Text
Week 8 Lecture Review
This week the movie is Fog of War and next week the movie is The China Syndrome. There will be a question in the final exam based on that movie.
When something goes wrong… what is the root cause? Human error.
Root cause analysis – blame everything on the last person to touch it, blame it on culture or on the system as a whole.
Human Weaknesses
Honesty
Humans lie
A study was done where Universities get students to sign honour codes. The results showed that people were more honest when they signed the honour code before rather than after filling out the information
People lie to themselves about their own honesty
Misdirection and limited focus
Chekhov's gun
People are bad at picking the right features for focus
We often look for a few factors, in a very large space
Logically important vs psychologically salient: People should focus on what is logically important. People usually focus on what is evident
Similarity matching: people use their past, what they are familiar with and what they are comfortable with when it comes to similar situations in the future.
Frequency gambling
If multiple patterns match, pick the one which you have the most experience with
What worked in the past will hopefully work in the future
Not always the best solution. Especially for new problems, which happens often in Security
Availability heuristic - Kahneman 3
Satisficing and bounded rationality
Satisficing is only doing good enough, rather than doing perfectly
Bounded rationality refers to how we have a limited amount of information
People prefer positive statements
We ignore what we don’t like, people convince themselves that they are right when the evidence doesn’t exactly line up.
Cognitive strain
Group-think syndrome
How people think when they’re in groups rather than as individuals
We prefer to keep the peace in a group rather than fight against collective ideas
The result is grouped become homogeneous
Good for analysing systems
Confirmation bias
We prefer the evidence that confirms what we believe
Is an example of cognitive bias and describes that people gather and recall information selectively/interpret in a selective manner
Accidents vs Attacks: Intent is the main difference. In an accident, “holes” don’t really line up. In an attack, the attacker will make those holes line up
Error
Human error is inevitable - how do we fight it?
3-mile island
Simplification: people will simplify situations to have only one cause when the truth is probably a lot of causes
Culture
Don’t just punish the person who made an error, or the last person who touched it
It’s about learning and stopping these situations in the future
Code
Complexity is bad
Coupling is bad
Cohesion is good
These together create defence in depth…A good system can fail at one point or another, but if it doesn’t fail at EVERY level, the system itself isn’t faulted (yet)
Systems that follow these rules are easier to maintain and more resilient to attacks
Cassandra Syndrome: knowing the truth but no-one believes you and occurs when valid warnings or concerns are dismissed.
Chekhov’s Gun: anything on-screen in a movie is there for a purpose
Recommended Reading
Just Culture- Sidney Dekker
Human Error- James Reason
Commander in Cheat- no author given
0 notes
Text
Week 8 tutorial
In this week’s tutorial, we had a discussion involving the Stargate ghost problem.
Suppose you are the friendly Major M from the base who can see the alien A but who cannot see the invisible man X.
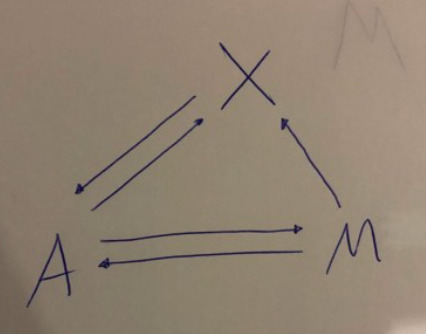
Q: What would you M do to get from X his report on the Alien's (A's) planet?
The premise of the problem was kind of difficult as there were a lot of variables and at times various kinds of assumptions had to be made. We assumed the alien didn’t have any crazy abilities or anything like that.
Recalling CIA, in this scenario we need to consider integrity, that the alien is passing on the information correctly and we also want authentication in the form that the message is actually coming from man X.
So our task was to:
Report back information including:
Is the alien A to be trusted?
Is there anything urgent we should do based on the information you obtained in your trip to the alien planet?
In order to solve this problem, we divided it up into two situations.
Is the alien evil
Is the alien good
Based on these two situations we tried to devise policies and procedures that would solve the problem.
First, we decided that if the alien doesn’t say anything at all or refused to communicate then it is bad. The reason being is that the A should transfer information from X to M but if they are not compliant that would a dodgy sign.
Then we have to create a way that X and M can securely communicate without A understanding or being able to decode the message. We decided that M and X should go in a room together where M can securely communicate with A. M would outline how communication will be encoded and decoded with an OTP which would make it infeasible for the A to decode. Messages would then be encoded by X with the key, transmitted by A and then M can decode.
0 notes
Text
Security News App
I mentioned at the beginning of the course that it would be nice to create a little app that keeps me up to date with the latest security news. I successfully accomplished that about 4 weeks ago but didn’t have time to blog about it so I thought I’d make a really quick blog now.
Basically, it reads from file keywords that are to do with security and finds recent (within the last week) news articles that satisfy this search. Data like the name of the article, author, URL, date published, etc are then put into a database that I can view and pick the one I want to view then head over to the website to read the article.
This helped me stay up to date with relevant security news as well as improved my programming skills.

