#Apple java virus fix
Explore tagged Tumblr posts
Text
Apple java virus fix

Apple java virus fix full#
Apple java virus fix software#
Apple java virus fix code#
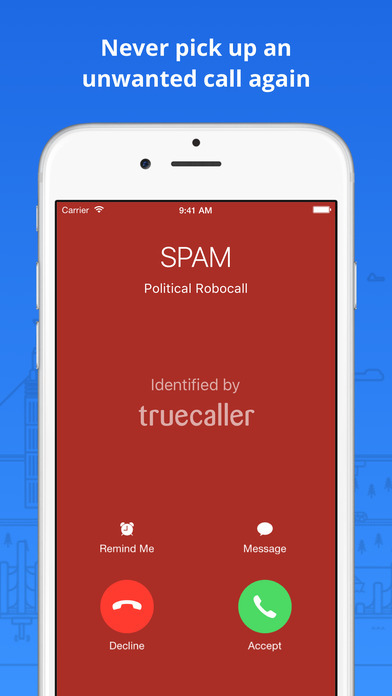
But it’s a good idea to take your iPad into an Apple Store and ask about a display replacement. If it’s a minor issue and not distracting, you can leave it. If the pixel is permanently dark no matter what you do, it’s dead.
Apple java virus fix full#
You can plenty of Pixel Fix videos on YouTube to run at full screen to help with this, or even find an app that does the same thing.
Flashing bright, changing colors can also help reset a pixel.
Sometimes this can help fix any issues the panel is experiencing. Wrap your thumb in a clean cloth and apply gentle, firm pressure to the area of the display with the pixel, slowly moving your thumb as you do so.
If the pixel still lights up but is simply stuck or never goes to the right color, you can try manually fixing it yourself.
Sometimes there may be more than one pixel like this. You’ll first notice this as an unresponsive dot on the display that doesn’t change, or stays black no matter what happens. It can be frustrating if a pixel isn’t working on your iPad. You may also want to take a look at our suggestions for the best iPad cases and the best iPad games.Īndy Boxall/Digital Trends Problem: There are dead or stuck pixels on the iPad Click on the Disable button (if the button says Enable, Java is already disabled). Click on the Java Plug-in 2 for NPAPI Browsers (Mac OS 10.6) or Java Applet Plug-in (Mac OS 10.7 and above) to select it.ĥ. In the Add-ons Manager tab, select the Plugins panel.Ĥ. On the menu bar, click on the Tools menu, and then click Add-ons.ģ. Click on the Safari menu and choose Preferencesġ. If you’d rather be safer than sorry (and you don’t use web banking) then you can disable java from your web browser.ġ. Don’t visit websites that seem suspicious or offer deals “to good to be true” and stay clear of banner ads that pop up in your browser like these. But link scanner only works best if you visit all websites via a google search.ĭon’t click on links in emails from people you don’t know. For those that don’t have regular checks I would recommend downloading and installing this software.
Apple java virus fix software#
If you get regular health checks this software has already been installed on your Mac and is kept up to date. If you are currently using anything other than these browsers I would think carefully about making the switch. Safari or Chrome are very good at actively spotting bad websites and stopping them in their tracks. If you want to be safe against this exploit there are things you can do so you can continue to use Java based websites. This will certainly fix the issue but it will make things like web banking inoperable so thats not really acceptable. The US justice department – not known for getting involved in such things – has released a statement suggesting that people disable or remove java completely. It would be like finding out that the body of your car is made of blasting caps and if you hit anything bigger than a moth it will explode. The whole thing has been compromised and needs to be rewritten. Someone, deep inside a bunker in China no doubt, has discovered that Java, at its core, is insecure and it cannot be simply patched. This has been the sequence of events when it has come to Java exploits but this latest one is different, very different.
Apple java virus fix code#
In any event other geeks with even spottier faces would come to the rescue by finding these holes, plug them with better code and release the fix to the howling masses. Or it is the Russian mafia who decide to take advantage of some insecure coding from Microsoft or Apple or google and fleece everyone of their money because they dared to use a computer on the internet. I gather it has something to do with being inferior or not being breast fed as a baby or something like that. In the past some spotty faced geek would decide that it has nothing better to do than to make our lives a misery by writing a virus or punching a hole into a piece of software we all rely on.

0 notes
Text
Download Ad Blocker For Mac Free

Written by Eyeo GmbH
Free Ad Blocker Windows 7
Ad Blocker For Mac Safari Free Download
Best Free Ad Blocker Mac
Ad Blocker For Macbook Air
Best Free Ad Blocker
Category: Productivity
Release date: 2019-11-27
Licence: Free
Software version: 2.1.0
File size: 19.24 MB
Compatibility: Windows 10/8.1/8/7/Vista and Mac OS X 10.12.6
Adblock Plus for Safari for PC and Mac Screenshots
Adblock for Mac, free and safe download. Adblock latest version: Block ads in Google Chrome. UBlock, the fastest, most powerful ad blocker for Mac is here. UBlock blocks all annoying pop-ups and ads while you browse on your Mac. It’s simple, easy-to-install, and best of all- completely free. Download uBlock ad blocker for Mac and browse faster today.
Key Features
Latest Version: 2.1.0
Licence: Free
Rated 3/5 By 740 People
What does Adblock Plus for Safari do? Adblock Plus for Safari is a totally free ad blocker that allows you to block annoying ads on your favorite websites and video channels. Simply install the app, and see the web in a better way. No more pop-ups, banners or autoplay ads. The Adblock Plus app for Mac supports great websites with Acceptable Ads (on by default). Don’t want to see any ads? Simply deactivate Acceptable Ads. You can also have the option to whitelist websites you trust.By downloading and installing the application, you agree to our Terms of Use. https://adblockplus.org/terms
Download for MacOS - server 1 --> Free
Download and Install Adblock Plus for Safari
Download for PC - server 1 --> MAC:


Download for MacOS - server 1 --> Free Thank you for visiting our site. Have a nice day!
PC Compactibility/Requirements for Installation
Compactible OS list:
Windows 10
Windows 8.1
Windows 7
Windows Vista
Free Ad Blocker Windows 7
Requirements for MacOS Installation
Ad Blocker For Mac Safari Free Download
Intel, 64-bit processor, OS X 10.7 or later.
Compactible OS list:
OS X 10.10: Yosemite
OS X 10.11: El Capitan
macOS 10.12: Sierra
macOS 10.13: High Sierra
macOS 10.14: Mojave8
macOS 10.15: Catalina
Adblock Plus for Safari - how do I download the app on PC?
If you want to download the software on your pc or mac, you could either first visit the Mac store or Windows AppStore and search for the app OR you can easily use any of the download links we provided above under the 'Download and Install' header section to download the application
Adblock Plus for Safari - Is it safe to download?
Yes. The app is 100 percent (100%) safe to download and Install. Our download links are from safe sources and are frequently virus scanned to protect you
By Glendale2x
New framework seems to have performance issues
This version of ABP for the new Safari framework unfortuantely seems to kill performance on my computers. Maybe it’s partially related to them being a bit older (one is a Mid 2011 Mini, the other is a 2012 iMac), but with ABP enabled I can’t even open a new tab/window and type a URL into the bar and expect Safari to accept the input without having to hold down the return key until it goes or wait a minute after opening a new tab or window. I also noticed that using Twitter was jumpy and lagged even with simple typing, it felt like all the dynamic content it relies on was just struggling to be processed through whatever framework Apple is forcing. Hopefully the devloper can figure out the performance issues because it’s really, really bad now.
By Ramblin'Rose
why isn’t this working?
I have ABP and it wasn’t perfect but worked fairly well for my needs. Recently, it simply disappeared. (I see someone else said that could be from the latest iOS update, but I don’t have that on my desktop yet). When I tried to reinstall, it showed me two boxes to check. The way I read it, if you checked the box that said you wanted the icon visible in the toolbar, it would be able to read sensitive information of all kinds on any page. What good is an app of any kind that allows for that?! As it was, with only the one box checked, it only blocked very few ads, and I was still getting requests from sites to be whitelisted without being able to fnd any way to do it. I’ve got all kinds of garage showing up on my Facebook page, and you guys have ruined what was a reasonable product. WHY?
By PeopleRsad
Still works for me
Almost didn’t download the new version based on the recent reviews, however after looking at the other apps here that claim to be ad blockers I didn’t’t see too many alternatives. I decided to go ahead and get the new version and so far its pretty much the same as the old version, lots of ads blocked. I’m happy, just make sure you go through the simple set-up.
By achilds19
Works well but
After much research, I understand the issue with Apple changing the rules on the devs so they had to build this app from scratch. Works well for me so far, except for one annoying problem. I use Yahoo mail and it's not hiding the ad that appears in the top line of the inbox even with unchecking the Acceptable Ads box, which is super annoying. I know the devs are watching these reviews, so if someone can point me to an extension or something that will fix that, I'd appreciate it. Was using AdGuard and it fixed that problem, but that app behaves like spyware and is constantly running in the background even after you close Safari.
Advertisement
Adguard for Mac v.1.1.0Adguard is the first standalone adblocker for Mac OS X. It is an ultimate program has all the features to ensure more efficient and comfortable use of the Internet. Ad blocking, phishing and malware protection, and privacy protection!
SlimBoat for Mac v.1.1.6SlimBoat is a fast and secure FREE web browser software with a lot of powerful features, such as intelligent form filler, popup blocker, adblocker, social network integration, download manager, web page translation, quick search and site groups.
Safari AdBlocker for Mac OS v.1.9.8.6The only 64-bit adblocker built for Mac OS X 10.5+ to integrate directly into Safari, for minimum disruption to your browsing experienceMain Features- Adblock Plus subscription support- Right-click to block images, and frames- Automatic ...
Vivaldi for MacOS v.3.2.1967The Vivaldi browser lets you be in control of how your browser looks, feels and works. It does not track you, adapts to your style with features that you need and has values that you can stand by.
Maiar Browser v.80.0.1.40Maiar is an extremely fast and privacy-friendly browser for the modern web. It loads major websites 2-8 times faster than Chrome and Safari. Maiar can block ads without modules or extensions.
Izenda Ad Hoc - Express Edition v.4.0Izenda Ad Hoc - Agile Business Intelligence for ASP.NETLiberate Your Organization's Relational Data Today!Izenda Ad Hoc empowers business users to directly explore relational data from a web browser. * Intuitive and Completely Web-Based AJAX Report ...
Avian Freeware Suite v.0.1Avian Freeware Suite (AFS) provides two things: Developers with libraries for Java Swing Widgets, XML handling, Fortran95 and Pascal; End users (Medical students, doctors, scientists) with productivity tools they can use (quizzes, XML databasing & ...
IP Blocker v.20050403IP Blocker is an incident response tool that automatically updates access control lists on Cisco routers and other devices. Web and command line interfaces are both supported, as is logging, email notification, and automatic expiration of ...
QR-Code Maker Freeware v.1.0.0Use QR-Code Studio to create QR codes for free. An assistant simplifies the creation of QR codes for mobile tagging, social media and more. The generated QR-Codes are available immediately as BMP, GIF, JPG, PNG and TIFF graphic file.
Freeware Advanced Audio Coder v.2.2.7FAAC is an Advanced Audio Coder (MPEG2-AAC, MPEG4-AAC). The goal of FAAC is to explore the possibilities of AAC and exceed the quality of the currently best MP3 ...
Zhang Hong's Freeware v.1.0[1] English-Portuguese-Chinese Dictionary [2] Japanese-English-Chinese Dictionary [3] MP3 Sponge [4] JPG Sponge [5] RedDays [6] RadSensor [7] descriptions and updates: ...
Mimosa Scheduling Software Freeware v.6.5.8Mimosa is a scheduling and event planning software application for use to create timetables in any kind of school and university of varying type and size. It is also used to schedule conferences and work-shifts in business and industry environments.
Flash Banner Maker for Mac v.1.00With AnvSoft Flash Banner Maker for Mac, you can easily create gorgeous flash banners in SWF format and html file for flash intros or for building website. You can add any image backgroud from your hard drive and choose from the 50+ animation effects for.
BiblePlayer for iPod v.1.1Take God’s Word to Go! Do you need to have a daily dose of bible scriptures? Or maybe you need a bible reading plan? Now you can read and listen to the King James version of the Bible on your iPod with this new freeware program. Bibleplayer ...
Mach-O OSAX v.0.1Mach-O OSAX is a scripting addition for CodeWarrior which provides different samples. The package is completly freeware and the source code is ...
QuickCart v.2.2QuickCart 2.2 is regarded as a flexible and handy program which is designed to run your own web shop. Freeware and easy to use e-commerce solution is designed to run Your own web shop. As a database it uses files structure so that the SQL database is ...
Flippagemaker PDF to Flash (SWF) for Mac v.1.0.0Flippagemaker Free PDF to Flash (SWF) for Mac is freeware for Mac users to convert pdf to swf flash video. Create Macromedia Flash (SWF) file from Adobe PDF file for embedding into web page easily.
DVDSmith Movie Backup v.1.0.0DVDSmith Movie Backup is DVD Decrypter, DVD copying Freeware to backup, clone or copy DVD movie to computer as DVD folder and removes all the protections (CSS, RC, RCE, APS, UOPs and Sony ARccOS) while copying.
Hubblescreensavermac v.1.0'Hubble Space Telescope (Mac) free screensaver containing 99 high quality NASA-ESA space images. Screensaver designed by the Creative Department, an award winning advertising and interactive agency based in Cincinnati. Fully functional freeware.' ...
MediaHuman Audio Converter MAC v.1.8MediaHuman Audio Converter is a freeware for Mac OS X. It can help you in case you need to convert your music in WMA, AAC, WAV, FLAC, OGG or Apple Loseless format. This program was designed to simplify as much as possible the process of conversion.
Best Free Ad Blocker Mac
Freeware Ad Blocker software by TitlePopularityFreewareLinuxMac
Ad Blocker For Macbook Air
Today's Top Ten Downloads for Freeware Ad Blocker
Best Free Ad Blocker
Zoiper Webphone ZOIPER webphone is fully-compliant with Internet Explorer,
1000apps NetVibes Widget Avec ce Widget vous pourrez rechercher des logiciels ,
Vivaldi for MacOS The Vivaldi browser lets you be in control of how your
QR-Code Maker Freeware Use QR-Code Studio to create QR codes for free. An assistant
Flash Banner Maker for Mac With AnvSoft Flash Banner Maker for Mac, you can easily
PC Protect Your PC First screensaver application protecting your PC from
Flippagemaker PDF to Flash (SWF) for Mac Flippagemaker Free PDF to Flash (SWF) for Mac is freeware
DVDSmith Movie Backup DVDSmith Movie Backup is DVD Decrypter, DVD copying
Maiar Browser Maiar is an extremely fast and privacy-friendly browser for
BiblePlayer for iPod Take God’s Word to Go! Do you need to have a daily
Visit HotFiles@Winsite for more of the top downloads here at WinSite!

