Don't wanna be here? Send us removal request.
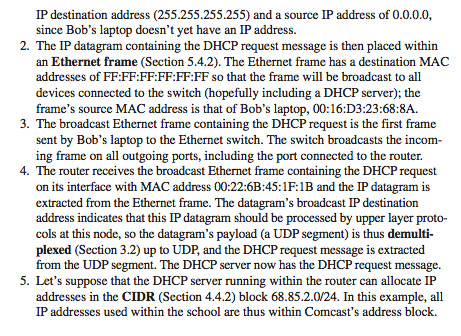
Text
F-stop, focal length, DOF
The greater the F-stop number the further the depth of field, vice versa.
Depth of field is the distance between the farthest and the nearest objects in a scene that is acceptably sharp.
F-stop is the ratio of the focal length and the aperture size. Assuming the focal-length is the same, the aperture size affects the image plane like so:
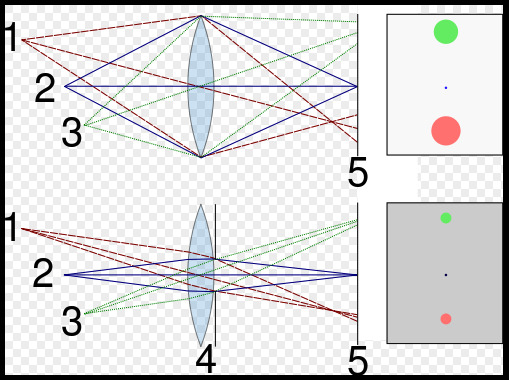
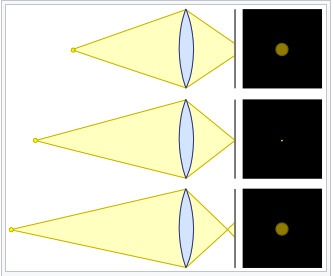
The greater the aperture, the greater the circle of confusion. Circle of confusion is occurs when a cone of light from a lens is not in perfect focus when on the image plane.
0 notes
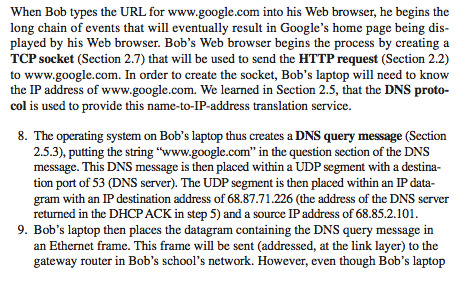
Text
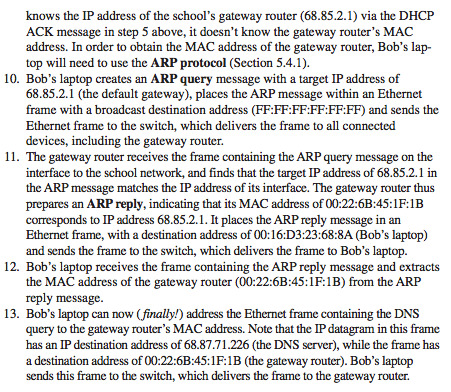
MetalBadExample
Optimizing metal could mean trying few things:
1. stage_in qualifiers to prevent indexing into buffers all the time. (https://developer.apple.com/metal/metal-shading-language-specification.pdf 4.3.5 stage_in qualifier and MetalByExample)
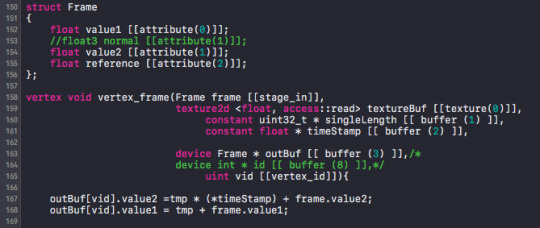
i. Create struct for each “vertex”.
