#visitor management software
Explore tagged Tumblr posts
Text
5 Ways Visitor Management Systems Improve Business Security

In today’s fast-paced and interconnected world, ensuring the safety and security of any organization is a top priority. A visitor management system plays a vital role in achieving this goal by helping businesses streamline and enhance the way they handle visitors. Whether it’s a corporate office, educational institution, or healthcare facility, managing visitors effectively not only strengthens security but also boosts efficiency and improves the overall experience for everyone involved.
Visitor management systems have evolved significantly from the traditional sign-in sheets to advanced visitor management software, which allows organizations to track, monitor, and manage visitors in real-time. In this post, we’ll explore what a visitor management system is, its benefits, and how adopting a modern solution can help your organization stay secure while improving operations.
What is a Visitor Management System?
A visitor management system is a digital solution that automates the process of tracking and managing visitors in a workplace or facility. This system replaces outdated methods like paper sign-in sheets, providing an efficient, secure, and professional way to manage visitor information.
By using a visitor management system, businesses can pre-register guests, issue digital badges, track entry and exit times, and maintain a detailed log of all visitors. This data can be accessed in real-time, helping organizations maintain accurate visitor records and improve security protocols.
Why is a Visitor Management System Important?
The importance of having a visitor management system goes beyond just signing visitors in and out. Here are some key reasons why it is crucial for modern businesses:
Enhanced Security: A visitor management system ensures that only authorized individuals gain access to your facility. By pre-screening visitors and verifying their identities, you can prevent unauthorized entry and reduce security risks.
Streamlined Operations: A digital system automates the entire visitor process, allowing receptionists and security staff to focus on other tasks. This increases productivity and reduces the time spent managing visitors.
Compliance: Many industries require organizations to keep detailed records of visitor activity for safety and legal reasons. A visitor management system helps businesses stay compliant with data protection regulations by securely storing visitor information.
Improved Visitor Experience: Visitors appreciate a seamless and professional check-in process. With a visitor management system, they can pre-register online, receive QR codes, and bypass long queues at the front desk.
Real-Time Notifications: Notify staff members instantly when their visitor arrives, saving time and ensuring a smoother visitor experience.
Key Features of a Modern Visitor Management Software
A modern visitor management software goes beyond basic visitor tracking. It offers a range of advanced features designed to improve security, compliance, and the overall visitor experience. Here are some essential features to look for:
1. Pre-Registration and Self Check-In
With visitor management software, visitors can pre-register before their visit, making the check-in process faster and more efficient. Self-check-in kiosks also enable guests to sign in without assistance, saving time and reducing the workload for front desk staff.
2. Visitor Badges and QR Codes
Visitor badges and QR codes provide an easy way to identify visitors. Digital badges are sent to visitors' mobile devices, allowing them to check in using their phones. This reduces the need for physical badges and enhances security.
3. Integration with Security Systems
To further boost security, visitor management software can integrate with existing security systems such as surveillance cameras, access control, and alarm systems. This integration provides a complete overview of visitor activity in real-time.
4. Real-Time Visitor Tracking
Organizations can monitor visitors throughout their stay, ensuring they are only in authorized areas. Real-time tracking also provides insights into peak visitor times, helping improve staffing and facility management.
5. Customizable Workflows and Notifications
A customizable visitor management software allows organizations to tailor the check-in process based on their specific needs. Notifications can be sent to relevant staff members when a visitor checks in, improving communication and response time.
6. Data Storage and Analytics
The software stores visitor data securely and provides analytics that helps businesses identify patterns, such as frequent visitors or high-traffic times. This information is invaluable for making informed decisions about security and operations.
Benefits of Implementing a Visitor Management Software
By transitioning from traditional methods to a visitor management software, organizations stand to gain a multitude of benefits that can enhance security, efficiency, and compliance. Let’s take a closer look at the main advantages:
1. Increased Security
Automated visitor tracking ensures that only authorized individuals are allowed access to your facility. By pre-screening visitors and keeping accurate logs, businesses can mitigate risks and respond quickly in case of a security breach.
2. Operational Efficiency
By eliminating the need for manual sign-ins, visitor management software streamlines the check-in process, freeing up front desk staff to focus on more important tasks. The system also ensures that visitors do not experience unnecessary delays upon arrival.