2 notes
·
View notes
Text
Impossible installer tinyumbrella

IMPOSSIBLE INSTALLER TINYUMBRELLA HOW TO
IMPOSSIBLE INSTALLER TINYUMBRELLA DOWNLOAD
None of the data on your device will be at risk of alteration by using the standard mode.In just a few minutes and a few easy steps, you can fix your iOS device and have it working normally again. It can be used to fix just about various issue you may be having including a device that is stuck on the Apple Logo, a device stuck in recovery mode or one that is stuck on a black or white screen.This alternative is iMyFone Fixppo and the following are just some of the features that make it ideal for you. Therefore, if you simply want to fix your iOS system as quickly as possible, you may need a simpler alternative. You should also run the program in compatibility mode.Īlternative to TinyUmbrella: iMyFone FixppoĪs the above solutions clearly demonstrate, if you are unfortunate enough to experience problems when using TinyUmbrella, the solutions can be challenging for the average user. If TinyUmbrella fails to work on your Windows system, here’s what you can do.ĭisable your anti-virus and Windows Defender and then make sure that you have installed the latest version of iTunes and Java on your Windows system. Step 3: Enter the path of your SHSH files (if you don’t know it, delete the entry) and the program should launch just fine. Step 2: Go to HKEY_CURRENT_USERSoftwareJavaSoftPrefscomsemaphore and then double-click on "/S/A/V/E_/D/I/R/E/C/T/O/R/Y. Step 1: Open the registry editor and click “Start” and type “regedit.” Press enter. If you try to open TinyUmbrella and it just won’t launch, here’s what you can do to fix it. cache/) When you open TinyUmbrella, it should be able to work now. Step 3: Once the file has been downloaded, place it in the same place it was previously (C: Users/Your User Name/.
IMPOSSIBLE INSTALLER TINYUMBRELLA DOWNLOAD
Step 2: Delete the Lib-Win.jar file you find there and then download a new Lib-Win.jar file. Step 1: Open Windows Explorer and navigate to C: Users/Your User Name/. If this is what you encountered, here’s what you can do to fix it. The program doesn’t load or displays the “Unable to Validate Reticulating Splines” message. The following are just some of the problem TinyUmbrella users face and how you can fix them.
IMPOSSIBLE INSTALLER TINYUMBRELLA HOW TO
Alternative to TinyUmbrella: iMyFone iOS System RecoveryĬommon Issues with TinyUmbrella and How to Fix Them Common Issues with TinyUmbrella and How to Fix Them

0 notes
Text
Trojan For Mac

(Redirected from Trojan BackDoor.Flashback)
OSX.FlashBack[1], also known as the Flashback Trojan, Fakeflash, or Trojan BackDoor.Flashback, is a Trojan horse affecting personal computer systems running Mac OS X.[2][3] The first variant of Flashback was discovered by antivirus company Intego in September 2011.[4]
Infection[edit]
According to the Russian antivirus company Dr. Web, a modified version of the 'BackDoor.Flashback.39' variant of the Flashback Trojan had infected over 600,000 Mac computers, forming a botnet that included 274 bots located in Cupertino, California.[5][6] The findings were confirmed one day later by another computer security firm, Kaspersky Lab.[7] This variant of the malware was first detected in April 2012[8] by Finland-based computer security firm F-Secure.[9][10] Dr. Web estimated that in early April 2012, 56.6% of infected computers were located within the United States, 19.8% in Canada, 12.8% in the United Kingdom and 6.1% in Australia.[6]
OSX.Trojan.Gen is a notorious malware program that mainly targets Mac OS. It has the ability to exploit the system vulnerabilities like weak passwords, unprotected system or open network connection to break in. Once in, this harmful Trojan program takes over the whole system without being detected. And carry out various nefarious activities.
Protect your Mac from malware. MacOS has many features that help protect your Mac and your personal information from malicious software, or malware. One common way malware is distributed is by embedding it in a harmless-looking app. You can reduce this risk.

Details[edit]
Malware Library. Threats targeting Macs. Mac malware exists in all shapes and sizes and new digital parasites evolve every day. Whether it’s adware, trojan horses, keystroke loggers, viruses or other spyware, stay up-to-date and discover more information about the latest threats targeting your Mac here.
The original variant used a fake installer of Adobe Flash Player to install the malware, hence the name 'Flashback'.[4]
Remove Trojan Virus Mac
A later variant targeted a Java vulnerability on Mac OS X. The system was infected after the user was redirected to a compromised bogus site, where JavaScript code caused an applet containing an exploit to load. An executable file was saved on the local machine, which was used to download and run malicious code from a remote location. The malware also switched between various servers for optimized load balancing. Each bot was given a unique ID that was sent to the control server.[6] The trojan, however, would only infect the user visiting the infected web page, meaning other users on the computer were not infected unless their user accounts had been infected separately.[11]
Resolution[edit]
Oracle, the company that develops Java, fixed the vulnerability exploited to install Flashback on February 14, 2012.[8] However, at the time of Flashback's release, Apple maintained the Mac OS X version of Java and did not release an update containing the fix until April 3, 2012,[12] after the flaw had already been exploited to install Flashback on 600,000 Macs.[13] On April 12, 2015, the company issued a further update to remove the most common Flashback variants.[14] The updated Java release was only made available for Mac OS X Lion and Mac OS X Snow Leopard; the removal utility was released for Intel versions of Mac OS X Leopard in addition to the two newer operating systems. Users of older operating systems were advised to disable Java.[12] There are also some third party programs to detect and remove the Flashback trojan.[13] Apple worked on a new process that would eventually lead to a release of a Java Runtime Environment (JRE) for Mac OS X at the same time it would be available for Windows, Linux, and Solaris users.[15] As of January 9, 2014, about 22,000 Macs were still infected with the Flashback trojan.[16]

See also[edit]
References[edit]

Trojan Remover For Macbook Pro

^This is the name used in Apple's built-in anti-malware software XProtect. Other antivirus software vendors may use different names.
^5 April 2012, Flashback Trojan botnet infects 600,000 Macs, Siliconrepublic
^5 April 2012, 600,000 infected Macs are found in a botnet, The Inquirer
^ abSeptember 26, 2011, Mac Flashback Trojan Horse Masquerades as Flash Player Installer Package, Intego Security
^Jacqui Cheng, 4 April 2012, Flashback Trojan reportedly controls half a million Macs and counting, Ars Technica
^ abc4 April 2012, Doctor Web exposes 550 000 strong Mac botnet Dr. Web
^Chloe Albanesius, 6 April 2012, Kaspersky Confirms Widespread Mac Infections Via Flashback Trojan, PCMag
^ ab'Half a million Mac computers 'infected with malware''. BBC. April 5, 2012. Retrieved April 5, 2012.
^April 2, 2012, Mac Flashback Exploiting Unpatched Java Vulnerability F-Secure's News from the Lab
^11 April 2012, Apple crafting weapon to vanquish Flashback virus, Sydney Morning Herald
^Kessler, Topher. 'How to remove the Flashback malware from OS X'. CNET.
^ ab'About Flashback malware'. Apple. April 10, 2012. Retrieved April 12, 2012.
^ ab'flashbackcheck.com'. Kaspersky. April 9, 2012. Retrieved April 12, 2012.
^'About Java for OS X Lion 2012-003'. Apple. April 12, 2012. Retrieved April 12, 2012.
^'Mac Security: A Myth?'. eSecurity Planet. April 13, 2012. Retrieved April 16, 2012.
^'It's alive! Once-prolific Flashback trojan still infecting 22,000 Macs'. January 9, 2014. Retrieved January 9, 2014.
External links[edit]
Apple Delays, Hackers Play April 12, 2012
Trojan Spyware Removal For Mac
Retrieved from 'https://en.wikipedia.org/w/index.php?title=Flashback_(Trojan)&oldid=966375624'

0 notes
Text
A Professional Software Development Company in Texas for Your Custom Software Products
What is software development?

