#cisco technology users lists
Explore tagged Tumblr posts
Text
What Can I Do With A Cisco CCNA Certification?
Cisco Certified Network Associates (CCNA) are one of the world's most sought-after network professionals. Having a CCNA certification opens up a wide variety of job opportunities and can lead to higher salaries.

A Cisco CCNA certification is valuable in terms of the potential salary and employment opportunities that result from this certification. MyComputerCareer also offers his CCNA training as part of the Cybersecurity Specialist Curriculum. For more information, please contact us immediately.
This article explains what a CCNA certification is, what it includes, and the skills it teaches. We will also discuss the different positions you can get with a CCNA certificate and the salaries you can earn with this certificate.
What Is The CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification is a well-known computer networking credential. CCNA certification helps entry-level network engineers, professional network engineers, support network engineers, and network administrators learn basic networking concepts.
Over one million CCNA certificates have been distributed to fully certified professionals since Cisco first introduced certificates in 1998. CCNA certifications cover a wide range of networking topics and help prepare learners for future advances in networking technology.
CCNA certification topics include:
OSI model: Physical Layer, Data Link Layer, Network Layer, Transport Layer, and Application Layer
IP routing: static and dynamic routing protocols
IP addressing: Fourth Generation IPv4 (IPv), Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), and Cisco IOS
Network security: Firewalls, password security, virtual private networks (VPNs), and intrusion detection systems
VLANs and WLANs: Access Control Lists (ACLs), VLAN Trunking Protocol (VTP), and Cisco Wireless LAN Controller (WLC) IP Services
Routing protocols (OSPF, EIGRP, and RIP): Cisco IOS, Cisco Express Forwarding (CEF), and Cisco Dynamic Multiprotocol Label Switching (DMVPN) WAN
CCNA certification validates many of the skills a network engineer needs. You will also need various soft skills such as communication, problem solving, organization and customer service. CCNA certification also provides network professionals with the information and skills they need to effectively operate Cisco and Microsoft Office suite applications. This certification empowers aspiring and current network engineers to use industry-specific tools in their daily work.
However, please note that Cisco certifications are valid for three years. If the certification expires, the holder may retake her CCNA certification exam, obtain another Associate certification, pass the Core Technology exam, or for renewal she must complete 40 Continuing Education (CE) credit must be obtained.
What IT Jobs Can You Get With a CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification validates a user's knowledge and skills in network administration. Salaries for this degree average about $80,000 per year. Many employees are looking for Cisco certified professionals because of their extensive experience with Cisco routers and switches. Cisco network equipment is used by most of the Fortune 500 companies.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Keep your network running smoothly and resolve any issues that may arise.
System Administrator: System administrators are responsible for the maintenance and operation of computer systems. It installs new software, patches existing software, and performs other tasks to keep your system running smoothly.
Network analyst: Network analysts are responsible for analyzing computer networks and making recommendations to improve their efficiency. They may also be responsible for designing new networks or implementing changes to existing networks.
Network design engineer: Network design engineers are responsible for designing and implementing computer networks. We work with our customers to understand their needs and design networks that meet those needs.
Infrastructure Engineer: Infrastructure engineers are responsible for the physical components of computer networks such as routers, switches, and cables. Install and maintain these components to keep your network running smoothly.
Unified Communications Engineer: Unified Communications Engineers are responsible for designing and implementing unified communications systems. Unified communication systems allow users to communicate across multiple devices such as phones, computers, and tablets.
Solution designer: Solution design engineers are responsible for designing and implementing solutions to problems encountered in computer networks. They work with customers to understand their needs and design solutions that meet those needs.
Cloud Engineer: Cloud engineers are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
Data Center Engineer: Data center engineers are responsible for the operation of data centers. Install and maintain the hardware and software that make up your data center.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Ensure the smooth operation of your network and fix any problems that may arise.
Cloud Architect: Cloud architects are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
VoIP Engineer: VoIP engineers are responsible for designing and implementing Voice over IP (VoIP) solutions. VoIP solutions allow users to communicate using voice and video over the Internet.
Cooperating engineer: Collaboration engineers are responsible for designing and implementing solutions that enable users to collaborate. Collaboration solutions allow users to share data, applications, and files.
Telecom Engineer: Telecommunications engineers are responsible for the design and implementation of telecommunications systems. Telecommunications systems allow users to communicate using voice, video, and data.
