#same smtp
Explore tagged Tumblr posts
Text
why's it so hard to set up a custom minecraft server...
#like cmon I have a public facing server already#I know it works since the logs dont show any errors#and like ive tried running the exact same hardware+software setup on my local network#but like unfortunately the public facing server only has IPv6#and I cant connect cause my ISP only issues IPv4#and the other people I want to play with probably only have v4 as well#I guess the hosting provider I have technically has a v4->v6 proxy to allow ppl with v4 only to connect to their servers#but it only passes through http imap and smtp traffic#so its pretty much useless for what I want to do#and like so far finding a proxy service that actually does what i want it to do seems impossible#like PLEASE I WANNA PLAY MINECRAFT WITH SOMEONE ELSE#I DONT WANNA SPEND TIME TRYING TO FIGURE OUT HOW TO GET THE SERVER RUNNING
3 notes
·
View notes
Text
Another Internet Whitepaper
I'm just gonna get into there is no way to preface this.
1) content should be hosted in their own countries for which they are meant.
2) therefore the website should split into Nation->Sub-nation sections. So things for Michigan would be closer to those in Michigan. With U.S.->Michigan.
--"independent" Nations are just gonna have to deal with being lumped together into a united region. It's simply physics.
--country wide servers and clouds, and worldwide services will still be available; but we need to develop protocols to make it easier to distribute data and declutter the internet-cloud.
3) a separate Intranet for official use and security will need to be developed alongside this while also being completely disconnected from the worldwideweb.
4) Splits;
IP Addresses redesign;
[Country/Region]:[State/Province]:[individual]
[Individual] will need to be controlled by local The Internet Assigned Numbers Authority (IANA) branches; likely to be reassigned to DMVs and SoSs.
5) Separate protocols For;
Streaming Services
Social Media Services
Bidirectional Interactions (like games and Virtual Machines)
Pornography needs to be completely identifiable by textual Web address.
5) you local region will be defaulted, but can be changed by the browser and not be hard-wired in.
Not indicating a region will automatically default to the local internet.
So typing in FBI.GOV in the U.S. will lead to the FBI website, and if you type it in the UK it'll lead to Mi:5 or something.
6) Social Media protocols will have to be integrated with the E-Mail SMTP protocols. Which will encourage a more decentralized internet. This will *also* have to find a way to work with phone text messages.
7) Cable TV and Streaming services will have to use the same protocols.
8) Because there's phone integration here; a phone number may have to be closer to a social security number going forward. Which will both be bad for animosity, but allow for people to not need login information.
-- This will technically also need to apply to your House; which will have to have an assigned street address.
9) all of these need to be obfuscated to casual observers.
10) this will deprecate our phone companies and require them to work with cable TV and internet companies in order to create more equitable protocols.
11) the current IP address and Domain Registry systems need to be deprecated; as it does not suit its original purpose.
[.xxx] will be assigned for all "adult" materials and be required for ALL "adult materials" posted online.
[.app] will be assigned for appstores.
[.store] for marketplaces like Amazon, eBay, and whatever else.
[.bank] will be for banking and credit purposes
[.social] will be for social media
[.stream] will be for streaming materials,
[.np] for non-profit use only.
[.donation] for donation collections and Kickstarter like services.
[.pay] for payment services like PayPal
Non "adult materials" can be streamed through other "front ends" .
13) These human readable extensions will be simplified on the backend to reduce the total data envelope size.
14) single digit ip-adresses will have to be regulated for use for high-capacity uses. These will need to be "extended" protocols that different services can use.
This will help even out everybody's data envelopes. This will have to be part of a cloud service that can be used by anybody that needs it. With certain restrictions that are deemed necessary by local and federal governments and international treaty reasons.
15) limits on how algorithms and "bots" can ping anything at one time need to be addressed or regulated.
This will be a massive undertaking with the cooperation of all the other governments around the world.
And will be a very lucrative endeavor at the end of it all.
This is just an outline to describe the form the future internet should take and can be changed or modified as required; especially for things I cannot see.
The current corporations will be expected to develop a plan of actions in tandem with current regulatory authorities; failure to do so will create a need for an ultimatum, which we all wish to avoid.
We're also going to need to find ways to encourage competition in these sectors so that they can be upgraded and modified as needed by local areas instead of waiting on these companies to bother with it.
13 notes
·
View notes
Text
observations on the future of social media in regards to P2P and Blockchains and decentralized protocols in general ie nostr/iris, bluesky etc, what it means in Threads, Tumblr and Twitter/X's case and what it means to us as users
prefacing this with I'm just a person with access to google and a hefty amount of curiosity and a layman's understanding of the subjects so I will most likely be wrong about a couple things but I just wanted to write this to get a discussion going in a public space about what these social medias mean for the future of the internet and what I think their goals are and also to just get my thoughts in order
P2P in the simplest of terms is how torrenting works, it is peer 2 peer sharing of information ie computer 2 computer, so for example if you download something sent to you by a person from google drive its person > google servers > you, however if you torrent somethings its person > you (well in actuality its Multiple people> you and that's what seeding is but I am keeping it simple for my own sake) So in my quest to find a way to p2p stream things directly from a computer to another computer not on the same network on github, I've found that a huge amount of research has been done in general on P2P implementation beyond just media sharing in the last couple of years
and subsequently I fell down a rabbit hole of P2P social media, so what that means is imagine a social media without a middle man or a direct company. Twitter right now works as such, person tweets > passes through twitter servers > you access their tweet as shown to you through the twitter servers this mode of information sharing requires physical servers to store this data on, most companies don't own their own servers but instead rent them, usually from amazon or google, and twitter is the same, in fact almost everything on the internet is hosted through amazon servers and they have intense monopoly worldwide (x) (x)
this is partially how countries can exert their laws on these social media companies
P2P makes all of this obsolete, reduces the overhead cost of servers and takes them out of the equation, the sharing of information will be pingponged through multiple computers instead of passed through one large middle man that can be prosecuted and contacted for hosting/platforming this data. personally I am very excited about the development of P2P technology however, this form of decentralized social media isn't new people have been experimenting with it since 2012 and the early internet ran on p2p (IRC), but the biggest difference now is that people have combined it with blockchains (bitcoin) (W3C ie Web.3 consortium pretentious name I know) and this brings me to the current Big Fish battle that is happening right now between IRIS(NOSTR)/Blusky and Threads, Twitter
So starting with IRIS, most people have probably not heard of IRIS but what IRIS is, is a p2p social media running on a protocol called NOSTR, ELI5 protocols are just Ways of doing things/sharing information/guidelines, ie emails are just a protocol called SMTP (simple mail transfer protocol) that companies can build things around ex: gmail, runs on SMTP protocol I stumbled on the ex CEO of twitter Jack Dorsey on IRIS and a couple things struck me first scrolling through the site and his account. first even though Jack Dorsey is on the board of directors for bluesky and helped in its development he more so wants NOSTR protocol and IRIS to succeed and seems to be pushing them more heavily even on his twitter secondly the little dollar amount tied to every post he makes,
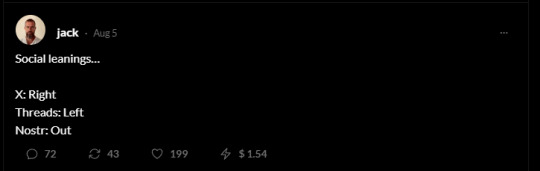
this literary banger is apparently worth a dollar and a half in "Zap Coins" this leads me to speculate on the future of bluesky because to me it seems like IRIS is being used as a testing ground for bluesky, bluesky currently DOESNT have bitcoin tied to its posts like nostr does but it does have the groundworks laid in in its protocol! I offhandedly mentioned previously that social medias are combining P2P and blockchain this time around and thats exactly what is happening in IRIS and what bluesky seems to be working towards, now what does this mean in IRIS's case? well from my understanding is that creating accounts on IRIS is exactly like creating a crypto wallet, in that your account will have its own unique generated hash encrypted number and every post you make is like making a transaction in the blockchain ie it has its own hash attached to it hence every post you make has a monetary value pros > makes you hard to find, posts are decentralized and spread over multiple computers worldwide and encrypted >can make as many accounts as you want no need for verification you just need to remember the unique hash attached to them >no servers hosting your information governments and companies have less control cons (to me anyways lol) >monetized posts >the power balance gets shifted from companies and goverments to ISP's and their abilities to connect you to other computers worldwide >nothing can ever actually be deleted its all recorded, you can orphan posts from your account I think? but they will still be findable
what does this mean in Blue sky's case?
