Text
Side Story (Analysis) Chapter 9: Guns are Good
Question: Laws to prevent school shootings?
First thing the question is: how do school shootings happen?
Situation one: Guns are legal
Situation two: Guns are illegal
How do students get guns in the first place?
Situation one: Going to assume the main way they acquire guns is via their parents. So enforce laws that require more security over accessing the gun. E.g. the guns have a tag similar to that of shopping tags
0 notes
Text
Wordpress Fail
Preface
If the content of this post may seem very vague or not clear, it is deliberate. To comply with “Responsible Disclosure”, I have tried to avoid putting in as much identification as I can.

So there is a very famous athlete that I’ve been following for sometime. He’s a powerlifter and he’s freakishly strong. For context, a powerlifter is someone who tries to be strong as opposed to bodybuilders who goes for aesthetics. It’s also become the trend for athletes to create their own brand, and he’s not any different. He charges something in excess of $30-$50 a month for his program because he’s not only an athlete, but a world-class coach. He trains athletes that even the Average Joe would have heard of. Nevertheless, I actually accidentally stumbled upon this extreme flaw via google and discovered all the files he uploads onto Wordpress. I had to research how Wordpress works and basically everything a WP creator does is via uploading files (such as his Programs for the Gym) and then unaccessible component is all the text and formatting which is on the WP server side. As the files are discoverable on google, I can’t open any of the folders above as the filenames giveaway too much information. The folders above represent each month.
0 notes
Text
Time Management: Week 8
As this week was preparation for my Something Awesome presentation alongside the development of my Job Application, I have resigned my Week 8 Lecture and Module blog posts for next week in order to manage my time more feasibly.
0 notes
Text
Main Story (The Lectures) Chapter 7: Rush Hour (Jackie Chan only)
Preface
In order to make sure my Something Awesome was up to date, some sacrifices were needed. Goodbye Chris Tucker :’(
Presenting Rush Hour the Remake without Chris Tucker
Diffie Hellman Key exchange
How do two people safely communicate over an insecure line and share a secret key so that both of them have the same key without divulging it to someone who is listening in on their conversation? Welcome to Diffie Hellman Key Exchange. When I thought about how Diffie Hellman works, it’s pretty obvious that it’s vulnerable to man-in-the-middle attacks since there’s no real method of authentication. A party can be certain that they’re exchanging a key with somebody, however they do not know with whom they are exchanging it with, so hypothetically the bad guy could be the one who receives the keys initially from both parties and then is able to decipher both parties messages as the bad guy is the other person with the private key. Regardless, it’s a pretty darn cool way to do a key exchange, and of course it has a weakness of brute forcing but with the nature of modulos having infinite equivalent classes, it’s wild.
Cyber Literacy - WoRds oF Th3 W33k
Vulnerability is a weakness that lives in something
An exploit is something that takes advantage of a vulnerability
A software bug is something with a mistake in it. A bug can be a vulnerability
The distinction between those three words is important, although similar. Knowing the correct use will help with clearer communication.
Bug Puzzles
I think the point to understand here was that bugs in code are what become vulnerabilities. Reminds me of chess tactics to be honest. For example, forks take advantage of a weakness/vulnerability in the opponents positioning, even though it was completely undesirable for the opponent.
Security Assets
The most sensible step when approaching security is to consider what are your most important assets. Why? By implication, the most important assets should mean the highest impact risks to an individual/party/pikachu. I suppose in the eyes of a threat actor, the most lucrative aspect to exploit, whether for chaos or tangible gain, would most likely have something to do with this asset.
Mentioned it before, but assets do not need to be tangible. If you consider a company such as Coca Cola, an important asset of theirs is their brand. This reminds me of when of the earlier lectures or analysis sessions when we discussed that one of UNSW’s most important assets is also their reputation whereas intuitively a lot of people answered their students or money.