3. Compliance with Regulations
Many industries, such as healthcare, education, and finance, require strict record-keeping for visitors. A visitor management system helps businesses stay compliant with regulations by securely storing data and providing audit-ready reports.
4. Enhanced Visitor Experience
An efficient and smooth check-in process leaves a positive impression on visitors. With features like pre-registration and self check-in, visitors spend less time waiting and more time engaging with their host.
5. Cost Savings
A digital visitor management software reduces the need for paper logs and physical badges, cutting down on administrative costs. Additionally, its automated features reduce the need for additional staff to manage visitor check-ins.
How to Choose the Right Visitor Management System
With many options available, selecting the right visitor management system can be overwhelming. To ensure that you make the right choice for your organization, consider the following factors:
1. Ease of Use
The system should be easy to use for both staff and visitors. An intuitive interface and user-friendly design will encourage adoption and minimize training requirements.
2. Scalability
Choose a system that can grow with your business. As your organization expands, your visitor management software should be able to handle increased visitor traffic and adapt to new security needs.
3. Integration Capabilities
Ensure that the software integrates seamlessly with your existing security systems, such as surveillance cameras, access control, and employee directories.
4. Customization Options
Every organization has unique security and operational needs. Look for a solution that allows you to customize workflows, notifications, and visitor badges to suit your requirements.
5. Compliance Features
If your industry requires detailed visitor logs or follows strict data protection regulations, choose a system that offers robust compliance features, such as secure data storage and detailed reporting.
Conclusion
Implementing a visitor management system is a critical step for organizations that prioritize security, efficiency, and compliance. By replacing outdated manual processes with modern visitor management software, businesses can enhance security, streamline operations, and create a better experience for visitors.
Whether you are a small office or a large facility, adopting a visitor management system will provide you with the tools needed to track visitors effectively and maintain a safe, secure environment for your staff and guests. Take the step towards better security and improved operations by exploring the right visitor management software for your organization today.
#Visitor Management#Visitor Management System#Visitor Tracking#Security Solutions#Digital Check-In#Visitor Experience#Compliance Management#Operational Efficiency#Access Control#Workplace Security#Business Solutions#Visitor Management Software#Pre-Registration#Real-Time Monitoring#Data Analytics#Safety Protocols#Automation#Facility Management#Guest Management#Healthcare Security
0 notes
Text
Top Visitor Management System Malaysia | Secure & Efficient Software WEBSITE
Revolutionize your facility's security and efficiency with our state-of-the-art visitor management system in Malaysia. Our visitor management software offers a comprehensive solution, combining flexible check-in options, advanced security features, and effortless appointment management. With virtual passes, biometric authentication, and real-time monitoring, our system ensures top-tier security while streamlining operations. The user-friendly interface makes managing visitor data, access lists, and reporting a breeze. Whether you're a small business or a large corporation in Malaysia, our visitor management system is designed to enhance guest experience, boost operational efficiency, and strengthen security measures. Upgrade your facility today with a visitor management software that's tailored to meet the unique demands of modern Malaysian businesses, making it an indispensable tool for safeguarding your premises and optimizing front desk operations.

#Visitor Management System#Malaysia Visitor Management System#Visitor Management Software#Malaysia Visitor Management Software
1 note
·
View note
Text
How Implementing a Visitor Management Application (VMS) Enhance Business Operations

An organization must prioritize employees' safety by adopting an ideal visitor management system to fend off unauthorized people. Remember that established places like commercial buildings receive thousands of visitors for interviews and formal meetings.
An organization must capture essential personal information, including the passports and phone numbers of all the guests who walk into their offices.
1 - Improves The Visitor’s Experience
Nowadays, companies have invested in self-help visitor management systems to enable visitors to access the premises or office easily. Usually, the system captures the individual's face and personal details to determine whether one deserves entry.
2 - Better Security
Secondly, visitor management helps employees to track all the outsiders who walk into their premises. Further, they ensure that strictly authorized people access guarded company sections like management's offices.
Therefore, employees can focus on their daily responsibilities as they feel safe while they work.
