Don't wanna be here? Send us removal request.
Text
Battle Against Cybercrime!
CEID100 Final project on Cybercrime with Fahmy, Samin, and Gurkirat!
0 notes
Text
Dear fellow citizens,
I am sure you are familiar with how digital technology has revolutionized our daily lives. The integration of digital technology has brought crucial changes in our lives, affecting communication, work, learning, and entertainment. The pace of innovation is rapid, and digital technology is increasingly becoming an integral part of our daily routines. It is clear that we are living in a digital transformation era.
In this era of technological advancements, we hold the ability to create a positive digital future. Three technologies that hold the power to provide a high positive impact are 5G, quantum computing, and blockchain. Below are several ways in which these technologies have the power to make a significant impact:
5G: High-speed connectivity and low latency of 5G technology can build impressive applications and services, such as factory automation, smart offices, and remote healthcare. 5G can positively impact the way we convey and communicate, building strong and sustainable systems that can enhance the quality of life while reducing our carbon footprint.
Quantum Computing: Quantum computing can be the answer to prominent problems like climate change and epidemics. Harnessing the ability to operate abundance of data in a reduced time block, quantum computing has the ability to enhance scientific research and breakthroughs in specializations like drug development and renewable energy.
Blockchain: Having the ability to use transparency, security, and efficiency, blockchain technology can revolutionize plenty of industries including finance, healthcare, and the pharmaceutical industry. Blockchain has the ability to build trust and accountability in various industries by creating decentralized systems that are powerful against fraud and hacking.
Throughout the transformation of the digital era, it is pivotal to understand that technology is a machine, and it is in our hands to use it for the greater good. With the power of 5G, quantum computing, and blockchain, we have the ability to build a more connected and efficient world.
We should come together and build a digital future that's innovative, efficient, and aids the well-being of all living beings and our planet.
Sincerely,
Fahmy
0 notes
Text
What is Javascript?
JavaScript is an interpreted, high-level programming language used mainly for building interactive web pages and web applications. It is a critical programming language for modern web development and is widely regarded as one of the core technologies of the internet. JavaScript implements developers to create dynamic and interactive user interfaces, modify web page content, and manage asynchronous events. Its adaptability is one of its significant advantages, as it can be utilized on both the server-side and client-side of web applications. Hence, it has become a widely popular programming language, with a significant community constantly contributing to its development and innovation. With its large popularity, proficiency in JavaScript has become an impressive skill for anyone wanting to pursue a career in web development or programming.
Utilizing codeacademy.com, I was able to learn about the important functions and utilities of Javascript. I took the Learn Javascript course, I did a few projects and some quizzes. I learned an extensive amount of knowledge on Javascript. Not only was the course super educational, it was also very fun! Take a look at some of my badges.



0 notes
Text
Epidemics and Outbreaks
In my role as the CTO of a new start-up Ahshav, I am ecstatic to convey our strategy to implement big data and deep learning to address the significant issues constituted by epidemics and outbreaks. These complex and ever-changing circumstances require quick and accurate data analysis to control their spread. We are positive that with the abundance of big data and improvements in deep learning algorithms, we can utilize these tools to transform the process of detecting, monitoring, and reacting to outbreaks.
COVID-19 revealed the disastrous impact of epidemics and the importance of swift action. However, traditional methods for detecting and managing outbreaks have been slow, leading to significant aftermath.
In module 9, the properties of deep learning and applications of AI are thoroughly conveyed. Our team aims to innovate an AI-driven system that can merge and scrutinize diverse forms of extensive data, such as medical records, social media, and environmental information, to present immediate perceptions into the progression and gravity of an epidemic. To make this possible, we will make use of deep learning algorithms to devise predictive models capable of recognizing patterns and irregularities within the data. Through constant evaluation of information obtained from various sources, our system can promptly notify healthcare practitioners and governing bodies about the initial stages of an outbreak, empowering them to adopt pre-emptive measures to halt its proliferation.
