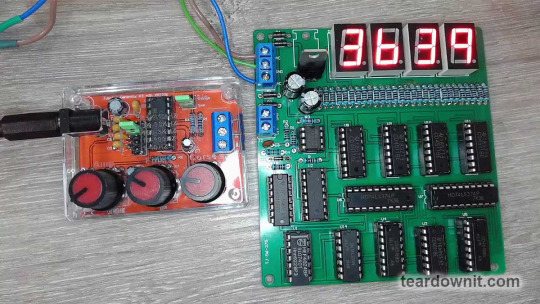
Adjusting the reference voltage can change the increment and decrement steps when pressing the corresponding buttons on the power supply's front panel.
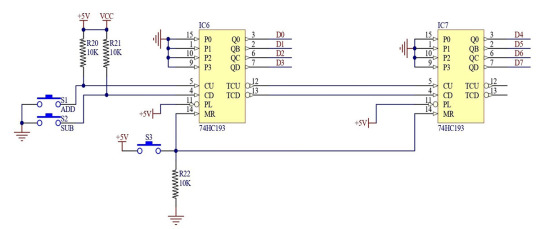
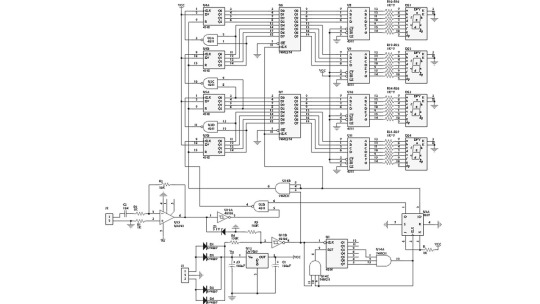
The digital value for converting to a voltage is set by two 74HC193 four-bit up/down counters.

These are presettable counters, similar to the ones we used as registers in our DIY 4-bit CPU.
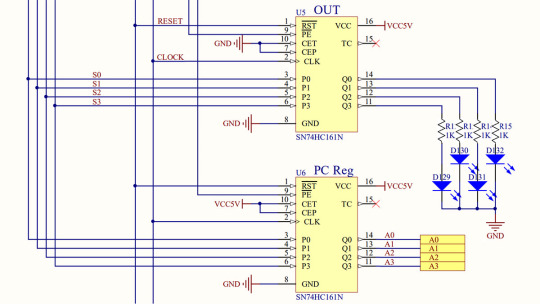
Each CPU's four registers used one SN74HC161L chip as a latch. The increment function was only used in the program counter (PC) register. The other three registers disabled it by grounding the CEP and CET control inputs.
We used the decrement function in a countdown timer that could be set to any number of seconds from 0 to 99.

Thanks to the preset function, the chosen value from the PRESET ROM of our electronic traffic light tells the second counter how long the current signal combination should last. The decrement function was also used there.
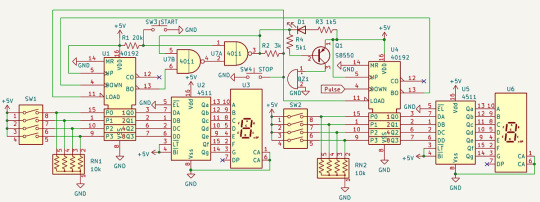
In today's power supply, we do not use the preset function but both increment and decrement counting. There's also a reset button to set both counters to zero.

Accordingly, the digital-to-analog converter will also be set to zero since both of its internal latches are permanently in transparent asynchronous mode.
To lock the chip in this mode, the ¬CS, ¬WR1, ¬WR2, and ¬XFER control inputs are soldered to ground.

We could make a power supply with non-volatile preset memory if we used a microcontroller instead of up/down counters. The microcontroller's analog-to-digital converter could be used for the voltmeter and ammeter.
And if the microcontroller doesn't have enough pins to connect the 8-bit DAC data bus, we could use a shift register for serial data transfer.
In this case, the DAC0832's latch registers could be very handy if the shift register doesn't have a built-in latch.
After all, to convert a binary number into a voltage, you must wait until the binary number is fully received from the microcontroller via the serial bus. Otherwise, you’d get meaningless voltage jumps, which are unacceptable in a power supply.
0 notes
Text
Career Online Counselling: Navigate Your Career Choices
Have you ever found yourself at a crossroads in your career, wondering which path to take? It’s a situation many of us encounter, whether we’re just starting out, looking to make a significant change, or aiming to advance in our current field. Navigating these career choices can be daunting, but there’s a powerful tool that can make this journey smoother and more manageable: career online counselling. In this comprehensive guide, we’ll explore how online career counselling can help you make informed decisions and navigate your career path with confidence.

Understanding Career Online Counselling
Definition and Concept
Career online counselling is a modern approach to career guidance that leverages digital technology to provide support and advice. Unlike traditional face-to-face counselling, online career counselling allows you to connect with a professional career counsellor through various digital platforms such as video calls, text chats, and emails. This method offers flexibility and convenience, making it easier for you to access expert guidance without needing to travel.
Modes of Online Career Counselling
Career online counselling comes in several forms, each catering to different preferences and needs:
Video Conferencing: This real-time interaction allows you to have face-to-face conversations with your counsellor through platforms like Zoom or Microsoft Teams. It’s ideal for those who prefer personal interaction and visual communication.
Text Chat: If you’re more comfortable with written communication, text chat counselling provides a platform for instant messaging. This method is convenient if you prefer to think through your responses before sending them.
Email Counselling: For those who prefer asynchronous communication, email counselling allows you to send detailed messages and receive thoughtful responses at your own pace. This can be especially useful for in-depth discussions.
Hybrid Approaches: Some online counselling services offer a combination of these methods, allowing you to choose the most suitable mode based on your needs and preferences.
How Online Career Counselling Works
The process of career online counselling generally involves several steps:
Initial Contact: You start by reaching out to a career counsellor or service to discuss your needs and goals. This initial interaction helps set the stage for your counselling sessions.
Assessment: The counsellor may conduct an initial assessment to understand your career background, skills, interests, and aspirations. This might involve taking various assessments or surveys.
Counselling Sessions: You engage in sessions where you discuss your career goals, challenges, and receive personalized advice. These sessions are designed to help you gain clarity and develop a plan of action.
Action Plan: Based on the insights gained from your sessions, you work together to create a detailed action plan with specific steps to achieve your career objectives.
Follow-Up: Regular follow-up sessions are crucial to track your progress, address any new challenges, and adjust your action plan as needed.
Benefits of Online Career Counselling
Flexibility and Accessibility
One of the most significant advantages of online career counselling is its flexibility. You can schedule sessions at times that work best for you, without the need to travel to a physical office. Whether you’re at home, at work, or traveling, you can connect with your counsellor from anywhere with an internet connection. This convenience makes it easier to fit counselling into your busy life.
Personalized Guidance
Online career counselling offers a high level of personalization. Your counsellor tailors their advice to your unique needs, goals, and career situation. For instance, if you’re considering a career change, your counsellor can provide specific strategies to help you transition smoothly, identify transferable skills, and explore new opportunities that align with your interests.
Cost-Effectiveness
In many cases, online career counselling can be more cost-effective compared to traditional in-person sessions. You save on travel costs and time, and many online services offer competitive pricing. Additionally, online platforms often provide various packages, allowing you to choose one that fits your budget while still receiving quality support.
Comfort and Confidentiality
Discussing career issues can sometimes feel uncomfortable, especially if you’re dealing with sensitive topics. Online counselling provides a private and secure environment where you can openly share your concerns. Being in a familiar setting, such as your home, can help you feel more at ease and facilitate honest and effective communication.
Key Features of Effective Online Career Counselling
Experienced and Qualified Counsellors
The effectiveness of online career counselling hinges on the expertise of the counsellor. It’s essential to choose a professional with relevant qualifications and experience. Look for counsellors who hold certifications in career guidance and have a proven track record of helping clients achieve their career goals. A well-qualified counsellor brings valuable insights and strategies to the table, enhancing the quality of the guidance you receive.
Comprehensive Assessments
Effective online career counselling involves comprehensive assessments to understand your career needs thoroughly. These assessments might include personality tests, skills evaluations, and career interest surveys. They provide valuable insights into your strengths, preferences, and areas for development, guiding the counsellor in offering tailored advice and support.
Setting Goals and Creating Action Plans
One of the critical aspects of online career counselling is setting clear, achievable goals. Your counsellor will work with you to define your career objectives and create a step-by-step action plan. This plan outlines specific actions you need to take to reach your goals, such as updating your resume, applying for jobs, or pursuing additional training. An actionable plan helps you stay focused and motivated as you work towards your career aspirations.
Ongoing Support and Feedback
Career development is a continuous process, and effective online career counselling includes regular follow-up sessions to monitor your progress. These sessions allow you to discuss any new challenges, adjust your action plan, and receive ongoing support. Continuous feedback ensures that you stay on track and make the necessary adjustments to achieve your career goals.
Choosing the Right Online Career Counselling Service
Research and Reviews
When selecting an online career counselling service, thorough research is crucial. Start by reading reviews and testimonials from other clients to gauge the effectiveness of the service. Look for feedback on the counsellors’ professionalism, the quality of advice, and the overall client experience. Positive reviews and high ratings are good indicators of a reliable and effective service.
Counsellor’s Expertise and Specializations
Ensure that the counsellor’s expertise aligns with your specific career needs. For example, if you’re looking to transition to a new industry, find a counsellor with experience in that field. Verify their qualifications and professional background to ensure you’re receiving high-quality guidance. A counsellor with relevant experience can offer valuable insights and strategies tailored to your situation.
Service Offerings and Pricing
Compare the services offered by different online counselling platforms. Some may provide a comprehensive range of services, including resume writing, interview coaching, and job search strategies. Check the pricing structures and packages to find one that fits your budget and includes the services you need. Transparent pricing and a clear breakdown of what’s included in each package can help you make an informed decision.
Trial Sessions and Consultations
Many online career counselling services offer free trial sessions or initial consultations. Take advantage of these opportunities to assess the counsellor’s approach and determine if it’s a good fit for you. Use the trial session to ask questions about their methods, experience, and how they can help you achieve your career goals. A trial session provides a glimpse into the counselling experience and helps you decide if it meets your needs.
Success Stories and Testimonials
Real-Life Examples
One of the best ways to understand the impact of online career counselling is through real-life success stories. For instance, consider the story of Alex, who used online career counselling to transition from a career in finance to a role in environmental science. With the counsellor’s guidance, Alex identified transferable skills, updated his resume, and successfully landed a position that aligned with his passion for sustainability.
Impact on Career Decisions
Success stories like Alex’s illustrate the tangible benefits of online career counselling. Whether you’re looking to advance in your current role, switch to a new career, or explore your options, online counselling can provide the support and direction you need to make informed decisions. Personalized advice and continuous support from a skilled counsellor can lead to significant career growth and success.
Navigating your career choices can be a complex and challenging process, but career online counselling provides a valuable resource to help you make informed decisions and achieve your goals. With its flexibility, personalized guidance, and cost-effectiveness, online counselling offers a modern solution to career development.
If you’re ready to explore your career options and take control of your future, consider our online career counselling services. We offer expert guidance to help you navigate your career path, whether you’re looking to advance in your current role, make a career change, or prepare for study abroad and entrance exams.
Embrace the opportunities that online career counselling provides and take the next step towards your dream career. Your career journey is unique, and with the right support, you can navigate it with confidence and success. Contact us today to get started and discover how our services can help you achieve your career goals.
0 notes
Text
what is layer 2 vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is layer 2 vpn
Layer 2 VPN Definition
Layer 2 VPN, short for Layer 2 Virtual Private Network, is a networking technology that enables the creation of a private and secure communication channel over a public network infrastructure. In the context of networking, the term "layer 2" refers to the data link layer of the OSI (Open Systems Interconnection) model, which is responsible for the reliable transfer of data between adjacent network nodes.
A Layer 2 VPN operates by establishing virtual connections, or tunnels, between different locations or endpoints, allowing them to communicate as if they were directly connected to the same physical network. Unlike Layer 3 VPNs, which operate at the network layer and rely on IP routing, Layer 2 VPNs operate at the data link layer and maintain the original MAC (Media Access Control) addresses of the devices involved in the communication.
One of the key advantages of Layer 2 VPNs is their ability to support a wide range of networking protocols and services, including Ethernet, Frame Relay, and ATM (Asynchronous Transfer Mode). This flexibility makes Layer 2 VPNs well-suited for scenarios where maintaining the existing network infrastructure and preserving the native protocol characteristics are important considerations.
Layer 2 VPNs are commonly used by businesses to connect geographically dispersed office locations or to extend their private networks to remote users or branch offices securely. Service providers also offer Layer 2 VPN services as part of their portfolio to meet the connectivity needs of enterprise customers.
In summary, Layer 2 VPNs provide a versatile and secure means of establishing private network connections over public infrastructure, making them a valuable tool for organizations looking to extend their network reach while maintaining control over security and performance.
Layer 2 VPN Protocols
Layer 2 VPN protocols are essential for creating secure and efficient virtual private networks. These protocols operate at the data link layer of the OSI model and are used to establish and maintain communication between different network devices. There are several Layer 2 VPN protocols available, each with its own features and functionalities.
One of the most commonly used Layer 2 VPN protocols is the Point-to-Point Protocol (PPP). PPP establishes a direct connection between two network devices over a communication link. It provides authentication and encryption capabilities, making it a secure option for VPN connections.
Another popular Layer 2 VPN protocol is the Layer 2 Tunneling Protocol (L2TP). L2TP combines the best features of PPP and the Layer 2 Forwarding (L2F) protocol. It is often used in conjunction with IPsec encryption to provide a highly secure VPN connection.
Ethernet VPN (EVPN) is another key Layer 2 VPN protocol that is gaining popularity. EVPN uses MAC address routing to enable communication between devices in different locations. It is highly scalable and efficient, making it suitable for large-scale VPN deployments.
Overall, Layer 2 VPN protocols play a crucial role in ensuring the security and functionality of virtual private networks. By utilizing these protocols, organizations can establish reliable and secure communication channels between their network devices, enabling remote access and data transfer in a safe and efficient manner.
Layer 2 VPN Technologies
Layer 2 Virtual Private Network (VPN) technologies play a crucial role in modern networking by securely connecting multiple locations, facilitating data exchange across a secure, private network. These technologies are widely used by businesses and organizations to ensure the confidentiality and integrity of their data transmissions.
One common Layer 2 VPN technology is Virtual Private LAN Service (VPLS), which enables geographically dispersed sites to communicate with each other as if they are on the same Local Area Network (LAN). VPLS creates a virtual bridge between sites, allowing for seamless communication and resource sharing.
Another popular Layer 2 VPN technology is Ethernet VPN (EVPN), which uses the Border Gateway Protocol (BGP) to provide advanced multi-tenancy support, scalability, and flexibility. EVPN is particularly effective in data centers and cloud environments where dynamic resource allocation and high availability are paramount.
Additionally, Layer 2 Tunneling Protocol (L2TP) and Point-to-Point Protocol (PPP) are commonly used for establishing secure connections over public networks. These protocols encapsulate data packets to ensure secure transmission between endpoints, making them ideal for remote access scenarios.
In summary, Layer 2 VPN technologies offer a secure and efficient way to interconnect multiple locations and enable seamless communication across a private network. By implementing these technologies, businesses can enhance their network infrastructure, improve data security, and streamline their operations in an increasingly interconnected world.
Layer 2 VPN Benefits
Layer 2 VPNs, or Virtual Private Networks, offer a range of benefits for businesses seeking secure and efficient communication solutions. These benefits span across various aspects of network management and operations, making Layer 2 VPNs a popular choice for organizations of all sizes.
One significant advantage of Layer 2 VPNs is their ability to provide a secure and private communication channel over a shared or public network infrastructure. By encapsulating data within the VPN tunnel, Layer 2 VPNs ensure that sensitive information remains protected from unauthorized access or interception by external parties. This level of security is crucial for businesses handling confidential data, such as financial transactions or customer information.
Moreover, Layer 2 VPNs facilitate seamless connectivity between geographically dispersed locations. Whether it's connecting branch offices, remote employees, or data centers, Layer 2 VPNs enable organizations to establish a unified network environment. This centralized approach simplifies network management and enhances collaboration by allowing users to access resources and applications securely from any location.
Additionally, Layer 2 VPNs offer flexibility and scalability, making them ideal for evolving business requirements. As organizations grow or undergo changes, Layer 2 VPNs can easily accommodate additional sites, users, or bandwidth without requiring significant infrastructure modifications. This scalability ensures that businesses can adapt to shifting demands without compromising performance or security.
Furthermore, Layer 2 VPNs support a wide range of network protocols and applications, including voice, video, and data transmission. This versatility enables businesses to leverage various communication tools and technologies while maintaining a consistent level of performance and security across their network infrastructure.
In conclusion, Layer 2 VPNs deliver numerous benefits, including enhanced security, seamless connectivity, flexibility, and support for diverse applications. By leveraging these advantages, businesses can optimize their network operations and empower their workforce to collaborate effectively in today's dynamic business environment.
Layer 2 VPN Implementation
Layer 2 VPN Implementation: Enhancing Network Connectivity
Layer 2 Virtual Private Networks (VPNs) have emerged as a crucial tool for businesses seeking to enhance their network connectivity and security. This implementation enables the creation of secure communication channels over existing network infrastructures, facilitating the seamless transfer of data between remote locations.
The implementation process for Layer 2 VPN involves several key steps:
Network Assessment: Before deploying a Layer 2 VPN, it's essential to conduct a comprehensive assessment of the existing network infrastructure. This includes evaluating network topology, bandwidth requirements, security protocols, and potential points of congestion.
Selecting the Right Technology: There are various technologies available for implementing Layer 2 VPNs, including MPLS (Multiprotocol Label Switching), VPLS (Virtual Private LAN Service), and Ethernet VPN (EVPN). The choice depends on factors such as scalability, cost-effectiveness, and compatibility with existing hardware.
Configuration and Deployment: Once the appropriate technology is selected, network engineers configure routers, switches, and other network devices to establish VPN tunnels. This involves defining Virtual Private Wire Service (VPWS) or Virtual Private LAN Service (VPLS) instances, assigning VLANs, and configuring routing protocols.
Security Measures: Implementing Layer 2 VPNs introduces new security considerations. Encryption protocols such as IPsec (Internet Protocol Security) and MACsec (Media Access Control Security) may be employed to ensure data confidentiality and integrity over the VPN tunnels.
Monitoring and Maintenance: After deployment, ongoing monitoring and maintenance are essential to ensure optimal performance and security. This includes tracking network traffic, identifying potential bottlenecks, and promptly addressing any issues that arise.
Layer 2 VPN implementation offers several benefits, including enhanced security, improved network scalability, and simplified management of geographically dispersed networks. By following best practices and leveraging appropriate technologies, businesses can establish robust Layer 2 VPNs to meet their connectivity needs effectively.
0 notes
Text
Lab 3: ADC, UART, DMA, and LCD Display
Goals Familiarity with the TM4C123 analog to digital converters Integrating timers and interrupts into an Analog to Digital Converters (ADC) application Understanding the relationship between the clock speed and power dissipation Configuring a Universal Asynchronous Receiver/Transmitter (UART) interface Understating DMA transfer modes, channels, triggers Interfacing a Liquid Crystal Display…

View On WordPress
0 notes
Text
Full Stack Developer Interview Questions

Are you preparing for a Full Stack Developer interview? Whether you’re experienced or new to full-stack development, acing the interview is essential to land your dream job. To help you prepare with confidence, we’ve compiled a comprehensive list of Full Stack Developer interview questions covering various topics and concepts you may encounter during the interview.
Explain Pair Programming.
Explain Long Polling.
Explain the meaning of multithreading.
What do you mean by CORS (Cross-Origin Resource Sharing)?
Explain the benefits and drawbacks of using “use strict”.
What is Callback Hell?
Explain the event loop in Node.js.
To develop a project from scratch, what technologies and languages would you need or what skills a full stack developer should have?
Explain dependency injection.
What do you mean by the observer pattern?
Can you tell me what are the latest trends in Full Stack Development? Also, how do you keep yourself updated about the new trends in the industry?
What is CI (Continuous Integration)?
What are some of the uses of Docker?
State the difference between GraphQL and REST (Representational State Transfer).
Is there a way to decrease the load time of a web application?
What is Spring Framework, and how does it work?
What is REST API, and how does it work?
What is the difference between a servlet and JSP?
Explain the difference between JDBC and Hibernate.
How do you handle exceptions in Java?
1. Explain Pair Programming
Pair programming is a collaborative software development method where two programmers work together on one computer. The driver writes code, while the navigator reviews it. This approach finds errors early, boosts creativity, and enhances code quality.
2. Explain Long Polling
Long polling is a web development technique. In this technique, the client sends a request to the server, and the server keeps the request open until it has new data to send back or a timeout occurs. It’s used to achieve real-time updates in web apps without checking the server. It’s handy for chat apps and similar scenarios that need immediate data updates.
3. Explain the meaning of multithreading
Multithreading is a programming technique where one program runs several threads simultaneously. These threads work independently while sharing resources like memory. This makes the program faster and more responsive.
4. What do you mean by CORS (Cross-Origin Resource Sharing)?
CORS, or Cross-Origin Resource Sharing, is a security feature implemented in web browsers. It controls access to resources on a web page from different domains. It allows or restricts web pages to make requests for resources hosted on other domains. CORS helps prevent potential security issues related to cross-origin requests, ensuring safer interactions between web applications.
5. Explain the benefits and drawbacks of using “use strict”
Using ‘use strict’ in JavaScript enforces stricter coding rules and helps catch common errors, leading to better code quality and improved error handling. It can potentially make code execute faster. However, it might necessitate rewriting existing code to adhere to strict mode, which can be a drawback.
6. What is Callback Hell?
Callback Hell, also known as the Pyramid of Doom, refers to a situation in asynchronous programming where multiple nested callback functions create complex and hard-to-read code. It occurs when callbacks are used extensively, making the code difficult to manage. It can be mitigated using techniques like Promises or async/await.
7. Explain the event loop in Node.js
The event loop is a crucial part of Node.js’s architecture. It’s responsible for handling asynchronous operations. Node.js is single-threaded, but it can perform non-blocking I/O operations by using the event loop. It continuously checks the message queue for pending tasks, executes them, and handles callbacks, making Node.js highly efficient for handling concurrent requests.
8. To develop a project from scratch, what technologies and languages would you need or what skills a full stack developer should have
A full stack developer starting a project from scratch should be comfortable with multiple programming languages like Java, Python, PHP, or Ruby. They should know front-end technologies like HTML5, CSS3, and JavaScript, and frameworks like React or Angular. Back-end skills with Spring, Django, or PHP are vital. Familiarity with databases like MySQL, Oracle, and MongoDB is necessary. Design principles, server administration, and basic Linux knowledge can also be helpful.
9. Explain dependency injection
Dependency injection is a design pattern used in software development where the dependencies of a class (external objects it relies on) are provided to it rather than being created within the class itself. This helps decouple components, making code more modular and testable. It enhances flexibility, as different implementations of dependencies can be injected without changing the core code.
10. What do you mean by the observer pattern?
The observer pattern is a behavioral design pattern where an object, known as the subject, maintains a list of its dependents, called observers. When the subject undergoes a change in state, it notifies its observers, ensuring that they are automatically updated. This pattern is commonly used in event handling and UI design, enabling components to react to changes in a subject’s state.
11. Can you tell me what are the latest trends in Full Stack Development? Also, how do you keep yourself updated about the new trends in the industry
Staying updated in Full Stack Development involves keeping an eye on trends like the rise of JavaScript frameworks (React, Vue.js), serverless architecture, microservices, and containerization (Docker). To stay informed, I regularly read tech blogs, follow industry news, participate in online forums, attend webinars, and take online courses to continuously enhance my skills.
12. What is CI (Continuous Integration)?
Continuous Integration (CI) is a software development practice. In CI, code changes are being combined with the main codebase. This helps prevent errors and maintain code quality. It streamlines development by building and testing new code additions.
13. What are some of the uses of Docker?
Docker is widely used in software development for containerization. It allows developers to package applications and their dependencies into containers, ensuring consistency across different environments. Docker is used for application deployment, microservices architecture, creating development and testing environments, and simplifying the management of complex applications.
14. State the difference between GraphQL and REST (Representational State Transfer)?
GraphQL and REST are both approaches to API design. GraphQL provides a more flexible way to request and retrieve data, allowing clients to specify their data requirements. In contrast, REST uses fixed endpoints for data retrieval, leading to over-fetching or under-fetching of data. GraphQL is better suited for modern, dynamic applications, while REST is more traditional and rigid in its structure.
15. Is there a way to decrease the load time of a web application?
Yes, several methods can reduce the load time of a web application, such as optimizing images, using external CSS and JavaScript files, reducing redirects, enabling browser caching, minifying code, and employing content delivery networks (CDNs). These techniques improve performance and enhance user experience.
16. What is Spring Framework, and how does it work?
The Spring Framework is a Java-based framework used for building enterprise-level applications. It simplifies development by providing dependency injection, aspect-oriented programming, and data access. Spring promotes modularity, testability, and scalability. Which makes it a preferred choice for creating robust and maintainable software.
17. What is REST API, and how does it work?
A REST API, stands for Representational State Transfer Application Programming Interface. It is a design style for building networked applications. It relies on HTTP requests to perform basic operations like creating, reading, updating, and deleting resources identified by URLs. REST APIs are stateless, which means every client request must contain all the necessary information. They’re used for web-based applications and services.
18. What is the difference between a servlet and JSP?
A servlet is a Java class that handles requests and generates responses on the server-side. It is primarily responsible for processing logic and business operations. In contrast, JSP (JavaServer Pages) is a technology for creating dynamic web pages. JSP combines HTML or XML with Java code to generate dynamic content for web applications. Servlets are more suitable for complex processing, while JSP simplifies the presentation layer.
19. Explain the difference between JDBC and Hibernate?
JDBC, or Java Database Connectivity, is a Java API used for connecting and interacting with relational databases. It involves manual SQL query writing and database interaction. On the other hand, Hibernate is an Object-Relational Mapping (ORM) framework that automates database interactions by mapping Java objects to database tables. Hibernate eliminates the need for manual SQL coding, simplifying database operations.
20. How do you handle exceptions in Java?
In Java, exceptions are handled using try-catch blocks. Code that might throw exceptions is placed within a try block, and specific exceptions are caught and handled in catch blocks. Developers can specify different catch blocks for different exception types, allowing for precise error handling. Additionally, the “finally” block can be used to execute code that should run regardless of whether an exception occurred or not. Exception handling ensures graceful error recovery and better program stability.
#datavalley#dataexperts#data engineering#data analytics#dataexcellence#business intelligence#data science#power bi#data analytics course#data science course#full stack course#full stack training#full stack web development#full stack developer
1 note
·
View note
Text
rnðtdətztɛəɪelshaɪovə
Pronounced: rnthtduhtztayuhielshaiovuh.
Pantheon of: judiciousness, ability, noise, otherworld, malleability, credibility, incompetence.
Entities
Mɑrərŋæɛfrðunwðəɒiʌf
Pronounced: mahruhrngaayfrthunwthuhouiuf Malleability: ductility. Credibility: cogency. Ability: form. Legends: pas, deactivation, asynchronous transfer mode, rub up. Prophecies: casus belli, whiz, sparring, naprapathy, thrombolytic therapy.
Npepɪtsməðʌrnwttɪʌðr
Pronounced: npepitsmuhthurnwttiuthr Malleability: ductility. Credibility: street credibility. Ability: contractility. Legends: percussion, rearmament, formation, development, functional magnetic resonance imaging. Prophecies: moral obligation, payment, knock. Relations: zɪiəlnfumɪzɪʌðdhfədŋ (parathion), vpnðæseɪtbnəəttʃhaɪdmt (economic rent).
Nttɛztedɑɛtənrtðwdmʃ
Pronounced: nttayztedahaytuhnrtthwdmsh Malleability: ductility. Credibility: plausibility. Ability: contractility. Legends: ransacking. Prophecies: hysterotomy, debilitation, reading, short division. Relations: tnnɪdlɪskpʌlævitɪʌmɛ (anionic compound), sfðnhðəzæzətɛɪhsnaɪnɪ (gold).
Sfðnhðəzæzətɛɪhsnaɪnɪ
Pronounced: sfthnhthuhzazuhtayihsnaini Malleability: flexibility. Credibility: cogency. Ability: form. Relations: vpnðæseɪtbnəəttʃhaɪdmt (pyrophosphate), əsmobobðɪfkwŋʃriəiðɑ (driftwood), npepɪtsməðʌrnwttɪʌðr (far cry).
Tnnɪdlɪskpʌlævitɪʌmɛ
Pronounced: tnnidliskpulavitiumay Malleability: flexibility. Credibility: cogency. Ability: form. Legends: challenge. Prophecies: mikvah.
Vpnðæseɪtbnəəttʃhaɪdmt
Pronounced: vpnthaseitbnuhuhttshhaidmt Malleability: ductility. Credibility: cogency. Ability: penetration. Legends: walkover, tax collection, waste of effort, duel. Prophecies: suturing, cleaning. Relations: nttɛztedɑɛtənrtðwdmʃ (phone).
Zɪiəlnfumɪzɪʌðdhfədŋ
Pronounced: ziiuhlnfumiziuthdhfuhdng Malleability: ductility. Credibility: authenticity. Ability: adaptability. Legends: union, invasion of privacy, pursuance, corporal punishment. Prophecies: smudge, snore, fight. Relations: əsmobobðɪfkwŋʃriəiðɑ (hudson seal), sfðnhðəzæzətɛɪhsnaɪnɪ (excelsior), vpnðæseɪtbnəəttʃhaɪdmt (profit sharing).
Əsmobobðɪfkwŋʃriəiðɑ
Pronounced: uhsmobobthifkwngshriuhithah Malleability: flexibility. Credibility: authenticity. Ability: magical ability. Legends: monstrosity, fall, breach of the covenant of warranty. Prophecies: standing, periodic motion. Relations: zɪiəlnfumɪzɪʌðdhfədŋ (euphorbium), npepɪtsməðʌrnwttɪʌðr (pseudoephedrine).
0 notes
Text
[ad_1] The most recent movement has wrapped up, and whilst there used to be sadly no phrase about , Nintendo has printed extra information about different video games which can be coming to Transfer. Amongst them is OlliOlli Global, which shall be launched on February eighth. The most recent OlliOlli recreation from Roll7 () is a skateboarding platformer, through which you ranking issues via pulling off tips as you are making your approach during the global of Radlandia. Together with there are two asynchronous multiplayer modes. In Gnarvana League, you'll be able to duke it out for the best possible ranking and the extra you play, the extra beauty pieces you'll be able to free up to your persona. Within the Gnarvana Portal mode, you'll tackle ranges which can be procedurally generated with a couple of customizable components in thoughts, reminiscent of taste, issue and period. You'll be able to proportion creations with different avid gamers the use of a code, which can paintings throughout all platforms. [embed]https://www.youtube.com/watch?v=IopOsBOMF2Y[/embed] Roll7 and writer Non-public Department have additionally introduced two expansions for OlliOlli Global. The Void Riders DLC, which can arrive in summer season, will upload extra ranges, characters, gameplay choices, cosmetics and a brand new biome. The second one enlargement is about for subsequent fall, and extra main points shall be printed later. In addition to Transfer, OlliOlli Global is coming to PC, PlayStation 4, PS5, Xbox One and Xbox Collection X/S. Pre-orders get started lately and the bottom model of the sport prices $30. The Rad version, which prices $45, comprises each expansions. House owners of the bottom recreation will be capable of purchase the DLC one by one. Different titles featured right through the Indie Global Exhibit come with . The sport, through which you paint the arena to discover and resolve puzzles, used to be a important hit previous this 12 months. It’s to be had on Transfer lately. Additionally coming to the hybrid console lately are the excellently named motion platformer Dungeon Munchies, celebration recreation Let’s Play! Oink Video games and stealth puzzle journey Timelie, for which a demo shall be to be had. and Omori are getting ported to Transfer this spring. A few of the new video games which can be environment sail for Transfer are Sea of Stars, an RPG prequel to The Messenger (which can arrive in vacation 2022), puzzle identify Aliisha – The Oblivion of Dual Goddesses (spring), Figment 2: Creed Valley (February, with a demo to be had lately) and River Town Ladies 2 (summer season). [embed]https://www.youtube.com/watch?v=NsSBN64IVpI[/embed] All merchandise really useful via Engadget are decided on via our editorial staff, impartial of our mum or dad corporate. A few of our tales come with associate hyperlinks. If you are going to buy one thing thru this sort of hyperlinks, we might earn an associate fee. [ad_2]
0 notes
Text
"An example of a technical decision said to be a typical result of design by committee is the Asynchronous Transfer Mode (ATM) cell size of 53 bytes. The choice of 53 bytes was political rather than technical.[2] When the CCITT was standardizing ATM, parties from the United States wanted a 64-byte payload. Parties from Europe wanted 32-byte payloads. Most of the European parties eventually came around to the arguments made by the Americans, but France and a few others held out for a shorter cell length of 32 bytes. A 53-byte size (48 bytes plus 5 byte header) was the compromise chosen."
0 notes
Text
Why MBA Course Distance Education Programs are Sought-after for Professionals and Students Alike
A growing number of distance learning institutions offer programs including mba finance courses or post-graduate diploma courses to students across all geographic locations. This makes education affordable, and accessible during the present times.
The effects of the Covid-19 pandemic have sparked greater interest and acceptance of new technological innovations, including online learning. This has led to a major shift in the manner in which universities and businesses operate. A survey by UGC, reveals that enrolments for online education such as MBA course distance education have grown by 170%, while open and distance learning has grown by 41.7% since the year 2020-21. Among the various factors, it is the higher degree of flexibility and learning autonomy, that makes students opt for distance learning for courses such as mba accounting and finance.
Among the best distance institutions, Symbiosis Centre of Distance Learning-SCDL has great course credibility, industry acceptance, and an institute reputation comparable with a MBA course distance mode. Continual education from SCDL stands out for several reasons in the resume.
What are the Most Sought-after Career Options for Distance Learning
Young adults feel that there is a need for people to acquire new, multidisciplinary skills. Many working professionals feel that a postgraduate or a continual education be it an MBA finance course or a PG diploma in finance and accounting will help them unlearn and relearn new knowledge.
In a recent survey conducted courses such as Data Science, Finance, Web development, and financial marketing has been some of the most sought-after courses for the year 2022.
Whether an MBA Accounting and finance course from a reputed institution or through distance learning mode, it is worthwhile considering several aspects of the institution. This include-Credibility of the institute, market recognition, alumni network, placement facilities, mentorship, and participation of the students in the program, to name a few.
What makes Distance Learning Popular Among Students
An extensive survey conducted among the students reveals that 60% of the students would like to learn new domain skills from time to time after they graduate; thereby suggesting that the growing demand for online postgraduate programs has now outstripped traditional programs.
With distance learning institutions like SCDL offering asynchronous online learning options through Post Graduate Diploma, Diploma, and Certificate courses in business management, finance, and banking, data and analytics, teaching and learning, and hospitality management, they are akin to any full-fledged post graduate courses like MBA finance course taught across other universities and colleges.
Flexible learning option- Distance learning courses are popular among working professionals, students or women who wish to step out for work after a long break. Not only it gives greater autonomy to participants, but it is also a wise option to balance career and studies simultaneously.
SCDL recognizes this aspect and facilitates a modular course system with a credit banking facility, which is otherwise offered by full-fledged courses like mba finance and accounting. This enables students to bank and accumulate credits for future transfer to other programs of SCDL, thus providing flexible learning opportunities.
Asynchronous learning experience- Students who wish to pursue courses from the best online mba colleges can now opt to do so without leaving their jobs and commitments. The idea is to now pursue lifelong learning anytime, anywhere around the world.
Employability and honing of skills Considering the fact that distance learning programs and other best online mba courses support employability, it helps in creating talent supply chains, thereby contributing to large-scale employment and skill development.
About SCDL
SCDL is among the pioneering institutions for distance learning, offering a wide range of AICTE approved Post Graduate Diplomas, Diploma and Certificate programs in over 40+ specializations. The course and course material are designed to be in line with the market demand and industry trends.
In the two decades of its operations, SCDL is well-known for its blended learning methodology and collaborative learning, which makes it a reputed Distance Learning institute in India. The curriculum of SCDL is comparable with the best distance-learning universities of the world. SCDL has a full-time faculty and over 350 adjunct faculty who are available for academic counseling, developing curriculum and assessment of students’ progress.
0 notes
Link
ATM machine की full form यानि full form of ATM machine होती है Automated Teller Machine जबकि कुछ लोग इसे Any Time Money या All Time Money भी कहते है लेकिन इसकी असल full form Automated Teller Machine ही होती है।
अब जैसा मैंने आपको पहले ही बताया की bank में हर कोई transaction करने नहीं आता और जिन लोगो को बस बैंक से पैसे ही निकालना होते है उनको हर बार बैंक जाने की कोई ज़रूरत नहीं होती बल्कि वो ATM machine से ही जब चाहे तब पैसे निकाल सकते है।
#what is the full form of atm#atm full meaning#full form of atm#atm full form in banking#full form of atm machine#atm full form any time money#asynchronous transfer mode
0 notes
Text
State-run ITI to implement India army communication network project for $1 billion
State-run ITI to implement India army communication network project for $1 billion

Photo: Communication Towers. For Representational Purposes Only.
New Delhi: India‘s army will soon be carrying out its internal communication on a modern, secure network, ensuring seamless connectivity with troopers posted at the borders with rivals China and Pakistan.
The project, approved by the country’s highest decision-making body on national security matters led by Prime Minister Nare…
View On WordPress
#Acquisition#Army#Army Static Switched Communication Network#ASCON#Asynchronous Transfer Mode Technology#Atmanirbar Bharat#Atmanirbarta#Atmanirbhar Bharat#Atmanirbharta#ATMT#Borders#Boundary#Cabinet Committee on Security#CCS#China#Chinese#Communication#Communication Network#Companies#Conflict#Confrontation#Connectivity#Coronavirus#COVID#COVID-19#Defence#Defence Ministry#Defense#Economy#Employment
0 notes
Photo

BYTE October 1997
An assortment of networking technologies (the “ATM” they were alternatives to was “asynchronous transfer mode”) and speedy modems were examined in this issue.
4 notes
·
View notes
Text
Sony Manufacturing 1394 Driver Download

The current official release of the driver is 6.4.6, released on September 26, 2011 by Christopher R. [email protected].
To download drivers, firmware updates, BIOS, and software, please select your model in the list below, or type the model name in the search box. Select your product type SVD Series. Sony I Link 1394 Adapter free download - 802.11g/b WLAN USB(2.0) Adapter, Sony Ericsson PC Suite, Broadcom 802.11g Network Adapter, and many more programs.
After more than a year of wrestling with the nuances of Microsoft's 64-bit operating systems, and with no small quantity of assistance from a few brave testers (you know who you are!), I am proud to officially release this next version of the CMU 1394 Digital Camera Driver, which includes:
Support for all present 64-bit versions of Microsoft Windows XP, Vista and 7, allowing both native (64-bit) and emulated (32-bit) applications to access camera data via a single driver interface.
A completely new demo application, written from the ground up to support both 32-bit and 64-bit Windows.
A litany of bugfixes, many of which were contributed by individual users (for which I am grateful!), including:
Squashment of the nefarious BSOD on resume-from-suspend bug
A closer-to-correct implementation of the Serial I/O functionality described in the IIDC 1.31 standard (closer = still a little quirky, but the quirks may be in the camera I am testing with)
Verified Strobe and Parallel I/O functionality (Strobe controls are also now integrated into the same dialog as Gain, Zoom, Focus, etc.)
.. and many others
New since the public beta:
Fully automated driver installation on 64-bit systems
Several minor bugfixes and documentation updates, but nothing that alters the API/ABI
Update: digital signatures for all kernel-mode software
All 64-bit versions of windows require a digital signature via an AuthentiCode certificate in order to run kernel-mode software. I would like to thank MathWorks for providing the funding for this certificate and allowing this driver set to continue to be published freely to the general public. MathWorks provides an adapter to the CMU 1394 Digital Camera driver as part of their Image Acquisition Toolkit to allow developers quick and easy access to images from firewire cameras within the MATLAB environment.

Known issues and limitations
Large-block asynchronous transfers. I have received several requests and offerance of patches that restore the ability to issue large asychronous I/O (i.e., larger than a single quadlet/register) requests to cameras. I am evaluating these and trying to fold them into the driver in a manner that supports 64-bit platforms.
Mysterious BSOD when using multiple 1394b cameras on the same bus under Windows 7. In experimenting with various configurations of cameras, 1394b host controllers, and driver settings, I have occasionally triggered inexplicable kernel panics while performing comparatively simple operations. Whether this is a quirk of the new Microsoft 1394 bus driver, of some particular host controller, of the 1394 camera driver's innards, or, most likely, of some combination thereof, remains to be seen. Using a single 1394b camera on a single bus is quite stable, however, and the circumstances where multiple cameras trigger this problem seem rare.
The usual assortment of bugs and quirks. Much of the frame-handling logic had to be altered to accommodate the curious limitations of DMA transfers on 64-bit systems. Although I have been unit-testing this code to the greatest extent possible, my experience is that no new code is completely bug-free. My thanks go out to the many beta testers who have helped me to this point, and further comments/questions/bug reports/etc. are especially welcome on this front.

If the 1394 drivers in Windows XP have become corrupted, then they can be restored using the steps provided below. Note:
Sony Manufacturing 1394 Driver Download Windows 7
The main files that the card should use are:
Sony Manufacturing 1394 Driver Download
1394.INF 1394BUS.SYS OHCI1394.SYS


Open up the Device Manager and uninstall the 'OHCI Compliant IEEE 1394 Host Controller' listing – may also be listed as a Texas Instruments or Standard OHCI Compliant IEEE1394 Host Controller
Minimize the Device Manager and then insert your Windows XP CD-ROM
Go from the Start menu up to run and type 'CMD' and then press enter. This should bring up a DOS shell
Change to the drive letter of the CD drive (press 'd:' if your CD drive is drive letter D)
Next change to the 'i386' directory -- 'cd i386 '
From this directory type: expand 1394.in_ c:windowsinf This should restore the 'INF' (information) file for the FireConnect board that should be used
Now open the Device Manager back up and highlight the 'Computer' listing at the top of the category list. Select the 'Action' pull-down menu and choose 'Scan for hardware changes'. This should reinstall the FireConnect adapter
Restart the system and test by connecting your Firewire device

1 note
·
View note