#vehicle-router
Explore tagged Tumblr posts
Text
Don't be afraid of the difficulty in the beginning, there are tricks to CNC processing! In 30 seconds, I will show you the secrets to getting started, and making money starts from here! 💡🚀 #CNCProcessing #StartupTips #ManufacturingMakingMoney
#CNC Machine Shop#CNC Machine Vacancy#CNC Machining Uk#CNC Mill Machine#CNC Portable Machine#CNC Routers Cutting Machine#CNC Screw-Machining For Heavy-Duty Vehicles#CNC Tube Bending Machine#CNC Turning Machine#CNC Waterjet Cutting Machines Manufacturers#Desktop CNC Routers Machine
0 notes
Text
neighborhood watch
neighbor!frankie morales x f!reader | wc: 5.7k | masterlist

Summary: When someone - or something - starts causing mischief around your new neighborhood, you and your neighbor Frankie are paired up for the new neighborhood watch.
Warnings: Not much, just cursing. Though this fic is rated T for Tame, this blog as a whole is 18+ mdni. Fluff and humor. Reader is a blank slate. No use of y/n.
A/N: This is my contribution to @punkshort's AU August Challenge to celebrate Shortie's 1-year tumblrversary. I was given the AU prompt neighbor!Frankie and ran with it. Hope you enjoy!
Palm trees lined both sides of the road, fronds gently swaying in the sea breeze as you drove through the picturesque neighborhood of bungalows to your new home. After a long and winding journey nearly halfway across the country to get there, you sighed in relief when you pulled your Wrangler into the small driveway. With all your – admittedly limited – worldly possessions shoved into the backseat, truck, and every other available crevice; you couldn’t wait to get out of the cramped space.
An old Florida 2/1 painted the color of green sea glass, the bungalow greeted you with a charming porch and two large windows bisected by the front door. The gabled roof offered taller ceilings and the wood flooring was original. By far, your favorite feature was the reading nook nestled into the living room with built-in shelves for books and the comfiest cushion to lounge on while reading or simply staring out the bay window.
Yeah, everything about this place beat what you left behind. Shitty apartment in a shitty part of a shitty town and an even shittier ex-boyfriend. Not that you were bitter about that or anything. You were still in awe that you managed to dig yourself out of that toxic situation before it completely destroyed you and scrounge up the money for this place. Thankfully, it came furnished. You didn’t have much money left for anything else.
You spent the afternoon unloading your belongings, organizing, and rearranging the place to your liking, blinds open to let the natural light in – anything to save on electric when the AC unit would be running nonstop. With the router and wifi connected, you curled up in the reading nook and watched as your new neighbors started coming home from work or set about walking dogs and mowing their small yards. A few glanced curiously at the sight of a vehicle in your driveway, no doubt wondering about the new resident.
Was this the type of neighborhood where neighbors would bring you casseroles to introduce themselves? Surely that was something only done in television shows and cheesy movies, right?
No less than an hour later, a kindly looking older woman knocked on your door, a covered dish in her hands. She greeted you with aged eyes and a toothy smile when you opened the door.
“Well, hello dear. I’m Stella and just wanted to welcome you to the neighborhood.” Stella casually peeked into the house as she spoke, not bothering to hide the blatant snooping, and you shook your head in amusement.
“Nice to meet you, Stella,” you replied, offering your name. “Would you like to come in?” The woman practically craned her neck to get a look, how could you not invite her in.
“Oh! That would be lovely, dear. As long as you don’t mind. Maybe we could snack on this key lime pie I made for you?” She bustled right in, making herself at home at your tiny dining table and you shut the door to follow her, grabbing plates and forks along the way.
“Would you like something to drink, Stella?” you asked from the kitchen. “I don’t have much yet, but I made lemonade.”
“Lemonade is great, thank you.” After a moment, she added, “Will anyone else be joining us?”
“Unless there’s a ghost hiding out in this place, I doubt it,” you replied, taking a seat across the table from her.
For the next hour, Stella grilled you for information – where were you from, what brought you to this particular neighborhood, were you single. The list of questions went on and on, but she was so kind and friendly about it that it didn’t feel intrusive. Still, relief washed over you when she changed topics from you to sharing information about the other neighbors. Much of it went in one ear and out the other until she got to someone who piqued your interest. Stella talked A LOT.
“There are two men about your age a few doors down. They are the nicest boys, always offering a hand when they can. Benny and Frankie are their names and they have been friends since they served in the military together. Quite handsome, too.”
Stella watched you as she spoke, keen eyes gauging your reaction, and she smiled when you perked up.
“Oh?” you said wanting to hear more.
“Mmhmm, thought those two might get your attention,” the older woman chuckled merrily. “Frankie is the one with dark hair and soulful eyes. He’d run into some sort of trouble a bit ago, which is why he lives with Benny while getting back on his feet.”
You hummed. “I know how that goes.” You wondered what kind of trouble he got into, but you didn’t ask Stella. That was something you’d want to hear firsthand from Frankie, if he ever wanted to share, not the rumor mill.
“Don’t we all,” Stella agreed. “Benny is the blonde one, a little younger and full of energy. Comes home with a bruised face a lot. I think he boxes or something. I’ll never understand young men and their desire to beat each other up.”
You smiled dreamily, mind wandering as Stella continued talking. While all the neighbors sounded normal, you looked forward to meeting Benny and Frankie from just the little Stella shared. They seemed most like your kind of people. The broken souls just trying to make it through life one day at a time.

It took a week to fully settle in and meet most of the neighbors. Stella lived right next door with another older couple, Ann and John, next to her. Benny and Frankie lived next door to them. One the other side of you lived a young couple, Kara and Matt, newlyweds who moved in not too long ago, followed by a quiet woman by the name of Lynn, and a busy couple in their 30s with two small children, who you referred to as “The Kellys”, finger quotes included. They scurried to and from their house like cockroaches afraid of the sun, never stopping to interact with the neighbors. You found it oddly amusing.
Across from you was another eclectic bunch of neighbors – an artist, two retired teachers, a retired cop, an insurance agent and housewife, and a variety of others whose names you were still learning.
You met Benny pretty quickly, crossing paths one morning while going for a run. Stella hadn’t lied, he was cute, but in like a golden retriever kind of way that made you want to scratch his head and throw him a ball to fetch. He was just not your type, if you even had a type. Given your track record… nah, you weren’t going down that road.
Frankie, on the other hand, was an elusive creature. He tended to work a lot if the hours were available, Benny told you. It took an extra week to meet him, and it happened completely by accident while going to check your mail. A collective mailbox area sat next to the small clubhouse, and you started swinging by at the end of your morning runs to check your mail. It gave you some time to cool down and get rid of the junk mail before you got home.
Eagerly awaiting the severance package from your last job, you excitedly rushed around the corner after that morning’s run to get to your mailbox. The collision with a hard chest knocked you right off your feet, leg muscles too fatigued from your three-mile run to stabilize after the impact.
“Oomph,” you grunted at the initial impact, quickly followed by, “Oh, shit!” as you fell backwards on your ass.
“Fucking hell! I’m so sorry!” came the rushed, masculine reply as strong arms shot out to catch you just a moment too late.
You stared up, wide-eyed, from your seated position on the grass – at least you didn’t crash down on the sidewalk – to meet the prettiest pair of baby cow eyes you’d ever seen, the irises a shade of coffee brown you could just drink in for days. Your eyes roved the man’s face, meeting tanned skin flecked with stubble and pouty lips, dark locks curled out beneath a ball cap, twisting around the backs of his ears and along the absolutely kissable stretch of skin on the back of his neck.
One large hand moved to rub along that exact expanse of skin, a nervous tic perhaps, as the other reached out to help you back to your feet.
“Are you alright? I’m really sorry ‘bout that. Wasn’t watching where I was going,” the man said once you stood before him.
Brushing the grass off your ass and the back of your thighs, you waved him off. “No, no, I’m fine and it was completely my fault. I charged around the corner like a bull in a China shop.”
The man laughed in relief, blush still visible on his pinchable cheeks. “Yeah, you kinda did. Almost knocked me off my feet, too.”
Eyeing his exceptionally broad form doubtfully, you shook your head. “I’m your new neighbor, by the way,” you said, reaching out a hand and giving him your name.
“Oh! I’ve heard about the pretty addition to the neighborhood,” he winked at you, taking your hand in a firm grip. “I’m Francisco Morales, but everyone calls me Frankie. I think you met my roommate Benny already. He’s the one who said you were pretty. He wasn’t lying.”
Heat rushed your face at the rambled compliments. Frankie was a delightful mix of flirty, nervous, and shy which you found incredibly endearing. He was also gorgeous.
Flustered and overheated, the need to flee overwhelmed you. “Well, it was nice to finally meet you, Frankie. I’m sure I’ll see you around,” you called over your shoulder as you moved to your mailbox in the back corner of the space.
“You can count on it,” he called back before departing. He didn’t notice you peek around the corner to check out his backside as he walked away. His jeans hugged his ass in a pleasing way and his shirt stretched across his shoulders, the seams hanging on for dear life.
Frankie was going to be trouble; you could feel it. The best kind of trouble, yes, but trouble none the less.