As well in module 9, the major concepts of supervised and unsupervised learning are conveyed. Supervised learning is the procedure of training an AI model using labeled data. Labeled data implies that the data is already classified, and the model can learn from it to make predictions on new data. In the context of epidemics and outbreaks, we can employ supervised learning to train models to detect patterns in healthcare data such as symptoms and diagnoses, and alert healthcare professionals of potential outbreaks.
Unsupervised learning is the procedure of training an AI model without labeled data. The model recognizes patterns and anomalies on its own, without being instructed on what to search for. In the context of epidemics and outbreaks, we can use unsupervised learning to identify patterns in social media data, news articles, and other information sources that may signify the initial stages of an outbreak.
Our goal is to use AI to detect and address outbreaks before they become global pandemics. Through big data and deep learning, our platform can significantly impact the fight against epidemics. We are ecstatic to continue our work and believe AI has the potential to revolutionize outbreak detection and response.
0 notes
Text
What is Notion?
Module eight conveys the topics of innovation. Notion is a popular productivity app that has innovated in the recent years. Infographic on Notion and Innovation utilizing concepts from Module eight below!
https://infograph.venngage.com/ps/9o24Zl8glo/what-in-notion #infographic
0 notes
Text
Malware and Cyberattacks
Cybersecurity has become a vital component of our everyday lives in the interconnected world we live in. Cyber attacks are a constant threat that affects personal devices and large-scale institutions alike. We no longer question whether an attack will happen in this digital era, but rather anticipate when it will occur.
In the NOVA Cybersecurity lab game, gamers are tested with various sorts of cyberattacks. A major concept in Module 7 is viruses. Malicious software that infects other programs, creates copies of itself, and proliferates to other computer systems is known as a computer virus. The NOVA game enhances our knowledge of viruses and aids in identifying them much quicker.
Another critical topic in Module 7 is ransomware. Ransomware is a type of malware that restricts a user's access to their device or files, and demands payment to regain access. This type of attack is not limited to specific targets, as both individuals and various entities like businesses and organizations are commonly targeted by ransomware attackers. The NOVA game puts us in the real world and exposes to various sorts of ransomware.
The third major concept in Module 7 is leaks and data breaches. A data breach is an occurrence where confidential, sensitive or protected information is made available to an unauthorized individual. In the NOVA games, users are exposed to extensive data breaches which enhances their knowledge on cyberattacks.
I had the chance to play the game myself and here is a screenshot of my progress! Enjoy!
0 notes
Text
PSA: Barriers to Access
Did you know that one in seven people have a disability? Have you thought about the countless barriers they face when they are on the web? One cannot comprehend the level of frustration and unwelcomeness they must feel. Let's make website accessibility a priority and create a more inclusive online environment for all users! Check out this video: PSA - Barriers to Access!- Samin, Fahmy and Gurkirat!
0 notes
Text
Misinformation, Disinformation and Malinformation
In module 5, we discuss the serious consequences of misinformation, disinformation and malinformation. Misinformation, disinformation and malinformation are different types of information that can mislead people. While they all have inaccurate information, their intent and level of accuracy differ.
Misinformation is false information that is not meant to deceive and can be spread unintentionally.
Disinformation, on the other hand, is deliberately misleading information that is spread with the aim of deceiving, creating confusion, or causing harm to individuals or organizations for personal gain. Disinformation is often spread through digital platforms and can lead to severe consequences.
Malinformation is incomplete or inaccurate information that is not intentionally deceptive, often due to lack of knowledge or misunderstanding.
Below are examples of misinformation, disinformation and Malinformation.
Misinformation
Incorrect Measures
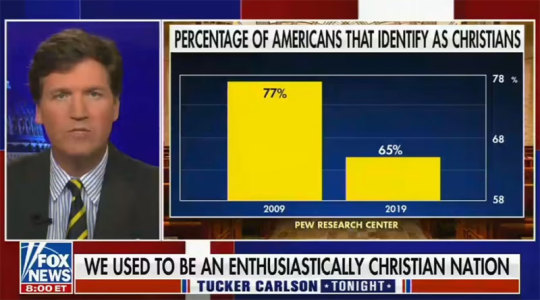
Graphically inaccurate statistic on Fox News
During a Fox News segment, the anchor presented a chart depicting the percentage of Americans who claimed to be Christians. The chart illustrated a significant decline in the number of Christians over the past decade. Specifically, it showed that in 2009, 77% of Americans identified as Christians, while in 2019, only 65% identified as such. However, it is important to note that the actual decrease is not as significant as the chart suggests. The graph's vertical axis starts at 58% and ends at 78%, making the 12% decline from 2009 to 2019 seem much more dramatic than it really is. This conveys misinformation using inaccurate statistical measures.