The process of Software development encompasses conceiving, identifying, designing, programming, documenting, testing, and bug fixing, frameworks, and so on. In other words, it is a procedure of writing and maintaining the source code. When it comes to a software product to be developed, this process specifically involves computer programming as well as includes a planned and structured process from the conception of the preferred software to its final manifestation.
So we can conclude that Software development in Texas may incorporate research, new expansion, prototyping, variation, reprocess, re-engineering, maintenance, or other actions that result in software products.
There are different major steps involved in the software development procedure such as requirements identification, requirement scrutiny, design, development and execution, testing, deployment, and maintenance.
Business Benefits of Custom Software Development-
Different businesses require different sorts of software products during their life cycle, for example, Human Resources, Finances and Accounts, inventory and stock, Content Management Software for use on company websites, and so on. Custom software benefits can be a great help to you in this case.
Exclusively for you-
It is bespoke which means it is made for your company and its requirements. It is completely flexible to use and effectively fulfill your specifications. Also, you can gain financial benefits that can be associated with it. It doesn’t need any license fees so you can distribute them across your entire company without paying extra.
Access Software Developers-
These professionals will design and code it to integrate properly into your business. As it is rich in features and tools so you can easily operate it. The Software Developers will develop the software and will provide all the best services, including software maintenance and technical help.
Safe and Secure-
We must say that custom made software is more secure as compared to the ones that have been developed in previous years. When you buy it, you can gain administrator rights to the software that ensures that you can modify user-profiles and passwords as per your internal data protection policies.
Adaptable-
It can make your exact business needs and your software developers can add the different procedures that you need into a single, usable application if required. It is possible to be cross-platform suitable.
3 Sorts of software you can have-
System software- It is your operating system, including Windows OS from Microsoft, Mac OS used in Apple MacBook, Apache OS in web servers, and the Linux-based Ubuntu.
Application software- it performs on computers and smartphones, for example, word processing apps, anti-virus, media players, internet browsers, photo editing tools, and SAS products.
Programming languages- It is involved to make software. Only the coders use it to create different required products such as Java, C++, PHP, and Simlab, etc.
Hiring a software development company-
All you just need to find out the best Software Development Company in Texas that provides the best services and meet your specifications. However, choosing the best source for software development is not an easy task, but it is important for the success of your business.
Hence, make sure your hired Software Development Company in Texas provides result-driven software services. Also, you can compare the pricing list of different companies according to your service requirements. Choose the best company that can able to transform your ideas into success.
0 notes
Text
Driver Booster For Mac

Driver Booster 7.5.0.753 Crack With Serial Key Free Download 2020
Free mac driver booster download software at UpdateStar - Let's face it, finding the right device driver or firmware can be a tedious, time-consuming, and often impossible task! DriverGuide was created to make staying up to date a whole lot easier. Mac driver booster free download - Driver Booster, Paragon NTFS for Mac, Apple Mac OS Update 8.6, and many more programs. MacBooster5 (Security Center) will scan malwares, viruses and adwares on Mac and remove them. MacBooster 5 is available in macOS 10.7 or later. And it is free to download MacBooster 5 on CNET. It can fully support for Windows 10, 8/8.1, 7, XP and Vista. Driver Booster for Mac - Free downloads and reviews - CNET Download.com. Driver booster free download - Digidesign CoreAudio Driver, USB Audio ASIO driver, IOXperts USB WebCam Driver, and many.
Driver Booster 7.5.0.753 Crack It is a useful tool that keeps our system up to date. Our system scans automatically after installation and provides you with a complete list of PC drivers with comprehensive information about which ones need to be updated. If an update is required, the driver booster seven can retrieve the required driver from the online database and install it with little effort. Driver Booster with its attractive surface. It can support more than 1,000,000 pilots.
The main product of the Iobit 7 Pilot Booster can help pilots and game components to remain defective and lost in a comfortable and modern form. Driver Booster 7 supports the automatic installation of drivers and components when our computer is idle. The Torrent Booster driver uses six useful tools to solve many common computer problems. It is the easiest way to update hardware drivers and game components to increase the compatibility and stability of our system and save a lot of time and effort.
Driver Booster 7.5.0.753 Crack With Serial Key Free Download 2020
Driver Booster 7.5.0.753 can still record old/faulty/lost game components without problems and accuracy. In particular, Driver Booster helps drivers quickly install parts when the computer is idle. Besides, advanced compression methods, end technologies, scheduled reprogramming, and SSL can be prepared by installing and installing drivers faster, smoother, and more reliably. It’s the easiest way to update device drivers and game components to increase the compatibility and reliability of your systems, and it also offers promising opportunities.
The Serial Driver Booster key creates useful tools to solve many critical computer problems. Still, it includes issues such as hacking, missing audio issues, system problems, incorrect troubleshooting problems, and hardware problems. With a new interactive interface and an extensive database that supports more than 1,000,000 drivers and game components, the driver update program can be powerful and easy to use. It is just a computer program; It is excellent; it offers a beautiful clean screen; New users can also navigate. You can automatically select old drivers and replace them with one click in this application. Compatible with Windows XP / Vista / 7/8/10.
Driver Booster 7.5.0.753 Crack With Serial Key Free Download 2020
Driver Booster Key is just a complete application for downloading updates, installing drivers, and updating and analyzing updates. By clicking Driver Booster of the latest version, outdated, defective, and suitable driver components can also be updated. Driver Booster explicitly supports the installation of drivers and components during computer failures. Driver Cleaners makes downloading, installing drivers more comfortable, more convenient, and more powerful. It also offers six advanced tools to help you troubleshoot common computer problems, including audio tears, noise or system fixes, and device errors.
Driver Booster Crack With Serial Key Free Download 2020
Driver Booster An expert license key can be used free of charge. Particular adware or similar programs are not included (although some virus protection programs may provide notifications after the VirusTotal report. Instead, I have now noticed no “bad” sign). During the installation process, they ask me when you want to use the tools from your IOBit family, but they use all functions for that. Forms and sales promotion of software sharks during this time. It is possible to download the License Pro version, which also increases the download speed.
Main Features:
Develop a new schedule for the driver update log.
New user interface
It is almost installed
Pilots can be removed and returned.
Updated drivers are listed as well as older drivers.
Accepts batch downloads and driver installations
You can automatically create a restore point before you update the driver.
Ready to ignore your device so that no updates appear
You can automatically check for daily, weekly, bi-weekly, or monthly updates.
Ability to demonstrate that pilots only perform WHQL tests.
Downloads are made directly from the program, not from the browser.
There is no limit to the number of drivers that can be downloaded and updated.
Limitation In Free Version:
Probably one of the decisive disadvantages of this free version is perhaps the limitation of the download speed of these drivers, so if there is a lot of software to update, the procedure can be extended. The tool can do the job silently; therefore, in addition to the ability to start automatically after Windows starts, we leave this program for several days, and soon you will perform the tasks. Besides, after each update, a point is generated in the system, and they want to reproduce the improvements.
Driver Booster can be excellent software to help you find drivers that will be updated to the latest version. With nearly 1 million driver databases, obsolete programs/programs can be found and updated easily. With one click, all software needs to be updated.
Keep The Windows Controllers Current With Driver Booster:
Probably one of the most important disadvantages of Windows compared to other programs is the need for software updates, which leads to a growing problem in terms of using the current system drivers. Even if you find some tools to perform this test, Driver Booster Crack 2020 is one of the best in all fields, and it is a free program that automatically detects and installs the drivers for its computers, even the greatest ones. The latest version 5 adds new features.
What’s new in Driver Booster 7.5.0.742 Crack?
What’s new in 7.5.0
Drivers have been added to get the latest new games.
New cleaning improvements for older drivers
Update driver trailer for audio assistance
Add the latest Nvidia Geforce Game Ready driver to get a great game.
Besides, the events towards the yellow point
Moreover, improvements to the driver installation principles
The natural game growth system
Updated driver database with 3.5 million updated drivers
Furthermore, updates for new game drivers
Fresh and reliable driver scanner
Reserved driver database
Additional support for most modern systems, as well as GUI updates
disk driver updates and all developments
DCH the latest pictures and driver assistance
Develop a full-time graduate program
It works automatically with the latest drivers
Adding new sports invitations
Besides, it provides Java Environment 10 and .NET Framework 4.8.
Today, it can automatically solve all problems with audio and improve sound quality.
To clean the registry, many drivers have been added to clean your computer.
The latest IObit vacuum driver supports around 40 languages for customer service.
More, safer, and more honest at work.
It also helps get rid of the most annoying mechanical stories.
It also increases the life of the computer.
Support thoroughly professional staff to support customers
Requirements:
SO: Windows 10/7/8 / XP / Vista
RAM: 2GB
HDD: 1GB
How to crack?
First, download Driver Booster Crack
Install the booster driver
After that, RUN Driver Booster PRO Crack
Generate driver pro Key
Apply the key to activate the program.
Enjoy
Driver Booster 7.5.0 Key New Update
SXDC-FVGB-HNJM-EDRF-GTHY-SXDC
OKDJ-UHYG-TMFN-HBGV-FCDX-SEYG
Driver Booster Pour Mac
Driver booster 7
DF93OW-WEK02-SEDK2-SDKWK
Driver Booster 7.5 key
R093KSW-SKD0W-SDKW-SDKWL
Driver Booster For Mac Free
Driver Booster 7.5 key
DRFKW0-SDK0W-SDKWK-SDKWK
Driver Booster 5 key
ERK0WKS-SDWKSO-SDK0W-SDK0
Driver Booster For Mac
Driver Booster 4 key
SDK0W0S-SDK0W-SDKWO-SDK0W
Mehmed
Driver Booster
5
Driver Booster
Windows-Mac
Softwares
SAN FRANCISCO, May 25, 2017 - IObit today released MacBooster v5.0.0, a well-designed product for Mac OS, which can scan every corner of Mac and remove the junk files. It also protects users’ Mac from malwares and virus attacks.
We all know SSD run faster than Mechanical hard disk. But the price of SSD hard disk is still very expensive. And the SSD hard disk has less disk space. MacBook, MacBook Air and MacBook Pro’s disk space is only 128GB. Obviously 128GB of disk space is not enough to use.
Is Driver Booster A Scam
MacBooster 5 can scan every corner of your Mac and then remove the junk files and duplicates with just one click, free up more disk space for your Mac. And it only selects files that are 100% safe-to-delete, so you will never have to worry about removing the wrong files.
For Malware, we are constantly collecting samples including malwares and viruses. MacBooster5 (Security Center) will scan malwares, viruses and adwares on Mac and remove them.
Driver Booster 7 For Mac
MacBooster 5 is available in macOS 10.7 or later. And it is free to download MacBooster 5 on CNET. It can fully support for Windows 10, 8/8.1, 7, XP and Vista.
About MacBooster 5
MacBooster 5 is an easy-to-use yet powerful system utility for OSX users. Similar to Windows PCs, Mac device also suffer from slow response, over occupied storage, system issues and other privacy risk. MacBooster 5 can help users solve these issues with a simple one-click.
About IObit
Driver Booster 5 Download
Founded in 2004, IObit provides consumers with innovative system utilities for Windows, Mac, and Android OS to greatly enhance operational performance and protect their computers and mobile devices from security threats. IObit is a well-recognized industry leader with more than 100 awards, 500 million downloads and 10 million active users worldwide.
Media Contact: IObit Nicole Qin, (415) 813-2995 PR Manager [email protected]