Working from home allowed you to keep a great schedule. No more long commutes to the office, getting caught in traffic on the interstate, spending too much money on gas, or racking up the mileage on your car. You loved the Wrangler, but fuel economy was not its best quality. Instead, you could sleep until a respectable hour, still get a morning run or walk in, and have time for a shower and breakfast before plopping down at your desk for the workday.
And you loved your new job. Not only did you get to work from home, but you were paid to learn and develop learning programs for corporate trainings all day. The nerd in you danced with joy every time you learned something new or received feedback on something you put together.
The only downfall to this new life of yours?
Loneliness.
Sure, video calls with clients and colleagues peppered your days and you occasionally ran into a neighbor on your morning runs. But real human connection? No, there was none of that. Aside from talking to the plants or yourself, you didn’t even have a pet to provide companionship.
Three weeks after settling in, you found yourself at the shelter browsing adoptable animals. Growing up loving animals but never allowed to have pets – even your asshole ex was adamant about not having any in the house, which you should have seen as a giant red flag much sooner – you were finally able to add a furry little being to your family. You weren’t picky either, going in completely open-minded and letting the universe choose a fur friend for you.
The universe delivered ten minutes after arriving at the shelter when a big-eared, blue-eyed, black and white shepherd looking dog bounded up to you excitedly, darting directly between your legs and goosing you so hard it felt like your soul left your body with the yelp that burst from your lips.
“Joshua! No!” a harried volunteer called out, rushing over to you and the overly eager four-legged fiend. “I am so sorry! He loves people and picks out his favorites with a little too much zest.”
The woman wrangled the dog, which was no easy feat. Bigger than a breadbox but smaller than a German Shepherd, Joshua was a sturdy boy – and strong, based on the visible muscles in his hind legs – presenting a challenge when he put his mind to it.
Right then, his mind focused on you, and he refused to leave your side, licking at your hands with his pink tongue, booping you with his snout until you scratched his head, ears perked up as he gazed at you with those ice blue eyes.
You fell in love instantly. Plopping down on the ground, right there in the middle of the kennel walkway, you ruffled Joshua’s short-haired fur. He practically smiled in delight and melted into you as you pet him, tongue lolling out of his mouth as he presented his belly.
A pile of paperwork and a small fee later, you and Joshua the two-year-old McNab Shepherd headed to the pet store for goodies to start your adventure together. Joshua herded you around the store with single-minded determination, choosing his toys and treats while you spoke to the staff about the best food to feed him. Hundreds of dollars later, a gangly teenager helped you load a large dog bed, 50-pound bag of dry food, and two bags full of toys and treats into the Wrangler. Joshua sat shotgun, head hanging out the window as you drove home.
Joshua settled right in with minimal fuss, spending his days laying under your desk while you worked, booping you with his snout when he needed attention or walkies, and – worst part – chomping on your right ass cheek when you weren’t going in the direction he wanted. That was a habit you needed to break, asap. With Joshua at your side, you found yourself outside more, stopping to talk to all the neighbors and being recruited to join the new neighborhood watch. Suddenly, you no longer felt lonely or left out.

Tim, the retired cop who lived across the street, started the neighborhood watch out of boredom, you reckoned. He served the public in larger cities for much of his law enforcement career, and the small-town life took a while for him to get used to. Thus, Tim liked to patrol the neighborhood, self-identifying as the Sheriff of Paradise, keeping an eye out for mischief.
Recently, Tim noticed evidence of some mischief in the form of knocked over garbage cans and missing or broken lawn ornaments. Minor things that could potentially be explained away by blaming the occasional trash panda searching for a midnight snack. Like a dog with a bone, Tim was unwilling to chalk it up to mischievous racoons and began recruiting neighbors to join him in keeping an eye on the neighborhood.
That’s how you found yourself seated on a couch in Tim’s living room, squeezed between the broad shouldered forms of Benny and Frankie, with other neighbors scattered around room. Tim stood in front of the small group with a dry erase marker in hand; a large whiteboard perched on a chair next to him.
“Thank you all for your interest in keeping this neighborhood safe. There have been several concerning things happening lately and I would like for us to make a collective effort in heading them off before things escalate,” Tim began.
His speech continued and the sudden vision of Scruff McGruff the Crime Dog popped into your head. You barely managed to stifle your laughter.
Out of the corner of your eye, you caught Benny flashing Frankie an incredulous look and mouthing “Is this guy for real?”
You wondered the same thing but kept those thoughts to yourself and listened as Tim continued.
“I took the liberty of assigning teams of two and setting patrol schedules,” he said, turning to the whiteboard. The sound of the dry erase marker squeaking across the board was the only noise in the room for a solid five minutes as you all stared at Tim’s back.
This dude was intense.
Frankie’s knee started bouncing next to you, jostling the cushion a little. Smiling warmly, you reached out a hand, placing it just above his knee to get him to stop. The warmth of his skin flowed through his jeans, igniting a fire inside your belly as his wide eyes shot to you, a hesitant smile on his face as he mouthed “Sorry”.
Tim spun around and called out the pairings then, breaking the eye contact between you and Frankie. Your breath caught when he announced your name and Frankie’s as the third team. Frankie beamed at you and bumped your shoulder.
“Looks like we’re a team,” he said, dark eyes shooting to frown at Benny over your shoulder for a moment. You turned to see what Benny did, but the man just grinned and winked at you.
“Yeah,” you replied, still a little flustered from the heat bubbling in your core. Jesus, could you not think of anything witty to say?
Tim called the meeting to an end ten minutes later – thank the fucking Lord above! – and you followed Frankie outside. He and Benny basically walked you to your door just to say hi to Joshua.
Your happy fur baby bounded down the front steps to say hi the moment you opened the door, tail wagging so hard his whole booty shook with the effort.
“No jumping, Joshua!” you called with a laugh as Benny practically fell to the ground to play with him.
After getting a few pets in, Frankie left the rambunctious pup to wrestle with Benny while he moved closer to you. “He’s really just a big kid,” he said with a chuckle.
“I can see that,” you replied, meeting Frankie’s chocolate eyes as a smile spread across your lips. Damn, he was gorgeous, and you could easily get lost in those eyes.
“So, uh, looks like our first neighborhood watch shift is tomorrow night from 9 ‘til midnight,” Frankie said as you both watched the makeshift WWE match happening in your little front yard.
“Yeah, that’s past my normal bedtime so it will be your job to keep me awake,” you responded with a laugh and a shrug of the shoulders. “Sad, but true.”
“Not a night owl? Me either. I’m sure I can come up with a few ways to keep you awake,” Frankie replied boldly, though a blush crept up his neck into his face.
You shot him a mock scandalized look before collapsing into laughter. “Yeah, I’m sure you could.” After a beat, you steered the conversation back to the neighborhood watch. “What do we need to do on this shift? I’ve never been part of something like this and, to be honest, I tuned out half of what Tim droned on about.”
Frankie’s smile widened until the dimple in his cheek popped, drawing your eyes. “That guy sure could talk, huh?” When you nodded, he added, “I guess we just walk around and make sure nothing’s happening. I’ll meet you here tomorrow night with flashlights in case we need them, feel free to bring Joshua. Nothing will get past the three of us.”
True to his word, Frankie stood at the base of your walkway at five minutes to 9 pm with a backpack containing bug spray, water, snacks, and flashlights. Joshua bounded towards him the moment you opened the door – you should have known to put his leash on first, but you were just as eager as the pup to see the handsome man waiting for you.
After handing you a flashlight, Frankie gestured for Joshua’s leash, clipping it to the dog’s collar and gripping it tightly in his right hand. You let Joshua lead the way, stopping every so often so he could sniff at something interesting.
You weren’t nervous, per say, but you did have some concerns about how awkward these three hours might be. Those concerns were all for naught as conversation flowed easy and free between the two of you as you both asked and answered questions about each other.
Frankie told you a little about his time in the military and how he met Benny and his other friends. He shared about his current job working on helicopters and trying to get his pilot’s license back after some misunderstandings. You told him about ditching your old life to start fresh, how your ex turned out to be controlling and isolated you from your friends. You told him about your new job and how happy you were to be in control of your own life again.
“Sounds like that guy was a real asshole. Me and the boys could go kick his ass for you, if you wanted.”
You appreciated the offer but turned it down. Instead, you asked about his love life. “You mean my complete lack of one?” Frankie replied teasingly.
“Hmmm,” you hummed distractedly. Something seemed off about Stella’s front garden. Your eyes narrowed, searching the shadows from the streetlights and Frankie followed your gaze, brows furrowed.
“That wasn’t like that when we passed by on our last lap,” he said as you both took in the destruction. Potted plants toppled over, some clay pots shattered, leaves ripped from shrubs, flowers crushed, and sporadic holes dug in the topsoil.
In a word, it was a mess.
“No, it most definitely was not,” you replied and immediately glanced around searching for the culprit. The street was empty save for the two of you. “I don’t see anyone. Whoever did this is hiding or long gone.”
“We better write this down in our notepad for Tim. He’ll want full documentation, so we can’t leave out a single detail.” Frankie pulled the small, spiral bound notepad and a pen from the front pocket of his backpack, handing them to you. At your raised brow, he shrugged with a boyish grin and added, “I’m holding a flashlight and your dog’s leash. Besides, you probably have much neater handwriting.”
“You’re lucky you’re cute.” Rolling your eyes, you accepted the items and flipped the notepad open to the first page. Noting the date, time, and location, you wrote a few notes about the destruction in Stella’s garden. After a moment, you pulled your phone from your back pocket and snapped a few pictures. Tim would appreciate the effort.
“You think I’m cute?” Frankie teased once you finished, sounding pleased as punch at the idea. You ignored him.
The rest of the night passed with no further incidents, and you waved to Frankie as he walked back to his house after handing you Joshua’s leash. Despite the exhaustion plaguing your body, your mind fixated on thoughts of Frankie for two more hours before you finally fell asleep with Joshua snuggled against your side.