2. Disinformation
QAnon

QAnon Logo
QAnon is a complex conspiracy theory that claims, among other things, that a group of Satanic pedophiles controls Hollywood and the upper echelons of the Democratic Party. The theory attributes the name Q to a supposed member of the "Q Team," a group of military intelligence and high-level civilian insiders who are working to dismantle the supposed cabal. The theory holds that the Q Team will collaborate with former President Donald Trump to achieve this goal. Those who believe in the QAnon conspiracy theory are anticipating the occurrence of two significant events - the "Storm," which refers to the mass arrest of powerful individuals, and the "Great Awakening," which denotes the moment when everyone will come to recognize the validity of the QAnon theory. QAnon conveys rapid disinformation spreading through online platforms.
3. Malinformation
Jeff Bezo's 2018 Texts

Jeff Bezos's texts sent to Lauren Sanchez
In the beginning of 2018, Jeff Bezos had announced his divorce with wife, Mackenzie Bezos. Soon after the announcement, it was revolved that he was engaging in an extramarital affair with Lauren Sanchez. Jeff Bezos allegedly sent her explicit photos and messages. These included a photo of his genitalia and several shirtless pictures. The leak of these private texts to Sanchez has led to multiple inquiries into how the Amazon founder, Washington Post owner, and one of the wealthiest people on the planet could have had his personal information extracted from his phone. This is a perfect example of malinformation with the intent to hurt Bezos's image.
0 notes
Text
Cybersecurity and Cybercrime
In Module 4, the main tasks were to create a group and propose a topic. Our group has chosen the topic of cybersecurity and cybercrime to propose for our final project. This topic is heavily encompassed throughout this course. We have discussed issues with cookies and site trackers. This can all correlate to the larger topic of cybersecurity and cybercrime. For our format, we have chosen Prezi and included a VoiceOver for our presentation. We hope you love our presentation as much as we loved making it! - Fahmy, Samin and Gurkirat!
0 notes
Text
Are you being watched right now?
"Don't find customers for your product. Find products for your customers."- Seth Godin
The internet is a vibrant community that connects the world together. It is also an amazing place to advertise and build a market. Businesses over the world have flourished due to online marketing and website tracking. Cookies are a type of website tracker that correlates an individual with ads they might have an interest in. Nowadays, almost every website has cookies and website trackers. Cookies and website trackers are a significant advancement in the field of advertising.
I visited over 6 sites, to track how much I was being tracked. Using Disconnect, I was truly able to conceptualize the extent of online tracking. I was mind blown by how much information is being gathered. The site that had the most amount of tracking was Amazon. I was searching for a phone charger and I had numerous website trackers and cookies gathering information.


In the above screenshots, the website trackers and cookies are visually conveyed. Google is a major website tracker and it generates a large revenue from ads. Almost every website, I visited had google as a website tracker. The idea of being tracked constantly and my information being gathered both intrigued me and terrified me. Advertisement and marketing is crucial for businesses, it also makes the Internet such a vibrant community. Although, It does bring up important questions on online privacy.
0 notes
Text
Investigating web accessibility of Gov.uk
CEID100 module 2 Tutorial assignment
5 annotations for web accessibility (Gov.uk)
0 notes
Text
Authenticity of Digital Media
"You cannot buy engagement, You have to build engagement."- Tara-Nichole Nelson
Over the past two decades, social media and online networking have changed our lives significantly. A critical portion of social media is about our self-presentation and self-branding. Being our true and authentic selves is a profound part of curating ourselves online. Personal image and brand in digital media plays a significant factor in our daily lives and relationships.