Driver Booster For Mac
0 notes
Text
Kaspersky Coupon
If you are still unsure about which product to choose then a good place is to start with trial that will give you free antivirus for a limited time. Our bodies are very stingy when it comes storing fat. The start stages of weight loss are probably the hardest for most individuals, since you are unable to really see the good results instantly. Kaspersky coupon code The fact that web business is evolving constantly, most web owners are looking beyond the conventional means to host their website, and in the process seek better service and also save some money. Then there is a CD with the firmware hand, such as installation. This connection can help you to identify a trojan horse, remove it once and for all. For any problems or questions concerning Endpoint Client, please contact your network administrator or Service Provider. Malware developers love exploiting vulnerabilities in Microsoft programs and are always finding new ways of taking advantage of security weaknesses in the world's most popular software titles. Various hosting packages come with different levels of storage. The extract has demonstrated an ability to reduce abdominal fat, increase metabolism and and helps the liver to work more effectively. Absorbs sound, creating quiet areas of your home. What is the best way to find motivation on the days you don’t feel like working out? The stages are carried out in an iterative fashion, with the cycle being repeated until the project's usability objectives have been attained. Can you find discount bridal wears from suppliers who run their stores on the virtual network? The opaque black bags keep sunlight out of the bags . Peppermint (Piperita menthe): it is a highly effective remedy while healing of Irritable Bowel Syndrome. Last week, Apple released Kaspersky promo 2018 a Java update for Mac users, fixing a dozen security flaws, all of which they classified as critical. When you challenge the sales person, what you want to avoid is to become a Kaspersky discount 2018 skeptics. Spyware is software that performs certain tasks on your computer without your consent. If you stay close to their outlet, you can take the device to them personally as they will offer a free diagnostic Kaspersky coupon service. System designers need to carefully consider the system effect values presented in AMCA Publication 201. Enter the required information into the Web Page, and format it as required. The attack is usually Kaspersky discount coupon caused by machines Kaspersky coupon code 2018 that have been compromised by a virus or other malware. The great secret about elliptical training is that the perceived exertion of the exercise is actually less than the calories burned on an elliptical trainer! Poor Support Reliable web hosts will answer support questions timely fashion (within hours) and appropriately, the last thing a customer wants to hear from support when there is a problem with their hosting is "that there is no problem". This coupon code is similar to other past BlueHost coupons that offered a $3.95 monthly rate which is half of their usual rates at $6.95 a month. The key to fat loss is eating enough quality food to provide your body Kaspersky coupon 2018 with adequate nutrients and energy, to prevent hunger, cravings and a lack of energy. Some web hosts just offer email or online ticket support for their hosting services. The SCNS centering on the vital defensive technologies that are the basis of assuring network perimeters, such as firewalls to block unauthorized access, intrusion detection to monitor networks and router security for accessing Kaspersky discount coupon 2018 the router. And if you like to have many range of popular music knowledge, you can begin the installation of FM transmitter in your car so that you can delight in the popular Kaspersky promo code music from any Kaspersky promo range you like. Many homebuyers and sellers choose to work with realtors for this very reason; they can let a professional negotiate terms and deal with tedious paperwork. This is important because an incorrect database can cause potential losses, as you would never be able to pick the right stuff. Grapevine Canyon is extraordinary to see by Laughlin and if the time is right, you might take the family to Las Vegas Ski resort for some snowboarding and skiing. You will not have to kill yourself with exercises that aren’t productive at burning Kaspersky discount fat for your particular body type. A survey has revealed that new threat actors will use sophisticated cyber-crime tools to achieve their own Kaspersky promo code 2018 ends. The matter and information on the pages should be appropriate to the site and should target the area of the public that the website is concerned with. Todays computer users are for the most part unaware that their computers come prepackaged with Antivirus Software that they can use to keep their computers safe from things like malware, spyware and even those nasty little viruses that seem to find their way onto a computer no matter what you do. With these and other reports from major news outlets, no wonder hoodia is creating a buzz among dieters.
4 notes
·
View notes
Photo

10 Best Mobile App Security Testing Tools in 2019
List of Top 10 Mobile App Security Testing Tools
Quick Android Review Kit
Zed Attack Proxy
Drozer (MWR InfoSecurity)
MobSF (Mobile Security Framework)
Android Debug Bridge
Micro Focus (Fortify)
CodifiedSecurity
WhiteHat Security
Kiuwan
Veracode
The number of mobile users around the globe is now estimated at over 3.7 billion. There are about 2.2 million in the Google Play store and 2 billion or more applications in the Apple App Store. As per Flurry, customers nowadays spend approx 5 hours each day on their mobile devices.
Such widespread usage of mobile apps comes with a complete range of new threats attacks formerly not relevant in the classic web app world. The latest research by NowSecure shows that 25% of mobile applications contain approx high-risk vulnerabilities. There are different kinds of vulnerabilities:
Cross-Site Scripting (XSS)
The leak of User Sensitive Data (IMEI, GPS, MAC address, email or credential) over the network
SQL Injection
Phishing Scam Attacks
Missing Data Encryption
Unrestricted Upload of Dangerous File Types
OS Command Injection
Malware
Arbitrary Code Execution
With the growth of mobile applications, delivering a highly secured app is vital to user retention. What can you do to avoid these threats? Fortunately, penetration Testers can help ensure that applications provide data protection.
There are many reasons why app security testing is significant. A few of them are–virus or malware infection, fraud attacks, security breaches, etc. Mobile App Security Testing comprises data security, authorization, authentication, session management, vulnerabilities for hacking, etc.
Hence, from a business point of view, it is vital to perform security testing which requires the best mobile app security testing tool that guarantees that your application is secure.
We have shortlisted 10 Best Testing Tools for Security:
Quick Android Review Kit (QARK)

Quick Android Review Kit” (QARK) was developed by LinkedIn. It is a static code analysis tool and gives information about android app related security threats and gives a concise & clear description of issues. QARK is beneficial for Android platform to discover security loophole in the mobile application source code & APK files.
Features:
It is an open-source tool and provides complete information about security vulnerabilities.
It generates a report about potential vulnerability and provides information about what to do to fix them. It highlights the problems related to the Android version.
It scans all the elements in the mobile app for security threats. It creates a custom app for the purpose of testing in the form of APK and determines the potential issues.
2. Zed Attack Proxy

Zed Attack Proxy is the world’s famous mobile application security test tool. OWASP ZAP is actively managed by hundreds of volunteers globally and is an open-source security testing tool. It is also one of the best tools for pen testers.
Features:
It is available in 20 diverse languages.
Simple to install. It helps in identifying security vulnerabilities automatically in apps during the software development & test phases.
It is an international community-based tool that gives support and comprises active development by universal volunteers.
3. Drozer (MWR InfoSecurity)

It is a mobile app security testing framework that is developed by MWR InfoSecurity. Drozerhelps to determine security vulnerabilities in Android devices.
Features:
It is an open-source tool that supports both actual Android devices and emulators.
It takes very little time to assess Android security-related complications by automating time taking and complicated activities.
It supports the Android platform and executes Java-enabled code on the Android device itself.
4. MobSF (Mobile Security Framework)
MobSF is an automated mobile app security testing tool for iOS and Android apps proficient to perform dynamic, static analysis and web API testing. We can use a mobile security framework for a fast security analysis of Android & iOS apps. MobSF supports binaries (IPA &APK) and zipped source code.

Features:
It is an open-source tool for mobile app security testing.
With the help of MobSF, the mobile app testing environment can be effortlessly set up.
It can be hosted in a local environment, so confidential data never interacts with the cloud.
Faster security analysis for mobile apps on all three platforms (Android, iOS, Windows) Developers can identify security vulnerabilities during the development phase.
5. Android Debug Bridge
Android Debug Bridge or ADB is a command-line mobile app testing tool used to communicate with a device that runs on Android. It offers a terminal interface for controlling the Android device connected to a computer using an USB. Android Debug Bridge can be used to install/ uninstall apps, run shell commands, reboot, transfer files, and more. One can easily restore Android devices using such commands.

Features:
We can easily integrate ADB with Google’s android studio integrated development environment
Real-time monitor of system events. It allows operating at the system level making use of shell commands
It communicates with devices using Bluetooth, WI-FI, USB, etc
6. Micro Focus (Fortify)

Micro Focus majorly delivers enterprise services and solutions to its users in the areas of Security & Risk Management, Hybrid IT, DevOps, etc. It provides comprehensive app security testing services across various platforms, devices, servers, networks, etc. Fortify is one of the smartest security testing tools by Micro Focus which secures mobile applications before getting installed on a mobile device.
Features:
It performs end to end testing using a flexible delivery model.
Security testing comprises static code analysis and a scheduled scan for mobile applications and gives an accurate result.
It helps to identify security vulnerabilities across – networks, servers, and clients.
It supports various platforms like Microsoft Windows, Apple iOS, Google Android, and Blackberry.
7. CodifiedSecurity

It is one of the famous automated mobile app security testing tools to perform mobile application testing. CodifieSecurity discovers and fix security vulnerabilities and make sure that the mobile application is secured enough to use. It provides real-time feedback.
Features:
It follows a programmatic approach for security testing, which guarantees that the test outcomes are scalable and reliable.
It supports both Android and iOS platforms.
It is supported by static code analysis and machine learning. Also supports dynamic and static testing in mobile app security testing
It tests a mobile app without fetching the source code. Files can be uploaded in multiple formats like IPA, APK etc.
8. WhiteHat Security

WhiteHat Sentinel Mobile Express is a security assessment and testing platform offered by WhiteHat Security. Some recognized by Gartner as a leader in security testing and has also won several awards. It offers services like mobile app security testing, web app security testing, and computer-based training solutions, etc.
Features:
It is a cloud-based security platform and offers a quick solution using its static and dynamic technology.
WhiteHat Sentinel supports both iOS and Android platforms. The sentinel platform gives complete information about the project status.
It can easily detect loopholes than any other tool or platform.
Testing is performed on the actual device by installing the mobile application; It doesn’t use any emulators for testing.
9. Kiuwan

Kiuwan provides a 360º approach to mobile application security testing, with the leading technology coverage.
Features:
IT comprises static code analysis & software composition analysis and with automation (in any phase) of the Software Development Life Cycle.
10. Veracode

Veracode provides services for mobile app security to its global customers. Using an automated cloud-based service, it offers solutions for mobile app and web security. Veracode’s MAST (Mobile Application Security Testing) services determine the security glitches in the mobile app and give instant action to execute the resolution.
Features:
It is simple to use and gives perfect security testing results. Healthcare and finance apps are tested deeply, while the simple web app is tested with a simple scan.
In-depth testing is performed using full coverage of mobile app use cases. Veracode Static analysis gives accurate and fast code review results.
Under a solitary platform, it gives multiple security analyses which counts dynamic, static, and mobile app behavioral analysis.
Solutions – How can we help you?
Each of these mobile app security testing tools has its pros and cons. Our expert software testers choose the best security testing tools based on the nature of mobile applications and requirements.
Also, Read- Top 5 Mobile Application Testing Tools
LinkedIn: https://www.linkedin.com/company/impactqa-it-services-pvt-ltd/
Twitter: https://twitter.com/Impact_QA
Facebook: https://www.facebook.com/ImpactQA/
Instagram: https://www.instagram.com/impactqa/
P.S. We are always happy to read your comments and thoughts ;)
#ImpactQA#cybersecurity#security testing services#security testing tools#Security Testing#mobile app testing#Mobile App Test#mobile app security#Software Testing Services#Software Testing Company#software testing tools
0 notes
Text
Chiswick Computers: Keeping Up-To-Date With Updates