Things only got stranger the next two nights you patrolled the neighborhood with Frankie.
“So, what do you do for fun, Frankie?” you asked, making conversation as you walked along the sidewalk.
“The usual, I guess. Hanging with friends, listening to music, playing the occasional video game, and having a few beers. Mostly just hang with the boys and reminisce about the old service days. Oh! And flying, of course. Can’t wait to get my license reinstated.” Frankie ran a hand along the back of his neck, a little embarrassed about how boring he sounded. “How about you?”
“Oh, you know, the same stuff,” you laughed. “I lead a very exciting life. I read, lounge on the couch watching reality tv shows, run in the mornings. Stuff all the cool kids do.”
“We’re an exciting pair, huh?”
“It only goes downhill from here.”
You bantered back and forth as you worked your way through the neighborhood, keeping an eye out for signs of mischief. Frankie was the first to spot the trouble in the mail area. A few mailboxes were wrenched open with envelopes and magazines ripped and scattered across the ground. Joshua sniffed at them unhelpfully.
“How’d someone even get these open?” you questioned. “They need a key.”
Frankie shrugged. “Must’ve pried them open with something. Wouldn’t be too hard, actually. These aren’t the best locking mechanisms. Here, write it down while I take some pictures.” He fished the notepad from the backpack and handed it to you, snapping photos of the mess while you jotted down observations.
“How long have you lived here?” you asked Frankie once you tidied up the mess into a small pile for the other residents to sort through in the morning.
“A few years. You?” He froze, realizing the stupidity of the question, and grimaced. “I clearly have foot in mouth disease. Forget I said that. Please.”
Waving him off with a chuckle, you told him not to fret. “Have you noticed anything like these shenanigans happening before?”
Silent for a few moments, Frankie thought about it. “Not that I recall, but I’m not too sure I paid much attention.”
“It’s weird though, right? Like all of this seems like something a couple of middle school kids would do but they wouldn’t be out this late. Shit, I haven’t even seen kids that age in this neighborhood.”
Frankie nodded. “Come to think of it, we haven’t seen any footprints or litter either. Kids always leave a mess, right? Like candy wrappers and soda cans and shit.”
The next night, things got more bizarre. Joshua stayed at home, exhausted after visiting the vet that afternoon and getting a few shots, leaving you and Frankie on your own.
Frankie spotted a light on in the detached single-car garage at Kara and Matt’s house after a few laps through the neighborhood. Both of you swore the light had been off the other times you passed by. It wouldn’t be so odd if it was a weekend night. But you knew the couple got up really early for work and there was no way one of them would be tinkering in the garage after 11 pm on a worknight.
The pair of you approached the garage warily, sounds of rummaging and glass breaking coming from inside the wooden structure. You looked to Frankie for direction. He gestured for you to stay put a couple yards back, shrugging the backpack from his shoulders, and pulled a handgun from the front pocket.
Your eyes widened at the sight of the weapon. “What are you gonna do with that?” you whispered as he handed you the bag.
“Nothing unless I have to,” Frankie replied quietly and edged closer to the garage. He crept up to the garage door, trying to peek through the dirt smudged windows, but it was impossible to see anything. Instead, he slowly made his way around toward the side of the garage.
A few steps from the corner, his foot caught on a stray cinderblock, causing him to trip with a yelp. The sound within the garage ceased, immediately followed by a scramble and rustling in the wooded area behind the garage. By the time Frankie righted himself and turned the corner, who- or whatever it had been in the garage was gone. A small window on the side of the garage sat open and Frankie peered inside, finding utter destruction within the garage.
“Well?” you inquired from your position. “Anything?”
“Nothing but a mess. I didn’t see anyone and there was nowhere for someone to hide.” He motioned you over now that it was clear. Slipping the weapon back into the bag, Frankie pulled out his phone and took photos through the window.
Gazing at the window, you said, “I can’t imagine they leave this open like this. It must be a person, right? How would an animal get a window like this open? Or turn on the light?”
Frankie shrugged. “I have no fucking clue. We should let Tim know about this. He’ll want to talk to Kara and Matt in the morning.”
Sliding the window shut, Frankie led you from the property.

“This is just getting ridiculous,” Benny muttered from the backseat. “I can’t believe that dickhead has us on a fuckin’ stakeout on a Friday night. Who died and made him Sheriff of fuckin’ Palmingham.”
“Sheriff of Palmingham,” you repeated with a guffaw. “Good one, Benny boy.”
You, Benny, and Frankie were parked at one end of the street in Frankie’s truck, with a few other neighbors stationed at the other end. A stakeout was Tim’s brilliant idea to finally catch the culprit terrorizing the otherwise quiet neighborhood. He created a few teams and stationed them at the end of the two main streets of the small neighborhood. Tim wanted the culprit caught tonight.
The first thing you learned about stakeouts was they were boring as fuck. If not for the company of two handsome men, you’d have been banging your head against the dashboard after the first fifteen minutes. After the first hour of staring through the windows, you and Frankie resorted to playing a variation of twenty questions.
“What is your favorite food?”
“To make or to order out?” you questioned. When Frankie rolled his eyes playfully, you added, “What? There’s a big difference!”
Nodding his head, Frankie laughed. “Ok, if you say so. Tell me both then.”
Sitting back in your seat, you tapped your chin with a finger. “Salmon to cook and beef wellington or scallops to order out. What about you?”
Benny watched from the backseat as the two of you went on and on. “For fuck’s sake, I feel like a third wheel on a first date,” he complained. “Will you just ask her out already?”
“Damnit, Benny,” Frankie growled. Enjoying the conversation with you so much, he almost forgot his friend was even there.
“You want some cheese to go with that whine, Ben Ben?” you teased. “I know little girls who whine less than you.”
“You want some cheese with that whine,” Benny mocked in a high-pitched voice. Leaning forward in his seat, Benny perched his chin on the back of the front bench seat, a shit-eating grin playing across his lips. “You know, if you like Salmon for the omega 3 fatty acids, my boy Fish here has some mega D fatty acid for you. It’s a lot better, or so I’ve heard.”
“What the fuck, Benny?!” Frankie exclaimed as your mouth dropped open in shocked amusement. He glared over his shoulder at the younger man before looking at you with dark, pleading eyes. “Please ignore this fucking idiot.”
“Come on, man. That shit was funny!” Benny insisted, broad shoulders shaking with laughter.
You patted Frankie’s thigh reassuringly. “I mean, it is pretty freaking hilarious, I’ll give him that. And Fish? Is that your nickname or something?”
“At least your girl has a sense of humor.” Benny slumped back in his seat at Frankie’s scowl.
Still staring down his friend in the rearview mirror, Frankie explained the call signs from their army days. Movement down the block drew his attention mid-sentence and he drifted to a stop. “Can you guys see that?”
You reached for the binoculars sitting on the dash, raising them to your eyes to peer into the distance. Something darted from the shadows into an area of the street brightened by a streetlight, and you gasped.
“It’s a fucking monkey!”
The rest of the night turned into a shitshow as the three of you chased a small monkey – a capuchin, you guessed – around the neighborhood. After a quick call to Tim, the other neighbors on stakeout joined you in the effort to capture the mischievous little bugger. Shortly before dawn, someone found the monkey asleep on a low-hanging tree limb and scooped the thing up, quickly containing him in a travel pet crate.
Exhausted yet exhilarated, you walked toward your house when a sudden commotion sounded a couple doors down. Ann and John rushed from their home, frantically searching for something in the yard.
“Where could he have gone?” Ann called out to John.
“How did he even get out?” John yelled back, moving to search the backyard.
Pausing mid-step, you turned toward where Frankie stood talking to Tim. The capuchin monkey sat in a pet crate at the former cop’s feet as they talked about what to do with it. Eyes narrowing, you looked back at the older couple scouring their yard.
The pieces clicked into place, and you rushed over to Frankie. “Hey, uh, I think this little cutie belongs to Ann and John,” you said, pointing over your shoulder. “They’re searching for a missing pet, and it seems awfully coincidental.”
Sure enough, the older couple were searching for the little monkey named Cosmo, who they were pet sitting for their grandson. The little rascal had been sneaking out each night to wreak havoc on the neighborhood out of boredom. Cosmo was used to a much higher level of activity than the older couple could offer. Thankfully, the grandson was coming later that day to take Cosmo home.
“Hey, you wanna come over for some brunch?” you asked Frankie once all the drama wrapped up, not wanting to part from him just yet. You really enjoyed his company and wanted to get to know him even more. “I’m thinking pancakes and mimosas. What do you think?”
“I, uh, think that sounds like a perfect first date,” he replied with a shy smile, one hand lifting his cap as the other combed through his curls.
“Oh yeah? I think this might count as a third date given all the time we’ve spent alone together this week.”
Frankie’s lips spread until his smile split his face and his dark eyes burned with want. “Third date, huh? Do you have a rule about third dates?”
“Why don’t you come in and find out?” Grasping his large hand in yours, you led him inside.
#shortieswritingchallenge#neighbor!frankie#frankie morales#frankie morales x f!reader#frankie catfish morales#frankie morales fluff#fluff and humor#frankie morales fanfic
173 notes
·
View notes
Text
Future Brisbane
So, at the end of “Surprise”, we get to see future-Brisbane, maybe 25-30 years in the future? A grown-up Bluey brings her child to visit her parents’ house, so her kid can blast Dad with tennis balls like she did.


Compare future Brisbane with current Brisbane

First of all, nice to see the house hasn’t fallen down, Dad and Mum have kept it in good repair (thanks Hammerbarn) and it now has solar panels, as do a number of other homes.
Many things have changed:
An incredible increase in land use density; multiple medium and tall towers (like in downtown) now are common in the suburban area. Assuming this means much more multifamily housing.
Roads much less dominant/conspicuous in the hills
Look how the trees have grown.
The communications towers on the hilltops are less conspicuous.
Three waste/recycling bins (addressing the green waste recycling issue)
Drone transport (for deliveries?)
Some things haven’t changed:
Sky is blue. That’s good.
The whole area hasn’t flooded from rising sea levels…
Adult Bluey drives, or at least is using a private vehicle, rather than something like an on-demand transit service. (Maybe the drone deliveries mean less congestion on the roads but traffic has never been a big issue in Bluey-Brisbane 😉)


Inside the house is not crazy-futuristic, some electronic gadgets, like a Roomba. (I was expecting more high-tech like a Mr. Fusion from “Back to the Future” but that’d probably be by the kitchen or by the garbage wheelie-bins.)
I know my parents still have the same stereo they had 30+ years ago, and much of the same furniture.
Note that 30 years of progress has not improved how Roombas dock with their charging stations.
Some other new tech in the front hall:
Electronic digital picture frames with weird floating connections to the wall.
Wifi router thing on ceiling
Spherical thing (maybe something like an Alexa?)
New comfy chair, replacing the red one.

Density Increase
The increase in land use density in the Brisbane suburbs where the Heelers live is one of those dreams of land use planners; more density in already developed areas is generally considered a plus, assuming the infrastructure can accommodate it. Higher density means more people in a given area making public transit more efficient and reducing costs to serve the homes with utilities.
Is that kind of growth possible in only a few decades? Yes, here’s a North American example… this is where I grew up, in the early 1980s it looked like this in Mississauga, ON around the Square One shopping centre…

…and now it looks like this in the 2020s.

