Don't wanna be here? Send us removal request.
Text
Splunk & RTO
some interesting challenge and course. Bascially on some Splunk and Red teaming stuff.
1. Hunting for indicators of compromise (IOCs) pertaining to APT29 attack techniques.
ATTCK T1036.002 Right-to-Left OverrideDefense Evasion The RTLO character is a non-printing Unicode character that causes the text that follows it to be displayed in reverse.
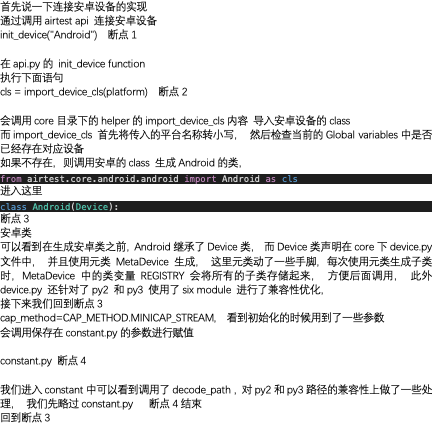
It's a bit tricky to hunt RTLO in Splunk since it's invisiable character. UNICODE explorer will be helpful when you are looking for some uncommon character. https://unicode-explorer.com/c/202E

In this case, we click copy, then paste to splunk, then we will find suspicous file name. The query seems still empty inside quote but the invisiable character indeed there.

Another possible way is to type this character manully, but didn't success in remote desktop unfortunately.
Windows:
hold alt type + type 202E release alt
Linux:
hold ctrl+shift type U 202E release ctrl+shift
2. Hunting network connection and process execution
There are two sysmon events were used in the challenge
Sysmon Event ID 1 - Process creation https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=90001
There are some lovely field that can help you corrlerate the process in the domain sope, especially for Guid that can help you link between child and parent process, LogonGuid also helpful when you want to corrlerate KDC event.
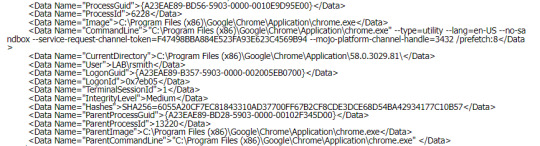
Classic scenario for phishing action chain Event ID 1: Process creation(Outlook) -> Event ID 11: FileCreate->Event ID 1: Process creation(Word with micro)-> Event ID 11: FileCreate(Malicious powershell)
Sysmon Event ID 3 - Network connection https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=90003
This event will help you to identify process connection, information like IP, Port, and Process name will be extremely helpful during the investigation.

PowerShellCore/Operational log EventCode=4104
This event will documents all script blocks processed when ScriptBlockLogging is enabled. We will be able to see the execution of a remote PowerShell command.
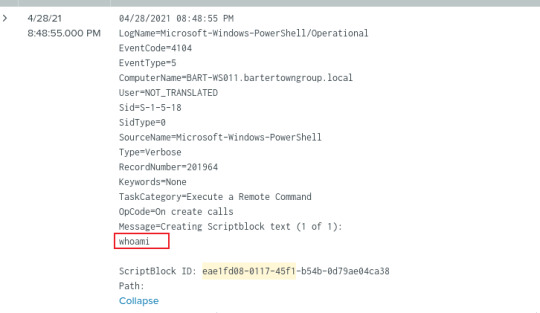
PowerShellCore/Operational log EventCode=4103
module logging is a bit different in that it includes the command invocations and portions of the script. It’s possible it will not have the entire details of the execution and the results. Example: malicious module to collect sensitive file

2. RTO compliance
Before starting the task, we need to double check if service hosting on some providers like amazon, azure, google, these platform has specific ruls when security assessments performed from infrastructure. For example, if red team compromised the client server that hosted on google, when google detected suspicious C2, it may cause unexpected service shutdown due to Google security policy violation and cause the business damage on client side. Red tean operator must confirm with the client to make sure both side understandstand the risk to build a mature plan and able to remediate the influence when unexpected serivce outage occured.
0 notes
Text
SDN yak shaving (ODL)
1.Download mininet VM
http://mininet.org/download/
· Import mininet to VMbox
· Set network to bridge mode
· Check IP in mininet VM
· Connect mininet through windows terminal


