#rto management software
Explore tagged Tumblr posts
Text
HypeLMS | Student Management System in Australia
Unlock the power of efficient student management with our AVETMISS- compliant system. Simplify, streamline, and succeed!
https://hypelms.com/
#RTO software in Australia#Student Management Systems Australia#SMS for RTO#Moodle for RTO#LMS RTO Provider#Learning Management System RTO#best rto software in australia#sms for rto australia#learning management system rto australia
0 notes
Text
Student Management Systems and RTO Software: Revolutionizing Education

In today's fast-paced educational landscape, the demand for efficient and streamlined management systems is higher than ever. Traditional methods of student and resource management are gradually being replaced by sophisticated software solutions, bringing forth a new era in education technology. Let's delve into the realm of Student Management Systems (SMS), RTO Software, and other related topics that are reshaping the way educational institutions operate.
1. Introduction
In the digital age, managing students, resources, and compliance can be a daunting task for educational institutions. This is where Student Management Systems and RTO Software come to the rescue. These comprehensive solutions are designed to automate and enhance various aspects of educational management, ensuring smooth operations and improved outcomes.
2. Understanding Student Management Systems
A Student Management System is essentially a digital platform that facilitates the efficient management of student-related data. From enrollment to graduation, an SMS centralizes student information, making it easily accessible to administrators, teachers, and students themselves. This not only saves time but also minimizes errors in data management.
3. Role of RTO Software in Education
Registered Training Organizations (RTOs) play a crucial role in providing quality education and training. To streamline their operations and ensure compliance with regulatory requirements, RTO Software comes into play. This specialized software assists in managing courses, assessments, and student records, contributing to a more organized and compliant educational environment.
4. Comparison with Traditional Systems
In the past, educational institutions relied heavily on manual record-keeping and administrative processes. However, these traditional systems often led to inefficiencies, inaccuracies, and increased workload. Modern Student and RTO Management Systems bring a paradigm shift by automating tasks, reducing errors, and enhancing overall efficiency.
5. Learning Management Systems in Australia
The Australian education sector has witnessed a surge in the adoption of Learning Management Systems (LMS). These platforms go beyond student data management and extend to the realm of delivering and tracking educational content. LMS in Australia is characterized by user-friendly interfaces and robust features that cater to the diverse needs of educational institutions.
6. Cloud-Based Solutions
The integration of cloud technology has revolutionized the way Student and RTO Management Systems operate. Cloud-based solutions offer accessibility from anywhere at any time, promoting flexibility in educational management. This ensures that administrators, educators, and students can access essential information seamlessly, fostering collaboration and efficiency.
7. Assessment Management Systems
Effective assessment management is critical for maintaining academic standards and ensuring fair evaluation. Assessment Management Systems seamlessly integrate with Student and RTO Management Systems, providing a holistic approach to education management. These systems facilitate the creation, distribution, and grading of assessments, streamlining the entire process.
8. Avetmiss Reporting System
The Australian Vocational Education and Training Management Information Statistical Standard (Avetmiss) reporting is a vital aspect of the education system. Avetmiss reporting systems integrated into Student and RTO Management Software ensure accurate and timely submission of data, contributing to compliance with national standards.
9. Choosing the Right Software
Selecting the right Student and RTO Management Software is a critical decision for educational institutions. Factors such as customization options, scalability, and user-friendliness should be carefully considered. A tailored software solution ensures that the unique needs of an institution are met, leading to optimal performance and outcomes.
10. Online Enrolment and Training Software
The shift towards online enrolment and training software has simplified administrative processes for educational institutions. These platforms facilitate seamless enrolment procedures, reducing paperwork and enhancing the overall experience for both students and administrators. Additionally, online training software provides a flexible learning environment, catering to the needs of diverse learners.
11. Compliance and Regulations
Navigating through the complex landscape of compliance and regulations in the Australian education system is a challenge. Student and RTO Management Systems play a pivotal role in ensuring that institutions adhere to these standards. The automation of compliance processes reduces the risk of errors and non-compliance, fostering a transparent and accountable educational environment.
12. RTO Training Resources
A key component of effective education is the availability of resources for RTOs. Whether it's course materials, assessments, or training modules, having a robust repository of resources enhances the learning experience for students. Student and RTO Management Systems contribute to the efficient organization and delivery of these resources.
13. Student Assessment Management
Fair and efficient assessment processes are fundamental to the success of any educational institution. Student Assessment Management Systems, when integrated into broader management systems, ensure that assessments are conducted transparently and consistently. This contributes to a fair evaluation of students' knowledge and skills.
14. Future Trends in Education Software
As technology continues to evolve, the landscape of education software is set to witness exciting advancements. Artificial intelligence, virtual reality, and adaptive learning are some of the future trends that will shape the educational experience. Institutions need to stay abreast of these developments to remain at the forefront of
15. Conclusion
In conclusion, the integration of Student Management Systems, RTO Software, and other advanced technologies is transforming the education sector in Australia. These solutions not only streamline administrative tasks but also contribute to a more efficient, compliant, and student-centric learning environment. Educational institutions that adopt these systems are better positioned to navigate the challenges of the digital age and provide a top-notch learning experience.
Frequently Asked Questions (FAQs)
Q: What is the significance of Avetmiss reporting in education?
A: Avetmiss reporting ensures accurate data submission, contributing to compliance with national standards and enhancing transparency in the education system.
Q: How do cloud-based solutions benefit Student and RTO Management Systems?
A: Cloud-based solutions provide accessibility and flexibility, allowing seamless collaboration among administrators, educators, and students from any location.
Q: What factors should educational institutions consider when choosing management software?
A: Customization options, scalability, and user-friendliness are crucial factors to consider when selecting Student and RTO Management Software.
Q: How do Assessment Management Systems contribute to fair evaluations?
A: These systems facilitate the creation, distribution, and grading of assessments, ensuring transparency and consistency in evaluation processes.
Q: What are the future trends in education software?
A: Emerging technologies like artificial intelligence, virtual reality, and adaptive learning are expected to shape the future of education software, providing a more personalized learning experience.
#learning management system#learning management system australia#rto student management system#cloud lms software#lms software#lms software in australia#learning management system in australia
0 notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
HR software biz BambooHR surveyed more than 1,500 employees, a third of whom work in HR. The findings suggest the return to office movement has been a poorly-executed failure, but one particular figure stands out - a quarter of executives and a fifth of HR professionals hoped RTO mandates would result in staff leaving.
While that statistic essentially admits the quiet part out loud, there was some merit to that belief. People did quit when RTO mandates were enforced at many of the largest companies, but it wasn't enough, the study reports.
More than a third (37 percent) of respondents in leadership roles believed their employers had undertaken layoffs in the past 12 months as a result of too few people quitting in protest of RTO mandates, the study found. Nearly the same number thought their management wanted employees back in the office to monitor them more closely.
The end result has been the growth of a different office culture, one that's even more performative, suspicious, and divisive than before the COVID pandemic, the study concludes.
6 notes
·
View notes
Text
Disaster Recovery as a Service (DRaaS) Market Accelerates with Increasing Compliance Requirements
Disaster Recovery as a Service (DRaaS) Market Size was valued at USD 11.7 Billion in 2023 and is expected to reach USD 76.0 Billion by 2032, growing at a CAGR of 23.1% over the forecast period 2024-2032.
Disaster Recovery as a Service (DRaaS) Market is experiencing significant traction as businesses prioritize uninterrupted operations and data resilience in an increasingly digital environment. With rising threats of cyberattacks, system failures, and natural disasters, enterprises across industries are seeking scalable and cost-effective recovery solutions to safeguard business continuity.