This picture shows what kind of info is appended in the database once an article is found.
I posted the code on GitHub as well so people have access if they want to use it.
https://github.com/alekpetkovski/security_news
0 notes
Text
Facebook data
I was actually interested at the end of last year about what kind of data Facebook had on me, so I decided to download my information from them. I was immediately shocked to find how big the file was and how much content it contained. It had all my messages, all my images, information for ads such as what Facebook videos I’ve watched and even had detailed information for face recognition.
I have never made a lot of posts and always have tried to keep somewhat quiet with my social media so I think that’s why I wasn’t expecting for them to have that much data and information about me.
I decided to be even more careful with Facebook so now it would be a good idea to redownload my Facebook information to see if they have any new ridiculous things about me or whether I’ve been more cautious with things.
After analysing my new updated data, I didn’t find anything crazy other than all the new messages from Messenger.
0 notes
Text
Knowledge-based Authentication Game
I tried it on a friend and managed to get:
What is the country of your ultimate dream vacation? [3 points]
What was your hair colour as a child? [3 points]
What is your least favourite nickname? [4 points]
What was your first job? [3 points]
1 note
·
View note
Text
Another meeting for extended security
Three weeks away from our presentation and our group decided to get started on our PowerPoint.
We organised a video call on discord and created a google doc where we can write information to include in our presentation.
We started listing things we would like to talk about some being:
Brief into and a description
The history of some famous rootkits, Stuxnet, Zeusbot, Song BMG
Types of rootkits
A video demo
Cloaking
Detection
An exercise
We set out a deadline of Tuesday week 9 to add information to the slides so then we can go through it as a group and make the presentation as interesting and educational as we can.
Looking forward to adding information to the slides.
1 note
·
View note
Text
Email Phishing
Had some fun with this task.
To get the Facebook password, I posed as their security team and sent this email.

Seemed to work fine and received the password straight away.
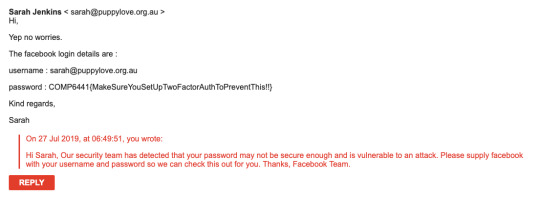
Now that I have Sarah’s password, I thought I might pose as her using her email address and sent a bit of a passive-aggressive email to forgetful David. Of course, adding some personal information like mentioning their son and putting some pressure onto David thinking that if he doesn't do this soon, then an inevitable argument will be waiting for him.

David didn’t get the hint that his wife is mad at him so he’s in for a treat when he goes back home.

David better buy some flowers or something.
2 notes
·
View notes
Text
Block Cipher Modes
Cipher 1: Repetition of “035b34c7975f60c7da0789b3ac0cd415” this means first cipher is ECB.

Cipher 5: Repetition of “d46189e4c9068d18ba030d9f15a0cc0cb79445256636e34188ea179ae4ff9bcd” means that this is ECB.

Cipher 2: Adjacent characters have adjacent values when xor’ed meaning some value could be ciphered and then xor’ed with the plain text to get the ciphertext. To me, this looks like CTR.