2.Install Opendaylight
· Download ubuntu-14.04.3-server-amd64
· Set network to bridge mode
· Install dependency
apt-get update
apt-get install maven git openjdk-7-jre openjdk-7-jdk unzip
· download opendaylight
wget https://nexus.opendaylight.org/content/repositories/public/org/opendaylight/integration/distribution-karaf/0.3.1-Lithium-SR1/distribution-karaf-0.3.1-Lithium-SR1.tar.gz
· unzip file
· cd distribution-karaf-0.3.1-Lithium-SR1
· set java path
export JAVA_HOME=/usr/lib/jvm/java-1.7.0-openjdk-amd64
Set network:
sudo vi /etc/network/interfaces
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet static# set your own network address make sure your c#omputer and your VM in the same subnet
address 192.168.172.105
netmask 255.255.255.0
network 192.168.172.0
broadcst 192.168.172.255
gateway 192.168.172.1
dns-nameservers 8.8.8.8
sudo shutdown -r reboot
cd unzip distribution-karaf-0.3.1-Lithium-SR1/bin
sudo ./karaf #start opendaylight
feature:install odl-restconf-all odl-l2switch-switch odl-dlux-all odl-mdsal-all
3.Association
After we use mininet create a network then we can associate the opendaylight GUI API with mininet
then we can visit the website(remember set mininet remote addr for this address)
http://192.168.172.105:8181/index.html
0 notes
Text
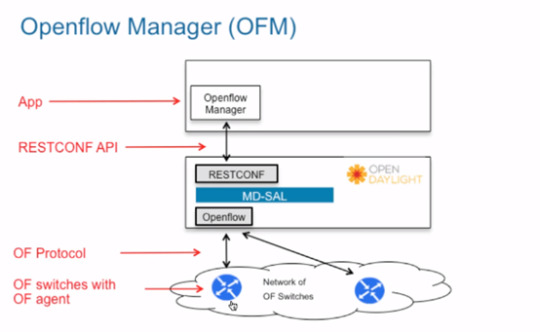
SDN basic
Today I will talk about how to use vSwitch to build a simple network for SDN
What is Open vSwitch?

Open vSwitch architecture
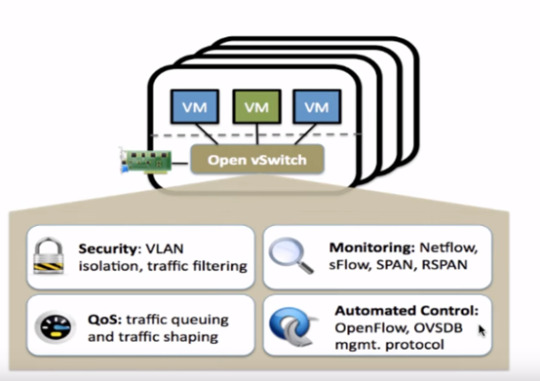
In later blogs, I will show you how to integrity with the OPENDAYLIGHT
First, we need to install GNS3 and GNS3 VM
Once we set our VM, we need to download the openvswitch-management file from the GNS3 website marketing field. No worries, totally free for use.
you can also download this file from my GitHub
https://github.com/RickyYhQi/SDN-Software-Defined-Network-/tree/master/SDN%20basic

drag the open switch to the blank area

build a simple topology using router 3725 notice: leave eth0/0 for openvSwitch management
then we can open the openvSwitch console and run some command
you can always check all the command in the page belowing
http://www.openvswitch.org/support/dist-docs/ovs-vsctl.8.txt

