Don't wanna be here? Send us removal request.
Text
Interactive Malware Analysis

The interactive analysis is becoming more popular every day. It can be used both for the analysis of regular samples and is also not replaceable if you come across unique malware samples. Let’s explore what interactive analysis is, and what are the main benefits.
But before we dive into the nuances of interactive analysis we need to understand what malware analysis is in general.
What is malware analysis?
Malware analysis is quite simply a process of studying a potential malware sample. During the study, a researcher’s goal is to understand the type, functions, code, and potential dangers of a malicious program.
Analysis can be performed for various reasons such as education or even as a hobby, but the most common goal is to study a malware sample to gain an understanding of how it works and to use this knowledge in developing countermeasures.
Why do we need malware analysis?
Imagine that a corporate computer gets infected by a new type of malware. For example, new ransomware. If the infection spreads to other PCs the attack may cost tremendous money or result in the loss of important information.
The goal of security researchers is to study the infiltrating malware and figure out what kind of mayhem it may cause. Which destructive functions the malware has. And how to prevent damage or repel subsequent attacks from the same malware family, should any occur in the future.
The main things to figure out during the analysis are:
What the malware can do.
How to detect it in the network.
How to carry out damage control and minimize the attack consequences.
Malware research also helps security professionals develop local and network signatures. Local signatures are like signs that point to files created or changed by a malicious program. They help find and identify malware on infected machines.
Network signatures on the other hand focus on identifying incoming and outgoing network requests, generated by the malware. For example, malware will often establish a connection with a control server to send over stolen data. These transmissions can give malicious programs away.
Types of malware analysis
Malware analysis is generally divided into two stages — static and dynamic. Static analysis is the first thing researchers will do to determine if a program is malicious and to learn about its functions. In some cases, static analysis is all you need.
However, if observing the code, strings, and headers in static form is not enough, researchers will start dynamic analysis to gain more insights about the behavior and capability of a malicious program. Dynamic analysis is more complicated and traditionally requires a lot more time to complete.
Static analysis
Static analysis is essentially just looking at the malware code with your bare eyes. It can tell important information and help create static signatures. For example, one technique that researchers use during static analysis is looking at strings. Strings often contain IPs and URLs and can point at the location of a control server for a particular malware sample.
However, while static analysis is very useful, it has limitations. Malware authors are developing more and more sophisticated programs and often create code that is designed to mislead researchers or conceal functions. This type of coding is called obfuscation and you will often see it in more advanced malware types.
Dynamic analysis
For dynamic malware analysis, researchers launch malware samples in control environments and study the processes that they create. Process Monitor and Process Explorer are two applications very often used to observe malware behavior during dynamic analysis.
If you are going to perform dynamic analysis, it is crucial to establish a secure environment where the virus can’t cause any damage to the machine. Usually, this means deploying a virtual machine and using some sort of VM software.
Or, an even better idea is to use ANY.RUN. Our service is designed specifically for dynamic malware analysis but also supports static analysis.
Actually, ANY.RUN takes it one step further by allowing for interactive dynamic malware analysis.
What is interactive malware analysis?

Benefits of interactive malware analysis
Interactive analysis has several other advantages:
It allows interacting with a malware sample directly.
It allows running several interdependent parts of the malware in one task to increase analysis quality.
It allows for acquiring data faster.
It reduces the required specification of the researcher.
It enables researchers to change operating system configuration based on malware behavior and re-run tasks much faster.
Furthermore, there are situations where other analysis types just aren’t sufficient. At least, unless the researcher is extremely experienced, and even then other analysis types would take way too long in comparison.
For instance, some malware samples will only execute if certain conditions are met.
One example is banking Trojans that may activate if a user visits a particular online banking website. Only then will the trojan try to steal and send information to the Command & Control server. Therefore, thanks to interactivity, analysts can collect more IOCs.
Additionally, some malware has kill switches in a form of files with specific names or registry keys. Analysts can try to include them in a virtual machine during analysis or check the language of the malicious document during analysis, change the system locale, and re-run tasks. This will allow the malware to work in full and give more IOCs.
Fully automated analysis programs may not know all execution scenarios. So they miss important steps and don’t paint the whole picture. Additionally, some samples within a malware family may have a unique execution process. Launching a separate automated analysis because of a single unique sample may not be viable. It’s just too much work, time, and money.