Well starting with the differences, Bluesky is NOT p2p it is running on its own self made "decentralized" protocol called ATP (@ protocol) it is very theoretical and doesn't have any actual implementation anywhere as opposed to NOSTR and other protocols that twitter and tumblr run on I read through it and looked up some things but I genuinely don't understand how its supposed to be decentralized especially with how it seems to be implemented in actuality, so currently bluesky has frequent outages and is slow to use, if it were decentralized these things shouldn't be affecting everyone? so from my understanding it says that everyone has their own server PDS (personal direct server) that will host their posts and that it all PDS will be connected via a crawler which will siphon that information to an app, which I GUESS is decentralized but what does PDS mean in this case? signing up to bluesky is most definitely not hosting your own server with your own posts, you are putting these posts on a server somewhere, but who is it owned by? I read some articles saying that bluesky is starting out by hosting their own servers for you in that case they've just invented twitter 2 but with more flexibility in regards to third party implementation anyways rant aside, the similarities, while iris isnt the same as bluesky, bluesky's philosophy seems to be in a similar vain to iris and blue sky is following iris' steps closely, while iris isn't owned by one single entity, blue sky board of directors want to make some cash money and I assume thats why they didnt fully lean into p2p
like I mentioned before Blue Sky's protocol has the capabilities for bitcoin integration baked into it (x) I dont know if they will try to monetize the posts in the same way directly in bluesky as is done in IRIS but the ATP is very flexible and what that means is that they can create a different monetary based app that you don't even need to sign up for you'd just use your bluesky credentials and you'd have a crypto wallet tied to your blue sky account because your ID isn't tied to just blue sky, its tied to anything running the ATP protocol
sound familiar? this is what Elon musk is trying to do with Twitter rn and this is basically where he got the idea, he wants to make twitter the one stop shop app for everything, but this isn't a fantasy unattainable idea this is coming directly from the protocols IRIS and Bluesky use, and I will not be surprised if in the near future we see him attempt to integrate bitcoin into twitter
Twitter, Threads and Tumblr (triple T haha 3T if you will) are all going to try and compete with Bluesky and Iris because ~money~, but they are doing so with.... *drum rolls* Mastedon! the dark horse or more accurately the protocol that Mastedon uses which is called ActivityPUB, Activitypub is older than both NOSTR and ATP and has a history of a wide range of implementation, however if you've ever used Mastodon you'd know its very limited in its capabilities when it comes to social media

This is basically I theorize/speculate is one of the reasons tumblr changed its looks, they are trying to standardize social media between all 3 of them and basically build bridges between each other so as to combat IRIS and BlueSky This is not to say they will become like Mastedon however, in fact between Threads which has a huge amount of money to throw at inventing things and polishing the Activepub protocol and Automattic which owns tumblr and has owned wordpress for even longer who have a familiarity with blogging platforms and multi integration across multiple platforms I think they can be strong competitors
dont ask me what twitter is doing, I am not even certain it will integrate activitypub 100% I just think thats the easiest and fastest way to try and achieve elon's goals and threads and tumblr are combining
so what does it mean exactly when these sites say they will use ActivityPub?
it just means that they are trying to build bridges between each other, that is very vague and obscure of course because idk how they will go about it, the most basic way is post sharing between sites will change and become easier but its not limited to just that, IDK if they will even change the sites themselves instead of just building addons but tumblr's aesthetic change makes me think that they will
more importantly what does this mean for us Users?
well if you've read this far, I just want to emphasize that this isn't something to doom about, while I don't support crypto 100% I think the next wave of social media is headed in a good direction in that people are Finally focusing on decentralizations, social media that isn't under the thumb of one company or hosted on one single server (tumblr servers for example ALLEGEDLY were hosted on one amazon server without backup x) we are finally moving in a direction that is more open as I listed in the pros section above when it comes to IRIS I personally think those ones are worth the cons, however I want people to understand when they are joining bluesky, threads etc the conversation isn't about what these websites are good at NOW, you are NOT joining a twitter copy, all the social medias are gearing up to move away into a new era of internet, it may look the same but under the hood their goals are different, as far as I can tell every social media's goals are focused on 3 things currently >decentralization (lowering their costs in moderation, hosting etc) >getting money, alot of money as fast as possible (crypto integration, selling your data) >beating their competition and surviving as the big fish (protocols are duking it out iris/bluesky vs the world)
like I said at the start of this post I am just a layman with a keyboard, these are just observations I've made, and I could be wrong about multiple things here! but either way, curious about where we are headed
10 notes
·
View notes
Text
fun fact: you can put whatever into the 'From:' field in SMTP. Like for example [email protected]
And just send mostly the same email those park rangers got about how they don't have to come to work from tomorrow on. Let's say to every policemen's address you can guess (there has to be a listing)
As a thought experiment. This post is about the technical shortcomings of an internet protocol
MAGA GOOFS: if we eliminate government jobs those departments will become more efficient so we have fired thousands of park rangers.
EVERYONE: okay what about police officers?
MAGA GOOFS: how dare you
2K notes
·
View notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
9 notes
·
View notes
Text
MailPal 2.0 Review - Send Unlimited Email In 1 Click

Welcome to my Review channel and MailPal 2.0 Review. Are you tired of sending emails? Can you not pay fees every month? Are you not making a profit from email marketing? Are you tired of googling the new rules of 2024? Don`t worry the MailPal Agency launched a new autoresponder Email sender software powered by DeepSeek. You send unlimited Gmail & Yahoo! Without any tech skills & monthly fees.
What Is MailPal 2.0?
MailPal 2.0 is a Gmail & Yahoo! Mail Sender autoresponder software. Send unlimited Gmail & Yahoo! Mail without any restrictions & any tech skills, or experience. The agency provides a 100% Done-For-You DMARC, DKIM & SPF-free policy setup.
Google made a rule compliance policy for Gmail & Yahoo! in the last year 2024. To comply set up DMARC, DKIM & SPF in Gmail & Yahoo! Whether Gmail & Yahoo! Will go to the spam folder. But we need a lot of technical skills to set the policy.
Don`t worry the MailPal 2.0 launched an autoresponder software powered by DeepSeek. They set all tools 100% don-for-you system & solution with no requirement to set up DMARC, DKIM & SPF policy. They require- just One click on the software.