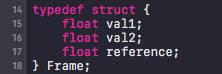
ii. describe the vertex attribute
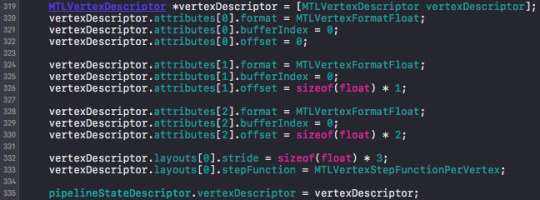
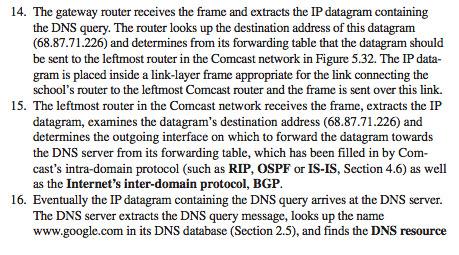
iii. create buffer as usual
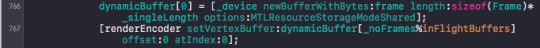
iv. in vertex shader use it assuming it is indexed into the right vertex already.
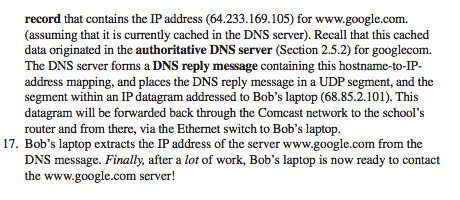
Note: this method I couldn’t write back into the frame. Thus I needed a outBuffer. Stage_in would work for vertex, fragment and kernel shaders.
2. Using NewBufferWithBytesNoCopy if possible to save memory and reduce copy speed (this requires power of 2 memory length).
3. Recycling buffer output to use as buffer input.
4. Use Dynamic buffers ie. tripple buffering. If processing time is longer than loading time, then commit up to 3 command buffers while waiting for the GPU to complete processing.
0 notes
Text
Working with Bytes python
Good reference here using the struct module and here.
0 notes
Text
AWS Lambda S3 execution
Creating an endpoint that triggers a lambda function to delete a file from S3 in Python. Using only the boto3 python module.
1) Create an IAM role to allow lambda to communicate with S3 and cloudwatch (for logging). example below:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents" ], "Resource": "arn:aws:logs:*:*:*" }, { "Effect": "Allow", "Action": [ "s3:PutObject", "s3:GetObject", "s3:DeleteObject" ], "Resource": [ "arn:aws:s3:::bucket-name/*" ] } ] }
first section gives cloudwatch permissions. Then gives permissions to execute S3.
2) Next we create an API gateway, and create resources. Which would be the endpoint from the given URL (after deployment) that will run the lambda.
Then create Method and select POST. Follow the prompts and choose Lambda function. which will again prompt to create a lambda function.
3) Creating a lambda function. Select a Blank canvas and choose API gateway as a trigger to the lambda function
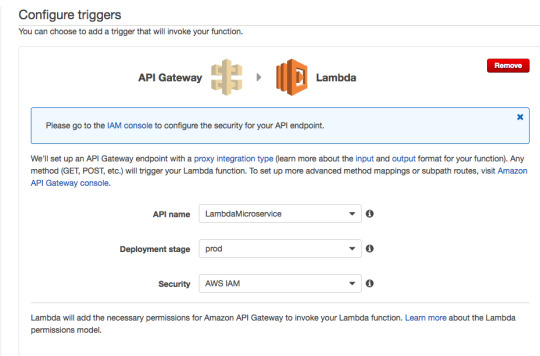
Just choose Python, input the code and hit next. You can test the function with JSON data. The Events parameter in the function contains the POST data.
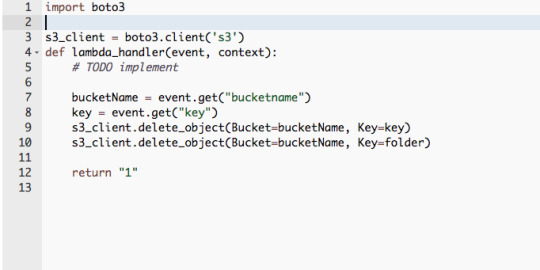
4) Choose Deploy stage. This generates a URL, where you attach a resources you created to build the URL that will trigger the lambda function. Good boto3 reference on how to call the relevant functions for S3: http://boto3.readthedocs.io/en/latest/reference/services/s3.html#S3.Client.delete_object
0 notes
Text
Python & IOS send POST request with JSON
PYTHON First import the modules: import requests, json
the structure of the request would be:
r = requests.post(url, data=json.dumps(data), headers=headers)
url would be the url string;
data = { “key” : “value”, “key2” : “value2″, “key3″ : “value3″}
headers = {'Content-type': 'application/json'}
print r.status_code if it’s 200.