U.S. remains the dominant region for DRaaS adoption due to high cloud infrastructure maturity and cybersecurity investments
Disaster Recovery as a Service (DRaaS) Market is evolving rapidly, fueled by the growing shift toward cloud-first strategies. Organizations are investing in DRaaS platforms to minimize downtime, comply with regulatory standards, and ensure seamless recovery processes that protect sensitive data and mission-critical systems.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/2780
Market Keyplayers:
IBM Corporation (IBM Cloud Disaster Recovery, IBM Resiliency Orchestration)
Microsoft Corporation (Azure Site Recovery, Microsoft Hyper-V Replica)
Amazon Web Services (AWS) (AWS Elastic Disaster Recovery, AWS Backup)
VMware, Inc. (VMware vSphere Replication, VMware Site Recovery Manager)
Sungard Availability Services (Recover2Cloud, Managed Recovery Program)
Acronis International GmbH (Acronis Cyber Protect, Acronis Disaster Recovery)
Zerto (Zerto Virtual Replication, Zerto Cloud Continuity Platform)
Veeam Software (Veeam Backup & Replication, Veeam Cloud Connect)
Dell Technologies (Dell EMC RecoverPoint, Dell EMC PowerProtect)
Cisco Systems, Inc. (Cisco UCS, Cisco HyperFlex)
Carbonite, Inc. (Carbonite Server Backup, Carbonite Endpoint Backup)
Arcserve (Arcserve UDP Cloud Direct, Arcserve Continuous Availability)
Axcient, Inc. (Axcient Fusion, Axcient Replibit)
Datto, Inc. (Datto SIRIS, Datto ALTO)
Market Analysis
The DRaaS Market is being driven by heightened awareness around data protection, business continuity planning, and compliance mandates. As digital transformation accelerates, enterprises face increasing complexity in managing IT systems, making third-party disaster recovery solutions both practical and essential. In the U.S., industries such as healthcare, BFSI, and government are actively deploying DRaaS to protect against data loss and maintain regulatory compliance. Globally, enterprises are moving away from traditional recovery methods toward fully managed, cloud-based DR solutions.
Market Trends
Surge in demand for cloud-native disaster recovery platforms
Integration of AI and machine learning for predictive failure analysis
Increased adoption by SMEs due to affordability and scalability
Hybrid cloud DRaaS models supporting both on-prem and cloud data centers
Regulatory compliance driving implementation in BFSI and healthcare sectors
Rising partnerships between cloud providers and DRaaS vendors
Real-time recovery solutions gaining traction for mission-critical workloads
Market Scope
The scope of the DRaaS Market extends beyond traditional data backup. Today’s DRaaS offerings deliver fast, automated, and secure recovery options for a wide array of industries and infrastructure models.
On-demand scalability with reduced infrastructure cost
Multi-region backup support for data sovereignty
Seamless integration with hybrid and multi-cloud architectures
RTO and RPO optimization through advanced automation
Enterprise-grade security and encryption protocols
Custom recovery plans for industry-specific compliance needs
Access Complete Report: https://www.snsinsider.com/reports/disaster-recovery-as-a-service-market-2780
Forecast Outlook
The DRaaS Market is set to expand steadily as businesses place increased emphasis on uninterrupted access to digital infrastructure. The ongoing shift to hybrid work, growing cyber risk landscape, and the demand for scalable IT resilience solutions are propelling DRaaS forward. Cloud-native recovery solutions, coupled with AI-driven automation, will continue to redefine disaster recovery standards. The U.S. will lead the charge, while Europe and APAC will contribute significantly to global adoption through growing investments in secure IT infrastructure.
Conclusion
In today’s always-on digital economy, the Disaster Recovery as a Service Market plays a vital role in ensuring operational resilience and data integrity. Enterprises can no longer afford prolonged downtimes or data losses—making DRaaS not just a precaution, but a strategic priority. As the market matures, its blend of flexibility, speed, and reliability is setting a new benchmark for disaster preparedness and business continuity.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Mechatronic Design Overview
Mechatronic design is an interdisciplinary engineering approach that integrates mechanical engineering, electronics, control systems, and software to create intelligent, automated systems. By combining these disciplines, mechatronic design enables the development of advanced products and systems, such as robots, autonomous vehicles, and smart devices, with enhanced functionality, precision, and efficiency. This 800-word overview explores the principles, applications, benefits, challenges, and future trends of mechatronic design, highlighting its pivotal role in modern engineering.
Principles of Mechatronic Design
Mechatronic design follows a holistic approach, emphasizing synergy between mechanical, electronic, and software components:
System Integration: Mechatronic systems combine mechanical structures (e.g., actuators, gears), electronic components (e.g., sensors, microcontrollers), and software algorithms to operate as a cohesive unit. This integration ensures seamless interaction between hardware and software.
Modeling and Simulation: Tools like MATLAB/Simulink or SolidWorks are used to create dynamic models of mechatronic systems, simulating their behavior under various conditions. This enables engineers to optimize designs before physical prototyping.
Control Systems: Mechatronic design relies on control algorithms, such as PID (Proportional-Integral-Derivative) or Model Predictive Control (MPC), to regulate system behavior. These algorithms ensure precise motion, stability, and responsiveness.
Sensors and Actuators: Sensors (e.g., accelerometers, gyroscopes) provide real-time data on system states, while actuators (e.g., motors, hydraulic systems) execute control commands. Their integration enables closed-loop feedback for accurate performance.
Embedded Software: Firmware, often written in C/C++ or using real-time operating systems (RTOS), manages hardware operations, processes sensor data, and implements control logic, ensuring real-time responsiveness in constrained environments.
Iterative Design Process: Mechatronic design follows an iterative cycle of modeling, simulation, prototyping, testing, and refinement. This reduces errors and aligns the system with performance requirements.
Applications of Mechatronic Design
Mechatronic design is integral to a wide range of industries, enabling innovative and efficient solutions:
Robotics: Mechatronic design powers industrial robots, humanoid robots, and drones. It integrates sensors, actuators, and control algorithms for tasks like assembly, navigation, and object manipulation.
Automotive Systems: Mechatronics drives advanced vehicle features, such as anti-lock braking systems (ABS), electronic stability control, and autonomous driving systems, enhancing safety and performance.
Aerospace: Mechatronic design is used in flight control systems, satellite actuators, and unmanned aerial vehicles (UAVs). It ensures precision and reliability in high-stakes environments.
Consumer Electronics: Smart devices, such as wearable fitness trackers and home automation systems, rely on mechatronic design for sensor integration, user interfaces, and compact, efficient hardware.
Medical Devices: Mechatronics enables precise control in devices like robotic surgical systems, prosthetics, and diagnostic equipment, improving patient outcomes and operational accuracy.
Industrial Automation: Mechatronic systems power automated manufacturing lines, CNC machines, and robotic arms, optimizing productivity and reducing labor costs in smart factories.
Benefits of Mechatronic Design
Mechatronic design offers significant advantages for product development and system performance:
Enhanced Functionality: By integrating mechanical, electronic, and software components, mechatronic systems deliver advanced features, such as adaptability, automation, and real-time responsiveness.
Improved Efficiency: Optimized control algorithms and precise actuation reduce energy consumption and operational waste, making systems more sustainable and cost-effective.
Reduced Development Time: Simulation and modeling allow engineers to test designs virtually, minimizing the need for costly physical prototypes and accelerating time-to-market.
Increased Reliability: Closed-loop control and fault-tolerant designs enhance system robustness, reducing failures and maintenance needs in critical applications.
Compact and Lightweight Designs: Mechatronic integration enables smaller, more efficient systems by combining functionalities into fewer components, ideal for applications like wearables or drones.