So that’s growth over about 30-40 years, which is a little longer than how much time has apparently elapsed in “Bluey”, but not a lot. It’s possible, and this kind of thing can snowball / accelerate once initial projects get underway.
Public opposition (NIMBY) can prevent this kind of thing from occurring in many cities.
79 notes
·
View notes
Text
very curious right now
*this can be either sexual or romantic, but im mostly thinking about sexual attraction
16 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Text
An indictment from the US Department of Justice may have solved the mystery of how disgraced cryptocurrency exchange FTX lost over $400 million in crypto. The indictment, filed last week, alleges that three individuals used a SIM-swapping attack to steal hundreds of millions in virtual currency from an unnamed company. The timing and the amount stolen coincides with FTX's theft. Meanwhile, in a letter obtained by WIRED this week, seven lawmakers have demanded the DOJ stop funding biased and inaccurate predictive policing tools until the agency has a way to ensure law enforcement won’t use them in a way that has a “discriminatory impact.”
In Florida, prosecutors say a 17-year-old named Alan Winston Filion is responsible for hundreds of swatting attacks around the United States. The news of his arrest was first reported by WIRED days before law enforcement made it public. It was the culmination of a multi-agency manhunt to piece together a trail of digital breadcrumbs left by the teenager. In Ukraine, unmanned aerial vehicles have been powerful tools since the Russian invasion began in February 2022. But as the war rages on, another kind of unmanned robot has increasingly appeared on the front-lines: the unmanned ground vehicle, or UGV.
For months lawyers affiliated with an India based hacker-for-hire firm called Appin Technology have used legal threats to censor reporting about the company’s alleged cyber mercenary past. The EFF, Techdirt, MuckRock, and DDoSecrets are now pushing back, publicly sharing details for the first time about the firm's efforts to remove content from the web. It’s a dangerous world out there, so we’ve also got a list of some major patches issued in January that you can use to update your devices to keep them secure.
And there’s more. Each week, we highlight the news we didn’t cover in-depth ourselves. Click on the headlines below to read the full stories. And stay safe out there.
China’s Hackers Keep Targeting US Water and Electricity Supplies
For years Western security officials have warned about the threat of China collecting data about millions of people and the country’s hackers infiltrating sensitive systems. This week, Federal Bureau of Investigation director Christopher Wray said hackers affiliated with the Chinese Communist Party are constantly targeting US critical infrastructure, such as water treatment plants, the electrical grid, and oil and gas pipelines. Wray’s testimony, at a House subcommittee on China, came as the FBI also revealed it removed malware from hundreds of routers in people’s homes and offices that had been planted by the Chinese hacking group Volt Typhoon.
“China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities,” Wray said in the public appearance. “Low blows against civilians are part of China’s plan.” The FBI director added that China has a bigger hacking operation than “every other major nation combined,” and claimed that if all of the FBI’s cyber-focused agents were assigned to work on issues related to China, they would still be outnumbered “by at least 50 to 1.”
While concerns about the scale of China’s espionage and cyber operations aren’t new, the US intelligence community has been increasingly vocal and worried about critical infrastructure being targeted by Volt Typhoon and other groups. “The threat is extremely sophisticated and pervasive,” NSA officials warned in November. In May 2023, Microsoft revealed it had been tracking Volt Typhoon intrusions at communications and transportation infrastructure, among other critical infrastructure, in US states and Guam.
The FBI and DOJ, also revealed this week that they remotely removed the KV Botnet malware from hundreds of routers infected by Volt Typhoon. The impacted routers, from Cisco and Netgear, were mostly at the end of their life, but were being used as part of wider operations. “The Volt Typhoon malware enabled China to hide, among other things, pre-operational reconnaissance and network exploitation against critical infrastructure like our communications, energy, transportation, and water sectors,” Wray said. It isn’t the first time US officials have obtained a court order to remotely wipe devices infected by hackers, but the move is still rare.
‘Untraceable’ Monero Transactions Have Been Traced, Police Claim
Since the first cryptocurrencies emerged more than a decade ago, there has been the assumption that the blockchain-based digital currencies are anonymous and untraceable. They are, in fact, very traceable. Researchers have shown how people can be linked to the transactions they make and law enforcement have used the techniques to help bust illicit dark web markets and catch pedophiles. There are, however, still some privacy-focused cryptocurrencies that appear to be less traceable than Bitcoin. This includes Monero, which is increasingly being adopted by sellers of child sexual abuse materials.
This week investigators in Finland said Moreno-tracing helped reveal the identity of a hacker who allegedly attacked psychotherapy company Vastaamo in 2020, stealing thousands of patient records and threatening to leak them unless people paid a ransom. Investigators from the Finnish National Bureau of Investigation claim they used heuristic analysis to infer where funds were moved to. The investigators did not reveal the full methods of how they allegedly traced the Monero payments, however, they add to the growing body of evidence that cryptocurrency tracing firms and investigators may be able to track the currency.
Russia Likely Behind a Spike in GPS Interference, Officials Say
Planes flying over Europe have faced a spike in accuracy issues with GPS systems used for navigation in recent months. The head of Estonia’s Defense Forces has claimed that Russia is likely the source of this interference, according to an interview with Bloomberg. “Someone is causing it, and we think it’s Russia,” Martin Herem told the publication, adding that Russia may be testing its electronic warfare capabilities and “learning” the most effective tactics. Across Europe, and particularly the Baltics region, there has been a reported increase in GPS jamming, with Finland reporting large interferences in December and pilots repeatedly reporting issues with their navigation systems.
Vault 7 Hacking Tools Leaker Joshua Schulte Sentenced to 40 Years
In 2017, the Vault 7 leaks exposed some of the CIA’s most sophisticated hacking tools, including how the agency could compromise routers, phones, PC, and TVs. Joshua Schulte, a former CIA engineer in the agency’s Operations Support Branch who prosecutors identified as being behind the data breach and responsible for leaking the materials to Wikileaks, was convicted in numerous trials in recent years. Schulte, who denied the allegations, has been sentenced to 40 years in prison for the espionage and also for possessing thousands of child abuse images. Judge Jesse Furman, sentencing Schulte, said he had caused “untold damage to national security.” In June 2022, The New Yorker published this comprehensive investigation into the data breach and Schulte’s troubled history working at the agency.
2 notes
·
View notes
Text
EXPLORING THE 5 COOL PARTNER SELLER ELECTRONICS PRODUCTS-Part1
Exploring the 5 Cool Partner Seller Electronics Products
Prologue
Are you an electronics enthusiast looking to expand your electronics project repertoire? Want to take your skills to the next level by exploring new and exciting products? Look no further than our list of five cool electronics products from partner sellers!
Whether you’re interested in building your own smart home devices, experimenting with sensors, or creating your own robot, these products are sure to inspire you. They cover a lot of application areas, from loop detectors used to monitor vehicle count in parking garages to Arduino CNC shields used in CNC machines, from simple pulse sensors used to detect cardiovascular pulse signals from fingertip to RGB LED panel light used in smart home, these products are unique, compact, and functional. Not only are these products fun to build and use but they’re also designed to help you learn new skills and techniques along the way.
What’s more, these products all come from trusted partner sellers who are committed to developing high-quality products. They’re happy to provide technical support for customers who have questions, so you can be sure you’re getting the best in electronics.
So get ready to dive into the world of electronics and explore these five cool partner seller products. You’re sure to find something that piques your interest and takes your own electronics projects to the next level.
Inductive Loop Vehicle Detector by Elektronika-ba
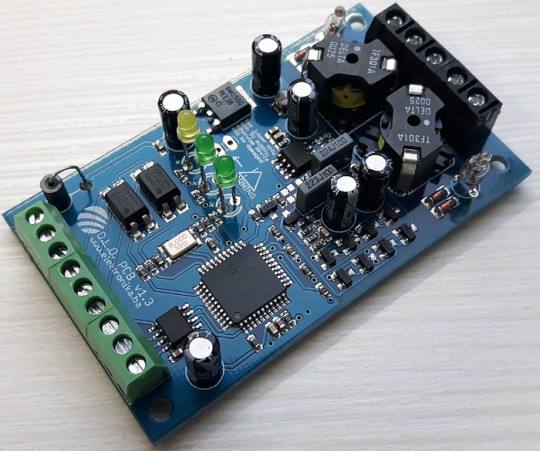
Whether you need to monitor occupancy and count vehicles in parking garages, control vehicle access at door and barrier controls, or facilitate traffic light installations and traffic controllers, the inductive loop detector is the perfect solution. It can even detect the direction and speed of vehicle traffic, making it an invaluable tool for a variety of traffic-related applications. In addition, this device can function as a stand-alone speed trap and can be easily interfaced with Arduino.
We can also provide a pre-programmed PIC chip to meet your project requirements.
Specifications
Number of operating modes: 4
Tuning: Automatic
Detection type: Presence/Pulse
Presence time: Adjustable in 3 steps
Pulse duration: 250 ms / 500 ms
Signal filtering: Adjustable in 2 steps (NORMAL, HIGH)
Loop inductance: 20 uH — 1000 uH
Frequency range: 20 kHz — 145 kHz
Frequency selection: 2 combinations (LOW, HIGH)
Sensitivity: Maximum 0.0025% Δf/f, adjustable in 8 steps
Detection speed: 10 ms by default, adjustable
Start-up time: ~ 1 second per channel (or longer if the frequency is not stable)
Temperature range: -35°C — 120°C
Sensor protection: Galvanic isolation + gas discharge tube for lightning protection
Don’t settle for less — click here to learn more about the Inductive Loop Vehicle Detector and experience the compact, yet cool detector!
Arduino CNC Shield V3.51 by Protoneer
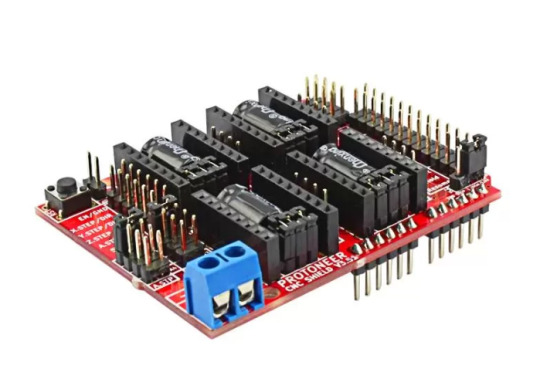
Designed by Protoneer, this kit is packed with features to ensure high precision control of your stepper motors, you can use it to easily build small CNC routers, DIY laser cutters, 3D printers, or any project that requires precise stepper motor control.
Our latest version 3.51 includes several enhancements to make assembly and installation even easier. We’ve added end-stop and probe signal filtering circuitry to eliminate false triggers and allow the use of unshielded cables for end-stops and probes. We’ve also increased the size of the solder pads for easier assembly and updated the probe pin labels to make installation a breeze.
With the Arduino CNC Shield Kit, you’ll have everything you need to build your own CNC router or mill with ease.
Features
Includes Noise Filers on all end stops and the probing pin. (New in V3.51)
GRBL 0.9 compatible. (Open source firmware that runs on an Arduino UNO that turns G-code commands into stepper signals https://github.com/grbl/grbl)
4-Axis support (X, Y, Z, A-Can duplicate X, Y, Z or do a full 4th axis with custom firmware using pins A4 and A3)
2 x End stops for each axis (6 in total)
Coolant enable
Uses removable Pololu A4988 compatible stepper drivers. (A4988, DRV8825 and others)(Not Included)
Jumpers to set the Micro-Stepping for the stepper drivers. (Some drivers like the DRV8825 can do up to 1/32 micro-stepping )
Compact design.
Stepper Motors can be connected with 4-pin molex connectors or soldered in place.
Runs on 12–36V DC. (At the moment only the Pololu DRV8825 drivers can handle up to 36V so please consider the operation voltage when powering the board.)
Don’t wait — click here to see more about the Arduino CNC Shield V3.51 and start your next project today!
Easy Pulse Mikro by Embedded Lab
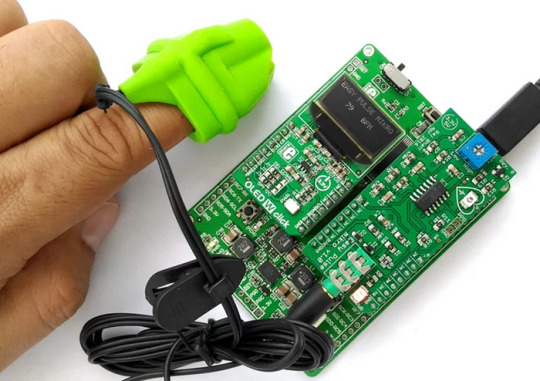
What’s more, the Easy Pulse Mikro is designed in the convenient Mikro bus form factor, making it easy to integrate with a wide range of mikroElektronika’s development boards. With all necessary instrumentation and amplification built right in, this powerful sensor provides a clean and precise analog PPG waveform output that’s routed to the AN pin of the mikroBus connector.
Whether you’re a hobbyist, student, or professional developer, the Easy Pulse mikro is the perfect tool for monitoring heart rate and other vital signs.
Click here to see more about the Easy Pulse mikro.
Features
Compatible with mikroBus socket.
Filtered and amplified analog PPG signal output
On-board potentiometer for adjusting amplifier gain, if needed (rotate clock-wise for increasing gain)
Onboard LED for indicating heartbeat. It flashes synchronously with the heartbeat on detecting the pulse from the fingertip.
2 notes
·
View notes
Text
Portable Automotive Wi-Fi Router Market To Witness the Highest Growth Globally in Coming Years