About ANY.RUN
ANY.RUN at the moment is the only service that provides interactive malware analysis. We would like to tell you how we came to this.
Being engaged in cybersecurity ourselves, we know that most existing analysis tools on the market are, frankly, not that user friendly. Not only do they require lots of knowledge, but they also lack the ability to present data in an easily readable form.
There are automated analysis tools, of course. But those can already be fooled by some malware samples and threat actors will implement new ways to throw off automated solutions.
We wanted to create a service that would simplify the analysis process through the use of a custom UI and take the best from automated sandboxes while allowing to retain an element of human supervision and interactivity.
And that is exactly what we did.
As a result, ANY.RUN effectively replaces and extends traditional analysis tools and builds a process that is centered around convenient process observation. As an online tool, it reduces equipment costs, while a graphical user interface makes malware analysis more accessible.
We are proud to say that today our service is used by over 300,000 researchers and trusted by industry giants such as Toyota, Canon, and many others.
Conclusion
Malware is becoming more and more sophisticated and, unfortunately, brand new samples are regularly introduced into the wild. Online security and solid defense against cyber threats are more important today than it ever was.
ANY.RUN is a unique service that makes malware analysis more accessible, fast, and safe. And on top of that, all our tools are available for free, so give ANY.RUN a try!
1 note
·
View note
Text
How to Get Free Malware Samples and Reports?

Malware hunters often look for malicious objects to investigate threat features and build protection strategies. The hindrance for striving cybersecurity specialists is to access new malicious code samples to practice on. ANY.RUN is an excellent resource for obtaining malware for free. In this post, we will tell you how to do it.
Where can you get malware samples?
ANY.RUN is an online interactive sandbox with a vast malware sample database of 3,780,111 public submissions. Each registered user can make use of these tasks to rerun and analyze a sample, get reports and IOCs, and other options. Fresh samples are delivered constantly. Researchers worldwide comprise this collection and run more than 9000 tasks every day.
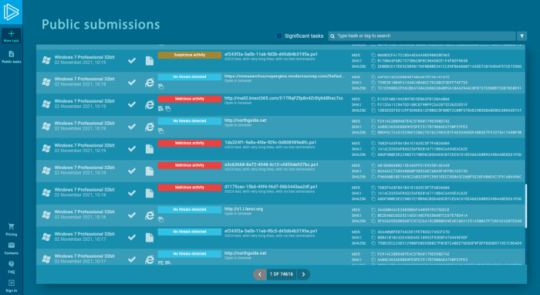
The “Public submissions” window is where you can dive into fresh malware samples and explore malware techniques. Here you can go through all the tasks that service users upload publicly. Users of premium subscriptions have an opportunity to analyze their tasks privately. So the window above includes only public submissions that a user chose to share with the community.
How to find a specific malware sample?
During the research, you may need an exact malicious program. To save your time in the search, ANY.RUN service has a helpful filter system. You can navigate through numerous samples using the following parameters:
Object
Hash
Run type of analyzed object (URL or file)
Extensions
Country
Verdict
You can also filter submissions using the sample’s threat level status and the verdict. There are three types of verdicts:
Malicious. Malicious activity is detected.
Suspicious. Suspicious activity was detected, and there is a possibility of the file being malicious, but it isn’t proven.
No threats detected. ANY.RUN has detected no malicious or suspicious activity.
Specified tag
You can find a sample by a malware name, family, technique, and vulnerabilities that the malicious program exploits. Read our blog post to check the list of tags and get more details about them. All the trending tags are displayed on the dashboard.
Context
You can type the sample’s unique data like a file hash, domain, IP address, MITRE ATT&CK, and Suricata SID in the context part.
Apply one or several parameters to find a specific malicious example. Try it yourself with a possibly infected IOC — use the filter, and similar cases will be displayed.

Once you find the sample you need, you see the analysis results immediately. They are shown in the visual form of a video or a screenshot slideshow.

What reports can you get?
Different reports on our malware samples site can help you examine the malicious object.

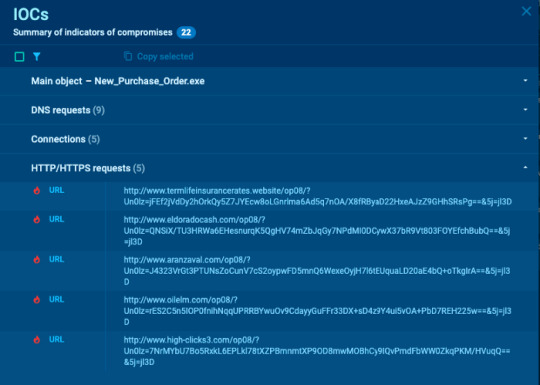
IOCs
Summary of indicators of compromise. Check out the object’s hash sums, DNS requests, connections, and HTTP/HTTPS requests. The window allows you to copy the necessary data and filter information. Icons and the number of IOCs let you run through the report and understand what you are dealing with at once.
Text report