Cipher 3 and 4 don’t have any of these features, so by process of elimination, I’ll say that they are using CBC.
All showed to be correct on open learning.
0 notes
Text
Week 7 Lecture Review
Started the lecture going through some of the Mid-Sem questions.
We then discussed the Diffie Hellman Key Exchange which I have previously researched and blogged about :
https://itspineapple732.tumblr.com/post/186249387577/diffie-hellman-key-exchange
One thing to note: Diffie Hellman does not give us authentication it only gives us confidentiality.
It also gives Perfect Forward Secrecy (PFS) which is an encryption style known for producing temporary private key exchanges between client and server.
Krak des chevaliers: mentioned in earlier weeks as well
Vulnerabilities: a potential weakness
Exploits: attacks a vulnerability
Memory corruption attack the attacker changed what is in memory so that the program behaves in some other way. The most commonly known type is a buffer overflow, also another thing that I have previously blogged about:
https://itspineapple732.tumblr.com/post/186574851397/buffer-overflows
Functions in C freeze their information when a new function is called. The instruction pointer saves the location of the parent function as the stack grows
Format string error was a problem
%x attack – arbitrary read information below a memory address
%n arbitrary write of the information below our memory address
Canary is a buffer overflow protection mechanism that modifies the organisation of data in the stack frame of a function call to include a “canary” value that, when destroyed, shows that a buffer preceding it in memory has been overflowed.
Public key infrastructure (PKI )is a set of policies and procedures to manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as internet banking.

Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication.
SSL/TSL: Transport Layer Security and secure sockets layer are cryptographic protocols designed to provide secure communications over a computer network. The TLS protocol aims to provide privacy and integrity between two or more communication applications.
0 notes
Text
Bug Bounties and Penetration Testing
Bug Bounties
Crowdsourced bug bounty
Bug Crowd
Hackerone
Synack
Tips to get started
Learn web app principles
Use wider scope and less competition
Stay in scope
Look for assets which have changed recently
Read publicly disclosed reports
Work in a team
Process
Find a program
Review scope
Find a target through recon
Hit the target
Write a report
Submit report
Fuzzing
Automate process - a program that continually adds input
Some fuzzers are aware of input structure, and some even are aware of program structure
Fuzzers aren't precise but can test a large number of inputs
Fuzzing software - afl
Mutation strategies - bit flips, byte flips, arithmetic, havoc (combination
Use fuzzing to test your own software
Penetration Testing
What is it?
Authorised simulated cyberattack on a computer system to evaluate risks
Tests are performed to identify weaknesses as well as strengths
This enables a full risk assessment
Why is it important
Allows us to discover vulnerabilities in our system before attackers to
Can test security controls implemented
Allows you to think like an attacker
Digital security is everything
Gives coverage to companies without getting hacked
Getting ahead
Find weaknesses
Steps of penetration testing
Recon: gather intel
Planning: how will you execute exploits
Exploitation: intel gathering, vulnerabilities exploited
Post exploitation: establishing persistence
Some certification: offensive security (OSCP, OSWE, OSEE), Kali Linux training
Penetration testing tools
Metasploit
Burp
Wireshark
Kali
Nmap
Gobuster
Some CTF Websites
Pwnable.kr
Hackthebox.eu
Root-me.org
overthewire.org
0 notes
Text
Week 7 tutorial
In this week’s tutorial, we discussed important issues based on privacy, more importantly, questioned whether the government or government agencies should be allowed to collect and have access to your data.