The report begins with an overview of the Portable Automotive Wi-Fi Router Market 2025 Size and presents throughout its development. It provides a comprehensive analysis of all regional and key player segments providing closer insights into current market conditions and future market opportunities, along with drivers, trend segments, consumer behavior, price factors, and market performance and estimates. Forecast market information, SWOT analysis, Portable Automotive Wi-Fi Router Market scenario, and feasibility study are the important aspects analyzed in this report.
The Portable Automotive Wi-Fi Router Market is experiencing robust growth driven by the expanding globally. The Portable Automotive Wi-Fi Router Market is poised for substantial growth as manufacturers across various industries embrace automation to enhance productivity, quality, and agility in their production processes. Portable Automotive Wi-Fi Router Market leverage robotics, machine vision, and advanced control technologies to streamline assembly tasks, reduce labor costs, and minimize errors. With increasing demand for customized products, shorter product lifecycles, and labor shortages, there is a growing need for flexible and scalable automation solutions. As technology advances and automation becomes more accessible, the adoption of automated assembly systems is expected to accelerate, driving market growth and innovation in manufacturing. Portable Automotive Wi-Fi Router Market Size, Share & Industry Analysis, By Vehicle Type (Passenger Cars, Commercial Vehicles), By Sales Channel Type (OEM, Aftermarket) And Regional Forecast 2021-2028
Get Sample PDF Report: https://www.fortunebusinessinsights.com/enquiry/request-sample-pdf/105485
Key Strategies
Key strategies in the Portable Automotive Wi-Fi Router Market revolve around optimizing production efficiency, quality, and flexibility. Integration of advanced robotics and machine vision technologies streamlines assembly processes, reducing cycle times and error rates. Customization options cater to diverse product requirements and manufacturing environments, ensuring solution scalability and adaptability. Collaboration with industry partners and automation experts fosters innovation and addresses evolving customer needs and market trends. Moreover, investment in employee training and skill development facilitates seamless integration and operation of Portable Automotive Wi-Fi Router Market. By prioritizing these strategies, manufacturers can enhance competitiveness, accelerate time-to-market, and drive sustainable growth in the Portable Automotive Wi-Fi Router Market.
Major Portable Automotive Wi-Fi Router Market Manufacturers covered in the market report include:
Major players operating in the global Portable Automotive Wi-Fi Router market include KuWFi Technology Co., Ltd, ZTE Corporation, Huawei Technologies Co., Ltd., TP-Link, Sierra Wireless, Linksys, Teldat Group, and NETGEAR Inc. among others.
The automotive companies’ are thus adopting Wi-Fi technology and are implementing advanced connectivity devices to deliver enhanced connectivity services to the customers. Additionally, the growing penetration of Internet of Things (IoT), and cloud computing in the automobile sector is permitting the automobile telematics and fleet management to offer improved solutions to the customers. Therefore, the thriving automotive industry is creating great opportunities for the portable automotive Wi-Fi routers in the global market.
Trends Analysis
The Portable Automotive Wi-Fi Router Market is experiencing rapid expansion fueled by the manufacturing industry's pursuit of efficiency and productivity gains. Key trends include the adoption of collaborative robotics and advanced automation technologies to streamline assembly processes and reduce labor costs. With the rise of Industry 4.0 initiatives, manufacturers are investing in flexible and scalable Portable Automotive Wi-Fi Router Market capable of handling diverse product portfolios. Moreover, advancements in machine vision and AI-driven quality control are enhancing production throughput and ensuring product consistency. The emphasis on sustainability and lean manufacturing principles is driving innovation in energy-efficient and eco-friendly Portable Automotive Wi-Fi Router Market Solutions.
Regions Included in this Portable Automotive Wi-Fi Router Market Report are as follows:
North America [U.S., Canada, Mexico]
Europe [Germany, UK, France, Italy, Rest of Europe]
Asia-Pacific [China, India, Japan, South Korea, Southeast Asia, Australia, Rest of Asia Pacific]
South America [Brazil, Argentina, Rest of Latin America]
Middle East & Africa [GCC, North Africa, South Africa, Rest of the Middle East and Africa]
Significant Features that are under offering and key highlights of the reports:
- Detailed overview of the Portable Automotive Wi-Fi Router Market.
- Changing the Portable Automotive Wi-Fi Router Market dynamics of the industry.
- In-depth market segmentation by Type, Application, etc.
- Historical, current, and projected Portable Automotive Wi-Fi Router Market size in terms of volume and value.
- Recent industry trends and developments.
- Competitive landscape of the Portable Automotive Wi-Fi Router Market.
- Strategies of key players and product offerings.
- Potential and niche segments/regions exhibiting promising growth.
Frequently Asked Questions (FAQs):
► What is the current market scenario?
► What was the historical demand scenario, and forecast outlook from 2025 to 2032?
► What are the key market dynamics influencing growth in the Global Portable Automotive Wi-Fi Router Market?
► Who are the prominent players in the Global Portable Automotive Wi-Fi Router Market?
► What is the consumer perspective in the Global Portable Automotive Wi-Fi Router Market?
► What are the key demand-side and supply-side trends in the Global Portable Automotive Wi-Fi Router Market?
► What are the largest and the fastest-growing geographies?
► Which segment dominated and which segment is expected to grow fastest?
► What was the COVID-19 impact on the Global Portable Automotive Wi-Fi Router Market?
Table Of Contents:
1 Market Overview
1.1 Portable Automotive Wi-Fi Router Market Introduction
1.2 Market Analysis by Type
1.3 Market Analysis by Applications
1.4 Market Analysis by Regions
1.4.1 North America (United States, Canada and Mexico)
1.4.1.1 United States Market States and Outlook
1.4.1.2 Canada Market States and Outlook
1.4.1.3 Mexico Market States and Outlook
1.4.2 Europe (Germany, France, UK, Russia and Italy)
1.4.2.1 Germany Market States and Outlook
1.4.2.2 France Market States and Outlook
1.4.2.3 UK Market States and Outlook
1.4.2.4 Russia Market States and Outlook
1.4.2.5 Italy Market States and Outlook
1.4.3 Asia-Pacific (China, Japan, Korea, India and Southeast Asia)
1.4.3.1 China Market States and Outlook
1.4.3.2 Japan Market States and Outlook
1.4.3.3 Korea Market States and Outlook
1.4.3.4 India Market States and Outlook
1.4.3.5 Southeast Asia Market States and Outlook
1.4.4 South America, Middle East and Africa
1.4.4.1 Brazil Market States and Outlook
1.4.4.2 Egypt Market States and Outlook
1.4.4.3 Saudi Arabia Market States and Outlook
1.4.4.4 South Africa Market States and Outlook
1.5 Market Dynamics
1.5.1 Market Opportunities
1.5.2 Market Risk
1.5.3 Market Driving Force
2 Manufacturers Profiles
Continued…
About Us:
Fortune Business Insights™ delivers accurate data and innovative corporate analysis, helping organizations of all sizes make appropriate decisions. We tailor novel solutions for our clients, assisting them to address various challenges distinct to their businesses. Our aim is to empower them with holistic market intelligence, providing a granular overview of the market they are operating in.
Contact Us:
Fortune Business Insights™ Pvt. Ltd.
US:+18339092966
UK: +448085020280
APAC: +91 744 740 1245
0 notes
Text
Conductive Foam Market Expanding Applications Across Multiple Industries
The conductive foam market has seen remarkable growth due to the increasing demand for ESD (Electrostatic Discharge) protection in various sectors, especially in electronics, automotive, telecommunications, and healthcare industries. Conductive foam, a material with both insulating and conductive properties, is primarily used to safeguard sensitive electronic components from electrostatic damage, offering superior cushioning and conductivity. With technological advancements and expanding end-user applications, the demand for conductive foam is expected to continue to rise, making it a critical component in several industries.
1. Understanding Conductive Foam
Conductive foam is made from a polymer matrix that is infused with conductive materials such as carbon, graphite, or metals. This unique material combines the characteristics of both foam (for cushioning and protection) and conductivity (to dissipate electrostatic charge). The primary function of conductive foam is to protect electrostatic discharge-sensitive devices such as semiconductors, circuit boards, and display screens from damage during manufacturing, storage, and transport.
There are two primary types of conductive foams: electrically conductive foam and static dissipative foam. The former is primarily used in industries where high conductivity is necessary, while the latter is designed to reduce and control static electricity, offering a lower level of conductivity suitable for more sensitive electronic components.
2. Key Drivers of Demand
Several key factors are driving the demand for conductive foam across multiple industries:
Rising Electronics Production: The global electronics market has been expanding rapidly, with consumer electronics, including smartphones, laptops, tablets, and wearables, leading the growth. These products are increasingly incorporating miniaturized components that are highly sensitive to electrostatic discharge, driving the need for protective materials like conductive foam. With a steady rise in the number of electronic devices being manufactured, the demand for conductive foam remains strong.
Growing Semiconductor Industry: Semiconductors are fundamental components of modern electronics. As the semiconductor industry grows, with innovations in processing power, memory, and connectivity, the demand for effective ESD protection is becoming more crucial. Conductive foam is increasingly used in semiconductor packaging and during transportation to prevent electrostatic discharge that could potentially damage or destroy microchips.
Automotive Electronics: Modern vehicles are equipped with a variety of electronic systems, from infotainment units to advanced driver assistance systems (ADAS) and electric vehicle (EV) technologies. As automotive electronics continue to advance, the need for protective solutions like conductive foam has increased. This is especially true in the case of electric vehicles, where battery management systems, electric circuits, and sensors must be protected from ESD during production and assembly.
Telecommunications and 5G Technology: The global rollout of 5G networks and increasing demand for telecom equipment has created new opportunities for conductive foam. Telecom equipment, including base stations, routers, and other communication devices, often contains highly sensitive electronic components that require protection from electrostatic discharge. With the rapid expansion of 5G infrastructure, the demand for conductive foam for packaging, transport, and protection applications is also increasing.
Healthcare Devices: The healthcare industry, especially in the field of medical devices and diagnostics, relies heavily on electronic systems that need to function without disruption. Conductive foam is used to protect electronic components in medical devices, such as MRI machines, ultrasound equipment, and patient monitoring systems. As the medical industry continues to innovate and incorporate advanced technologies, the need for conductive foam solutions is expected to grow.

