Text
Three Ways You Can Keep HIPAA Security Compliance

To begin understanding compliance, healthcare organizations would be wise to consider three key recommendations. 1. Analyze the past to avoid making the same mistake twice It is important for hospitals and healthcare facilities to look at some of the common mistakes that are repeatedly noted in HIPAA security reviews. HIPAA states that out of all the reviews completed, there are a number of frequent compliance violations and issues that are found each year. This includes impermissible uses and disclosures of protected health information, lack of safeguards to protect health information, lack of patient access to their personal health information, lack of administrative safeguards on electronic protected health information, and use or disclosure of more than the minimum protected health information. Protecting valuable data by analyzing past mistakes is an important step in the compliance process. 2. Perform a risk assessment and gap analysis One preventative measure in assessing an organization’s compliance with HIPAA is a risk analysis and a gap analysis. The confusion and lack of understanding around the two examinations has been common among healthcare professionals in the marketplace for some time. Not understanding the differences can be detrimental to an organization, and puts them at a significantly higher risk. According to HHS and Office for Civil Rights (OCR) guidelines, all healthcare organizations must specifically conduct a risk analysis to be considered within HIPAA compliance. A HIPAA gap analysis can be used to measure the organizations information security standing against HIPAA, which is part of HHS audit protocol. Comparing the organization’s current practices to the HHS OCR audit protocol will identify the strengths and weakness of the security program. From there, the organization can determine whether they have reasonable and appropriate administrative, physical, and technical safeguards in place to protect patient health. Performance of the gap analysis also allows the organization to develop an audit response toolkit which includes the data and documentation that would be able to support compliance with the HIPAA regulations to regulatory agencies. 3. Develop an action plan and a response toolkit For many healthcare organizations, the question is not if they will receive a HIPAA audit or an OCR investigation, but when. The OCR, which is responsible for completing HIPAA audits, will contact the organization. The OCR will further ask for a variety of documents and data. Once these documents and data are reviewed, the OCR will send the organization a preliminary copy of its findings. This preliminary report gives healthcare organizations the opportunity to respond to the OCR, and have its responses included in the final report.From the final report, the OCR will determine if an organization was in compliance of HIPAA and, if not, where an organization was lacking. If an organization was not in total compliance, the OCR will provide corrective action and technical assistance the organization can use to work toward compliance. Developing an action plan and evaluating the organization’s information security against the OCR audit protocol to develop an audit response toolkit will leave organizations with practical actions that serve their best interest, eliminate mistakes, and mitigate risk. Read More about HIPAA violations are expensive. SecurEnds product performs user access reviews and audits as required by HIPAA compliance. https://www.securends.com/fulfill-hipaa-compliance/
0 notes
Text
Cloud Infrastructure Entitlement Management (CIEM)

Cloud Adoption
is at an all-time high and enterprises around the world are adopting a ‘cloud first’ strategy. Along with that, there is a dramatic increase in the number of organizations getting breached in the cloud space – and majority of those breaches had something to do with Identities and its related entitlements.
What is CIEM?
CIEM Solutions focuses on
IAM Governance
, mainly by reducing the risk of over-privileged identities in a dynamic multi-cloud infrastructure. CIEM mitigates the risks associated with privilege escalation, compromised credentials and other suspicious access activities by providing deep visibility into cloud entitlements and access risks.
Core CIEM Capabilities:
Visibility and Inventory:
Inventory of all Human and Machine Identities across Multi Cloud
View Overall IAM Compliance Score by Cloud Account or Account Groups
Detect identities and resources with excessive permissions and entitlements
View and monitor Access Key usage
Deep visibility into entitlements and access patterns.
Auditing:
Timeline view of changes to sensitive resources
Track recent access changes across cloud infrastructure
Track user activities generate audit reports
View traffic patterns in the network
Audit granular permissions of IAM users, roles and service accounts.
Governance:
Enforce predefined and custom IAM policies
One Click Remediation for unused entitlements
Right size roles across cloud service providers
Diagnose and fix IAM failures.
Reporting:
Generate IAM Compliance reports
Generate IAM Executive Summary reports
Generate Activity Audit Report for Human and Machine users
Generate User Entitlements reports.
The SecurEnds Approach to CIEM
SecurEnds is launching its
SecurEnds Access Control
to address all the problem statements mentioned above and help enterprises gain complete control over identities and infrastructure entitlements, and right size identity privileges. SecurEnds Access Control would be closely integrated with the SecurEnds Cloud Control platform and will help enterprises automate cloud infrastructure entitlement and manage identities at scale.
Get in touch
with us to learn more about SecurEnds CIEM capabilities.
0 notes
Link
Using SecurEnds organizations can convert visitors to registered users, validate identity and verify before a user account is created. With additional interactions
Read More:
https://www.securends.com/customer-identity-access-management/
0 notes
Link
Using this integration, applications owners / administrators can request for provisioning and de-provisioning in SecurEnds. A ticket will get created automatically in ServiceNow.
REad More:
https://www.securends.com/identity-management-for-servicenow/
0 notes
Text
How Can You Easily and Effectively Prove HIPAA Compliance?