3 - Remote Visitor Management
Today, IT specialists integrate a visitor management system (VMS) with employees. Therefore, a company’s employee can get more information about the visitor and decide whether to let them from the comfort of their laptops.
4 - Minimizes Unnecessary Time Wastage by Employees
In the past, supervisors had to interrupt employees to handle guests to ensure only authorized people access specific office sections. Today, an organization only needs a security officer to welcome and direct them to the VMS machine.
5 - Enhances Organization and Order in Offices
Today, a visitor like an interviewee, must visit the organization's VMS to book beforehand. Therefore, the organization can schedule different days for each interviewee to prevent unnecessary congestion.
Therefore, employees can complete the interview on time and resume their other daily duties hours before the day ends.
4 Features that Make a Standard Visitor Management System (VMS)Ideal for Businesses
Here are the crucial functionalities that developers add to a visitor management software application.
Check-In Functionality
A well-designed VMS has this feature to compel guests to identify themselves and indicate their destination. At the same time, the system alerts the host worker that their employee has arrived.
Automatic Badge Printing
This system generates a badge for each authorized guest with their information and host employee. Additionally, it features the visitor's passport and the company logo.
In the past, employees had to prepare these badges, resulting in too much time wastage.
Notification
Always include this functionality to alert the host worker that you have arrived for them to authorize your entry. Usually, the guest must fill out basic information like their full name, destination, and the reason for their visit.
Blacklist Section
Nowadays, this application must have this feature that stores the details of all unauthorized guests. Usually, the system compares a guest's details with unauthorized people to determine whether they should grant them entry.
Therefore, a criminal or another ill-intentioned does not enter the office lest they interrupt business operations.
In Short
Adopting a self-help visitor management system is so paramount that it can safeguard your workers against possible health risks. This modern technology reduces unnecessary direct human interaction, warranting the physical and health safety of a company's employees.
NTSPL has been at the forefront of addressing specific challenges on visitor management with its visitor management system. All these solutions aim to streamline visitor check-ins, bolster security, and improve how the security team handles visitors.
Additionally, we ensure that any visitor visiting your premise undergoes thorough security checks to ensure the entire visitor management process is hassle-free and effective. By integrating advanced tech solutions, such as automated notifications and visitor badges, NTSPL ensures that hosts do not encounter any security breaches.
Source: NTSPL Blog
0 notes
Text
Four Vital Functions To Consider When Choosing A Visitor Management Software

In today's hectic globe, handling site visitors properly is actually essential for the safety as well as smooth function of any company. Visitor management applications supply a hassle-free option to enhance the check-in method, boost safety and security, and also provide a much better adventure for both site visitors and also personnel. Having said that, along with many possibilities offered, choosing the correct visitor management application could be discouraging. To assist you make an informed decision, listed here are 4 necessary functions to try to find:
Personalized Entry Procedures
A great visitor management ought to enable you to customize the check-in procedure to suit your association's particular needs. This features the potential to create custom fields as well as inquiries for site visitors to submit throughout enrollment. As an example, you may desire to gather various information from contractors compared to frequent site visitors. Look for an application that permits you customize the check-in process easily, ensuring a seamless experience for both guests and also personnel.
Assimilation with Access Management Platforms
Integration along with your institution's access control systems is actually yet another important function to look at. This allows real-time syncing of visitor information with access control systems, making certain that only accredited individuals can enter marked regions. Appear for a visitor management solution that supports assimilation along with popular access control systems like RFID memory card viewers or biometric scanning devices. This integration certainly not just improves security but additionally simplifies the method of dealing with access permissions for visitors.
Advance Guest Registration and Self-Service Check-In
To streamline the check-in process as well as minimize wait opportunities, seek a visitor management software that sustains pre-registration and self-check-in possibilities. Pre-registration allows website visitors to offer their information and also accomplish any called for documentation prior to coming in on-site, saving time for each celebrations. Self-check-in booths or mobile applications even further accelerate the procedure by permitting website visitors to check themselves in upon delivery, lessening the work on event workers. These attributes certainly not only boost effectiveness however likewise enhance the general visitor experience.