Cross-Disciplinary Innovation: Mechatronic design fosters collaboration between mechanical, electrical, and software engineers, leading to innovative solutions that push technological boundaries.
Challenges in Mechatronic Design
Despite its advantages, mechatronic design presents several challenges:
Complexity: Integrating multiple disciplines increases design complexity, requiring expertise in mechanical, electronic, and software engineering, as well as system-level thinking.
High Initial Costs: Tools like CAD software, simulation platforms, and prototyping equipment involve significant investment, which can be a barrier for smaller organizations.
Interdisciplinary Coordination: Aligning mechanical, electronic, and software teams can be challenging due to differing terminologies, tools, and priorities, potentially leading to miscommunication.
Real-Time Constraints: Mechatronic systems often operate in real-time environments, requiring precise timing and low-latency performance, which complicates software and hardware design.
Testing and Validation: Ensuring system reliability across diverse operating conditions demands rigorous testing, including Hardware-in-the-Loop (HIL) and environmental simulations, which can be resource-intensive.
Future Trends
The future of mechatronic design is shaped by emerging technologies and industry needs:
Artificial Intelligence (AI) and Machine Learning: AI enhances mechatronic systems by enabling adaptive control, predictive maintenance, and autonomous decision-making, particularly in robotics and automotive applications.
Internet of Things (IoT) Integration: Mechatronic systems are increasingly connected, enabling real-time data sharing and remote monitoring in smart homes, factories, and cities.
Miniaturization: Advances in microelectromechanical systems (MEMS) and nanotechnology are driving smaller, more efficient mechatronic designs for wearables and medical implants.
Sustainability Focus: Mechatronic design is prioritizing energy-efficient systems, such as electric vehicle drivetrains and renewable energy controllers, to support global sustainability goals.
Digital Twins: Mechatronic systems are leveraging digital twins—real-time virtual models—for continuous monitoring, optimization, and predictive maintenance, enhancing system lifecycle management.
Conclusion
Mechatronic design by Servotechinc is a cornerstone of modern engineering, blending mechanical, electronic, and software disciplines to create intelligent, efficient systems. Its applications in robotics, automotive, aerospace, and medical devices demonstrate its versatility and impact. While challenges like complexity and cost persist, advancements in AI, IoT, and miniaturization are expanding its potential. As industries demand smarter, more sustainable solutions, mechatronic design will continue to drive innovation, delivering systems that are precise, reliable, and transformative in an increasingly automated world.
0 notes
Text
FreeRTOS Design Routine Based on i.MX9352 Development Board M Core
In the embedded systems, the application of embedded real-time operating systems (RTOS) is becoming increasingly widespread. Using an RTOS can utilize CPU resources more reasonably and efficiently. As a lightweight and mature real-time operating system kernel, FreeRTOS has complete core functions, including task management, time management (such as delays and timers), synchronization mechanisms (semaphores, mutexes), inter-process communication (message queues), and so on. These features enable it to meet the needs of small and medium-sized embedded systems with relatively limited resources.
i.MX 9352 is a new generation of lightweight edge AI processor launched by NXP, which integrates 2 x Cortex-A55 cores and 1 x Cortex-M33 real-time core. Its architecture design fully reflects the balance between real-time and complex task processing capabilities. To help developers fully leverage the real-time capabilities of the i.MX 9352 M33 core, the FreeRTOS examples provided in the accompanying M-core SDK package are divided into two categories. One category introduces the features of FreeRTOS system components, such as semaphores, mutexes, and queues. The other category shows how to use peripheral interfaces in FreeRTOS. Examples from each of these two categories are selected for demonstration.
▊ Demo platform: Forlinx Embedded OK-MX9352-C Development Board
1. FreeRTOS-generic
The sample code of FreeRTOS features supported by the Forlinx Embedded OK-MX9352-C is as follows:
freertos_event: Demonstration Routine for Task Event
freertos_queue: Demonstration routine for implementing inter-task communication using queue messages
freertos_mutex: Routine for using mutexes
freertos_swtimer: Usage of software timers and their callbacks.
freertos_tickless: Routine for delayed wake-up using LPTMR or wake-up by hardware interrupt.
freertos_generic: Demonstration routine for the combined use of tasks, queues, software timers, tick hooks, and semaphores.
Since the FreeRTOS_generic routine uses many FreeRTOS features, let's focus on analyzing this routine.
(1)Software implementation
The content of the example program includes: task creation, queues, software timers, system tick clocks, semaphores, and exception handling. Specifically:
Task creation:
The main function creates three tasks: a queue sending task, a queue receiving task, and a semaphore task.// Create the queue receiving task if (xTaskCreate(prvQueueReceiveTask, "Rx", configMINIMAL_STACK_SIZE + 166, NULL, mainQUEUE_RECEIVE_TASK_PRIORITY, NULL) != pdPASS) // Create the queue sending task if (xTaskCreate(prvQueueSendTask, "TX", configMINIMAL_STACK_SIZE + 166, NULL, mainQUEUE_SEND_TASK_PRIORITY, NULL) != pdPASS) // Create the semaphore task if (xTaskCreate(prvEventSemaphoreTask, "Sem", configMINIMAL_STACK_SIZE + 166, NULL, mainEVENT_SEMAPHORE_TASK_PRIORITY, NULL) != pdPASS)
Queues:
The queue sending task blocks for 200ms and then sends data to the queue. The queue receiving task blocks to read from the queue. If the data is read correctly, it prints the current number of received items in the queue.// The queue sending task blocks for 200ms and then sends data to the queue static void prvQueueSendTask(void *pvParameters) { TickType_t xNextWakeTime; const uint32_t ulValueToSend = 100UL; xNextWakeTime = xTaskGetTickCount(); for (;;) { // The task blocks until the 200ms delay ends. vTaskDelayUntil(&xNextWakeTime, mainQUEUE_SEND_PERIOD_MS); // Send data to the queue. A blocking time of 0 means it will return immediately when the queue is full. xQueueSend(xQueue, &ulValueToSend, 0); } } //The queue receives the task, and the task is blocked to read the queue. If the data is read correctly, the number received by the queue at this time is printed. static void prvQueueReceiveTask(void *pvParameters) { uint32_t ulReceivedValue; for (;;) { //The task keeps blocking until data is read from the queue xQueueReceive(xQueue, &ulReceivedValue, portMAX_DELAY); //The queue data is consistent with the sending, and the queue receiving quantity+1 outputs the queue receiving quantity at this time if (ulReceivedValue == 100UL) { ulCountOfItemsReceivedOnQueue++; PRINTF("Receive message counter: %d.\r\n", ulCountOfItemsReceivedOnQueue); } } }
Software timers:
Set the software timer period to 1 second. When the time is up, call the callback function, record the number of times, and print it via the serial port.// Create a software timer task with a time of 1 second and cyclic operation. xExampleSoftwareTimer = xTimerCreate( "LEDTimer", mainSOFTWARE_TIMER_PERIOD_MS, pdTRUE, (void *)0, vExampleTimerCallback); //Start the software timer xTimerStart(xExampleSoftwareTimer, 0); //Callback function static void vExampleTimerCallback(TimerHandle_t xTimer) { //Enter the callback function once every 1s, and the count increases ulCountOfTimerCallbackExecutions++; PRINTF("Soft timer: %d s.\r\n", ulCountOfTimerCallbackExecutions); }
System tick clock:
Set the task tick interrupt frequency by setting configTICK_RATE_HZ in the FreeRTOSConfig.h file. When starting the task scheduler, the system will calculate the value to be written to the tick counter according to another variable configCPU_CLOCK_HZ (CPU frequency) and start the timer interrupt.