Like many businesses, you may already claim that your organization is “HIPAA Compliant” somewhere on your website. No matter how true your statement is, self-attestation is not always—or is it even terribly often—considered the most reliable source of information about such crucial matters.
While your word may be good enough for vendors with whom you have worked for years, their other clients and associates may not think it enough to protect them from risk. Every business along the chain of association must answer to someone else; therefore, it is essential to have verifiable proof of HIPAA compliance.
Following are three ways to prove your organization has officially achieved HIPAA compliance, so your enterprise’s hard work is easily and verifiably recognized.
1. Self-Assessments
With the self-assessment path to proving HIPAA compliance, there is no need to obtain third party verification or auditing services. Of course, this way of providing proof is the easiest, most expedient and least expensive, in terms of immediate costs.
The downsides add up quickly, though. The need to comb through all the policies and procedures on your own—without the assistance of a well-versed, professional HIPAA auditing team—can be laborious, to say the least.
Take a quick look at some additional challenges of taking on self-assessments:
Self-attestation requires reviewing mountains of supporting documentation, which may include screen shots of settings and links to policies, to illustrate an organization’s compliance. Many businesses need to craft reports that thoroughly document the path to HIPAA compliance. Not surprisingly, self-attestation can become a long and arduous process for everyone involved.
Some organizations do invest in specialized software that lays out all the policies and procedures, but it is still time-consuming and grueling for staff, including legal compliance personnel, to sift through so much information without regular exposure to it.
While self-attestation is manageable and doable for your team—and acceptable in the healthcare industry—the cost of human and administrative resources can cause your budget to spiral out of control while the sheer volume of work can cause your progress to stagnate.
2. Third Party Audits and Attestations
Reaching out to a trusted auditing firm to engage them to conduct an assessment of the potential risks and vulnerabilities to the Confidentiality, Integrity and Availability of ePHI collected by your organization, which then stores, processes and transmits may be the easiest way to prove HIPAA compliance. Even with a somewhat greater initial cost, the expertise and instant assurance make this path to proof highly attractive to busy healthcare organizations.
The HIPAA auditor will compare his or her gathered data against the standards established by HIPAA to ensure that you have completely achieved HIPAA compliance. At the end of the audit, your auditor will provide an attestation and documentation, and you will have all the materials you need to provide verifiable proof of your organization’s full compliance.
3. Purchase Software to Achieve HIPAA Compliance
If you find the first method of proving HIPAA compliance to be too risky for your vendors and other associates, and the second method to be too expensive, you may consider buying your own software to ultimately streamline the process of ensuring HIPAA compliance.
Many software programs provide thorough guidance to assist you in your HIPAA compliance goals.
The primary downsides to this method of providing proof include the fact that such a software program can be expensive, and you will need to seek regular updates through the product’s manufacturer, which may cost more money over time.
Get more information: https://www.securends.com/fulfill-hipaa-compliance/
Would You Like to Discuss Additional Ways You Can Prove That Your Organization Has Achieved HIPAA Compliance?
Are you interested in learning about more ways you can prove your organization’s HIPAA compliance? Perhaps you need assistance becoming HIPAA compliant. Either way, our I.S. Partners, LLC. team is eager to talk to you about your needs and concerns when it comes to protecting ePHI and other issues you may encounter.
Call us at 678-374-4243 or submit a contact form today for HIPAA compliance services.
0 notes
Text
HIPAA Compliance and the Cloud

