I'm a woman with 20+ years of experience in IT who wants to help answer your questions and wants to help you be better at privacy and security. Please ask me questions and follow for articles I come across and basic tutorials. Let me help you with it! Obligatory disclaimer: While I work in IT and will endeavor to give you good information, I am not liable for any action taken in these articles. There's a lot that can go wrong in the wonderful world of IT and I encourage you to trust but verify before you take any action. Also please check your local laws before you use any of the tools recommended in this blog. if you or anyone you know is a victim of harassment, abuse or stalking, please contact your local law enforcement agencies (I know, I know) and victim's rights advocates.
Don't wanna be here? Send us removal request.
Text
More on DNS Archeology (with PowerShell), (Fri, Oct 25th)
I while back I posted a “part 1” story on DNS and DHCP recon ( http://bit.ly/364G6Lv ) and recent events have given me some more to share on the topic. Read more @ http://bit.ly/2MQdAWB via CMNatic’s Bot. This account is un-monitored. Check below for info. My owner: CMNatic cmnatic.tumblr.com http://bit.ly/2mPsPRf http://www.twitter.com/cmnatic cmnatic(at)cmnatic.co.uk
1 note
·
View note
Text

If there was a way to run SUPER MEGA AD BLOCKER on this website I fucking would
418K notes
·
View notes
Text
Google Will Now Pay Anyone Who Reports Apps Abusing Users' Data
In the wake of data abuse scandals and several instances of malware app being discovered on the Play Store, Google today expanded its bug bounty program to beef up the security of Android apps and Chrome extensions distributed through its platform. The expansion in Google’s vulnerability reward program majorly includes two main announcements. First, a new program, dubbed ‘Developer Data Read more @ http://bit.ly/2Ztzead via CMNatic’s Bot. This account is un-monitored. Check below for info. My owner: CMNatic cmnatic.tumblr.com http://bit.ly/2mPsPRf http://www.twitter.com/cmnatic cmnatic(at)cmnatic.co.uk
3 notes
·
View notes
Text
yall look at this shit ad*be is tryna pull now on ppl who have outdated software:
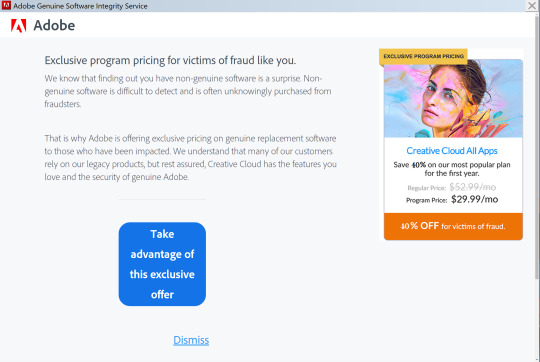
(note for context: i’m all for piracy, but in this case my copy of CS6 was downloaded years ago when they were giving it away to students. i got it totally legally.)
436K notes
·
View notes
Text
I havent seen anyone talk about this yet so im making a post.
So lets say you’re researching something for a paper (or just for fun) and the research paper you want to read is behind a paywall, or the site makes you create an account first, or makes you pay to download, or limits you to only 5 free articles, or otherwise makes it difficult for you to read what you want.
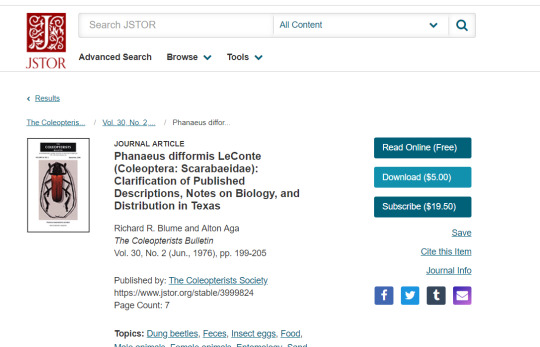
do not fear! copy the link to the article

go to sci-hub.se (the url is always changing so its best to check out whereisscihub.now.sh to find what the current url is)

slap the article link in there

bam! free access!
156K notes
·
View notes
Link
ONE MORNING A couple of weeks ago, I handed my iPhone to my wife and asked her to help with a privacy experiment. She would use my handset to track my location for the next few days, and with only the software I already had installed. Like a lot of couples, my wife and I know each other’s phone PINs. So I left her with the device as I walked into our bathroom to take a shower, simulating an opportunity that I figured would present itself daily to snooping spouses.
I’d barely turned on the water before she handed the phone back to me. A few seconds had passed, and she had already configured it to track my location, with no notification that it was now telling her my every move.
I’d embarked on this strange exercise with the blessing of a group of researchers who focus on the scourge of “stalkerware,” a class of spyware distinguished by the fact that it’s typically installed on a target device by someone with both physical access to the phone and an intimate relationship with its owner. Often explicitly marketed as a way to catch a cheating husband or wife in the act, these programs have become a tool of domestic abusers and angry exes—a breed of hacker who often possesses practically zero technical skills but does have plenty of opportunity for hands-on tampering with a victim’s handset. Perpetrators can install these apps, also sometimes known as spouseware, to monitor where their targets go, who they communicate with, what they say, and virtually every other part of their life the phone touches.
After years of neglect, the antivirus industry has finally begun to recognize stalkerware’s danger and flag the apps as malicious, a development that’s long overdue given that a quarter of women in the US and one in nine men experience some form of physical abuse or stalking by an intimate partner.
read more
671 notes
·
View notes
Photo