Depending on your skills, years of experience, valid qualifications, and other criteria, you may be better suited for one job than another. The Cisco Certified Network Associate (CCNA) is a great place to start for anyone looking to get into networking.
Conclusion
Earning the Cisco Certified Network Associate (CCNA) certification is a great way to start your networking career. A CCNA certification contains a wealth of knowledge that will help you in your career. A CCNA certification can lead to higher salaries and help you find jobs in a variety of occupations. There are a variety of Cisco certifications you can earn, each useful in your career. A CCNA certification is just the beginning of your journey to a successful networking career.
591cert offers a certification program that includes CCNA Certification. If you're interested in becoming a CCNA and growing your IT career, take a free career assessment. We are happy to answer your questions.
2 notes
·
View notes
Text
Cold Chain Rfid Market Overview, Size, Share, Trend and Forecast to 2033 | Market Strides

Cold Chain Rfid Market
The Global Cold Chain Rfid Market size is projected to grow at a CAGR of XX% during the forecast period.
The Global Cold Chain Rfid Market Research Report provides a comprehensive evaluation of the present industry scenario and future growth prospects over the forecast period. The research report analyzes and summarizes all important aspects of the market including technological evolution, recent industry trends and competitive landscape, market segmentation and key regions.
Research Methodology
Our research methodology constitutes a mix of secondary & primary research which ideally starts from exhaustive data mining, conducting primary interviews (suppliers/distributors/end-users), and formulating insights, estimates, growth rates accordingly. Final primary validation is a mandate to confirm our research findings with Key Opinion Leaders (KoLs), Industry Experts, Mining and Metal Filtration includes major supplies & Independent Consultants among others.
The Global Cold Chain Rfid Market Report provides a 360-degree view of the latest trends, insights, and predictions for the global market, along with detailed analysis of various regional market conditions, market trends, and forecasts for the various segments and sub-segments.
Get Sample Report: https://marketstrides.com/request-sample/cold-chain-rfid-market
List Of Key Companies Profiled:
IBM
Cisco Systems
HPE
Juniper Networks
Huawei
NEC
Pica8
Brocade Communications Systems
Ciena
Intel
Pluribus Networks
Big Switch Networks
SEGMENTATION
By Type
Tags
Readers
Other Hardware Devices
Software and Services
By Application
Food and Beverages
Pharmaceutical&Biomedical
Others
Get In-Detail : https://marketstrides.com/report/cold-chain-rfid-market
Cold Chain Rfid Market Regional Insights
North America
United States: The U.S. economy has shown resilience post-pandemic but faces inflationary pressures, particularly in housing and consumer goods. The Federal Reserve's interest rate policies remain a focus, as the balance between controlling inflation and avoiding recession has impacted spending, borrowing, and business growth. Key sectors like tech, finance, and renewable energy are experiencing dynamic changes, with AI, fintech, and green technology receiving heavy investments.
Canada: Economic stability remains a hallmark of Canada’s economy, although housing affordability and household debt are pressing issues. Canada continues to emphasize a green energy transition, investing in hydroelectric, wind, and solar power. The nation is also focused on attracting skilled labor, especially in technology, healthcare, and energy, as part of its economic strategy.
Mexico: Mexico has benefited from a nearshoring trend, as companies look to relocate manufacturing closer to the U.S. market. With a strong trade relationship via USMCA (the U.S.-Mexico-Canada Agreement), Mexico is seeing investments in its automotive, aerospace, and electronics industries. However, inflation, interest rates, and a need for infrastructure development remain areas of focus.
Buy Now : https://marketstrides.com/buyNow/cold-chain-rfid-market?price=single_price
FAQ
+ What are the years considered for the study?
+ Can the report be customized based on my requirements?
+ When was the Research conducted/published?
+ What are the mixed proportions of Primary and Secondary Interviews conducted for the study?
+ When will the report be updated?
𝐀𝐛𝐨𝐮𝐭 𝐔𝐬
Market Strides is a Global aggregator and publisher of Market intelligence research reports, equity reports, database directories, and economic reports. Our repository is diverse, spanning virtually every industrial sector and even more every category and sub-category within the industry. Our market research reports provide market sizing analysis, insights on promising industry segments, competition, future outlook and growth drivers in the space. The company is engaged in data analytics and aids clients in due-diligence, product expansion, plant setup, acquisition intelligence to all the other gamut of objectives through our research focus.