That is an easy way to build high-converting, profitable lists and send emails without paying through the nose every month. You gain a lot of profit and save 1000 dollars monthly using the MailPal 2.0 software.
GET THE MailPal 2.0 APP
Why Unique The MailPal 2.0?
Every software has unique parts and features that are happy for the customer. I will show you the NeoCast unique sites.
100% Done For You DMARC, DKIM, And SPF
Send UNLIMITED Emails
All-in-one e-Commerce Autoresponder:
Use MailPal's drag-and-drop builder to automate
Gain clear insights from detailed segment
No monthly and no restrictions at all
Free SMTP for unlimited Email sending
100% beginner-friendly
Enjoy 24/7 expert support
FULL Commercial License Included
Grow a quality list of subscribers
100% inbox delivery with High-Quality servers
World Class customer support.
Overview Of MailPal 2.0
First, a customer optimizes the product`s quality or benefits the site. Who is the person who built the app? Discount price: why build the app? And who is the best choice for it? Everything. That is an ideal customer`s quality. Don`t worry; I covered the part for an ideal person. I think you are an idealistic reader.
Author/vendor – Venkateshs
Product – MailPal 2.0
Launce date – 21/02/25
Official website – VISITE HERE
Front-end price - $17
Refund – 30 days
Business – ok
Social Media Marketing – Number One
passive income – ok
Recurring System – OK
Payment – ONE Time
Send Gamil & Yahoo! – Any Language
Local Business – High Recommend
Money-Back – 30 Days Money-Back Guarantee
Funnel/Tool – Automated & Done-For-You
Support – Effective
Niche – Any Niche of your choice
That`s How It Works – MailPal 2.0
Wow! It works with many simple steps. A user can use the app easily. The MailPal 2.0 agency made a done-for-you-all tool for a customer. They want to satisfy an audience. So many users follow the role “How does it work? “. I`m sure you don`t use the same app yet.
I want to start the part for my idealistic reader. MailPal 2.0 works in 3 simple systems.
Step 1. Login with Ease
Login to your AI-based email marketing platform. Nothing to set up or configure, simply log in and you’re ready.
Step 2. Upload Your List
Upload your email list, or if you don’t have one, use MailPal 2.0’s 1-click opt-in package to instantly start getting top-quality leads.
Step 3. Start Making Money
Start sending emails and start making money. With MailPal, you can even send SMS texts and social media messages to increase your conversions and your profits.
Why This System Is A Game-Changer? – MailPal 2.0
Advanced Email Template Builder – They have a lot of ready high-converting templates. You use the template and send unlimited mail without any skill.
Single/Double Opt-in Support – The agency knows double opt-in is so hard that they build a single opt-in list faster and safer, user friendly.
Powerful Email Marketing Solution with No Recurring Fee – You get only one-time access. There aren`t any monthly fees and made a powerful email marketing strategy.
Ai Powered Email App – Mailpal 2.0 powered by DeepSeek software. So we can send unlimited unique emails without any restrictions.
Free SMTP for unlimited Email sending – You can send unlimited emails to unlimited subscribers using our Free SMTP service.
All-in-one e-commerce Autoresponder - You can leverage customer data to create effective strategies that drive engagement and sales
100% Done For You DMARC, DKIM, And SPF – We build all tools 100% done for you as a user including DMARC, DKIM, and SPF Policy solutions.
Send UNLIMITED Emails – There are thousands of ready-made templates and user-friendly tools. You send emails without any hassle.
Awesome Features Of MailPal 2.0
Software indeed depends on some valuable features. The MailPal software will be attractive because of its features. Besides, how to work the MailPal software features smoothly or effectively in the future. Firstly, a customer consideration before purchasing this app.
Therefore, an agency builds any software`s features discerningly for a client. After pricing, an agency wants honesty and satisfaction from its customers. It has responsibilities or accountability to a customer.
The MailPal software boosts your earnings 10x with its awesome and interesting features, I can say obviously. I described the software beautifully below.
>> All-in-One e-Commerce Autoresponder
>> Done For You DMARC, DKIM, And SPF
>> Ai Powered Email App
>> Unlimited Lead Generation Using 1 Click Smart technology
>> Free SMTP for Unlimited Email Sending
>> Powerful Email Marketing Solution with No Recurring Fee
>> Manage lists & subscribers easily with MailPal 2.0
>> Unlimited Everything Without Any Restriction
>> Single/Double Opt-in Support
>> 100% Cloud-Based Software
>> Autoresponder for Subscriber Welcome/unsubscribe Emails
>> List Segmentation Support
>> Open/click/unsubscribe Tracking & Statistics Reporting
>> Advanced Email Template Builder
>> Smart Automation Features
>> Subscription Form Builder
>> MailPal 2.0 Helps You to Build Massive Email List Faster
>> 100% Easy to Use Beginner Friendly Email App
GET THE MailPal 2.0 APP
Free A Commercial License – MailPal 2.0 Review
A free commercial license allows individuals or businesses to use, modify, and distribute software, content, or products without paying licensing fees, even for commercial purposes. Unlike personal-use-only licenses, it permits monetization, such as selling the product or incorporating it into commercial projects.
Popular examples include open-source software under MIT or Apache 2.0 licenses. However, users must comply with specific terms, such as attributing the original creator or sharing modifications under the same license. Free commercial licenses foster innovation, collaboration, and accessibility, making them valuable for startups, developers, and creators seeking cost-effective solutions. Always review the license terms to ensure compliance and understand any restrictions.
The Best Part Of MailPal 2.0


Can Do For You – NeoCast
Here is a more interesting part. Software isn`t perfect for every person. Who is the best choice for it? Or how to get benefits using the app. I will explain in the review. So, I can start explaining with the perfect or benefit part.
E-commerce Marketer – An e-commerce marketer can send unlimited email promotions for her products.
Freelancer - A freelancer sends mail to a hand client and knows about her service without any hassle.
Affiliate marketers – They can get more subscribe and profit with MailPal.
Businessman – This is a good opportunity to communicate with each other.
CPA Marketer – There are thousands of free ready templates.
Other Person – Every person uses this mail software of their choice in any niche.
Why do I recommend Using The MailPal 2.o?
>> Build the software autoresponder AI powered by DeepSeek Features that don`t have other software.
>> There are available 1 click lead generator systems.
>> We can send unlimited emails without any hassle.
>> The agency provides an IP pool to get better inboxing and open rates for all your emails.
>> One-time payment opportunity don`t require every month payment.
>> The agency provide 24/7 days customer support.
GET THE MailPal 2.o APP
Done-For-You DMARC, DKIM, & SPF Autoresponder
This is a lot of technical policy to verify your email sending. But we give you an auto solution. We solved the fix problem and built a don-for-you integrated autoresponder mail software. You can get everything done for you in your Free Unlimited SMTP. The agency provides an IP pool to get better inboxing and open rates for all your emails.
Money-back guarantee – MailPal 2.0
A 30-day money-back guarantee is a customer-friendly policy that allows buyers to request a full refund within 30 days of purchase if they are unsatisfied with a product or service. This policy builds trust and confidence, encouraging potential customers to purchase with minimal risk. It demonstrates the seller's commitment to quality and customer satisfaction.