r.json() is the server’s response. Objective - C
Using semaphore’s if i want the request to be synchronous.

0 notes
Text
Key value observing
Key Value Observing allows us to be notified when the value for a variable has been changed. This can be Class A notified when a value in class B has been changed or Class B notified when its own variable has been changed.
Eg. when downloading a file, and a ViewController is presenting a downloadprogress bar. The minute a byte has been downloaded, the download progress bar should be notified of the change in bytes downloaded. A long and “traditional” method of doing this would be to use thread and a couple pointers. Thus we can pass the pointer around and have the thread spin on the dereferenced pointer. EXHIBIT A: I did this by having a queue sleep for 0.5 seconds, then waking up calling a getter of the observing object if the variable has changed.
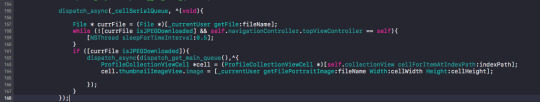
EXHIBIT B: On a background thread, malloc a couple pointers. pass the pointers to the object. Dereference the pointers and update the UI according to the value. The example below contained legacy code, after changing the approach slightly. But initially the pointers would be passed in at the beginning. Then we can just read the value by dereferencing it everytime.
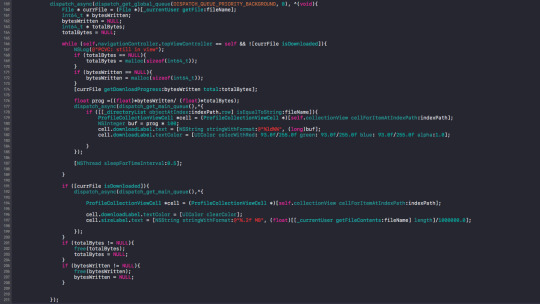
OKV: This works on 3 main things. 1)Key value code, KVC, a variable is represented by the String. 2) registering an observing and observer object. 3) the context to determine which object changed.
Note:
Changes in the variable are registered only by using the setters and getter. eg. self.var instead of _var.
works for all types except pointers. Because technically the value is the address, and that never changes, would have to dereference that.
When notified, the process would be running on the same thread that changed the variable.
I register and unregister observers like this:
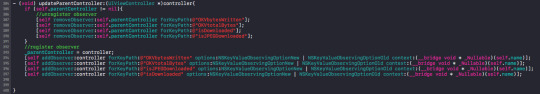
Example of how to change the variable. Eg. changing self.isDownloaded.
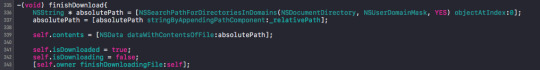
When self.isDownloaded = true. Observe value for keypath gets called, keypath contains the KVC of the variable changed. To determine which object that was downloaded, assuming if i download multiple objects at the same time, I register the observer with name as the context. Thus when notified, I use the name to determine which object has just been downloaded.
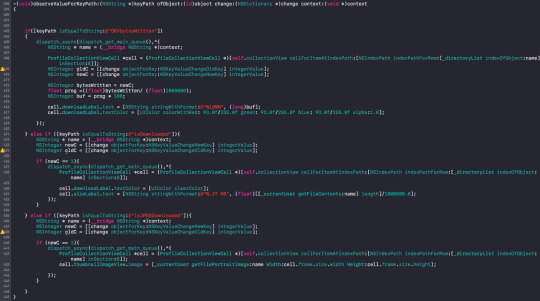
This saves me a lot of queue management. Alot less code and easier to track!