Immediate Visitor Surveillance and Updates
youtube
Real-time visitor monitoring capacities are vital for checking that is actually on-site at any sort of offered time. Try to find a visitor management application that gives real-time presence into visitor movements, including check-in as well as check-out times, in addition to their current area within the facilities. Additionally, the application must support notices to sharp appropriate personnel when specific website visitors get here or even depart. This feature improves safety by enabling timely reactions to any type of protection events or unexpected emergencies that might arise.
To conclude, deciding on the right visitor management app is vital for making certain the safety as well as efficiency of your company's visitor management process. By looking at these 4 important attributes-- adjustable check-in process, integration along with accessibility control systems, visitor pre-registration and self-check-in, as well as real-time visitor tracking and also notices-- you can decide on an application that meets your association's particular requirements as well as gives a smooth expertise for both guests and workers.
0 notes
Text
Awebstar's Visitor Management System for Smart, Secure, and Seamless Meet!
Managing visitors efficiently is crucial for any organization's security. Awebstar's Visitor Management System is a game-changer! With seamless check-ins and visitor badge printing, it simplifies the entire process. Real-time notifications alert hosts when their guests arrive, enhancing your front desk's productivity.
Awebstar's VMS also offers detailed visitor logs for better record-keeping and compliance. The customizable features allow you to tailor the system to your unique needs. Say goodbye to paper logbooks and embrace the future of visitor management with Awebstar. It's not just convenient; it's secure and smart.

1 note
·
View note
Text

Visitor Registration System
Visitor Access Control System Dubai
Visitor Access Control System in Alain
Visitor Management Systems in Sharjah
#visitor management system abu dhabi#visitor management software in uae#visitor access control system uae#visitor registration system in uae#visitor management software#visitor management software in alain#visitor access control system in bur dubai#visitor registration systems in uae#visitor management software in sharjah#Visitor Access Control Systems in UAE
0 notes
Text
Visitor Management Systems With Emirates id Integrations
Creating a visitor management system with Emirates ID integration involves combining visitor registration and check-in processes with the verification of visitors using their Emirates ID cards. Here are the key steps to create such a system:
System Requirements and Planning
Define the specific requirements and goals of your visitor management system.
Identify the hardware and software needed, including Emirates ID card readers and compatible software.

Emirates ID Card Reader Integration
Acquire Emirates ID card readers that can extract data from the cards.
Integrate the card readers with your system, which may involve writing or obtaining software drivers for communication.
Visitor Registration :-
Create a user-friendly visitor registration interface where visitors can input their information.
Capture necessary visitor details, such as name, purpose of the visit, date, and time.
Include a field for Emirates ID card scanning.

Data Validation :-
Implement data validation routines to ensure the accuracy and completeness of the visitor's information.
Verify that the scanned Emirates ID card matches the entered data.
Database Integration :-
Store visitor information and check-in/check-out times in a secure database.
Ensure data encryption and security measures to protect visitor data.

Notification System :-
Implement a notification system to alert hosts when their visitors arrive.
Send automatic notifications via email, SMS, or a mobile app.
Access Control :-
Integrate your system with access control mechanisms, such as electronic door locks or turnstiles, to grant or deny access based on visitor status.
Emirates ID Verification :-
Develop a module that communicates with the Emirates ID card reader.
Retrieve relevant data from the card, such as name, date of birth, and Emirates ID number.
Validate the ID card against a government database for authenticity.

Visitor Tracking :-
Maintain a real-time log of visitor movements within the premises.
Allow hosts to view the status and location of their visitors.
Reporting and Analytics :-
Provide reporting capabilities to generate visitor logs, statistics, and analytics.
Create reports for security audits and compliance.
Compliance with Regulations :-
Ensure that your system complies with UAE data protection and privacy regulations.
Keep up-to-date with any changes in laws related to visitor management.
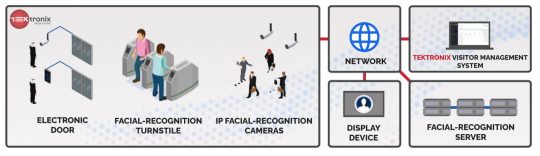
User Training and Support :-
Train employees and system users on how to use the visitor management system effectively.