// Set the system tick clock to 1000/200 = 5ms #define configTICK_RATE_HZ ((TickType_t)200)
Semaphores:
In each system tick clock interrupt, call the function vApplicationTickHook. After accumulating 500 times, which is 500 * 5ms = 2.5s, send a semaphore. After the semaphore task acquires the semaphore, it counts and prints the accumulated number of times.// The system tick is 5ms. Release the event semaphore every 500 * 5ms = 2.5s. void vApplicationTickHook(void) { BaseType_t xHigherPriorityTaskWoken = pdFALSE; static uint32_t ulCount = 0; ulCount++; if (ulCount >= 500UL) { //Release the event semaphore in the interrupt xSemaphoreGiveFromISR(xEventSemaphore, &xHigherPriorityTaskWoken); ulCount = 0UL; } } //The task blocks and waits for the semaphore. After receiving, the number of receiving times increases and is printed through the serial port. static void prvEventSemaphoreTask(void *pvParameters) { for (;;) { //Task blocks until semaphore can be acquired if (xSemaphoreTake(xEventSemaphore, portMAX_DELAY) != pdTRUE) { PRINTF("Failed to take semaphore.\r\n"); } //Accumulate the number of times the semaphore is received ulCountOfReceivedSemaphores++; PRINTF("Event task is running. Get semaphore :%d \r\n",ulCountOfReceivedSemaphores); } }
Exception handling:
When memory allocation fails, a stack error occurs, or a task is idle, the program enters the corresponding function. Users can add corresponding handling functions.// Memory allocation failure function. When memory allocation fails, the program enters this function. void vApplicationMallocFailedHook(void) { for (;;) ; } //Stack error check function, which is entered when stack overflow occurs void vApplicationStackOverflowHook(TaskHandle_t xTask, char *pcTaskName) { (void)pcTaskName; (void)xTask; for (;;) ; } // Idle task, with the lowest priority and no practical significance. It's just to keep the CPU busy. Users can add their own functions. void vApplicationIdleHook(void) { volatile size_t xFreeStackSpace; xFreeStackSpace = xPortGetFreeHeapSize(); if (xFreeStackSpace > 100) { } }
(2)Experimental Phenomenon Part
① Compile the program: Manually load the M-core program in U-Boot.
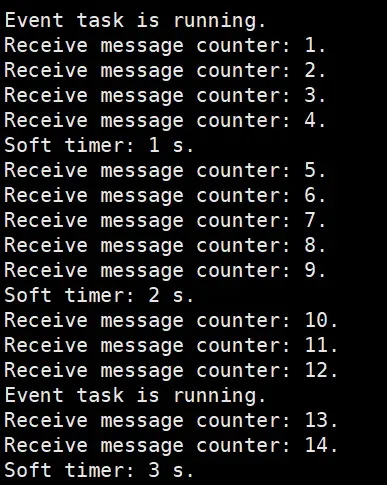
② Queue: Every 200 milliseconds, the sending task of the queue sends data, and the receiving task of the queue retrieves data. The receiving task transitions from the blocked state to the running state and prints the count.
③ Software timer: Every 1s, when the time is up, the callback function is called, and the count is printed.
④ Semaphore: Every 5ms, the system clock tick interrupt calls a function. After more than 500 times, the semaphore is released. The semaphore task acquires the semaphore, changes from the blocked state to the running state, and prints the count.
2. FreeRTOS-Peripherals
The Forlinx Embedded OK-MX9352-C development board supports using FreeRTOS to drive various peripherals. The following are some example codes:
freertos_uart: FreeRTOS UART demonstration routine
freertos_lpi2c_b2b: FreeRTOS I2C demonstration routine
freertos_lpspi_b2b: FreeRTOS SPI demonstration routine
Since the freertos_uart routine uses typical FreeRTOS features, focus on analyzing this routine.
(1) Software implementation
The example program content includes: serial port initialization task, serial port sending task, and serial port receiving task. Specifically:
Serial port initialization task:
It mainly includes the initialization of serial port peripherals, sending and receiving mutexes, and sending and receiving event groups. The initialization of serial port peripherals has been demonstrated in the bare-metal running serial port example, so it will not be detailed here.// Create a serial port sending mutex. handle->txSemaphore = xSemaphoreCreateMutex(); // Create a serial port receiving mutex. handle->rxSemaphore = xSemaphoreCreateMutex(); // Create a flag group sending events handle->txEvent = xEventGroupCreate(); // Create a flag group receiving events handle->rxEvent = xEventGroupCreate();
Serial port sending:
The semaphore is obtained before sending, the sending process is started, and the sending completion event flag is set in the interrupt. After acquiring the event, the send task releases the send semaphore.//1 Get the send semaphore if (pdFALSE == xSemaphoreTake(handle->txSemaphore, 0)) { return kStatus_Fail; } handle->txTransfer.data = (uint8_t *)buffer; handle->txTransfer.dataSize = (uint32_t)length; //2 blocking transmission status = UART_TransferSendNonBlocking(handle->base, handle->t_state, &handle->txTransfer); if (status != kStatus_Success) { (void)xSemaphoreGive(handle->txSemaphore); return kStatus_Fail; } // 3. Wait for the event of transmission completion ev = xEventGroupWaitBits(handle->txEvent, RTOS_UART_COMPLETE, pdTRUE, pdFALSE, portMAX_DELAY);// Wait and evaluate multiple event flags if ((ev & RTOS_UART_COMPLETE) == 0U) { retval = kStatus_Fail; } // 4 Transmission completed, release the transmission semaphore. if (pdFALSE == xSemaphoreGive(handle->txSemaphore)) // Release the transmission semaphore. { retval = kStatus_Fail; }
Serial port receiving:
Before receiving, obtain the semaphore, call the serial port receiving function, and set the event flag in the interrupt. After the receiving task obtains the event, release the receiving semaphore.// 1. Obtain the receiving semaphore. if (pdFALSE == xSemaphoreTake(handle->rxSemaphore, portMAX_DELAY)) { return kStatus_Fail; } handle->rxTransfer.data = buffer; handle->rxTransfer.dataSize = (uint32_t)length; //2 serial port receiving function status = UART_TransferReceiveNonBlocking(handle->base, handle->t_state, &handle->rxTransfer, &n); if (status != kStatus_Success) { (void)xSemaphoreGive(handle->rxSemaphore); return kStatus_Fail; } //3 Obtain the receiving event ev = xEventGroupWaitBits(handle->rxEvent,RTOS_UART_COMPLETE | RTOS_UART_RING_BUFFER_OVERRUN | RTOS_UART_HARDWARE_BUFFER_OVERRUN, pdTRUE, pdFALSE, portMAX_DELAY); // Wait and check the event bit indicating the completion of receiving // 3.1 Hardware receiving error if ((ev & RTOS_UART_HARDWARE_BUFFER_OVERRUN) != 0U) { UART_TransferAbortReceive(handle->base, handle->t_state); (void)xEventGroupClearBits(handle->rxEvent, RTOS_UART_COMPLETE); // Clear the event bit indicating receiving completion. retval = kStatus_UART_RxHardwareOverrun; local_received = 0; } //3.2 Receiving buffer overload error else if ((ev & RTOS_UART_RING_BUFFER_OVERRUN) != 0U) { UART_TransferAbortReceive(handle->base, handle->t_state); (void)xEventGroupClearBits(handle->rxEvent, RTOS_UART_COMPLETE); // Clear the event bit indicating receiving completion. retval = kStatus_UART_RxRingBufferOverrun; local_received = 0; } //3.3 Receiving completed else if ((ev & RTOS_UART_COMPLETE) != 0U) { retval = kStatus_Success; local_received = length; } else { retval = kStatus_UART_Error; local_received = 0; } //4. Release the received signal quantity if (pdFALSE == xSemaphoreGive(handle->rxSemaphore)) { retval = kStatus_Fail; }
(2)Experimental Phenomenon Part
① Compile the program and manually load the M-core program in U-Boot.