3. Emerging Applications and Demand Growth
While traditional uses of conductive foam in ESD protection continue to dominate the market, new applications are emerging that further bolster demand. The integration of conductive foam with 3D printing is one such example. 3D printed electronics and conductive inks are growing rapidly, and conductive foam plays an important role in the production, packaging, and protection of these components during and after manufacturing.
Additionally, the sustainability trend is pushing the demand for more eco-friendly conductive foams. Manufacturers are working towards developing conductive foams made from biodegradable or recyclable materials to meet the growing demand for green products across industries.
4. Regional Demand for Conductive Foam
North America: North America is one of the largest markets for conductive foam, primarily driven by the strong electronics, automotive, and telecommunications industries in the United States and Canada. The region has a well-established semiconductor manufacturing industry, which is a major contributor to the demand for conductive foam. Additionally, advancements in automotive electronics and electric vehicles continue to drive market growth in North America.
Asia-Pacific: The Asia-Pacific region is experiencing the highest growth in the conductive foam market. Countries like China, Japan, South Korea, and India are major players in the electronics and semiconductor industries, making the region a dominant market for conductive foam. China, in particular, is both a large producer and consumer of electronics, making it a key market for ESD protection solutions like conductive foam. Moreover, the rise of electric vehicles and the push for 5G infrastructure in Asia-Pacific is further contributing to the demand.
Europe: Europe has seen steady growth in the conductive foam market, particularly driven by the automotive and telecommunications sectors. Countries like Germany and the United Kingdom, with strong automotive manufacturing industries, are significant consumers of conductive foam for use in vehicle electronics. Furthermore, Europe’s emphasis on sustainable development and green technologies is pushing manufacturers to focus on producing eco-friendly conductive foam.
5. Challenges in the Conductive Foam Market
Despite the positive growth trends, the conductive foam market faces several challenges:
High Production Costs: The production of high-quality conductive foam materials can be expensive, especially when using advanced conductive materials or striving for eco-friendly alternatives. The cost factor can make it difficult for manufacturers, especially in price-sensitive industries, to adopt conductive foam on a wide scale.
Competition from Alternative Materials: Conductive films, bags, and mats are gaining traction as alternative ESD protection solutions. These materials often offer cost advantages over conductive foam and can be more versatile, especially for packaging and transportation.
Material Innovations and Sustainability: As sustainability becomes a major focus across industries, there is an increasing push for more eco-friendly conductive foam solutions. Developing recyclable or biodegradable conductive foam without compromising its performance remains a challenge for manufacturers.
6. Market Outlook
The future of the conductive foam market looks promising, with strong growth expected due to the increasing demand from the electronics, automotive, telecommunications, and healthcare sectors. Innovations in material science, such as the development of eco-friendly conductive foam, as well as the increasing adoption of conductive foam in new applications, will likely drive further demand. Additionally, the ongoing growth of industries like electric vehicles, semiconductors, and telecommunications infrastructure presents lucrative opportunities for market expansion.
Conclusion
In conclusion, the demand for conductive foam is expected to continue expanding across various industries, driven by the need for effective ESD protection and the growing reliance on electronics and advanced technologies. As manufacturers address challenges such as cost and sustainability, conductive foam is poised to remain a crucial component in ensuring the protection and functionality of sensitive electronic components.
0 notes
Text
How to Install WiFi in a Car and What are its Steps?