Offer ongoing support and maintenance for the system.
Testing and Quality Assurance :-
Conduct thorough testing to identify and address any bugs or issues.
Test the system with various scenarios, including different types of visitors and Emirates ID cards.
Deployment :-
Deploy the system across your organization or at client sites.
Ensure a smooth transition from any existing visitor management processes.
Monitoring and Updates :-
Continuously monitor the system's performance and security.
Provide regular software updates and improvements.

Feedback and Iteration
Gather feedback from users and hosts to make necessary improvements.
Consider adding features based on user needs and changing regulations.
Implementing a visitor management system with Emirates ID integration can enhance security, streamline visitor check-in processes, and improve overall visitor experience. However, it's important to work with professionals who are knowledgeable about UAE regulations and data security to ensure compliance and protect visitor privacy.
youtube
Contact Details

Tektronix Technology Systems Dubai-Head Office
[email protected] +971 50 814 4086 Office No.1E1 | Hamarain Center 132 Abu Baker Al Siddique Rd – Deira – Dubai P.O. Box 85955
#Visitor Management System#Visitor Management Software#Visitor Management Software Dubai#Visitor Management Software Abu Dhabi#Visitor Management Software UAE#Visitor Access Control System#Visitor Registration System#Youtube
0 notes
Text
How do visitor management systems handle visitor data privacy?
Visitor management systems are designed to ensure that visitors to a facility are properly identified, tracked, and managed. However, with the collection of personal data, there is a need to ensure the privacy and security of the information collected. Here are some ways visitor management systems handle visitor data privacy:
Data collection: Visitor management systems typically collect data such as the visitor's name, contact information, purpose of visit, and other relevant information. However, they only collect the necessary data required for the purpose of the visit, and the data is collected and stored in compliance with privacy laws and regulations.
Data storage: Visitor management systems use secure servers to store visitor data. This data is encrypted to ensure that it is not easily accessible to unauthorized persons. Additionally, visitor data is stored for a limited period, after which it is securely deleted, to ensure that it is not retained for longer than necessary.
Data access: Access to visitor data is restricted to authorized personnel only. Visitor management systems use various security measures to ensure that only authorized persons can access the data. This includes password-protected access, access controls, and other security measures.
Data sharing: Visitor management systems do not share visitor data with third parties unless required by law or with the visitor's explicit consent. Additionally, visitor management systems ensure that any third-party partners comply with data privacy regulations.
Data deletion: Visitor management systems have a data deletion policy that ensures that visitor data is securely deleted after a specified period. This helps ensure that visitor data is not retained for longer than necessary.
In conclusion, visitor management systems handle visitor data privacy by collecting only the necessary data, storing it securely, restricting access to authorized personnel, not sharing data with third parties without consent, and securely deleting the data after a specified period. These measures ensure that visitor data is collected, stored, and managed in compliance with privacy laws and regulations.
#visitor management software#visitor management system in Delhi#visitor management system in India#Electronic visitor management
0 notes
Text
The Shift from Conventional to Current Visitor Management
Traditional visitor management methods, similar to logbooks and paper sign-in sheets, are becoming old as additional associations perceive the advantages of current VMS arrangements. The shift from customary to current guest the executives can be credited to a couple of key elements:
Advanced Change
As associations keep on embracing advanced change, manual cycles are being supplanted with computerized, cloud-based arrangements. This shift further develops effectiveness and takes into consideration better information the board and upgraded security.
Center around Guest Experience
Present day organizations focus on making a positive, marked guest experience. A VMS with adaptable elements permits associations to grandstand their image and give a consistent, touchless registration process.
Security and Consistence
A VMS empowers associations to keep a protected climate and stick to industry-explicit consistence prerequisites. It assists with guaranteeing that main approved people enter the premises and keeps an exact, accessible record of guest information.
How Does Digital Visitor Management System Works? Programming for visitor management is fundamental for smoothing out the inviting system. A online visitor management software welcomes visitors to your foundation by really taking a look at them in and cautioning the host staff to make associations rapidly and successfully. The program guarantees that guests sign in safely, that their personalities are affirmed, that guest photos and electronic marks are taken, and that all activity is carefully recorded. The touchless innovation diminishes collaborations among staff and visitors and outputs temperature to stop the spread of infection.