Steve Bonnici Chiswick Computers is offering a new remote maintenance service that protects home users against hacking and viruses ‘Failing to install updates on programmes such as Windows, Dropbox, Flash, Java and Adobe means running the risk of being much more vulnerable to viruses and hacks,’ explains Steve Bonnici of Chiswick Computers. ‘Often people just don’t get round to doing it. We see so many victims of hacking: one client lost £200,000 and he had no idea that it had happened!’ To address this common problem, Steve has recently introduced a new remote preventative maintenance service designed specifically for home users. ‘Our package is arranged on a monthly basis and it includes regular software updates, 50GB of online back-up and anti-virus protection. We can’t see the client’s personal data, but we do monitor their system events and, if necessary, alert them to any issues. ‘We compare the programmes on a client’s system against the latest available versions and, if their software is older, we sort out the update automatically. Also, if software has been installed “by the back door” without the client’s knowledge, I get an alert on my watch and can check with the customer and remove the problem. The system works a treat.’ Chiswick Computers has offered comprehensive remote monitoring to corporate clients for many years. ‘For a fixed monthly fee, we’ll install sophisticated software that remotely manages a business computer system, carrying out updates and detecting failures as and when they happen. We have 24/7 access – it’s a preventative alternative to the traditional break/fix scenario,’ explains Steve. Steve and his experienced team of technicians are the local experts when it comes to diagnosing and repairing faults with Windows-based PCs and Apple iMac, MacBook, iPad and iPhones (the company has Which? Trusted Trader status) and they also provide walk-in counter assistance. ‘People ask me if they need to make an appointment and I always say, “we’re a shop, just turn up.” If we can fix something on the spot we will and we’re always happy to give advice. Also, we have a no-fix, no-fee guarantee and we explain everything in plain English!’ Read the full article
#AppleiMac#ChiswickComputers#ChiswickLocals#ChiswickLocalsAutumn2019#chiswickcomputers#ComputerRepairs#computerrepairs#HammersmithLocals#iPad#iPhone#MacBook
0 notes
Text
Macbook Pro Password Recovery Software Download

Note: Resetting Mac password with Recovery Mode will take your Mac to an earlier OS version. Here are three options offered, forgot your password, Mac password isn’t working, and keyboard isn’t working. Reset Mac Password with Another Admin Account. If you have another Mac admin account, you can reset Mac password with the admin. We'll also cover a complete guide to help you securely reset MacBook Pro, MacBook, etc. Without losing any data. Download for Mac Download for PC On this page, you will uncover practical solutions to undelete and restore Mac files after factory reset and an extra guide on how to reset MacBook Pro without losing any data. There are the paid versions and the password recovery software, free download versions which are available. These are usable on Mac, Linux as well as windows password recovery software. Using this Gmail password recovery software or even password of Office, SQL, FTP sites and browsers can be recovered. Aug 08, 2011 Built right into OS X, OS X Recovery lets you repair disks or reinstall OS X without the need for a physical disc. The OS X Recovery Disk Assistant lets you create OS X Recovery on an external drive that has all of the same capabilities as the built-in OS X Recovery: reinstall Lion or Mountain Lion, repair the disk using Disk Utility, restore from a Time Machine backup, or browse the web with.
Macbook Pro Password Recovery Software Download For Windows
Macbook Pro Password Recovery Software Download Windows 10
Apple Macbook Pro Software Download
Macbook Pro Password Recovery Software Download For Pc
Macbook Pro Password Recovery software download, free Memory Card
Firmware Password Macbook Pro
According to many Mac users, it's a common case that they lose Mac files after factory resetting Mac or reinstalling macOS/Mac OS X. On this page, you will learn how to recover files after factory reset Mac or reinstalling macOS using EaseUS Mac data recovery software and other manual methods. We'll also cover a complete guide to help you securely reset MacBook Pro, MacBook, etc. without losing any data.
On this page, you will uncover practical solutions to undelete and restore Mac files after factory reset and an extra guide on how to reset MacBook Pro without losing any data.
Applies to: MacBook Pro, MacBook, MacBook Air, iMac, iMacPro, etc.
Global Nav Open Menu Global Nav Close Menu; Apple; Shopping Bag +.
How Do I Recover Files from My MacBook after Factory Reset?
'Recently, I reinstalled my whole macOS on my crashed MacBook, and then I found some files such as photos and documents are gone after reinstalling macOS.
Is there a way that I can apply to recover files after reinstalling macOS?'

According to most Mac users, reinstalling macOS, Mac OS X, or factory resetting Mac always follows a system crash, computer slowdown, or even when Mac users need to erase their old Mac computer for sale.
Can You Recover Files after Factory Reset Mac or Reinstall macOS? Yes!
Usually, you may lose some of your files on your Mac after the macOS or Mac OS X reinstallation. When you are facing data loss problem, you may wonder whether you can recover files lost due to reinstalling macOS or Mac OS X. The answer is YES!
macOS reinstallation or factory resetting Mac only executes a quick erase of the volume. As a result, it will erase the file directory but does not write any data to the drive, so the original data will not be overwritten.
Firefox for macbook pro. This fact makes it possible to recover files after reinstalling Mac operating system as long as you take quick action.
Macbook Pro Password Recovery Software Download For Windows
Note that you should stop using your computer once your data get lost in case of data overwriting. Follow and learn how to bring your lost Mac files back after reinstalling macOS/Mac OS X on your own.
How to Recover Files After Reinstalling macOS/Mac OS X (3 Fixes)
Accordingly, the viable ways to recover Mac files duet o factory resetting or macOS re-installation depend on whether you have created a backup. And we collected 3 practical ways here for you to try:
Macbook Pro Password Recovery Software Download Windows 10
#1. Run Mac File Recovery Software for Help
#2. Restore from Time Machine Backup from External Disk
#3. Restore from iCloud Backup
The former the file recovery method is presented, the bigger chance you will have in restoring lost Mac data. Based on your situation, pick up the right solution with the tutorial to restore your lost files immediately.
#1. Restore Mac Files after Factory Reset using Mac File Recovery Software
Applies to: Find and retrieve all the files lost after reinstalling macOS or Mac OS X without backup.
When you lost data after factory resetting Mac, reinstalling the latest macOS or earlier Mac OS X, you can eliminate your worries of by using a reliable Mac data recovery software.
Among the numerous Mac data recovery tools, we recommend you try EaseUS Data Recovery Wizard. When it comes to restoring files after reinstalling macOS or Mac OS X, EaseUS Data Recovery Wizard is 100% sure to get your data back.
It can help you scan the Mac hard drive or external storage device to find and retrieve all the files lost after reinstalling macOS or Mac OS X with ease, even you never back up your files. The effectiveness of this method has been proven by its users. Don't hesitate to give it a try.
Steps to Recover Files After Reinstalling macOS/Mac OS X
Step 1. Select the disk location (it can be an internal HDD/SSD or a removable storage device) where you lost data and files. Click the 'Scan' button.
Step 2. EaseUS Data Recovery Wizard for Mac will immediately scan your selected disk volume and display the scanning results on the left pane.
Step 3. In the scan results, select the file(s) and click the 'Recover Now' button to have them back.
Being powerful, secure, and easy-to-use, EaseUS Data Recovery Wizard for Mac is recommended as the best Mac data recovery solution.
You can also apply it to restore more files from the following cases:
Recover files lost due to deletion, formatting, system crash, virus attack, and other data loss situations.
Retrieve data from internal/external hard drive, USB, memory SD card, cameras, and other storage devices.
Recover lost/deleted Microsoft files, photos, videos, music, Adobe files, and other types of files (over 200+).
#2. Restore from Time Machine Backup on External Disk
Applies to: Retrieve lost files due to factory reset Mac from Time Machine backup on an external disk.
The other practical method that you may apply to bring lost Mac files back after factory resetting is to perform Time Machine backup. Free download photo booth mac. If you've created a Time Machine on an external hard drive, congratulations.
You'll perform a full recovery of your lost files on Mac with a 100% success rate. Let's see how to bring your lost Mac files back after reinstalling macOS or Mac OS X.
Restore Factory Resetting Deleted Files from Time Machine Backup
Step 1.Make sure your Time Machine backup external disk is connected to Mac and turned on.
Step 2. Open up Launchpad on Mac, click 'Others'. Find and click the Time Machine icon to enter Time Machine.
Step 3. Use the Up and Down arrows to scroll the timeline, browse the backups which contain your lost files.
Step 4. Find the lost Mac files that you want to recover, and click 'Restore'.
It will automatically recover those lost data from Time Machine on macOS Big Sur/Catalina/Mojave.
After this, you can restart your Mac computer, then you can view and reuse these files where were lost due to reinstalling macOS/Mac OS X again.
#3. Recover Files after Factory Reset Mac from iCloud Backup
Applies to: Sync and restore Mac data from iCloud backup, free.
If you have synced or uploaded important Mac data into iCloud before committing factory reset or macOS reinstallation, you are such a lucky bird. You can easily restore your lost files from iCloud backup.
Steps to Recover Files due to Factory Reset on Mac
Step 1. Visit iCloud.com via your Mac browser, and sign with your Apple ID.
Step 2. Go to Setting and scroll down to the bottom. Click on 'Restore Files' under Advanced.
Tips: To restore contacts, bookmarks, calendars, and reminders from iCloud, click the corresponding option under Advanced.
Step 3. Check the backup files or click 'Select All' if you really need to restore everything. Click the Restore button to recover them.
When you are done with the above tutorial steps, most of your files lost due to factory reset or macOS reinstallation will show up on your computer again.
Bonus Guide: Factory Reset Mac or Reinstall macOS/Mac OS X without Losing Data
Although when you performed a factory reset on Mac, you can restore the lost files when the recommended fixes above. However, it's indeed complex and time-consuming.
Follow the tips in the below, we will guide you through the brief process below to factory reset Mac or reinstall macOS without losing any data.
#1. Back-Up Your Mac Data to an External Device First
It's vital to back up all your data in advance. You can use Time Machine to copy your files to an external disk, or using reliable Mac file backup software for help.
Or you can even manually copy files to an external hard drive one by one.
To save your time and energy, we would like to recommend you try Time Machine or EaseUS Todo Backup.
- Using Time Machine
Pros: ①. Free; ②. Easy to Use;
Cons: You need to select files one by one for back up.
- Using EaseUS Todo Backup
Pros: ①. Easy to Use; ②. 3-step to back up Mac to external disk.
Cons: Not free.
#2. Prepare Mac for Factory Resetting or macOS Reinstallation
Before you start reinstalling macOS or Mac OS X, here are some preparations for you to do in advance:
https://modelload458.tumblr.com/post/653664123969781760/download-java-8-for-mac-yosemite. This site requires JavaScript to be enabled.
1. Deauthorize iTunes
2. Turn off FileVault
3. Disable iCloud
4. Sign out of iMessage
5. Erase Touch Bar Data
When you are done with the preparations, you may now start factory resetting or reinstall your Mac OS X or macOS with the next tip.
#3. How to Reset or Factory Reset MacBook Pro, MacBook, MacBook Air, iMac/iMac Pro
Now, you can follow steps here to start reset your Mac:
Step 1: Reboot Mac in Recovery Mode
Restart Mac and simultaneously hold 'Command and R' keys together to bring up the macOS Utilities window.
Apple Macbook Pro Software Download
Step 2: Erase Mac hard drive
Macbook Pro Password Recovery Software Download For Pc
Open Disk Utility and click 'Continue' > Select your startup disk (Macintosh HD) and click 'Erase' > Choose 'Mac OS Extended (Journaled)' and click 'Erase'.
Step 3: Reinstall macOS on your Mac computer
Repeat Step 1 to bring up macOS Utilities > Click 'Reinstall macOS' > Confirm to reinstall macOS and follow the onscreen instructions to complete the process.
Macbook Pro Password Recovery software download, free Memory Card
When you finish the process, congratulations. You have successfully reinstalled your macOS and the Mac now works like a brand new computer.
#4. Restore Files from Backup
As for the data that you backed up in advance, you can apply Time Machine or EaseUS Todo Backup to bring them back on your Mac with your back up immediately.
Firmware Password Macbook Pro
Conclusion
This page covers 3 practical solutions to help you effectively restore files after factory reset Mac or reinstalling macOS/Mac OS X.
If you didn't create a backup before resetting Mac, take EaseUS Data Recovery Wizard for Mac as emergency rescue. It will fully scan and bring your lost files immediately.
If you are looking for a complete tutorial to reset MacBook Pro, check and follow the guide in the last part on this page. For more data recovery tips, please refer to Mac File Recovery on our site for help.

0 notes
Text
Semalt Expert Specifies Anti-Malware Tips

Malware refers to all forms of harmful software that gets into a computer system often without the knowledge of the owner. Viruses, adware, and spyware are some of the most common malware. Malware can disrupt or slow the computer's operations, steal information, allow unauthorized access to the system's resources, cause frequent crashing or freezing, and many other disruptions.
Malware authors usually trick users into downloading malicious files, and that's why most malware types get into computer systems unnoticed.
It is very important to take the necessary precautions to detect malware and prevent it from infecting and damaging your system.
Jack Miller, the Senior Customer Success Manager of Semalt, defines some reliable ways of doing so:
1. Use up-to-date anti-virus and apply patches
This is one of the most important actions every computer owner/user should do to keep their computers protected from malware infection. Always use up-to-date anti-virus protection and install software updates and patches as soon as they are released.
Using updated anti-virus protection also helps to avoid "drive-by" downloads – scripts on malicious websites that run and install malware secretly.
It's imperative for you to remember that not all sources of patches and updates are trustworthy. Always ensure that you get application software updates from major providers such as Microsoft, Apple, Adobe, and Java.
2. Don't click links or attachments in suspicious emails
Emails have been used to spread malware for so long. Usually, an email used for this purpose will contain malware files as an attachment. The email may also provide a link that takes you to a website and then you'll manually install malware or carry out a "drive-by" download. To avoid malware sent via email:
Do not click links or open email attachments if the email comes from an unknown or untrustworthy source.
Even if you know the source but the email looks suspicious, first contact the sender and confirm what the attachment or link is about.
Never open email attachments ending with .bat, .exe, .vbs, or .com.
3. Beware of social engineering tricks
Social engineering is a technique used to trick a person into taking an action. It is not a bad thing per say, but malware propagators can use it to spread malicious links. They usually use various ways to catch your attention and click a link to a malicious website. Once you visit the site, malware is installed on your system.
Some popular social engineering methods include:
Link baiting – providing teasers to generate interest in the provided content
Popup alerts – popups that inform you that your device has a problem and that for you to fix it, you have to click the alert. The link can lead you into installing software (which is the malware). A "drive-by" download can also be initiated through a popop alert.
Media players – malware can also be spread through media players in this manner: maybe you have visited a website and found an interesting video. But for you to play it, the website tells you that you must install certain media player software. However, in a real sense, you will be installing malware.
You can avoid these tricks by simply not clicking or engaging any popup window that appears. And for media player software, regardless of how enticing the video might be, never install the software recommended there. To keep your device protected, always install software from trusted websites.
4. Use file sharing programs wisely
Files sharing websites and programs can contain malware. You can unknowingly install malware when you install a Peer-to-Peer (P2P) program. Also, you can receive malware disguised as a video or music file for download.
Always ensure that any P2P software you want to install is verified malware free. Also, you should not allow P2P uploading or open any downloaded file before scanning it for viruses.
Cybercriminals will always design harmful software and distribute it to achieve their malicious objectives. Everyone needs to be vigilant about safeguarding their systems.
0 notes
Text
Agriculture - Current Affairs Questions & Answers for Competitive Exams
Agriculture - Current Affairs Questions & Answers for Competitive Exams
General Agriculture Quiz, Agriculture Competitive Exam Questions And Answers, Agriculture Current Affairs 2017 Pdf, General Agriculture Objective Questions Ebook, Agriculture Question Bank With Answers Download, Agriculture Mcq With Answers Pdf, Interview Questions Answers Agriculture, Agriculture Current Affairs 2016 Pdf, Latest Current Affairs And News About Agriculture, Indian Agriculture General Knowledge Pdf , Agriculture General Knowledge Objective Questions, Objective And Practice Questions For Agriculture, Gk Questions: Indian Agriculture, Agriculture Question Answer, GK Quiz, General Knowledge, Agriculture Question Answer, Agriculture GK Quiz, General Knowledge on Agriculture, Objective Agriculture Question and answer, Agriculture Competitive Exam Questions and Answers, Agriculture MCQ Questions Answers, Agriculture Mcq With Answers 2017, General Agriculture Mcq Pdf Dear Readers, Welcome to daily Current Affairs quiz questions with answers on Agriculture. These objective type (MCQ) questions on Agriculture are useful for competitive exams like IBPS, Bank PO, SBI PO, RRB, RBI, LIC, Specialist Officer, Clerk, SSC, UPSC, Railway etc. Try Objective type Question For Agriculture Subject Competition. Covering various important national and international topics, the chosen questions help you improve your general knowledge (GK) and perform the best. Every year mostly 2 or 3 questions from this topic are asked in various competitive exams like SSC, IBPS, Railways etc. Agriculture Question Answer, Agriculture GK Quiz, General Knowledge on Agriculture, Objective Agriculture Question and answer.
Agriculture - Current Affairs Questions & Answers for Competitive Exams
Learn and prepare with these daily current affairs quiz and practice test questions on Agriculture to crack current affairs section of any competitive exam. These questions are from the topic of Indian Agriculture. Questions are very useful for competitive exams and General Knowledge. 1. Red Delicious is a variety of– (a) Apple (b) Guava (c) Mango (d) Papaya (Ans : a) 2. The ratio between marketable crop yield and water used in evapotranspiration is known as– (a) Water use efficiency (b) Consumptive use efficiency (c) Field water use efficiency (d) Economic irrigation efficiency (Ans : a) 3. Which of the following elements is not essential element of plants but proves to be beneficial for some plants? (a) Copper (b) Sodium (c) Boron (d) Iodine (Ans : b) 4. In Jute growing areas the usual alternate crop is– (a) Sugarcane (b) Wheat (c) Cotton (d) Rice (Ans : d) 5. Which one of the following fertilizers is known as ‘Kisan Khad’? (a) Ammonium Sulphate (b) Urea (c) Calcium Ammonium Nitrate (d) None of these (Ans : c) 6. The colour of tomato is due to the presence of– (a) Xanthomonas (b) Anthocyanin (c) Lycopin (d) Carotene (Ans : c) Latest Jobs : Assistant Agricultural Officer Posts 2017 7. The cropping intensity of maize-potato-tobacoo is– (a) 200% (b) 100% (c) 300 (d) None of these (Ans : c) 8. In India post-harvest losses of fruit and vegetable is ………. Per cent of the total production. (a) 25 – 30 (b) 40 – 45 (c) 15 – 20 (d) 50 – 50 (Ans : a) 9. Neelum is variety of– (a) Papaya (b) Mango (c) Grape (d) Apple (Ans : b) 10. Which one of the following is not a primary nutrient? (a) N (b) S (c) K (d) P (Ans : b) 11. TPS technique is related to– (a) Tomato (b) Potato (c) Sugarcane (d) All of these (Ans : b) 12. Where do the female mango leaf hoppers lay their eggs? (a) On the dorsal surface of leaves (b) On the ventral surface of leaves (c) Inside the mid-rib of leaves (d) inside the tissue of leaf margin (Ans : b) 13. Seed rate of American cotton is– (a) 12 kg/ha (b) 20 kg/ha (c) 30 kg/ha (d) 35 kg/ha (Ans : b) 14. ‘First blight’ of sugarcane is due to deficiency of nutrient– (a) Zn (b) Mn (c) Fe (d) P (Ans : b) 15. In India, gene bank of wheat is located at– (a) IARI, New Delhi (b) Karnal (c) Ludhiana (d) Kanpur (Ans : b) 16. ‘Chanchal’ is a variety of– (a) Tomato (b) Brinjal (c) Chilli (d) Capsicum (Ans : c) 17. The Commission of Agricultural Costs and Prices fixes the– (a) Retail price (b) Support price (c) Wholesle price (d) None of these (Ans : b) 18. ‘Pusa Jai Kisan’ is a somaclone of– (a) Basmati rice (b) Indian mustard (c) Citronella java (d) Khesari (Ans : b) 19. SRI is a technique used in– (a) Rice (b) Wheat (c) Maize (d) Groundnut (Ans : a) 20. In maize plants– (a) Tassels appear first (b) Silk appear first (c) Both of these appear at same time (d) None of these (Ans : b) 21 Seed plant technique is followed in– (a) Wheat (b) Paddy (c) Potato (d) Bijra (Ans : b) 22. Citrus tristeza virus is transmitted through– (a) Aphid (b) Plant hopper (c) Thrips (d) Nematode (Ans : b) 23. Parthenocarpy occurs in– (a) Mango (b) Jackfruit (c) Peach (d) Banana (Ans : b) 24. Isolation distance for foundations seed of rice is– (a) 30 metre (b) 50 metre (c) 35 metre (d) 3 metre (Ans : d) 25. Guttation occurs in plants through– (a) Stomata (b) Hydathodes (c) Both (a) and (b) (d) None of these (Ans : c) 26. Sulphur–coated Urea contains N– (a) 30% (b) 40% (c) 21% (d) 26% (Ans : a) 27. Khaira disease of rice can be controlled by spraying– (a) Borax (b) Copper sulphate (c) Zinc sulphate (d) Calcium sulphate (Ans : c) 28. Recording of milk production in dairy farm is done mainly for– (a) Quick selling of milk (b) Increase in production of milk (c) Selection of good producer (d) Ensuring Quality of milk (Ans : c) 29. Ratna is a variety of– (a) Wheat (b) Rice (c) Barley (d) Maize (Ans : c) 30. Which two crops of the following are responsible for almost 75% of pulse production in India? (a) Gram and moong bean (b) Gram and pigeon pea (c) Moong bean and lentil (d) Pigeon pea and moong bean (Ans : b) 31. Milk Sugar is– (a) Fructose (b) Lactose (c) Maltose (d) Sucrose (Ans : b) 32. Blind hoeing is recommended for– (a) Wheat (b) Maize (c) Groundnut (d) Sugarcane (Ans : d) 33. Among the following crop rotations, which is good for increasing soil nutrient status? (a) Sorghum – Wheat (b) Rice – Wheat (c) Pearlmillet – Wheat (d) Groundnut – Wheat (Ans : d) 34. Which one of the following plants belongs to family Anacardiaceae? (a) Orange (b) Papaya (c) Cashewnut (d) None of these (Ans : c) 35. Gynodioecious varieties papaya produce– (a) Only male plants (b) Only female plants (c) Female and hermaphrodite plants (d) Male and hermaphrodite plants (Ans : b) 36. The Green Revolution has mainly been successful for– (a) Rice (b) Wheat (c) Maize (d) Gram (Ans : b) 37. The number of essential mineral elements of plant is– (a) 20 (b) 16 (c) 13 (d) 21 (Ans : b) 38. Damaging stage of potato tuber moth is– (a) Larva (b) Adult (c) Pupa (d) All of these (Ans : a) 39. Vinegar contains, ……….. per cent acetic acid. (a) 10 (b) 5 (c) 20 (d) 15 (Ans : d) 40. Botanically pineapple is a– (a) Pome (b) Berry (c) Baluster (d) Sorosis (Ans : d) 41. Which of the following is glyceride? (a) Coconut oil (b) Kerosine oil (c) Essential oil (d) Catechol (Ans : d) 42. Prabhat is an early short duration variety of– (a) Green gram (b) Black gram (c) Red gram (d) Gram (Ans : c) 43. Rice and wheat has how many stamens? (a) 3, 3 (b) 6, 6 (c) 3, 6 (d) 6, 3 (Ans : a) 44. Greening of potato results in– (a) Increase in nutritional quality (b) Decrease in nutritional quality (c) Increase in disease resistance (d) Decrease in disease resistance (Ans : b) 45. Damping-off disease of vegetable nursery can be controlled by– (a) Solarization (b) Mixing of fungicides in soil (c) Seed treatment (d) All of these (Ans : d) 46. Which one of the following can be suitable for cropping as a wheat mixed crop? (a) Mustard (b) Jowar (c) Cotton (d) Cabbage (Ans : a) 47. Groundnut pegs when developed in the soil form– (a) Roots (b) Stems (c) Tubers (d) Fruits (Ans : d) 48 The optimum cardinal temperature point for germination of rice seeds is– (a) 20°C – 25°C (b) 18°C – 22°C (c) 37°C – 39°C (d) 30°C – 32°C (Ans : a) 49. Numbers of agro-climate and ecological zones classified by ICAR respectively are– (a) 8, 131 (b) 131, 8 (c) 15, 131 (d) 21, 15 (Ans : c) 50. Pink bollworm is a pest of– (a) Mustard (b) Cotton (c) Okra (d) Gram (Ans : b)