To claim a refund, customers typically need to return the product in its original condition or cancel the service within the specified period. This guarantee is commonly used in industries like software, e-commerce, and subscription services. While it can increase sales, businesses must ensure clear terms to prevent abuse. Overall, it’s a win-win, offering customers peace of mind and businesses a competitive edge.
Pros & cons – MailPal 2.0 Review
The part! Any app has some pros & cons. But such an app hasn`t cons or bad sites. Accordingly, I covered the part that information an agency delivered to me. I hope you don`t waste your quality time reading useless articles. I tried to write a more informative or helpful article for the reader. Now, I want to start with the pros and cons of the software.
Pros Of MailPal 2.0 Review
Unlimited Email send
DMARC, DKIM, & SPF opportunity
24/7 days support
1 click set all system
Done-for-you templates
One time payment
AI-powered
High converting rates
Single/Double opt-in support
Cons Of MailPal 2.0 Review
Depending on the internet connection
Effortless
Bonus
There is a customer who gets a free valuable bonus from the agency. An agency wants to convenience their client, or they want to hold customers. Where do you get the free valuable bonus? But the agency gifts you a valuable bonus of a thousand dollars.
1-BONUS >> Modern Email Marketing And Segmentation ( Value: $197 )
2-BONUS >> Strategy for Creating Email Funnels ( Value: $297 )
3-BONUS >> Email List Guru ( Value: $147 )
4-BONUS >> Email Marketing For Newbie Marketers ( Value: $147 )
5-BONUS >> Writing Engaging Emails ( Value: $197 )
6-BONUS >> Automated Email Marketing Funnel ( Value: $197 )
Frequently Asked Questions Of MailPal 2.0 Review.
Thousand of questions in a customer's mind. The app be good or bad? Have they a money-back guarantee? Have a bonus? Etc. I cleared your dude of mind.
Particularly, a new customer has dude too much. Because they are a smart person of the current generation, generally, they don`t want to waste their valuable time. Ok, no problem, I clear dude questions of your mind.
I covered some important questions that help customers buy the app or take the service.
Are there any monthly fees?
No. There aren`t any monthly fees. Just a time payment.
Is there any money-back guarantee?
Yes, there is a 30-day money-back guarantee.
Will I get support?
The agency provides world-class customer support.
Do you update your product and improve it?
Yes, we always update your products and features.
Affiliate disclaimer
Thank you for reading my honest review. My honest opinion is shared in the review.
An affiliate disclaimer is a statement to inform audiences that a company or individual may earn a commission or other compensation if they purchase products or services through links on their website, blog, social media, or other platforms. This disclaimer is essential for maintaining transparency and complying with legal requirements, such as those set by the Federal Trade Commission (FTC) in the United States. It ensures readers or viewers know of any potential bias or financial incentive behind recommendations.
Typically, the disclaimer is placed prominently, either at the beginning or end of content, and clearly states the nature of the affiliate relationship. For example, "This post may contain affiliate links, meaning I earn a commission if you purchase through my links at no extra cost." This builds trust with the audience while protecting the content creator from legal issues.
0 notes
Text
How to Pick the Most Trustworthy SOCKS5 Proxy
With the continuous development of network technology, network security issues have become increasingly prominent. In this era of information explosion, how to protect personal privacy, break through network restrictions, and improve the security of data transmission has become the focus of attention of the majority of netizens. As an advanced network proxy protocol, SOCKS5 proxy is gradually becoming the patron saint of modern network security.
Definition and advantages of SOCKS5 proxy
SOCKS5 proxy is a network proxy technology that allows users to route their network traffic through an intermediate server (proxy server). This proxy not only hides the user’s real IP address and provides anonymity, but also helps users access network resources that may not be accessible when connected directly. SOCKS5 proxy supports multiple network protocols, including but not limited to HTTP, HTTPS, FTP, and SMTP, making it a versatile network tool. At the same time, it provides authentication functions, enhances the security of network communications, and becomes an effective tool for protecting user privacy and breaking through geographical restrictions.
How SOCKS5 proxy works
The working principle of SOCKS5 proxy is to establish a two-way, reliable TCP connection between the client and the server through a proxy server. When the client makes a request to the server, the proxy server collects the client’s request data and forwards it to the target server. The data returned by the server is sent to the client through the proxy server using the TCP protocol. Since the SOCKS5 proxy uses a reliable transmission protocol, the integrity, accuracy and reliability of the data can be guaranteed. In addition, the SOCKS5 proxy also supports the UDP protocol, enabling it to handle more types of network requests, including live streaming, online games, etc.
Application scenarios of SOCKS5 proxy
SOCKS5 proxy shows its unique advantages in many fields, including but not limited to the following aspects:
1. E-commerce field
In e-commerce platforms, different countries or regions may have different regulations and restrictions on the purchase and sale of products. Using SOCKS5 proxy can help merchants circumvent these geographical restrictions and access blocked or restricted markets. At the same time, encrypted connections through proxy servers can improve the security of data transmission and protect user privacy.
2. Data collection
For data analysis and researchers, SOCKS5 proxy can easily bypass geographical restrictions and access blocked content or services, thereby collecting more comprehensive data. This is of great significance for market research, public opinion analysis and other work.
3. Network security
SOCKS5 proxy plays an important role in protecting user privacy and security. By hiding the user’s real IP address and providing data encryption, SOCKS5 proxy can protect the user’s device from network attacks. At the same time, it can also act as a barrier to filter out some malicious traffic and protect the user’s network security.
4. Entertainment and Games
For users who like online games and entertainment, SOCKS5 proxy can speed up access to overseas game and entertainment platforms and enhance the user’s gaming experience. By selecting a proxy node close to the target server, the data transmission path can be shortened and network latency can be reduced.
How to choose and use SOCKS5 proxy
When choosing and using SOCKS5 proxy, users need to pay attention to the following points:
1. Choose a reliable service provider
Make sure that the selected service provider has a good reputation and credibility, and the proxy servers provided are stable and widely distributed. Avoid using free or unknown proxy services to avoid network security risks.
2. Choose the right package according to your needs
Different users have different needs, so you need to choose the right package according to your own situation. For example, for users who need high-speed network connection, you can choose a high-performance proxy server package; for users who need to access multiple regions, you can choose a package that supports multi-region IP addresses.
3. Correctly configure proxy settings
Before using SOCKS5 proxy, you need to correctly configure the proxy settings. This includes setting the IP address, port number and other information of the proxy server in the operating system, browser or other network applications. Only after ensuring that the configuration is correct can the proxy service be used normally.
4. Check the proxy connection regularly
In order to ensure the stability and security of the proxy connection, users need to check the status of the proxy connection regularly. If you find that the connection is abnormal or the speed is slow, you should contact the service provider in time for troubleshooting and resolution.
Conclusion
With the continuous development of network technology, SOCKS5 proxy, as the guardian of modern network security, will play an increasingly important role in protecting user privacy, breaking through network restrictions, and improving data transmission security. As users, we should correctly choose and use SOCKS5 proxy services to ensure that our network security and privacy are protected to the greatest extent.
