Don't wanna be here? Send us removal request.
Text
The GrackerAI Content Engine: Quality Standards & SEO Excellence
🚀 Content that ranks, converts & compounds—automatically
GrackerAI's 20-step AI engine solves the quality vs quantity problem:
✅ 50+ SEO checks per piece
✅ Answer engine ready (ChatGPT/Claude)
✅ Zero manual oversight
✅ Scales to 1000s of pages
While competitors struggle with thin content, smart companies build authority at scale.
Ready to 10x your content?
#AI #ContentMarketing #SEO
0 notes
Text

Author Pages aren’t just bios — they’re SEO powerhouses.
If you're a SaaS or B2B publisher, you need to start treating your author hubs as trust-building assets. With Google's focus on E-E-A-T (Experience, Expertise, Authoritativeness & Trust), your content creators should be instantly verifiable.
✅ Bio best practices ✅ Person schema markup ✅ Article archives ✅ Credentials + awards ✅ Internal linking for topical authority
We’ve broken it all down in a step-by-step guide — with code, copy, and design examples that boost credibility and visibility.
📘 Read the full playbook here: 👉 https://blog.gracker.ai/author-pages-e-e-a-t-the-complete-playbook-for-saas-b2b-publishers/
0 notes
Text

🚀 Digital Marketers & SEOs — Want Free Access to Google’s Raw Data? Stop relying only on tools like Ahrefs or SEMrush.
🎯 Discover 30+ powerful Google Search Operators that give you: ✅ Real-time SEO audits ✅ Competitive intel ✅ Link-building opportunities ✅ Keyword & content gap insights
💡 Learn how to fish with a spear—not a net.
🔍 Read the full 2025 guide now 👉 https://blog.gracker.ai/30-google-search-operators-every-digital-marketer-must-know-in-2025/
0 notes
Text
🔍 Want to rank higher on Google? Start with Seed Keywords!

Seed keywords are the foundation of every winning SEO strategy. They help shape your content, uncover long-tail keywords, and drive organic traffic.
🚀 Learn how to: ✅ Find the right seed keywords ✅ Expand into long-tail opportunities ✅ Structure your site with SEO in mind
📖 Read the full guide now: https://blog.gracker.ai/unveiling-the-power-of-seed-keywords-the-foundation-of-successful-seo/
0 notes
Text

🔗 Thinking of a career in SEO? Start with Link Building! Link building is one of the most in-demand skills in digital marketing today—and businesses are actively hiring specialists who can drive organic growth with quality backlinks.
In our Ultimate Guide to Becoming a Link Building Specialist, you’ll discover: ✅ What the role involves 💼 Salary ranges (entry-level to senior) 📈 Career paths & freelance opportunities 🧠 Key skills, tools & certifications 🌍 Industry trends & future growth potential
Whether you're just starting out or leveling up your SEO game, this guide has everything you need.
📖 Read the full guide now and start building your future, one link at a time!
0 notes
Text

📍 Track Your Local Rankings Like a Pro!
Discover the 10 Best Local Rank Tracker Tools with our in-depth comparison guide. 🛠️ Compare features, pricing, and benefits to find the perfect tool for your business.
📖 Read the blog:
0 notes
Text

🚨 Stay Updated on Cybersecurity News 🚨 The FBI recently took a major step by removing PlugX malware from thousands of systems, showcasing the fight against cyber threats. 🛡️ Want such updates directly in your inbox? 📧 Subscribe to the Gracker Cybersecurity Newsletter and get fresh news every 2 days!
🔗 Subscribe: https://gracker.ai/cybersecurity-news-roundup-subscription/
#Cybersecurity #GrackerAI #CyberNews #StaySecure
2 notes
·
View notes
Text

🎯 Simplifying Cybersecurity Marketing
Created this pyramid to show how we're transforming complex security content into clear, engaging stories with GrackerAI.
The result?
👉 15+ hours saved weekly
👉40% higher engagement
👉Better lead quality
👉Instant SEO-optimized blogs
Try it free: https://gracker.ai/
#CybersecurityMarketing #AI #ContentCreation
0 notes
Text
AI Tools for Cybersecurity Marketers