0 notes
Text
Objc dispatch aysnch
Dispatch queus and little things to remember. KNow more here: https://developer.apple.com/library/content/documentation/General/Conceptual/ConcurrencyProgrammingGuide/OperationQueues/OperationQueues.html#//apple_ref/doc/uid/TP40008091-CH102-SW1
Each dispatch queue is a code block. When the queue is first entered, the task returns immediately, but if there is a while loop within the block, and the loop breaks, the task will not return again.
Use each block by independently, create variables from scratch. always check variables still same. Remember that there is a limit of 64 threads, thus use dispatch queues sparingly with lockz
0 notes
Text
IOS objc useful tips.
1) To pass callback methods in obj c.
http://stackoverflow.com/questions/26778798/how-to-pass-callback-method-as-parameter-in-ios
2) Otherwise to create completion blocks:
http://stackoverflow.com/questions/16324095/custom-completion-block-for-my-own-method
3) When creating ViewControllers. Use Segue (show) without always using navigation view controller, And pass parameters between VCs like this.
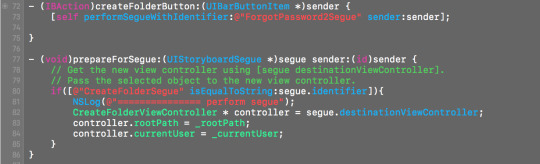
To pop to previous VC.
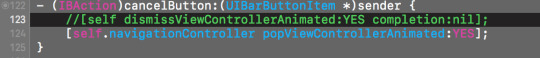
Note: [self dissmissVCAnimated:YES completion:nil] would actually dismiss the whole navigation stack, and return to the last navigation controller, which may be tooo far back. Where as popVC just removes the top VC.
4) Notifier for internet connection
To be notified when there’s a change in internet connectivity. Instead of having a background thread constantly polling for internet. Uses Reachability.h and NSnotificationcenter. Similar to Key value observing.
To setup the notifier:
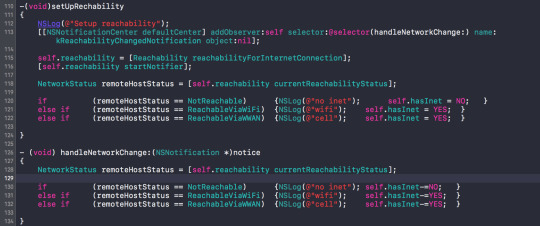
Remeber to remove observer from nsnotificationCenter when object not needed.
0 notes
Text
NAT (network address translation)
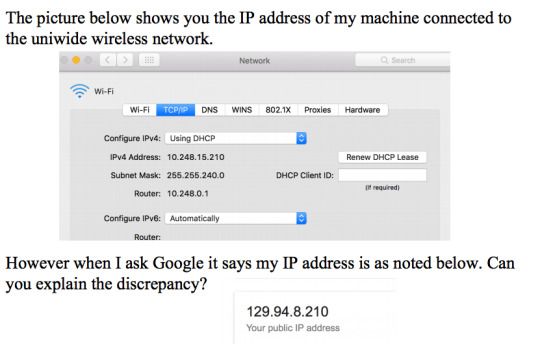
10.248.15.210 is the ip address in the private network. This only makes sense in the private network. This is behind the NAT router.
The public facing interface of the NAT router will have the public ip address which is the ip address Google shows, the NAT router.
The subnet mask is 255.255.240.0 which indicates that the network part of the address is 20 bits and the host part is 12 bits.
The CIDR address of the subnet is 10.248.0.0/20.
The broadcast address in the subnet is 10.248.15.255
The total # of usable address and thus hosts is 2^12 -2 = 4094 hosts. (-2) 1 for broadcast address, 1 for network address.
NAT
- Range of IP addresses not needed from isp. just one ip is needed.
0 notes
Text
The nuts and bolts of how google.com gets served on everyone’s web browser!