② After the device is powered on, the serial port prints the program information. At this time, input 4 characters via the keyboard, and the M-core debugging serial port will echo. Repeating the input and echo of characters proves that the program runs successfully.

The above is an example demonstration of FreeRTOS software design on the M-core of the Forlinx Embedded i.MX 9352 development board. Hope it can be helpful to all engineer friends.
0 notes
Text
HR Management in 2025: What’s New & Noteworthy

Navigating the Future of HR: A 2025 Perspective
As we move through 2025, Human Resource Management is undergoing one of its most significant transformations in decades. Shaped by the rapid rise of AI, remote work evolution, and a new wave of employee expectations, HR leaders are rethinking every aspect of their strategy—from hiring and retention to learning and development.
The post-pandemic workforce is more diverse, digitally native, and deeply focused on purpose and well-being. Meanwhile, businesses face mounting pressure to stay competitive by leveraging people analytics, promoting inclusivity, and driving productivity in hybrid and distributed work models.
It's no longer enough for HR to simply support operational needs; it must now lead strategic initiatives that align with business growth and human potential. In this article, we explore the top HR trends defining 2025, backed by expert research and global insights—plus a powerful software solution that helps modern HR teams manage it all: One24 — Best HRMS Software.
1. AI-Powered Personalization & Decision‑Making
AI is scaling from simple automation to tailored coaching, benefits, notifications, and more—offering hyper‑personalized employee experiences at scale .
Compensation strategies are becoming smarter too: AI-driven tools like Payscale’s Verse and Peer are now widely used for benchmarking, helping HR stay salary‑competitive and transparent businessinsider.com.
2. Shifting Focus: Skills Over Degrees
Leading HR experts (Gartner, SHRM, Deloitte) confirm the transition toward skills-centric hiring, where abilities and adaptability matter more than formal education .
As AI and new-collar jobs emerge, continuous upskilling, micro‑learning, and soft‑skills training have become critical retention strategies.
3. Redefining Workforce: Blue‑ & New‑Collar Inclusion
HR leaders are now blurring lines between deskless and desk‑based roles, investing in tools and development opportunities that empower both groups.
Innovative work models like “silent hours” and elder‑care leave are gaining traction, especially in India, to attract Gen Z timesofindia.indiatimes.com.
4. Odyssey of Hybrid & Well‑Being Focus
Post-pandemic shifts continue: flexible schedules, mental health perks, mindfulness programs, elder‑care and even pet‑PTO are becoming standard to encourage retention and well-being .
5. People Analytics, E‑HRM & Ethical AI
HR technology has evolved: rich analytics, e‑HRM platforms with AI‑based forecasting, sentiment and retention signals, are reshaping decision-making.
As complexity grows, HR’s strategic role deepens—driving culture, inclusion, and ethical AI integration gartner.com.
6. A Stressful Profession Pushed to the Brink
HR teams are under growing stress—managing layoffs, RTO policies, immigration compliance, and rising incivility. Burnout, turnover, and existential pressure are now widespread .
Verdict
HR in 2025 stands at an inflection point—anchored in AI, analytics, and agility, while refocusing on humanization, well-being, and equity. As technology transforms HR operations, the profession itself needs to adapt—embracing strategic roles rooted in culture, ethics, and innovation.
Curious about how One24’s platform supports AI‑driven analytics, micro‑learning, or employee experience tools? Happy to explore it with you!
0 notes
Text
Embedded Systems Industry: Driving Innovation Across Digital Ecosystems
The Embedded Systems Industry is a critical enabler of modern technology, supporting automation, connectivity, and intelligent computing across a wide range of sectors. From controlling basic electronic devices to powering advanced robotics and real-time automotive systems, embedded systems are the invisible backbone of the digital world. The global industry was valued at USD 90.6 billion in 2023 and is expected to grow to over USD 149.3 billion by 2030, advancing at a compound annual growth rate of 7.5.
Emerging Trends in the Embedded Systems Industry
The industry is rapidly evolving with new applications and technologies that expand its reach and functionality. Key trends include:
The rise of AI-powered embedded systems at the edge
Demand for ultra-low power consumption in mobile and wearable devices
Integration of wireless connectivity (Wi-Fi, Bluetooth, Zigbee) into embedded platforms
The adoption of real-time operating systems (RTOS) for time-sensitive applications
Increase in security and cryptographic modules to protect connected devices
These trends are pushing the embedded systems industry into the forefront of innovation in both hardware and software domains.
Segment Insights
By Component
Hardware remains the largest segment, including microcontrollers, digital signal processors, and system-on-chips.
Software is growing as embedded applications demand increasingly complex, secure, and user-friendly interfaces.
By Application
Real-time systems dominate in applications such as autonomous vehicles and industrial robots.
Standalone and networked systems are widely used in consumer electronics and smart appliances.
Industry Applications
Automotive
The automotive industry is a major consumer of embedded systems, using them in advanced driver-assistance systems, infotainment units, powertrain management, and electric vehicle battery systems.
Industrial Automation
Factories and logistics environments depend on embedded systems to drive machine control, process monitoring, and predictive maintenance, enabling Industry 4.0 capabilities.
Consumer Electronics
Embedded systems are integral to devices like smart TVs, mobile phones, gaming consoles, and home appliances, offering intuitive control and energy-efficient operation.
Healthcare
Medical devices from pacemakers to digital diagnostics rely on embedded systems for accuracy, reliability, and real-time patient monitoring.
Aerospace and Defense
Embedded control systems provide stability, responsiveness, and secure communication in military drones, navigation tools, and satellite communication systems.
Regional Outlook
Asia-Pacific is the largest industrial hub for embedded systems, benefiting from strong manufacturing and electronics development.
North America leads in embedded software innovation, particularly in defense, aerospace, and healthcare.
Europe is expanding with investments in automotive and industrial automation.
Latin America, Middle East, and Africa are emerging with increased demand in telecom and consumer technology.
Leading Industry Players
Several companies dominate the global embedded systems industry with diversified portfolios, robust innovation, and strong regional presence:
Intel Corporation
STMicroelectronics
Microchip Technology
Texas Instruments
Renesas Electronics
Arm Holdings
NXP Semiconductors
Cypress Semiconductor
Infineon Technologies
Qualcomm Incorporated
These players continue to develop scalable, secure, and energy-efficient embedded systems for modern applications.
Conclusion
The embedded systems industry is essential to powering the next generation of intelligent and connected technologies. With applications spanning from industrial automation to digital health, embedded systems are becoming more efficient, secure, and adaptive. The industry is poised for sustained growth, fueled by continuous innovation and the rising complexity of digital devices.
Trending Report Highlights
Explore complementary markets helping shape the digital and embedded future:
Barcode Scanner Market
United States Managed Services Market
SEA Robotic Process Automation Market
SEA Led Lighting Market
Hand Tools Market
0 notes
Text

Learning Management System
🎓 Dive into the world of Learning Management Systems! 💻✨ Explore our comprehensive services including Online Learning, Course Creation, Assessment and Quizzes, Easy Reassessment, and much more! 📚💡
https://hypelms.com/learning-management-system/
#RTO software in Australia#Student Management Systems Australia#SMS for RTO#Moodle for RTO#LMS RTO Provider#Learning Management System RTO
0 notes
Text
Unleashing the Power of Student Management Systems: A Comprehensive Guide
In the dynamic landscape of education and training, institutions strive to stay ahead by integrating efficient and robust Student Management Systems (SMS). These systems play a pivotal role in shaping the educational experience, enhancing administrative processes, and ensuring compliance with regulatory standards. In this comprehensive guide, we delve into the intricacies of SMS, explore cutting-edge technologies like cloud-based Learning Management Systems (LMS), and provide insights into the best practices for RTO (Registered Training Organization) software in Australia.
