Don't wanna be here? Send us removal request.
Text
Cybersecurity on AWS: How to Secure Your Cloud Environment in 2025

1. Introduction
The cloud has been a priority for more organizations, and security has become a major focus. Amazon Web Services (AWS) is a leading cloud provider in the world, but knowing how to use it securely requires understanding security tools and best practices.
This blog will look at how to manage cyber security effectively in AWS using AWS features and established practices.
2. The Importance of Cybersecurity in AWS
AWS provides scalable and reliable cloud services, but in the same way any other infrastructure can become vulnerable to cyber threats if not managed. Cybersecurity in AWS can be directed at the following features:
Data breaches, misconfigurations and weak access controls can expose sensitive information, so it is important to focus on Cybersecurity in AWS because it is important to protect:
Customer data
Intellectual property
Application integrity
Business continuity
3. Core Security Concepts in AWS
The AWS security consists of these foundational concepts:
Confidentiality: Making data private and secure
Integrity: Making data accurate and untampered with
Availability: Keeping systems running and available
Compliance: Meeting regulatory and legal obligations (e.g., GDPR, HIPAA)
4. Key AWS Security Services
AWS offers a variety of services to help you secure your cloud environment.
AWS Identity and Access Management (IAM): Manage who has access to your AWS resources
AWS Key Management Service (KMS): Manage your encryption keys for securing data lots
AWS CloudTrail: See and monitor all account/finding activity
Amazon GuardDuty: Identify threats. Uses intelligent threat analysis.
AWS Config: Monitor changes and ensure compliance
AWS WAF (Web Application Firewall): Protect web applications from common attacks.
Amazon Inspector: Automatically evaluates security vulnerabilities on EC2 instances.
AWS Security Hub: A single view of security alerts and findings.
5. Best Practices for Securing AWS Environments
In order to secure your AWS environment use best practices such as:
- Employing IAM roles as well as a least-privilege (or as little as possible to complete the assignment) approach
- Enabling MFA
- Encrypting data at rest and in transit when possible (using AWS KMS)
- Reviewing and rotating credentials regularly
- Employing AWS CloudTrail and GuardDuty for continuous monitoring
- Isolating workloads, if possible, using VPCs or security groups
- Regularly applying patches
- Automating checks with AWS Config or AWS Lambda
6. Common Threats and How AWS Helps
Threat
AWS Protection Tools
Data Breach
KMS, IAM, S3 Bucket Policies
Misconfiguration
AWS Config, AWS Trusted Advisor
Unauthorized Access
IAM Policies, MFA, GuardDuty
DDoS Attacks
AWS Shield, WAF
Insecure APIs
API Gateway + WAF + Cognito
7. Shared Responsibility Model
In AWS, security is a Shared Responsibility Model:
Your security responsibilities: securing what you put into the cloud (data, apps, user access, configurations)
AWS responsibilities: securing your environment (hardware, software, networking, facilities)
Understanding how this is divided is critical to managing cloud security.
8. Conclusion
AWS provides a vibrant cloud environment from which to build and scale applications, but it is your responsibility to secure it. AWS offers many available native security services and best practices if you follow them, you will have a secure, compliant, and resilient environment.
Cybersecurity is not optional in the cloud; it is mandatory. Facebook posts may be optional, but security is not. Start early, audit often, and leverage what AWS provides for your environment to implement the security posture against threats.
0 notes
Text
A Beginner’s Guide to Infrastructure as Code (IaC)
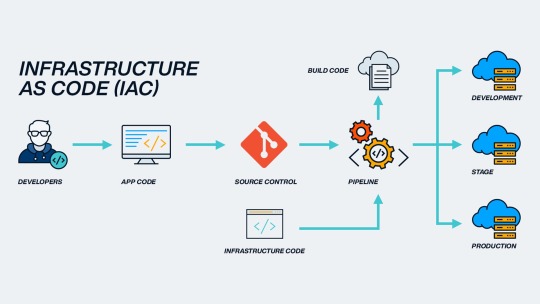
1. Introduction
In the past, infrastructure wasn’t so fast—servers were installed, packages were installed, and environments were initialized by doing things manually one step at a time. In today’s fast-moving development world, that isn’t the case anymore. This is when Infrastructure as Code (IaC) comes into play. IaC enables teams to provision and manage cloud infrastructure via code instead of the manual processes that existed previously. In this blog, we will explain what IaC is, why you need to use IaC, and how you can get started.
2. What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) is the operation of maintaining and provisioning IT infrastructure like servers, networks, and databases using machine-readable code. Instead of navigating through cloud dashboards and clicking or typing commands manually, you write configuration files that tell your infrastructure what it should be. Those configuration files are put into version control systems like Git and executed automatically.
3. Why IaC Is Important in Today's Development
Speed & Automation
IaC is automating infrastructure so teams can spin up environments in minutes instead of hours or days.
