#for one year validity voice calling and internet data
Explore tagged Tumblr posts
Text
Avoid These Common SIP Trunk Configuration Mistakes
For businesses in Hyderabad looking to enhance their communication systems, implementing a SIP trunk is a smart move. However, the success of your SIP trunk depends heavily on proper SIP trunk configuration. Incorrect setup can lead to poor call quality, dropped calls, and security vulnerabilities that disrupt your business operations.
At A1 Routes, we specialize in seamless SIP trunk configuration to ensure your business enjoys crystal-clear calls and uninterrupted connectivity. To help you avoid costly errors, here are some common SIP trunk configuration mistakes and how to prevent them.
1. Ignoring Network Requirements
One of the biggest mistakes businesses make during SIP trunk configuration is neglecting the underlying network setup. SIP trunks rely on stable internet connectivity and adequate bandwidth. Without proper network quality of service (QoS) settings, voice traffic may compete with other data, resulting in latency, jitter, or packet loss.
Tip: Work with a provider like A1 Routes that assesses your network and configures QoS to prioritize voice traffic, ensuring superior call quality.
2. Incorrect Firewall and NAT Settings
Firewall and Network Address Translation (NAT) issues are common causes of failed or dropped SIP trunk calls. Incorrectly configured firewalls can block SIP traffic or the necessary ports, while improper NAT settings may cause one-way audio problems.
Tip: During SIP trunk configuration, verify that your firewall allows the correct SIP and RTP port ranges, and that NAT traversal is properly set up. A1 Routes’ experts handle these configurations to prevent call failures.
3. Using Default or Weak Security Settings
SIP trunks are vulnerable to security threats such as toll fraud, eavesdropping, and denial of service attacks if not properly secured. Using default passwords or neglecting encryption during configuration leaves your system exposed.
Tip: Always customize passwords, enable TLS/SRTP encryption, and implement IP-based authentication. A1 Routes prioritizes secure SIP trunk configuration to protect your business communications.
4. Not Testing Before Going Live
Skipping thorough testing after your SIP trunk configuration can lead to unexpected issues once your system goes live. Problems like poor call quality, registration failures, or incorrect call routing may arise if configurations are not properly validated.
Tip: Conduct comprehensive testing, including inbound/outbound calls, failover scenarios, and audio quality checks. Our Hyderabad-based team at A1 Routes performs detailed pre-launch testing to ensure smooth deployment.
5. Overlooking Proper Documentation
Failing to document your SIP trunk configuration settings can cause delays and confusion during troubleshooting or future upgrades. Without clear records, resolving issues or scaling your system becomes unnecessarily complex.
Tip: Maintain detailed documentation of all configuration parameters, including IP addresses, ports, credentials, and routing rules. A1 Routes provides clear documentation for every client to simplify ongoing management.
Why Choose A1 Routes for SIP Trunk Configuration in Hyderabad?
Setting up a SIP trunk requires technical expertise and attention to detail. With years of experience, A1 Routes helps businesses in Hyderabad avoid common pitfalls through expert SIP trunk configuration and ongoing support. Our team ensures your communication system is reliable, secure, and optimized for the best call quality.
#high-quality sip trunks#international calling solutions#reliable sip trunking provider#sip trunk#sip trunk configuration
0 notes
Text
Hackers' code-free exploit: pretend to be cops

Back in 1994, Bill Clinton signed CALEA into law, mandating that all switches capable of carrying voice-traffic include a “lawful interception” backdoor that would let cops listen in on phone calls without having to actually physically access the switch itself.
https://en.wikipedia.org/wiki/Communications_Assistance_for_Law_Enforcement_Act
CALEA came with three promises:
The backdoor would only be used by cops;
They would get a warrant first;
It would only apply to voice traffic, not the internet.
All of these promises were lies. Anyone who’s ever watched a detective show where a PI says, “I have a cop who can run that license plate” knows that if you give cops oversight-free, unaudited access to a database, you’re also giving access to anyone any cop owes (or sells) a favor to.
When CALEA passed, its opponents warned that a “voice capable” switch would soon be indistinguishable from an “internet” switch. Less than a decade later, the FBI successfully argued that all internet switches were now capable of carrying voice traffic, so they, too, must have CALEA backdoors.
That didn’t just expose Americans to surveillance by cops, their friends, and anyone who gained access by pressuring or impersonating a cop. Vendors installed CALEA backdoors in all their switches, to ensure that they could access the US market. These backdoors made their way into countries without CALEA mandates, where they were abused.
Most notoriously: the Greek government and prime minister were wiretapped in 2004 in order to sabotage the Greek Olympics bid. Greece doesn’t have CALEA on its law-books, but it did have CALEA-compliant switches in its telephone network.
https://www.schneier.com/blog/archives/2007/07/story_of_the_gr_1.html
Any time you mandate “extraordinary access” to an otherwise secure system, you create an opportunity for exploitation by criminals, spies, and snoops.
Take the “Emergency Data Request” (EDR), a US system that allows cops to demand warrantless access to your online account data. This is supposed to be used in white-hot emergencies, like kidnappings or Jack Bauer-style hypotheticals where there’s a ticking bomb and only warrantless access will let you defuse it.
By their nature, EDRs are meant to be obeyed without a sanity-check or other verification. When a provider gets an EDR from a cop, they’re supposed to hop to, because the alternative might abet a murder or other grave crime.
If a provider thinks an EDR is legit, they’ll honor it. But with 18,000 US police agencies, there’s no way to validate and EDR a priori, and if just one of those police agencies suffers a breach, anyone who can exploit it can issue their own EDRs.
Ever hear of LAPSUS$? That’s the notorious hacker gang (which appears to have been helmed and operated primarily by teenagers) that has been on a planet-wide rampage, stealing and dumping sensitive data and blackmailing its targets, from governments to corporations to individuals.
https://www.wired.com/story/lapsus-okta-hack-sitel-leak/
LAPUS$’s methods have been a mystery, but now, Brian Krebs has shed some light on how the gang pulled off its data-heists: they pretended to be cops, and issued EDRs to service providers, who just handed over the data they needed to break into agencies, companies, and personal accounts.
https://krebsonsecurity.com/2022/03/hackers-gaining-power-of-subpoena-via-fake-emergency-data-requests/
In 2021, a criminal connected to LAPUS$ — a 14 year old who used the handle Everlynn — advertised that they could generate EDRs from a real law-enforcement agency, and sold this capability to would-be hackers for $150.
Everlynn understood something that the creators of EDRs did not. In their sales pitch, they wrote, “This is very illegal and you will get raided if you don’t use a vpn. You can also breach into the government systems for this, and find LOTS of more private data and sell it for way, way more.”
Everlynn’s identity was revealed by a dox attack allegedly launched by “White,” a founder of LAPUS$; they were colleagues in an earlier hacking group called Recursion Team. White, in turn, was allegedly outed by the staff who worked under him at a site called Doxbin, who were upset that White’s mismanagement exposed the site’s user database. These children aren’t criminal mastermind prodigies, in other words: they’re normal, fallible people, who nevertheless gained access to LDR facilities that compromised governments, corporations and individuals around the world.
Everlynn isn’t the only bad actor using EDRs to compromise accounts. One of Krebs’s sources, who goes by KT, reports that this is a common tactic, and the go-to pretense is “Terroristic threats with a valid reason to believe somebody’s life is in danger.”
Among the targets successfully compromised with this tactic is Discord, which was induced to reveal sensitive user information in less than 30 minutes. Discord admitted to Krebs that it had been fooled: “we later learned that [the law enforcement account that sent the EDR] had been compromised by a malicious actor.”
How do bad actors gain access to police emails? The same way they gain access to any service: compromising the website and installing a reverse shell; guessing passwords; or recycling passwords breached from other services.
Krebs’s expert sources are pessimistic about the possibility of fixing the EDR system. Former DoJ prosecutor Mark Rasch told him that “spotting unauthorized EDRs would require these companies to somehow know and validate the names of every police officer in the United States.”
UC Berkeley’s Nicholas Weaver told Krebs that securing EDRs is “a fundamentally unfixable problem without completely redoing how we think about identity on the Internet on a national scale.”
This is a lesson as old as CALEA — if you create a backdoor that tens of thousands of people can access, then you create a backdoor that anyone can access, because it’s impossible to prevent the impersonation, subordination, or corruption of that many people.
Image: Paulo Valdivieso (modified) https://www.flickr.com/photos/p_valdivieso/42906748201/
CC BY-SA 2.0: https://creativecommons.org/licenses/by-sa/2.0/
82 notes
·
View notes
Text
5m Mathmrs. Mac's Messages

TLDR: With a bit of research and support we were able to demonstrate a proof of concept for introducing a fraudulent payment message to move £0.5M from one account to another, by manually forging a raw SWIFT MT103 message, and leveraging specific system trust relationships to do the hard work for us!
5m Mathmrs. Mac's Messages App
5m Mathmrs. Mac's Messages Message
5m Mathmrs. Mac's Messages To My
5m Mathmrs. Mac's Messages For Her
Before we begin: This research is based on work we performed in close-collaboration with one of our clients; however, the systems, architecture, and payment-related details have been generalized / redacted / modified as to not disclose information specific to their environment.
A desktop application for Instagram direct messages. Download for Windows, Mac and Linux.
Have a question, comment, or need assistance? Send us a message or call (630) 833-0300. Will call available at our Chicago location Mon-Fri 7:00am–6:00pm and Sat 7:00am–2:00pm.
5m Mathmrs. Mac's Messages App
With that said.. *clears throat*
The typical Tactics, Techniques and Procedures (TTPs) against SWIFT systems we see in reports and the media are - for the most part - the following:
Compromise the institution's network;
Move laterally towards critical payment systems;
Compromise multiple SWIFT Payment Operator (PO) credentials;
Access the institution's SWIFT Messaging Interface (MI);
Keys in - and then authorize - payment messages using the compromised PO accounts on the MI.
This attack-path requires the compromise of multiple users, multiple systems, an understanding of how to use the target application, bypass of 2FA, attempts to hide access logs, avoid alerting the legitimate operators, attempts to disrupt physical evidence, bespoke malware, etc. – so, quite involved and difficult. Now that’s all good and fine, but having reviewed a few different payment system architectures over the years, I can’t help but wonder:
“Can't an attacker just target the system at a lower level? Why not target the Message Queues directly? Can it be done?”
A hash-based MAC might simply be too big. On the other hand, hash-based MACs, because they are larger, are less likely to have clashes for a given size of message. A MAC that is too small might turn out to be useless, as a variety of easy-to-generate messages might compute to the same MAC value, resulting in a collision. WhatsApp Messenger is a FREE messaging app available for iPhone and other smartphones. WhatsApp uses your phone's Internet connection (4G/3G/2G/EDGE or Wi-Fi, as available) to let you message and call friends and family. Switch from SMS to WhatsApp to send and receive messages, calls, photos, videos, documents, and Voice Messages. WHY USE WHATSAPP. Garrick Hello, I'm Garrick Chow, and welcome to this course on computer literacy for the Mac. This course is aimed at the complete computer novice, so if you're the sort of person who feels some mild anxiety, nervousness, or even dread every time you sit down in front of your computer, this course is for you.
Well, let's find out! My mission begins!
So, first things first! I needed to fully understand the specific “section” of the target institution's payment landscape I was going to focus on for this research. In this narrative, there will be a system called “Payment System” (SYS). This system is part of the institution's back-office payment landscape, receiving data in a custom format and output's an initial payment instructions in ISO 15022 / RJE / SWIFT MT format. The reason I sought this scenario was specifically because I wanted to focus on attempting to forge an MT103 payment message - that is:
In this video I will show you where to locate the serial number on a Western golf cart. Ebay Store: Please SUBSCRIBE. Western golf cart serial number lookuplastevil.
MT – “Message Type” Literal;
1 – Category 1 (Customer Payments and Cheques);
0 – Group 0 (Financial Institution Transfer);
3 – Type 3 (Notification);
All together this is classified as the MT103 “Single Customer Credit Transfer”.
Message type aside, what does this payment flow look like at a high level? Well I’ve only gone and made a fancy diagram for this!
Overall this is a very typical and generic architecture design. However, let me roughly break down what this does:
The Payment System (SYS) ingests data in a custom - or alternative - message format from it's respective upstream systems. SYS then outputs an initial payment instruction in SWIFT MT format;
SYS sends this initial message downstream to a shared middelware (MID) component, which converts (if necessary) the received message into the modern MT format understood by SWIFT - Essentially a message broker used by a range of upstream payment systems within the institution;
MID forwards the message in it's new format on to the institution's Messaging Interface (let's say its SAA in this instance) for processing;
Once received by SAA, the message content is read by the institution's sanction screening / Anti-money laundering systems (SANCT).
Given no issues are found, the message is sent on to the institution's Communication Interface (SWIFT Alliance Gateway), where it's then signed and routed to the recipient institution over SWIFTNet.
OK, so now I have a general understanding of what I'm up against. But if I wanted to exploit the relationships between these systems to introduce a fraudulent payment without targeting any payment operators, I was going to need to dig deeper and understand the fundamental technologies in use!
So how are these messages actually 'passed' between each system? I need to know exactly what this looks like and how its done!
More often than not, Message Queues (MQ) are heavily used to pass messages between components in a large payment system. However, there are also various “Adapter” that may be used between systems communicating directly with the SAG (Such as SAA or other bespoke/3rd party systems). These are typically the:
Remote API Host Adapter (RAHA);
MQ Host Adapter (MQHA);
Web Services Host Adapter (WSHA).
Having identified that MQ was in use, my initial assumption was that there was most likely a dedicated Queue Manager (QM) server somewhere hosting various queues that systems push and pull messages from? However, due to SWIFT CSP requirements, this would most likely - at a minimum - take the form of two Queue Managers. One which manages the queues within the SWIFT Secure Zone, and another that manages queues for the general corporate network and back office systems.
Let's update that diagram to track / represent this understanding: Now I could research how this 'messaging' worked!
There are multiple ways to configure Message Queues architectures, in this case there were various dedicated input and output queues for each system, and the message flow looks something like this: Full disclosure, turns out it’s hard to draw an accurate - yet simple - MQ flow diagram (that one was basically my 4th attempt). So it’s.. accurate 'enough' for what we needed to remember!
5m Mathmrs. Mac's Messages Message
Now I had a good understanding of how it all worked, it is time to define my goal: 'Place a payment message directly on to a queue, and have it successfully processed by all downstream systems'.
This sounds simple, just write a message to a queue, right? But there are a few complications!
Why are there few indications of this attack vector in the wild?
How do I even gain “write” access to the right queue?
What protects the message on the queues?
What protects the messages in transit?
What format are the messages in?
What is the correct syntax for that message format at any particular queue (0 margin for error)?
Where does PKI come in? How / where / when are the messages signed?
Can I somehow get around the message signing?
What values in the messages are dependent / controlled / defined by the system processing them (out of my control)?
What is the maximum amount I can transfer using Straight Through Processing, without alerting the institution / requiring manual validation?
But OK, there's no point dwelling on all of that right now, I'll just clearly define what I want to do! The goal:
Successfully write a payment instruction for 500,000 GBP;
Inject that message directly onto a specific queue;
Have the message pass environment-specific validation rules;
Have the message pass sanctions and AML checks.
Have the message successfully signed;
Have the message pass SWIFTNet-specific validation rules;
What I was not interested in doing for this research - yet needed to understand nevertheless for a full attack chain was:
How to compromise the institution's network;
How to gain access to the MQ admin's workstation;
How to obtain the pre-requisite credentials.
What I wanted to 100% avoid at all costs:
The attack involving SWIFT payment operators in any way;
The attack involving SWIFT application access in any way;
A need to compromise signing keys / HSMs;
A need to compromise SWIFTNet operator accounts or certificates or any type of PKI;.
Now I had an idea of what to do, I needed to make sure I could write a raw MT103 payment instruction! Typically, even when operators write payment messages using a messaging interface application like Alliance Access, they only really write the message “body” via a nice GUI. As raw data this could look something like:
I'll break this down in the following table:
NameFieldValueTransaction Reference20TRANSACTIONRF103Bank Operation Code23BCRED (Message is to 'credit' some beneficiary)Value Date / Currency / Amount32A200102 (02/01/2020) GBP 500,000.00Currency / Original Credit Amount33BGBP 500000,00 (£500,000.00)Ordering Customer50KGB22EBNK88227712345678 (IBAN) JOHN DOE (Name) JOHN'S BUSINESS LTD (Line 1) 21 JOHN STREET, LONDON, GB (Line 2)Beneficiary59KFR20FBNK88332287654321 (IBAN) ALICE SMITH (Name) ALICE'S COMPANY (Line 1) 10 ALICE STREET, PARIS, FR (Line 2)Remittance Information7012345-67890 (essentially a payment reference)Details of Charge71ASHA (Shared charge between sender and receiver)
Now as this is a valid message body, if I were targeting a payment operator on SWIFT Alliance Access, I could - for the 'most' part - simply paste the message into SAA's raw message creation interface and I'd be pretty much done. With the exception of adding the sender / recipient BIC codes and most likely selecting a business unit. However, these values are not stored in the message body. Not stored in the message body you say? Well that complicates things! Where are they stored exactly?
The message “body” is referred to as “block 4” (aka the “Text Block”) within the SWIFT MT standard. As suggested by the name, there is probably also a block 1-3. This is correct; and these blocks are typically generated by the payment processing applications - such as SWIFT Alliance Access - and not necessarily input by the operators. A 'complete' MT103 message consists of 6 blocks:

Block 1 – Basic Header
Block 2 – Application Header
Block 3 – User Header
Block 4 – Text Block
Block 5 – Trailer
Block 6 – System block
So it looked like I was going to need to learn how to craft these various “blocks” from scratch.
Block 1 (Basic header)
Reading through some documentation, I crafted the following “Basic header” block:
A breakdown of what this translates too is as follows:
NameValueContextBasic Header Flag1Block 1 (Not 2, 3, 4, or 5)Application TypeFFIN ApplicationMessage Type0101 = FIN (I.e not ACK/NACK)Sender BICEBNKGB20EBNK (Bank Code) GB (Country Code) 20 (Location Code)Sender Logical TerminalATypically A, unless they are a significantly large institution and require multiple terminalsSender BranchXXXAll X if no branch neededSession Number0000The session number for the messageSequence Number 999999The sequence number of the message
Taking a step back, I already identified two potential problems: the “session” and “sequence” numbers! These are described as follows:
Session Number – Must also equal the current application session number of the application entity that receives the input message.
Sequence number – The sequence number must be equal to the next expected number.
Hmmm, at this point I was not sure how I could predetermine a valid session and/or sequence number - considering they seemed to be application and 'traffic' specific? But there was nothing I could do at the time, so I noted it down in a list of 'issues/blockers' to come back to later.
Block 2 (Application Header)
A bit more dry reading later, I managed to also throw together an application header:
Again, I’ve broken this down so it makes sense (if it didn’t already; I’m not one to assume):
NameValueContextApplication Header Flag2Block 2I/O IdentifierIInput Message (a message being sent)Message Type103103 = Single Customer Credit TransactionRecipient BICFBNKFR20FBNK (Bank Code) FR (Country Code) 20 (Location Code)Recipient Logical TerminalXAll General Purpose Application Messages must use 'X'Recipient BranchXXXAll General Purpose Application Messages must use 'XXX'Message PriorityNNormal (Not Urgent)
Awesome! No issues crafting this header!
Note: At this point I should probably mention that these BIC codes are not 'real', however are accurate in terms of in format and length.
Block 3 (User Header)
The third block is called the “User Header” block, which can be used to define some “special” processing rules. By leverage this header, I could specify that the message should be processed using “Straight Through Processing” (STP) rules which essentially attempts to ensure that the message is processed end-to-end without human intervention. This could be specified as follows:
However, this was not yet a valid header! As of November 2018 the user header requires a mandatory “Unique end-to-end transaction reference” (UETR) value, which was introduced as part of SWIFT's Global Payments Innovation initiative (gpi)! This is a Globally Unique Identifier (GUID) compliant with the 4th version of the generation algorithm used by the IETF standard 'RFC4122'. This consists of 32 hexadecimal characters, divided into 5 parts by hyphens as follows:
where:
x – any lowercase hexadecimal character;
4 – fixed value;
y – either: 8, 9, a, b.
This value can be generated using Python as seen below:
With an acceptable UETR generated, this is how the third block looked:
And as before, a breakdown can be found below:
NameValueContextUser Header Flag3Block 3Validation Flag119Indicates whether FIN must perform any type of special validationValidation FieldSTPRequests the FIN system to validate the message according to the straight through processing principlesUETR Field121Indicates the Unique end-to-end transaction reference valueUETR Value8b1b42b5-669f-46ff-b2f2-c21f99788834Unique end-to-end transaction reference used to track payment instruction
Block 5 and 6 (Trailer and System Blocks)
I’ve already discussed “block 4” (the message body), so to wrap this section up, I'll be looking at the final 2 blocks: Block 5, aka the “Trailer”; and block S, aka the “System” block.
Before going forward, let me take a moment to explain the pointlessly complicated concept of input and output messages:
An “input” message (I) is a message which is traveling “outbound” from the institution. So this is a message being “input” by an operator and sent by the institution to another institution.
An “output” message (O) is a message which is traveling “inbound” to the institution. So this is a message being “output” by SWIFTNet and being received by the institution.
OK, moving swiftly (aaaahhhhh!) on.
For Input messages, these blocks were not too much of a problem. The headers only really seemed to be used to flag whether the message was for training / testing or to flag if it was a possible duplicate, which syntactically took the following form:
Where “TNG” indicated “training” and “SPD” indicated “possible duplicate”.
However, with Output messages, it got considerably more complicated. An example of what the trailer and system block could look like on an Output message is the following:
A breakdown of these various values is:
Trailer ((5:) MAC – Message Authentication Code calculated based on the entire contents of the message using a key that has been exchanged with the destination bank and a secret algorithm; CHK – This is a PKI checksum of the message body, used to ensure the message has not been corrupted in transit; TNG – A flag to indicate that the message is a Testing and Training Message.
System ((S:) SPD – Possible Duplicate Flag SAC – Successfully Authenticated and Authorized Flag. This is only present if:
Signature verification was successful.
RMA (Relationship Management Application) authorization and verification was successful.
COP – Flag indicating that this is the primary message copy; MDG – The HMAC256 of the message using LAU keys.
However, these seemed to only be values I would need to consider if I was to try and forge an “incoming” message from SWIFTNet or an 'outbound' message on the output of the SAG.
So.. I'll stick with crafting an “input' message trailer:
Now, having said all that, it turned out the trailer block did seem to sometimes hold a MAC code and a message checksum (sigh), meaning I actually needed to construct something like:
So that was +2 to my 'issues/blockers' list. However, issues aside, I now understood the complete message format, and could put it all together and save the following as a draft / template MT103 message:
Highlighted in bold above are the areas of the message I was - at this point - unable to pre-determine. Nevertheless, a summary of what that the message describes is:
Using the transaction reference “TRANSACTIONRF103”;
please transfer 500,000.00 GBP;
from John Doe, (IBAN: GB22EBNK88227712345678) at “English Bank” (BIC: EBNKGB20);
to Alice Smith (IBAN: FR20FBNK88332287654321) at “French Bank” (BIC: FBNKFR20);
Furthermore, please ensure the transaction charge is shared between the two institutions;
and mark the payment with a reference of “12345-67890”.
To wrap up this section, i wanted to take a moment to explain some logic behind the target of 500,000 GBP, as it is also important.
Aside from the many reasons it would be better to transfer (even) smaller amounts (which is an increasingly common tactic deployed by modern threat actors), why not go higher? This is where it’s important to understand the system and environment you are targeting.
In this instance, let's assume that by doing recon for a while I gathered the understanding that:
If a message comes from SYS which is over £500k;
even if it has been subject to a 4 eye check;
and even if it is flagged for STP processing;
route it to a verification queue and hold it for manual verification.
This was because a transaction over £500k was determined to be “abnormal” for SYS. As such, if my transaction was greater, the message would not propagate through all systems automatically.
OK, so now that I understood:
how the system worked;
how it communicated;
the fundamental structure of a raw MT103 payment messages;
and how much I could reliably (attempt) to transfer.
And with that, it was time to take a break from MT standards and establish an understanding of how I would even get into a position to put this into practice!
To place a message on a queue, I was going to need two things:
Access to the correct queue manager;
Write access to the correct queues.
Depending on the environment and organisation, access to queue managers could be quite different and complex. However a bare-bones setup may take the following form:
An MQ Administrator accesses their dedicated workstation using AD credentials;
They then remotely access a dedicated jump server via RDP which only their host is whitelisted to access;
This may be required as the queues may make use of Channel Authentication Records, authorizing specific systems and user accounts access to specific queues;
The channels may further be protected by MQ Message Encryption (MQME) which encrypts messages at rest based on specific channels. As such, even if someone was a “super duper master admin” they would only be able to read / write to queues specifically allocated to them within the MQME configuration file (potential target for another time?);
The MQ Admin can then use tools such via the Jump Server to read/write to their desired message queues.
So, in this scenario, to gain access to the message queues I - as an attacker - would need to compromise the MQ admin’s AD account and workstations, then use this to gain access to the jump host, from where I could then access the message queues given I knew the correct channel name and was configured with authorization to access it.. and maybe throw some MFA in there..
That is understandably a significant requirement! However, when discussion sophisticated attacks against Financial Market Infrastructure (FMI), it is more than reasonable to accept that an Advanced Persistent Threat (APT) would see this as a feasible objective - We don't need to dig into the history of how sophisticated attacks targeting SWIFT systems can be.
Next, it was time to finally identify a feasible attack vector for message forgery.
Now with an idea of how to gain the right access, as well as an understanding of the various technologies and security controls in place; I update my diagram:
You may have noticed I've added something called “LAU” around the SAA-to-SAG adapter, and another “LAU” to the MID-to-SAA MQ channels, which I have yet to explain. “Local Authentication” (LAU) is a security control implemented by SWIFT to authenticate messages using a pair of shared keys between two systems. These keys are combined and used to generate a SHA256 HMAC of the message and append it to the S block. This can then be validated by the recipient system. Effectively, this validates the origin and authenticity of a message. As such, even if an attacker was in position to introduce a fraudulent payment, they'd first need to compromise both the left and the right LAU signing keys, generate the correct HMAC, and append it to the message in order to have it accepted / processed successfully.
But LAU aside, I now just needed to figure out which queue to target! There were a lot of queues to work with as each system essentially has multiple “input” and “output” queues. With that in mind, it was important to note that: an incoming message would require being in the format expected by the target system (from a specific upstream system) and an outgoing message would need to be in the format “produced” by one target system and “expected / ingested / processed” by its respective downstream system. So to figure this out, I worked backwards from the Gateway.
Targeting SAG
This was the least feasible attack vector!
I hadn't really looked into how the SWIFT adapters worked - If only I could research literally everything);
SAA and SAG implemented LAU on messages sent between them - An excellent security control!;
The output of SAG was directly on to SWIFTNet which would entail all sorts of other complications - this is an understatement)!
Next!
Targeting SAA
So what if I wanted to drop a message on the “outbound” channel of SAA?
LAU and the SWIFT adapter aside, remember those session and sequence numbers? Well, messages which leave SAA are in the near-final stages of their outbound life-cycle, and as far as I understood would need to have valid session and sequence values. Given I didn't know how to generate these values without gaining access to SAA or how they worked in general (and lets not forget the LAU signing) this didn't currently seem feasible.
Next!
Targeting SANCT
This solution didn't actually transport messages back and forth; it just reads messages off the queues and performed checks on their details. Not much I could wanted to leverage here.
Targeting MID
To target MID, I could try and inject a message onto SAA’s “input” queue, or the “output” queue of MID. This would only need to match the format of messages produced by the Middleware solution (MID). Following this, in theory, the (mistial) message session and sequence number would be added by SAA, along with the UETR. This was promising!
However, MID was a SWIFT “message partner”, which are typically solutions developed using the Alliance Access Development Kit that allows vendors to develop SWIFTNet compatible software, and consequentially, implement LAU. So again, in-order to forge a message here, I’d need to compromise the left and right LAU signing keys used between SAA and MID, manually HMAC the message (correctly!), and then place it on the correct queue.. This also no longer looked promising..
Targeting SYS
OK, how about the input of the next system down - the 'Payment System'?
5m Mathmrs. Mac's Messages To My
As described previously, the inbound data was a custom “application specific” payment instruction from the institutions back office systems, and not a SWIFT MT message. This would be an entirely new core concept I'd need to reverse - not ideal for this project.
But how about the output queue?
Although SYS received custom format data, I found that it output what seemed to be an initial SWIFT MT messages. This was perfect! Additionally, SYS did not have LAU between itself and MID because (unlike MID) SYS was not a SWIFT message partner, and was just one of many-many systems within the institution that formed their overall payment landscape.
Additionally, because SYS was esentially just one small piece of a much larger back office architecture, it was not part of the SWIFT Secure Zone (after all you cant have your entire estate in the Secure Zone - that defeats the purpose) and as such, made use of the Queue Manager within a more accessible section of the general corporate environment (QM1). Konica minolta bizhub c352 driver mac os xcompubrown recovery tool.
With this in mind, and having - in theory - compromised the MQ admin, I could leverage their access to access on the corporate network to authenticate to QM1. I could - in theory - then write a fraudulent payment message to the SYS “output” queue, which we will call “SYS_PAY_OUT_Q” from here on.
OK! It seems like I finally had an idea of what to do! But before I could put it into practice, I of course needed to create a diagram of the attack:
I think it’s important to take a minute to refer back to the concept of “trust” which is what lead to this attack diagram. My theory behind why this may work is because the MID application, implicitly trusts whatever it receives from its respective upstream systems. This is intentional, as by design the security model of the payment landscape ensures that: at any point a message can be created, a 4 (or 6) eye check is performed. If there was a system whose purpose it was to ensure the validity of a payment message at any point upstream, the downstream systems should have no real issue processing that message (with some exceptions). After all, It would be next to-impossible to maintain a high-throughput payment system without this design.
And with that said, the plan was now clear:
Leverage the access of a Message Queue administrator;
to abuse the “trust relationship” between SYS, MID, and SAA;
to introduce a fraudulent payment message directly on to the output queue of SYS;
by leaning on my new found understanding of complete MT103 payment messages.
It was finally time to try to demonstrate a Proof-of-Concept attack!
So at this point I believe I had everything I needed in order to execute the attack:
The target system!
The message format!
The queue manager!
The queue!
The access requirements!
The generously granted access to a fully functional SWIFT messaging architecture! (that’s a good one to have!)
The extra-generously granted support of various SMEs from the target institution! (This was even better to have!)
Message Forgery
I needed to begin by creating a valid payment message using valid details from the target institution. So before moving on I was provided with the following (Note: as with many things in this post, these details have been faked):
Debtor Account Details – John Doe, GB12EBNK88227712345678 at EBNKGB20
Creditor Account Details – Alice Smith, GB15EBNK88332287654321 at EBNKGB20
Some of you may have notice that the sending and receiving BIC’s are the same. This was because, for the sake of the research, I wanted to send the message back to the target institution via SWIFTNet so that I could analyse its full end-to-end message history. Furthermore, you may have noticed we are using 'test & training' BIC code (where the 8th character is a 0) - this was to make sure, you know, that I kept my job.
But yes, with access to these 'valid' account details and the knowledge gained during the research so far, I could now forge a complete Input MT103 messages:
Note: Field 33B is actually an optional field, however, the MT standard stated that “If the country codes of both the Sender’s and the Receiver’s BIC belong to the country code list, then field 33B is mandatory”. As such, if 33B was not present in the message, it would fail network validation rules and SWIFTNet would return a NAK with the error code: D49.
Optional / Mandatory fields aside, it was not quite that simple! There were a few minor changes I needed to make based on the specific point in the message's its life-cycle I was planning to introduce it!
As I list these changes, remember that the objective is to introduce the message to the output queue of SYS (Which exists before MID, SAA and SAG)
The first 3 blocks needed to be placed on a single line;
Remove field 121 (UETR) from the User Header, as this would be generated by SAA during processing;
Remove 1 character from the transaction reference as it needed to be exactly 16 characters (classic user error);
Add decimal point to transaction amount using a comma - otherwise it would fail syntax validation rules;
Ensure the IBAN's were real and accurate, otherwise it seemed the message would fail some type of signature validation on the SWIFT network. The IBANs are fake here, but during the real PoC we used accurate account details in collaboration with the target institution;
Remove the trailer block (5) - as this would be appended by SAA during processing;
Remove the System Block (S) - as this would be completed by the SAG.
And the final message was as follows:
Note that the location in which I introduce the message has resolved all of the 'issues / blockers' I'd tracked whilst researching the message structure! It would seem the further upstream you go, the easier the attack becomes - given MQ is still used as a transport medium.
Message Injection
Now I had my raw MT103 message, I just need to save it to a file (“Message.txt” - sure why not) and place onto the “SYS_PAY_OUT_Q” queue using one of the admin's tools:
With access to a sole MQ Administrator's AD account;
We connect to the MQ admins machine;
Log into the Jump Server;
Open our MQ tools of choice and authenticate to queue manager (QM1) where the output queue for SYS was managed;
Connected to the 'SYS_PAY_OUT_Q' queue;
Selected my forged “Message.txt” file;
Invoked the “write to queue” function;
And it was off!
Loggin in to Alliance Access and opening the message history tab, we sat awaiting for an update. Waiting, waiting, waiting… waiting… and..
ACK! It worked!
That's a joke; did we hell receive an ACK!
See, this last section is written slightly more 'linear' than what actually happened. Remember those 'tweaks' used to fix the message in the previous section? I hadn't quite figured that out yet..
So roughly seven NACKs later - each time troubleshooting and then fixing a different issues - we did indeed, see an ACK! The message was successfully processed by all systems, passed target system validation rules, passed sanctions and AML screening, passed SWIFTNet validation rules, and SWIFT’s regional processor had received the message and sent an 'Acknowledgement of receipt' response to the sending institution!
For the sake of completeness, I’ve included the ACK below:
And of course a breakdown of what it all means:
NameValueContextBasic Header Flag1Block 1Application TypeFF = FIN ApplicationMessage Type2121 = ACKInstitution CodeEBNKGB20AXXXEBNKGB20 (BIC) A (Logical Terminal) XXX (Branch)Sequence and Session No.19473923441947 (Sequence No.) 392344 (Session No.)Date Tag177200103 (Date) 1102 (Time)Accept / Reject Tag4510 = Accepted by SWIFTNet
Excellent! WooHoo! It worked! .. That took a lot of time and effort!
Closer Inspection
But the ACK wasn't enough, I wanted to make sure I understood what had happened to the message throughout its life-cycle. From the message I placed on the initial queue, to being processed by SWIFTNet.
Thankfully, as we sent the message back to the target institution we could see its entire message history. I already knew what the raw message placed on the queue looked like, so I wanted to focus on what became of the message once it had been processed by SAA:
The end-to-end tracking UUID had been generated and added (b42857ce-3931-49bf-ba34-16dd7a0c929f) in block 3;
The message trailer had been added ((5:(TNG:))) where I could see that - due to the BIC code used - SAA had flagged the message as 'test and training'.
Additionally, an initial System Block segment had been added ((S:(SPD:))), tagging the message as a possible duplicate. I wonder why - *cough* 7th attempt *cough*?
OK, so that was SAA. Now let’s see how it looked it once it passed through the Gateway and regional processor:
OK, we can see a few changes now.
The session and sequence numbers have been populated (1947392344);
The I/O identifier in block 2 has been updated to track that it is now an 'Output' message;
The additional data within Block 2 is a combination of the input time, date, BIC, session and sequence numbers, output date/time, and priority;
The trailer has been updated with a message authentication code (MAC) calculated based on the entire contents of the message using a pre-shared key and a secret algorithm;
Additionally, a checksum of the message body has been stored within the trailer’s “CHK” tag. This is used by the network to ensure message integrity.
I also took a look at the entire outbound message history, just to see all the “Success” and “No violation” statements to make it feel even more awesome!
So that's that really..
With a bit of research and support I was able to demonstrate a PoC for introducing a fraudulent payment message to move funds from one account to another, by manually forging a raw SWIFT MT103 single customer credit transfer message, and leveraging various system trust relationships to do a lot of the hard work for me! https://arfox158.tumblr.com/post/655263262721638400/wireless-external-hard-drive-for-mac.
As mentioned briefly in the introduction, this is not something I have really seen or heard of happening in practice or in the 'wild'. Perhaps because it clearly takes a lot of work.. and there is a huge margin for error. However, if an adversary has spent enough time inside your network and has had access to the right documentation and resources, this may be a viable attack vector. It definitely has its benefits:
No need to compromise multiple payment operators;
No requirement to compromise - or establish a foothold within - the SWIFT Secure Zone;
No requirement to bypass MFA and gain credentials for a messaging interface;
No generation of application user activity logs;
No payment application login alerts;
No bespoke app-specific and tailored malware;
And all the other things associated with the complex task of gaining and leveraging payment operator access.
All an attacker may need to do is compromise one specific user on the corporate network: a Message Queue administrator.
The industry is spending a lot of time and effort focused on securing their payment systems, applications, processes, and users to keep - among other things - payment operators safe, Messaging Interfaces locked down, and SWIFT systems isolated. But the reality is,; the most valuable and most powerful individual in the entire model, might just be a single administrator!
As always, a security model is only as strong as its weakest link. If you're not applying the same level of security to your wider institution, there may very well be many weak links within the wider network which chain together and lead to the comrpomise of systems which feed into your various payment environment.
I think the main thing to remember when reflecting on this research is that it did not abuse any vulnerabilities within the target institution's systems, or even vulnerabilities or weaknesses within the design of their architecture. It simply leverages the legitimate user access of the Message Queue administrators and the trust relationships that exist by design within these types of large-scale payment processing systems.
So the harsh reality is, there is no particular list of recommendations for preventing this type of attack in itself. However, the main point to drive home is that you must ensure the security of your users - and overall organisation - is of a high enough standard to protect your highest privileged users from being compromised. Things such as:
Strong monitoring and alerting controls for anomalous behaviour;
Requirements for Multi-Factor authentication for access to critical infrastructure;
Segregation of critical infrastructure from the wider general IT network;
Strong password policies;
Well rehearsed incident detection and incident response policies and procedures;
Frequent high-quality security awareness training of staff;
Secure Software Development training for your developers;
Routine technical security assessments of all critical systems and components;
The use of 3rd party software from reputable and trusted vendors;
However, in the context of Message Queues, there is one particular control which I think is extremely valuable: The implementation of channel specific message signing! This, as demonstrated by SWIFT's LAU control, is a good way in which to ensure the authenticity of a message.
As discussed, LAU is - as far as I know at the time of writing - a SWIFT product / message partner specific control. However it's concept is universal and could be implemented in many forms, two of which are:
Update your in-house application's to support message signing, natively;
Develop a middleware component which performs message signing on each system, locally.
This is a complex requirement as it requires considerable effort on the client’s behalf to implement either approach. However, SWIFT provides guidance within their Alliance Access Developers guide on how to implement LAU in Java, Objective C, Scala and Swift;
Strip any S block from the FIN message input. Keep only blocks 1: through 5;
Use the FIN message input as a binary value (unsigned char in C language, byte in Java). The FIN message input must be coded in the ASCII character set;
Combine the left LAU key and the right LAU key as one string. The merged LAU key must be used as a binary value (unsigned char in C language, byte in Java). The merged LAU key must be coded in the ASCII character set;
Call a HMAC256 routine to compute the hash value. The hash value must also be treated as a binary value (unsigned char in C language, byte in Java). The HMAC size is 32 bytes;
Convert the HMAC binary values to uppercase hexadecimal printable characters.
An example of how this may work in the more flexible middleware solution proposed is where the original service is no longer exposed to the network, and is altered to only communicate directly with the custom 'LAU-eqsue' service on its local host. This service would then sign and route the message to its respective queue.
When received, the core of the recipient payment service would seek to retrieve its messages from the queues via the 'LAU-esque' signing middleware, which would retrieve the message and subsequently verify its origin and authenticity by re-calculating the signature using their shared (secret) keys. Key-pairs could further be unique per message flow. This design could allow for the signing to be used as a way to validate the origin of a message even if it had passed through multiple (local) intermediary systems.
As a final bit of creative effort, I made yet another diagram to represent what this could perhaps look like - if life was as easy as a diagram:
If you made it this far thanks for reading all.. ~6k words!? I hope you found some of them interesting and maybe learned a thing or two!
I'd like express our gratitude to the institution who facilitated this research, as well as specifically to the various SMEs within that institution who gave their valuable time to support it throughout.
Fineksus - SWIFT Standard Changes 2019
https://fineksus.com/swift-mt-standard-changes-2019/
Paiementor - SWIFT MT Message Structure Blocks 1 to 5
https://www.paiementor.com/swift-mt-message-structure-blocks-1-to-5/
SEPA for corporates - The Difference between a SWIFT ACK and SWIFT NACK
https://www.sepaforcorporates.com/swift-for-corporates/quick-guide-swift-mt101-format/
SEPA for corporates - Explained: SWIFT gpi UETR – Unique End-to-End Transaction Reference
https://www.sepaforcorporates.com/swift-for-corporates/explained-swift-gpi-uetr-unique-end-to-end-transaction-reference/
M DIBA - LAU for SWIFT Message Partners
https://www.linkedin.com/pulse/lau-swift-message-partners-mohammad-diba-1/
Prowide - About SWIFT
https://www.prowidesoftware.com/about-SWIFT.jsp
5m Mathmrs. Mac's Messages For Her
Microsoft - SWIFT Schemas
https://docs.microsoft.com/en-us/biztalk/adapters-and-accelerators/accelerator-swift/swift-schemas
SWIFT FIN Guru - SWIFT message block structure
http://www.swiftfinguru.com/2017/02/swift-message-block-structure.html

2 notes
·
View notes
Text
What Mimo Can Achieve in the Next Decade
What Mimo Can Achieve in the Next Decade
The global Massive MIMO mobile network is expected to expand at a very high rate and thereby a high CAGR within the next twenty years. According to a recent report by MRFR, a leading market research firm, the global network of mobile communication is growing at a pace of 60 percent per year. This statistical analysis has been provided by Market Research Future Reports. Massive MIMO is further defined as Multi Input Multi Output as it is an unswitched interconnectivity of mobile devices that enables sending and receiving data signals over the same single radio frequency. The major components of this technology include Wide Area Networks (WAN), Short Message Service (SMS), Voice over Internet Protocol (VoIP), Pagers, Mobile Broadband and Personal Digital Assistants (PDAs).
There are two main components that are contributing to the growth of Massive MIMO. One is the increasing use of smart phones in the market segment and the second is the deployment of WAN and mobile broadband connections. According to the research report, there are four major manufactures that are dominating in the industry. These are namely: HTC, Samsung, LG, and Motorola.
Further, there are different types of services that are being offered by these companies for enabling mass usage of various applications. One such application is Massive MIMO, which is used for enabling voice, video and multimedia communications. The application of Massive MIMO in this case is found to be quite successful. A major advantage of using this system for mobiles is that the users need not have any sort of router or cable connection for enabling a high speed internet connection. All these advantages are being counteracted by the presence of another major competitor in the mimo market - Cisco.
Mimo does not use the technology supported by Cisco. Further, the Cisco system is found to be not supporting any sort of business process integration (BPI) with the application. Some of the top users of this technology are telecommunication companies that use it for enabling voice calls and multimedia conferences. These companies use Mimo for enabling secure communication between the employees located at different locations.
Another important segment in the mimo market includes the massive global market for access networks. Access networks are basically networks that are large and which are meant for distributing data at fast speeds. The major companies that are providing this kind of service are T-Mobile, AT&T, Verizon and Vodafone. This segment is also witnessing growth due to the availability of the High Speed Multiple Input/ Multi Output (HSMOUTP) feature and the lower costs of Broadband connections.
In the meantime, another market segment that is growing at a faster pace is that of the Wide-Area-Internet network (WAN). Mimo can support the Wide-Area-Internet (WAN) because it has the necessary spectrum for connecting large areas. With the help of WAN, companies can create Local Area Networks (LANs) within small geographical locations and link them together via leased lines. Some of the major companies that are making investments in time are Dell, Cisco, Microsoft, Kaspersky and others.
It is very important to understand the forecast period for the market as the growth prospects of mimo are highest during the second half of this year. It is projected that the demand for services will continue to grow and companies will be increasing their network capacity at an unprecedented rate. This is the time when the companies will start deploying their own private branch networks. They may also choose to deploy their managed services for their clients. Even though the forecast period is still early, it is not too late to invest in mimo market segments and prepare for a massive media platform.
It should be noted that Mimo forecasts are not directly influenced by media reports. Media reports can only have a direct or indirect effect on the overall market growth of mimo. Media reports can focus on either one or two markets, whereas the data provided by him can address a wide variety of markets. The data provided by mimo can also address different time frames for the market growth such as the three months to five years' forecasts. These three months to five-year forecasts form the critical data that investors and business managers use to decide whether to launch a venture or nThe research team projects that the SU-MIMO Wi-Fi Chipset market size will grow from XXX in 2020 to XXX by 2027, at an estimated CAGR of XX. The base year considered for the study is 2020, and the market size is projected from 2020 to 2027.
The prime objective of this report is to help the user understand the market in terms of its definition, segmentation, market potential, influential trends, and the challenges that the market is facing with 10 major regions and 50 major countries. Deep researches and analysis were done during the preparation of the report. The readers will find this report very helpful in understanding the market in depth. The data and the information regarding the market are taken from reliable sources such as websites, annual reports of the companies, journals, and others and were checked and validated by the industry experts. The facts and data are represented in the report using diagrams, graphs, pie charts, and other pictorial representations. This enhances the visual representation and also helps in understanding the facts much better.
By Market Players: Qualcomm Technologies(US) Samsung Electronics(South Korea) Texas Instruments Incorporated. (US) MediaTek(Taiwan) Marvell Technology Group(Bermuda) Intel Corporation (US) Peraso Technologies(Canada) Cypress Semiconductor Corporation (US) STMicroelectronics (Switzerland) Quantenna Communications(US)
By Type 802.11ay 802.11ax 802.11ac Wave 2 Others
By Application Smartphones Tablet PCs Access Point Equipment Connected Home Devices Others
By Regions/Countries: North America United States Canada Mexico
East Asia China Japan South Korea
Europe Germany United Kingdom France Italy Russia Spain Netherlands Switzerland Poland
South Asia India Pakistan Bangladesh
Southeast Asia Indonesia Thailand Singapore Malaysia Philippines Vietnam Myanmar
Middle East Turkey Saudi Arabia Iran United Arab Emirates Israel Iraq Qatar Kuwait Oman
Africa Nigeria South Africa Egypt Algeria Morocoo
Oceania Australia New Zealand
South America Brazil Argentina Colombia Chile Venezuela Peru Puerto Rico Ecuador
Rest of the World Kazakhstan
Points Covered in The Report The points that are discussed within the report are the major market players that are involved in the market such as market players, raw material suppliers, equipment suppliers, end users, traders, distributors and etc. The complete profile of the companies is mentioned. And the capacity, production, price, revenue, cost, gross, gross margin, sales volume, sales revenue, consumption, growth rate, import, export, supply, future strategies, and the technological developments that they are making are also included within the report. This report analyzed 12 years data history and forecast. The growth factors of the market is discussed in detail wherein the different end users of the market are explained in detail. Data and information by market player, by region, by type, by application and etc, and custom research can be added according to specific requirements. The report contains the SWOT analysis of the market. Finally, the report contains the conclusion part where the opinions of the industrial experts are included.
Key Reasons to Purchase To gain insightful analyses of the market and have comprehensive understanding of the global market and its commercial landscape. Assess the production processes, major issues, and solutions to mitigate the development risk. To understand the most affecting driving and restraining forces in the market and its impact in the global market. Learn about the market strategies that are being adopted by leading respective organizations. To understand the future outlook and prospects for the market. Besides the standard structure reports, we also provide custom research according to specific requirements.
The report focuses on Global, Top 10 Regions and Top 50 Countries Market Size of SU-MIMO Wi-Fi Chipset 2016-2021, and development forecast 2022-2027 including industries, major players/suppliers worldwide and market share by regions, with company and product introduction, position in the market including their market status and development trend by types and applications which will provide its price and profit status, and marketing status & market growth drivers and challenges, with base year as 2020.
Key Indicators Analysed Market Players & Competitor Analysis: The report covers the key players of the industry including Company Profile, Product Specifications, Production Capacity/Sales, Revenue, Price and Gross Margin 2016-2021 & Sales by Product Types. Global and Regional Market Analysis: The report includes Global & Regional market status and outlook 2022-2027. Further the report provides break down details about each region & countries covered in the report. Identifying its production, consumption, import & export, sales volume & revenue forecast. Market Analysis by Product Type: The report covers majority Product Types in the SU-MIMO Wi-Fi Chipset Industry, including its product specifcations by each key player, volume, sales by Volume and Value (M USD). Markat Analysis by Application Type: Based on the SU-MIMO Wi-Fi Chipset Industry and its applications, the market is further sub-segmented into several major Application of its industry. It provides you with the market size, CAGR & forecast by each industry applications. Market Trends: Market key trends which include Increased Competition and Continuous Innovations. Opportunities and Drivers: Identifying the Growing Demands and New Technology Porters Five Force Analysis: The report will provide with the state of competition in industry depending on five basic forces: threat of new entrants, bargaining power of suppliers, bargaining power of buyers, threat of substitute products or services, and existing industry rivalry.
COVID-19 Impact Report covers Impact of Coronavirus COVID-19: Since the COVID-19 virus outbreak in December 2019, the disease has spread to almost every country around the globe with the World Health Organization declaring it a public health emergency. The global impacts of the coronavirus disease 2019 (COVID-19) are already starting to be felt, and will significantly affect the SU-MIMO Wi-Fi Chipset market in 2021. The outbreak of COVID-19 has brought effects on many aspects, like flight cancellations; travel bans and quarantines; restaurants closed; all indoor/outdoor events restricted; over forty countries state of emergency declared; massive slowing of the supply chain; stock market volatility; falling business confidence, growing panic among the population, and uncertainty about future
For more details conntect as https://www.reportmines.com
1 note
·
View note
Text
IS CENSORSHIP THE DEATH OF CONTENT CREATIVITY?
Censorship, unquestionably, is not just a deterrent to an individual's expression of creativity, but in fact, the very curtailment of their freedom. Since ages past, Censorship has been a tool utilized by ruling bodies, be it kings, queens, priests, religions, or in the present case, democratic governments, to curb expressions of dissent either by an individual or communities. Although an ancient tool, it is still quite popular and in wide use by modern governments worldwide, granted its severity differs from nation to nation. However, foremost, presenting facts: Censorship is always a product of the essentially dominant zeitgeist, which is without exception defined by the ruling social class (more often than not conservative), which wants to maintain the status quo of a specific region. Censorship is no new subject, and to better understand, we have to study both the present and the past. Even today, this is an issue that will undoubtedly affect our country's future.
Let us first state the precise definition of Censorship: "Censorship is the suppression of speech, public communication, or other information, on the basis that such material is considered objectionable, harmful, sensitive, or "inconvenient." Censorship can be conducted by governments, private institutions, and other controlling bodies.” This is a standard definition of Censorship. However, what people fail to realize is that Censorship's scope spans far and wide beyond the scope of just entertainment and news media. Not to mention the methodology of implementing censorships.
Nevertheless, how about we first trace the history of Censorship up to the present date. The first, most famous instance of Censorship is known to have happened in ancient Greece, where the great philosopher Socrates was charged with "corrupting" the youths and was henceforth executed. ‘Censorship by death’ might seem a thing of the past but is still very much a part of the present world. Censorship keeps reappearing as a blot in the history of humankind, as a sinister spectre. We remember the brutal killings by the church in the 16th century against the progress of science, the mass Censorship of literature in the 17th century by James I, the bloody Censorship in the 18th century during the Reign of Terror, not to mention the censorships implemented by Great Britain when India began its freedom struggle. Even in recent times, Censorship is an ever-looming presence. It was only 40 years ago when Indira Gandhi had implemented the emergency curtailing any and all criticism against the Government. Unfortunately, it is no revelation that India is right now going through a phase where a new kind of Censorship might emerge. A Censorship where there will not be a need to suppress the truth since the truth itself might stop existing hidden under the dirty disguise of propaganda and the veil of patriotism. This Censorship is the courtesy of ******** **** belonging to *** party.
From the examples, it can be easily surmised that no single incident exists where Censorship as a practice led to a positive result. More often than not, Censorship has been a product of conservative social practices and orthodox morality. It is always geared towards thwarting the path of progress. In maintaining the status quo. Several justifications are given in favour of Censorship. All valid reasons in themselves, but the rampant misuse made by the privileged few seriously casts a shadow of doubt on the systemic of Censorship. As previously mentioned, Censorship is subject to a conservative morality, and furthermore, a tool by the Government. These two forces combined only work to hinder the freedom of speech of the average citizens. Severe direct criticism against the ruling body or the upper class is not taken kindly. The so-called 'sentiments' being hurt belong only to the Savarna Heteronormative world, when they feel an 'attack'. But when it comes to the straight-up unconstitutional portrayal and slurs against the Queer and economically depressed classes, our democratic system invariably fails at protecting their constitutional rights.
Censorship is beyond a doubt the bane of content creativity. The combination of the psychological aspect and malignancy of censorship further create sinister dynamics worth our study. In an environment riddled with Censorships, there is psychologically established a safe zone and a danger zone in the individual's mind, creating an isolation of ideas and further constriction of mind. For fear of physical and mental harm, the user/creator remains within the arbitrarily made safe zone, created and defined by those in power. Once the zones are psychologically established, they start taking social roots. The safe zone creepily and silently becomes the core of social values. Hence, in essence, Censorship, in proxy with social values, becomes unquestionable. This further extends the safe zone in the social environment. Stepping out of that safe zone results in facing the wrath of the society itself. It, of course, is an obvious fact that societal norms are ingrained in an individual since infancy and hence get rooted inside the mind. Again, gaining a psychological aspect and here we witness the vicious circle of isolating the information and categorizing it as right or wrong, not through any critical judgment but simply because it becomes a predefined entity by an arbitrary authority (The ruling body). A fixed societal system then leads to a stale system of information where nothing new or creative can exist; rather, nothing new or creative is allowed to exist.
Additionally, Censorship is not merely an act of banning or removing certain content or proliferation of specific ideas. It is a sheer exercise in redacting the truth and hiding it behind a veneer of lies. Just like creativity can be expressed in multitudes of ways beyond the limited scope of media, similarly there exist nuanced censorship practices aimed at crushing deviant and creative modes of thinking. Censorships aimed at creating only one designated path. The different types of Censorship are: Censoring certain content (Removal), spreading false information to overshadow facts (Misleading), capturing means of information (Hijacking), Destabilising communications (Isolation of areas), Interference in collecting data, active prevention of expressing of one's views (Banning protests), ignoring or refusing to acknowledge specific outlets of expression (Disregarding), the threat of harm to relatives or the personnel themselves, and in the most extreme case Censorship by Death. With the coming of the digital age, the act of Censorship has become far more nuanced and harder to detect. And while the people keep struggling to find new ways of expressing their creativity\ the hounds of censorship keep up the chase. The freedom of the Internet is like a double-edged sword. Finding accurate facts among the propaganda and Whatsapp forwards is like trying to find a needle in the haystack. Perhaps part of the issue lies with the overload of information that has become possible with the Internet culture of our time.
Without a doubt, all the blame and critical talk surrounding Censorship should fall on the Government, regardless of the party. The Government's responsibility is to listen to the people's voices, not dictate that voice. A common argument in favour of Censorship is that Government is trying to protect the people from harmful, negative or disturbing media and discouraging its promotion. Media such as child pornography, disturbing and traumatizing videos of murder and gore, texts which might not be suitable for specific age groups. Fair enough. But my question is, why doesn't the Government try to eradicate the problems themselves? How is it that no action against the crime itself is taken? The very existence of such media is proof of how miserably our Government is failing.
Moreover, when someone raises these issues explicitly, those people are silenced on the grounds of spreading 'disturbing' content. Media handles spreading hate violence against communities, and misogynist content are allowed to do what they want willy-nilly, but porn websites are like the ultimate taboo, Oh! What a ruin of 'Indian values’. The ‘disturbing’ content which so endangers our peace and freedom is nothing more than the artist holding a mirror to the society. The artistic freedom exists in the fact that the artist can hold the mirror in any angle to show the dirty side-lines which nourish our established societal foundations. Censorship only exists to break those mirrors. It is an inability to confront the rotten reality, to face the cost of maintain the status quo. We are concerned about the children seeing the scars on a woman’s naked body; Mind! We are not concerned about the scars but about the nakedness! But why ashamed now, when you so proudly beat her up in front of your own child? We are concerned about an abuse in a TV show; Mind! We don’t care about the abuse, but about the fact that it is being hurled at our shining, virtuous culture! But why worried now when the abuses you threw on the young Dalit boy, are being thrown back on you? His are the abuses which are probably the fairest.
An interesting incident comes to my mind, which will also serve as a nice metaphor. Back in February, one of our glorious leaders invited a foreign leader for a political visit. They were supposed to tour certain parts of the country, to show its beauty. In preparation, we made walls along the roads! For very good reasons surely, and not to hide the dirt and the poverty lining the streets. So, the tour continued and our leaders travelled our beautiful country through those clean, immaculate, and wonderful roads, lined with walls on either side. I think the name of the walls was ‘Censorship’. And so it is, that we kill and wall off creativity and the truth. Because the fact is there is no one truth. The diversity and the creativity are all their own forms of truth. All those paths exist for us to explore and learn. But censorship allows only one road. The clean one. Which only the virtuous, the rich and the clean can walk.
Baudrillard's insight into the creation of reality is incredibly useful and a much-recommended read. His much-acclaimed theory has been, how in the present age of information explosion, the one who controls the flow of information is the one who controls reality. We have already witnessed how dangerous Censorship can be during Stalin's reign, where around 80000 people simply vanished. A similar pattern can be seen today with mob lynching and murders of journalists and reporters who dare to raise their voice against fascism. The riots, the protests, the beatings and the killings are the signs of our time. Hence it is not just the threat of ‘Death of creativity’ that we face, but it is almost a matter of life and death. Only us, the people can stand against it and openly raise our voices by our Freedom of expression and speech. The question remains: When will we come together to fight it?
By- Aditya Singh
2 notes
·
View notes
Text
COVID-19
Today, I went into public specifically to Stop & Shop. My boyfriend needed to pick up his prescription at the pharmacy and my mother needed some things from the grocery store as well. Before going out, my boyfriend and I prepared accordingly. We put on our masks, layered our clothes, brought extra gloves, and Clorox wipes to disinfect things as we went through this process. Of course it feels like a lot to do just to go out to the grocery store, but this is a very rare time in the world. While we were at the store, there were maybe 30 people in the whole store and about a third of them were wearing some sort of PPE in response to the pandemic. We were turning down one aisle when this older man was walking passed us in the opposite direction. We weren’t expecting what had happened next. With what I know about age, this man appeared to be in his 70′s if not 80′s and did not have any mask on or gloves. For my boyfriend and I, respecting other people is always our main concern unless they have given us a reason not to. After passing us, when he was about 7 to 8 feet away, he said “Oh my god, people are ridiculous. Just ridiculous” as he shook his head in disapproval and looked back at us like we were alien to him. It was that moment that I was genuinely moved and knew I’d be writing something when I returned home. As a 25 year old in generally good health, I am not very concerned about my own health during this time. The corona virus has so far only been fatal to the elderly and those with underlying conditions. Despite realizing I am not directly at risk, certain members of my family are older, or have underlying conditions, or both. In order for those members in my family to remain safe and healthy, I must protect myself too. Younger people have proven to be carriers and beacons for this virus to thrive and spread. I of course worry about my family first, but as rare as this quality is- I actually care about the health of even the people I may not personally know. The man spoke these words because he simply needed us to hear them. He raised his voice to a suitable volume and made a spectacle in order to express how he felt. In my personal opinion, I believe this man needed to validate himself this way because he too, is scared. Regardless of my beliefs during this pandemic, and how I think it is absolutely necessary to sanitize and take precautions for our loved ones and all people, I also believe in just respecting people. If you do not wish to wash your hands and wear a mask when you go to the food store, that’s your personal choice. Everyone has a right to carry out their lives in the way they feel is necessary, but there is utterly no reason to be disrespectful to those who feel differently. I was wearing a mask not just for my family, but for that old man, and others that may fall into his bracket. There were two other women who made the same comments towards my boyfriend and I. These two women were chatting at the end of one of the aisles. One seemed to be in her 60′s while the other appeared to be in her 70′s if not 80′s. Again we heard “People are just crazy.” I’m saddened by the ignorance and I was genuinely baffled that it felt like there were two separate types of people in the store. I understand that some people believe that this is not serious and although I think those people are very wrong and inconsiderate to others, I would never go out of my way to disrespect them in public or shame them in anyway.
With that being said, this pandemic is not a joke and should not qualify as “not that bad.” I understand people die from things everyday, it’s inevitable. I also understand that the human race has come into contact with certain viruses in the past that we as a community survived. However, we were not prepared for a pandemic of this magnitude. If we have the medical supplies and the hospital beds, sure, you will be able to receive the care that you need. The precautions that the government and the medical officials are putting into place are to stop this number from growing more and more. The amount of people who are infected is doubling and will only increase the rate in which it advances. In just a small a amount of time, our country’s stock on medical supplies has been almost entirely depleted. If we do not have the medical supplies and the beds to treat those who are sick, I can promise you this virus will not be “no big deal.” Every human life has so much value and my heart goes out to all the families of the COVID- 19 patients who have died and/or who are being treated. I live in New Jersey, next to the biggest infection populated state and city in America. I personally believe that New York, at it’s current rate of infection, will become the virus epicenter at least for our continent. Even if it doesn’t, the number of infections are going up. There is a 14 day incubation period where the infected hosts do not show any symptoms. The amount of interactions that occur between people is incomprehensible. There is no physical way for the government or the medical officials to accurately keep control and data on who is infected and who is not. What they can provide is the numbers of cases that have been confirmed and information that is finite. What we can do as human beings, is make sure we do our part to lessen the number of people infected. We have the proper supplies, but when we run out of the supplies, what do you think will happen? This is not a time for panic, though I too struggle with anxiety over this issue. This is the time to just be smart and proactive. We need to be mindful of our hands and what they touch. We need to practice social distancing and understand that everything we do now is to lessen the number of those needing our medical supplies and attention. Even if you do not think you are sick, if you have left the house and been subjected to the public in the past two to three weeks, you could very well have the virus and simply just not know. Again, that doesn’t call for panic. However it does call for understanding that this is much bigger than your own knowledge or perception. We all (healthy or sick) need to cover our mouths with the inside of our elbow when we cough or sneeze, we need to wash hands and refrain from touching our faces, we need to be mindful about the people around us and listen to the medical precautions posted on TV and on the internet. We have to do this together.
10 notes
·
View notes
Text
Will Writing - Exactly How To Select A Professional Firm
Legalzoom Online Will Evaluation
Content
If You Don'T Wish To Utilize A Solicitor
Indication Your Will In Front Of Witnesses.
To Establish Who Will Take Care Of Your Minor Kid
Key Records To Have Along With Your Last Will And Testament.
When Should You Obtain Legal Advice To Prepare Your Will?
Making Older Individuals'S Voices Heard.
Full An Estate Tax Type.
Utilizing A Lawyer To Compose Your Will
What Is Probate?
What To Expect From Your Solicitor
If You Don'T Intend To Use A Solicitor
You might think that the generated paper shows your desires, however you would not recognize if there was a much better method due to the fact that you have no solicitor leading you. Further, if points fail, customers won't necessarily have the ability to complain to the Lawful Ombudsman or any one of the various other regulators if they depend on membership of the SWW or IPWW alone. Whilst the SWW as well as IPWW have a grievances service, they have no real comparable power to claim, the Legal Ombudsman, SRA, CILEX or ACTION. By contrast, a qualified lawyer such as a Solicitor or Chartered Legal Executive should follow a stringent specialist Standard procedure and also can be sanctioned both by the Ombudsman and also by their corresponding Regulatory authorities.
You can learn about the recommended minimum contribution quantity, and details of lawyers that can assist on the Will Aid website. Every November, participating solicitors will create a basic will at no cost in return for a contribution to Will Help. Prior to making a decision on who to make use of, it's constantly suggested to get in touch with a couple of neighborhood solicitors to discover just how much they bill. The fees for creating a will vary between lawyers and also depend on the intricacy of the will. However, will-writing firms are not controlled by the Legislation Culture so there are couple of safeguards if things go wrong.
The requirements for a valid will are much less strict for service employees on active service. If somebody makes a will yet it is not legitimately valid, on their death their estate will be shared out under particular rules, not according to the dreams shared in the will. They will need to accumulate with each other all the possessions of the estate, deal with all the documentation and also pay all the financial obligations, taxes, funeral service and also administration expenses out of money in the estate. Executors are the people who will be accountable for carrying out your wishes and for figuring out the estate.

Possibly you're not sure of your dreams-- or don't know what the best alternatives to take may be to safeguard your estate for the future generation. When this occurs a person's assets are dispersed according to a collection of guidelines called Intestacy Rules. This is a set legal order which decides where your money goes-- and the outcome might not mirror your desires. Many individuals recognize exactly how crucial it is to have a will in position-- yet an alarming number don't yet have one in place, as well as haven't place their desires down in writing. Mostly individuals put it off since they see it as something to deal with when they are older, or they know they require to sort it out however then forget it.
Who should keep the original Will UK?
1. Leave it with a solicitor. If a solicitor writes your will, they will usually store the original free of charge and give you a copy – but ask them to make sure. Most solicitors will also store a will they didn't write, but there will probably be a fee.
Release your brand name and increase exposure to hundreds of wills as well as probate professionals daily by protecting an advertising and marketing room on the Today's Wills & Probate web site and once a week newsletter. Established in 2014, Today's Wills & Probate is the leading news magazine for wills and probate experts. We offer comprehensive training, technical support, as well as literature/resources to our accredited members, and offer fully detailed estate planning services. Our Consultants are available free of charge on the internet consultations as well as telephone consultations, to use you suggestions on all your estate planning requirements, whilst you stay in the security and comfort of your very own home. We additionally have 2 workplaces in Hellesdon, Norwich as well as St Ives, Cambridgeshire and are using Face-to-face appointments in accordance with Government standards on social distancing.
Indication Your Will In Front Of Witnesses.
I'm single or single without children.Even if you lived with your companion, your making it through companion is not qualified to anything.
I'm single or solitary with children.Even if you dealt with your companion, your enduring partner does not inherit anything.
plenty of software supplies a certain degree of legal protection for married or civil-partnered couples, however this protection doesn't apply to cohabiting pairs-- also if you've been together for 20 years as well as have 3 kids.
The rules are complex though, so legal recommendations deserves having, and things vary discreetly across the UK nations.
Actually, there are just limited civil liberties for cohabiting companions.
If you're not married or in a civil collaboration, also if you split up, there is generally no lawful commitment to merge your assets and also divide them.
In response to the coronavirus pandemic and also the fact some individuals need to 'protect', the Federal government has actually introduced regulation enabling the observing of wills to be done using video clip.
If you have no making it through blood relatives, your estate will go to the Crown.
If it's less than ₤ 2million, consider looking in other places, as you may discover it tough to get payment from companies supplying much less than this should points go wrong. A lot of lawyers save wills for free if you made the will with them.
To Identify Who Will Take Care Of Your Minor Kid
Your will writing firm might maintain your details on data and advise you when it's time to review your will. It's a great concept to assess your will often to guarantee that it stands and still reflects your dreams. If you leave an old will as well as don't upgrade it you might locate that it does not abide by current laws and also might leave your estate available to Intestacy Law.
Solicitors operate in a controlled market, which indicates that you have much more rights as a customer need to something fail with your Will. Typically, you can get in touch with the Legal Ombudsman to whine if you have actually talked with the solicitor directly and also your issues aren't attended to. Many Will-writing services are covered by the Customer Civil Liberty Act 2015, yet it deserves examining as policies can vary from business to firm. Some also come from main organisations that can action in to assist you out if you're not delighted with the procedure.
Can I leave my wife out of my will UK?
Under UK law you have a lot of freedom in your Will to leave your Estate to whoever you like. However, you need to be aware that legally you have to provide reasonable support to all people who are financially dependent on you (e.g. spouse, children etc.) and anyone you maintained / supported financially.
Secret Documents To Have Together With Your Last Will As Well As Testimony.
Complete the form below to find out more concerning any of our solutions. By giving away today, you might aid us respond to much more phones call to our recommendations line, project harder for older people's rights and also fair therapy as well as provide normal relationship calls to people who are frantically lonesome. If you have children as well as your spouse or companion is deceased your youngsters will acquire every little thing, split equally between them.
youtube
The new will should start with a provision specifying that it withdraws all previous wills and also codicils. Withdrawing a will implies that the will is no longer legally legitimate. You can also ask the firm to get in touch with lawyers in the area where the individual lived to ask if they hold a will. The individual that has actually passed away, or their solicitor, may have registered their will with a commercial organisation such as Certainty () as well as, after the person's death, you can spend for a search of the wills signed up on the firm's database.
April King's team of attorneys is led by Paul King, a complete member of the Culture of Trusts as well as Estates Practitioners. ACTION is the worldwide expert association for practitioners that specialise in family members inheritance and succession preparation. Full ACTION participants like Paul are internationally acknowledged as professionals in their area, with proven credentials and experience. In addition, even if the service states that the Will is inspected by a certified person later on, that person can not correctly check the paper suits your conditions since there is no interview or notes to compare to!
youtube
Use our rapid online service and also established your own will within 20 mins. Alternative 1-- You can look our directory of will writing experts, which you can discover right here. from a lawyer in case of a complicated scenario, such as multiple separations, abroad investments, organization properties or large estates.
When Should You Obtain Lawful Advice To Prepare Your Will?
Will-writing solutions start at around ₤ 80, and also will increase to a few hundred extra pounds, depending on the intricacy of your estate, as well as the competence of the firm. When writing a will, many people select to take the DIY course rather than seek professional aid.
Can my husband throw me out of our house UK?
In short, then you cannot simply kick your husband out of the house. Instead, you will need to apply for your own occupation order from the court, which will determine who can occupy the property.
Along with becoming part of an acknowledged network of professionals, becoming a member of the IPW can help your business attract attention versus competitors, demonstrating the high requirement of your solutions. Coronavirus (COVID-19) Update 22/09/ In accordance with the current Federal government suggestions, we have actually returned to functioning from residence. Our solutions continue to be uninterrupted and also our functioning hrs are customarily. This is excellent for any individual that doesn't have an e-mail address or would simply choose to speak to an expert. In this circumstance, your partner would additionally inherit 100% of your ₤ 325,000 tax obligation allowance, giving them an overall allowance of ₤ 650,000.
Making a Will enables you to define where your properties must go on your death. You can attend to liked ones and also in doing so, show that you care. Furthermore, Wills can cover issues such as philanthropic gifts, guardianship for small youngsters, care for pet dogs and whether the testator wishes to be hidden or cremated. Every Will is backed-up with ₤ 2m of specialist indemnity insurance.
If you are in any uncertainty regarding whether or not you ought to make a will, you need to consult a solicitor or a Citizens Advice neighborhood office that can provide you lists of solicitors. Regardless of whether you choose ahome check out, telephone orvideo chatappointment, the same team of pleasant, skilled legal professionals will direct you through the intricacies of writing your Will.

This is due to the fact that it is followed up by on-going area guidance to improve knowledge every step of the means. Distinctively, we are the only network to evaluate and inspect every Will that is written. Finally, we are the only Will writing company to take duty for ALL suggestions provided. An extremely sincere organization as well as have actually currently made myself reassured that my family is secured.

Your partner might after that leave an estate as much as the value of ₤ 650,000 without needing to pay any type of estate tax. The estate tax rate for 2019/20 is ₤ 325,000-- this is additionally known as the nil price band. If your estate is worth greater than ₤ 325,000, you will typically have to pay 40% on whatever over the zero price band. Nonetheless, if you're married or in a civil partnership and also your companion is domiciled in the UK, anything you delegate your partner will be free of tax, regardless of the size of your estate.
What is better a will or a trust?
Unlike a will, a living trust passes property outside of probate court. There are no court or attorney fees after the trust is established. Your property can be passed immediately and directly to your named beneficiaries. Trusts tend to be more expensive than wills to create and maintain.
The most well-recognised organisations are the Institute of Expert Willwriters and also the Culture of Will Writers. It's also worth inspecting if they're certified by the Trading Specification Institute Customer Codes Authorization Plan. Ultimately, you ought to ask the Will-writing business where their indemnity cover starts.
youtube
If you as well as a spouse or partner want substantively the exact same wills - called mirror wills - you'll generally obtain a discount rate for writing both at once. Before writing your will, it deserves recognizing all the possessions you have, along with any type of emotional products you wish to leave to enjoyed ones.
If you do not feel great writing a will online, among our specialists would certainly enjoy to make your will over the phone. We can then get it printed, bound and also sent to you in the blog post. After writing a will and getting it inspected by our specialists, you require to print and authorize it before 2 witnesses to make it lawfully binding. You can do it from the comfort of your very own home in simply 15 minutes. Create a will online in as little as 15 minutes and also take care of what actually matters.

You ought to also work out plans for your kids's care, and take into consideration whether you would love to leave details guidelines for your funeral. If you're intending to write a will, you can choose whether to do it yourself or seek aid from a professional. The right alternative for you will depend upon exactly how complex your affairs are, as well as how much help you're most likely to require. We discuss your options for doing-it-yourself, making use of a solicitor, or hiring a will-writing service below.
What happens if the witness to your will Dies UK?
That said, the death of a witness does not necessarily invalidate a will. At the outset of probate proceedings, if the witnesses have not survived, the executor will be required to produce proof that the original witness signatures were valid, as well as proof of the witnesses' deaths.
The Will Associates is just one of the UK's largest estate planning companies, being experts in Wills, Depends On, Powers of Attorney as well as Probate. We have hundreds of qualified professionals and head office team and we have actually aided over 7,000 individuals protect in excess of ₤ 1.5 BN in properties. If you are named in someone else's will as an administrator, you may need to look for probate to ensure that you can take care of their estate. There are rigorous time limits for testing a will and if you intend to test a will, you must look for legal advice immediately.
#Making a will#Will writing services#How to make a will#Fixed Fee Will Writing#Online Will Writing#Will Aid#Will Writing Specialist#will template#how to write a simple will#will writing services near me#legal will#online will#family will#simple will#how to end a will
1 note
·
View note
Text
Digital Marketing Trends You Must Know In 2020!

With the ever-evolving ambitious business projects, innovation and application of new digital marketing trends to bring in more productive outputs increasing profitability and hence tops the priority list of every business venture in 2020.
Like every business enterprise, if you aspire to withstand the competitive online market at present, you must accustom to the swiftly developing profitable changes in digital marketing. After witnessing the unpredictable customer behaviour patterns, preferences and ever-increasing demands, marketers can no longer trust the old strategies or marketing techniques in the hope of reaping the same projected profits. If you want your business to achieve more success this year, we suggest you to equip and employ the new technological advancements in your marketing campaigns.
Want to know more? We would love to help you!
1. Artificial Intelligence-driven Advertising : This can also be called as Programmatic advertising where Artificial Intelligence is employed to automate the ad buying process and hence you can target a more specific audience and prospects for your business. An example of programmatic ad buying is Real-time bidding where ad inventories/spaces are purchased and sold based on impressions through an automated mechanism. Introducing automation in digital marketing processes will reflect positive effects on other business processes. Programmatic advertising campaigns take into account more than hundred of metrics like keywords, demographics, regions, customer habits, lifestyle, time-slots and many more to personalize advertisements and targets the right audience more precisely based on the customer data. Automation will make the entire marketing mechanism efficient, economical and quick, resulting in higher conversions rates, minimum customer acquisition costs and increased returns on investment.
Want to know more? We would love to help you!

2. Artificial Intelligence-driven Chatbots : The AI-driven Chatbots are trending and the most interesting part of digital marketing, it will remain an influential factor in digital marketing strategies in 2020. This AI-based technology employs instant messaging bots or programmed chat messengers in real-time based on a set of rules, customer data, analyzed market reports, company's products/services and other vital information so that it can efficiently handle customer queries and resolve customer issues round the clock, without any human interference. Automated chats will engage your customers/site visitors and respond to their queries. Along with that it will learn customer behaviour and analyze the customer data suggesting better marketing inputs and increase profitability. Reports show that Chatbots will assist more than 80% of customer care by 2020. Major benefit of Chatbots are round-the-clock service, quick responses to customer queries as the majority of customers prefer chat facility rather than calling to customer support as it is time-saving and more intelligent. Surveys show that more than 70% of Businesses are about to utilize this virtual assistance for their business as its responses are accurate, available 24/7 and keeps track of the customer's buying journey. Need help? Contact us, we are available to help you!

3. Lens- Visual Search : Businesses are about to invest in Visual search feature for improving the customer experience where the audience/customers can upload an image of the product they wish to purchase and search. The mechanism will provide the user with more specific results. For example, brands like Pinterest's Lens now approves more than 2 billion fashion objects and influences the majority of search results. In partnership with brands like Samsung to induce visual search in its latest mobiles/smartphones to target the right audience for the products, they are searching. Another example is of Google Lens which is a visual search engine. It recognizes things/objects like a book or painting through the smartphone camera or an uploaded image.

4. Voice Search : Voice search highly used feature by the customers, reports suggest more than 50% of product searches will be done through voice by 2020. Voice search provides customers more comfort and instant response to their search saving their efforts and valuable time. These AI-driven Voice searches are smart and efficiently locates the user requirements and provide relevant data. Brands like Dominos and Paypal have employed voice search for improving customer experience, building brand awareness and optimizing search results. Errors made by these virtual voice assistants have been reduced considerably. Voice search enhances customer engagement. We are available to help you! 5. Progressive Web Applications (PWAs) : These are interactive websites that operate similar to mobile apps. Where they offer features of a native mobile application and loads quickly, it shows push notifications, different modes, device in use, platforms etc. Progressive Web Applications enhances audience engagement and provides opportunities for revenue generation.

6. IoT Advertising : Internet of Things (IoT) is having its influence on every scope of our lives, right from home appliances, mobile devices, wearable technologies to smart cars, everything is getting connected to every other thing through technology. This development has enabled digital marketers and advertising agencies to collect a huge amount of customer data about their likes and dislikes, their lifestyle, whereabouts, profession, about people they hang out with and almost everything, which is then utilized for tailoring effective brand marketing strategies, advertising and business growth. 7. Social Media Marketing : In 2020, You can add more efficiency to your marketing strategies by leveraging the benefits of Social media marketing. This is a well tested and effective strategy which plays an active role in influencing the audience, targeting the right prospects and generating leads. The power of social media is Interactive content like Surveys, Polls, Quizzes, Contests and much more. Along with that visual content wins the attention of the crowd and keeps the audience engaged. Social media marketing if executed in genuine a way for educating the masses through good quality content, it helps in building a community of loyal customers. As per many reports, to sustain in social media marketing in 2020 humanization of your business brand is necessary to grow genuine rapport with the audience. For example, Instagram planned of removing likes feature after realizing the adverse effects of seeking social validation on mental health, Instagram has started focusing on inculcating good human values to connect with their audience in a better way.

CONCLUSION :
These leading digital marketing trends will benefit you in 2020. To gain an edge over your competitors it is necessary to bring in better changes in our existing marketing mechanism to reap better results. Strive to revamp your older technologies, tools and methodologies with new ones to achieve the success your business deserves. Need assistance? Contact with our expert digital marketing team here!
12 notes
·
View notes
Text
Pluralistic: 14 Mar 2020 (Free audio of Masque of the Red Death and When Sysadmins Ruled the Earth, Ada Palmer on censorship, Women of Imagineering, Glitch unionizes, Tachyon/EFF Humble Bundle, Canada Reads postponed, data-caps and liquid bans paused, Star Wars firepits)

Today's links
Masque of the Red Death: Macmillan Audio gave me permission to share the audiobook of my end-of-the-world novella.
When Sysadmins Ruled the Earth: A new podcast audiobook of my 2005 end-of-the-world story.
Ada Palmer on historical and modern censorship: Part of EFF's Speaking Freely project.
Glitch workers unionize: First-ever tech union formed without management opposition.
Women of Imagineering: A 384-page illustrated chronicle of the role women play in Disney theme-park design.
Tachyon celebrates 30 years of sff publishing with a Humble Bundle: DRM-free and benefits EFF.
Honest Government Ads, Covid-19 edition: Political satire is really hard, but The Juice makes it look easy.
TSA lifts liquid bans, telcos lift data caps: Almost as though there was no reason for them in the first place.
CBC postpones Canada Reads debates: But you can read a ton of the nominated books online for free.
Star Wars firepits: 750lbs of flaming backyard steel.
This day in history: 2005, 2015, 2019
Colophon: Recent publications, current writing projects, upcoming appearances, current reading

Masque of the Red Death (permalink)
Edgar Allan Poe wrote "The Masque of the Red Death" in 1842. It's about a plutocrat who throws a masked ball in his walled abbey during a plague with the intention of cheating death.
https://www.poemuseum.org/the-masque-of-the-red-death
My novella "The Masque of the Red Death" is a tribute to Poe; it's from my book Radicalized. It's the story of a plute who brings his pals to his luxury bunker during civlizational collapse in the expectation of emerging once others have rebuilt.
https://us.macmillan.com/books/9781250242334
Naturally, they assume that when they do emerge, once their social inferiors have rebooted civilization, that their incredible finance-brains, their assault rifles, and their USBs full of BtC will allow them to command a harem and live a perpetual Frazetta-painting future.
And naturally – to anyone who's read Poe – it doesn't work out for them. They discover that humanity has a shared microbial destiny and that you can't shoot germs. That every catastrophe must be answered with solidarity, not selfishness, if it is to be survived.
Like my story When Sysadmins Ruled the Earth, the Masque of the Red Death has been on a lot of people's minds lately, especially since this Guardian story of plutes fleeing to their luxury bunkers was published. Hundreds of you have sent me this.
https://www.theguardian.com/world/2020/mar/11/disease-dodging-worried-wealthy-jet-off-to-disaster-bunkers
I got the message. Yesterday, I asked my agent to see if Macmillan Audio would let me publish the audiobook of my Masque of the Red Death for free. They said yes, and asked me to remind you that the audiobook of Radicalized (which includes Masque) is available for your delectation.
I hope you'll check out the whole book. Radicalized was named one of the @WSJ's best books of 2019, and it's a finalist for Canada Reads, the national book prize. It's currently on every Canadian national bestseller list.
There's one hitch, though: Audible won't sell it to you. They don't sell ANY of my work, because I don't allow DRM on it, because I believe that you should not have to lock my audiobooks to Amazon's platform in order to enjoy them.
Instead, you can buy the audio from sellers like libro.fm, Downpour.com, and Google Play. Or you can get it direct from me. No DRM, no license agreement. Just "you bought it, you own it."
https://craphound.com/shop/
And here's the free Macmillan Audio edition of Masque of the Red Death, read with spine-chilling menace by the incredible Stefan Rudnicki, with a special intro from me, freshly mastered by John Taylor Williams. I hope it gives you some comfort.
https://craphound.com/podcast/2020/03/13/the-masque-of-the-red-death/
(Here's the direct MP3, too)
https://archive.org/download/Cory_Doctorow_Podcast_332/Cory_Doctorow_Podcast_332_-_The_Masque_of_the_Red_Death.mp3

Ada Palmer on historical and modern censorship (permalink)
My EFF colleague Jillian C York's latest project is Speaking Freely, a series of interviews with people about free expression and the internet, including what Neil Gaiman memorably called "icky speech."
http://journal.neilgaiman.com/2008/12/why-defend-freedom-of-icky-speech.html
The latest interview subject is the incomparable Ada Palmer: historian, sf writer, musician, and co-host of last year's U Chicago seminar series on "systems of information control during information revolutions," which I co-taught with her. Ada's interview synthesizes her historian's distance from the subject ("yes, this is my subject, and these people are terrible, and it's kind of fun in that way") with her perspective as a writer and advocate for free speech.
"One of the victims of censorship is the future capacity to tell histories of the period when censorship happened….. It renders that historical record unreliable… makes it easier for people to make claims you can't refute using historical sources… It's similar to how we see people invalidating things now—like 'that climate study wasn't really valid because it got funding from a leftist political group"—they're invalidating the material by claiming that there has to be insincerity its development.
"Pretty much every censoring operation post-printing press recognizes that it isn't possible to track down and destroy every copy of a thing…An Inquisition book burning was the ceremonial burning of one copy. The Inquisition kept examples of all of the books they banned."
Fascinating perspecting on whether nongovernmental action can really be called "censorship."
"The Inquisition wasn't the state – it was a private org like to Doctors Without Borders or Unicef, run by private orgs like the Dominicans and it often competed with the state." As she points out, everything the Inquisition did would be fine alongside the First Amendment, because it was entirely private action.
Next, Palmer talks about market concentration and how it abets this kind of private censorship. This is something I've written a lot about, see for example:
https://locusmag.com/2020/01/cory-doctorow-inaction-is-a-form-of-action/
"If you have a plural set of voices, then you're always going to have some spaces where things can be said, just like you have a plurality of printers printing books, and some will only print orthodox things and some will only print radical ones."
And while the internet could afford many venues for speech, in practice a concentrated internet makes is plausible to accomplish the censor's never-realized dream: "You can make a program that can hunt down every instance of a particular phrase and erase it."
Tiny architectural choices make big differences here ("Architecture is politics" -Mitch Kapor). Amazon can update your Kindle books without your permission, Kobo can't. Amazon could delete every instance of a book on Kindles, but Kobo would need cooperation from its customers.
Palmer is just the latest subject of Jillian's series. You can read many other amazing interviews here:
https://www.eff.org/speaking-freely

When Sysadmins Ruled the Earth (permalink)
Over the past two weeks, hundreds of people have written to me to draw comparisons between the pandemic emergency and my 2005 story "When Sysamins Ruled the Earth" – an apocalyptic tale of network administrators who survive a civilizational collapse.
https://craphound.com/overclocked/Cory_Doctorow_-Overclocked-_When_Sysadmins_Ruled_the_Earth.html
I started writing this story in the teacher's quarters at the Clarion Workshop, which was then hosted at MSU. It was July 6, 2005. I know the date because the next day was 7/7, when bombs went off across London, blowing up the tube train my wife normally rode to work. The attacks also took out the bus I normally rode to my office. My wife was late to work because I was in Michigan, so she slept in. It probably saved her life. I couldn't work on this story for a long time after.
Eventually, I finished it and sold it to Eric Flint for Baen's Universe magazine. It's been widely reprinted and adapted, including as a comic:
https://archive.org/details/CoryDoctorowsFuturisticTalesOfTheHereAndNow/mode/2up
I read this for my podcast 15 years ago, too, but the quality is terrible. The more I thought about it, the more I thought I should do a new reading. So I did, and John Taylor Williams mastered it overnight and now it's live.
https://craphound.com/podcast/2020/03/13/when-sysadmins-ruled-the-earth-2/
There's a soliloquy in this where the protagonist reads a part of John Perry Barlow's Declaration of Independence of Cyberspace. Rather than read it myself for the podcast, I ganked some of Barlow's own 2015 reading, which is fucking magnificent.
https://vimeo.com/111576518
Anyway, I hope you enjoy this. I've spent a lot of imaginary time inhabiting various apocalypses, driven (I think) by my grandmother's horrific stories of being inducted into the civil defense corps during the Siege of Leningrad, which began when she was 12.
Anyway, I hope you enjoy this. I've spent a lot of imaginary time inhabiting various apocalypses, driven (I think) by my grandmother's horrific stories of being inducted into the civil defense corps during the Siege of Leningrad, which began when she was 12.
You can subscribe to the podcast here:
http://feeds.feedburner.com/doctorow_podcast
And here's the MP3, which is hosted by the @internetarchive (they'll host your stuff for free, too!).
https://archive.org/download/Cory_Doctorow_Podcast_331/Cory_Doctorow_Podcast_331_-_When_Sysadmins_Ruled_the_Earth.mp3

Glitch workers unionize (permalink)
The staff of Glitch have formed a union. It seems to be the first-ever white-collar tech-workers' union to have formed without any objections from management (bravo, Anil Dash!).
https://cwa-union.org/news/releases/tech-workers-app-developer-glitch-vote-form-union-and-join-cwa-organizing-initiative
The workers organized under the Communications Workers of America, which has been organizing tech shops through their Campaign to Organize Digital Employees.
https://www.code-cwa.org/?gclid=EAIaIQobChMIovDRsc-S6AIVCuDICh0rFQCMEAAYASAAEgJb1PD_BwE
"We appreciate that unlike so many employers, the Glitch management team decided to respect the rights of its workforce to choose union representation without fear or coercion."

Women of Imagineering (permalink)
Next October, Disney will publish "Women of Imagineering: 12 Careers, 12 Theme Parks, Countless Stories," a 384-page history of a dozen pioneering woman Imagineers.
https://thedisneyblog.com/2020/03/13/new-book-highlights-stories-from-the-women-of-walt-disney-imagineering/
Featured are Elisabete Erlandson, Julie Svendsen, Maggie Elliott, Peggy Fariss, Paula Dinkel, Karen Connolly Armitage, Katie Olson, Becky Bishop, Tori Atencio, Lynne Macer Rhodes, Kathy Rogers, and Pam Rank.
When I worked at Imagineering, the smartest, most talented, most impressive staff I knew were women (like Sara Thacher!). It's amazing to see the women of the organization get some long-overdue recognition.

Tachyon celebrates 30 years of sff publishing with a Humble Bundle (permalink)
For 30 years, @TachyonPub has been publishing outstanding science fiction, including a wide range of stuff that's too weird or marginal for the Big 5 publishers, like collections of essays and collections.
https://tachyonpublications.com/
Now, they've teamed up with Humble Bundle to celebrate their 30th with a huge pay-what-you-like bundle that benefits EFF. There are so many great books in this bundle!
https://www.humblebundle.com/books/celebrating-25-years-scifi-fantasy-from-tachyon-books
Like Bruce Sterling's Pirate Utopia, Eileen Gunn's Stable Strategies, and books by Michael Moorcock, Thomas Disch, Jo Walton, Jane Yolen, Nick Mamatas, Kameron Hurley, Lauren Beukes, Lavie Tidhar and so many more!
I curated the very first Humble Ebook Bundle and I've followed all the ones since. This one is fucking amazeballs. Run, don't walk.

Honest Government Ads, Covid-19 edition (permalink)
Good political satire is hard, but @thejuicemedia's "Honest Government Ads" are consistently brilliant.
https://www.youtube.com/channel/UCKRw8GAAtm27q4R3Q0kst_g
The latest is, of course, Covi9-19 themed. It is funny, trenchant, and puts the blame exactly where it belongs.
https://www.youtube.com/watch?v=Hks6Nq7g6P4
If you like it, you can support their Patreon.
https://www.patreon.com/TheJuiceMedia

TSA lifts liquid bans, telcos lift data caps (permalink)
Your ISP is likely to lift its data-caps in the next day or two. @ATT and @comcast already did.
https://www.vice.com/en_us/article/v74qzb/atandt-suspends-broadband-usage-caps-during-coronavirus-crisis
And TSA has decided that 12 ounces of any liquid labelled "hand sanitizer" is safe for aviation, irrespective of what's in the bottle.
https://www.theverge.com/2020/3/13/21179120/tsa-hand-sanitizer-liquid-size-airport-screening-coronavirus-covid-19
What do these two facts have in common? Obviously, it's that the official narrative for things that impose enormous financial costs on Americans, and dramatically lower their quality of lives, were based on lies. These lies have been obvious from the start. The liquid ban, for example, is based on a plot that never worked (making binary explosives in airport bathroom sinks from liquids) and seems unlikely to ever have worked, according to organic chemists.
Keeping your "piranha bath" near 0' C for a protracted period in the bathroom toilet is some varsity-level terrorism, and the penalty for failure is that you maim or blind yourself with acid spatter.
https://www.schneier.com/blog/archives/2006/08/on_the_implausi.html
And even if you stipulate that the risk is real, it's been obvious for 14 years that multiple 3oz bottles of Bad Liquid could be recombined beyond the checkpoint to do whatever it is liquids do at 3.0001oz.The liquid ban isn't just an inconvenience. It's not even just a burden on travelers who've collectively spent billions to re-purchase drinks and toiletries. It's a huge health burden to people with disabilities who rely on constant access to liquids.
https://www.youtube.com/watch?v=0m12mLXgO1A
And as we knew all along, the liquid ban was a nonsense, an authoritarian response to a cack-handed, improbable terror plot. It embodies the "security syllogism":
Something must be done. There, I've done something.
Think of all those checkpoints where all confiscated liquids were dumped into a giant barrel and mingled together: if liquids posed an existential threat to planes, they'd dispose of them like they were C4, not filtered water. No one believed in the liquid threat, ever. TSA can relax the restrictions and allow 12oz of anything labeled as hand-san through the checkpoints. There was no reason to confiscate liquids in the first place. But don't expect them to admit this. The implicit message of the change is "Pandemics make liquids safe."
Now onto data-caps. Like the liquid ban, data-caps have imposed a tremendous cost on Americans. In addition to the hundreds of millions in monopoly rents extracted from the nation by telcos through overage charges, these caps also shut many out of the digital world. They represent a regressive tax on information, one that falls worst upon the most underserved in the nation: people in poor and rural places, for whom online access is a gateway to civic and political life, family connection, employment and education.
We were told that we had to tolerate these caps because of the "tragedy of the commons," a fraudulent idea from economics that says that shared resources are destroyed through selfish overuse, based on no data or evidence.
https://thebaffler.com/latest/first-as-tragedy-then-as-fascism-amend
(By contrast, actual commons are a super-efficient way of managing resources)
https://www.onthecommons.org/magazine/elinor-ostroms-8-principles-managing-commmons
Telcos insisted that if they didn't throttle and gouge us, their networks would become unusable – but really, what they meant is that if they didn't throttle and gouge us, the windfall to their shareholders would decline.
What's more likely: that pandemics make network management tools so efficient that data-caps become obsolete, or that they were a shuck and a ripoff from day one, enabled by a hyper-concentrated industry of monopolists with cozy relationships with corrupt regulators?
So yeah, maybe this is the moment that kills Security Theater and data-caps.
https://techcrunch.com/2020/03/12/coronavirus-could-force-isps-to-abandon-data-caps-forever/
(Image: Rhys Gibson)

CBC postpones Canada Reads debates (permalink)
The folks at the @CBC have postponed next week's televised Canada Reads debates, so we're going to have to wait a while to find out who wins the national book prize.
https://www.cbc.ca/books/canada-reads-2020-postponed-1.5497678
Obviously, this is a bummer, though equally obviously, it's a relatively small consequence of this ghastly circumstance.
And on the bright side, the CBC have just released a ton of excerpts from the nominees:
https://www.cbc.ca/books/canadareads/read-excerpts-from-the-canada-reads-2020-books-1.5496637
If you're looking for some Canada Reads lit for this moment, my novella "Masque of the Red Death" appears in my collection Radicalized, one of the finalists. I put up the story as a free podast last night (thanks to Macmillan Audio for permission).
https://craphound.com/podcast/2020/03/13/the-masque-of-the-red-death/

Star Wars firepits (permalink)
West Coast Firepits went viral when they produced a Death Star firepit, though of course, I lusted after their Tiki Firepit.

https://www.westcoastfirepits.com/shop/tiki-firepit-69825
But now they're really leaning into the Star Wars themed pits, with an Interceptor pit ($2500):

https://www.westcoastfirepits.com/shop/interceptor
Or, if you prefer a post-apocalyptic version, there's a Crashed Interceptor pit, also $2500.

https://www.westcoastfirepits.com/shop/crashed-interceptor
If those prices seem high, consider that they're hand-made onshore, and contain 750lbs of 1/4" and 1/8" steel.

This day in history (permalink)
#15yrsago How DRM will harm the developing world https://web.archive.org/web/20050317005030/https://www.eff.org/IP/DRM/itu_drm.php
#5yrsago Anti-vaxxer ordered to pay EUR100K to winner of "measles aren't real" bet https://calvinayre.com/2015/03/13/business/biologist-ordered-to-pay-e100k-after-losing-wager-that-a-virus-causes-measles/
#1yrago A massive victory for fair use in the longrunning Dr Seuss vs Star Trek parody lawsuit https://www.techdirt.com/articles/20190313/09554041791/big-fair-use-win-mashups-places-youll-boldly-go-deemed-to-be-fair-use.shtml
#1yrago A detailed analysis of American ER bills reveals rampant, impossible-to-avoid price-gouging https://www.vox.com/health-care/2018/12/18/18134825/emergency-room-bills-health-care-costs-america
#1yrago Ketamine works great for depression and other conditions, and costs $10/dose; the new FDA-approved "ketamine" performs badly in trials and costs a fortune https://slatestarcodex.com/2019/03/11/ketamine-now-by-prescription/
#1yrago Facebook and Big Tech are monopsonies, even when they're not monopolies https://www.wired.com/story/facebook-not-monopoly-but-should-broken-up/

Colophon (permalink)
Today's top sources: EFF Deeplinks (https://www.eff.org/deeplinks/), Waxy (https://waxy.org/), Slashdot https://slashdot.org).
Currently writing: I've just finished rewrites on a short story, "The Canadian Miracle," for MIT Tech Review. It's a story set in the world of my next novel, "The Lost Cause," a post-GND novel about truth and reconciliation. I've also just completed "Baby Twitter," a piece of design fiction also set in The Lost Cause's prehistory, for a British think-tank. I'm getting geared up to start work on the novel next.
Currently reading: Just started Lauren Beukes's forthcoming Afterland: it's Y the Last Man plus plus, and two chapters in, it's amazeballs. Last month, I finished Andrea Bernstein's "American Oligarchs"; it's a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I'm getting really into Anna Weiner's memoir about tech, "Uncanny Valley." I just loaded Matt Stoller's "Goliath" onto my underwater MP3 player and I'm listening to it as I swim laps.
Latest podcast: When Sysadmins Ruled the Earth https://craphound.com/podcast/2020/03/13/when-sysadmins-ruled-the-earth-2/
Upcoming books: "Poesy the Monster Slayer" (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we're having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
"Attack Surface": The third Little Brother book, Oct 20, 2020. https://us.macmillan.com/books/9781250757531
"Little Brother/Homeland": A reissue omnibus edition with a new introduction by Edward Snowden: https://us.macmillan.com/books/9781250774583
27 notes
·
View notes
Text
52 things I learned in 2019
Each year humanity produces 1,000 times more transistors than grains of rice and wheat combined. [Mark P Mills]
The maths of queuing are absolutely brutal and counter-intuitive. [John D Cook]
Emojis are starting to appear in evidence in court cases, and lawyers are worried: “When emoji symbols are strung together, we don’t have a reliable way of interpreting their meaning.” (In 2017, an Israeli judge had to decide if one emoji-filled message constituted a verbal contract) [Eric Goldman]
Harbinger customers are customers who buy products that tend to fail. They group together, forming harbinger zip codes. If households in those zip codes buy a product, it is likely to fail. If they back a political candidate, they are likely to lose the election. [Simester, Tucker & Yang]
Baijiu is the world’s most popular spirit, with 10bn litres sold each year, almost entirely in China. The second most popular spirit in the world is vodka, with just 5bn litres sold. [Feyi Fawehinmi]
A Python script, an Instagram account and quite a bit of free time can get you free meals in New York City. [Chris Buetti]
At least three private companies have fallen victim to ‘deep fake’ audio fraud. In each case, a computerised voice clone of the company CEO “called a senior financial officer to request an urgent money transfer.” [Kaveh Waddell, Jennifer A. Kingson]
Drunk shopping could be a $45bn /year industry, and only 6% of people regret their drunk purchases. [Zachary Crockett]
Placebos are so effective that placebo placebos work: A pain cream with no active ingredients worked even when not used by the patient. Just owning the cream was enough to reduce pain. [Victoria Wai-lanYeung]
Since the 1960s, British motorways have been deliberately designed by computer as series of long curves, rather than straight lines. This is done for both safety (less hypnotic) and aesthetic (“sculpture on an exciting, grand scale”) reasons. [Joe Moran]
Between 1880 and 1916, Ireland had its own timezone, which was 25m 21s behind Greenwich Mean Time. After the Easter Rising, the House of Commons in London introduced GMT in Ireland and abolished Dublin Mean Time [Elena Goukassian]
Drug names are changing: X and Z names (Prozac, Seroxat) are giving way to names ending in O or A (Natesto, Qsymia) which are more appealing to speakers of Romance languages in Europe and South America. [Pascaline Faure]
The UK male suicide rate is the lowest since accurate records began in 1981. [Office for National Statistics]
The goal of walking 10,000 steps per day may have originated when a Japanese pedometer manufacturer noticed that the 万 symbol (which means 10,000) looks a little like someone walking. The actual health merits of that number ‘have never been validated by research.’ [Amanda Mull]
People hate asking sensitive questions. However, it turns out that people don’t hate being asked sensitive questions. So talking around difficult questions in research interviews is a waste of time and money. [Hart, VanEpps, Schweitzer]
The Korean Police force includes five labradors who are clones of ‘Quinn’, a bomb-sniffing dog who found fame after finding a missing girl’s body in a 2007 kidnapping. [Kim Tong-hyung]
As mobile phones became mainstream in the US in the early 1990s, the murder rate fell sharply. Street drug dealing became less popular, so gang-related turf wars were less common. (Other factors were also involved, obviously.) [Alexis C. Madrigal]
Mechanical devices to cheat your phone pedometer (for health insurance fraud or vanity) are now all over AliExpress. [Matthew Brennan]
In 2017 Google and Facebook lost $100 million between them to one scammer who sent them fake invoices. [Jeff John Roberts] [found by TomBot*]
Teenagers with acne get higher marks, are more likely to complete college and, if female, eventually get paid more than people without teenage acne. [Hugo M. Mialon & Erik T. Nesson]
72% of classical musicians have taken beta blockers for performance anxiety. [Composed]
Black women in the United States die in childbirth at roughly the same rate as women in Mongolia. [Annie Lowrey]
Sometime in the 1990s, it seems the US forgot how to make a critical component of some nuclear warheads. [Nick Baumann]
“Mushrooms and truffles are fungi, more closely related to humans than they are to plants.” [Lynne Peskoe-Yang]
In the US Northwest, rain can damage the fruit on cherry trees. So helicopter pilots are paid to fly over the orchards, using their downdraft to dry the fruit as it ripens. For the pilots, it’s a risky but potentially profitable job. [Maria Langer]
Gravitricity is a Scottish startup planning to store energy by lifting huge weights up a disused mine shaft when electricity is cheap, dropping them down to generate power when it is expensive. Using a 12,000 tonne weight (roughly the weight of the Eiffel tower), it should be half as expensive as equivalent lithium ion battery. [Jillian Ambrose]
Spotify pays by the song. Two three minute songs are twice as profitable as one six minute song. So songs are getting shorter. [Dan Kopf]
Fashion++ is a Facebook-funded computer vision project that looks at a photo of your outfit and suggests ‘minimal edits for outfit improvement’ like tucking in a shirt or removing an accessory. [Wei-Lin Hsiao & co] (In 2019, Fluxx helped launch Vogue Business.)
Three million students at US schools don’t have the internet at home. [Michael Melia & co]
No babies born in Britain in 2016 were named Nigel. [Jonathan Ore] (Correction: Robert Colvile, who broke the original story, points out that there could have been one or two Nigels in 2016 — the ONS only reports names with three or more examples)
Using machine learning, researchers can now predict how likely an individual is to be involve in a car accident by looking at the image of their home address on Google Street View. [Kinga Kita-Wojciechowska]
In 2018, the Nigerian government spent more on subsidies for petrol than on health, education, or defence. [Andrew S Nevin]
According to WaterAid research, women spend 97 billion hours a year looking for a safe place to go to the loo. That equals 46 million working years, which is the same workforce as Germany, the fourth largest economy in the world. [Caroline Criado Perez via Tanya Gold]
28% of people like the smell of (their own) urine after eating asparagus.[Rolf Degen]
AliBaba is investing $15m to research Chinese dialects, hoping to improve the performance of their voice recognition systems. [Emma Lee]
At least half of the effort of most AI projects goes on data labelling, and that’s often done in rural Indian villages. [Anand Murali]
Worldwide, growth in the fragrance industry is lagging behind cosmetics and skincare products. Why? ‘You can’t smell a selfie’. [Andrea Felsted and Sarah Halzack]
CD sales still make up 78% of music revenue in Japan (compared with less than 30% in the UK). Japanese pop fans have been encouraged to buy multiple copies of their favourite releases to win rewards (buy 2,000 copies, win a night at a hot spring with your favourite star). One 32 year-old fan was charged with illegally dumping 585 copies of a CD on the side of a mountain. [Mark Mulligan] [found by TomBot*]
Two disgruntled game developers wrote a script to generate and release identical but differently-named slot machine apps (sample names: Deer Antler Spray Slots, 3D Ravioli Slots). Eventually, the slot machine apps earned them $50,000. [Alex Schwartz & Ziba Scott]
80% of prisoners released late 2018 in a presidential pardon have opted to return to Kinshasa’s infamous Makala jail due to lack of means to live. [Olivier Kalume]
Disco, a Japanese high tech manufacturing company, has introduced an internal billing and payment system, where every cost is charged back to workers. Renting a conference room costs $100. “People really cut back on useless meetings,” says one staffer. [Yuji Nakamura & Yuki Furukawa]
A man who bought the personalised number plate NULL has received over $12,000 of parking fines, because the system records ‘NULL’ when no numberplate has been recorded. [Jack Morse]
The islands of Orkney generate 120% of their energy needs using wind and solar. However, 57% of homes in Orkney are in fuel poverty, where a household spends more than 10% of income on fuel. [Chris Silver] (This year I worked briefly with Community Energy Scotland on a project with Energy Systems Catapult)
Some blind people can understand speech that is almost three times faster than the fastest speech sighted people can understand. They can use speech synthesisers set at at 800 words per minute (conversational speech is 120–150 wpm). Research suggests that a section of the brain that normally responds to light is re-mapped in blind people to process sound. [Austin Hicks & R Douglas Fields]
SpottedRisk is a disgrace insurance company built on data: “Firstborns are at slightly higher risk of disgrace, as are those… who’ve suffered recent breakups — until the passage of time sends the bereft partner back down the ‘risk-decay curve.’” [Boris Kachka]
SDAM (Severely Deficient Autobiographical Memory) is a rare syndrome where otherwise healthy, high-functioning people are unable to remember events from their own life. There is also an exhausting syndrome called Highly Superior Autobiographical Memory, where people can remember precise details about every single day of their life. [Palumbo & Alain]
“Polling by phone has become very expensive, as the number of Americans willing to respond to unexpected or unknown callers has dropped. In the mid-to-late-20th century response rates were as high as 70%… [falling to] a mere 6% of the people it tried to survey in 2018.” [The Economist]
In 2012, only one sports team (Manchester United) was worth more than $2bn. Today, there are 52 sports teams worth more than $2bn. [Kurt Badenhausen]
Flamin’ Hot Cheetos were invented by a cleaner at a Frito-Lay factory. He’s now VP of multicultural sales for PepsiCo America. [Zachary Crockett]
Six reluctant Chinese hitmen who hired each other to carry out a murder went to jail when their outsourcing scheme collapsed. [Eric Cheung]
Fast fashion is hitting the wiping rags businesses, because some clothing is just too badly made to be sold as rags. [Adam Minter] (In January, Fluxx worked with Fibretrace to develop new ways to make the circular economy work in fashion.)
Asking ‘What questions do you have for me?’ can be dramatically more effective than ‘Any questions?’ at the end of a talk. (Many more good tips in this thread. [Jacqueline Antonovich]
2 notes
·
View notes
Text
Jio New Recharge Plan – Reliance Jio stoped unlimited voice calling and started charging!

HIGHLIGHTS New Recharge Plan for Jio Prime Customers New Recharge Plan for Jio Phone Users Top Voucher & Talktime Details New Call Charges Details in Jio How to Check Jio Balance 10 Things to Know about Jio's new rules Why Jio is Charging for Voice Calls? Future Jio charges possibilities Reliance Jio The biggest Telecom Operator in India announced on 10-October-2019 that they are stopping unlimited calling to others network and start charging to their customers 6 per minute for voice calls made to other telecom network. This would have no doubt come as a biggest shock for Jio users who have been enjoying free unlimited voice calls till date. Jio, which came the Indian telecom market with a newly and created a massive war ever since. Jio is doing this to recover the 6 paise/minute IUC (Interconnect Usage Charge) that the corporate pays alternative telcos to use their network throughout calls. Customers can got to pay IUC charges till TRAI brings the fee all the way down to zero, that is predicted to happen on 2020. The new regulation by Jio is already in impact.
New Jio Recharge Plan - 2019
For Jio Prime User - Popular Prepaid Plans Applicable for Android, Apple iOS & 4GB Handset Users PLAN Recharge Validity Prime Membership (FRC) - For new subscriber only. - Access to Jio Money - Jio TV - Jio Cinema - JioSaavn Music - Unlimited Jiotune Rs. 99/- 1 Year (Officially) Plan 399 + 10 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 124 Minutes for others network voice calling Rs. 399/- + Rs. 10/- 84 Days Plan 399 + 20 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 249 Minutes for others network voice calling Rs. 399/- + Rs. 20/- 84 Days Plan 399 + 50 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 656 Minutes for others network voice calling Rs. 399/- + Rs. 50/- 84 Days Plan 149 + 10 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 124 Minutes for others network voice calling Rs. 149/- + Rs. 10/- 28 Days Plan 149 + 20 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 249 Minutes for others network voice calling Rs. 149/- + Rs. 20/- 28 Days Plan 149 + 50 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 656 Minutes for others network voice calling Rs. 149/- + Rs. 50/- 28 Days For Jio Phone User - Popular Prepaid Plans These plans will work only if the Jio SIM is in JioPhone. PLAN Recharge Validity Plan 49 - 1GB High Speed Data - Unlimited Jio to Jio voice calling - 0 (Zero) Minutes for others network voice calling Rs. 49 28 Days Plan 99 + 10 - 0.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 249 Minutes for others network voice calling Rs. 99/- + Rs. 20/- 28 Days Plan 99 + 20 - 0.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 249 Minutes for others network voice calling Rs. 99/- + Rs. 20/- 28 Days Plan 99 + 50 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 656 Minutes for others network voice calling Rs. 99/- + Rs. 50/- 28 Days Plan 149 + 100 - 1.5 GB per Days High Speed Data - Unlimited Jio to Jio voice calling - 1362 Minutes for others network voice calling Rs. 99/- + Rs. 100/- 28 Days Top Up Voucher Details - Reliance Jio The voucher benefits works when you have activated any main plans. PLAN Talk-time Validity 10/- Rs 7.47 Unlimited 20/- Rs 14.95 Unlimited 50/- Rs 39.37 Unlimited 100/- Rs 81.75 Unlimited 500/- Rs 420.73 Unlimited 1000/- Rs 844.46 Unlimited
Call Charges for Jio Subscriber - 2019
If your questing is "What is the call charges from Reliance Jio?" here is the answer. Network Charges Jio to Jio - from Jio to Jio Numbers - Local & STD 0.00/- Jio to Others Operator - Mobile - Land Line - Local - STD 6 paisa /min ISD Calls Rs. 0.5/- to 100/- per min (based on country)
How to Check Balance in JIO
In 4 easy way you can check your Jio balance, Data and Validity- Dial *333# to check balance & validity Install MyJio App (for smart phone users only) Give a missed call to 1299 Login to to Jio Website Here's a fast 10-point explainer of what this implies to you for New Charges in Jio: 1. underneath the new rules, a Jio subscriber line of work somebody employing a completely different operator like Airtel or Vodafone-Idea are charged half-dozen paise per minute until the time you retain ringing. The 6 paise per minute charge are created through IUC indefinite quantity vouchers. 2. Jio is providing four new IUC plans that conjointly go along with further knowledge edges so as to make sure there's no increase in tariff for purchasers. -- The Rs ten set up offers 124 IUC minutes to non-Jio numbers and 1GB further knowledge. -- The Rs twenty set up offers 249 IUC minutes and 2GB knowledge. -- The Rs fifty set up offers 656 IUC minutes and 5GB knowledge -- The Rs one hundred set up offers one,362 IUC minutes and 10GB knowledge. 3. Jio assures that the half-dozen paise per minute charge can solely apply for Jio users line of work non-Jio users. All Jio to Jio calls can still stay free as can all incoming calls, Jio to phone line calls and calls created mistreatment WhatsApp, FaceTime and alternative similar platforms. 4. Jio says that it's been hit by the worth differential of free voice on Jio network and high tariff on 2G networks on Airtel and Vodafone-Idea. Jio says it receives 25-30 large integer uncomprehensible calls daily by 2G users, which ends in 65-75 large integer minutes of outgoing traffic instead of incoming traffic. 5. 2 years past, TRAI brought down IUC charge from fourteen paise to six paise per minute with associate intention to scrap the charge from Jan one, 2020. because of the high tariff on 2G networks, Jio is presently web|internet|cyber web|net|cyberspace|information superhighway|world wide web|Infobahn} money handler of IUC whereas Airtel and Vodafone plan square measure net revenue gainers, Economic Times reports. "So far, within the last 3 years Jio has paid nearly Rs thirteen,500 large integer as web IUC charges to the opposite operators," Jio aforementioned within the statement. 6. TRAI recently set to hunt views on delaying zero IUC charge as there square measure still voluminous 2G subscribers UN agency haven't enraptured to VoLTE, thus it looks unlikely that the zero-IUC regulation can inherit result any time presently. 7. Analyst say that Jio's move can profit rivals Airtel and Vodafone-Idea, that has been hurt financially for the past few years because of the ultra-low tariffs offered by Jio. Now, Airtel and Vodafone-Idea could use this chance to hike voice rates, transportation associate finish to the tariff war. 8. Vodafone plan skillful Jio's move during a statement expression that the announcement "comes closely to the action taken recently to doubtless hurt revenues of alternative operators with its recent unilateral action of reducing ringing time." the corporate adds, "Vodafone plan operates basis the singular principle of pro-consumer and pro-choice. consequently, our offerings square measure fully clear, reasonable and cater to a cross section of society and customers with variable consumption wants via multiple technologies 2G, 3G and 4G." 9. Airtel conjointly issued an announcement wherever it reiterates Vodafone Idea's position that the telecommunication business is during a state of deep money stress. The adoption of VoLTE has been slow whereas 2G subscribers square measure still high, inflicting associate imbalance in traffic. "Given the huge 2G client base in India, value|the value|the price} of the decision at half-dozen paise is already considerably below the important cost of finishing the decision." 10. Jio says the IUC rate are charged until the time TRAI moves to zero termination charge, that is anticipated to happen by New Year's Eve, 2019. Conclusion Why is Jio doing this? Jio needs the TRAI to travel for zero IUC charge which looks to be happening by early 2020. whereas different operators charge their customers for calls, Jio offers free calls on its network and therefore, it's connected losses as Jio pays the IUC charge for each decision created to a different network. "The change to the IUC laws in 2017 was once goodly deliberations and consultations. during this background the consultation paper has created regulative uncertainty and so Jio has been compelled, most reluctantly and inevitably, to recover this regulative charge of vi paise per minute for all off-net mobile voice calls farewell as IUC charges exist," says Jio. When can the IUC charges finish for Jio customers? "Jio once more assures its thirty five large integer customers that the vi paise per minute charge on outgoing off-net mobile calls shall continue solely until the time TRAI abolishes IUC, in line with its gift regulation," says Jio. Credit & Thanks: Picture Credit: Pixabay News Credit: Times of India, Business Today, Jio Press Release Content & Information Credit: Wikipedia, Jio Official Website If you find the information useful please give appropriate rating and share. If you still have any questing or any doubt please comment below. Read the full article
1 note
·
View note
Note
What defines radical feminism as opposed to other forms of feminism, and why should people who espouse it be blocked? If you have a link to an explanation at the top of your page or something I'd appreciate just a link, as I browse Tumblr mobile and can't see it. Sincerely asking, btw. I've seen terms used in varying ways and the categories of feminist thought seem blurry to me.
Classes of feminism are not very sharply defined. Any feminist can espouse ideas influenced by radical feminism, and vice versa. Indeed, intersectional feminism is a reaction to and evolution of radical feminism.
Feminism in the Western world is roughly sorted into four “waves.” Non-western feminism addresses different cultural needs than western feminism and does not necessarily follow these patterns. It emphatically does not follow this timeline.
What we consider first wave feminism arose from upper class white women in the late 19th century. The suffragette movement, reduction of hysteria diagnoses, etc were “first wave” actions. By far, the first wave was the wave of respectability. In a world where women were property, being seen as human was already a large task.
The methodology used to achieve this “humanization” was very much focused on improving the state of the uppermost class of women, with vague notions of “coming back for the rest” later. Or not at all.
Nevertheless, first wave feminism- what we might today call “white feminism”- was the foundation upon which later western feminist ideologies were built. It is also where the first strides towards legal equality for women (voting rights, inheritance law, etc) came from.
The second wave of feminism arose in the 1960s, alongside other major protest cultures. Modern radical feminism generally considers itself to be “second wave.” Where the first wave focused on basic legal rights of personhood, the second wave focused on social limitations and domestic rights, as well as examining the specific struggles and consequences of being a woman in a man-centered society.
This included things such as attempting to abolish dress codes that required excessive levels of modesty or infringed on the freedom of expression of women. It also included successes such as no-fault divorce, domestic abuse studies and shelters, title IX sports and education protections, etc.
It also included and fostered an enormous amount of hatred towards men. The second-wave was the wave of militancy and separatism. There was a persistent belief that if men could be eliminated from the lives of women, women would magically become utopian creatures.
This fostering of separatist attitudes also exacerbated a lot of what we would now call intersectional issues: any woman who disagreed with the party line was clearly just hypnotized by the patriarchy, and needed to be forced to agree with the party.
This led to ignoring a lot of very valid concerns from a great many women. Such as:
+ Ssecond wave feminism’s separatist attitude seeking in many cases to separate women from their sons and other beloved male family members,
+ The hatred of women who were assigned male at birth,
+ The hatred of women who worked with or for men, especially those who worked in sex,
+ Hatred for sexuality involving men,
+ Hatred for sexuality between women,
+ Hatred for women of color,
+ Hatred for religions and religious women involved in anything other than Christian derived mother-goddess paganism,
And so on.
These are problems that still exist in today’s “radical feminists” who seek to recreate, or never left, the second wave. Indeed, while transgender status prior to the rise of second wave feminism’s influence in the US was hardly a cakewalk, it was second wave feminists, with their hatred of all things “male” who exacerbated tensions, or entirely created new ones, and created many of the most horrifying aspects of transphobia that we see today.
The third wave of feminism rose in the late 80s and early 90s.
Taking inspiration from the many, many, many women who were attacked and hated by second wave policies, the third wave of feminism, today called, “intersectional feminism,” sought to examine just what it was that caused women who weren’t in the ruling class of feminist momvements throughout history to experience a combination of patriarchal misogyny and hegemonic racism/queerphobia/classism that was greater than the sum of its parts.
Many Black and queer feminist scholars were especially active and especially well regarded during this time period. The expansion of queer theory and racial equality efforts in academia and certain public sectors including child education in the third wave time period was also a prominent influence on third wave feminism.
One especially important aspect of third wave feminism was individualism. The belief that there is no “one right way” to be a woman, and that womanhood is necessarily influenced by the individual’s other identities, as well as their internal truths. This is what led to many feminine subcultures: feminine academics, feminine punks, feminine queers.
Unfortunately, one draw back of the third wave’s strong focus on individualism was that it lacked the cohesive force of early waves. Organization of large scale protest and revolution is very difficult when no one can entirely agree on what is being fought for.
Another critical factor of the third wave, and the defining point between third and fourth wave feminism, is that the third wave existed before the spread of internet access and internet culture. This contributed to the communication problems and scale problems third wave feminists experienced.
The fourth wave of feminism is where we currently exist today.
In effect, it is the third wave, but with broadly accessible systems of communication and organization. Intersectionality 2.0, as it were.
Information overload is common in fourth wave spaces. While everyonenow knows what conflicting access needs are, at least, there is little experience in satisfactorily dealing with them.
Because so much of fourth wave feminism is “talking the talk” rather than “walking the walk,” it gives the impression of being a toothless cacophony of young modern feminists screaming at each other incoherently. Because everyone has a platform, it is difficult for leaders to emerge who are not falling back on earlier, more “cohesive” waves: the first and second.
On the other hand, when everyone has at least the potential to have a voice, then people who have existed in silence for generations finally get to speak: people with multiple stacking intersections of marginalization. People who lack the access to historic methods of learning feminist theory can now get a firm foundation in gender equality without needing to pay for 4 years at a liberal arts college. People who are too weird, too queer, to black or brown or disabled or fat or traumatized to participate in the historical forums of feminism can participate in the fourth wave, due to its strong online presence.
With easy, omnipresent recording and data collection methodologies, it becomes increasingly difficult for people to deny the existence of misogyny. With easy, omnipresent communication platforms, this data can be spread to people it could reach before. People who are trapped in controlled environments of abuse, people who are too poor or disabled or anything else to escape the small town hyper-conservative bubble they were born into.
The fourth wave has been “in progress” for between 6 and 10 years, depending on who you talk to. Currently, it doesn’t have a catchy name, but if I were going to give it one, I might call it “accessible feminism.” The barriers to entry have never been lower.
And yet, it has its many problems, too.
No social movement is perfect, because the people involved in it are not perfect. And each wave of feminism overlaps with and influences those that came before and after it.
But, given the choice, I would say each subsequent wave of feminism has been “better” than those before it, and I would also say that no wave of feminism was as openly and violently hostile as second wave feminism and the radical feminists who still espouse it. That it was more effective than the first wave is a point in its favour, but little else is.
That many modern radical feminists seek to undo the leaps and bounds we have made in the decades since radical feminism fell out of favour as the dominant feminist ideology is somewhere between regressive and openly horrifying.
So, I suppose that wasn’t necessarily as helpful as it could have been, in terms of specifically identifying radical feminist ideology today.
But with any luck, it has given you enough of a foundation upon which to build your own research in the future.
XOXOX
💮 Yazminx 💮
PS: The title of our blog is a pun. You should only block people who you, personally, feel should be blocked. If you want to use our work as a guideline, then by all means do so. However, we are not operating any kind of blocklist here.
78 notes
·
View notes
Text
Reliance jio plan of rupees 2999 valid for 12 months active sim voice call data sms internet free in 250 monthly charges
Reliance Jio annual plan: There are many customers who are looking for an annual subscription for themselves. So that there is no tension to charge them every month. Here you are told about one such annual plan of Rs 2,999 from Jio whose monthly expenses are around Rs 250. In Jio’s Rs 2,999 plan, your SIM card is active all year. Not only this, since the SIM card is active, customers also get…

View On WordPress
0 notes
Text
Changes in the Past and Future of Robotic Process Automation
Robotic processes Automation (RPA) is one of the most interesting developments in business process management (BPM) in recent history. Some industry experts believe that it can be even more transformative than cloud computing.
However, is this game changing technology so new? Any BPM practitioner with a sense of history knows that RPA has been around for a long, long time. For example, inbound call centers have been using interactive voice response systems (IVRS) for years. These systems employ robots to guide clients, accept the tone of the keys or voice-based responses and pass the instructions to the underlying application to complete a transaction. Similarly, optical character recognition (OCR) technology, also classified as software robots, has been used for some time to offer high automatic extraction efficiencies. In addition, since the advent of web-based solutions, the industry has always used Internet BOT (abbreviated form for robots) for the automatic publication of data. The software testing industry has used a similar type of automation for many years to publish data in applications to manage functional, integration, users and, more significantly, regression tests.
What is different from the latest wave of RPA is the maturity of both the technology and the business processes to which it applies. The RPA market is advancing rapidly, and the widespread adoption of robotic automation could radically reshape the BPM market. In my opinion, this transformation will be driven by the search for five results:
Cost reduction: software robots generally have at least one third of the price of an offshore FTE.
Efficiency: RPA can operate 24x7 without interruptions as long as the underlying applications are available.
Accuracy: Human FTEs make errors in data entry, while robots perform the same task in the same way as long as a judgment call is not required when processing transactions.
Improved audit and regulatory compliance: robots can provide detailed audit records that enable advanced business analysis and better compliance.
Easy change management: robots preserve the integrity of the application and data by leveraging the existing application's presentation layer and reusing application logic, existing databases and validation without deep understanding or reengineering.
In summary: RPA is not new. Undoubtedly, you and your organization have already been affected by robotic automation in one way or another. However, they say that there is nothing as powerful as an idea whose time has come. And the moment of transformation driven by RPA is now.
To get a best rpa training — rpa training in chennai | best rpa training in chennai | rpa training in bangalore | rpa training in pune | rpa online training
1 note
·
View note
Text
Understanding The Background Of SEO 2019
Content marketing plus SEO are two frequently utilized terms and broadly discussed subjects in digital marketing. Screaming Frog SEO Index tool does it for you personally inside a few seconds, even with regard to larger websites. SEOs also used to believe that buying links was the valid method of link developing; however, Google will now punish you for buying links within an attempt to manipulate page rank. Ultimately, achievement in SEO in 2018 plus forward will depend on generating amazing content and making this as easy as possible with regard to search engines like google in order to understand exactly what that content material is all about. Answer: When you focus about SEO for voice search an individual need to create your written content around long tail keywords because people tend to use a lot more words in voice search. SEO is the practice associated with increasing the search engine ratings of your webpages so that will they appear higher in lookup results, bringing more traffic in order to your website. In the particular previous example, Bob's home web page might have the title, "Bob's Soccer Store - Soccer Shoes or boots and Equipment. " The name is the most important component of SEO, since it shows the search engine exactly exactly what the page is all regarding. 47. When creating SEO content material, keep the social layer within your mind. For those who have time to get good search engine optimisation education, after that combine this knowledge with greatest practices and you are upon your way to become a good SEO expert. 46. Use SEO practices in order to optimize your social media content. 4. Mobile SEO plus Local Business: - As we all mentioned before, users tend in order to search for local business upon the smartphones. An extensive dental marketing plus dental SEO campaign can become attained by the enterprise just if the web address associated with a dental practice contains directly into all the promotional materials with regard to the business. This shows the importance of focussing voice search engine results within order to grow your company, marketing, and Search Engine Optimization(SEO) strategies. They obtain this by increasing their internet site rank through a method known as SEO or even search engine optimization. Just like most other SEO approaches, be certain your links are appropriate, plus be careful to not cross the particular line into excessive linking -- you don't want your website visitors to obtain annoyed. Bryan Yeager, Research Director at Gartner, may share 9 Key Insights through Gartner's Marketing Technology Survey in order to Help You Prepare for 2019 and Beyond. SEO is a combination associated with digital marketing efforts all functioning together to increase a web site's value to users and presence in search. On-page SEO (also recognized as "on-site" SEO) will be the action of optimizing different parts associated with your site that affect your own search engine rankings. In 2019, we'll have to optimize voice research answers with CTAs that Google's algorithms don't pick up upon, but humans do. Dan Mallette, Lead SEO Strategist at each InVue Digital & HearstDMS, forecasts that SEOs will need in order to optimize for voice search in order to find new avenues as SERP real-estate shrinks. Obviously, a social networking web page that has more interaction will bring bigger SEO benefits in order to some business than one that will has less interaction, but basically having a social presence is usually a good start. SEO differs from local lookup engine optimization in that the particular latter is targeted on customizing a business' online presence therefore that its web pages is usually going to be displayed simply by search engines when a consumer enters a local search regarding its products or services. The challenge for webmasters plus SEO is that Google will not want company owners to rank regarding lots of keywords using autogenerated content especially when that creates A LOT of pages upon a website using (for instance) a list of keyword variants page-to-page. In time, the collection between social networking management, channel advancement, and SEO will be considerably blurrier than it really is definitely today. In 2016, SEO experts have got determined which factors are almost all likely to affect your SEARCH ENGINE OPTIMIZATION rankings. Customers and marketers will need in order to begin implementing multiple forms associated with digital marketing tactics including compensated search, social media marketing, nearby SEO, in addition to SEARCH ENGINE OPTIMIZATION if they hope to control a given Google SERP. Before beginning with this, the SEO experts should visit your business and realize each and every aspect associated with your company so that these people can help your achieve your own marketing goals. What really matters in SEARCH ENGINE OPTIMIZATION in 2018 is what a person prioritise today to ensure that will in 3-6 months you may see improvements in the high quality of your organic traffic. Mobile will account for 72% of US digital ad invest by 2019. Search engine optimization (SEO) is one of the particular most important marketing things to consider about your studio website. SEO might generate a sufficient return upon investment However, search engines are usually not taken care of organic search visitors, their algorithms change, and presently there are no guarantees of continuing referrals. An excellent starting point whenever using keywords for SEO is definitely to identify existing pages that will may use some optimization. These are called keywords, plus as you will see, these people are an important part associated with SEO. In fact, this particular will actually hurt your home page's SEO because search engines such as google will recognize it because keyword stuffing - or the particular act of including keywords particularly to rank for that key word, rather than to answer the person's question. Prior to we begin, one thing a person want to keep in brain when using one of the following SEARCH ENGINE OPTIMIZATION elements is not to overdo it. You might be enticed to shove a lot associated with keywords onto your pages, yet that is not the objective. In situation you create links to additional websites and reverse, it will certainly improve your SEO ranking. In fact Cisco predicts that globally, on-line video traffic will be eighty percent of all consumer Web traffic by 2019 (a amount that is up from sixty four percent in 2014). I've bookmarked therefore many SEO websites and sources that it's overwhelming to actually look at. Link authority is the major component of SEO, yet purchasing links is forbidden simply by Google, Bing, and other research engines.

SEO organizations are able to track almost every aspect of their technique, like increases in rankings, visitors and conversions. The methods which were the simplest (reciprocal links or directory submissions) perform not work anymore, therefore the particular SEOs spend a lot associated with time trying different approaches. The particular Moz Pro is another place of Tools that check the particular important factors related to your own website's search ranking. Selection of key phrases or phrases plays an essential component in an SEO campaign considering that it saves you the pictures in the dark. In 2019 the particular digital marketing companies can anticipate a lot of voice queries, and by 2020, about 50 percent of the searches will become either voice searches or image-based searches. Read our Mobile SEO 2019 Checklist before you decide in order to implement. This first element of optimizing images is definitely including your keywords in this image file name (seo_guide. jpg). The inevitable adjustments that will occur in SEARCH ENGINE OPTIMIZATION in the near future are usually abolition of keywords stuffing plus spam backlinks, real-time personalized customer support by online marketers, improvement within the quality of visual content material as a result of creativity of video SEO, optimization associated with websites with conversational keywords plus generating massive quantity of current data. SEARCH ENGINE OPTIMIZATION remains one of the lengthy term marketing strategies that function best for companies that are usually looking to improve their on-line visibility.

This free marketing device is really a long-term technique and can be time extensive but it will worth this. A good user experience is definitely the key to satisfaction and also a powerful SEO. 1 SEO might target different kinds of research, including image search, video research, academic search, 2 news research, and industry-specific vertical search motors. All of us are in the fourth fraction of 2018, it is typically the right time start thinking concerning the year ahead and fresh changes SEO realm might anticipate. We've long known that client opinions, input, and sentiment regarding a brand deeply impact SEARCH ENGINE OPTIMIZATION rankings, but we wanted the particular information to prove it. Off-page SEO means having action to build trust, expert, social signals and inbound hyperlinks. How video affects SEO actually depends on your goals whenever using video in your marketing and advertising campaign and which video system you use. LSI is not really what most SEO professionals claim it to be. This is certainly not a idea that can be used simply by the average web designer or even webmaster to improve their lookup engine listings, and it will be not what many people, which includes myself, has written it in order to be. Nevertheless, first some history. This particular video walks you through the particular specific steps you have to get increased rankings in 2018, including launching speed, technical SEO, content, hyperlinks, and more. Considering that it is, all across this year companies specializing in SEO were active recovering and finding new procedures to optimize the search motor even better than what their particular competitors were doing. Carrying out technical SEARCH ENGINE OPTIMIZATION for local search engines will be really a similar process. Search engine optimization (SEO) is definitely a way to generate even more (and desired) traffic to your own site with the help associated with better search engine rankings with regard to a keyword. SEO had gone through drastic changes over the yrs and getting higher rankings upon search engines by stuffing the particular information with too many key phrases is a thing of the particular past. This should become a crucial part of any local SEARCH ENGINE OPTIMIZATION checklists, as reviews and rankings could make it easier to stand out in search engine results. Lookup Engine Optimization, or SEO, need to rank in as one associated with the biggest part of your own finances for online advertising. SEO or even Search Engine Optimisation is the particular name given to activity that will attempts to improve search motor rankings. Search engine marketing Ten Taboos About SEO 2019 You Should Never Share On Twitter (SEO) is the procedure intended for affecting the visibility of the website or a web web page in a web search engine's unpaid results—often referred to since " natural ", " natural ", or "earned" results. Nearby SEO utilizes a variety associated with strategies — getting your web site ranked on search engines such as Google, business directories such because Yelp, Superpages, Foursquare, Yellowbook, Search engines My Business listing, Bing Areas for Business page, localized content material on your website, online evaluations and other strategies. We frequently compose in-depth analyses on the method SEO and digital marketing will be used to improve the traffic in order to various websites. Given that lookup engines have complex algorithms that will power their technology and everybody's marketing needs are unique, wish unable to provide specific SEARCH ENGINE OPTIMIZATION advice to our customers. All of us think SEO in 2019 might find a shift to focusing a lot more on user intent, problem resolving, and hyper locality in purchase to capitalize on the ongoing rise of voice search. Private demographic information would come in a great deal handier in 2019 as much as the ranking of key phrases is concerned. Links are one of the particular most important SEO ranking elements. However, more advanced that will readers will recognize the reduce quality of sites employing dark hat SEO at the expenditure from the reader experience, which usually will reduce the site's visitors and page rank over period. So - THERE IS SIMPLY NO BEST PRACTICE AMOUNT OF FIGURES any SEO could lay down since exact best practice to GUARANTEE a title will certainly display, in full in Search engines, at least, since the search little title, on every device. While getting as many pages listed in Google was historically the priority for an SEO, Search engines is now rating the high quality of pages on your own site plus the type of pages this really is indexing. Jerrika Scott, Digital Marketing Specialist from Archway Cards Ltd, also feels in voice being the craze of 2019 rather than 2018. Today, regardless of all the hype about regardless of whether SEO is dead, we discover that organic search is nevertheless one of the highest RETURN ON INVESTMENT digital marketing channels. The Technical Audit Checklist Produced For Human Beings — Within this post by Distilled, a person will find a link in order to a Google sheet that offers an technical SEO audit guidelines and links to resources upon how to complete each checkbox. Then each time the term SEO appears on your web site, it's automatically changed into the link you specified. Keyword Study for SEO: The Definitive Guideline — This comprehensive guide simply by Brian Dean teaches you the number of strategies for getting keywords and determining intent with regard to your target market. On-page and off-page SEO function together to improve your lookup engine rankings in complementary style; however, SEOs generally advise obtaining your on-page SEO ducks within a row before focusing as well much on off-page SEO. Within 2019, web-based businesses will follow more voice-to-text technology to boost engagement and search activity. There are many SEO internet sites suggesting that they can offer a service to make our own website LSI friendly, or satisfy ‘LSI requirements'. The particular art of web SEO is situated in focusing on how individuals search for things and knowing what type of results Search engines wants to (or will) screen to its users. Social press SEO would encourage your present customers to come back whilst helping you develop authority with regard to potential ones. He is an expert in SEO, Content Marketing, plus Pinterest Marketing. An SEARCH ENGINE OPTIMIZATION expert plays a huge function in helping companies build their particular businesses and attract new clients through website traffic.

Join us for the three-day, one-track conference full involving forward-thinking, tactical sessions in SEARCH ENGINE OPTIMISATION, growth marketing, the mobile panorama, analytics, content marketing, and even more. The objective regarding SEO is to get a new website ranked as high because possible on search engines, for example Google. In case you are improving user encounter by focusing primarily on the particular quality of the MC associated with your pages and avoiding : even removing - old-school SEARCH ENGINE OPTIMIZATION techniques - those certainly are usually positive steps to getting even more traffic from Google in 2018 - and the type associated with content performance Google rewards is usually in the end largely with least about a satisfying consumer experience. For instance, when I'm logged in to Google+ and We search for SEO, I have the following in my top 5 search results. Black head wear SEO practice involves breaking just about all of the rules and rules of the search engine. Every time you notice or hear the phrase research engine optimization, ” substitute exactly what create quality and indicating relevance” and you'll have the correct mindset permanently SEO work. SEOs conveniently call this effect ‘domain authority' and it appeared in order to be related to ‘PageRank' -- the system Google started in order to rank the web within 1998. In case you have more time plus are keen to follow the particular SEO industry, subscribe to Moz and Search Engine Land. Integrating these keywords into the blog post allows you to add range while still retaining SEO energy.

This guide will be made to describe all locations of SEO—from locating the terms plus phrases (keywords) that generate visitors to your website, to producing your web site friendly to search motors, to building links and advertising the unique associated with your own site. Without having SEO, a website can end up being invisible to search engines. On-page SEO refers to be able to every strategy, technique, and instrument you utilize within your internet site to optimize your web web pages and content for search machines like google. Today, the quality of inbound links is evaluated higher when compared with their quantity and may add your SEO efforts. Lookup engine optimization (SEO) tools assist companies position themselves to obtain a favorable ranking in internet search engine results. The particular second biggest SEO trend within 2019 will be voice lookup. Jooxie is long past mobile search plus voice-search being a ‘trend' -- they are the full upon normal now, outdoing desktop lookup in both volume and SEO-favorability. Rather compared to marketing at people, you require to make it possible intended for them to find you whenever they want you, and gowns where SEO is available within. Prior To going BlowFish SEO full Time, Robert Headed very successful internet incoming marketing campaigns for Bella Sante Day Spa's of Boston plus Red Door Spas increasing their particular yearly Gift Card Sales simply by over 400% and increasing consumer appointments over 300%. In 2019 and past, the majority of the on the internet searches will be in the particular form of conversation, and because a result, the online entrepreneurs will give more importance in order to artificial intelligence keywords for marketing of the web content. A great SEO service includes a great deal of research and lots associated with smart keywords application which may period website at a increased notch and provide it the higher ranking in Google web search engine. Professional SEO content authors work on creating articles just after understanding the nature associated with your business, your industry, competition and what kind of posts your business might most want for maximum benefits; in the particular short-term and the long-term. Linking to other webpages within your site, as well because linking to other sites plus getting other sites to url to yours, is a great method to improve your SEO. Influencer marketing doesn't seem in order to be slowing down anytime quickly, so it will probably obtain bigger in 2018 and actually bigger in 2019 when even more companies start to catch upon to this trend. Keeping within mind the last point, SEARCH ENGINE OPTIMIZATION agencies are fluent in navigating via a wide range of on the web marketing tools that helps raise the value of your marketing technique. Search Engine Optimization (SEO) will be a powerful process that may help make you and your own research more visible to research engines like Google and Search engines Scholar. I have simply no clue about SEO only several basics that is available almost all over the place and I actually feel this article must aid as your other articles assisted me give some direction upon recovering my lost traffic plus generating more content as properly as repurposing old content. With internet customers who use their mobiles in order to search on the increase, because an SEO consultant it can make sense to possess a look at the particular effects SEO marketing is putting on search engine optimization. The sole purpose of SEARCH ENGINE OPTIMIZATION Services is to improve your own search engine ranking. Guarantee redirected domains redirect through the canonical redirect and this too offers any chains minimised, although Produce sure to audit the backlink user profile for any redirects you stage at a page just such as reward comes punishment if these backlinks are toxic (another kind of Google opening up the particular war which is technical seo on a front it's not really, and in fact is speak, to building backlinks to your own site). In order to smoothen out the software plan interface problem, the web developing team as well as the particular SEO specialist work together in order to build the major search motors friendly programs and code that could be easily integrated into the user's website. They will possess to find SEO expert sites, who will help the company owner's site have many clients in internet marketing. This is mainly because they are not SEO pleasant and can affect your positioning significantly. These SEO crawler programs are similar to Google's own crawlers and will provide you an overview showing exactly how your page will perform within SEO rankings. Google is making certain it takes longer to notice results from black and white hat SEARCH ENGINE OPTIMIZATION, and intent on ensuring the flux in its SERPs structured largely on where the searcher is in the world during the particular time of the search, plus where the business is situated near to that searcher. Performing SEO upon your own websites is the great method to practice plus hone your SEO ability. We optimize your web site both of internal and exterior factors thats Google's engine believe in and reliable for top rank search result, Gurantee your SEARCH ENGINE OPTIMIZATION ranking No succeed can refundable. Looking deeper: An SEARCH ENGINE OPTIMIZATION cost often means one associated with two things: the investment inside your organic search strategy, or just how much you pay for compensated search engine marketing (SEM) providers like Google AdWords. All of us are dealing with new methods designed to target old design SEO tactics and that concentrate around the truism that WEBSITE ‘REPUTATION' plus Plenty of WEBPAGES plus SEO equals Plenty associated with Keywords equals LOTS of Search engines traffic. BrightonSEO is a one-day search advertising conference and series of coaching Blog9T courses held, unsurprisingly, in Brighton. From narrowing straight down target markets to changing the particular way content is written, AI and voice search will possess a continuous effect on SEARCH ENGINE OPTIMIZATION moving forward. One aspect of SEO will be link building, which we can discuss slightly below, which generally leads to thin content. Applications for this 2018-2019 cycle of the SEO Progress programme are now closed plus will re-open again in Springtime 2019. SEO could be complex because search engines are often reevaluating and changing how these people prioritize search engine results. Moreover, it will help SEARCH ENGINE OPTIMIZATION by gaining backlinks, likes, remarks or shares. Therefore, cheer up and tools up to policy for SEO- the particular organic top-ranking practice. SEARCH ENGINE OPTIMIZATION (search engine optimization) places your own website within the natural outcomes section of search engines. SEO is specifically important for businesses because it guarantees they're answering their audience's greatest questions on search engines, whilst driving traffic to their items and services. Regarding marketers who were brought upward in the ‘traditional SEO marketplace, ' 2018 is really the time to adapt or expire. White hat SEO includes most the SEO practices we've spoken about so far which possess a long term approach in order to site optimization and focus upon the user experience and exactly what people need. Cost effectiveness - SEO will be one of the most most affordable marketing strategies because it focuses on users who are actively searching for your products and solutions online. The reality is that you can obtain top Search engine ranking jobs spending a little bit associated with money and working on the particular project yourself or paying the professional Seo services thousands associated with dollars to get your Internet site on the first page. Although black hat SEARCH ENGINE OPTIMIZATION methods may boost a cyberspace search engine page rank within the short term, these strategies could also get the web site banned from the search motors altogether. According in order to research and advisory firm Forrester, programmatic marketing is expected in order to account for 50% of almost all advertising by 2019.

1 note
·
View note
Text
Will ‘Dr. Disinformation’ Ever Face the Music?
Earlier this month, Dr. Rashid Buttar posted on Twitter that covid-19 “was a planned operation” and shared an article alleging that most people who got the covid vaccine would be dead by 2025.
His statement is a recent example in what has been a steady stream of spurious claims surrounding the covid vaccines and treatments that swirl around the public consciousness. Others include testimony in June by Dr. Sherri Jane Tenpenny before Ohio state legislators that the vaccine could cause people to become magnetized. Clips from the hearing went viral on the internet. On April 9, 2020, Dr. Joseph Mercola posted a video titled “Could hydrogen peroxide treat coronavirus?” which was shared more than 4,600 times. In the video, Mercola said inhaling hydrogen peroxide through a nebulizer could prevent or cure covid.
These physicians are identified as members of the “Disinformation Dozen,” a group of top superspreaders of covid vaccine misinformation on social media, according to a 2021 report by the nonprofit Center for Countering Digital Hate. The report, based on an analysis of anti-vaccine content on social media platforms, found that 12 people were responsible for 65% of it. The group is composed of physicians, anti-vaccine activists and people known for promoting alternative medicine.
The physician voices are of particular concern because their medical credentials lend credence to their unproven, often dangerous pronouncements. All three continue to hold medical licenses and have not faced consequences for their covid-related statements.
But leaders of professional medical organizations increasingly are calling for that to change and urging medical oversight boards to take more aggressive action.
In July, the Federation of State Medical Boards, the national umbrella organization for the state-based boards, issued a statement making clear that doctors who generate and spread covid misinformation could be subject to disciplinary action, including the suspension or revocation of their licenses. The American Board of Family Medicine, American Board of Internal Medicine and American Board of Pediatrics issued a joint statement Sept. 9 in support of the state boards’ position, warning that “such unethical or unprofessional conduct may prompt their respective Board to take action that could put their certification at risk.”
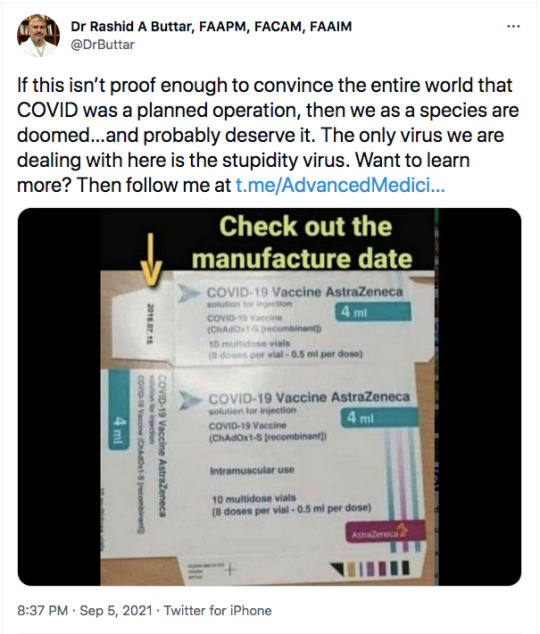
And the superspreaders identified by the center’s report are not alone. KHN identified 20 other doctors who have made false or misleading claims about covid by combing through published fact checks and other news coverage.
For example, at an Indiana school board meeting in August, Dr. Dan Stock claimed the surge in covid cases this summer was due to “antibody mediated viral enhancement” from people receiving covid vaccines. PolitiFact rated his claim “Pants on Fire” false.
Dr. Stella Immanuel, a member of a group America’s Frontline Doctors, which has consistently made false statements about covid, said in a video that went viral in July 2020 that masks weren’t needed because covid could be cured by hydroxychloroquine. Immanuel’s website currently promotes a set of vitamins, as well as hydroxychloroquine and ivermectin, as covid treatments.
Two of the doctors mentioned by name in this article responded to requests for comment. Mercola offered documents to rebut criticisms of his hydrogen peroxide covid treatment and took issue with the center’s “Disinformation Dozen” report methodology. Buttar defended his positions, saying via email that “the science is clear and anyone who contests it, has a suspect agenda at best and/or lacks a moral compass.” He also pointed to data from the Centers for Disease Control and Prevention’s Vaccine Adverse Event Recording System, considered inconclusive by many experts.
Since the onset of the covid pandemic, misinformation has been widespread on social media platforms. And many experts blame it for undermining efforts to curb the coronavirus’s spread. A recent poll showed that more than 50% of Americans who won’t get vaccinated cited conspiracy theories as their reasons — for example, saying the vaccines cause infertility or alter DNA.
Some physicians have gained notoriety by embracing covid-related fringe ideas, quack treatments and falsehoods via social media, conservative talk shows and even in person with patients. Whether promoting the use of ivermectin, an anti-parasitic drug for animals, or a mix of vitamins to treat covid, doctors’ words can be especially powerful. Public opinion polls consistently show that Americans have high trust in doctors.
“There is a sense of credibility that comes with being a doctor,” said Rachel Moran, a researcher who studies covid misinformation at the University of Washington. “There is also a sense they have access to insider info that we don’t. This is a very confusing time, and it can seem that if anyone knows what I should be doing in this situation, it’s a doctor.”
While covid is a novel and complicated infectious disease, physicians spreading misinformation generally have no particular expertise in infectious diseases. Dr. Scott Atlas, who endorsed former President Donald Trump’s unproven statements about the course of the pandemic, is a radiation oncologist.
Traditionally, the responsibility of policing physicians has fallen to state medical boards. Beyond overseeing the licensing process, these panels investigate complaints about doctors and discipline those who engage in unethical, unprofessional or, in extreme cases, criminal activity. Any member of the public can submit a complaint about a physician.
“The boards are relatively slow and weak and it’s a long, slow process to pull somebody’s license,” said Arthur Caplan, founding head of the Department of Medical Ethics at New York University. “In many states, they have their hands full with doctors who have committed felonies, doctors who are molesting their patients. Keeping an eye on misinformation is somewhat down on the priority list.”
To date, only two doctors have reportedly faced such sanctions. In Oregon, Dr. Steven LaTulippe had his license suspended in December 2020 for refusing to wear a face mask at his clinic and telling patients that masks were ineffective in curbing the spread of covid, and even dangerous. Dr. Thomas Cowan, a San Francisco physician who posted a YouTube video that went viral in March 2020 stating that 5G networks cause covid, voluntarily surrendered his medical license to California’s medical board in February 2021.
Dr. Humayun Chaudhry, president of the Federation of State Medical Boards, however, said it’s possible some doctors could already be the subject of inquiries and investigations, since these actions are not made public until sanctions are handed down.
KHN reached out to the medical and osteopathic boards of all 50 states and the District of Columbia to see if they had received covid misinformation complaints. Of the 43 that responded, only a handful shared specifics.
During a one-week period in August, Kansas’ medical board received six such complaints. In all, the state has received 35 complaints against 20 licensees about spreading covid misinformation on social media and in person. Indiana has received about 30 in the past year. South Carolina said it had about 10 since January. Rhode Island didn’t share the number of complaints but said it has taken disciplinary action against one doctor for spreading misinformation, though it hasn’t moved to suspend his license. (The disciplinary measures include a fine, a reprimand on the doctor’s record and a mandate to complete an ethics course.) Five states said they had received only a couple, and 11 states reported receiving no complaints regarding covid misinformation.
Confidentiality laws in 13 states prevented those boards from sharing information about complaints.
Social media companies have also been slow to take action. Some doctors’ accounts — specifically those among the Disinformation Dozen — have been suspended, but others are still active and posting misinformation.
Imran Ahmed, CEO of the Center for Countering Digital Hate, said social media platforms often don’t consistently apply their rules against spreading misinformation.
“Even when it’s the same companies, Facebook will sometimes take posts down, but Instagram will not,” Ahmed said, referring to Facebook’s ownership of Instagram. “It goes to show their piecemeal, ineffective approach to enforcing their own rules.”
A Facebook spokesperson said the company has removed over 3,000 accounts, pages and groups for repeatedly violating covid and vaccine misinformation policies since the beginning of the pandemic. Buttar’s Facebook and Instagram pages and Tenpenny’s Facebook page have been removed, while Mercola’s Facebook posts have been demoted, which means fewer people will see them. Tenpenny and Mercola still have Instagram accounts.
Part of the challenge may be that these doctors sometimes present scientific opinions that aren’t mainstream but are viewed as potentially valid by some of their colleagues.
“It can be difficult to prove that what is being said is outside the range of scientific and medical consensus,” said Caplan. “The doctors who were advising Trump — like Scott Atlas — recommended herd immunity. That was far from the consensus of epidemiologists, but you couldn’t get a board to take his license away because it was a fringe opinion.”
Even if these physicians don’t face consequences, it is likely, experts said, that the public health will.
“Medical misinformation doesn’t just result in people making bad personal and community health choices, but it also divides communities and families, leaving an emotional toll,” said Moran, the University of Washington researcher. “Misinformation narratives have real sticking power and impact people’s ability to make safe health choices.”
KHN (Kaiser Health News) is a national newsroom that produces in-depth journalism about health issues. Together with Policy Analysis and Polling, KHN is one of the three major operating programs at KFF (Kaiser Family Foundation). KFF is an endowed nonprofit organization providing information on health issues to the nation.
USE OUR CONTENT
This story can be republished for free (details).
Will ‘Dr. Disinformation’ Ever Face the Music? published first on https://nootropicspowdersupplier.tumblr.com/
0 notes