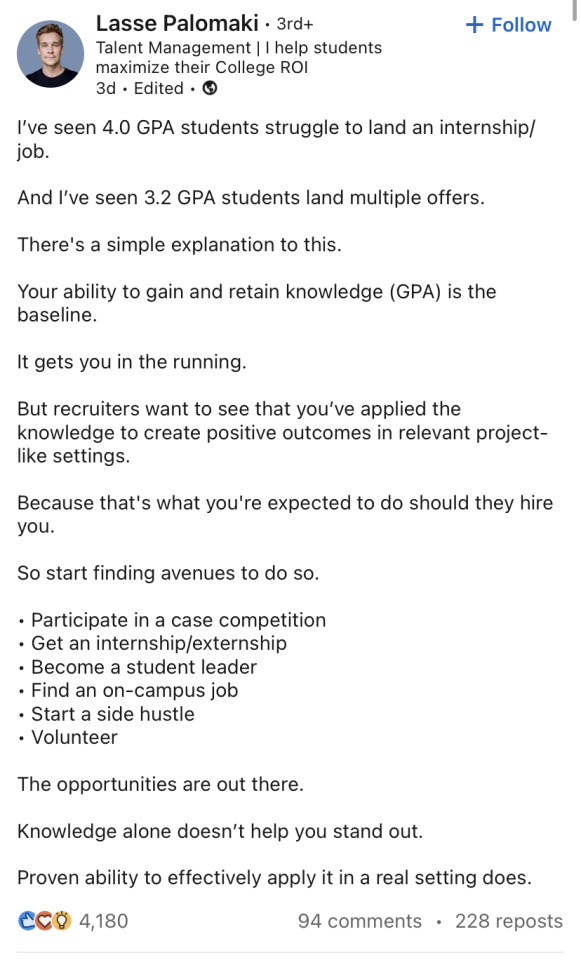
In module 1, we discuss the inner workings of personal branding. We examine an infographic with guiding principles and swot analysis. In the above screenshot from LinkedIn, Lasse helps students build connections and make leaps in their career. His personal brand and target is aimed at ambitious students in post secondary. His competitive advantage comes from his network relations and expertise. What makes this post stand out is the authenticity and engagement. He starts off the post with an authentic experience he has seen, and then he engages his target audience by providing them with advice they are interested in. Throughout the post, he is very distinctive and marketable. This is a perfect example of what a genuine and successful personal branding is.
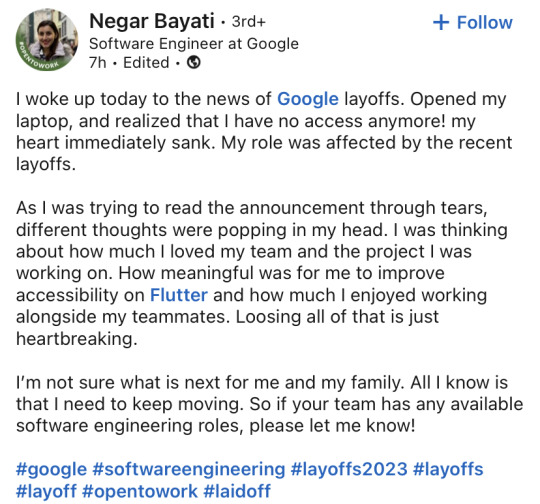
Life has its ups and downs. In the digital media age, usually the best parts of our lives are displayed. This gives others an illusion of our lives. In the above screenshot from LinkedIn, Negar discusses her layoff from Google. Obviously, she is very upset about her layoff. She posts on digital media and informs her network about this unfortunate situation. In module 1, we also discuss the idea of putting on a costume and displaying our best moments on digital media. We discuss a book, The Presentation of Self in Everyday Life (1959) by Erving Goffman which correlates to the current representation of social media. Negar breaks this ideology by providing her peers and network with one of the most vulnerable and authentic moments. This breaks the idea that life is always perfect, which is enormously conveyed through digital media. This is an ideal representation of breaking the idea of marketable self-presentation.
These social media communications provide us with a deeper meaning of self-branding and being our authentic selves in self-presentation. Be yourself but always be your exceptional self.
1 note
·
View note