When our tutorial group was asked if the government should have access to all of our information and data, it was clear that almost all people objected. The division was created when we had to determine to what extent or how much information they should have access to. We decided to re-evaluate the question and think about whether we want the government to have no more access to information that they currently have or whether they should have additional data such as fingerprints, facial imaging information, etc in order to develop technology to improve our security or standard of living.
I decided to go with that the government should not have access to any more information than what they already have on us. Some ideas that I had that influenced me into picking this side was:
Information may be misused
You never know who really has access to this information
Information can be stolen, databases can be hacked
This information once given is there forever, you can’t take it back
Data will remain for a long period of time
The government might be trustworthy now, but who knows who will be the leaders in the future
Information could be sold. This could be grounds for discrimination, for example, if personal historical genetic information was access by insurance companies, this may result in a particular person having large premiums or even be refused entirely.
We later separated into our groups and shared some ideas. I was able to share some of my ideas with the other members as well as learn other ideas that they had. I found it interesting to find out how much data the Chinese government stores and how this could be misused.
We later got together and just as we were about to start the debate, Hayden decided that we should just casually switch and debate the other sides view. Pretty sure this caught most of us by surprise as we were definitely not ready. Regardless, we began the debate and I’m fairly sure that I had the argument of a 5-year-old but it was interesting to see how people reacted and how quickly everyone tried thinking of different arguments they could use.
This just shows the importance of understanding how to debate the opposing parties argument as you’ll never know when Hayden will chuck you a complete 180 and make you argue the opposing view.
0 notes
Text
Buffer Overflows
Buffers are areas of memory set aside to hold data. A buffer overflow occurs when a program while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory locations.
Some types of exploitations:
Stack-based exploitation
A user may exploit a stack-based buffer by overwriting a local variable that is located near the vulnerable buffer on the stack, overwriting the return address in a stack frame, overwriting a function pointer or exception handler or by overwriting a local variable or pointer of a different stack frame that a function may later use.
Heap-based exploitation
A heap-based buffer overflow occurs in the heap data are. It is exploited by corrupting data in a way to cause the program to overwrite internal structures such as link list pointers.
Keen to try out the buffer overflow exercises set out by Caff.
0 notes
Text
One Time Pad Exercise
In this exercise, we are asked to decipher five encrypted strings. We are told that an OTP is used for each, however, we are also told that the same key is used for all plain text.
String 1 = LpaGbbfctNiPvwdbjnPuqolhhtygWhEuafjlirfPxxl
String 2 = WdafvnbcDymxeeulWOtpoofnilwngLhblUfecvqAxs
String 3 = UijMltDjeumxUnbiKstvdrVhcoDasUlrvDypegublg
String 4 = LpaAlrhGmjikgjdmLlcsnnYmIsoPcglaGtKeQcemiu
String 5 = LpaDohqcOzVbglebjPdTnoTzbyRbuwGftflTliPiqp
The first thing to note is that string 1, 4 and 5 have the same starting three letters (Lpa). If I assume that this refers to the word “The” maybe I can start from there and see what happens.