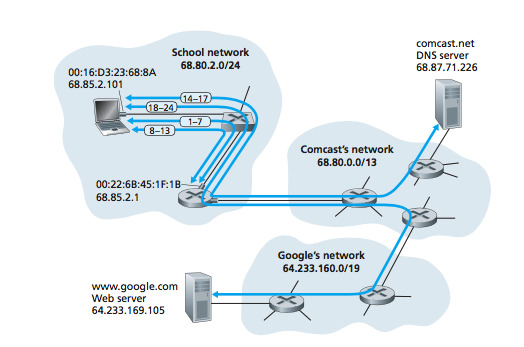
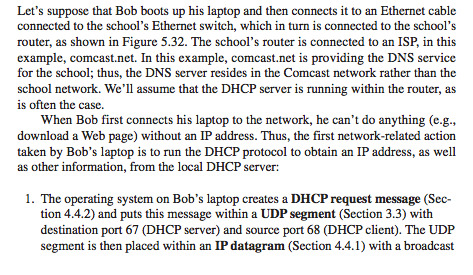



0 notes
Text
OS terms
Binary Translation - The emulation of one instruction set by another through translation of binary code. Static binary translation aims to convert all of the code of an executable file into code that runs on the target architecture without having to run the code first. Dynamic binary translation looks at a short sequence of code then translates it and caches the resulting sequence. Eg. running Super Mario Bros NES - to - x86.
QEMU - Hypervisor that performs hardware virtualization (not complete hardware virtualization). Emulates CPUs through dynamic binary translation and provides a set of device models to run a variety of unmodified OSs.
Linux kernel - monolithic unix-like computer operating system kernel.
KVM - is a virtualization infrastructure for the linux kernel that turns it into a hypervisor. KVM requires a processor with hardware virtualozation extensions.
Paravirtualization - is a virtualization technique that presents a software interface to virtual machines that is similar but not identical for the underlying hardware. Eg. an api by the guest os for the host os to communicate with each other, thus little modification is necessary.
Trap and Emulate - in virtualization, when the VMM can trap all attempts by other guest OS that might conflict with other guest OS and the host OS seizes control and take alternative actions while the guest OS is still unaware.
Note: Most definitions are wikipedia definitions.
0 notes
Text
Co-routines/setjmp/longjmp in C!
To abstract away the low-level coroutine process, we need 4 interface functions. They are: yield(int id), init_coroutine(), exit_coroutine() and coroutine_wake(int id).
An example of a way to use coroutines can be seen in the example of calling sleep(1000):
1) In the event loop when a syscall is received. we call init_coroutine(), this returns an id. In here the coroutine struct is setup, the individual stack for the function, change the stack pointer fr the curr stack to the new stack and the setjmp(loop).
2) Then we call the function that handles sleep (handle_sleep). Within we register a timer with a callback function which is coroutine_wake(id) to be called when the timer wakes up. After registering the timer, we call yield() to block, so that we wont return to user from the syscall.
3) Within yield(id). We simply setjmp(sleep), then longjmp(loop) to go back to when setjmp(loop) was called in (1) by init_coroutine from the event loop. This allows us to go back to the event loop to handle other syscalls or IRQs.
4) When the timer is up and the callback function -> coroutine_wake(id) is called. Where setjmp(loop) is called (to save the current context), then longjmp(sleep) back to yield() in (3). Where yield will return to the handle_sleep function and syscalls back out to user land.
5) handle_sleep then return to the event loop which calls exit_coroutine(id) at the end of the loop. which simply calls longjmp(loop) which jmps to when setjmp(loop) was called in coroutine_wake in (4) to switch the state back to the previous context before timer interrupt. Back in coroutine_wake, next it will call dealloc_coroutine which frees the stack.
6) Then it returns from coroutine_wake to timer_pop and back to the timer_interrupt in the syscall_loop.