We accept that a large portion of these issues can be promptly settled by introducing the right visitor management system. In this blog we examine the main 10 motivations behind why it is basic for schools to do as such - not simply as far as accomplishing their security objectives yet additionally in computerizing their everyday activities.
Entry2Exit visitor management software allows you to categorize visitors for better footfall management. Identify and categorize visitors as per their purpose of visit and direct them accordingly. With our integrated queue management system Dubai , all types of visitors can be catered to in an organization without using a second product or complicated integration.
For More Details
Address
Office No.208, Rawdat Al Wasl Bldg Business Bay, Dubai
United Arab Emirates
Mobile : +971 50 1374167
E-mail : [email protected]
#visitor management solution#Visitor Management Software#visitor management software uae#visitor management system#https://www.quest-me.com/visitor-management-system/#https://www.quest-me.com/
0 notes
Text

Maintain security & safety protocols while creating an inviting experience for guests. Reduce your security and compliance risk while improving your organization’s brand. with the help of Proctur visitor management platforms you can manage of guest timing in your education institutions. For more information, visit us - www.proctur.com
0 notes
Link
Track and manage visitor's information easily through the best visitor management software. Find the list of top visitor systems to improve visitor experience here.
#best visitor management software#visitor management software#visitor management systems#top visitor management software
0 notes
Text
Enhance Security and Efficiency with Visitor Management Software
In today's fast-paced business environment, maintaining security and efficiency is crucial. Visitor Management Software (VMS) provides a robust solution to streamline visitor check-ins, enhance security, and manage visitor data effectively. Here’s a comprehensive look at its benefits, with insights from recent news, historical context, and a case study.
Latest News in Visitor Management Software
Visitor Management Software has seen significant advancements recently. Modern VMS solutions now feature touchless check-ins, health screenings, and real-time notifications, which have become essential in the post-pandemic era. These innovations help businesses maintain a secure and efficient visitor management process.
Historical Insight
Traditionally, visitor management relied on manual logbooks, which were inefficient and prone to errors. The advent of digital visitor management systems revolutionized the process, providing accurate data management and enhancing security. The transition from paper to digital marked a significant improvement in how businesses handle visitor information.
Case Study: Implementing Visitor Management Software in a Corporate Office
A large corporate office previously managed visitors through a manual process, leading to long wait times and security lapses. After implementing a VMS, the office streamlined its check-in process, significantly reducing wait times and enhancing security. The software provided real-time visitor data, allowing for better tracking and management. Employees and visitors experienced a more efficient and secure environment.
Key Benefits of Visitor Management Software
Enhanced Security: Ensures only authorized visitors access the premises.
Efficiency: Streamlines the check-in process, saving time for visitors and employees.
Data Management: Maintains accurate records of all visitors, aiding in compliance and reporting.
Customization: Adapts to the specific needs of different businesses.
Integration: Works seamlessly with other security systems like access control and surveillance.
Implementing VMS in Various Settings
Corporate Offices: Enhances security and professionalism.
Educational Institutions: Ensures student safety by monitoring visitors.
Healthcare Facilities: Manages patient visitors and ensures a secure environment.
Government Buildings: Provides stringent security measures and efficient visitor tracking.
Conclusion
Visitor Management Software is essential for modern businesses, enhancing security and efficiency. By adopting advanced features and integrating them into daily operations, companies can ensure a safer and more organized environment for everyone.
0 notes
Text
Why Cloud-Based Access Control Systems Are Essential for Modern Enterprises
In today’s fast-paced and digitally driven world, the need for secure and efficient access control systems has never been more critical. As enterprises grow and diversify, traditional access control systems often fail to meet modern demands. Enter cloud-based access control systems — a game-changer for businesses striving to balance security, scalability, and convenience.
This blog explores why cloud-based access control systems are indispensable for modern enterprises and how they are shaping the future of workplace security.

What Is a Cloud-Based Access Control System?
A cloud-based access control system allows enterprises to manage and monitor entry to their premises via the internet. Unlike traditional systems that rely on on-site servers, these modern solutions leverage cloud technology for storage, management, and real-time updates. They offer features like remote access, data analytics, and seamless scalability.