this command for checking all ports in the bridge
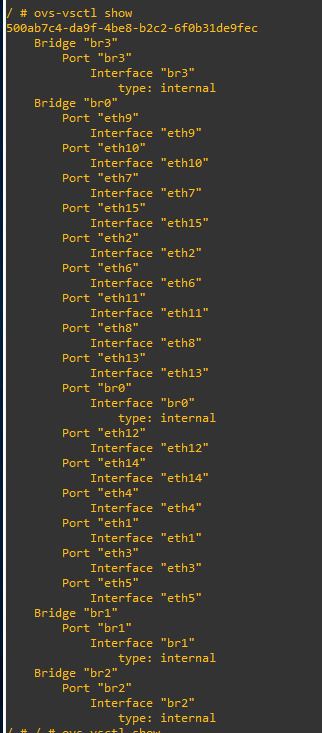
we can see that eth1 and eth2 in bridge 0 witch connecting two routers
===========================================================
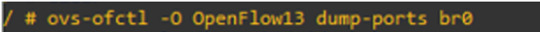
this command for checking all ports traffic belong bridge 0
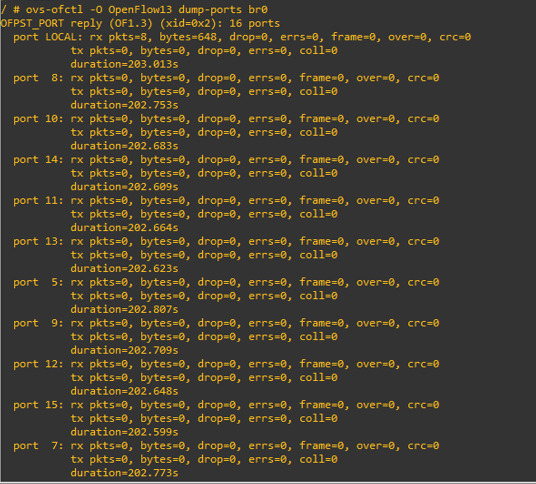
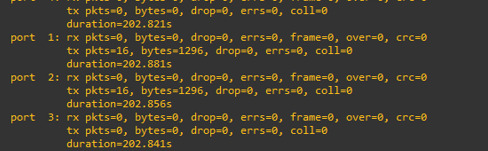
and for port 1 and port 2, the current traffic is 0 because we just start up our topology.

run this command to check all the flows belong br0
=============================================================
I am gonna create some traffic for br0
let’s config R1 and R2 first
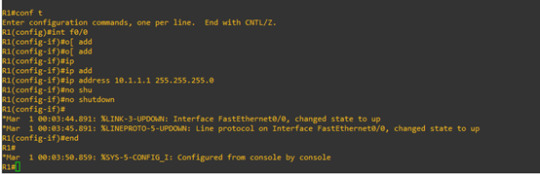
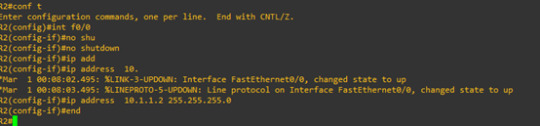

and run ping command from R2
Now we should have some traffic in br0 port
now we re-run the command

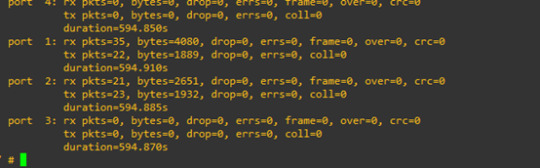
then Port 1 and port 2 are not 0 traffic anymore
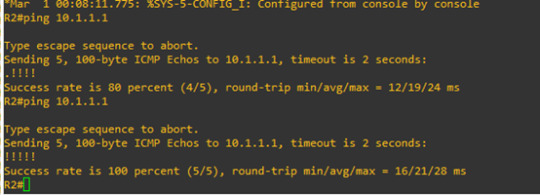
Ping again
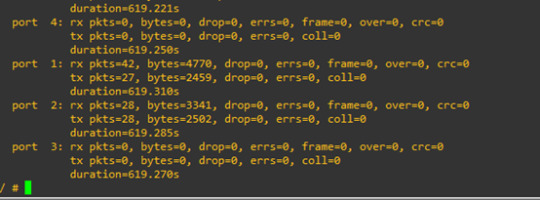
we can see that the traffic value increased.
//
This is a simple network for SDN
good luck :-)
0 notes
Text
Authentication
Create a phishing website which use OAUTH technology to lure Barbara to input the password, Once we get the Auth from google, we can get all the information from she’s account.
0 notes
Text
week8 reflection
This is week 8.
In this week, Richard introduce lots of book for us. I am very interest in a book called [Honesty - commander in cheat].
These books are awesome, I put this book on my top of the list. we talked about three root cause for something ERROR.
Human error, culture, the system. and introduce some pattern for predicting the result like similarity matching, Frequency gambling.
At night, we almost spent all hours talk about the nuclear system and accident, the system is very complex, and there are so many parts connected with each other. Although the system is designed with some failures in mind, it is still impossible to predict all possible failures.
I watched the Chernobyl incident after the course, let me the deepest impression is because of human error in the test procedure lead to the explosion of the entire plant, it just confirms said before the biggest reason is human error, although the plant has some protective measures, but the real runtime even designers can't consider all the situation, like backup generator, the main generator can not work normally, backup generators need one minute to start, this can lead to uncontrolled nuclear fission
0 notes
Text
Case study #Alien