The text reports are convenient. The most significant data is at the top, so you won’t miss anything. A detailed report contains general information about a sample, behavior activities, screenshots, data about the process, registry, files, network, debug output, etc.
You can also export or print this report in a preferable form — hide blocks by clicking on the “eye” icon.
The export in different formats is also available:
JSON Summary
JSON IOC
HTML Document
Export Process Graph (SVG)
JSON MISP format
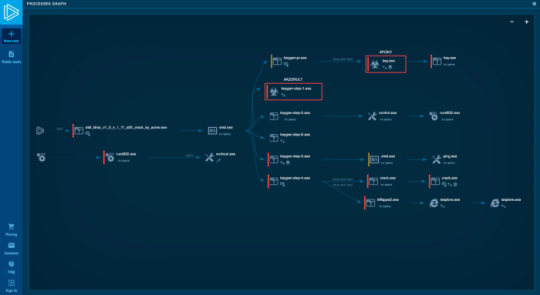
Process graph
The best overview of a sample is to examine its events in the process graph. A brief look, and you already know what is going on here.
MITRE ATT&CK matrix
The more information you have, the better analysis you perform. MITRE ATT&CK matrix gives a full view of the investigated malware’s tactics.

Of course, that is not all the details that you get. Each process has descriptive information about network stream, static discovering, and advanced information about events. You can find it out during the analysis or go through our guide on how to use ANY.RUN.
PCAP files
You can download PCAP files from the tasks to further analyze the network traffic in programs such as Wireshark. If the task was started with HTTPS MITM Proxy on, then the SSL Key Log file will also be available for download that allows you to decrypt HTTPS traffic.
Rerun a task that you have found in the public submissions and watch the process by yourself. With ANY.RUN’s premium subscriptions — Searcher and Hunter, you get extra features: customize configurations and see malware behavior on VM in a different environment. Check out a video to watch these plans in action:
Be attentive if you want to submit a malware sample and research files with sensitive information. A Community account’s investigation is available to the public by default.
ANY.RUN is an online sandbox. But it is also a service for education and research. If you are interested in malware trends, you can take a look at our Malware Trends Tracker to monitor malicious activity daily with its dynamic articles.
Check out the public submissions and start your analysis of malware samples with detailed reports now!
The malware samples used in the post: https://app.any.run/tasks/064e8183-009b-486c-9e5b-6d549a568612/ and https://app.any.run/tasks/a76e4684-0d7b-46de-af71-0538a5cde0f8/
0 notes
Text
Malware History: I LOVE YOU