To ensure privacy and safeguard an individuals’ medical data the Health Insurance Portability and Accountability Act (HIPAA) was passed in the year 1996. HIPAA applies to any covered entity that:
collects
creates
or transmits
Protected health information electronically and their business associates who encounter such health information in any way throughout the work that has been contracted.
HIPAA mandates such entities to comply with a set of standards that outline the lawful use and disclosure of protected health information.
Healthcare organizations and their business associates are migrating to cloud at a rapid pace on account of the:
scalability
flexibility
cost-efficiency that cloud has to offer
However, they are worried about “how to make the most of the cloud while being HIPAA compliant and secure?”
While the HHS’s guidance on HIPAA and cloud computing states that:
the cloud service providers (CSP) should sign a business associate agreement and;
that CSP’s are directly liable for compliance with applicable requirements of HIPAA rules
The enterprises often overlook the security responsibility in the shared responsibility model that cloud service providers operate.
A CSP can only put in place safeguards to enable cloud usage in a manner that is HIPAA compliant; but the covered entity is responsible for ensuring HIPAA compliance and ensuring there is no misuse or misconfiguration.
No data should be shared through the cloud unless protected by an end-to-end encryption. The covered entity should ensure that the CSP uses the highest level of encryption. However, encryption alone does not give the necessary protection and satisfy all security rule requirements. The covered entity should be able to define all the security rules in the cloud and implement the best security practices to ensure their protection in the cloud.
At SecurEnds, we believe that coveted entities under HIPAA must conduct an ongoing assessment to know who has access to what resources and whether that access is appropriate. SecurEnds products once configured as a single unit or as a bolt-on to existing Identity Access Management (IAM) solution will create powerful governance and provisioning/ de-provisioning tool across clinical, financial and back-office applications. The CEM module will allow recurring automated access review campaigns that validate users within systems and ensure their access rights are appropriate while the ILM module will drive the management of dormant and orphan accounts. IRA module applies AI and ML to detect anomalies and user group outliers for faster remediation.
Get to know more about challenges of fulfill HIPAA compliance
0 notes
Link
0 notes
Link
If your company is preparing for merger or acquisition SecurEnds can help you with Identity Management and AD Cleanup. Using SecurEnds, you can certify current users before AD integration. SecurEnds with its leading AI/ML allows you to do a rapid discovery of identities within Active Directory. This will ensure that there are no over-provisioned accounts or orphaned accounts before the directory sync.
Read More:
https://www.securends.com/ad-cleanup-for-seamless-it-integration/
0 notes
Text
How Can You Quantify the Value of Automated Provisioning and Deprovisioning?

IT managers face a constant challenge to justify spending, demonstrate business value and quantify the impact of security incidents. Organizations too often fail to prioritize security until a crisis arises. Identity and access management (IAM) domains are key because they enable IT teams to address risk and facilitate operational and revenue gains.
Automated provisioning and deprovisioning value calculations are no different. Provisioning and deprovisioning improve the user experience, operational efficiency and security policies and are integral to business operations. It’s important to view provisioning and deprovisioning as a business matter, not an IT issue.
The Value of Provisioning and Deprovisioning –
Automated Provisioning and deprovisioning activities include creating and propagating user accounts; requesting, approving and granting access to resources; changing users’ access over time; and decommissioning accounts when no longer needed.
A well-built business case should include the fully loaded costs of software, process changes, organizational changes, hosting, change management and even effects in culture. The costs must be balanced against a full comprehension of value achieved. Whether or not the value exceeds the costs, there is value in simply demonstrating to your stakeholders that you fulfilled every aspect of diligence.
Below are some important value drivers for automated provisioning and deprovisioning.
Value No. 1: Operational Efficiency
Value No. 2: Improving the User Experience
Value No. 3: Identity Management as a Strategic Differentiator
Value No. 4: Standardized Technology Platforms, Processes and Policies
Value No. 4: Standardized Technology Platforms, Processes and Policies
Click to know more challenges about the value drivers for automated provisioning and deprovisioning for the below link:
https://www.securends.com/workday-integration-for-automated-provisioning-and-de-provisioning/
SecurEnds is leading the market with its lightweight, highly configurable and industry first flex-connector product that keeps companies secure while meeting audit and compliance requirements. Our software allows you to load user data from multiple system of record, connect dynamically to applications, match identities with user credentials, manage heartbeat identities across connected and disconnected, schedule one-time or periodic access recertifications and create proof of compliance for external auditors. In only 30 minutes we can demo why our SAAS software is now a leading choice for identity governance.
#Automated Provisioning and Deprovisioning#Identity and access management (IAM) domains#SAAS software#Periodic access recertifications#Automated provisioning and deprovisioning value calculations
0 notes
Photo
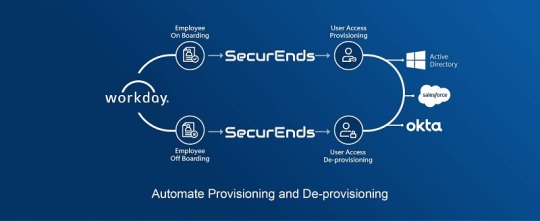
In addition, manual process is inefficient and error-prone, resulting in lost productivity and increased security risks. Automating provisioning and deprovisioning improves the user experience, operational efficiency and security policies.
Read More:
https://www.securends.com/workday-integration-for-automated-provisioning-and-de-provisioning/
#Automated Provisioning and Deprovisioning#Identity and access management (IAM) domains#SAAS software#Periodic access recertifications#Automated provisioning and deprovisioning value calculations
0 notes
Link
ADP is a leading provider of Human Resources Management System (HRMS). It is an intuitive SaaS product that allows companies to manage essential employee information.
Read More:
https://www.securends.com/adp-integration-for-identity-lifecycle-management/
0 notes
Link
SecurEnds integrates with Workday to manage the employee lifecycle from “join” to “move” to “leave” across every IT system, including enterprise applications, enterprise databases, cloud applications and non-standard applications.
Read More:
https://www.securends.com/workday-integration-for-automated-provisioning-and-de-provisioning/
0 notes
Link
SecurEnds helps comply with Part 11 to limit user access and their privileges by automating the certification process for organization.
Read More:
https://www.securends.com/fda-21-cfr-part-11-automated-user-access-entitlement-reviews/
0 notes
Link
SecurEnds helps organizations speed time to M&A value by securely integrating IT systems and reducing the likelihood of a breach.
REad More:
https://www.securends.com/increase-ma-agility/
0 notes
Photo