There are three roles in this sinearial, ghost solider, alien, major
major <-> alien alien <-> ghost solider ghost solider <- major
we don't know weather the alien is trustworthy, so our group decide to encrypt everything through the alien. our group first come up with some ideas about using asymmetric method to encrypt the message, the solider should remember his own private key and public key before he becomes to a ghost, then the major and solider can communicate with each other, and alien can get nothing. But there is a problem of using the asymmetric method because we don't know the alien's technology level, maybe they can break the asymmetric easily. And there is no way for preventing the message be modified from the alien.
Then we come up with an idea for using one-time-pad, before this tutorial, I've done the activity for cracking many-times-pad. I know that there is no way to crack the one-time-pad unless the keystream is used for twice. But we stuck by how to make sure the alien don't know our one-time-pad key. If we use a keystream, like a book, how we make sure the alien don't know the book we used?
Blocking alien outside for using one-time-pad encrypt the message may be a good method, but, if there is another ghost, how we keep it safe? the only way I can think is to share a key(like a date stream) between the major and solider before the solider to a ghost this pre-share-key stream can be increased by the date so we can change it every day. Then use this pre-share-key combine with a one-time-pad keystream encrypt the message and tail with a hash value of the message inside the encryption data.
Then we keep all the CIA to make sure our message safe.
Other groups come up with some idea such as invite many alien to transfer message and reduce the risk probability of modified or using diffie-hellman to encrypt the message. However, Diffie-hellman can be easily hacked by MITM attack.
Then the tutor talks about the solution - just using the hash method to make sure our message Integrity.
We can test alien by checking some test message. If they are trustworthy, then we can transmit the message without any encryption.
0 notes
Text
Trump Phishing
Dear Donald:
This is an Email from Kasparsky Anti-Spam Lab
Our transit mail server recently intercepted a number of destinations for your mailbox fraud mail.
Our security team immediately analyzed it.
We found the latest unknown Trojan in these emails. Once your phone receives these emails, all your account information will be read and uploaded
Please download our anti-virus software and scan your phone as soon as possible
link: https://www.spam-killer.com/product/
Please don't forget to reset your account password
To analyze spam emails, Kasparsky Lab experts need the original message with all headers. Attach a sample of spam in the MSG or EML format and send it to [email protected].
Only emails received not older than 48 hours are suitable for analysis. Your request will be processed automatically; please do not expect any response from the experts.
Kind Regards Kasparsky Anti-Spam Lab
0 notes
Text
Email Phishing
This is a hard one.
I spend almost 2 days... until I realize there is no way to use the first flag to login the facebook...

for phishing, the first step must be information collection.
We need to get as much information as possible
after we find their mail address, we can be a fake person.
what I want to do in the first email is to pretend to be real facebook and send a fake facebook login address.
Then I got the flag.

after the whole day, I tried to use the given account to login facebook...
But there is no way to login facebook...
in the second day, I tried the different method to send the bank email to Sarah.
Sarah then recommend me to send a mail to David

David seens busy.. unless I declare this thing is urgent.
He finally gives me flag.