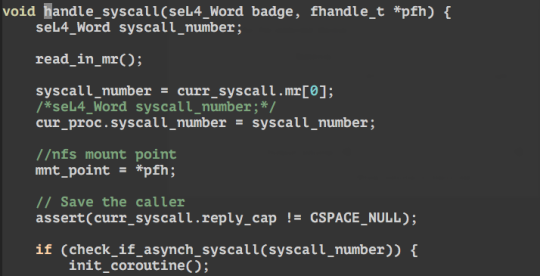
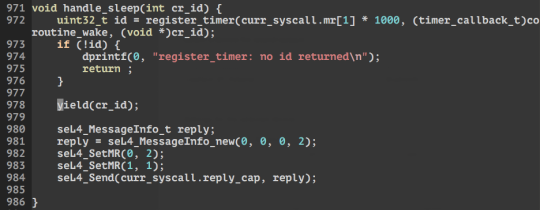
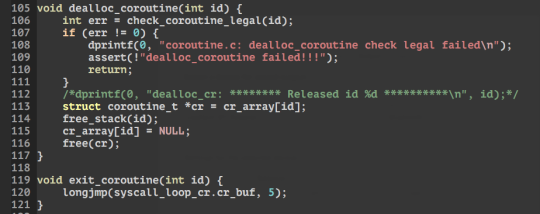
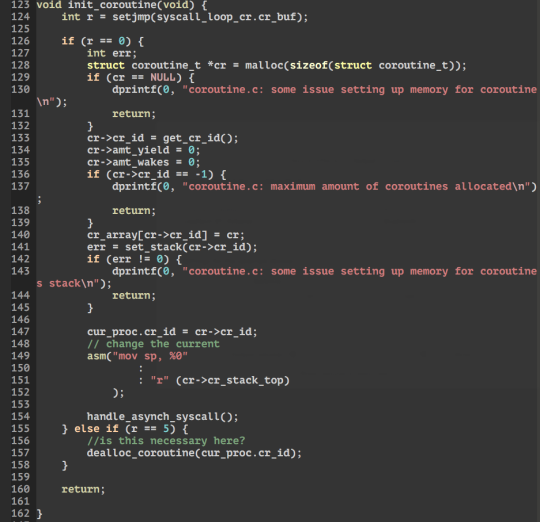
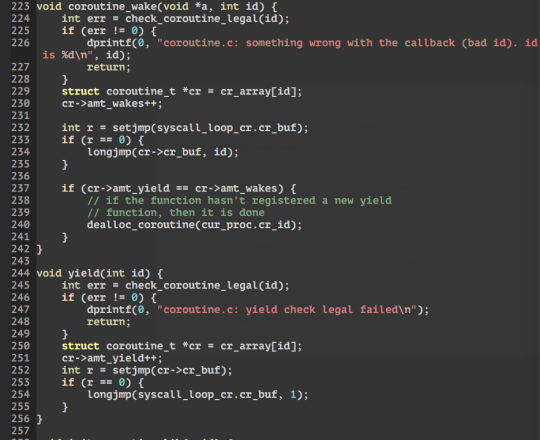

=====================UPDATE================== Co-routines allow multiple entry points into a function whilst suspending and resuming execution in certain locations. In my interest this is suitable for multitasking/ cooperative tasks! C provides to functions to achieve this from the setjmp.h library suitable for C99, they are setjmp and longjmp defined here. in summary: int setjmp(jmp_buf env); Saves the state of the current environment into the buffer jmp_buf. returns 0 when this macro is called, and returns an int when return from a longjmp. void longjmp(jmp_buf env, int value); restores the environment saved into env, and returns to when setjmp was last called. Setjmp that returns from longjmp will return whatever that was passed into value. Still learning how to implement it for the sos on seL4. but so far here, here, here and here are great resources for basic understanding.
0 notes
Text
HTTPS, SSL CERTS, letsEncrypt!
For the last 2 weeks I had been struggling to setup the SSL certs on a wordpress site hosted on AWS-EC2. What I have learnt, is that there are 3 types of certs (http://docs.aws.amazon.com/elasticloadbalancing/latest/classic/ssl-server-cert.html). - The server.crt (with your domain name) DOMAIN.crt - the intermediate/chain crts (these are the crts that your CA were issued, its like CA1 issues to CA2 and CA2 issues to YOUR-CA, these 3 crts make up the chain crt, so that your crt can be traced to the root cert, CA1, to ensure it is really valid). - the private key (often a one-off downloaded key, cannot lose or fk up). The issue with these certs is that they have to be from a certified authority (CA) or browsers wont trust the cert (compared to a self-signed crt). You can pay for a crt or use lets encrypt (https://letsencrypt.org/getting-started/) for a free one yet still by a CA? it was crowd funded! As the wordpress site used bitnami i followed this guide (https://docs.bitnami.com/aws/components/apache/#how-to-install-the-lets-encrypt-client). which was fairly easy, except they didnt mention it, but you need to change the conf file to include the chain.crt or it still wouldnt be secure. To include the chain.crt i used this guid (https://seiler.it/lets-encrypt-your-server/). I checked with https://www.sslshopper.com/ssl-checker.html , so glad to see the green ticks. fk yea.