On the 4th of May 2000, a new malicious program was released into the wild — ILOVEYOU, also known as Loveletter and Lovebug. We didn’t know it then, but this worm would forever change how we view malware, causing devastating damage.
Twenty years ago the internet was different. Then, people were not used to receiving tons of spam emails. It is not surprising then, that one of the first malware to use social engineering and massive email spam campaigns would cause nothing short of a malware pandemic.
In the end, the world has suffered billions of dollars in losses, up to 80% of computer networks in select countries become infected and the malware itself has acquired a Guinness book record for causing the most damage.
ILOVEYOU behavior
ILOVEYOU was a computer worm designed to spread through emails of Microsoft Outlook users. First victims of this malware received an email with a subject reading “ILOVEYOU”. An email like this was hard to miss in an uncluttered mailbox. Attached was a file, named LOVE-LETTER-FOR-YOU.TXT.vbs.
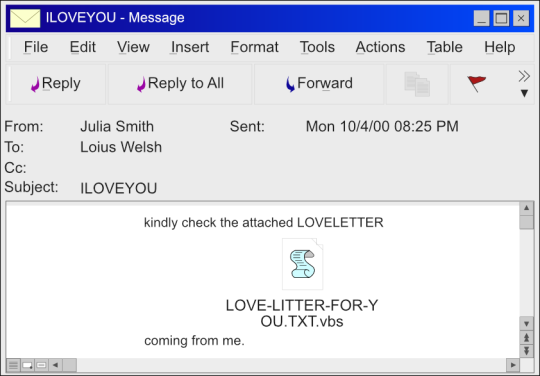
The malware would run after the unsuspecting victim downloaded the infected file. Once opened, ILOVEYOU would overwrite or hide a lot of the files on the infected machine. Usually JPGs MP2, MP3, and various document files. Replacing most of the files would render a machine unbootable. Then, having gained access to the Microsoft Outlook of the victim, the malware would send itself to all addresses found in the Outlook address book.
The worm usually makes its way into machines with an infected VBS file, that victims download from emails. When the ILOVEYOU execution begins, the malware first copies itself in the Windows directory. Then, the worm creates a registry key MSKernel32. Additionally, the worm generates a new Local Machine RunServices key Win32DLL, which causes it to launch at system boot before the user is even logged into the system. Then, ILOVEOYOU downloads a trojan and creates a registry key for it as well. Finally, the worm begins looking for files to modify, overwriting them, and copying itself. The malware keeps the original file names but adds a .VBS file extension to all compromised files.
ILOVEYOU Distribution
The damage from the Loveletter was first felt in South-East Asia. Then, it scaled over to Europe and the USA. Data varies on how many victims were infected but based on different evaluations ILOVEYOU compromised from 30 to 80 percent of computer networks in specific countries.
As the worm was spreading, security companies began making cures. Unfortunately, most were ineffective. Writing in VBScript gave the attackers a way to easily introduce changes to the malware code. Soon after launch, multiple versions of ILOVEYOU circulated in the wild. Each targeted different files and exhibited modified behavior, such as changed email subject lines.
Some of the subjects used included:
fwd: Joke;
Important! Read Carefully!!;
FRIEND MESSAGE.
Other subject matters were:
An airline ticket receipt from Arab Airlines;
A rage email, presumably from a friend;
An antivirus designed to protect from ILOVEYOU;
A present for Mother’s day, a holiday celebrated in the US.
When security professionals began creating cures for the malware, many targeted an older version, rendering their efforts near useless.
What resulted, was a cyberattack we simply weren’t prepared for. ILOVEYOU proceeded to infect millions of machines.
Not only could the malware spread further and further after each victim, but consequent emails were distributed from familiar addresses. People began receiving letters from their acquaintances. Most would presume them to be safe and open the love letter. At the time, an ingenious way to make users drop their guard.
According to data from the Trend Micro company, ILOVEYOU infected over 3.5 million devices around the world, including the network of the US Department of Defense. The malware caused about $15 million worth of damage.
ILOVEYOU Creator
Soon after launch, researchers learned that ILOVEYOU originated in the Philippines. Authorities began investigating two local programmers, Reonel Ramones and Onel de Guzman.
By tracing messages from European users to a Filipino internet provider, the investigation was found conclusive and Ramones was put into custody. De Guzman, however, at the time escaped the arrest.
The evidence was pointing at the programmers, but neither was charged. In 2000 there simply aren’t any laws related to hacking in the Philippines. First, authorities wanted to use credit card fraud as a substitute, then malicious mischief. But neither could apply completely.
In addition, de Guzman who just graduated from a programming class with a project extremely similar to ILOVEYOU claimed that he could have released the malware by accident. He never admitted to being responsible. When asked if he created ILOVEYOU, he would reply “maybe” and “I could have done it without realizing the consequences” through his lawyer.
Only 20 years after, when Geoff White of the BBC News tracked down de Guzman, the hacker admitted to being behind the ILOVEYOU attacks. Allegedly, all the students wanted to do was steal internet passwords, as he wasn’t able to afford his own connection. According to de Guzman’s words, he had no idea about the mayhem his creation could cause.
According to his words, after launching the worm de Guzman left to hang out with friends, soon forgetting about his actions. He only discovered the chaos he caused, by learning from his mother that the Police are looking for a dangerous hacker in Manila.
Conclusion
A lot has changed since the year 2000. At the time, creating malware was more of a hobby. A way to prove programming skills to co-workers and friends. But ILOVEYOU showed the world just how effective and devastating malicious programs can be. In doing so, it helped shape the cybercrime landscape into what it is today.
Twenty years later nobody takes malicious programs for granted. Today, they are highly specialized and sophisticated tools designed to cause damage. They target businesses and sometimes private users with one goal — stealing money or information that leads to money. Now, there are people who develop and operate these programs professionally.
In the last 20 years, the malware was evolving. Despite better modern cyber defenses and anti-viruses, some programs can spread even faster than ILOVEYOU, causing even greater damage.
We are likely to see a lot of attacks utilizing botnets. They will be more automated and more complex. Many are likely to resemble WannaCry, attacking in multiple stages.
Users can trigger a massive outburst of malware by simply opening a phishing email or following a phishing URL. In some instances, simply clicking on a malicious link can compromise the network router, opening even more backdoors, and enabling the attackers to redirect network traffic to malicious websites.
That’s why today more than ever we must be extremely cautious when working with emails. Especially when they contain links or attached files. Even if an email is from somebody you know — it is not a guarantee that it is safe. Vigorously checking all suspicious content is a vital step in building an effective security perimeter. Luckily, with ANY.RUN it is extremely easy.
Test everything; don’t risk infection of the entire network. Take care of yourself and your data!
10 notes
·
View notes