Effective User Access Reviews | SecurEnds
In summary the challenge for security teams remains how to add security at the speed of digital transformation. User access reviews provide a time-tested method to flush out orphaned accounts that hackers use for malicious activities.
0 notes
Text
Effective User Access Reviews

User access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. Implementing user access review best practices can help to eliminate or avoid the mentioned risk scenarios.
Best practices that application business owners can implement to help ensure effective user access reviews include:
When a new business user joins the team, the application business owner attests and provides relevant roles and access levels for the business user.
When a business user leaves the team or changes roles, the application business owner validates the user and the user’s access level for any updates or removal.
At predetermined intervals (prescheduled part of calendar of activity), a business user access review is automatically triggered or manually initiated. The application business owner receives a list of existing business users, roles and access privileges. The application business owner then takes action to remove or change any incorrect privileges.
Any change to the application business owner and/or delegate is to be updated as part of transition from current contact to new contact.
IT User Access Review Best Practices
IT users need to have access to the application back end to execute their responsibilities. IT users’ access privileges are dependent on their team and role.
The application’s IT owner is responsible for the effectiveness of the user access review control for IT users. The owner can assign a delegate to assist with this activity, but the application’s IT owner remains accountable for this control and any violations. The IT owner is the custodian of the business data. Therefore, after the IT owner completes the access review, he or she must get approval from the application business owner to complete the user access review cycle.
If the application business owner is not an IT expert, the application IT owner can set up a clarification session with the business owner to explain the application and the IT responsibilities. This effort can increase trust between the business team and the IT team and result in a more productive workplace, as improved trust enhances speed and reduces cost.
SecurEnds is leading the market with its lightweight, highly configurable and industry first flex-connector product that keeps companies secure while meeting audit and compliance requirements. Our software allows you to load user data from multiple system of record, connect dynamically to applications, match identities with user credentials, manage heartbeat identities across connected and disconnected, schedule one-time or periodic access recertifications and create proof of compliance for external auditors. In only 30 minutes we can demo why our SAAS software is now a leading choice for identity governance.
Learn more information about the “User Access Reviews: Enabler for Digital Transformation”:
https://www.securends.com/user-access-review-enable-for-digital-transformation/
#user access review best practices#Digital Transformation#IT User Access Review Best Practices#effective user access reviews
0 notes
Link
Access Request For Microsoft ADFS | SecurEnds
SecurEnds Self Service portal is super easy to install and is extremely secure for Single Sign-On (SSO) authorization service.
Read More:
https://www.securends.com/active-directory-federation-services/
0 notes