Understanding the Essence: Student Management Systems
Student Management Systems form the backbone of educational institutions, streamlining tasks related to enrollment, assessment, and overall student lifecycle management. These systems act as a centralized hub for administrative processes, allowing educational providers to efficiently handle tasks ranging from student registration to compliance reporting.
The Evolution of SMS in Australia
Australia, being at the forefront of educational innovation, witnesses a surge in demand for advanced RTO software and Learning Management Systems. The need for streamlined processes, compliance adherence, and enhanced user experience has led to the evolution of cloud-based solutions tailored to the unique requirements of Australian educational institutions.
Navigating the Educational Technosphere: Key Terminologies
Cloud LMS: Redefining Accessibility
Cloud-based Learning Management Systems revolutionize the educational landscape by providing unparalleled accessibility and scalability. Institutions benefit from the flexibility of accessing educational resources and administrative tools from any location, fostering a seamless learning experience.
RTO Compliance Software: Ensuring Regulatory Adherence
In the realm of Registered Training Organizations, compliance is paramount. RTO Compliance Software emerges as a game-changer, offering features that automate reporting, track student progress, and ensure adherence to AVETMISS standards. This not only simplifies administrative tasks but also positions institutions as leaders in compliance excellence.
Unveiling the Gems: Features of Leading SMS and LMS
Cloud LMS Software in Australia: A Technological Marvel
Cloud LMS Software in Australia combines innovation and functionality, offering a feature-rich platform for educational institutions. From content delivery to real-time analytics, these systems empower educators and administrators alike.
RTO Management System: A Holistic Approach
An effective RTO Management System integrates student data management, assessment tracking, and compliance reporting. It acts as a centralized hub, promoting efficiency and transparency in operations.
Choosing the Right Tools: Considerations for Educational Providers
Assessments for RTOs: Elevating Evaluation Processes
In the ever-evolving educational landscape, the role of assessments cannot be overstated. Assessment Management Systems for RTOs redefine evaluation processes, providing tools for creating, administering, and analyzing assessments seamlessly.
Online Enrolment Software Australia: Simplifying Admissions
The digital era demands streamlined processes, and Online Enrolment Software in Australia answers this call. Institutions benefit from simplified admissions, reduced paperwork, and enhanced efficiency in managing student enrollment.
Staying Ahead: Best Practices and Recommendations
Course Management Software in Australia: Tailoring Educational Offerings
For institutions aiming to offer diverse courses, Course Management Software in Australia becomes a strategic ally. This software enables educational providers to design, deliver, and manage courses effectively.
LMS Providers in Australia: Choosing Wisely
Selecting the right LMS provider is pivotal for institutions seeking to enhance the learning experience. A thorough evaluation of features, user interface, and customer support ensures a seamless integration into the educational ecosystem.
The Road Ahead: Embracing Innovation
As educational technology continues to advance, institutions must embrace innovation to stay competitive. The integration of AMS Online and Online Training Platforms in Australia opens new avenues for collaborative learning, real-time feedback, and personalized educational experiences.
Conclusion
In the ever-evolving educational landscape of Australia, leveraging advanced Student Management Systems and Learning Management Systems is not just a choice but a strategic imperative. Institutions that invest in cutting-edge technology, embrace cloud-based solutions, and adhere to compliance standards position themselves as leaders in the realm of education and training.
0 notes
Text
Seamless Integration with EtherCAT Master Technology
In today’s fast-paced industrial landscape, the ability to integrate systems with minimal complexity and maximum performance is not just beneficial — it’s essential. As industries adopt smarter, more agile automation solutions, EtherCAT Master technology is emerging as the gold standard for achieving high-speed, synchronized control across a wide array of devices and applications.
What is EtherCAT Master Technology?
EtherCAT (Ethernet for Control Automation Technology) is an open, real-time Ethernet-based fieldbus system developed for automation applications. At the heart of every EtherCAT network lies the EtherCAT Master, which acts as the central controller that manages all communication and synchronization between slave devices such as sensors, actuators, drives, and PLCs.
The EtherCAT Master sends out a data packet that travels through all devices and returns with status updates, ensuring real-time control with minimal latency and jitter.
Why Seamless Integration Matters
In industrial environments, integration isn't just about plugging devices into a network — it's about ensuring those devices can communicate effectively, reliably, and without unnecessary delays. Seamless integration with an EtherCAT Master offers:
Plug-and-Play Connectivity: Most EtherCAT-compatible devices are designed for rapid configuration and interoperability, enabling quick setup and reduced engineering time.
Real-Time Communication: Achieve deterministic data exchange that ensures systems respond in real-time — critical for applications like motion control, robotics, and CNC.
Hardware & Software Compatibility: Modern EtherCAT Masters are compatible with a broad range of automation components and support various operating systems including Windows and real-time operating systems (RTOS).
Scalability: As systems grow or change, EtherCAT networks can be expanded easily without impacting performance, allowing industries to scale operations without redesigning infrastructure.
Key Benefits of EtherCAT Master Integration
Low Latency and High Precision EtherCAT Masters deliver cycle times as low as 100 µs, enabling tight synchronization across distributed nodes — ideal for high-speed manufacturing or robotic control.
Simplified Network Design The daisy-chain architecture of EtherCAT reduces the need for complex switches or hubs, resulting in simpler wiring and lower installation costs.
Robust Diagnostics and Monitoring Built-in monitoring features enable quick detection of failures, cable breaks, or device malfunctions, improving uptime and maintainability.
Cost Efficiency By using standard Ethernet hardware and cables, EtherCAT reduces the cost of integration compared to proprietary solutions.
Applications of Seamless EtherCAT Integration
Industrial Automation: From packaging lines to material handling, seamless EtherCAT Master integration improves responsiveness and reliability.
Robotics: Enables tight coordination between axes and components, improving accuracy and performance.
CNC Machines: Provides the speed and synchronization needed for precision cutting, milling, and forming.
Testing and Measurement Systems: Real-time data acquisition and control for high-speed, data-driven environments.
Conclusion
Whether you're building a new automation system or upgrading an existing one, seamless integration with EtherCAT Master technology offers unmatched speed, flexibility, and reliability. By reducing complexity and boosting performance, it enables manufacturers to stay competitive in an increasingly connected and automated world. https://kingstar.com/products/ethercat/
Interested in learning how EtherCAT Master integration can transform your operations? Visit us or get in touch:
200 Fifth Avenue, FL 6, STE 6020 Waltham, MA 02451 Phone: +1 781 209 2810 Fax: +1 781 795 0158 Email: [email protected]
0 notes
Text
How a Computer Repairs Service Can Save Your Business from Tech Disasters
In today’s digital-first world, your business might be just one unexpected glitch away from crippling downtime, data loss, or even customer trust erosion. A well‑equipped computer repair service can be the shield safeguarding your operations from such tech disasters. This article explores how partnering with a reliable service goes beyond fixing laptops—it offers strategic resilience, proactive prevention, and swift recovery in the moments that matter most.