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Photo

You can create the best email in the world, but it won’t matter if it doesn’t make it to your subscriber. And that’s why it’s vitally important you work with an email service provider (like FeedBlitz!) who places the highest possible focus and dedication on their deliverability practices. But what does deliverability mean? And how and when does it actually happen? And is there anything you can do to help? The answers to those questions and many more are what you will find in this post. There’s a lot of ground to cover when it comes to email deliverability, so without further delay, let’s jump right in. In this post, you’ll learn: What is email deliverability? Deliverability is a fairly common buzzword in the world of email marketing. However, unless you’re in the business of establishing and safeguarding it — or have had your email efforts impacted because of the lack of it — there isn’t a lot of clarity around the term and how companies achieve, monitor, and protect a high deliverability status. In the simplest of terms, deliverability is the processes and protections that allow your emails to reach your subscribers. It sounds pretty simple, but everything that takes place to get your emails from creation to open is much more complex. Knowing the ins and outs of email deliverability will help you make wiser decisions regarding your email marketing efforts. And it’ll also offer vitally important clarity when deciding which email service provider (ESP) to work with. Because again, you can design the prettiest emails possible, filled with the best content of your life, but it all means nothing if you’re with an ESP who cuts corners and your emails don’t actually get delivered. Key terms related to email deliverability. Anytime you’re working with a complex topic, starting with a foundation of key terms is best. The following terms will be helpful to know as you dig deeper into this blog post: Deliverability – getting your emails to a subscriber.Inboxing – getting your emails to a subscriber’s inbox (including Gmail’s promotions tab) as opposed to the spam folder.Reputation – receiving internet service providers (ISPs) review, judge, and estimate the safety of emails being sent by a particular email address — based on their own top-secret set of rules and guidelines — which ultimately determines whether your email will be allowed or denied.Authentication – a process to further validate the sender of your emails established through SPF, DKIM and DMARC, which use DNS to ensure permission has been granted. What happens when you send an email? Deliverability checks are not something that takes place one time, in one specific step of the email sending process. It can — and does — happen at multiple stages of the process every time one of your emails begins to send. To help give you a better idea of how and when this can happen, we’ll start with all the things that happen when you send an email, i.e., the path your email takes from the moment it begins sending to its arrival at your subscriber’s door. There are many more steps than you may realize, and that’s because most of the process takes place behind the scenes. The full process is a bit more nuanced and detailed than what’s outlined here, but the six steps highlighted below will give you a solid frame of reference for the process. While most ESPs follow similar, if not the same steps, below is a FeedBlitz-specific version to help show additional checks performed throughout the way: Step 1 – You create an email. And when working in FeedBlitz, before you’re even able to send or schedule the mailing, the content is checked against our in-house protocols. For example, you won’t even be allowed to send an email that may potentially be rejected by ISPs. Step 2 – The email begins sending. A unique email copy is created for each subscriber and sent to one of our outbound SMTP servers. (SMTP = the internet’s email protocol) Step 3 – Our SMTP servers send the email to the ISP. FeedBlitz’s SMTP servers then send your mailing to the receiving ISP’s servers. Step 4 – ISP reputation check. The receiving ISP’s inbound email server runs a series of reputation checks (on the sender) and content scans (on the email). Step 5 – Receive, reject or quarantine. The ISP will then either allow your email through, immediately reject it, or quarantine the email by sending it to a subscriber’s spam folder. Step 6 – Email received! (or bounced/rejected) FeedBlitz gets feedback on whether your email was received or recorded as a bounce/undeliverable.At any step of the process, deliverability and reputation checks can kick in and prevent your email from arriving. Luckily, the strict standards and practices many ESPs (like FeedBlitz!) have in place work to catch anything before the email even reaches outbound servers. They will also diligently monitor all feedback loops from ISPs and swiftly suspend any list whose feedback is not up to par. Actions you can take to boost your deliverability and sender reputation. Good email deliverability isn’t only in the hands of your ESP. You as a client can have a significant impact on your reputation with your subscribers, which can and will boost your individual deliverability success. Below are five action items you can do to help boost your own deliverability and sender reputation even further. Set up authentication for your sending domain.Authentication is an added layer of verification to let ISPs know you are the true, valid sender of the email and that you’ve okayed FeedBlitz to do that for you. It involves SPF, DKIM, and DMARC. However, DMARC is typically used by high-level enterprise clients.FeedBlitz servers send your campaigns on behalf of the sending email you supply. (Note: This is why you may notice your email reads via [email protected] in email apps like Gmail or Outlook.) Authentication provides additional validation by saying, “Yes! This email is from me, and I authorize FeedBlitz to send it on my behalf! But please show me as the true sender.”This reinforces the level of trust an ISP forms with you and your emails. Hello, reputation booster.Are you a FeedBlitz client and not sure where you stand on your authentication? Click here to log in and run a quick scan.And if you’re ready to put authentication into action for your FeedBlitz-support campaigns, these steps walk you through how to set things up for your account: Protect Your Brand with SPF and DKIM and What Is and How to Create a DMARC Profile.Keep an eye on engagement data for your campaigns.How your email is received by subscribers is a strong indicator of the reputation you have with your audience. Are they opening? Clicking? Complaining? Unsubscribing? These data points are very important to FeedBlitz, fellow ESPs, and to individual ISPs who decide whether to prioritize (or deprioritize!) your emails.Healthy engagement is the strongest indicator of a healthy mailing list. And everyone likes healthy when it comes to deliverability.In FeedBlitz, you can track engagement data for each campaign from the list dashboard, dive deeper into in on the individual mailing dashboards, or pull a full engagement report to see engagement data over a chosen period of time.Note: Not sure what a good open rate is? Check out this episode of Win the Inbox to learn more.Review your content strategy and email best practices.This may seem a bit broad, but it relates back to something in section 4 of this post: Your audience ultimately determines what is or is not spam.Along with your quality content, you want to deliver a smooth, seamless experience for your subscribers. This means taking into consideration details such as:– Are you mailing regularly? A consistent cadence sets your subscribers’ expectations and can heighten open rates.– Is your branding all connected? From your website to your email template, the colors, the images, etc.? This helps with brand recognition, emphasizing you are someone the subscriber knows, likes, and trusts. (Again, better engagement is the result!)– Are you sending the content your audience signed up to receive? This can be a big determining factor in the frequency of how often a subscriber opens your emails. Deliver on what you promised when they signed up!– Is your template accessible for different audiences? This is where font size, color contrast, alt text for images come into play. The easier your email is to read and engage with, the wider your audience can become.That’s a small selection of things to consider, but it’s a great start to creating a smooth experience for your subscribers.Subscribe to your own list.Somewhat related to actionable #3 above, subscribing to your own mailing list not only ensures the end-to-end subscriber experience is up to your standards but also lets you know immediately if your emails are potentially being routed to somewhere other than the inbox.This also falls into best practices as you’re able to view test emails across different platforms and devices before hitting send.Again, the idea is to make sure your subscribers are having a seamless experience with every campaign you send, so it’s always best to check on different devices and email agents when possible.Remove people who are no longer opening or clicking your emails.While FeedBlitz handles unsubscribes and bounces for you automatically, if there“s one thing the team recommends the most to clients across the board, it’s removing inactive subscribers. This keeps your list — and engagement data — healthy.If a subscriber hasn’t opened or clicked one of your mailings in 60+ days, chances are they’ve lost interest. So instead of keeping them on your list with the mindset of “a bigger list is a better list!” set them free and move