What we learn:
set 2FA, even hacker get the password they can’t do anything on your account.
Don’t trust anyone, especially someone who said himself from the official account.
Be sensitive to keywords: payment, account, dollars.
Appropriately challenge the other party’s identity
0 notes
Text
Homework: find examples of (serious) fraudulant certificates being issued
In March 2011, Comodo, the company with the highest market share in the certificate market, was hacked. Seven digital certificates were stolen from seven networks, including: mail.google.com, addons.mozilla.org and login.yahoo. COM, At that time, some people called the incident "CA version of the 911 attack."
In the same year, the Dutch CA agency DigiNotar was also hacked and issued a large number of forged certificates. Millions of users have been attacked by man-in-the-middles because of these forged certificates.
In 2013, the “Prism Gate Incident” broke out. Snowden’s leaked documents revealed that the National Security Agency used some of the forged SSL certificates issued by CA to intercept and crack a large number of HTTPS encrypted network sessions.
0 notes
Text
Security everywhere
Cooling fan
This is the cooling fan in front of the Library of the University of New South Wales Law Lirary.

Many leaves have been attracted by the fan
The goal of this fan is a cooling foam on a huge device.
When more and more leaves are covered in the fan
The wind speed of the fan will drop, and the efficiency of the cooling system will drop at any time.
When all the leaves cover the fan, the cooling system will not work properly.
The system may be abnormal
Improvement measures:
regular maintenance
away from large floating objects
0 notes
Text
CASE STUDY# SNOOP
CASE STUDY# SNOOP
Hi Guys,
This week in your tutorial class you'll be debating privacy - specifically should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
This is an important topic which you should form views about as a thinking citizen.
There is no right and wrong answer here - there are many differing opinions in society held by sensible people - but there are right and wrong approaches to working out your opinion. Work it out based on careful analysis and consideration of as many facts and diverse points of view as you can find. And then, when you have worked out your position, be open minded and prepared to change it as you learn and observe new things.
You'll debate it in class. make sure you are able to debate both sides as you won't get to pick which side you are on in the debate :)
cheers,
Richard
This week's case study is about whether we support the government's collection of privacy issues.
We were divided into two groups of discussions. At the beginning, our group's view was that it did not support the government's collection of privacy. However, in the actual discussion, our position was forcibly transformed, and we had to solve the problems we had given ourselves before. . .
We begin to discuss the possible views of the other party and try to refute them.
I think the other party may mention the idea of collecting the benefits that privacy brings to people. For this, we can refute the problem by explaining that the cost of building facial recognition is too high and the benefits to people are limited.
The following is a general point of view, I summarize but not all, including the views of some teammates.
Should not be
The government can't guarantee 100 percent security of citizens' information --》 may be hacked by hacker group、insider attack
The exchange of information between people is limited because governments keep only the information they want --》 Satoshi Nakamoto ? kill before he create the bitcoin,Preventing technological innovation
There is no guarantee that the information they collect will not be misused and All institutions will share information with the government Health record/shopping record/browsing record/potential password-> build database for analysis-》 --》 People's information is aggregated and analyzed without their knowledge
Large input and output (against terrorism) -》 less cost-efficiency
Should be National security, surveillance is necessary to maintain network order, national sentiment -》Punishing cybercriminals
Deter potential criminals- good people/bad people don't do bad things CCTV =》 people believe the government is doing good things
Life is convenient and saves time -》 People don't need to be certified by document in hospital/ unmanned supermarket
Locate criminals and find children -》 Increase law enforcement efficiency
Metadata reviews require very rigorous steps -》 Need multiple departments to agree at the same time -》 When it seriously affects national security
In my turn I tried to use the privacy to shock the bad guys to argue against the opponent and give some examples about CCTV. This time my turn is over, but our teammates still seem to want to go back and rebut... So we started the second round, each person limited to speak for two minutes... In the second round, the other party gave a lot of examples about some governments collecting privacy to harm innocent people.. It was my turn: I talked about some questions about the depth of privacy collection. By collecting only the necessary information to avoid excessive leakage of personal information, I listed the way Huawei and Apple phones save fingerprints. Huawei saves them locally, and Apple saves them on the network. Apple's fingerprint server leaks, people's fingerprint information will be made public, and security will be affected..
Time is up, the game is over, it is clear that the other party’s argument is more powerful, but I have to say that the other’s direction is correct. After all, at the end everyone said they didn’t like to be collected by the government. Very interesting debate, everyone is very committed
1 note
·
View note
Text
0x0009#Mis-Association attack
Introduction
There is a difference between Deauthention attack and Mis-Association attack.
The goal of Deauth attack is to force the client to leave the WIFI router, but for Mis-Association, we want to force the client to connect to the fake wireless network
Weakness
For all the Windows-base system, there is a list called Preferred Network List(PNL).
Every time the computer wants to connect to the network, it will check the PNL list which store the previous SSID we connected. Once windows/phone find the environment has wifi frame which broadcast the same SSID in PNL, our device will automatically connect that SSID.
This action gives the attacker chance of cheating the computer to connect a Fake name SSID.
An attacker can build a fake AP with the same SSID base the real SSID. And adjust the WIFI adapter with a higher power to broadcast to computer/phone. For a reconnection action of the client, the attacker may init a Deauth attack to force all the client to leave the WIFI router.
When the client leave the original wifi router, the attacker stops the Deauth attack. Then client will find two same SSID in their PNL list. Because the fake SSID has a stronger signal than the original AP, the client will associate the Fake SSID.
After that, the client is connecting to the hacker’s computer.
The hacker then may implement the further attack:
Monitor all Traffic
MAC spoofing
DNS spoofing
Reverse shell
Web exploit
Phishing
Feasibility:
This kind of attack can be implement for windows and some old device, and need attacker close to the target client as possible for better signal strength.
Steps:
For the stronger signal, we need to set our wifi adapter manully