Computer Repairs Service
1. Digital Threats Looming: Why You Need a Computer Repairs Service
Every business—whether a bustling retail store or a boutique agency—relies heavily on computers, networks, and data. But technology isn't infallible:
Hardware failure: Hard drives have a finite lifespan; power surges and overheating can wreck even newer machines.
Cyberattacks: Malware, ransomware, phishing—these can bring operations to a grinding halt overnight.
Human error: Accidental file deletion, misconfiguration, or system mismanagement are more common than you think.
Without expert support on call, these issues can escalate into full-blown crises. That’s where a dependable computer repairs service steps in, preventing, diagnosing, and remediating complex tech failures before they snowball.
2. Rapid Response Cuts Downtime
Downtime is the silent revenue drainer. Every minute your systems are offline, you risk stalled transactions, frustrated customers, and lost income.
A professional computer repair service provides:
Fast triage and diagnosis: Skilled technicians pinpoint the root cause—whether it’s a corrupted system file or a failing hard drive—with efficiency.
On‑site or remote repair: Whether they dispatch a technician to your office or fix issues remotely, service is swift and flexible.
Priority access: In urgency, they're the equivalent of a 24/7 emergency crew—no waiting days for help.
Example: A retailer facing point‑of‑sale system failure at midday can have a tech on‑site within hours, restoring sales before the lunch rush ends.
3. Fortify Together: IT Disaster Recovery & Data Backup
A core offering of a quality computer repair service is establishing a robust disaster recovery or business continuity plan. This includes:
3.1 Regular, Automated Backups
Daily or hourly backups replicate data across internal servers, external drives, or secure off‑site/cloud storage.
Mirroring vital files ensures no single hardware failure jeopardizes your business.
3.2 Recovery Point Objectives (RPO)
Your IT partner helps you determine acceptable data loss windows—for example, “max 30 minutes of data” at risk.
3.3 Recovery Time Objectives (RTO)
With an agreed RTO (e.g., “systems back online in under 2 hours”), they tailor processes and tools to meet it.
Source: Ready.gov emphasizes making such IT recovery strategies central to business planning cbh.com.
4. Proactive Protection Prevents Disasters
Beyond post‑breakdown fixes, a professional computer repairs service should help you build defences:
System health audits: They monitor hard drives, battery status, and cooling systems to preempt hardware failure.
Security reviews: They ensure security patches, antivirus software, network firewalls, and multi-factor authentication (MFA) are in place and updated.
User policy & training: Teaching staff to click safely, not ignore warnings, and report anomalies can minimize human error.
Source: Managed IT services experts recommend regular audits, cyber hygiene, and tabletop exercises to identify weak points.
5. Cyberattack Response: Fast & Forensic
Imagine your business falls prey to ransomware—your files get encrypted, a ransom note appears, and panic sets in. This is where your computer repairs service makes the difference:
Containment: Disconnect infected systems to stop the spread.
Assessment: Evaluate damage—encrypted data, network impact, and backup viability.
Recovery: Use clean backups to restore systems, reinstall software, and secure endpoints.
Cleanup: Remove malware, apply patches, and install additional safeguards like enhanced firewalls and EDR tools.
Documentation & closure: Report on what happened and how further incidents will be prevented.
This holistic response saves businesses from paying ransoms and reduces disruption—and it's a major reason to engage with a tech-savvy computer repairs service proactively.
6. Data Recovery: Salvaging Lost Information
Sometimes, hardware failure strikes severely—hard drives with critical data crash or become unreadable.
A professional computer repair service often includes:
Advanced data-recovery tools and tried-and-tested methods.
Specialist rescue labs for emergencies like physical disk damage.
Tests to confirm recovered data integrity before treating it as business-ready.
7. Compliance & Audit Support
For regulated industries—law, finance, healthcare—demonstrating IT safeguards isn’t optional. A trusted computer repairs service assists by:
Providing audit-ready documentation of backups, incident logs, patch updates, and user training.
Certifying data protection mechanisms (encryption, MFA, firewall rules).
Supporting compliance frameworks like GDPR, HIPAA, or ISO 27001.
This structured approach simplifies audits and demonstrates due diligence in keeping clients’ data safe.
8. Tailored Care: No-Surprise Service Agreements
The best tech partnerships are built on trust and transparency:
Service-level agreements (SLAs) define response times, update schedules, and reporting cycles.
Scheduled “health check” visits, monthly reports, and yearly strategy reviews help keep your IT aligned with growth plans.
Flexible pricing models—hourly, block hours, or managed monthly plans—ensure your tech spending is predictable.
These guard against unexpected repair costs and make long‑term planning smoother.
9. Real-World Case Studies
1. E‑commerce Business
A mid-sized online retailer struggled with slow SQL database performance. The computer repairs service performed:
System optimization to remove inefficiencies.
Scheduled backups tied into cloud storage.
24/7 monitoring to prevent repeat issues.
Result: 60% reduction in downtime and a smoother customer experience.
2. Professional Services Firm
After being hit with ransomware, they turned to a repair service that:
Cleared the malware and segmented the threat.
Used backups to restore all systems within a few hours.
Added system hardening and multi-factor authentication.
Result: No ransom paid; lessons learned and systems fortified.
10. Choosing the Right Computer Repairs Service
Key questions to ask before you commit:
Criterion Why It Matters:-
Response Time : How quickly can they act in an emergency?
Backup Strategy : Are backups frequent, secure, and tested?
Security Protocols : Do they review vulnerabilities, patch regularly, and support MFA?
Expertise Level : Can they manage hardware, software, network, and cloud?
Incident Handling : Is there a defined recovery workflow after cyberattacks?
Client Reviews : Are past customers satisfied with their preventative and responsive service?
Conclusion
In a digital-first economy, every business runs on technology. A trusted computer repair service is more than a tech fixer—it’s your strategic partner against downtime, cyber threats, data loss, and compliance violations. From immediate hardware repair to comprehensive data recovery and security planning, such a service safeguards your operational continuity and your reputation.
#Computer Repairs Service#Best Computer Repairs Service For Business#Affordable Computer Repairs Service#Computer Repair
0 notes
Text
Powering the Future of Mobility: A Deep Dive into the Automotive Hypervisor Market
The automotive industry is undergoing a monumental transformation, shifting from hardware-centric vehicles to sophisticated, software-defined machines. At the heart of this evolution lies the automotive hypervisor – a crucial technology enabling the consolidation of diverse electronic control units (ECUs) and the seamless, secure operation of multiple software systems on a single hardware platform. This blog post delves into the automotive hypervisor market, offering a comprehensive look at its growth drivers, key trends, challenges, and future outlook.
The Genesis of Automotive Hypervisors: Why Now?
Historically, vehicles were a collection of discrete, single-function ECUs. As cars became more complex with the advent of advanced driver-assistance systems (ADAS), infotainment systems, connectivity features, and eventually autonomous driving capabilities, the number of ECUs proliferated, leading to increased complexity, weight, wiring, and cost. This is where automotive hypervisors step in.
A hypervisor, essentially a software layer, allows multiple operating systems (OS) and applications to run concurrently and independently on a single piece of hardware. In an automotive context, this means that safety-critical functions (like braking and steering) can run on one virtual machine with a real-time operating system (RTOS), while less critical functions (like infotainment) can run on another virtual machine with a different OS (e.g., Linux or Android Automotive OS), all sharing the same underlying hardware. This isolation is paramount for functional safety and cybersecurity.
Key Drivers Fueling the Hypervisor Boom
Several factors are converging to accelerate the adoption of automotive hypervisors:
Increasing Complexity of In-Vehicle Electronics: Modern vehicles are mini-supercomputers on wheels, packed with sophisticated ADAS, advanced infotainment, and connectivity features. Hypervisors are essential for managing this escalating complexity, enabling efficient execution of diverse applications on fewer, more powerful ECUs.