Solutions like those offered by Spintly have become the go-to for businesses aiming to implement sophisticated yet user-friendly access control systems.
Key Benefits of Cloud-Based Access Control Systems
1. Centralized Management
With cloud-based systems, enterprises can manage multiple locations from a single platform. This centralized approach streamlines operations, making it easier to control and monitor access across global offices.
2. Enhanced Security
Traditional systems often struggle with real-time updates, leaving security gaps. Cloud-based systems, however, ensure instant updates and patches, reducing vulnerabilities. Advanced encryption and authentication protocols further bolster security.
3. Remote Accessibility
In a hybrid or remote working environment, administrators can grant or revoke access remotely. Whether it's adding a new employee or managing a contractor's temporary access, cloud solutions make it effortless.
4. Scalability
As businesses expand, cloud-based systems can easily scale to accommodate new locations, users, or devices without significant hardware investments.
5. Cost-Effectiveness
By eliminating the need for extensive on-site hardware and maintenance, cloud-based access control systems significantly reduce costs. Subscription-based pricing models make it easier for businesses to budget effectively.
6. Integration with Other Systems
These systems can integrate seamlessly with other enterprise tools, such as visitor management, time tracking, and building management systems, offering a unified security solution.
Real-World Applications of Cloud-Based Access Control Systems
1. Corporate Offices
Managing large workforces in corporate environments becomes simpler with cloud-based systems. They allow for role-based access, ensuring employees can only access authorized areas.
2. Co-Working Spaces
These systems offer flexibility for managing dynamic environments like co-working spaces, where access needs can change daily.
3. Retail Chains
Retail businesses with multiple outlets benefit from centralized management, ensuring consistent security protocols across all locations.
4. Educational Institutions
Schools and universities can use these systems to secure sensitive areas while providing easy access for students and staff.
5. Healthcare Facilities
In healthcare, where compliance with regulations like HIPAA is crucial, cloud-based access control ensures secure and auditable entry to restricted areas.
How Cloud-Based Systems Outperform Traditional Access Control
Feature - Traditional Systems v/s Cloud-Based Systems
Setup & Maintenance
Requires extensive on-site hardware | Minimal hardware; cloud-hosted
Updates
Manual, often delayed | Automatic and real-time
Scalability
Limited by hardware capacity | Virtually unlimited
Remote Access
Not possible or limited | Fully enabled
Cost
High upfront and ongoing maintenance | Subscription-based, cost-efficient
Integration
Challenging with legacy systems | Seamless with modern platforms
The Role of Cloud Technology in Boosting Security
Cloud-based systems bring advanced security features that are crucial in today’s threat landscape:
Real-Time Monitoring: Receive instant alerts for unauthorized access attempts.
Data Encryption: Secure sensitive information in transit and storage.
Two-Factor Authentication: Add an extra layer of security for high-risk areas.
Audit Trails: Maintain detailed logs for compliance and incident analysis.
For modern enterprises, solutions like those provided by Spintly offer robust security without compromising on ease of use.
Challenges and How to Overcome Them
While cloud-based systems offer numerous benefits, they are not without challenges:
Data Privacy Concerns: Enterprises must choose providers that comply with regulations like GDPR or CCPA.
Dependence on Internet Connectivity: A reliable internet connection is essential for uninterrupted functionality. Offline modes and redundancy plans can mitigate this issue.
Initial Transition Costs: While long-term savings are significant, businesses may face higher initial transition costs when migrating from legacy systems.
By partnering with experienced providers like Spintly, enterprises can navigate these challenges with ease.
Future Trends in Cloud-Based Access Control Systems
The evolution of cloud technology continues to transform access control systems. Here are some emerging trends:
AI-Powered Access Control: Predictive analytics and facial recognition enhance security.
IoT Integration: Connecting access control with smart devices for a holistic security approach.
Blockchain for Data Security: Immutable records for added trust and compliance.
Mobile-First Solutions: Increasing reliance on smartphones as access credentials.
Why Choose Spintly?
Spintly offers state-of-the-art cloud-based access control systems tailored to the needs of modern enterprises. Their solutions are scalable, secure, and easy to deploy, making them a preferred choice for businesses worldwide.