Something to look into
Buffer overflows
%s %n? attacks
Responsible Disclosure
NOP Sled
PKI
0 notes
Text
Main Story (The Lectures) Chapter 6: Block Ciphers and Authentication
AES
It stands for Advanced Encryption Standard. It’s pretty peculiar that although AES is now broken academically, the breaks don’t mean that AES isn’t valid anymore (quite the contrary). The way it works in steps is:
Plaintext comes in and is chopped up into 16 byte blocks
XOR the plaintext with 16 bytes of this iterations key
Each block is then used as an index into an S-box table. This table maps 8-bit inputs to 8-bit outputs. S-boxes are identical
Bytes are rearranged
Bytes are mixed in groups of four using a linear mixing function. Linear in this instance means each output bit of the mixing function is the xor of several of the input bits.
Repeat 10-14 times.
Authentication
What is Authentication?
Authentication is the set of methods used to prove that the identity provided is true
What are factors?
A factor is a category of methods for proving identity/authentication. Example:
Knowledge: your PIN
Biometrics: your physical attributes
Possession: your bank card
Actions: your handwriting
Geographic location: being physically present at the bank
Methods of Authentication
There are multiple methods of authentication, below are some of them.
Multifactored Authentication
Self explanatory. Examples:
ATM transactions (you need the card + pin hence two factors. The card is a form of identification, not authentication though). However this is arguable just verification.
2FA means two-factor authentication
Mutual Authentication
A method where both parties authenticate each other. This prevents impersonation attacks aka man-in-the-middle attacks, or at least makes it much harder. This can be coupled with multifactored authentication.
Passwords
This is a single factor of authentication but a particularly strong one if done appropriately. Some cool facts about brute force cracking:
If a password is all lowercase and eight characters long, it could take 1-2 minutes to crack.
If a password is the same password but use both uppercase and lowercase it will take could take 6 days to crack.
If we add numbers into the mix, a little more than 25 days to crack.
If we use numbers, uppercase, lowercase, and symbols, it will take on average 2 years to crack with an average workstation.
Password hygiene
Can be difficult to remember strong passwords which can encourage writing them down somewhere. But this defeats the purpose and hence is considered bad hygiene.
Manual synchronisation of passwords
Using the same password everywhere.
0 notes
Text
SecSoc: CTF + pwnable.kr
Did the first challenge for fun on pwnable.kr, it was pretty easy and enjoyable and then my friends invited me to come to the SecSoc event on the weekend. It was really challenging and to be honest, I felt very unequipped for the event. But I grinded it out and managed to get 400 (though it was more like 250) points for my team!
I solved:
Two pdf CTF’s where you had to edit the pdf code via vim to unlock the flag,
Cipher
And a free 150 point challenge (hence why it was more like 250).
I realised that CTF’s dabble a lot in different security methods like Forensics unlike my grossly misguided impression that it was just pentesting. I’ll look into doing more CTF’s when I have free time in the future because I see that I could learn a lot.
0 notes
Text
BITSA: Industry Mentoring
Successfully applied for BITSA’s Industry Mentoring program, specifically Cybersecurity, so I’ll have a mentor from the Industry! Excited. Starts next week.
0 notes
Text
Side Story (Analysis) Chapter 7: Debate
Question: Should the government or government agencies collect and have access to your data for good purposes, or should citizens, e.g. you, have a right to privacy which stops them?
I am team affirmative.
The assumption here is that the government is benevolent, or at the very least, the access to your data is for good purposes. Hence, if that is the case, then if you are an individual who doesn’t do anything bad, then there is nothing to worry about as this tactic has the intention to weed out bad individuals. Then, you can make the conclusion that this ability will allow the government to prevent catastrophic crimes and at the same time lower the overall crime rate in general.
The right to privacy is a fair concern, however, the reality is when sifting through data of tens of millions of people, the trifling matters in your own personal life will not be of a concern to the government, and very obviously the method they’ll have to surveil data is through some algorithm that will be prompted for whatever reason, and hence will ignore your online personality if you have nothing to hide. Thus, it provides an almost similar privacy just by sheer volume of data, with the only sacrifice being that your data will be scanned by a machine and ignored since you are a good citizen.
It should be understood as well that there will would be very strict protocols in place to prevent the concerns of misuse of data. The argument that all our data will be revealed to the government and be misused is odd since the government already has access to much of your essential data already e.g. your birthday, licence number, TFN, your passport, what your assets are, what you look like, etc. and then at the same time your online data is being sold constantly already by companies.
If the fear that the government could make you guilty of crimes w/o reason hold the presupposition that the government cannot already do that which is naive. Even if we do ignore that naivety, well, why doesn’t that happen already? Well the answer would lie in the structure of our government that prevents this kind of tyranny from happening.
My teams arguments
Transparency
Track down malicious activity - the government has the infrastructure to track the hackers
Strong form of counter-terrorism
Convenient
Get people who cheat the system
Other teams arguments
Citizen data is human right
Data is hacked
Too much power - attack single point of failure
Impersonate people to trick the social credit system
Ash’s point
A really interesting point that he brought up that I never considered was the question: how is the data being transferred? Do governments need to break the encryption that companies provide? Or do the companies have to break their own encryption? Does that mean that governments are making companies provide encryption that’s breakable? Well, sure it could prevent counter-terrorism but then doesn’t weaker encryption allow other individuals or bodies from other countries to participate in breaking into our information?
Other things
Important to know the difference between:
Software Bug
Vulnerability
Exploit
a software tool designed to take advantage of a flaw in a computer system, typically for malicious purposes such as installing malware.
0 notes
Text
Side Story (Analysis) Chapter 6: A Sad Day
Possible Attacks
Hack into location services
Mess with submarine navigation
Take control of drones
Cause social chaos
Attacking small businesses
You and Your Mission
Make sure the cyber-team itself isn’t compromised (to be honest probably already have this)
Can’t really avoid security by obscurity
Add a level of physical security for public infrastructure that is solely intangible i.e. software
Surveillance via reading emails and messages etc
NSA level. If you can identify threats before they’re acted out on, well good defence.
Controlling internet accessibility within Australia
Prevents communication from threats to Australia radicalising civilians etc
Enforce a mandatory level of cybersecurity for businesses
The bigger the business, the higher level of cybersecurity required i.e. the more important their economic value is to Australia, the more security required in particular banks.
Conscription involves cybersecurity
0 notes
Text
Something Awesome: Chapter 3
3. Direct Kernel Object Manipulation
What is it?
The act of directly changing/manipulating main memory since all operating systems store internal record-keeping data within main memory
3.1 Kernel Queue Data Structures
Information is stored as a queue. Just queue data structures tbh. There are four different types of queue data structures:
Singly-linked lists
Singly-linked tail queues
Doubly-linked lists
Doubly-linked tail queues
There are a total of 61 macros for declaring and operating on these structures.
All the info is in the header file <sys/queue.h>
Some basic ones are:
LIST_HEAD Macro
LIST_HEAD_INITALIZER Macro
LIST_ENTRY Macro
LIST_FOREACH Macro
LIST_REMOVE Macro
3.2 Synchronization Issues
Unlike hooks, when you manipulate main memory directly, you run the risk of data corruption. This might happen if there a congruent processes running at the same time or another thread manipulates the same objects.
Solution: resource access controls.
3.2.1 The mtx_lock function
What is it?
Looking at the code, the function is passed a mutex. The mutex provides mutual exclusion for one or more data objects and are the primary method of thread synchronisation. If another thread is holding the mutex, the caller will sleep until it is available. Kinda like you need the baton to run in a relay race (not exactly true but you feel me)

3.2.2 The mtx_unlock function

WHAT THAT MOUTH DO? GIMME THAT MUTEX BOIIIIIIIII (but will give it to a higher priority thread if it be in the line too because this is TRIAGE)
Practical component
I have begun trying to apply the knowledge I have so far. I have been using github to transfer code from the book to my virtual machine. It’s been really difficult so far but I’m slowly getting the hang of everything. I want to try and make a system call hook soon since it’s nearly Week 8 and I’ve only messed around with basic KLDs.
0 notes
Text
Halfway Boss: Midsem Exam
The preparation I will have for the exam includes:
Looking at lecture slides for content I do not understand
Study anything I don’t know
Looking at class notes for content I do not understand
Study anything I don’t know
Practice substitution ciphers
I’ll update this as I make progression. Found a cool textbook I found a textbook called: The Basics of Information Security by Jason Andress. I have decided to use this alongside my research for specific topics to assist my understanding.
C.I.A Made sure I understood Confidentiality, Integrity and Authentication. Really explored authentication and it’s relationship with identification (yes, I know the I stands for integrity for any nerds out there).
Authorisation and Access Controls No recollection of this being covered in the lectures but briefly covered it just in case. No such thing as too safe!
Accountability Covered what it is and this includes nonrepudiation. Analysis Session
Learn about why asymmetric vs symmetric.
RSA method
Look into Enigma if you have enough info to explain
Bits of security
Image resistance
0 notes
Text
Side Story (Analysis) Chapter 5: Jonny Cab
Preface
Was not able to access the case study on openlearning to do the pre-readings.
Will update this blog as the day progresses.
Slide 1 - Assets we are concerned about
The intellectual property of the programming of the cars
If exposed, people can figure out vulnerabilities
The cars themselves
If stolen, ceebs
Reputation (if something goes wrong)
Shares
Everything else in the company will be affected
E.g. make sure it’s not hackable
Slide 2 - Top (Three or Fours) risks you are concerned about
People dying
Reputation
Legislature
Moral dilemmas
Slide 3 - What the company should do to address each risk
Don’t have people in the car when testing the self-driving mechanism
Make sure the rollout is perfect
Navigation works seamlessly. Nothing more annoying that navigation that sucks.
Compliance with the law (covers ‘Legislature’)
Self-driving mechanism works perfectly including being efficient at parking, turning etc.
Car is long-lasting. Want it to be virtually the same as a normal car in terms of fuel-consumption, repairs etc except that it has the convenience
Testing edge cases
Slide 4 - Recommendation: should the company proceed with this project? No. Still a very new area. We are concerned with the security of the company. Self-driving cars are still an extremely new field so there is no point if we have financial security in many other areas. Hold the belief that self-driving cars work best in an environment of other self-driving cars.
Analysis - What’s the point?
Well, this is an example of a threat analysis. We have to consider: our assets, risks affecting our assets, how to address those risks, and then after that our evaluation as to whether this task is worth following through. This was fun.
0 notes
Text
Side Story (The Modules) Chapter 5: Vulnerabilities
Martha’s Recipes
Recipe 1 - Simple Vanilla Cake
The issues here are:
The temperature of the oven should be celsius instead of Fahrenheit. (Source)
No measurements for the ingredients
Recipe 2 - Caramel Slice
The issues here are:
No mention of the golden syrup and the condensed milk
No exact measurement for the condensed milk
I suppose the exact chocolate brand wasn’t mentioned in the ingredients compared to what is asked for in the recipe. I doubt this would be catastrophic though.
Recipe 3 - Cheese Souffle
The issues here are:
Preparation time : 20 min, Cooking time: 30 min, Ready in 50 min
Sprinkle with Parmesan cheese and bake in the centre of the oven for about 10-15 minutes
Cook for 30 minutes but reality is that you only cook for 10-15?
I C Your Problem There
Program 1
If you pass length a negative integer, then length which is of type short, will undergo conversion to an int type after get_network_short(sockfd) is called. This means that the negative signed bit in short, no longer represents negative and adds 2^16 to the number.
0 notes
Text
Something Awesome: 1.4-2.5
1.4 System Call Modules

1.4.1 The System Call Function

1.4.2 The sysent structure

1.4.3 The Offset value

1.4.4 The SYSCALL_MODULE Macro

1.5 Kernel/User Space Transitions

1.5.1 The Functions

1.6 Character Device Modules

1.6.1 cdevsw Structure

1.6.2 Character Device Functions

1.6.3 The Device Registration Routine

1.7 Linker Files and Modules

2. Hooking
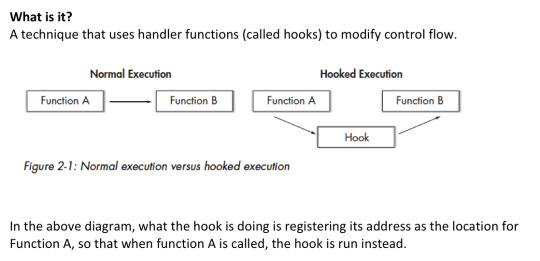
2.1 Hooking a System Call

2.2 Keystroke logging
Need to do sys_read when you want to use read
2.3 Kernel Process Tracing
ktrace command:
ktrace.out is unreadable.
This file is found in /usr
kdump command:
Reads the ktrace.out file in a readable format for humans
What's the point of these?
Well, if you don't know shit about the kernel, how do you figure out what syscall functions to hook? Well, since ktrace will follow the assembly, it'll find all the system calls before executing them to perform the kernel operation called e.g. ls. Then you can just hook one of these calls
2.4 Common System Call Hooks

2.5 Communication Protocols

0 notes
Text
Side Story (The Modules) Chapter 4: Hashing and MACS
Exercise
Nearly cried when I realised the answer to the question. I initially thought you had to figure out the password to figure out the verify code. So, I wrote a C program to calculate what the CDC code for all the three messages would be. Then I had no idea how to reverse engineer the CDC codes I had with the Verify Codes of the three messages. I probably spent an hour trying to figure it out before I caved and went to the consultation. Here, Cass hinted strongly what it was and then I realised I just needed to append ‘0′ to the end of the PAYBOB100 to figure out PAYBOB1000. Insert cry.
Avalanche Effect
Interesting concept that if you change the input slightly, you get an entirely different output. Reminds me of the butterfly effect.
Unclear concepts
Didn’t completely understand what MACs were. I should endeavour to learn more about MACs as they seem like an interesting topic.
0 notes
Text
Side Story (The Modules) Chapter 4: Human Weakness & Moral Hazards
Lockout Laws
The circumstances leading to lockout laws is argued by the liberal government to be for public safety. By this, they mean to decrease the number of assaults occurring in the CBD by alcohol-fuelled violence. The trigger for the discussion was in 2014 when a Teenager Daniel Christie died in January 2014, the victim of a one-hit punch. It is in contention whether the radius of the lockout laws intentionally did not include ‘The Star’ due to obviously some bribe or financially benefitting position for helping out the Packers.
An alternative method
If the concern was public safety, well a more intuitive solution would rather be to increase the number of security personnel venues are required to have or increase the number of patrolling police officers on Friday-Saturday nights. A public marketing campaign to discourage violence could also be an effective method to couple this with, as marketing campaigns for anti-smoking and anti-littering have proven to be very effective with the Australian public. The costs to hire patrolling police officers for the CBD could be paid for by the tax money that would be generated from having more foot traffic and businesses in the CBD during those nights. Honestly, if Sydney or more importantly, the NSW state government weren’t complete bellends, they would look at Melbourne for a better example of how to handle nightlife.
Analysis
Although this task may seemingly have no other relation to the course besides the analysis of human weakness which is a big component in cyber security, it also brings up the concept of risk. To elaborate, doing anything creates new risk, and then the argument becomes balancing the risk with the activity and then evaluating whether the activity is worth following through with. If you want a nightlife, you have to balance it out with alcohol-fuelled violence, you can’t avoid having either one of them.
0 notes