Consistency & Repeatability
Code is being used to guarantee that all environments—that is, development, staging, production—are consistent.
Version Control & Collaboration
IaC allows you to version your infrastructure changes just like you would your application code. Teams are more efficient and can roll back to earlier states when they want to.
Cost Savings
Through putting infrastructure in code, you can avoid over-provisioning resources and you can turn off your idle environments - which could lead to cost savings over time.
4. Popular IaC Tools
There are several tools that are most commonly used for Infrastructure as Code:
Terraform – Open-source, cloud-agnostic, and declarative syntax (HCL)
Pulumi – Uses actual programming languages (TypeScript, Python)
AWS CloudFormation – Built-in to AWS, YAML or JSON
Ansible – Most commonly used for configuration management and provisioning
Chef and Puppet – Enterprise tools for system automation
Both have their advantages and your choice depends on your use case or existing skills in your team.
5. How IaC Works (Simple workflow)
Write Code: Describe your infrastructure in code (e.g. a file, main.tf in Terraform)
Plan: See what the code will change in your environment.
Apply: Run the code to provision or update your infrastructure.
Maintain: Put your code into version control so you can go back and make future updates or roll-backs.
6. Common Use Cases of IaC
Provisioning cloud infrastructure on AWS, Azure, or GCP
Managing Kubernetes clusters
Automating testing environments
Scaling infrastructure with auto-scaling groups
Setting up a monitoring and alerting system
Creating disaster recovery environments
IaC is utilized for startups, and enterprises, by DevOps teams and SRE teams alike.
7. Best Practices for IaC
Keep your IaC code in a version control system (like Git)
Use modules and reusable pieces
Review changes using code reviews and CI pipeline practices
Don't include secrets and sensitive data in code files
Test infrastructure changes in a staging environment before production
Use remote state storage, in tools like Terraform, so that they can collaborate
8. Conclusion
By automating deployment and management, Infrastructure as Code is changing the way we create and manage infrastructure. It provides automation, repeatability and speed to the people, processes, and technology that once were slow manual, unreliable and error-prone.
Whether you are bringing a basic deployment to the cloud for the first time, or scaling complex systems to operate as a single unit with fault tolerance, and elasticity either way, it's an important skill to learn and apply to modern software development. Start easy, learn to use a single tool well and grow from there!
0 notes
Text
Cybersecurity in 2025: Top Trends and How to Stay Protected

1. Introduction
In 2025, cybersecurity is an increasingly vital concern for companies of every kind. With increasing digital footprints, businesses face daily threats—from ransomware to automated attacks using AI. Meanwhile technology is changing and adapting in order to combat these [...] risks.
This blog considers what cybersecurity looks like today, the latest trends, and how to secure your data and systems—increasingly important as cyberspace continues to be the new battlefield.
2. What is Cybersecurity?
Cybersecurity is the practice of preventing unauthorized access, retrieval, damage, or disruption to systems, networks, and data. They include everything from firewalls and anti-virus programs to advanced threat detection and user training.
Good cybersecurity addresses:
Data protection
Network protection
Application protection
Identity and Access management
Incident management
3. Why Cybersecurity is More Important Than Ever in 2025
Increase in AI-Enhanced Threats
Cybercriminals are now leveraging AI to increase the level of sophistication and automation to launch highly targeted attacks, making malware and phishing/fraud campaigns even harder to detect.
Remote and Hybrid Worker Vulnerabilities
With more employees working remotely or in hybrid work arrangements, they are at a greater risk of exposing themselves to insecure Wi-Fi, using personal devices, and poor authentication policies.
Cloud Security Vulnerabilities
While the cloud has given businesses an unprecedented level of flexibility and adaptability, misconfigured cloud services, poor access controls, and unmonitored privileges can continue to pose significant vulnerabilities.
Ransomware and Phishing Threats Started to Evolve
Ransomware groups have raised their targets for ransoms; double extortion tactics are becoming common. Phishing emails are becoming increasingly difficult to detect, thanks to AI-generated text.
Data Privacy & Protection Laws
Governments are implementing stricter data privacy laws. Violation of applicable laws can result in significant fines, and many companies are realizing that security and privacy must co-exist.
4. Cybersecurity Trends to Expect in 2025
Zero Trust Architecture: "Trust nothing by default... verify everything--external and internal to your network."
AI-Powered Threat Detection: Security teams use AI tools to detect out-of-the-norm activities faster and to better prevent breaches.
Passwordless Authentication: increased implementation of biometrics and/or one-time codes instead of passwords.
Secure-by-Design Development: Building applications with security in mind from the start.
Extended Detection and Response (XDR): Unified experiences for advanced threat detections on endpoint, networks, and servers.
Cyber Insurance: As companies are finding it more difficult to recover when attacked, more are investing in insurance.