Visit Spintly to explore how they can transform your access control infrastructure.
Conclusion
In an era where agility and security are paramount, cloud-based access control systems are no longer a luxury but a necessity for modern enterprises. They offer the perfect blend of convenience, security, and scalability, enabling businesses to adapt to the demands of today’s fast-paced world.
Whether you’re managing a single office or a global enterprise, investing in a cloud-based access control system is a step towards future-proofing your security infrastructure. Choose a provider like Spintly to ensure you’re equipped with the best-in-class solutions.
#access control system#access control solutions#mobile access#visitor management system#accesscontrol#spintly#smartacess#biometrics#smartbuilding#cloudbasedsolutions#cloud based software
0 notes
Text
Visitor Management System – Enhancing Workplace Security and Efficiency
Introduction to Visitor Management Systems
What is a Visitor Management System?
A Visitor Management System (VMS) is a digital solution designed to track, monitor, and manage visitors within an organization’s premises. It replaces traditional logbooks with efficient, automated processes for welcoming and recording guests.
Why Every Organization Needs One
In an age where safety and professionalism are paramount, a VMS ensures secure access control, streamlines visitor handling, and enhances overall brand image.
Key Features of a Visitor Management System
Pre-Registration
Visitors can register in advance, reducing waiting times and allowing staff to prepare for their arrival.
ID Verification
Modern systems include ID scanning to verify visitor identity, ensuring secure access.
Digital Check-In and Check-Out
Automated check-in processes replace manual entries, while check-out systems track exit times, providing a complete visitor log.
Visitor Badge Printing
Generate badges with visitor names, photos, and access permissions for easy identification.
Integration with Security Systems
Integrates seamlessly with surveillance cameras, access control, and emergency protocols to enhance security.
Benefits of Using a Visitor Management System
Enhanced Security
By verifying identities and restricting access, a VMS reduces risks of unauthorized entry.
Streamlined Visitor Experience
Quick check-ins and pre-registration features make the process hassle-free, leaving a positive impression on visitors.
Data Collection and Compliance
Maintain accurate visitor logs and ensure compliance with safety regulations like GDPR or HIPAA.
Professional Branding
A sleek, tech-savvy system reflects a modern and professional image to clients and partners.
Types of Visitor Management Systems
Cloud-Based Solutions
Accessible from anywhere, these systems offer scalability and frequent updates with minimal IT involvement.
On-Premise Systems
Provides greater control over data but requires dedicated IT resources for management.
Hybrid Systems
Combines the flexibility of cloud-based systems with the control of on-premise solutions.
Industries Leveraging Visitor Management Systems
Corporate Offices
Enhances workplace security while creating a smooth check-in experience for clients and guests.
Healthcare Facilities
Ensures only authorized personnel and visitors access sensitive areas, protecting patient privacy.
Educational Institutions
Tracks visitors to enhance student safety and comply with regulatory standards.
Government Buildings
Provides an additional layer of security for facilities dealing with sensitive information and assets.
How to Choose the Right Visitor Management System
Assessing Your Organization’s Requirements
Identify your unique needs, such as multi-location support or integration with existing tools.
Checking for Scalability
Ensure the system can grow with your organization’s increasing demands.
Ease of Use and Implementation
Opt for a user-friendly system that requires minimal training for staff and visitor parking management software.
Support and Training from the Vendor
Look for providers offering robust support and training for smooth implementation and ongoing usage.
Future Trends in Visitor Management Systems
AI and Machine Learning Integration
Future systems will use AI to predict visitor needs and automate routine processes.
Touchless Solutions
Post-pandemic, touchless technologies like QR codes and facial recognition are becoming the norm.
Real-Time Analytics
Advanced analytics will offer real-time insights into visitor patterns and security concerns.
Conclusion
Visitor management systems are an essential tool for modern organizations looking to enhance security, streamline operations, and present a professional image. By automating processes and integrating with existing systems, a parking management software not only improves visitor handling but also future-proofs your organization against emerging challenges.
0 notes
Text
Learn How Digital Age Visitor Management Systems Can Guarantee School Safety
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes