Self Taught Cybersecurity student! Main focuses (for now) are Blue Team. OSINT and Malware Analysis are becoming my specialties, looking to learn more and connect with any other Cybersecurity folk like me!
Don't wanna be here? Send us removal request.
Text
Ok Boomer Malware Analysis Part 2
First, I downloaded the pcap file from https://www.malware-traffic-analysis.net/2019/11/12/index.html and extracted the .zip file. I also downloaded the pdf answer sheet, just to have something to refer to if I got stuck.
Continuing off from Part 1
What is the user account name used to log into the Windows host at 10.11.11.200?
The account name is brandon.gilbert
I first filtered out the ip address, 10.11.11.200 by selecting the filter in the “Endpoints” tab (Part 1 goes into detail on filtering out ip addrs and protocols).
The next part I add to do some googling...I found that a user account name can be found using the CNAME string/filter. This string can be found under Kerberos, an authentication protocol (Port 88).
Note: What I found via Google: A Canonical Name or CNAME record is a type of DNS record that maps an alias name to a true or canonical domain name. The CNAME is directly points to another name, not the IP address.
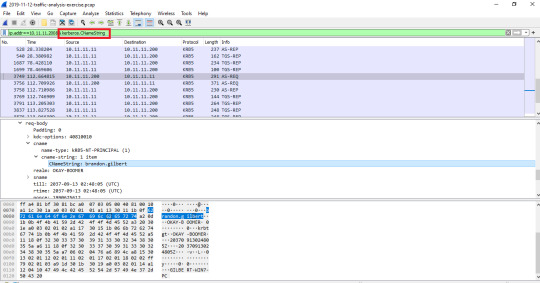
After adding the ip address filter, I added “&& kerberos.CNameString” as seen in the screenshot above. In the screen under the packet information, scroll down until you see Kerberos, press the arrow and you see another tab that reads “req-body”. Open that tab and scroll down until you see “addresses”. This will also have something like: 1-item GILBERT-WIN7. I guessed that was the PC host name.
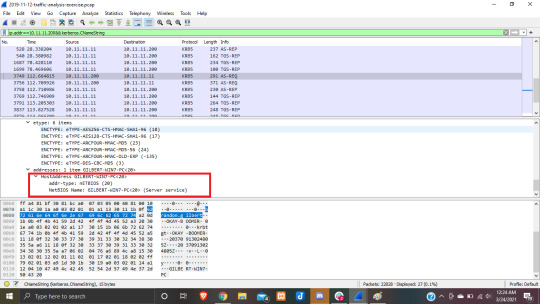
I actually found the user name in the third window here the hex values are!
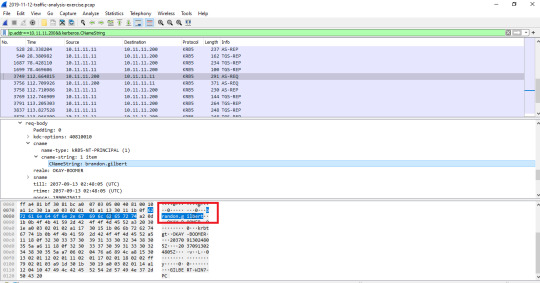
I clicked “brandon.gilbert” and it led me to this screen:

You can see it led me directly to the CNameString which allowed me to find the user brandon.gilbert.
What operating system and type of device is on 10.11.11.217?
Using the same method as I have with the previous questions like this, I was able to find that the device is an iPad. The OS however, I had to google as well lol.

It turns out the OS is ipadOS version 13.2.2.
What IP is the Windows host that downloaded a Windows executable file over HTTP?
This one took me a while, but my first action was typing http && ip contains “program” into the display filter bar. No luck.
I decided to play around with the filter I typed for a bit and deleting http && , showed me that ip contains “program” still came up green. I hit enter and a single packet shows. The answer is the destination: 10.11.11.203