root@kali:~# ifconfig wlan0 down close the interface root@kali:~# iw reg set US set the region root@kali:~# iwconfig wlan0 txpower 30 set power to 30 root@kali:~# ifconfig wlan0 up open the interface

We can see here, our wifi adapter power from 20dbm to 30dbm.
Listen our target and find SSID, MAC, channel airmon-ng start wlan0mon

airodump-ng wlan0mon -c 3 listen all the client in channel 3 we can see that A4:BA:76:6E:E3:BA is connecting to the target AP
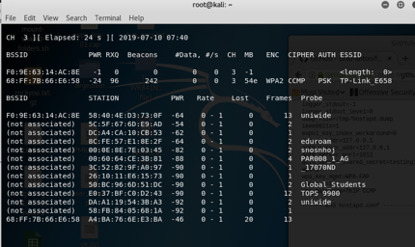
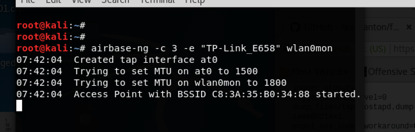
root@kali:~# airbase-ng -c 3 -e "TP-Link_E658" wlan0mon create the fake SSID with the same name of running AP
Implement deauth attack for a specific WIFI Router -0 means infinite sent packets root@kali:~# aireplay-ng --deauth 0 -a 68:FF:7B:66:E6:58 wlan0mon
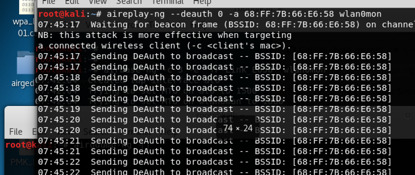
Then we listen again, we can see there is no client connect our target wifi-router Now we stop deauth attack, let the client make reconnect action

When the client makes a reconnection, it will check the NPL list, then the client should find there are two same SSID in there, because attacker’s wifi has a higher power, so the client will choose the attacker to connect the internet. Once the client connects with the attacker, we can see the message from the terminal.