In our modern connected world, WiFi in your car makes travelling much more enjoyable, as passengers can amuse themselves, do some work, or use navigation apps. WiFi in a vehicle may seem tricky to install, but it is easier than one may think. You can turn a car into a mobile hot spot with the right equipment. In this article, we will take you through setting up WiFi in your car. From choosing the right device to installation, we'll cover everything you need to know about staying connected on the go. Let's bring WiFi to your car.
Why to Install WiFi in Your Car?
Installing Wi-Fi in your car can significantly enhance your driving experience. It enables you and your passengers to stay connected while you enjoy long trips or run errands. Here are some reasons why it's worth considering: - Constant Connectivity: With WiFi in your car, you can always stay connected to the internet. This allows seamless communication, downloading, accessing essential apps, or replying to emails immediately. - Entertainment on the Go: WiFi makes streaming favourite movies, shows, or music easier. Passengers can enjoy gaming, browsing, or unwinding with videos while travelling. It ensures delightful travels for everyone in the vehicle. - Work Flexibility: Travelling doesn't have to mean losing productivity. WiFi allows you to attend video calls, check emails, or work on documents while commuting. It's perfect for professionals who need to stay connected even while on the road. - Improve Navigation: WiFi embeds many advantages that it brings to navigation, such as real-time traffic updates, weather reports, and accurate maps. This helps you avoid roadblocks and construction zones and gives you alternate routes.
How to Set Up WiFi in a Car?
Setting up WiFi in your car is more straightforward than one thinks. Depending on what a person wants or needs, there are several ways to get one's vehicle online. Here are the top methods: 📶Using a Mobile Hotspot Device The easiest way to get an internet connection inside a car is to use a smartphone or tablet for a mobile hotspot, which can provide stable connectivity by activating the 4G or 5G connection. This alternative is quite convenient since most of us carry our smartphones everywhere. However, there is a potential for draining battery life and running into data caps. 📱Hotspot Devices If you experience weak internet connectivity inside your car, a small router or mobile hotspot device could provide a solution. These mobile hotspot devices offer portability and better connectivity than those on smartphones or tablets. The battery lives in coordination with these hotspot devices for longer. However, you'd have to buy a dedicated plan for the service. 🚗Inbuilt Car WiFi Many modern cars have built-in integrated systems. This makes it easy to establish an internet connection inside a car. These routers have very strong signals and fast speeds. They can also be used to send diagnostic reports as well as to upload over-the-air updates for the car. 📡Wireless Routers Offering a more robust option than some of the above types, wireless routers for cars cover longer ranges at faster speeds. A viable option for downloading and uploading large files or live streaming. Like mobile hotspots, routers require their own data plan or subscription, which are generally more expensive. OBD-II Devices While OBD (On-Board Diagnostics) ports perform vehicle diagnostics, they can be connected to enhance Wi-Fi connectivity and provide high-speed internet. These devices are more mobile than built-in routers but are not as portable as smartphones or tablets. OBD-II devices are generally much more expensive than mobile hotspots.
Things to Consider When Installing In-Car WiFi
When adding WiFi to your vehicle, you should consider various factors for the best experience. Those include: 🌐 Connectivity Options: When choosing a WiFi solution, it is worth checking up on a stable one. Find a Wi-Fi solution that has a reputation for reliability. While hotspots and routers depend on cellular networks, high coverage is crucial. 💰 Installation Cost: This is a matter of personal choice. Portable mobile hotspot devices or smartphone hotspots would perhaps be the least expensive. On the other hand, installing built-in permanent routers at a higher cost should be expected. 🔋 Power Consumption: WiFi devices consume tremendous battery power from cars, so be sure to opt for solutions designed with minimal energy consumption in mind. Some mobile hotspots can be powered via your car's USB port. 📊 Ensuring Data Plans: Ensure you pick a data plan that fits your usage. Some hotspot devices and car systems need additional data plans. Assess your data needs based on how often you use the Wi-Fi in the car. 📡 Network Compatibility: Ensure the Wi-Fi device or system you buy will be compatible with the network bands you travel to for coverage. There are instances where some devices can operate on particular networks.
Maintenance Tips for In-Car WiFi
Regular maintenance will keep your car's Wi-Fi running smoothly. Here are some tips for long-lasting, efficient performance: 🛠️ Regular Software Updates: Always update the mobile hotspot or in-car Wi-Fi router regularly. It provides better connections and has enhanced security features, eventually increasing long-term performance. 📶 Check Signal Strength: One should always check signal strength upon noticing reduced speed or connectivity. It could mean a network change or optimal placement of the mobile hotspot to ensure complete coverage and good connection. 🧹 Keep Devices Clean: Over time, dust and dirt settle down on Wi-Fi devices, causing these devices to malfunction. Regular cleaning can prevent build-up that can affect performance. Also, make sure to keep the car charger ports free from debris. 📊 Monitor Data Usage: Knowing how much data you have been using helps ensure you do not exceed the limits of your plan. Most mobile hotspots will let you monitor your usage through an app. Monitoring allows you to control the data you use. 🔒 Lock Your Network: Change the password for Wi-Fi and encrypt it so it is not available for others to log onto your network. This sets up a powerful connection that cannot be compromised easily by unwanted data thefts.
Is It Worth Installing a WiFi in a Car?
Installing Wi-Fi in a car can be beneficial, but it's always better to weigh the pros and cons of it. It's an excellent convenience for long travels since streaming or blazing through social media will keep the passengers entertained. If you are someone who works on the way to your destination, Wi-Fi in the car will keep you connected and productive. Even kids will have access to their online educational apps while on a trip. However, maintaining Wi-Fi will be a continuing cost. You will have to pay for data plans besides the upkeep of devices. Additionally, the connection quality will vary from place to place based on signal strength. Hence, before you make a decision, consider your needs and budget. Having WiFi in your car is a game-changer. With it, you'll have permanent internet access no matter where you go. On top of that, in-car WiFi brings you safety via emergency services and ensures you are always connected with your loved ones on social media and video calls. Each trip is worthwhile with the convenience and benefits of in-car WiFi.
FAQs about Installing WiFi in a Car
What are the different ways to get WiFi in a car? A car can have WiFi with a mobile device, a phone with a hotspot facility enabled, and built-in systems with WiFi functionality in a vehicle. Can I use my smartphone as a mobile hotspot for in-car WiFi? Yes, you can use it. When you use your cell phone to share a data connection, you can enjoy seamless Wifi in the car. How much does it cost to install WiFi in a car? The installation costs may vary, depending on the range. Mobile hotspot devices begin at around ₹400 - ₹3000. Built-in systems or permanent routers can cost hundreds, including installation fees. What is the most reliable way to set up WiFi in a vehicle? The best option is to use a mobile dedicated WiFi router for the car or a WiFi system on board if your vehicle has one. Both provide reliable connections. Are OBD-II WiFi devices a good option for car internet? WiFi OBD II is built for diagnostics. However, they can also provide internet access in your car. How many devices can be connected with in-car WiFi at one time? This depends on the device. Most hotspots can support up to 10 devices, while the more expensive mobile routers can handle more. Can a permanent WiFi router be installed in a car? Yes, installing a permanent WiFi router in your car can provide a stable and long-term internet solution. How secure is in-car WiFi for online activities? In-car WiFi can be secure if WPA2 encryption and a strong password are used. It's essential to monitor connected devices to avoid potential threats. Do modern cars come with built-in WiFi systems? Many newer cars have built-in WiFi, often requiring a subscription to a mobile data plan. Check your vehicle's features to see if it includes this option. What factors should I consider when choosing a WiFi solution for my car? Consider connectivity options, cost, power consumption, data plans, and specific usage needs when selecting a WiFi solution for your car. How do I activate WiFi in my car? To activate WiFi in your car, either turn on the built-in WiFi feature through your car's settings, connect a mobile hotspot device, or enable the hotspot on your smartphone. Can I use in-car WiFi while driving? Yes, in-car WiFi can be used while driving. However, ensuring that your devices don't distract the driver or interfere with safe driving practices is essential. What is the range of in-car WiFi? The range of in-car WiFi depends on the type of device. A mobile hotspot typically has a range of 30-50 feet, allowing passengers in the car to connect to the internet. Will using WiFi in a car affect my phone's battery? Yes, using WiFi in your car can drain your phone's battery, mainly if you use it as a hotspot. Consider keeping your phone plugged in or using a separate device to provide WiFi. Can I install WiFi in an older car? Yes, you can install WiFi in older cars using mobile hotspot devices, dedicated routers, or aftermarket solutions to provide internet connectivity. Read the full article
1 note
·
View note
Text
Multilayer Pcb Market set to hit $171.7 billion by 2035, as per recent research by DataString Consulting

Higher trends within Multilayer Pcb applications including consumer electronics, telecommunications, automotive and healthcare; and other key wide areas like consumer electronics and telecommunications are expected to push the market to $171.7 billion by 2035 from $87.3 billion of 2023.
Multilayer circuit boards play a role in smartphones, laptops and smart home gadgets as they provide dense connections and reliable performance. Leading companies such, as Apple and Samsung depend heavily on multilayer circuit boards for their top of the line products. In the field of telecommunications infrastructure Multilayer PCBs play a role in enhancing the performance and speed of 5th generation networks as well as data centers and routers. Leading companies like Huawei and Cisco employ multilayer configurations to advance their communication systems, for the future.
Detailed Analysis - https://datastringconsulting.com/industry-analysis/multilayer-pcb-market-research-report
Multilayer designs are being transformed by incorporating both active components into PCB layers. This advancement is driving miniaturization possibilities.
Industry Leadership and Strategies
The Multilayer Pcb market within top 3 demand hubs including U.S., China and Japan, is characterized by intense competition, with a number of leading players such as Apple, Samsung, DuPont, Panasonic, Huawei, Cisco, Tesla, Bosch, Siemens, GE Healthcare, Molex and Fujitsu. Below table summarize the strategies employed by these players within the eco-system.
Leading Providers Provider Strategies Apple, Samsung High-performance PCBs for compact devices Huawei, Cisco Advanced PCBs for 5G infrastructure Tesla, Bosch Reliable PCBs for EVs and ADAS GE Healthcare Precision PCBs for diagnostic and wearable devices
This market is expected to expand substantially between 2024 and 2030, supported by market drivers such as advancements in 5g technology, miniaturization of devices, and rise of electric vehicles (evs).
Regional Analysis
North America dominates the Multilayer PCB industry, thanks to research and development in consumer electronics and telecommunications fields along with the healthcare sector being involved as well with companies such as Apple and Cisco, at the forefront of pushing for new ideas and technology integration.
Research Study analyse the global Multilayer Pcb market in detail and covers industry insights & opportunities at Type (4-6 Layers, 8-10 Layers, 10+ Layers), Application (Consumer Electronics, Automotive, Telecommunications, Healthcare) and End User (Electronics Manufacturers, Automotive OEMs, Telecom Operators, Medical Device Companies) for more than 20 countries.
About DataString Consulting
DataString Consulting assist companies in strategy formulations & roadmap creation including TAM expansion, revenue diversification strategies and venturing into new markets; by offering in depth insights into developing trends and competitor landscapes as well as customer demographics. Our customized & direct strategies, filters industry noises into new opportunities; and reduces the effective connect time between products and its market niche.
DataString Consulting offers complete range of market research and business intelligence solutions for both B2C and B2B markets all under one roof. DataString’s leadership team has more than 30 years of combined experience in Market & business research and strategy advisory across the world. Our Industry experts and data aggregators continuously track & monitor high growth segments within more than 15 industries and 60 sub-industries.
0 notes
Text
Optimizing Wireless Network Performance: The Importance of Channel Selection

In wireless communication, a "channel" refers to a specific subdivision within a frequency band that serves as a dedicated pathway for wireless signals. Think of it like a lane on a highway, where each lane accommodates different vehicles (or signals) to ensure smooth traffic flow.
Wireless communication channels are essential for reducing interference between signals from various devices. For example, Wi-Fi routers typically operate within the 2.4 GHz frequency band, which is divided into 14 channels. However, only a few of these channels (such as 1, 6, and 11) are non-overlapping and can be used simultaneously without interference.
The 5 GHz frequency band, in contrast, offers more channels and is less prone to congestion, making it suitable for higher bandwidth applications that require faster data transfer and more reliable connections. However, the 5 GHz band has a shorter range compared to the 2.4 GHz band, so it may not be ideal for areas with thick walls or physical barriers that could block the signal.
Selecting the right channel is crucial for optimal network performance, especially in environments with multiple wireless networks. If too many devices use the same channel, network speed can decrease due to congestion. To mitigate this, users can utilize tools that analyze the wireless environment and help identify the least crowded channels.
In addition to channel selection, factors such as signal strength, interference from other devices, and the physical layout of the space can influence wireless communication performance. Thus, it’s important to account for these elements when designing and optimizing a network.
In summary, understanding the role and significance of wireless communication channels is essential for ensuring reliable and high-performance networks. By selecting the appropriate channel and considering other environmental factors, users can create more efficient and stable wireless connections.
0 notes
Text
The Evolution of RV Trailers Over the Past 5 Years in the U.S. and Europe
In recent years, recreational vehicles (RVs) and travel trailers have seen remarkable growth and transformation, both in the United States and across Europe. Factors such as increasing consumer demand for outdoor experiences, shifting traveler preferences, and advancing technology have all contributed to the evolution of this vibrant industry. Below is an overview of key trends and developments observed over the last five years.