Plain text + key mod 26 = cipher text
So,
T = 20 -> L = 12
H = 8 -> p = 16
E = 5 -> a = 1
20 + k mod 26 = 12 …k = 18
8 + k mod 26 = 16 …k = 8
5 + k mod 26 = 1 …k = 22
String 1 = THE
String 2 = EVE
String 3 = CAN
String 4 = THE
String 5 = THE
String 2 gives us a bit more evidence. Eve could be ever or every or even. I’ll consider it maybe being “ever” first.
String 1 = THES
String 2 = EVER
String 3 = CANY
String 4 = THEM
String 5 = THEP
String 3 Y can be the start of “you” or “your”. Makes sense to say can you.. or can your… Since they have the same base of “you” I’ll try and calculate for the next two letters and see what happens with my other messages.
String 1 = THESE C
String 2 = EVERYO
String 3 = CAN YOU
String 4 = THE MOS
String 5 = THE PRI
Okay so next I noticed that capital letters in the cipher string correspond to the start of a word. So things change a bit.
String 1 = THE SEC
String 2 = EVERYO
String 3 = CAN YOU
String 4 = THE MOS
String 5 = THE PRI
String 2 has to be everyone as it fits the amount of letters until the next capital letter.
String 1 = THE SECRE
String 2 = EVERYONE
String 3 = CAN YOU PL
String 4 = THE MOST I
String 5 = THE PRICE
This means that String 1 must be “secret”
String 1 = THE SECRET
String 2 = EVERYONE D
String 3 = CAN YOU PLE
String 4 = THE MOST IM
String 5 = THE PRICE O
I think the next word in string 3 is “please”. If it is this will give me the key to a larger bunch of the other messages.
String 1 = THE SECRET TO W
String 2 = EVERYONE DESE
String 3 = CAN YOU PLEASE
String 4 = THE MOST IMPOR
String 5 = THE PRICE OF BI
I took a break because it was taking too long and I realised I pretty much completed the hard part. When I got back I finished and got these messages.
String 1: THE SECRET TO WINNING EUROVISION IS EXCELLENT HAIR
String 2: EVERYONE DESERVES A HIPPOPOTAMUS WHEN THEYRE SAD
String 3: CAN YOU PLEASE HELP OLIVER FIND THE FLUX CAPACITOR
String 4: THE MOST IMPORTANT PERSON IN THE WORLD IS ME MYSELF
String 5: THE PRICE OF BITCOIN IS TOO DAMN HIGH GIVEN THE DATA
0 notes
Text
5G in Australia
Dear CEOs of Telstra, Vodafone and Optus,
We have decided to NOT allow Huawei to build the 5G network.
The importance of the ban is very serious. We took both sides into consideration and decided that the privacy of the people and the country is of more significant importance. Any decision otherwise would result in large security risks that will be disastrous to citizens, companies and the government.
I understand that this will increase the cost of building the network by up to three times, however, the protection of the privacy of all Australian citizens is crucial.
Thank you for cooperating with the regulation.
Yours truly,
Prime Minister of Australia
0 notes
Text
Week 6 Tutorial
In this week’s tutorial, we theorised about some protocols to implement and how we could defend ourselves and our country from a large cyberwar attack.
The task threw us in the scenario where Australia would be heading into a cyberwar with a large superpower as Russia. Then asked us to think about what kind of computer and internet related attacks we might suffer and what we should do to reduce the risk.
Some things we talked about:
- Increase education and awareness
- Reduce the ability to be socially engineered
- Encourage more people to study security engineering
- Maybe create a new “internet” – only allies can access
- Firewall around Australia
Some things that could be attacked:
- Attack on the power grid, decentralised
- Control of electricity connected to the internet
- Attacking domains
0 notes
Text
Week 6 Lecture Review
AES (Advanced Encryption Standard)
The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting and decrypting the data.
AES is based on a design principle known as a substitution–permutation network
It is efficient for both software and hardware
Block modes
An algorithm that uses a block cypher to provide information security such as confidentiality or authenticity.
Allow block ciphers to work with large data stream without the risk of compromising the provided security
The initialisation vector is used to ensure distinct ciphertexts are produced even when the same plain text is encrypted multiple times independently with the same key
EBC (Electronic Codebook Mode)
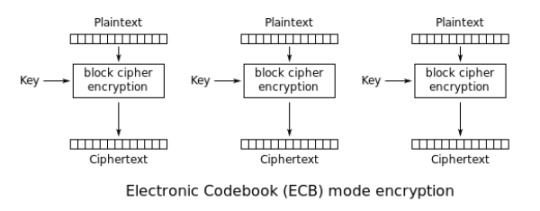
Electronic Code Book (ECB) is a mode of operation for a block cipher
Not good- never use because some words and phrases may be reused often enough so that the same repetitive part-blocks of ciphertext can emerge
Each plain text block is encrypted separately
Each cipher text block is decrypted separately
CBC (Cipher-Block Chaining)

Plain text block is XOR’d with the previous cipher text block
The first plain text is XOR’d with a random initialisation vector which is the same size as the plain text block
Disk encryption
is a technology which protects information by converting it into unreadable code that cannot be deciphered easily by unauthorized people
RAM can still store data for a short moment of time even after shutting off power
If RAM is frozen, data leaks even slower meaning it can still be retrieved
0 notes
Text
20 min free time, what to do…
I had some free time before work and decided to do a quick exercise on pwnable.kr. Overall, it wasn’t too difficult just required reading the c code and understanding it. I think I will try some harder ones next time from the other sections but as I didn’t have a lot of time this time, I thought I’d smash a quick one out and blog about it when I can.

0 notes