To change all assets on web page to ssl secure https://managewp.com/wordpress-ssl-settings-and-how-to-resolve-mixed-content-warnings
To check for unsecure assets on page : https://www.whynopadlock.com/
0 notes
Text
Stack in python
To implement a stack in python.
Use an array, because it is ordered and you can pop by array.pop(0) (pop the zeroth index everytime), and can poll by just accessing the 0th index.
Basic functions
- To push: if value not in array: array.append(value)
- pop: array.pop(0)
- poll: array[0]
0 notes
Text
How to write an AI
Problem:
- The AI has to play a game http://webapps.cse.unsw.edu.au/webcms2/course/index.php?cid=2441&color=colour8, it has to decide either to move or to perform an action. If it has to move, it has to decide which tile to move to. If it has to perform an action it has to decide what action to do.
- Furthermore, AI has to decide when to use the tools. Ei. when does it know to walk away from a door, if it has no keys. and when to walk to a door if it has a key.
Solutions:
- Potential solution is to use potential fields. Based on a smart algorithm and logic, the tiles will be constantly updated with pf (potential field) values. Eg. if a tile has a key, the pf value for that tile and its neighbouring tiles will be very low.
- The agent then decides which tile to move to based on the pf Values.
- All the logic for deciding where to go next based on what it sees is decided in the pf calculations. Ie. the pfUpdate will update the tiles if a door is seen but agent has no key, so no priority is given to move to door yet because agent cant do anything, but probably higher priority is now given to finding a key.
- Agents only sole purpose is to read the pf values and perform action appropriately.
Note:
- This is done in python, will try to rmb to update with python stubs
0 notes
Text
basic dictionary, OrderedDict, keys
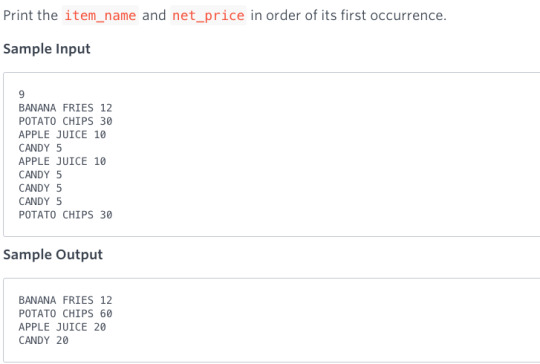
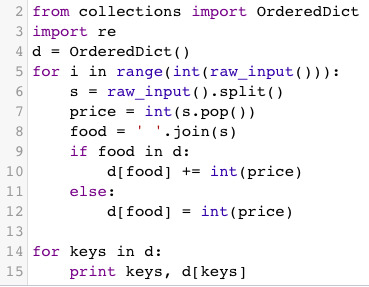
note: - line 9, 14, to check if a key is in a dictionary, just use key in d. - line 14, similar to perl - note use of OrderedDict, to maintain the order keys are added to the dict. THis is an issue in perl
0 notes
Text
Regex, repeating chars

To filter out a string that dont fit the above criteria. The trickiest for me was vetting numbers with 4 repeating numbers in a row.
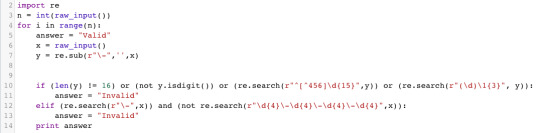
Note line 10: this was done with the last condition, (\d)\1{3}, this means if a character is repeated more than 3 instances, it will be invalid. This is a regex expression I have not encountered before.
0 notes