Now, the client has connected to us, the attacker can implement some further attack.
This is the Mis-association attack.
How to prevent it:
I would suggest that people should update their system to WIN10 or Use mac/Linux system. For example, every time MacOS connection will record both ESSID(Name) and BSSID(MAC), if there are the same ESSID in the environment, mac will check if the BSSID is the previous one, if not, MacOS will pop up a notice to make user know this WIFI is not the previous one.
1 note
·
View note
Text
Cipher mode


Interesting challenge. I got it all
First of all, I first judge the ECB mode. For fixed length ECB encryption, the ciphertext is always the same. The first thing is to find the corresponding character in a plaintext block. I increase the number of plaintexts. When the array is satisfied 1111111111111111 Adding a character will cause some encrypted content to multiply. I judge this length is the upper limit of the encrypted block. The internal usage of the excess should be filled by the program with 0. When I copy the string 11111111111111111111111111111111 For 1 and 5, the encrypted content appears to be duplicated, I judge it is the ECB mode. When I only add a few characters, only the cipher2 ciphertext corresponds to a few characters. Considering the stream cipher feature of CTR, I think cipher2 corresponds to the CTR mode. Exclusion method, the rest is the CBC mode
0 notes
Text
Week7 lecture reflection
At the beginning of the course, Richard discussed the two questions with the lowest scoring rate. I was glad that I got them all right, but because of the English problems, I often made wrong understanding of the long questions, which I think is also my weakness to make up.
In the course, we demonstrated Diffie Hellman's encryption with a practical demonstration. Richard first explained the mathematics of the method by applying (a^b)^c = (a^ c) ^b = a^ (b*c).
It is interesting to generate the same secret key and at the same time make it impossible for other unrelated people to infer the secret key from the information transmitted in the public channel. Maybe I should study how to attack this method after class. I have a vague idea waiting to be implemented
After that, we also talked about how to attack the stack with format string. We can check the contents of the stack by using the variable passed in printf or write data randomly in memory using %n
This is absolutely amazing. Since I learned programming, I have learned such an attack mode for the first time. It is also a common attack mode to use shell code to obtain the permissions and contents of the system. We also talked about asset safety, how do you identify the most valuable asset, and the fastest way to do that is to ask everybody and then come up with a list of assets
We need to update it regularly. Richard showed us a short video, which let us know that while protecting people's rights and interests, we should also pay attention to protecting people's assets. I think we need to do some trade off here.
Because sometimes sacrifice is inevitable. We talked about the red box, need certification of fingerprint, iris, voice can unlock the U disk, Richard let us think how to attack him, I think this fingerprint can be collected, voice is by collecting samples and then use software simulation, I think the most difficult is fake iris certification, this needs to be under the condition of certain specific action to induce goals after iris information collected by contact lenses and prosthesis to fake iris
It's difficult, but it can happen.
In the evening, we first discussed bug discovery and introduced some platforms used, such as bug crowd, hackerone, and Hacker101, a platform for training
Pentest group showed how to use kali's built-in tool gobuster to blow up the directory under the url, and then showed how to directly obtain the root permission of MAC. I restarted my computer on the spot and tried it, but it was really successful
Later, Richard discussed how to attack public key with MITM, and discussed the concepts of PKI and PGP, as well as the hierarchical signature authentication of x509 involved, and introduced some practical x509 services such as SSL and TLS
At the end of the course, I choose to stay and watch the movie, this movie is about the second world war the United States air force received a bomb attack using the instructions, when the President found, for a variety of signal receiving device damage caused by accident, the last even cracked three letters cannot stop attacking, eventually the irreversible radiation damage, the movie I think the best place is the password of this method is used for the air force to accept the key to decrypt, and people in the face of the disaster, it is worth mentioning, after the success to get three letters, everyone is happy and cheer up, But the problem is not solved. I think this is the most alarming place. When people get carried away by the superficial victory, as security personnel, they should repeatedly ask themselves whether the problem is really solved and all the potential consequences.