forward.In FeedBlitz, there are two ways you can go about this: one would be to send a re-engagement campaign and check if these inactive subscribers are still interested in sticking around, and the other would be to identify and remove them in one fell swoop. The choice is yours. Just remember, the name of the game is healthy, engaged mailing lists! Some of these action items you can work on and complete right away, and others you may choose to take a week or month to focus on. Either way, the suggestions outlined above will not only have a positive impact on your deliverability but also on the relationships you have with your subscribers. How FeedBlitz safeguards and boosts deliverability. In this section, you will learn some of the secrets, standards and practices FeedBlitz has in place to protect and boost email deliverability. These practices not only keep our clients’ emails going but allow us to consistently maintain our industry-leading deliverability rate of 99.8%. When an ESP works hard to safeguard their reputation, they’re also working hard to safeguard yours. It’s important to take deliverability practices into consideration if you’re comparing ESPs to see which is a good fit for you. While an ESP may not go into great detail on their in-house practices, you’re welcome to use the six items outlined below as a guideline for questions to ask. Without going into too much detail — we do have to protect some industry secrets, and we’re highly aware that bad actors read this to learn how to try and skirt the rules — below are six deliverability-related items you may find interesting. (Or, at the very least, you may find them insightful if you’ve ever had a list suspended or mailing halted!) We own all of our servers.That means when you’re sending with FeedBlitz, you’re not sharing a server with anyone who hasn’t been well-vetted or anyone who also isn’t being monitored 24/7/365. We have complete control over our infrastructure.Owning our own servers is hugely important. Some ESPs do not own their servers, and ultimately, they do not have full control over their reputation management. This leaves you vulnerable to your emails being potentially stopped if an unknown bad actor sends from the shared server your emails are sending from, the entire server, and everyone on it, is taken down.When this happens, the server’s IP can be added to a blocked list which is monitored by ISPs (who then reject your emails, not letting them through the door), as well as third-party lists many ISPs check as well — all because of emails you didn’t even send!One bad apple really can ruin the barrel in these situations…which is why FeedBlitz doesn’t cut corners when it comes to protecting deliverability. Feedback loops and changes with major ISPs (i.e., Gmail, Yahoo, Comcast, etc.) are constantly monitored.Meaning, we keep very close tabs on things such as how your audience interacts with your emails, any rejections or bounces which come through, oddly large groups of hard bounces, and velocity-based triggers. Resulting in your email having the best chance of getting through to your subscriber.As part of the monitoring process, if one of our servers is being throttled by an ISP, your campaigns will be quickly routed away from the machines in question so they can continue sending while further research is completed on the server and IP.If an ISP has cleared out a batch of old or undeliverable emails, we’ll confirm this is correct and not merely a glitch in the email ecosystem.Every email list and every subscriber is checked before they’re even allowed in the door.And that is not an understatement. It doesn’t matter if you have 10 subscribers or 10 million subscribers, each and everyone is checked against our own set of internal block lists, matched against 3rd party known purchased or rented lists, and will result in immediate suspension — and quite possibly being blocked from FeedBlitz all together — if an email address returns as a spam trap.We ruthlessly guard imports to protect the reputation of all FeedBlitz clients. If a list is suspended due to a blocked import or poor quality metrics (more on this below), it will remain suspended for at least 24 hours while the import file is being reviewed. After reviewing, the deliverability team will evaluate whether or not the import will be allowed to proceed and if the list will be reinstated.To put it plainly, we check receipts on each and every subscriber you try to bring into our home so our clients can rest easy knowing everyone is held to the same high level of quality control.Before you’re able to leave the editor, your emails go through the same content filters ISPs will run when deciding whether to allow or deny your email entry to the subscriber.Step four in the process listed above is where the destination ISP runs a series of checks to then decide what to do with your email.FeedBlitz created a series of content-based checks within the Visual Mailing Editor (VME) to mirror those an ISP will run.And while the industry has evolved quite a bit, and there is less emphasis on the presence of common spam/trigger words when it comes to deciding whether to allow your email through or not, it is still a factor to take into consideration.These content scans are also a safeguard against making sure your account has not been compromised.It’s frustrating, but bad emails can still come from good places, and that’s why multiple checks and balances are in place throughout the email creation and sending process to help ensure the success of your efforts.Important note: Because reputation extends to the links in your emails as well, this is why FeedBlitz doesn’t even allow an email that links out to a bad IP to be sent. We’re always looking out for you!How your subscribers engage with your mailings has a big effect.Just because a mailing passes our filters, ultimately, it’s up to your audience to decide whether or not it’s spam.Even if your email isn’t flagged as spam, ISPs (and FeedBlitz!) track all feedback from subscribers in how they interact with your mailings.This includes opens, clicks, and unsubscribes. It all has an impact on your deliverability. ISPs keep just as close tabs on this as we do. For example, when emails aren’t opened frequently, a subscriber’s ISP makes note of this and can demote or deprioritize them.FYI: If a mailing comes back with a lot of unsubscribes or complaints, it’s suspended in FeedBlitz for at least 24 hours while our team conducts a thorough review.This all works to keep your reputation and the reputation of all FeedBlitz clients in as good of standing as possible. And as you’ve probably picked up on by now, we don’t play around when it comes to sending reputations.New practices are regularly implemented.As the world of email evolves, so do we. Our team continually adjusts our in-house practices and protocols, as well as implementing new items. For example…– In April of 2022, we informed clients our deliverability team was increasing our email capacity by 40% by warming up a new batch of servers. Deliverability ✅– Large lists with a very low open rate (
0 notes
Text
Web Stagnation
Why does TikTok do that the thing where the previous video is still playing and the one your on doesn't start?
Why does every Online Service suffer from DDOS attacks all the time?
At my previous Job, we created a TikTok-like for watching video snippets for work video tutorials.
And even though we had reduced the amount of videos to be watched to a limited amount and/or limited to videos on the device itself; I was tasked with trying to figure out why it has the same Issue TilTok does.
Which; theoretically because we reduced the overall capacity of the app from "essentially unlimited" to ten; should've alleviated the problem.
This problem also occured on Local hosting the entire app.
I don't even think YouTube found a fix for this.
Now there are two ways to stream a video; either you download the whole thing, or you use a data-buffer.
A data-buffer allows you download a partial sequence of a file, while *still* opening it as normal; which means you can start using the file or watching the video *despite* it still being downloading.
Which is how many services both video and audio avoid these kinds of problems.
Well; the issue *actually* lays in the HTTP protocol itself. And all fixes for this issue have to be built around the limitations of HTTP itself, AND around browser Video operation limitations.
Multi media content like audio and video tend to be packaged as it's own "pseudo-app" in the web page. And this is the same no matter how you're using a web page, through a browser or an app.
Reusable modular design and all.
And all of the current APIs, whether you're using your own, or you're using a ready made solution, have this problem.
Just so you can know our solution; we downloaded ALL the videos and created a MediaPlayer that had limitations on how fast you could switch between videos. Which had to stop video playback, unload the current media, load the new media, and then start playing.
Load/Unload means the media container we were using to play content.
It isn't the best solution, but it's the way we needed to make it work.
But what does that have to do with DDOS attacks you might be saying.
Well; the HTTP protocol is the same no matter how you use it; Offline, online, virtual, whatever...
And hundreds if not thousands of not hundreds of thousands of users have to connect to a single webserver to use a service.
These Valid Users can look like a "DDOS Attack" because of the information lost for each failed connection.
You know when you're loading a webpage with a crappy connection and the loading bar keeps getting stuck half way and you've got no response for the server?
Failed connection.
This doesn't mean that certain hackers aren't DDOSing cuz they're boarded and can't afford the game; it's just that it's mostly the limits of Physics.
Both of these issues combined give us a view of the internet that is a bit dated. We haven't really updated the protocols we use in a bit.
Social Media could use the same Protocol we use for E-Mail (SMTP) for everything it does; but it doesnt.
Either because they don't want the ability to connect outside of the app itself, or because they just didn't think about it.
So they use AJAX and HTTPS connections for these things.
But even if they did try; I think even our Email services are avoiding SMTP for a lot of operations.
All of this adds up to the same reasoning. Our aging Internet Infrastructures aren't really prepared for this kind of communication. Especially when we start using VPNs for Security and Internet Traffic Reduction.
Just think about it this way; we're using the same internet protocols we had when Nintendo Sattellevision was a thing that did make it to America.
And this affects the *whole* internet.
Even the web addresses we have designed are too heavy; leading Elon Musk to finally get his server address x.com instead of Twitter.
Yes, that simple reduction in the web address increased Twitter speeds ten-fold.
These are simply the limitations we're facing, and simply increasing internet speeds won't fix them.
0 notes
Text
How to Segment Your Email List for Better Conversions with the Best Email Marketing Platform in USA
Imagine this: a business owner who knows every customer by name, understands their preferences, and always has the perfect recommendation waiting for them. This personal touch makes customers feel valued, and as a result, they’re far more likely to make a purchase. Now, think about applying that same level of personalization to your email marketing. With segmented email lists, you can do just that — providing highly targeted content that resonates with each group on your list. And the results speak for themselves: segmented campaigns can lead to a 14.31% higher open rate and a 100.95% higher click-through rate, according to Mailchimp.
So, how do you make sure you’re reaching the right people with the right message? The answer lies in email segmentation. Let’s break it down and explore why it matters, how you can do it, and the tools that make it all easier.
Why Segmentation Matters
Segmentation allows you to break your email list into smaller, more focused groups. This means you can tailor your content to the specific interests, needs, and behaviors of each segment, making your emails more relevant and engaging. When your emails feel personal and targeted, engagement skyrockets, and your conversion rates will follow.

Key Benefits of Email Segmentation:
Increased Open Rates: Personalized subject lines can increase open rates by 50% (and we know that first impressions matter).
Higher Click-Through Rates: Targeted emails can give you a 100.95% boost in click-through rates, leading to more meaningful interactions.
Improved Customer Retention: Segmentation helps improve customer retention and can reduce unsubscribe rates by sending the right message at the right time.
Effective Segmentation Strategies
Demographic Segmentation Group your list based on details like job title, location, age, and gender. For example, a cold email automation software provider in the USA might send different messages to small business owners in New York versus tech entrepreneurs in California.
Behavioral Segmentation Look at past behavior: purchases, website activity, email interactions, etc. If someone has already bought a product from you, send them emails about related products. This keeps them engaged and drives more sales.
Psychographic Segmentation Target groups based on values, lifestyle, and interests. Knowing what your customers care about helps you create more meaningful, engaging content that speaks to their needs.
Tools to Enhance Your Segmentation
To get the most out of your email campaigns, you’ll need the right tools to optimize your efforts.
Email Verification Tools: Use email verification tools to ensure your list is clean, accurate, and up-to-date. This reduces bounce rates and improves deliverability.
Cold Email Automation: Leverage cold email automation software like Sendcrux to create personalized email sequences at scale, targeting your segmented lists with ease.
SMTP for Cold Email: Use a reliable SMTP for cold email to ensure your messages land in your recipients’ inboxes and not the spam folder.
Email Rotation: Implement email rotation to distribute your email traffic evenly and avoid being flagged as spam. This tactic uses different email addresses and IPs to keep your deliverability rates high.
Advanced Segmentation Techniques
Domain and IP Warmup: Warm up your domain and IP to avoid deliverability issues. This gradual process helps ensure that your emails are more likely to reach your customers without being flagged as spam.
Dedicated IP: For better control over your email reputation, use a dedicated IP for your cold email campaigns. This increases trust with email providers and boosts deliverability.
Crafting Compelling Subject Lines: Remember, the subject line is your first impression. Personalize it! Personalized subject lines can increase open rates by 26%, so make sure your message grabs attention from the get-go.
Conclusion
Segmentation is a game-changer for your email marketing strategy. By personalizing your content to meet the unique needs of each group within your audience, you’ll see higher engagement, more conversions, and a stronger connection with your customers. To take things further, consider leveraging tools like Sendcrux, cold email automation software, and SMTP for cold email to optimize your efforts. And if you’re ready to elevate your strategy even more, working with the best cold email marketing agency in the USA can help you maximize the potential of your segmented campaigns.
So, are you ready to take your email marketing to the next level? Let’s make sure you’re using the best email marketing platform to reach your goals and drive results.
#emailmarketingplatform#emailcampaignservices#emailmarketinfsoftware#sendcrux#bestcoldemailmarketingagencyintheusa#coldemailSMTP#Unlimitedemailsender#bulkEmailing#emailverifiersoftware#bulkemailverifier#bulkemailverifiersoftware#bulkemailverifiertool#bulkemailsender#B2Bleadgeneration#EmailMarketing#MarketingTool#SmallBusiness#EmailAutomation#AutomationTools#DigitalMarketing#ContentMarketing#MarketingStrategy#EmailStrategy#Emailcampaigns#EmailBranding#leadgeneration#emailverifieronnlieunlimited#SMTPserverforemailmarketing#DedicatedSMTP#IProtation
0 notes
Text
What's the difference between TCP and UDP? Take you to understand network protocols in seconds!
TCP and UDP are two very important transport layer protocols in network communication. Although they are both used to transfer data in the network, their working methods and application scenarios are very different. The following is a detailed analysis of the differences between TCP and UDP, as well as their respective advantages and disadvantages.

1. Transmission
TCP (Transmission Control Protocol)
TCP is a connection-oriented protocol, which means that before sending data, the two sides need to establish a reliable connection. tcp will segment the data during transmission, and each packet arrives at the target location in order. If a packet is lost during transmission, TCP automatically retransmits the packet until it is received by the target device.
UDP (User Datagram Protocol)
UDP is a connectionless protocol that does not establish a connection or perform packet acknowledgments. Data is sent in separate datagrams, which may not be received in the same order as sent by the receiver, and packets are not automatically retransmitted after they are lost. This makes UDP transmission more efficient but less reliable.
2. Reliability
TCP: High Reliability
TCP establishes a connection through three handshakes and uses an acknowledgement mechanism and flow control during data transmission to ensure reliable data transmission. If data is lost or an error occurs, TCP will retransmit it. This reliability makes TCP widely used in scenarios that require high-precision data transfer, such as file transfer, email services, web browsing, etc.
UDP: Less Reliable
UDP does not provide packet acknowledgement and retransmission mechanism, so the data transmission is faster but less reliable. If the network quality is not good, UDP may suffer from data loss, duplication or disorder. Therefore, UDP is mostly used in applications that require high real-time performance but lower data integrity, such as live video streaming, online games, VoIP (Voice over Internet Protocol), etc.
3. Speed and efficiency
TCP: Slower but stable
Since TCP requires connection establishment and packet acknowledgement, the transmission speed is relatively slow. However, this slowness is exchanged for a stable and reliable transmission, which is especially suitable for applications that require complete data transmission.
UDP: Fast, but unstable
UDP has no connection establishment and confirmation mechanism, so the data transmission speed is very fast. However, because of this, it is less stable and less reliable, and is suitable for scenarios that do not require 100% accuracy of data, but require a quick response.
4. Application Scenarios
TCP: Suitable for scenarios that require reliable data transmission, such as file transfer (FTP), mail transfer (SMTP), web browsing (HTTP/HTTPS), etc.
UDP: Suitable for scenarios that require high speed and allow partial data loss, such as video streaming (live), online games, VoIP, etc.
TCP and UDP have their own advantages and disadvantages and are suitable for different application scenarios. If you are building a network application, choose the appropriate transport protocol according to the actual needs.711Proxy can provide you with high-quality proxy IP services in multiple nodes around the world, ensuring you a smooth flow in any network environment.
0 notes
Text
127.0.0.1:62893: Understanding the Meaning and How to Fix It?

127.0.0.1:62893 is a unique IP address referencing the machine from which you are operating. Working on your computer, have you ever come across the mysterious code 127.0.0.1:62893? Though it seems complicated, knowing its components will be beneficial! The error message "Disconnected from the target VM, address: 127.0.0.1:62893" often shows up on the screen throughout the development process. IPv4 and IPv6 are the two varieties of IP addresses. While IPv6 addresses are 128-bit values written in hexadecimal (e.g., 2001:0b8:85a3:0000:0000:8a2e:0370:7334), IPv4 addresses are 32-bit numbers generally expressed in dotted decimal form (e.g., 192.168.1.1). However, port numbers are used on a device to name particular operations or services. They separate traffic for distinct uses so that several services may run on a single IP address. For HTTP, for instance, online traffic usually uses port 80; for HTTPS, port 443; for SMTP, port 25. This blog post will dissect what 127.0.0.1:62893 represents, how it operates, and how to correct a typical issue. Value In Knowing Network Fundamentals Anyone in IT, networking, or software development needs a strong foundation in network principles. Knowing IP addresses and port numbers enhances security network resource protection, performance optimization, and diagnosis of connectivity problems. Furthermore, it enables experts to set and debug systems properly, guaranteeing seamless connection between devices and services. Summary Of The Subject: 127.0.0.1:62893 An IP address and a port number combine in the address 127.0.0.1:62893. 127.0.0.1 is the loopback address—a special-purpose IP address a host uses to interact with itself. Combined with a port number, it allows local machine testing and development free from system exposure to outside networks. We will examine the details 127.0.0.1:62893 in this blog, including its relevance, typical problems, and recommended methods for diagnosing and maximizing its use. Whether your job is network administrator, developer, or IT enthusiast, knowing this IP can help you to control and fix local network configurations. What Is 127.0.0.1? ( Loopback Address) The most often used loopback address in IPv4 is 127.0.0.1. Reserved for a host to send messages to herself, loopback addresses are a spectrum of IP addresses (127.0.0.0 to 127.255.255). It's a local testing method for network applications without transmitting traffic across the real network. Using 127.0.0.1 causes network traffic to return to the same machine. Because it lets you replicate network environments without impacting other devices, this is very helpful for development, testing, and troubleshooting needs. For instance, if you run a web server on your local computer, you can access it by 127.0.0.1 to guarantee it's operating as it should without letting the internet know. What 127.0.0.1:62893 Can Do for You? There are various benefits to address 127.0.0.1:62893. It gives developers a safe space free from public view by letting them test and troubleshoot programs within. Learning about networking concepts, including TCP/IP systems and client-server communication, benefits one. Early identification and reduction of any security risks depends on local-host traffic monitoring. Debugging helps to identify problems connected to networks, enhancing the stability and performance of applications. Working in a controlled environment, localhost avoids issues with other programs. How to Use 127.0.0.1:62893 The address works as follows in a basic sense: Your device runs an application trying to interact with another process. It wants to interact with a service on the same system, so it uses "localhost," (127.0.0.1). The port number (62893) informs the operating system which service or application should handle incoming traffic. For example, a development tool might utilize this address to interface with a local server for debugging needs. Safety Concerns Although port 62893 and the loopback address are usually safe, there are a few factors to consider: Make sure that your firewall settings allow communication across port 62893 if needed. Blocking this port could stop some programs from operating as they should. If you are unfamiliar with the application or service, be cautious of any software trying to interact with this port. Malicious programs could use this port for illegal correspondence. Now and then, make sure no illegal programs are using any other suspicious port or port 62893 on your machine. Please Note: Even though localhost is designed chiefly for local use, the concepts you gain from experimenting can be used in general networking scenarios. You should now be able to interpret and utilize 127.0.0.1:62893 with ease. The Step-by-Step Troubleshooting Guide STEP 1: Verify whether the service is currently running. Check that the service meant to be listening on 127.0.0.1:62893 is running. Open Command Prompt and run: cmd netstat -an | find "62893". Mac or Linux: Run bash from an open terminal using lsof -i:62893. This command will list the process utilizing port 62893 and indicate whether any service is listening on that port. If no service turns up, start the application or service and try again. STEP 2: Look for port conflicts. Verify no other service makes use of port 62893. If you discover another service, you can stop it or switch the port used for your application. STEP 3: Confirm Firewall Guidelines On particular ports, firewalls can restrict access To be sure port 62893 is permitted, review your firewall settings. Firewall from Windows: Advanced Security Open Windows Defender Firewall Review Inbound and Outbound Rules to find rules blocking Port 62893. Firewall from Apple: Under Security & Privacy, under Firewall Settings in System Preferences STEP 4: Review application settings. To guarantee your program is configured correctly to access 127.0.0.1 and port 62893 Review the configuration files or settings of it. STEP 5: Restart network services Restarts of network services occasionally help to fix underlying problems. Windows: cmd netsh winsock reset Restart the network service using the bash sudo system Linux/Mac. STEP 6: Update or reinstall network drivers Issues can arise from corrupt or antiquated network drivers. Make sure your drivers either reinstall them if needed or are current. Conclusion The combination of a local IP address and a port number utilized by a specific service on your computer is represented as 127.0.0.1:62893, more than simply a string of digits. It is essential for anyone working in web development, networking, or information technology to grasp the significance of port numbers, IP addresses, and local hosts. It is crucial to know how to use localhost and the loopback address 127.0.0.1 while troubleshooting network issues, whether you are a developer testing your latest online application or an IT specialist. If you know what these statistics mean and how to manipulate them, you can keep your local services safe and running efficiently. FAQs Can my browser make an HTTP local request if I am not connected to a network? Indeed, your computer communicates with itself without any network! This is so because your computer connects to a default address—127.0.0.1—which is not particular to any network when it lacks an internet connection. How do IPv6 addresses differ from localhost addresses? Acting as the host entry for any data for a given computer, localhost is the basic IPv4 address stated numerically as 127.0.0.1 together with port 62893. Conversely, IPv6 addresses are a numerical series 127.0.0.1-based internet protocol in the v6 sequence. This is a loopback address, unlike IPv4 addresses, which would not allocate many addresses. Can I block a website using a local host address? If yes, in what manner? Certainly. Just follow a few guidelines as described here: Open Notepad under Administrator; utilize the User Account Control prompt Click File, then Open. View the host file open. Enter 127.0.0.1 in the address bar, then Save and Restart your machine. Read the full article
0 notes