1. Rising Popularity and Demand
United States
Surge in Domestic Tourism: The U.S. has long been a major market for RVs, but over the past half-decade, there has been a significant increase in first-time RV buyers. Partly fueled by a desire for safer, more flexible travel options—especially after global disruptions in travel—families and retirees have turned to RVs as a way to explore national parks and scenic byways.
Younger Demographics: Previously, the RV market was most associated with retirees seeking a leisurely cross-country lifestyle. Recently, however, Millennials and even Gen Z travelers have embraced the convenience and freedom of RV travel, attracted by remote work possibilities and the growing trend of “van life” or minimalistic living.
Europe
Expanding Market and Higher Demand: Although the market in Europe has historically been smaller than in the U.S., many Europeans now see travel trailers as an affordable and flexible alternative to traditional travel. Campgrounds and road-trip destinations have become increasingly popular from the Mediterranean coasts to the Scandinavian fjords.
Rise of Camper Vans and Compact Models: Due to narrower roads and denser city layouts, European consumers often favor smaller, more maneuverable camper vans and compact travel trailers. This trend has sparked innovation among European RV manufacturers, resulting in lightweight, space-efficient designs that appeal to a wider audience.
2. Technological Advancements and Innovations
Smart Systems and Connectivity
Wi-Fi and Mobile Integration: Modern RVs often come equipped with built-in Wi-Fi routers and advanced mobile connectivity, making it easier for travelers to work remotely or stay connected while on the road.
Smart Control Panels: Many new models feature integrated control panels that allow users to monitor energy consumption, water levels, and temperature settings, all from a smartphone or tablet. This technology enhances convenience and efficiency, appealing to a younger, tech-savvy market.
Sustainable Materials and Eco-Friendly Designs

Solar Power and Energy Efficiency: Solar panels have become more common on RV rooftops in the U.S. and Europe, reducing reliance on traditional fuel-powered generators. Advances in battery technology also allow RV owners to operate off-grid for longer periods.
Lightweight Construction: To cut down on fuel consumption, manufacturers are adopting lightweight composite materials, ensuring better aerodynamics and improved handling. This focus on eco-conscious designs caters to increasingly environmentally aware consumers on both continents.
3. Shifts in Lifestyle and Use Cases
Work-from-Anywhere Culture
Remote Work Opportunities: As remote work has become more widespread, many professionals are capitalizing on the ability to work from anywhere with a stable internet connection. RV living has thus become a lifestyle choice, allowing people to merge their career with travel and personal freedom.
Digital Nomad Communities: New online communities and social media groups have formed, enabling RV owners to connect and share experiences about road trips, workspaces, and best practices for remote living.
Family and Multi-Generational Travel
Enhanced Amenities: Modern RVs offer amenities like larger refrigerators, microwaves, air conditioning, heating systems, and even washers/dryers in some high-end models. These comforts have broadened their appeal to families and older adults looking to maintain a standard of living while on the move.
Growing Rental Market: The rise of peer-to-peer rental platforms has made it easier for families to test out different RV types without a large upfront investment. This rental model has increased overall awareness and acceptance of the RV lifestyle in both the U.S. and Europe.
4. Market Growth and Economic Impact
U.S. Market Expansion
Record Sales: The last five years have seen record-breaking RV sales in the U.S., with industry reports indicating continuous year-over-year growth. Even pre-owned RVs have become more valuable, reflecting strong consumer demand.
Boost to Local Economies: States and small towns along popular road-trip routes have benefitted from increased tourism spending. Campgrounds, gas stations, and local attractions have all seen an uptick in visitors, contributing to local economic vitality.
European Growth and Infrastructure
Improved Campground Facilities: To accommodate increased travel trailer use, many European countries have invested in upgrading campsites with modern facilities—high-speed Wi-Fi, electric hook-ups, and sanitary stations—all of which have contributed to a more comfortable experience for travelers.
New Manufacturing Hubs: Regions like Germany, France, and the UK have seen a boost in RV manufacturing, from artisanal camper conversions to large-scale production lines. This has led to job creation and new opportunities within the European RV supply chain.
5. Future Outlook
Continued Innovation: Technology will likely continue to drive the RV industry forward, including the potential integration of electric tow vehicles and further improvements in solar and battery systems.
Sustainability Focus: With environmental concerns on the rise, manufacturers in both the U.S. and Europe are exploring ways to reduce the ecological footprint of RV travel, from greener materials to more efficient engine designs.
Growth in Rental and Sharing Models: The popularity of camper-sharing platforms is expected to grow, making RV travel more accessible and attractive to new audiences who might not want to purchase a unit outright.
Conclusion
Over the past five years, RV trailers and travel vehicles have seen remarkable development in both the United States and Europe. Advancements in technology, an ever-expanding demographic of travelers, and evolving lifestyles have contributed to a robust market that shows no sign of slowing down. As manufacturers invest in innovative designs and eco-friendly solutions, and as more travelers embrace the freedom and flexibility of life on the road, it’s clear that the RV sector will remain a defining force in the global travel industry for years to come.
1 note
·
View note
Text
9410Khz 0457 26 DEC 2024 - BBC (UNITED KINGDOM) in ENGLISH from ASCENSION ISLAND. SINPO = 45135. English, s/on unmodulated carrier until 0458z Bowbells int. fb ID, pips and Newsday preview. @0501z World News anchored by Neil Nunes. § Syria's new rebel-led authorities say 14 interior ministry personnel have been killed and 10 injured in an "ambush" by forces loyal to ousted President Bashar al-Assad in the west of the country. They say the fighting took place near the Mediterranean port of Tartous on Tuesday. Reports say the security forces were ambushed as they tried to arrest a former officer in connection to his role at the notorious Saydnaya prison, close to the capital Damascus. Just over two weeks ago, Assad's presidency fell to rebel forces led by the Islamist Hayat Tahrir al-Sham (HTS) faction. § Japan Airlines said on Thursday it was hit by a cyberattack that caused delays to some domestic and international flights. The attack began at 7:24 a.m. (2224 GMT) and affected the company's internal and external systems, JAL said. The company said it temporarily shut down a router that was causing system malfunctions and also suspended ticket sales for flights departing on Thursday. § Tearful mourners prayed Thursday as ceremonies began across Asia to remember the 220,000 people who died two decades ago when a tsunami hit coastlines around the Indian Ocean, in one of the world's worst natural disasters. On December 26, 2004, a 9.1-magnitude earthquake off Indonesia's western tip generated a series of massive waves that pummelled the coastline of 14 countries from Indonesia to Somalia. § A prison riot in Mozambique's capital Maputo left 33 people dead and 15 injured, the country's police general commander Bernardino Rafael said on Wednesday. About 1,534 people escaped from the prison but 150 of them have now been recaptured, he said. The prison break comes a day after at least 21 people were killed in unrest that erupted when Mozambique's top court on Monday confirmed the victory of the long-ruling Frelimo party's presidential candidate, Daniel Chapo, in disputed October elections. § Five journalists have been killed in an Israeli strike overnight when their parked vehicle was blasted in front of a hospital in Gaza, their Palestinian news outlet said on social media. There has been no immediate comment from the Israeli government. It had previously said, however, that it would not deliberately attack journalists but that members of "an organized armed group" would be targets. § President Biden on Wednesday denounced Russia’s latest attack on Ukraine, declaring the wave of missiles and drones “outrageous.” Russia, in the early hours of Wednesday, launched an attack on Ukraine’s energy supplies and infrastructure using 78 air and ground missiles and 106 Shahed drones, Ukraine’s air force said. The strikes damaged equipment and caused power outages. @0506z “Newsday” begins. 100’ (30m) of Kev-Flex wire feeding “Magic Wand” antenna hanging in backyard tree w/MFJ-1020C activeb antenna (used as a preamplifier/preselector), JRC NRD-535D, 125kW, beamAz 27°, bearing 103°. Received at Plymouth, MN, United States, 9763KM from transmitter at Ascension Island. Local time: 2257.
0 notes
Text
Multi-function Solutions (MFS) / ISE (Integrated Solutions Engineered) - Techni3

The signature of today’s advanced technology – whether it’s autonomous vehicles, 5G-enabled devices, sensors creating an internet of things, or home routers – is high-speed, high-volume data transfer in increasingly dense packages. It poses new and unprecedented signal interference and heat dissipation challenges for design engineers worldwide.
New products operate at higher frequencies and use more powerful ICs/SOCs to facilitate enhanced data transfer and capabilities. Therefore, these electronics generate an even higher potential for a significant amount of electromagnetic signal interference. But EMI is only one part of the problem. More components make electronics more powerful, but also hotter, thus increasing the need for fast, reliable heat dissipation. Don’t forget about increasing needs for mechanical and environmental durability, space constraints, and lightweight designs. Enclosures are not just simple, aesthetic housing. They are functional, essential parts helping to address EMI and thermal challenges while protecting devices and systems from potentially harsh environments.
Design engineers face a quandary: How do I effectively solve both signal interference and heat dissipation challenges in tight (and shrinking) spaces?
Laird´s new Integrated Solutions portfolio addresses these multifaceted challenges with a unique range of multifunctional products and solutions – from electrically conductive fabrics to board level shield covers with thermal transfer capabilities. Combining our decades-long wealth of expertise in EMI products, precision metals, RF absorber and thermal solutions – with the latest material and manufacturing innovations – sparked a new way of thinking and has resulted in a plethora of value-add solutions. Significantly reducing your total cost of ownership and maintaining premium performance while lowering design iteration efforts is Laird´s driver for ISE (your Integrated Solutions Engineered).
Laird ISE is your one-stop-shop: from simulations/modeling to co-engineering, co-designing and high-quality manufacturing. Challenge us to trust us.
Explore Solutions:
Metal-ISE:
Thermally and electro-magnetically enhanced die-cast, stamped, deep-drawn precision metal parts at board level (e.g. board level shields and RF absorbers) or subassembly level (e.g. automotive heatsinks).
Structur-ISE:
Highly durable mechanically stable solutions at enclosure and I/O interface level (e.g. radomes, using state-of-the-art injection molding or forming capabilities).
Hybrid-ISE:
Homogeneous single layer or heterogeneous multi-layer polymeric solutions offering multi-functional signal interference mitigation and heat dissipation (e.g. a thermally conductive RF absorber).
Textil-ISE:
Electrically conductive fabrics enabling sensor, switch, and heating functionality (e.g. selectively plated stretch fabric).
Multi-function Solutions (MFS) / ISE (Integrated Solutions Engineered) Groups
Hybrid - ISE
Merge Device Functionality. Laird Hybrid-ISE solutions merge thermal, EMI shielding, and microwave absorbers into a single engineered package. You have more heat, higher frequencies and ever-smaller packages. Hybrid-ISE delivers answers.
Structur - ISE
Improve performance with smart components. Device enclosures can offer more than just physical and environmental protection. Sensors and antennas need smart structural materials to keep out unwanted signal interference. Discover Structur-ISE.
Metal - ISE
Enable enhanced functionality. Metal-ISE solutions utilize Laird’s automation capabilities to enhance precision metal components with our portfolio of thermal and EMI materials. Get complete thermal and EMI solutions from one global manufacturer.
Textil - ISE
Finding solutions in smart fabrics. Textil-ISE uses selectively-plated flexible conductive fabric (stretchable and non-stretchable) to create assemblies providing more than just a conductive path. Textil-ISE provides a host of compelling solutions.
0 notes