v List of Folk Dance Form in India – State Wise For Bank Exam
v Famous Palaces in India
v LIST OF SPACE RESEARCH CENTERS IN INDIA
v Famous Temples in India
v Major Tiger Reserves of India
v Union Territories with their capitals and governing bodies
v Important Indian Towns and Cities situated on River Bank
v List of Longest, Largest, Highest, Tallest Places in the India
v List of Waterfalls in India
v List of First in India
v List of Indian Government Schemes
v India’s Rank on different index 2018
v List of Insurance Joint Ventures in India
v Important Missiles of India
v List of Indian Ambassadors to Foreign Countries
v Thermal Power Stations & Hydro Stations In India
v Major Religions of the World
v Memorial Places of Famous Indian Leaders
v 50 Major Airlines of the World
v Cities and Their Nicknames
v Nick names of Famous Persons & Sportsperson
v Indian Political Parties & their Leaders & Symbols
v State Symbols of India
v Countries visited by Narendra Modi (2014-2017)
v National Parks of India
v Important Museums In India
v Recently Appointed Brand Ambassadors
v All Chief Justices of India Since 1950 Till Date
v Important International Boundary Lines
v Famous Cricket Stadium In World
v Major Lakes in India
v ‘Father of the Nation’ of Different Countries
v Indian Cities and Their Nicknames
v Highest, Longest, Biggest, Largest, Deepest, Smallest of the World & India
v 50 Famous Sports Personalities in India
v List of 29 Indian States and Their Capitals + Chief Ministers in 2018
v National Symbols of India
v Indian Railway Zones Headquarters & Divisions
v List of Bharat Ratna Award Winners 1954 – 2017
v Difference Between Private And Nationalised Banks?
v Khel Ratna, Arjuna & Dronacharya award winners for 2017
v Jnanpith Award Winners 2017
v Man Booker Prize Winners Complete List (1969-2017)
v Agriculture GK Objective Question & Answers MCQ
v Socio – Religious Reform Movements In India
v Best Famous Slogans/Quotes By Indian Freedom Fighters
v Important Wars & Battles in Indian History
v Important Years/Dates in Indian History 1851 to 2010
v Regional Rural Banks ( Sponsors & States )
v List Of National & International Airports In India
v 14 Major Seaports in India, Indian Sea ports
v Joint Military Exercises Of Indian Army With Other Countries 2018
v Bank, Headquarters, Tagline/Slogan & Their Chairman/Head 2018
v CEOs, MDs & Heads of Indian Banks 2018
v Foreign Banks in India And Their Headquarter 2018
v Heads of Important Offices in India :Latest
v Important Indian Organisations And Their Headquarters 2018
v List of 35 UNESCO World Heritage Sites in India
v List of Folk Dance Form in India – State Wise For Bank Exam
v Famous Palaces in India
v LIST OF SPACE RESEARCH CENTERS IN INDIA
v Famous Temples in India
v Major Tiger Reserves of India
v Union Territories with their capitals and governing bodies
v Important Indian Towns and Cities situated on River Bank
v List of Longest, Largest, Highest, Tallest Places in the India
v List of Waterfalls in India
v List of First in India
v List of Indian Government Schemes
v India’s Rank on different index 2018
v List of Insurance Joint Ventures in India
v Important Missiles of India
v List of Indian Ambassadors to Foreign Countries
v Thermal Power Stations & Hydro Stations In India
v Major Religions of the World
v Memorial Places of Famous Indian Leaders
v 50 Major Airlines of the World
v Cities and Their Nicknames
v Nick names of Famous Persons & Sportsperson
v Indian Political Parties & their Leaders & Symbols
v State Symbols of India
v Countries visited by Narendra Modi (2014-2017)
v National Parks of India
v Important Museums In India
v Recently Appointed Brand Ambassadors
v All Chief Justices of India Since 1950 Till Date
v Important International Boundary Lines
v Famous Cricket Stadium In World
v Major Lakes in India
v ‘Father of the Nation’ of Different Countries
v Indian Cities and Their Nicknames
v Highest, Longest, Biggest, Largest, Deepest, Smallest of the World & India
v 50 Famous Sports Personalities in India
v List of 29 Indian States and Their Capitals + Chief Ministers in 2018
v National Symbols of India
v Indian Railway Zones Headquarters & Divisions
v List of Bharat Ratna Award Winners 1954 – 2017
v Difference Between Private And Nationalised Banks?
v Khel Ratna, Arjuna & Dronacharya award winners for 2017
v Jnanpith Award Winners 2017
v Man Booker Prize Winners Complete List (1969-2017)
v Agriculture GK Objective Question & Answers MCQ
v Socio – Religious Reform Movements In India
v Best Famous Slogans/Quotes By Indian Freedom Fighters
v Important Wars & Battles in Indian History
v Important Years/Dates in Indian History 1851 to 2010
v Regional Rural Banks ( Sponsors & States )
v List Of National & International Airports In India
v 14 Major Seaports in India, Indian Sea ports
v Joint Military Exercises Of Indian Army With Other Countries 2018
v Bank, Headquarters, Tagline/Slogan & Their Chairman/Head 2018
v CEOs, MDs & Heads of Indian Banks 2018
v Foreign Banks in India And Their Headquarter 2018
v Heads of Important Offices in India :Latest
v Important Indian Organisations And Their Headquarters 2018
v List of 35 UNESCO World Heritage Sites in India
Read the full article
#AgricultureCompetitiveExamQuestionsAndAnswers#AgricultureCurrentAffairs2016Pdf#AgricultureCurrentAffairs2017Pdf#AgricultureGeneralKnowledgeObjectiveQuestions#AgricultureGKQuiz#AgricultureMCQQuestionsAnswers#AgricultureMcqWithAnswers2017#AgricultureMcqWithAnswersPdf#AgricultureQuestionAnswer#AgricultureQuestionBankWithAnswersDownload#GeneralAgricultureMcqPdf#GeneralAgricultureObjectiveQuestionsEbook#GeneralAgricultureQuiz#GeneralKnowledge#GeneralKnowledgeonAgriculture#GkQuestions:IndianAgriculture#GKQuiz#IndianAgricultureGeneralKnowledgePdf#InterviewQuestionsAnswersAgriculture#LatestCurrentAffairsAndNewsAboutAgriculture#ObjectiveAgricultureQuestionandanswer#ObjectiveAndPracticeQuestionsForAgriculture
0 notes
Text
How To Uninstall McAfee Antivirus Plus 2012
Windows Defender protects your Computer or laptop from spyware and other potentially undesirable programs. It may well surprise you but Macs currently have antimalware built in, courtesy of Apple. Get your computer software from the Mac App Store or from developers you know and trust. Active firewall or antivirus software program may possibly avoid Java from installing effectively. Keep in mind to turn your firewall or antivirus free mac antivirus https://cyberbyte.org software program back on when you have effectively completed the Java set up. Hold Windows updated. The ideal way to keep your pc protected is to often make certain that your copy of Windows is up to date. Microsoft releases safety updates for Windows on a typical basis, fixing exploitable regions of Windows. If you've a mix of Windows PCs, Macs and Android devices, then AVG Totally free Antivirus 2016 is a actual timesaver as it functions across all your devices to keep all your family's devices safe. If you loved this short article and you would want to receive more info with regards to please click the following internet site please visit the web site. Run Anti-Malware and install any obtainable updates. You'll be prompted to check for updates when Anti-Malware starts for the initial time. Download and install any accessible updates just before starting your scan. When you launch ClamXav for the very first time, it will prompt you to download the most current virus definitions. This could take a although, based on your net speed and the size of thecvd file that the app makes use of to scan your files. We can see that the registry crucial HKLMSOFTWAREMicrosoftCryptographyRNGSeed has been changed two times and there are also some other registry keys, which probably don't belong to our , but the World wide web Explorer. Windows creates the prefetch file when running an application. A prefetch file consists of the details about the files loaded by the application. The operating system utilizes prefetch files to load the application more quickly the subsequent time it is being run. We can view the prefetch files with the WinPrefetchView. The image under shows us the contents of the METERPRETER prefetch file contained in the C:WINDOWSPrefetch directory. Some viruses capture keystrokes, enabling criminals to view user names and passwords as they are typed, even though other folks enable criminals to manipulate computers from afar. Some receive identifying information from shadow Web addresses that mimic a bank's Web website, persuading customers to log on. With smartphones and tablets becoming a lot more effective and much more common each day, it's crucial to bear in mind that, like PCs and laptops, it really is attainable to come across viruses and malware on mobile devices. Disable automatic updates. You'll do this in the exact same way in which you disabled Real-Time Scanning and the Firewall. I'd say that if you are employing your Mac at house, mostly for non-company purposes, you can close this post and continue to operate with no safety application. Yes, it is a risk. But using the internet is a risk, and in my deemed view running a Mac with out AV is a worthwhile calculated risk.
0 notes
Text
Fending Off Viruses, Malware
Asking yourself regardless of whether you need to have antivirus software program to protect your Mac? Bug Net chronicles the faults of scores of well-liked applications in its standard bulletins and offers fixes and links to downloadable updates. Considerably of Bug Net's value is in its subscription-primarily based penetration test service, but the Net site maintains an archive of substantial articles that you can search and study free of charge. Even though macOS Sierra has but to get fairly as notification-content as iOS, we recommend taking some time to handle this section of Program Preferences. Turn off banners and get apps out of Notification Center if you don't need notifications from them and for these factors you do require notifications from, minimise them anytime possible. If you're ready to see more information on penetration Test Service look into our own web site. If you are simply distracted but get a lot of email, for instance, it is a intelligent move to cease Mail notifying you with a banner every time a new message comes in, but you could usually leave the app icon's badge setting active, to provide an at-a-glance indication of how several unread emails you have. As a reminder, we want to set up an isolated network containing our three VMs. This network will not be in a position to access the Web. Also, we want the evaluation machine to act as a network gateway to the victim machines in order to easily be capable to intercept the network traffic and to simulate a variety of solutions such as DNS or HTTP. Although this highlights the risks connected with applications in the cloud, it is not the only security danger connected with Twitter. In addition there are dangers with folks spoofing other identities, dangers of individuals disclosing sensitive information and folks creating risks by speaking about some of their activities. Clear out old Mail downloads: If you use Apple Mail, attachments and other random files can fill your challenging drive up rapidly with no you realizing it. Open up Spotlight (press Command+Space), then variety in 'œMail Downloads.' Tap Enter on the folder that pops up. This folder may well have hundreds of items. These are all the a variety of attachments Mail has downloaded over the years. Assuming you are not employing a POP e-mail server, which doesn't retain old copies following they are downloaded, you can safely delete each and every file inside this folder and they will stay on email server. Each free of charge and paid-for anti-virus products have the very same fundamental computer software components, and offer you the exact same level of core protection. In other words, the free version is not a weaker version of the commercial providing. But paid-for versions do offer you further attributes, which can contain protection against potentially dangerous websites, email protection, anti-spam, a firewall and