Rise of Software-Defined Vehicles (SDVs): SDVs promise a future where vehicle functionalities are primarily driven by software, allowing for over-the-air (OTA) updates, new feature deployments, and personalized experiences throughout the vehicle's lifespan. Hypervisors are foundational to SDVs, providing the flexibility and isolation needed for this dynamic software environment.
Growing Demand for Advanced Driver-Assistance Systems (ADAS) and Autonomous Driving: These systems require immense processing power, real-time performance, and strict safety assurances. Hypervisors enable the consolidation of ADAS functions and the isolation of safety-critical components, crucial for achieving higher levels of autonomy.
Enhanced Safety and Cybersecurity Concerns: With increased connectivity comes increased vulnerability to cyber threats. Hypervisors play a vital role in isolating critical systems from non-critical ones, preventing malicious attacks or software failures from compromising essential vehicle operations. Regulatory standards like ISO 26262 (functional safety) and ISO 21434 (cybersecurity) further push the adoption of hypervisor solutions.
ECU Consolidation and Cost Optimization: By allowing multiple functions to run on a single hardware platform, hypervisors enable automakers to reduce the number of physical ECUs, leading to lower manufacturing costs, reduced weight, and simplified wiring harnesses.
Electrification of Vehicles (EVs): Electric vehicles demand advanced software management for battery management, power distribution, and in-car connectivity. Hypervisors are instrumental in managing these diverse systems efficiently.
Get Free Sample For Automotive Hypervisor Market- https://www.theinsightpartners.com/sample/TIPRE00004120
Challenges on the Road Ahead
Despite the promising outlook, the automotive hypervisor market faces certain challenges:
High Development and Integration Costs: Designing, developing, and integrating hypervisor solutions into complex automotive architectures can be resource-intensive, particularly when dealing with legacy systems.
Interoperability and Standardization: Ensuring seamless interoperability between hypervisors, different operating systems, and various hardware components from diverse vendors remains a challenge. The lack of universal standards can complicate development and deployment.
Cybersecurity and Data Privacy Concerns: While hypervisors enhance security through isolation, the hypervisor itself becomes a critical attack surface. Robust security measures and continuous updates are crucial to mitigate risks.
Regulatory Compliance: Meeting stringent functional safety standards like ISO 26262 requires rigorous testing and validation, adding to the development timeline and costs.
Leading the Charge: Key Players
The automotive hypervisor market features a competitive landscape with several prominent players. Some of the key companies driving innovation in this space include:
DENSO CORPORATION
Green Hills Software
LUXOFT
Mentor
NXP Semiconductors
Renesas Electronics Corporation
Sasken Technologies Ltd
TCL Communication
Visteon Corporation
Recent developments in the market include acquisitions (e.g., Qualcomm acquiring virtualization assets from OpenSynergy) and collaborations aimed at enhancing safety-critical functions and accelerating the development of software-defined vehicles.
The Road Ahead: A Software-Defined Future
The automotive hypervisor market is undeniably poised for significant expansion. As vehicles become increasingly intelligent, connected, and autonomous, the demand for robust, secure, and efficient virtualization solutions will only intensify. The future of mobility hinges on the ability to manage complex software ecosystems, and automotive hypervisors are the unsung heroes making this transformation a reality. Companies that can effectively address the challenges of integration, standardization, and cybersecurity while delivering innovative and cost-effective solutions will be well-positioned to capitalize on this burgeoning market. The journey towards a fully software-defined vehicle is a marathon, and automotive hypervisors are paving the way.
0 notes
Text

Comparison of Ubuntu, Debian, and Yocto for IIoT and Edge Computing
In industrial IoT (IIoT) and edge computing scenarios, Ubuntu, Debian, and Yocto Project each have unique advantages. Below is a detailed comparison and recommendations for these three systems:
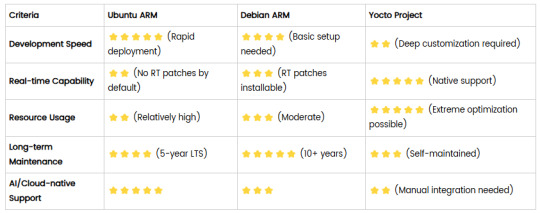
1. Ubuntu (ARM)
Advantages
Ready-to-use: Provides official ARM images (e.g., Ubuntu Server 22.04 LTS) supporting hardware like Raspberry Pi and NVIDIA Jetson, requiring no complex configuration.
Cloud-native support: Built-in tools like MicroK8s, Docker, and Kubernetes, ideal for edge-cloud collaboration.
Long-term support (LTS): 5 years of security updates, meeting industrial stability requirements.
Rich software ecosystem: Access to AI/ML tools (e.g., TensorFlow Lite) and databases (e.g., PostgreSQL ARM-optimized) via APT and Snap Store.
Use Cases
Rapid prototyping: Quick deployment of Python/Node.js applications on edge gateways.
AI edge inference: Running computer vision models (e.g., ROS 2 + Ubuntu) on Jetson devices.
Lightweight K8s clusters: Edge nodes managed by MicroK8s.
Limitations
Higher resource usage (minimum ~512MB RAM), unsuitable for ultra-low-power devices.
2. Debian (ARM)
Advantages
Exceptional stability: Packages undergo rigorous testing, ideal for 24/7 industrial operation.
Lightweight: Minimal installation requires only 128MB RAM; GUI-free versions available.
Long-term support: Up to 10+ years of security updates via Debian LTS (with commercial support).
Hardware compatibility: Supports older or niche ARM chips (e.g., TI Sitara series).
Use Cases
Industrial controllers: PLCs, HMIs, and other devices requiring deterministic responses.
Network edge devices: Firewalls, protocol gateways (e.g., Modbus-to-MQTT).
Critical systems (medical/transport): Compliance with IEC 62304/DO-178C certifications.
Limitations
Older software versions (e.g., default GCC version); newer features require backports.
3. Yocto Project
Advantages
Full customization: Tailor everything from kernel to user space, generating minimal images (<50MB possible).
Real-time extensions: Supports Xenomai/Preempt-RT patches for μs-level latency.
Cross-platform portability: Single recipe set adapts to multiple hardware platforms (e.g., NXP i.MX6 → i.MX8).
Security design: Built-in industrial-grade features like SELinux and dm-verity.
Use Cases
Custom industrial devices: Requires specific kernel configurations or proprietary drivers (e.g., CAN-FD bus support).
High real-time systems: Robotic motion control, CNC machines.
Resource-constrained terminals: Sensor nodes running lightweight stacks (e.g., Zephyr+FreeRTOS hybrid deployment).
Limitations
Steep learning curve (BitBake syntax required); longer development cycles.
4. Comparison Summary
5. Selection Recommendations
Choose Ubuntu ARM: For rapid deployment of edge AI applications (e.g., vision detection on Jetson) or deep integration with public clouds (e.g., AWS IoT Greengrass).
Choose Debian ARM: For mission-critical industrial equipment (e.g., substation monitoring) where stability outweighs feature novelty.
Choose Yocto Project: For custom hardware development (e.g., proprietary industrial boards) or strict real-time/safety certification (e.g., ISO 13849) requirements.
6. Hybrid Architecture Example
Smart factory edge node:
Real-time control layer: RTOS built with Yocto (controlling robotic arms)
Data processing layer: Debian running OPC UA servers
Cloud connectivity layer: Ubuntu Server managing K8s edge clusters
Combining these systems based on specific needs can maximize the efficiency of IIoT edge computing.
0 notes
Text
0 notes