After the end of the film, I began to prepare lab information, tomorrow I have to do it, because as an international student, I can't guarantee that I can present my idea clearly in the debate, even if will my idea clearly, I have to put all things clear in advance, to predict each person's position and consider what they might retort, although these may end up nothing with... But I want to try my best to finish these tasks.
It's almost 1 a.m. The nearest birds are very noisy around 3am and 4am. Hopefully, I won't be woken up by them in the morning. Goodnight.
0 notes
Photo






One(many)-time-pad
The start guess eve -> every. Change index to 1 canyo->canyou. Change index to 2 everyo->everyone. Change index to 1 thesecre->thesecret. Change index to 0 canyouple->canyouplease thesecrettowinin -> thesecrettowining … index 0 : thesecrettowinningeurovisionisex index 1 : everyonedeservesahippopotamuswhe index 2 : canyoupleasehelpoliverfindtheflu index 3 : themostimportantpersonintheworld index 4 : thepriceofbitcoinistoodamnhighgi
Picture5: Emmm…there’s seems a small bug.. every time a ‘f’string number input the function will return None…let’s fix this…
Picture6: Oh…there still some bugs there, I will rewrite my code I find that in some condition the result text will represent 26, which the (plaintextnum + keynum) mod 26 will never equal to 26…Then I fixed it with a special number -0 Every time the program read 0, it will jump this number to next
Finally, result in the picture
my code:
_a,_b,_c = ['LpaGbbfctNiPvwdbjnPuqolhhtygWhEuafjlirfPxxl', 'WdafvnbcDymxeeulWOtpoofnilwngLhblUfecvqAxs', 'UijMltDjeumxUnbiKstvdrVhcoDasUlrvDypegublg', 'LpaAlrhGmjikgjdmLlcsnnYmIsoPcglaGtKeQcemiu', 'LpaDohqcOzVbglebjPdTnoTzbyRbuwGftflTliPiqp'],[],[] def strnum(_str):return ord(_str.lower()) - 96 def tostr(_num):return chr(_num + 96) [_b.append([ strnum(_a[_][e]) for e in range(len(_a[_]))]) for _ in range(5)] mykey,currentText = [],'themostimportantpersonintheworld' # change text everytime currentLine = 3 ## and the index plain = [strnum(x) for x in currentText] for i in range(len(plain)): res_str,ori_str,find = _b[currentLine][i],plain[i],0 for key_str in range(1,27): if (ori_str + key_str) % 26 == res_str: mykey.append(key_str);find = 1;break; if find == 0:mykey.append(0) for _ in range(5): temp = [] for key_index in range(len(mykey)): key_str,res_str = mykey[key_index],_b[_][key_index] if key_str == 0:temp.append('=');continue;find = 0 for ori_str in range(1,27): if (res_str - key_str) % 26 == ori_str: temp.append(tostr(ori_str));find = 1;break _c.append(temp) [print( "index" , _c.index(i) , ": ","".join(i)) for i in _c]
0 notes
Text
Security Everywhere
Card system

Today is Sunday, the upper limit of the bus is only 2 dollars, I think of the past things when I swipe the card
When I get the inbound brush but don't get the outbound brush, the transit system will deduct the money until the limit is reached
Damn the setup.
I remember that day I only brush the inbound, but because the outbound machine was broken, I did not brush it, because the balance of the card was about 9 dollars.
When I got on the bus after I had walked for more than 10 minutes, the balance on my card turned out to be negative $5
I think this is a vulnerability in the public transportation system, or it may be an intentional vulnerability
I swipe my card when I get in (point A)
I didn't swipe my card when I left the station (point B)
Then switch to another new bus stop (point C).
A-->B-->C 1 0 1
The system will assume that I get on at point A and get off at point C and deduct A lot of expenses, but geographically, point A and point C are not on the same bus route
In other words, if point A gets on the bus and goes along the route, it should never be point C when it gets off. The system should automatically recognize this point
The most reasonable thing to do
When getting on the train at point C, the settlement shall start from the exit of route A nearest to point C, and the expenses shall be recalculated from point C
0 notes