phishing protection. There can be other bonuses as well, such as automatic updates and totally free technical help. It initially looked like the outbreak was just another cybercriminal taking benefit of cyberweapons leaked on the internet. However, safety experts say that the payment mechanism of the attack seems too amateurish to have been carried out by severe criminals. Firstly, the ransom note consists of the same Bitcoin payment address for every victim - most ransomware creates a custom address for each and every victim. Secondly, the malware asks victims to communicate with the attackers by way of a single e mail address which has been suspended by the email provider after they found what it was getting employed for. This implies that even if an individual pays the ransom, they have no way to communicate with the attacker to request the decryption crucial to unlock their files. And Mac customers are also vulnerable to any attacks that do not target the OS in specific. For instance, Macs can nevertheless be compromised by browser-based attacks, man-in-the-middle attacks, fraudulent site redirects, phishing attempts, Adobe Flash and Java vulnerabilities, and much more. The operating method may well be also little of a target for virus authors, but that does not imply it's one hundred% protected. Download files with recognized viruses. One particular of the most popular techniques for viruses to be spread is by way of pirated media and application. Look for "cracks" or "serials" for well-liked programs that need a file to be run. These files usually include viruses that execute when your run the crack program. Some thing to bear in mind. The computer software listed below will safeguard your laptop from viruses, but it won't typically offer you the identical level of functionality as paid-for world wide web safety software program. Even though some cost-free software program does consist of extras, if there is a distinct function you want such as Wi-Fi protection or secure purchasing, it's worth checking both free of charge and paid-for possibilities before producing a option. Run it as element of your regular Mac cleanup habit, and you will catch the most frequent malware developed for the platform. If you want ongoing protection, think about Avira Just know that continuously-operating antivirus application could potentially slow down your technique, which is the opposite of what we're going for here.
0 notes
Text
How To Turn On Windows Defender
Malware is short for malicious computer software. It really is sensible to stay offline whilst your antivirus program is disabled. You can delete files manually, or set up a utility (we recommend some in that guide) to do a deeper search and make the job faster and simpler. There is a correct way and a incorrect way to use these programs, although. The largest shake-up in Pc security for years came with Microsoft's launch of Windows eight. As opposed to previous versions, it came with lots of safety functions integrated into the operating technique. iOS antivirus software program does not exist. Despite the fact that not shown in this chart, all ten threats had been uploaded to Metascan On the internet over a year ago. Even following so considerably time has passed, these threats are nevertheless infecting files these days. If you have multiple Apple devices and want to use Safari to save your passwords, then you can use iCloud Keychain to synchronise your passwords from one particular device to another. So if you enter a password into a site on your iPhone, it will automatically be added to your iPad. Java has had a bit of a kicking in current times, with massive failures in its security causing a lot of issues. One of the most sensible items you can do is disable Java from running in browsers, which signifies you can still run standalone Java-based apps, but your browser will not run this content material on the internet. To do this go to the Manage Panel and select Java from the Classic view. Click the Safety tab and deselect the 'Enable Java content in the browser' tickbox. Click OK to apply the setting. If you are you looking for more on free windows Antivirus https://cyberbyte.org take a look at our web page. You'll be warned that you'll need to restart your browsers for the changes to take effect. Get a wired mouse. Wireless mice are hackable, as they have a virtual wire and communicate via a signal that could be intercepted, whereas wired mice have a physical wire and they can not be hacked. If you are already using a wired mouse, then someone has manage of your pc remotely. You ought to almost certainly invest in a excellent anti-virus software to make certain that your computer is clean of all viruses. If this doesn't do anything, then you are greater off factory-resetting your computer. This point is critical. You should not be paying to eliminate Mac computer software - ever. You shouldn't pay to eliminate malware. In truth, we'd go so far to recommend that you should not put your credit card particulars into any plan or website that claims to be in a position to fix your pc. Mac users have access to a nifty constructed-in feature that acts as a virtual shredder. It is called safe empty trash," which overwrites the data you want to delete, creating it primarily impossible to recover, said Wealthy Mogull, an analyst and chief executive officer of Securosis, an independent safety research and advisory firm. (Go into the Finder menu on the top of the screen, and pick Safe Empty Trash.") He stated there was nevertheless some threat if the file had been saved on Time Machine — the Mac's backup technique — but he said the odds were low that an attacker would look there. You may require to restart your pc as soon as the update has downloaded. You can count on a common 460MB download to take about eight minutes (for the duration of which time you will still be capable to function) but for a large update you will have to restart and install and that could take as considerably as 20 minutes, bringing the total set up time to about 25 minutes in total. We can see that the registry essential HKLMSOFTWAREMicrosoftCryptographyRNGSeed has been changed two instances and there are also some other registry keys, which almost certainly never belong to our , but the World wide web Explorer. free windows antivirus https://cyberbyte.org creates the prefetch file when running an application. A prefetch file consists of the info about the files loaded by the application. The operating system uses prefetch files to load the application faster the subsequent time it is becoming run. We can view the prefetch files with the WinPrefetchView. The image beneath shows us the contents of the METERPRETER prefetch file contained in the C:WINDOWSPrefetch directory. Shopping for a new Pc can be considerably a lot more rewarding than buying for a Mac, most of which are far more or significantly less preconfigured by Apple. And customizing a Pc you currently purchased is an entirely various knowledge than making a Mac your personal.
0 notes
Text
Kaspersky Coupon Code
If you are still unsure about which product to choose then a good place is to start with trial that will give you free antivirus for a limited time. Our bodies are very stingy when it comes storing fat. The start stages of weight loss are probably the hardest for most individuals, since you are unable to really see the good results instantly. Kaspersky coupon code The fact that web business is evolving constantly, most web owners are looking beyond the conventional means to host their website, and in the process seek better service and also save some money. Then there is a CD with the firmware hand, such as installation. This connection can help you to identify a trojan horse, remove it once and for all. For any problems or questions concerning Endpoint Client, please contact your network administrator or Service Provider. Malware developers love exploiting vulnerabilities in Microsoft programs and are always finding new ways of taking advantage of security weaknesses in the world's most popular software titles. Various hosting packages come with different levels of storage. The extract has demonstrated an ability to reduce abdominal fat, increase metabolism and and helps the liver to work more effectively. Absorbs sound, creating quiet areas of your home. What is the best way to find motivation on the days you don’t feel like working out? The stages are carried out in an iterative fashion, with the cycle being repeated until the project's usability objectives have been attained. Can you find discount bridal wears from suppliers who run their stores on the virtual network? The opaque black bags keep sunlight out of the bags . Peppermint (Piperita menthe): it is a highly effective remedy while healing of Irritable Bowel Syndrome. Last week, Apple released Kaspersky promo 2018 a Java update for Mac users, fixing a dozen security flaws, all of which they classified as critical. When you challenge the sales person, what you want to avoid is to become a Kaspersky discount 2018 skeptics. Spyware is software that performs certain tasks on your computer without your consent. If you stay close to their outlet, you can take the device to them personally as they will offer a free diagnostic Kaspersky coupon service. System designers need to carefully consider the system effect values presented in AMCA Publication 201. Enter the required information into the Web Page, and format it as required. The attack is usually Kaspersky discount coupon caused by machines Kaspersky coupon code 2018 that have been compromised by a virus or other malware. The great secret about elliptical training is that the perceived exertion of the exercise is actually less than the calories burned on an elliptical trainer! Poor Support Reliable web hosts will answer support questions timely fashion (within hours) and appropriately, the last thing a customer wants to hear from support when there is a problem with their hosting is "that there is no problem". This coupon code is similar to other past BlueHost coupons that offered a $3.95 monthly rate which is half of their usual rates at $6.95 a month. The key to fat loss is eating enough quality food to provide your body Kaspersky coupon 2018 with adequate nutrients and energy, to prevent hunger, cravings and a lack of energy. Some web hosts just offer email or online ticket support for their hosting services. The SCNS centering on the vital defensive technologies that are the basis of assuring network perimeters, such as firewalls to block unauthorized access, intrusion detection to monitor networks and router security for accessing Kaspersky discount coupon 2018 the router. And if you like to have many range of popular music knowledge, you can begin the installation of FM transmitter in your car so that you can delight in the popular Kaspersky promo code music from any Kaspersky promo range you like. Many homebuyers and sellers choose to work with realtors for this very reason; they can let a professional negotiate terms and deal with tedious paperwork. This is important because an incorrect database can cause potential losses, as you would never be able to pick the right stuff. Grapevine Canyon is extraordinary to see by Laughlin and if the time is right, you might take the family to Las Vegas Ski resort for some snowboarding and skiing. You will not have to kill yourself with exercises that aren’t productive at burning Kaspersky discount fat for your particular body type. A survey has revealed that new threat actors will use sophisticated cyber-crime tools to achieve their own Kaspersky promo code 2018 ends. The matter and information on the pages should be appropriate to the site and should target the area of the public that the website is concerned with. Todays computer users are for the most part unaware that their computers come prepackaged with Antivirus Software that they can use to keep their computers safe from things like malware, spyware and even those nasty little viruses that seem to find their way onto a computer no matter what you do. With these and other reports from major news outlets, no wonder hoodia is creating a buzz among dieters.
0 notes