Cybersecurity marketing has its own challenges, particularly when working with limited budgets and the need to show results. To make the most of your resources, it’s essential to choose the right AI tools that offer measurable benefits and are worth the investment. This guide provides a detailed look at AI tools which are useful for cybersecurity marketers, including their pricing and key features, to help you find the right fit for your marketing needs.
Introduction: The Business Case for AI in Cybersecurity Marketing
The cybersecurity industry is projected to reach $345.4 billion by 2026, making it one of the fastest-growing sectors in technology. Marketing teams need powerful tools to produce more content with limited resources, demonstrate clear ROI on marketing investments, maintain technical accuracy while scaling operations, and compete effectively in a crowded marketplace.
1. Content Creation
GrackerAI: Specialized Cybersecurity Content Partner
Value Proposition: GrackerAI tackles a major headache for cybersecurity marketing teams - keeping up with the constant flood of industry news and creating content that matters. It's like having a smart radar that never sleeps, scanning for vulnerabilities, data breaches, and trending cyber topics.
Pricing:
Starter: $49/month (20,000 words)
Professional: $99/month (50,000 words)
Enterprise: Custom pricing for unlimited words
ROI
A cybersecurity marketing team producing 10 technical articles monthly traditionally spends $5,000 ($500 per article) on content creation. Using Gracker.ai reduces this to $1,500 ($150 per article) through faster research and writing, delivering a monthly saving of $3,500. With the Professional plan at $99/month, the ROI is approximately 3,400% monthly.
Copy.ai
Value Proposition: Copy.ai revolutionizes content creation by dramatically reducing social media content creation time, generating multiple copy variations instantly, and improving email campaign engagement. The platform's ability to understand context and maintain brand voice makes it invaluable for consistent content creation across channels.
Pricing:
Free Plan: 2,000 words/month
Pro: $49/month (unlimited words)
Team: $299/month (5 seats)
ROI
A typical social media manager spending 20 hours per week on content creation at $35/hour ($2,800 monthly) can reduce time spent to 5 hours weekly using Copy.ai, cutting costs to $700 monthly. With the Pro plan at $49/month, this represents a monthly saving of $2,051, delivering an ROI of 4,085%.
Jasper AI
Value Proposition: Jasper AI excels in producing long-form content with exceptional speed while reducing research time and improving SEO ranking through optimized content. The platform's deep understanding of technical subjects makes it particularly valuable for cybersecurity content creation.
Pricing:
Creator: $49/month (50,000 words)
Teams: $99/month (100,000 words)
Business: Custom pricing
ROI
A marketing team producing 4 weekly blog posts traditionally spending $2,000 weekly ($8,000 monthly) on content creation can reduce costs to $2,400 monthly using Jasper AI. With the Teams plan at $99/month, this represents a monthly saving of $5,501, resulting in a 5,456% ROI.
2. Visual Content Creation
DALL·E 2
Value Proposition: DALL·E 2 transforms visual content creation by eliminating stock photo costs and reducing design time while creating unique, branded visuals. The platform's ability to understand technical concepts enables the creation of accurate cybersecurity-related imagery.
Pricing:
Pay-per-use: Starting at $0.016 per image
Volume pricing available for enterprise users
ROI
Creating 50 custom technical illustrations monthly typically costs $2,500 ($50 per image). Using DALL·E 2 at approximately $1 per image reduces this to $50, saving $2,450 monthly, representing a 4,900% ROI.
Canva: Comprehensive Design Solution
Value Proposition: Canva revolutionizes design processes by reducing creation time, maintaining brand consistency across all materials, and enabling rapid content iteration. The platform's extensive template library and AI-powered features make professional design accessible to all team members.
Pricing:
Free: Basic features
Pro: $12.99/month per user
Enterprise: $30/month per user
ROI
A marketing team spending $3,000 monthly on graphic design can reduce costs to $500 using Canva. With the Pro plan at $12.99/month, this represents a monthly saving of $2,487, delivering an ROI of 19,045%.
3. Voice Content
Descript
Value Proposition: Descript transforms audio production by reducing editing time substantially, improving content accessibility, and enabling quick content repurposing. The platform's advanced editing features make technical content more engaging and accessible.
Pricing:
Creator: $15/month
Pro: $30/month
Enterprise: Custom pricing
ROI
Producing 4 technical podcasts monthly traditionally costs $2,000 ($500 per episode) in editing time. Using Descript reduces this to $400 ($100 per episode). With the Pro plan at $30/month, this represents a monthly saving of $1,570, delivering an ROI of 5,133%.
Lovo.ai
Value Proposition: Lovo.ai revolutionizes voice content by eliminating voice actor costs, enabling rapid localization, and maintaining consistent brand voice across markets. The platform's ability to handle technical terminology makes it particularly valuable for cybersecurity content.
Pricing:
Free: Limited credits
Professional: $49/month
Business: $129/month
ROI
Creating voiceovers for 10 training videos in 3 languages traditionally costs $9,000 ($300 per video per language). Using Lovo.ai reduces this to $900. With the Professional plan at $49/month, this represents a monthly saving of $8,051, delivering an ROI of 16,331%.
4. Audio Processing
Sonix.ai
Value Proposition: Sonix.ai delivers exceptional transcription accuracy for technical content, comprehensive multilingual support, and creates a searchable content archive. The platform's understanding of technical terminology ensures accurate transcription of cybersecurity content.
Pricing:
Standard: $10/hour
Premium: $5/hour (bulk pricing)
Enterprise: Custom pricing
ROI
Transcribing 20 hours of technical content monthly traditionally costs $2,400 ($2 per minute). Using Sonix.ai reduces this to $400 ($10/hour). This represents a monthly saving of $2,000, delivering an ROI of 500%.
Otter.ai
Value Proposition: Otter.ai transforms meeting documentation with instant notes creation, searchable conversation archives, and powerful team collaboration features. The platform's ability to handle technical discussions makes it invaluable for cybersecurity teams.
Pricing:
Basic: Free (300 minutes/month)
Pro: $16.99/month (6,000 minutes)
Business: $30/user/month
ROI
A team spending 40 hours monthly on meeting documentation at $35/hour ($1,400) can reduce this to 4 hours ($140) using Otter.ai. With the Pro plan at $16.99/month, this represents a monthly saving of $1,243, delivering an ROI of 7,216%.
5. Video Content
Synthesia
Value Proposition: Synthesia transforms video production by reducing production costs significantly, enabling rapid content updates, and providing multilingual capabilities. The platform's professional presenters and customization options ensure high-quality cybersecurity content.
Pricing:
Personal: $30/month
Corporate: $300/month
Enterprise: Custom pricing
ROI
Creating 5 professional training videos monthly traditionally costs $10,000 ($2,000 per video). Using Synthesia reduces this to $1,500 ($300 per video). With the Corporate plan at $300/month, this represents a monthly saving of $8,200, delivering an ROI of 2,633%.
Pictory.ai
Value Proposition: Pictory.ai revolutionizes content repurposing by automating video creation, transforming existing content efficiently, and increasing content reach across platforms. The platform's understanding of content structure ensures effective video creation from technical articles.
Pricing:
Creator: $23/month
Professional: $47/month
Enterprise: Custom pricing
ROI
Converting 20 blog posts to video content monthly traditionally costs $4,000 ($200 per video). Using Pictory.ai reduces this to $800 ($40 per video). With the Professional plan at $47/month, this represents a monthly saving of $3,153, delivering an ROI of 6,609%.
6. SEO and Content Optimization
Grammarly
Value Proposition: Grammarly enhances content quality by reducing editing time, improving overall content quality, and maintaining a consistent brand voice. The platform’s technical writing capabilities make it especially valuable for cybersecurity content. It ensures that your content is clear, concise, and free from errors, which is crucial in the technical and often complex world of cybersecurity. By offering suggestions for grammar, tone, and readability, Grammarly helps cybersecurity marketers produce professional, easily understandable content, making it an essential tool for effective communication in this industry.
Pricing:
Free: Basic features
Premium: $12/month
Business: $15/user/month
ROI
A content team spending 30 hours monthly on editing at $35/hour ($1,050) can reduce this to 10 hours ($350) using Grammarly. With the Premium plan at $12/month, this represents a monthly saving of $688, delivering an ROI of 5,633%.
Surfer SEO
Value Proposition: Surfer SEO transforms content optimization by improving SERP rankings, reducing optimization time, and increasing organic traffic. The platform's understanding of technical content ensures effective optimization for cybersecurity topics.
Pricing:
Basic: $59/month
Pro: $119/month
Business: $239/month
ROI
Monthly SEO consultant costs of $2,000 can be reduced to $500 using Surfer SEO. With the Pro plan at $119/month, this represents a monthly saving of $1,381, delivering an ROI of 1,060%.
7. Social Media Management
Buffer
Value Proposition: Buffer transforms social media management by saving significant posting time, improving post engagement, and providing comprehensive analytics for optimization. The platform's scheduling and analytics features ensure consistent social media presence.
Pricing:
Free: 3 social channels
Essentials: $5/channel/month
Team: $10/channel/month
ROI
A social media manager spending 60 hours monthly on posting and scheduling at $35/hour ($2,100) can reduce this to 15 hours ($525) using Buffer. With the Team plan at $100/month (10 channels), this represents a monthly saving of $1,475, delivering an ROI of 1,375%.
Hootsuite
Value Proposition: Hootsuite revolutionizes social media operations by centralizing management, improving team collaboration, and providing advanced analytics. The platform's robust features enable effective management of cybersecurity content across channels.
Pricing:
Professional: $49/month
Team: $129/month
Business: $739/month
ROI
A social media team spending 100 hours monthly on management at $35/hour ($3,500) can reduce this to 40 hours ($1,400) using Hootsuite. With the Team plan at $129/month, this represents a monthly saving of $1,971, delivering an ROI of 1,428%.
Conclusion
When implementing these AI tools, consider starting with high-impact, low-cost tools and measuring baseline metrics before implementation. A recommended starter stack might include:
Content Generation: Gracker.ai ($49/month) Design: Canva ($12.99/month) Content Optimization: Grammarly ($12/month) Social Media: Buffer ($49/month)
Remember that while these tools require initial investment, they become increasingly valuable through reduced production time, increased content output, improved content quality, and better audience engagement. Start small, measure results, and scale what works for your specific needs. The key to success is finding the right balance between automation and human expertise while maintaining focus on content quality and effectiveness.
Originally published at: https://blog.gracker.ai/ai-tools-for-cybersecurity-marketers/
0 notes
Text

📰 Stay ahead of evolving cyber threats with our Cybersecurity News Roundup!
Get expert insights, latest updates, and essential tips delivered straight to your inbox.
Don’t miss out—subscribe now! 🔐
👉 https://gracker.ai/cybersecurity-news-roundup-subscription/
#Cybersecurity #TechNews #StaySecure #GrackerAI #CyberUpdates
1 note
·
View note
Text

🚀 Unlock Your Competitive Edge with Keyword Gap Analysis! 🕵️♂️
Struggling to outpace your competition in search rankings? 🔍 Our latest blog, “Keyword Gap Analysis: The Ultimate Guide”, reveals how to:
✔️ Identify untapped keyword opportunities
✔️ Boost your SEO strategy
✔️ Drive targeted traffic to your website
Whether you're a marketer, content strategist, or SEO enthusiast, this guide will empower you to outperform your competitors. 💼
👉 Dive into the full guide here: https://blog.gracker.ai/keyword-gap-analysis-the-ultimate-guide/
Join the conversation and share your thoughts or strategies!
💬 Let’s grow together. 🌟
#SEO #KeywordGapAnalysis #GrackerAI #DigitalMarketing #ContentStrategy
0 notes
Text

🚀 Ready to skyrocket your SEO game?
🌟 Unleash your potential as a Technical SEO Specialist:
📊 Optimize website performance for better rankings.
💼 Unlock exciting career opportunities with competitive salaries.
🔧 Master tools and techniques to fix crawlability, speed, and more.
🔍 Become the go-to expert in the field.
👉 Dive into the full blog: https://blog.gracker.ai/the-complete-guide-to-becoming-a-technical-seo-specialist
💬 Share your insights or favorite SEO tips below!
🔗 Tag someone aiming to dominate search rankings!
#SEO #TechnicalSEO #DigitalMarketing #CareerGrowth #GrackerAI
0 notes
Text

🚨 Facing challenges in building backlinks and improving SEO?
🌟 Discover your career potential as a Link-Building Specialist:
📈 Learn high-demand skills to boost your website’s visibility.
💼 Explore lucrative career paths and salary opportunities.
🔑 Master proven strategies for effective link-building.
🛠 Get insights into tools and techniques for success.
👉 Read the full blog: https://blog.gracker.ai/the-complete-guide-to-becoming-a-link-building-specialist-career-path-salary-and-opportunities/
💬 Let me know your thoughts or share your link-building tips below!
🔗 Tag someone who’s ready to elevate their SEO game!#SEO
#LinkBuilding #DigitalMarketing #CareerDevelopment #GrackerAI
0 notes
Text

🌟 Seeking Feedback on My Blog: Majestic SEO Guide 🌟
I recently published a blog titled "Majestic SEO: The Ultimate Guide to Backlink Analysis and SEO Metrics"
👉 Read Here: https://blog.gracker.ai/majestic-seo-the-ultimate-guide-to-backlink-analysis-and-seo-metrics/
This blog covers everything from understanding Majestic SEO’s metrics like Trust Flow and Citation Flow to how it helps with backlink analysis for a solid SEO strategy.
💡 I would love your insights on:
The content's depth and clarity: Does it provide enough actionable takeaways?
Visual elements: Are the images, charts, or data presentations engaging?
SEO-focused tips: Did I miss any key points about Majestic SEO?
🔍 For future blogs, I’m aiming to:
Make complex concepts even simpler and beginner-friendly.
Add more real-life case studies or examples.
Expand content into video or infographic formats for a better experience.
Your feedback is invaluable in helping me improve and create better content. Please drop your thoughts or suggestions below.
#SEO #MajesticSEO #BacklinkAnalysis #ContentFeedback #Blogging
#ai generated#seo marketing#magesticSEO#seo strategy#content creation#content strategy#blog strategy#search engine optimisation
1 note
·
View note
Text
10 Proven SEO Strategies for Cybersecurity Companies
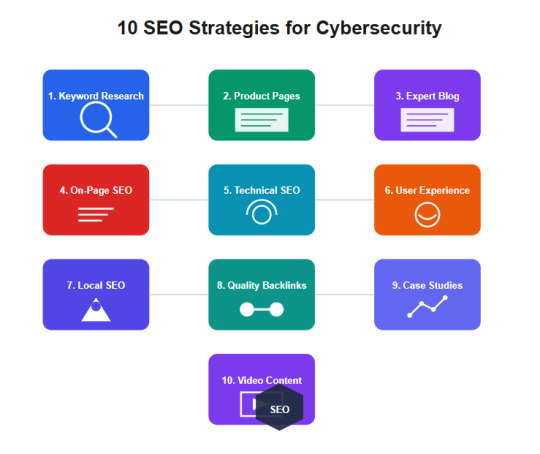
Introduction
The cybersecurity industry is experiencing an unprecedented rise in demand, driven by a notable increase in cyber threats. In Q3 2024, an average of 1,876 cyber attacks per organization was recorded, marking a 75% increase compared to the same period in 2023 and a 15% rise from the previous quarter.
In the third quarter of 2024, there was a dramatic increase in cyber attacks around the world. During this time, both the number and severity of these threats grew significantly, highlighting how cybercriminals are changing their tactics and the urgent need for stronger cyber defenses.
All these factors make cybersecurity firms a lot more important now than they have ever been. The fast increase in the number of cybersecurity firms also increases competition, and some firms are compelled to fight for visibility. For cybersecurity companies, SEO is now a vital means of standing out, driving organic traffic, and reaching prospective clients. That is where cybersecurity SEO comes in.
In this blog, we discuss 10 actionable SEO strategies for cybersecurity companies. These strategies panoramic a balanced approach in both technical and content-oriented search engine optimizations. Whether a cybersecurity startup or an established firm, the following tactics will definitely help you improve visibility for your company and drive high-quality leads.
How Crucial is SEO for Cybersecurity Businesses
SEO for cybersecurity websites is an important way to reach people who are already searching for your products or services. While strategies like pay-per-click (PPC) ads and social media marketing (SMM) can give you quick visibility, SEO takes more time and effort. The advantages are significant, as they result in enduring outcomes and organic traffic in the long term.
Boost Visibility: Achieving high rankings on search engines boosts visibility among potential clients looking for cybersecurity services.
Build Trust and Authority: Appearing on the first page of search results enhances credibility, particularly for businesses in critical sectors like cybersecurity.
Drive Targeted Traffic:Effective SEO ensures that individuals searching for specific cybersecurity services can easily find your company.
Increase Conversions:SEO attracts users who are actively seeking solutions, resulting in higher conversion rates and a more effective return on investment.
Proven SEO Strategies for Cybersecurity Companies
SEO for cybersecurity companies is a powerful tool that can greatly enhance your website traffic, draw in high-quality leads, broaden your customer base, and boost your profits when implemented with the right strategy. As with any marketing technique, it's crucial to apply proven methods that are customized to your unique business needs to ensure you're maximizing your resources.
Here are some effective strategies that cybersecurity firms should think about:
1. Comprehensive Keyword Research
To effectively attract your target audience, start with thorough keyword research. For cybersecurity, your keywords should address specific threats, services, and solutions. Here are key points to consider while researching keywords for cybersecurity SEO:

Example Table: High-Impact Cybersecurity Keywords

Assess Competition and Keyword Potential
Examine the rankings of your competitors for your target keywords. This will help you uncover content gaps and opportunities. Here’s how to do it:
Review Competitor Pages: Analyze the types of content, keyword usage, and formats that are achieving good results.
Investigate Backlinks: Utilize tools like Moz or Ahrefs to discover which backlinks your competitors are securing. This information is valuable for shaping your link-building strategy.
Assess Content Quality: Look into the depth of content on high-ranking competitor pages and strive to surpass it by incorporating unique insights, visuals, or the latest data.
2. Optimize Product Pages to Improve Ranking
Optimizing your product pages is essential for targeting commercial and transactional keywords because these types of searches usually lead to higher conversion rates.
Unlike informational keywords that attract users looking for general information, transactional and commercial keywords (like “buy endpoint protection software” or “cybersecurity solutions for businesses”) are used by people who are ready to make a purchase. This is why product pages are crucial for turning visitors into customers.
To improve your rankings and conversions, you should:
Write clear and engaging product descriptions that emphasize the advantages and features of your cybersecurity services. Steer clear of generic phrases and concentrate on the specific challenges your target audience encounters. For creating engaging and distinctive product descriptions, consider using the LogicBalls AI Product Description Generator Tool.
Seamlessly incorporate relevant keywords throughout the product page, particularly in headings, subheadings, and the product description. This strategy will enhance your page's visibility to potential customers. However, be cautious not to overstuff keywords, as this can compromise readability and negatively impact your search rankings.
Use relevant keywords in your title tags and meta descriptions, and make sure they are catchy enough to encourage clicks.
Include clear calls-to-action (CTAs), like “Get a free demo” or “Start your trial today.” These CTAs help guide users to the next step in their buying process.
3. Build and Optimize an Expert Blog for Top Keyword Performance
A blog not only drives traffic but also positions your brand as an industry authority. For cybersecurity, consider topics like data protection, cyber risk management, and the latest cyber threats.
Use Data and Trends: Cybersecurity audiences appreciate data-driven insights. Include statistics, case studies, and current threat information.
Update Content Regularly: Cybersecurity trends evolve quickly, so regular updates keep your blog relevant.
Create SEO-Driven Content: Write blog posts around keywords like “cybersecurity SEO” and “data breach protection” to increase targeted traffic.
4. Optimize for On-Page SEO
On-page SEO, often referred to as on-site SEO, is the practice of optimizing specific web pages to improve their rankings in search results and draw in more organic traffic. Here are the main elements to concentrate on:
A. Optimize Title Tags and Meta Descriptions for Keywords
Title tags and meta descriptions are the initial elements that users encounter when your pages show up in search results. These components are essential in determining whether users choose to click on your link.
Title Tags: Use the main keyword near the beginning of the title tag. Keep it under 60 characters and make sure it clearly describes what the page is about.
Meta Descriptions: Include the primary keyword and summarize what readers can expect from your page. Keep these under 160 characters.
B. Optimize H1-H6 Headings for Keywords
Using keywords in your headings helps structure your content for both readers and search engines.
H1: This is your main title and should include the focus keyword. It needs to be clear and relevant to the page's topic.
H2-H6: These are subheadings that help organize your content. Include secondary keywords where appropriate, as this improves readability and helps search engines understand your content better.
C. Optimize Your Content for Keywords
The body of your content is where you can provide value through keyword optimization.
Include primary keywords within the first 100 words and throughout longer content.
Use secondary keywords throughout the text to support the primary keywords.
D. Build a Strong Internal Linking Structure
Internal linking connects different pages of your website, which can improve SEO by making navigation easier for both users and search engines.
Understand your website’s layout and identify your most important pages.
Link important pages together so users can easily find valuable content.
Use clear and descriptive link text (anchor text) to let users know what to expect when they click a link.
Create a logical structure without overloading any single page with too many links; place them naturally.
E. Optimize Your Images
Image optimization improves loading speed and user experience, which is important for SEO.
Name your image files clearly, using descriptive names that include keywords. Instead of “image1.jpg,” use something like “ransomware-prevention-tool.jpg” so search engines understand what the image is about.
Add alt text that describes the image, including keywords if relevant. Alt text helps images rank better in search and assists visually impaired users.
Compress images and choose the right formats to ensure they load quickly. Use JPEG for photos and PNG for graphics.
F. Implement Structured Data
Structured data offers extra context to search engines, allowing them to grasp your page content more effectively. This can enhance the chances of your content being featured as a rich snippet at the top of search results, boosting visibility and traffic.
Typical types of structured data for cybersecurity companies include FAQs, product reviews, service listings, and how-to guides. Incorporating structured data aids search engines in categorizing and showcasing your content more efficiently in search results.
5. Optimize Your Technical SEO
Even if your content is well-optimized, technical errors can hinder Google's ability to crawl, index, and rank your pages properly. These issues can also lead to a frustrating experience for users, prompting them to leave your site quickly.
This is where technical SEO services play a crucial role—they address these problems to ensure seamless navigation on your site.
Here are some important areas to focus on:
A. Site Loading Speed
To ensure a loading speed of 1 to 2 seconds is crucial. If your site takes longer, visitors might get frustrated and leave, resulting in higher bounce rates. Search engines may interpret this as a sign that your site lacks a good user experience.To enhance speed, consider the following:
Optimize images to reduce their size.
Minimize the number of HTTP requests your site makes.
Use browser caching to speed things up.
B. JavaScript Rendering
If your website relies heavily on JavaScript, search engines may have difficulty rendering and indexing your pages completely. This could result in important content being absent from search results. Consider implementing server-side or dynamic rendering to ensure that your site is fully indexed.
C. Mobile Responsiveness
With Google prioritizing mobile-first indexing, it’s essential for your website to function well on mobile devices. If the mobile version of your site isn’t responsive or offers a poor user experience, it could negatively impact your rankings and deter user engagement.
D. Incorrect Server Response Codes
Server errors such as 404 (page not found) or 5xx (server errors) can damage your SEO efforts. If search engines are unable to access your pages or if users encounter broken links, they are likely to leave quickly. Utilize tools like Google Search Console to identify and resolve these issues. Additionally, remember to set up 301 redirects when relocating content to help users find what they’re looking for.
E. Core Web Vitals
Google’s Core Web Vitals are important performance metrics that reflect how users experience your website. Optimizing for these metrics is crucial for both SEO and user satisfaction.
The largest Contentful Paint (LCP) measures how fast your main content loads. Aim for a score of under 2.5 seconds to keep users engaged and improve your search rankings.
Cumulative Layout Shift (CLS) assesses the stability of your page layout. To provide a better user experience, aim for a CLS score of less than 0.1 to prevent unexpected content shifts that can frustrate users.
Interaction to Next Paint (INP), which has taken over from First Input Delay (FID), gauges how fast a page becomes interactive after user engagement. A desirable INP score is under 200 milliseconds, promoting a seamless and responsive experience for users.
6. Improve User Experience
A good user experience (UX) is important for SEO because it helps keep users engaged and influences factors like bounce rate, dwell time, and click-through rate (CTR), all of which affect your search rankings.
Bounce Rate
A high bounce rate often means that users aren’t finding what they expect or are having trouble navigating your site. By improving UX—through easy navigation, relevant content, and fast loading times—you can lower your bounce rate. This sends a clear message to search engines that your content is valuable and worth showing to others.
Dwell Time
Dwell time refers to how long users stay on your website after clicking a link from search results. The longer they stay, the better it looks to search engines. You can encourage users to linger longer by enhancing your site’s UX.
Click-Through Rate (CTR)
Your UX begins influencing users even before they visit your site. Well-optimized title tags, meta descriptions, and rich snippets can entice users to click on your link in the search results. Once they arrive on your page, a strong UX keeps them interested.
A well-designed user experience keeps visitors engaged, reduces bounce rates, and improves conversion rates. This means having easy-to-use navigation, fast loading times, and well-organized content. High bounce rates can signal to search engines that your site isn’t providing a good experience, which may hurt your rankings.
Importance for Cybersecurity Professionals
For those in cybersecurity, a good user experience (UX) not only enhances SEO but also plays a crucial role in boosting conversions. A well-structured website, straightforward navigation, and a design that works well on mobile devices can keep users engaged longer and lead them toward taking action.
Clear Navigation: Cybersecurity topics can be intricate, so a well-organized website allows users to quickly find what they need. By logically categorizing information and using concise content along with clear calls-to-action (CTAs), you enhance your chances of turning visitors into customers.
Mobile Optimization:With more than 92% of users accessing the internet via their phones, having a mobile-friendly design is essential. It not only improves your search rankings but also ensures that everyone can easily access information on any device.
Trust Signals: Trust is vital in the cybersecurity field. By incorporating key trust signals, such as security certifications, customer testimonials, and transparent privacy policies, you can reassure visitors and motivate them to choose your services.
In summary, focusing on a strong user experience not only supports your SEO initiatives but also fosters trust and boosts conversions for your cybersecurity business.
7. Local Search Engine Optimization
According to Google, local searches are on the rise:
“Near me” searches have increased by over 500% in the past two years.
Searches for “___ near me now” have grown by more than 150%.
Searches for “___ near me today/tonight” have skyrocketed by over 900%.
Searches for “open now near me” have risen by 200%.
For cybersecurity brands operating in various areas or cities, local SEO is crucial for engaging a nearby audience. By focusing on local search optimization, businesses can connect with individuals actively looking for cybersecurity solutions in their vicinity.
A robust local SEO strategy can attract more qualified leads, especially if your business provides in-person consultations or on-site services. This is particularly vital for sectors with specific regulations, such as healthcare or finance, which can differ by region.
When your cybersecurity company is optimized for local searches, potential customers in your area will easily discover you when they require services like penetration testing, vulnerability assessments, or network security audits.
Here’s how to optimize for local search:
Claim and Optimize Your Google Business Profile: This helps your business show up in Google’s Local 3-Pack, which features the top three local results in Google Maps and search results. Make sure to:
Keep your business name, address, and phone number (NAP) consistent and accurate.
Use relevant keywords in your business description, such as “cybersecurity solutions for small businesses in CityX.”
Add high-quality images, service categories, and customer reviews to your profile.
Regularly update your profile with new information like operating hours and available services.
Get Local Citations: Make sure your business name, address, and phone number are listed on various websites, including local directories, industry-specific sites, and your social media profiles. Don’t forget general directories like Yelp, Bing Places, and Apple Maps.
Use Location-Based Keywords: Target your local customers with keywords specific to your area. Instead of just “cybersecurity services,” use phrases like “cybersecurity services in Boston” or “IT security solutions in Arizona.”
Encourage Customer Reviews: Positive reviews on your Google Business Profile and sites like Yelp can increase your visibility and build trust with potential clients. Ask your customers for reviews and respond to them promptly to show that you value their feedback.
For businesses targeting global markets, it's essential to utilize international SEO services to make sure your cybersecurity solutions are easily discoverable across various languages and regions. By prioritizing local SEO, you can effectively cater to your community and expand your business!
8. Build High-Quality Backlinks
Building backlinks is a crucial element of off-page SEO on Google; it's also commonly referred to as external links. They are hyperlinks coming from another person's website, directing users to a web address on your site. Essentially, they signal to search engines that your content is trustworthy, authoritative, and valuable.
The more authoritative the linking website, the stronger the "link juice," boosting your search rankings and overall SEO performance.
Here’s how to get high-quality backlinks:
Guest Posts on Industry Blogs: Contribute guest posts to reputable blogs within your niche. This lets you showcase expertise while acquiring a backlink to your site. Aim for blogs with a similar audience and high domain authority.
Create Valuable and Unique Content: Produce insightful, relevant content. You can add a link to your website in your bio or within the content itself, as long as it makes sense in context.
Request Link Insertion: Ask website owners to insert your link into their already published, relevant content. This works especially well if your content adds value to their article or supports its main argument.
Distribute Newsworthy Press Releases: Press releases are a great way to gain backlinks. Announce significant business updates—such as new products, awards, or partnerships—with a press release. News agencies and industry blogs often pick these up, providing valuable links back to your site
Monitor Your Backlink Profile:Regularly review your backlinks to identify those that help or harm your SEO. There are several tools you can use for this:
Ahrefs: Offers deep insights into backlinks, including source and domain ratings, plus tracking for competitors' backlinks.
SEMrush: Provides an overview of total backlinks, referring domains, and potentially harmful links.
Moz Link Explorer: Gives a breakdown of your backlink profile, including link quality, domain authority, and trends over time.
If building a strong backlink profile seems daunting, consider an SEO outsourcing company. For example, cybersecurity firms targeting other businesses need content and backlinks that resonate with B2B audiences—especially those seeking corporate cybersecurity. If on a budget, seek affordable SEO services that can deliver results without compromising quality.
9. Develop Data-Driven Case Studies
Case studies provide evidence of your expertise and can be powerful for SEO.
Focus on Real-World Applications: Showcase how your services helped clients overcome cyber threats.
Optimize for SEO: Use keywords related to your service area and link back to relevant product pages.
Promote on Social Media and Email: Sharing case studies increases visibility and can attract quality backlinks.
10. Integrate Video Content for Engagement
More and more, video is the go-to medium when holding a prospect's attention—or even improving search engine ranking.
Create Educational Videos: Cover all aspects of cybersecurity, from data protection tips to emerging threats.
Use YouTube and Website Embedding: Let your videos hold a place on YouTube and implant them into your website for viewership extension.
Optimize Video Descriptions: Add your target keywords in the titles and descriptions of your videos to increase visibility.
Conclusion
For cybersecurity companies, this ongoing competition demands clarity in SEO strategy. With the use of the aforementioned approaches, the company will surely see its search ranking improved, qualified leads generated, and brand authority developed. An SEO comprehensive approach—from keyword research to high-quality backlinks and well-balanced content—can be the separating key between the visible and invisible cybersecurity companies.
#ai generated#content marketing#content creation#seo marketing#seo services#seo strategy#content strategy#search engine optimisation#blog strategy#cybersecurity
1 note
·
View note
Text
Best Tools to Extract Text from Photos in 2024

Undoubtedly, our lives have drastically evolved due to the significant influence of technology. From hiring remote workers from all around the globe to getting online education, the extreme impact of digitalization affects our every step.
Readdressing our subject, digital documents, are a critical aspect of this continuously changing digital industry. Consequently, the OCR technology is the result of the same advancements.
Whether you want to correct important data and information in your image or want an editable form of the texts of the images, the OCR technology is here to provide you with a helping hand and make the editing process smooth and trouble-free.
Therefore, in today’s discussion, we will highlight the basic concept of OCR technology and explore the best tools to extract text from photos in 2024. So, let’s dig in…
OCR Technology: A Quick Rundown
OCR allows its users to extract texts, in the form of alphabets, numbers, alphanumeric, symbols, and special characters, from scanned images as well as raw photos.
Whether you want to correct important data and information in your image or want an editable form of the texts of the images, the OCR technology is here to provide you with a helping hand and make the editing process smooth and trouble-free.
With every passing day, the idea of OCR is getting more advanced, making the text-extracting process from images more simple, quick, and effective.
Best Tools to Extract Text from Photos in 2024
1. Image To Text Converter
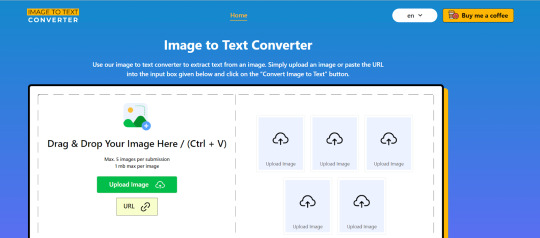
Image to Text Converter is an online OCR solution that not only provides a clear, undistracted but user-friendly interface. So the users can easily navigate and complete their text-extracting process. This tool also supports multiple input methods, including direct copy-paste, using URL, Dropbox, and uploading data, and allows processing 5 images per submission. So, whether you want to upload an image from your device’s gallery or want to extract text from online sources, this tool is going to save you time and effort and provide you with comprehensive and accurate text from the images.
Pros
Supports an extensive range of languages
Supports low-resolution images
Free unlimited access
Reliable and secure
Cons
Grammatical errors are expected
Might need multiple scanning for accurate results
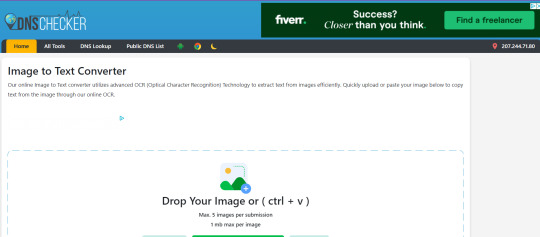
2. DNS Checker
Pros
Simple User Interface
Multiple image input methods
Supports multiple formats
Supports a wide range of languages
Cons
Text formatting might be compromised
Multiple uploads for accurate results
3. Adobe Acrobat
Pros
Provides cloud-based storage
Comprehensive features
Security guaranteed
Free trials
Cons
Quite expensive
Complex user interface
4. ABBYY FineReader

Pros
Excellent document comparison feature
Supports manual corrections
Multiple exporting format
Simple and effective user interface
Cons
Lacks full-text indexing
Tables might not be detected
5. MyQ X
Pros
Support an extensive range of languages
Multiple output formats including doc, PDF, RTF, and more
Cloud storage facility
Strong safety and privacy
Cons
Lengthy logging process
Prolonged scanning experience
6. Docsumo
Pros
Excellent data extraction feature
24/7 Customer Support
Convenient and quick
Support third-party integrations
Cons
Complex User Interface
No Import data option
Conclusion
The above-listed tools have no doubt made the lives of designers easy, all thanks to the developers of OCR technology. By using multiple features, these OCR tools can enhance the quality of raw and captured images, and help in customizing the texts without any troubles or delays.
0 notes
Text
5 Best AI Poem Generators to Boost Your Creativity
Unleash your poetic potential with AI-powered tools! Explore the 5 best AI poem generators to inspire creativity and craft beautiful verses effortlessly.

We all know that writing poems is a task that requires the highest level of creativity. However, this is not always possible for human writers. So, what should they do if they get stuck and can’t generate creative ideas? There is no need to worry… as the advancements in Artificial Intelligence have provided an excellent solution to this issue.
There are numerous AI-powered poem generators available online (most of them are free) that amateur and professional writers alike can use to expand their creative thinking for effective poem writing. However, the wide availability of generators may cause difficulties for you in picking the most dependable one.
So, to make things easier, we have personally researched and tested a number of AI poem generators and then selected the 5 best ones that will be discussed in this blog.
Top AI-Based Poem Generators That Can Be Useful for Enhancing Creativity
Below we have discussed some of the most reliable AI-powered poem generators that can be used to spark new ideas for poem writing.
1. Editpad
On top of the list, we have Editpad. It is basically a freemium (free & paid) toolkit offering a bunch of advanced writing tools including an AI poem generator. This free AI tool works on Natural Language Processing (NLP) and Generative AI technology.
The NLP effectively understands the meaning and context of human input, while GenAI contributes to generating a poem that you can carefully review to get new ideas for maximized creativity.
Moreover, the best thing is that Editpad will generate 3 poem versions for a single topic at once. This way, you will have the opportunity to interact with each version and collect different ideas for effective poem writing.
To demonstrate better, we provided the following prompt to the tool to see what response it would provide.
Input Prompt: “Explore the fleeting nature of beauty, whether it’s a flower, a moment in time, or a human connection.”

So, now there is no need to manually brainstorm ideas. Instead, make use of Editpad and give a boost to your creative thinking within seconds. When it comes to features, the Editpad generator supports poem generation of several types including Epic, Free Verse, Sestina, and many more. Besides this, it also provides you the option to select length; Short, Medium, or long.
Key Highlights:
Available for free
Useful for brainstorming ideas quickly
Supports different poem types
Offers different length options
Creates 3 poem versions for a single prompt
2. LogicBalls
Logicballs also offers a freemium (available in both free and paid plans) poem generator that can be used to enhance creativity skills for streamlined writing. It works on state-of-the-art Natural Language Processing and Machine Learning algorithms to effectively comprehend the given input and then generate a poem accordingly.
You just need to pay proper attention to the generated poem and get the ideas needed to start the writing process.

Talking about features, the tool has a lot to offer. For instance, the tool allows you to choose the poem length; Short, Medium, or Long.
Besides this, it also gives the authority to select the writing tone such as Casual, Dry, or Formal, etc., of the generated poem. However, it is important to note that not every tone is available in free mode, some require a paid subscription.
To cater to the needs of a worldwide audience, the tool supports poem generation in numerous languages including English, German, Italian, and many more. One unique feature that makes this tool stand out is that it allows you to either convert the generated poem into voice or download it as a PDF. The voice conversion is an excellent option for people who are not good at reading.
Key Highlights:
Offers both free and paid plans
Provides the option to generate poems of different tones
Multilingual support
Different length options
Download as a PDF or convert the generated poem into a voice
3. Remagine AI
This is yet another excellent AI-powered poem writer that can be used to boost creativity. It is available for free, which means you can make use of it unlimited times without paying a single penny.
It is trained on human writing patterns and utilizes a diverse set of intelligent AI algorithms to properly understand and then craft a unique poem accordingly. So, to effectively beat creative writing block, you can consider creating a poem with this AI tool first, then get useful ideas from the response, and start writing to your full potential.

Talking about features, this AI generator also provides users with the option to select how many versions (1, 5, 10, and 20) they want to generate for a single prompt. Apart from this, it can create poems in multiple languages including English, Chinese, Hindi, and French.
However, it is important to note that it does not offer the option to generate poems of different types. But still, it can come in handy for sparking new ideas for effective poem writing.
Key Highlights:
Completely free to use
Option to generate multiple poem versions against a single input
Supports multiple languages
Does not ask for signup/registration, instead just land & use
4. Rewordingtool.io
Rewording Tool is a toolkit providing numerous AI-powered tools including a poem generator to a worldwide audience. The generator is totally free which means you can create unlimited poems without spending a single penny.
When it comes to the working mechanism, it uses advanced Deep Learning and Large Language Model (LLM) algorithms to create interesting and fictional poems quickly and accurately according to the input prompt.
The AI-generated poem will help spark new ideas and boost overall creativity. However, we recommend you create poems on the same topic with this tool again and again. This way, you will gather multiple ideas and get a creativity boost.
Moreover, to serve the needs of a wide audience, the tool supports multiple poem types including Limerick, Haiku, Acrostic, and Villanelle.

Apart from multiple-type support, this generator also gives the option to adjust the length of a poem such as Short, Medium, and Long.
Key Highlights:
Works on Deep Learning & LLM algorithms
Completely free to use
Supports different poem types
Multiple length options
5. AIchatting
This is the final AI-powered poem generator that you can consider for boosting creativity. This tool is also available in free and paid plans. In free mode, it uses GPT-3.5 algorithms to quickly create an exquisite poem according to the given prompt, whereas in the premium mode, the tool uses GPT-4.0 technology for generation.
So, you can interact with the generated poem with the intention of getting unique and interesting ideas, which will ultimately boost your creativity. To generate fully personalized poems, the tool allows you to select the writing style (Haiku, Sonnet, etc.) and tone (Reflective, Nostalgic, etc.).
The unique feature is that the tool allows you to add any “Additional Instructions” about the poem.

Just like other poem generators listed above, this one is also capable of creating poems in different languages including English, Spanish, Portuguese, and many more.
However, it does not provide the option to choose the length of the poem. But still, we believe it can be used for enhancing creativity.
Key Highlights:
Allows selecting poem style & tone
Supports several international languages
Option to add specific details about the poem that the tool would generate
Available in both free & premium plans
Wrapping Up
Sometimes you may not be able to brainstorm good ideas needed for a poem. This is mainly due to a lack of creativity. Fortunately, there is an effective solution available to this issue – AI poem generators.
They quickly craft a unique and compelling poem, which you can consider as a sample to spark new ideas. In this blog post, we have discussed the five most reliable AI generators that you can consider using.
0 notes