If we look under Internet Protocol Version 4, we can see the Source and Destination IP addresses. The Source being where the executable was downloaded from, the Destination being where the executable was sent to.
What is the URL that returned the Windows executable file?
Staying on the same packet, no new filters or anything, I Follow TCP Stream and found the host to be: acjabogados.com. That’s the host page but I need the whole URL.
In the TCP stream, the first line should be: GET /40group.tiff HTTP/1.1. In HTTP, GET is used to request data from a specified resource.
So when we combine the host and the GET request from /40group.tiff, we get our URL, acjabogados.com/40group.tiff
What is the SHA256 file hash for that Windows executable file?
Start by going to the File tab and go down to ‘Export Objects’ then choose ‘HTTP’. You’ll get a long list but I filtered out what I needed by typing the first letters of that link I found. It’ll filter everything out with the first 3 letters.
So we’ll export that and save it into wherever, I saved it into the folder I made for this malware analysis.
From there, you now have a .tiff file!
Now we will be using Command Prompt (WOOO). Using ‘sha256′ and the file you saved. go into command prompt and type:
sha256 -a 256 [insert .tiff here]
it should return the 256 hash of the file. I got: 8d5d36c8ffb0a9c81b145aa40c1ff3475702fb0b5f9e08e0577bdc405087e635
What is the detection rate for that SHA256 hash on VirusTotal?
Using VirusTotal, copy your SHA256 hash and paste it into the search bar on VirusTotal. It will give you a detection rate, not sure if it will change later on but I got a: 58 out of 71 detection rate.
What public IP addresses did that Windows host attempt to connect over TCP after the executable file was downloaded?
I referred to the notes given on the Malware-Traffic-Analysis to help me find out this one. Using the filter given on the notes:
ip.addr eq 10.11.11.203 and !(ip.dst eq 10.11.11.11)
I had looked for failed connections as he question did ask for the IP addresses that the host ATTEMPTED to connect. I found some packets that had TCP retransmission. They were also dark and dark = error or something like that. these 2 IP addresses were the only IPs with the retransmission:
5.188.108.58 and 138.201.6.195
What is the host name and Windows user account name used on that IP address?
Using the IP address that downloaded the .tiff file, 10.11.11.203, we can get the user that downloaded the file. Using the CNAME string, we can find this user.
The CNAME string is associated with Kerberos on Wireshark. I learned more about this filter here.
From there, I was able to find out that our Host is: Tucker-Win7-PC and our user is candice.tucker.
I was able to learn plenty in navigating on Wireshark and building a methodology on tracing back on what was downloaded where and just navigating on traffic altogether.
Thanks for checking out my analysis!
0 notes
Text
OK Boomer - Malware Analysis Part 1
PCAP Enviornment: LAN segment range: 10.11.11.0/24 (10.11.11.0 through 10.11.11.255) Domain: okay-boomer.info Domain controller: 10.11.11.11 - Okay-Boomer-DC LAN segment gateway: 10.11.11.1 LAN segment broadcast address: 10.11.11.255 Note: Before I start, I recommend that you use a VM (Virtual Machine) before you start opening malware 'n stuff on your computer.
First, I downloaded the pcap file from https://www.malware-traffic-analysis.net/2019/11/12/index.html and extracted the .zip file. I also downloaded the pdf answer sheet, just to have something to refer to if I got stuck. Pcaps are great for beginners, first, because they are audit logs of network traffic. Second, there's no actual malware that can damage your OS!
But still....use a VM.
What operating system and type of device is on 10.11.11.94?
Answer: Chrome OS and the device is a Chromebook
To get to this answer, I had to filter out the ip address given to me.
You can simply type: (http) && (ip.addr==10.11.11.94) into the bar on Wireshark. To reach that filter, you need to start in the ‘Statistics’ drop down menu. Select Statistics, Protocol Hierarchy. From there scroll down until you see Hyper Text Transfer Protocol or HTTP and right-click, apply filter, “Selected”.
After applying this filter, go back to the Statistics menu and select Endpoints. Look for the ip address given and right-click, “apply filter” and choose “..and selected”, this will add on this filter to the HTTP filter added before.
From there, we can see all http activity that is involved with our given ip address.
To find the device, right click any of the packets and right click, you should see “Follow”, go to follow and select “TCP Stream”. TCP stream will show us the Device and OS. You should see this:

And there’s your OS and device. CrOS is the Chrome (Cr) Operating System (OS) and the CrOS runs on the Chromebook.
Fun Fact! The Red shows info coming from the source whereas the Blue shows us the response from the server.
What operating system and type of device is on 10.11.11.121?
This is pretty much doing the same thing we did for the previous question. So rinse, repeat and
Answer: Samsung Galaxy Note 8

So from the image, Wireshark shows us that it’s an Android 9; Samsung SM-N950U. I googled this and narrowed it down to SM-N950U which came up as the Galaxy Note 8.
Based on the MAC address for 10.11.11.145, who is the manufacturer or vendor?
To find the manufacturer is in the open I realized while searching haha...
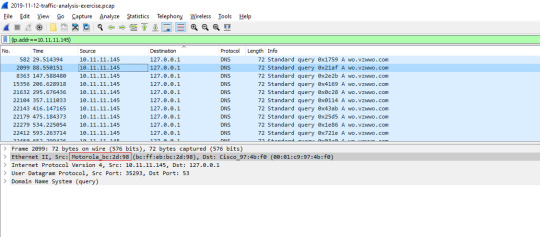
It’s Motorola.
What operating system and type of device is on 10.11.11.179?

Answer: The OS is the Mac OS X 10.15.1 (I googled to find it is the Catalina update, the 16th major release update) this runs on a Macbook which is the Macintosh.
What version of Windows is being used on the host at 10.11.11.195?
Answer: Windows 10 (Windows NT = Windows 10)

While I was searching and going through all the notes I made in regards to the filters I found that you can find the answer without having to follow the TCP stream. you can click the arrow where HTTP is and it will show you it to haha ( It’s pretty hard explaining it so I put a picture below to show what I mean)

So, I’m officially halfway done and I’m stopping here. I’ll post Part 2 once I start working on this again. But yeah I hope this kind of helps in understanding how packet analysis works. I’m trying my best in including my steps and the writing this in a way that is similar to how I think.
0 notes
Text
Objectives of Malware Analysis
The goal of malware analysis is identify the type of malware and the entire scope of what it can do. When identifying the malware, we want to find whether is a Keylogger, Spyware, Trojan, RAT Trojan, etc. We also want to find it’s purpose, was it an intentional attack (targeted attack) or a phishing attack and how it communicates to the attacker.
In the malware, we can exfiltrate useful data like filenames. This can be used to generate signatures that can be used for future detection.
More information on the topic can be found here:
https://cloudshark.io/articles/using-packet-captures-in-malware-analysis-webinar/
I have also been downloading some pcap files for practice here:
https://www.malware-traffic-analysis.net/
Note: Some of the files can have ACTUAL malware on it. I used the exercise “OK Boomer” for starters. It is pretty good in learning the basics of packet analysis.
1 note
·
View note