5. Ways to Improve Cybersecurity in Your Organization
Conduct regular security training
Ensure all systems have multi-factor authentication (MFA) enabled
Ensure users keep all software and systems up to date
Continuously monitor networks and endpoints
Securely back up your critical data and periodically test recovery
Review access controls and permissions regularly to limit access
Document and regularly update incident response plan
6. Cybersecurity Tools to be aware of
There are many tools that are critical to your digital environment:
Firewalls and VPNs (Examples: Palo Alto, Fortinet)
Endpoint Detection and Response (EDR) (Examples: CrowdStrike, SentinelOne)
Identity and Access Management (IAM) (Examples: Okta, Azure Active Directory)
Security Information and Event Management (SIEM) (Examples: Splunk, LogRhythm)
Phishing protection (Examples: Proofpoint, KnowBe4)
When using tools, choose along a spectrum of company size, risk level, and industry specifications.
7. Summary
The state of cybersecurity in 2025 is a business rather than a technical issue. The same way that threats develop and evolve, so too must your approach to defense. Regardless of whether you are a start up, scale up, or enterprise company, an investment in strong cybersecurity measures is essential in protecting your data, reputation, and ultimately your future.
Follow up and continue to learn. Become proactive in how you think about and approach cybersecurity. Devise a way that cybersecurity will become a way of life and an essential part of the cultural landscape of your company.
0 notes
Text
Kubernetes Application Management in 2025: A Simple Guide for Modern Teams

1. Introduction
Kubernetes has become the backbone of cloud-native infrastructure. However, although powerful, managing applications on Kubernetes can be quite complex—particularly at scale.
By 2025, successful teams will not only have to run Kubernetes but manage applications on Kubernetes with proficiency. They will have to manage deployments, monitoring, scaling, and reliability without getting lost in whatever YAML.
2. What is Kubernetes Application Management?
Kubernetes application management describes the management of applications deployed on a Kubernetes cluster throughout its lifecycle, including deployment, updates, organization, scaling, and monitoring the applications during their lifecycle.
It encompasses:
Defining an application (manifests or Helm charts)
Managing the application (deployment, rollouts, rollbacks)
Having an observability strategy (i.e., logs, hits, and alerts)
Resource optimization (i.e., CPU/memory)
Security and compliance
3. Why Kubernetes Application Management Matters in 2025
Scalability
Today, applications reach a global audience. Kubernetes gives you the ability to scale workloads horizontally to meet demand, but to do so effectively requires strategic (and automated) nimbleness.
Cost Optimization
Over-provisioning can use up servers and your cloud spend. But with proper app management, workloads will consume resources sparingly—essentially wasting nothing.
Resilience
Our modern distributed world of microservices means that failure is the expected condition. Kubernetes has the ability to self-heal applications, but only when they are configured and monitored accurately.
Deployment Automation
You can't manually deploy apps at scale reliably. GitOps, Helm, and CI/CD pipelines for deployment automation are now synonymous with updating apps quickly and safely.
AI-Assisted Operations
Moving forward into a 2025 world, many teams will incorporate AI to help manage Kubernetes applications, such as auto-tuning the resources being put to use, anomaly detection, and predicting failures.
4. Important Tools and Platforms that Exist for Managing Kubernetes Applications
The initiatives below will all be in a good position, in 2025, to help your organization manage Kubernetes applications.
Helm – Package manager for Kubernetes applications.
Argo CD – Continuous delivery based on GitOps.
Kustomize – Allows you to customize configuration in Kubernetes manifests.
Prometheus + Grafana – Monitoring and visualization.
Lens – Kubernetes IDE that gives you visibility to manage the cluster.
OpenTelemetry – A standard to follow for tracing and observability.
AI software – There are cost analyzers, auto-scalers, and intelligent debuggers.
5. Best Practices for Kubernetes App Management
Use Helm or Kustomize to deploy your application configuration
Configure CI/CD pipelines for automated deployments
Utilize GitOps for safer, auditable change control
Monitor resource utilization and set requests/limits accordingly
Add liveness and readiness probes to every deployment
Use namespaces and labels to better organize application deployments
Implement RBAC policies for access control
6. Common Challenges and How to Solve Them
Challenge
Solution
YAML sprawl
Use Helm charts or Kustomize
Complex rollbacks
Implement GitOps with Argo CD
Over-provisioning resources
Use vertical pod autoscaling or Goldilocks
Debugging in production
Add logging, tracing, and observability tools
Multi-cluster management
Use centralized dashboards or tools like Rancher
7. Conclusion
Kubernetes is a robust system, but in 2025, managing applications with it is more than pressing the deploy button for a few pods. Successful teams will be those that are continually automating, observing, securing, and optimizing their applications.
If you're still manually managing your Kubernetes applications, it is time to transform the way you work. Begin small as you bootstrap: use Helm, automate your applications to the best of your ability, add some observability. As you mature, you can progress into GitOps, AI-assisted operations, and smart scaling.
The management of Kubernetes applications is not simply about keeping it all running; it is about keeping it all running better.
1 note
·
View note