The new zero-day vulnerability resides in #Windows Task Scheduler utility and has been tested and confirmed to be successfully working on a fully patched and updated version of Windows 10, 32-bit and 64-bit, as well as Windows Server 2016 and 2019.
Here’s a PoC Video… https://t.co/KamXgyH1bU (via Twitter http://twitter.com/TheHackersNews/status/1131090253685465088)
3 notes
·
View notes
Text


If there was a way to run SUPER MEGA AD BLOCKER on this website I fucking would
418K notes
·
View notes
Photo

When the malware is smart but not like... too smart.
0 notes
Text
FBI: Don’t Trust HTTPS or Padlock on Websites
FBI: Don’t Trust HTTPS or Padlock on Websites

The FBI has been forced to issue an alert warning users that the sight of “HTTPS” and a padlock icon in the address bar may not be enough to prove the authenticity of a website.
The latest Public Service Announcement from the bureau’s public-facing Internet Crime Complaint Center (IC3) revealed that cyber-criminals are increasingly abusing trust in TLS-secured websites to improve the success rate of phishing attacks.
“They are more frequently incorporating website certificates — third-party verification that a site is secure — when they send potential victims emails that imitate trustworthy companies or email contacts,” it warned.
“These phishing schemes are used to acquire sensitive logins or other information by luring them to a malicious website that looks secure.”
Corin Imai, senior security adviser at DomainTools, argued that the falling price of SSL-TSL certificates make it a no-brainer for malicious webmasters.
“Thankfully, education is the single security measure against which criminals can’t work around: an aware user, who has been trained to look for misspellings in the URL of a web page and knows not to trust a padlock icon, is much harder to lure into giving away personal information or clicking on malware-spreading links,” she added.
“Organizations should therefore invest in solid training programs, which cannot be limited to a one-day workshop on what a phishing scam looks like, but need to be continuous, thorough and impactful.”
To that end, the FBI urged users to go back to basics, by not clicking on links in any suspicious-looking emails and to follow-up with the sender directly even if the contact is known.
Hackers are also hosting malware on cloud services such as Azure and benefiting from their HTTPS certificates indirectly this way, experts have revealed.
Read more @ http://bit.ly/2XEqIB3 via CMNatic’s Bot. This account is un-monitored. Check below for info. My owner: CMNatic cmnatic.tumblr.com http://bit.ly/2mPsPRf http://www.twitter.com/cmnatic cmnatic(at)cmnatic.co.uk
1 note
·
View note
Text
I really don’t understand anyone who still posts selfies at this point like. we’re all fully aware that the feds are monitoring us and using our photos to build a surprise database that will help them later it’s just not fucking worth it anymore
63K notes
·
View notes
Photo

Google Helps Police Identify Devices Close to #Crime Scenes Using its “SensorVault” Location History Database and Track Narrowed-Down Suspects or Witnesses.
https://t.co/hF0tPAGUxM
—by @Swati_THN https://t.co/A6hYJoXWCm (via Twitter http://twitter.com/TheHackersNews/status/1117760225052749824)
3 notes
·
View notes
Text
How email really works ;)

502 notes
·
View notes
Text
This image is a TCP/IP Joke. This post is a UDP joke. I don't care if you get it.

Via https://twitter.com/KirkBater/status/953673704734683136
102 notes
·
View notes
Text
Modems are the biggest racket in the cable business. Don't opt for theirs, you pay $12/month for life, as apposed to the one time cost of $30 - $100. Only set up required is giving the ISP the Mac address on the box, and you dont have to wait for the installer to come "between 8am and 2pm"
I used to work for an ISP B2B sales team. They paid us well for selling rented Modems because usually they were used, given back by the last renter. Or if they renter didn’t return them, they still have to replace it with a new one. So it was recurring revenue without a cost to the ISP
And no, there is no advantage to renting. They don’t service Modems rented differently than one you bought
Source: reddit.com/r/LifeProTips
67 notes
·
View notes
Photo

Opinions are like MAC addresses
163 notes
·
View notes
Video
tumblr
Transmission Control Protocol Communication Process
(CCNA Network Fundamentals - Tumblr Assignment 2)
This video illustrates the TCP process in simplified terms as it relates to the Transport Layer of the OSI Model.
It must be noted that as the encapsulated application data moves down the source host stack so does it also move up the corresponding layers of the OSI stack on its way to the destination host.
At the transport layer, a three way handshake occurs beginning with SYN (synchronize) control flag at the source host to initiate the exchange of data. A response from the destination web server in the form of SYN-ACK (acknowledgement that SYN segment received) control flag is returned. This opens a session from client to server and the flow of information continues as encapsulated segments of data from the source client are sent via a transmission window at a reliable rate of transfer towards the destination server. The window size and flow control for this session are both determined at the Transport Layer.
The destination web server decapsulates and reassembles the client’s information and responds by returning the data requested. At this point, the entire process repeats itself in reverse. This time, it is the web server that sends SYN segment to open a session back to the client. The client sets SYN-ACK to web server and all remaining segments are exchanged.
During the previous process, there may be factors (such as network congestion) that can cause packets to be dropped. In a TCP session, any dropped packets would be retransmitted thus ensuring the reliable transfer of data between client and server.
When each side has completed transferring all of its data the TCP session must be terminated at both ends. This is done by both source and destination and is set by FIN control flag
FIN from client > FIN-ACK from web server > FIN from web server > FIN-ACK from client
Session is then terminated from client to server and server to client.
18 notes
·
View notes