𝐂𝐨𝐧𝐭𝐚𝐜𝐭 𝐔𝐬:[email protected]
#Cold Chain Rfid Market Size#Cold Chain Rfid Market Share#Cold Chain Rfid Market Growth#Cold Chain Rfid Market Trends#Cold Chain Rfid Market Players
0 notes
Text
Software-Defined Networking Study by Latest Research, Trends, and Revenue till Forecast

Leading Forces in the Software-Defined Networking Market: Forecasts and Key Player Insights Through 2032
This Global Software-Defined Networking research report offers a comprehensive overview of the market, combining both qualitative and quantitative analyses. The qualitative analysis explores market dynamics such as growth drivers, challenges, and constraints, providing deep insights into the market's present and future potential. Meanwhile, the quantitative analysis presents historical and forecast data for key market segments, offering detailed statistical insights.
According to Straits Research, the global Software-Defined Networking market size was valued at USD XX Billion in 2023. It is projected to reach from USD XX Billion in 2024 to USD XX Billion by 2032, growing at a CAGR of 28.37% during the forecast period (2024–2032).
Who are the leading companies (Marketing heads, regional heads) in the Software-Defined Networking
Arista Networks Inc.
Broadcom Inc.
Cisco Systems, Inc.
Citrix Systems, Inc.
Dell Technologies, Inc.
Extreme Networks, Inc.
Hewlett Packard Enterprise Development LP
International Business Machines Corporation
Juniper Networks, Inc.
We offer revenue share insights for the Software-Defined Networking Market, covering both publicly listed and privately held companies.
The report integrates comprehensive quantitative and qualitative analyses, offering a complete overview of the Software-Defined Networking. It spans from a macro-level examination of overall market size, industry chain, and market dynamics, to detailed micro-level insights into segment markets by type, application, and region. This approach provides a holistic view and deep understanding of the market, covering all critical aspects. Regarding the competitive landscape, the report highlights industry players, including market share, concentration ratios, and detailed profiles of leading companies. This enables readers to better understand their competitors and gain deeper insights into the competitive environment. Additionally, the report addresses key factors such as mergers and acquisitions, emerging market trends, the impact of COVID-19, and regional conflicts. In summary, this report is essential reading for industry players, investors, researchers, consultants, business strategists, and anyone with a stake or interest in entering the market.
Get Free Request Sample Report @ https://straitsresearch.com/report/software-defined-networking-market/request-sample
The report integrates comprehensive quantitative and qualitative analyses, offering a complete overview of the Software-Defined Networking markets. It spans from a macro-level examination of overall market size, industry chain, and market dynamics, to detailed micro-level insights into segment markets by type, application, and region. This approach provides a holistic view and deep understanding of the market, covering all critical aspects. Regarding the competitive landscape, the report highlights industry players, including market share, concentration ratios, and detailed profiles of leading companies. This enables readers to better understand their competitors and gain deeper insights into the competitive environment. Additionally, the report addresses key factors such as mergers and acquisitions, emerging market trends, the impact of COVID-19, and regional conflicts. In summary, this report is essential reading for industry players, investors, researchers, consultants, business strategists, and anyone with a stake or interest in entering the market.
Global Software-Defined Networking Market: Segmentation
By Component
Solutions
Physical Network Infrastructure
Virtualization & Control Software
Software-defined Networking Applications
Services
Professional Services
Managed Services
By Organization Size
Large Enterprises
Small- & Medium-sized Enterprises
By End-User
Telecommunication Service Providers
Cloud Service Providers
Enterprises
By Industry Vertical
IT
Consumer Goods & Retail
BFSI
Defense
Telecom
Healthcare
Others
Explore detailed Segmentation from here: @ https://straitsresearch.com/report/software-defined-networking-market/segmentation
The report forecasts revenue growth at all geographic levels and provides an in-depth analysis of the latest industry trends and development patterns from 2022 to 2030 in each of the segments and sub-segments. Some of the major geographies included in the market are given below:
North America (U.S., Canada)
Europe (U.K., Germany, France, Italy)
Asia Pacific (China, India, Japan, Singapore, Malaysia)
Latin America (Brazil, Mexico)
Middle East & Africa
This Report is available for purchase on Buy Software-Defined Networking Market Report
Key Highlights
To explain Software-Defined Networking the following: introduction, product type and application, market overview, market analysis by countries, market opportunities, market risk, and market driving forces
The purpose of this study is to examine the manufacturers of Software-Defined Networking, including profile, primary business, news, sales and price, revenue, and market share.
To provide an overview of the competitive landscape among the leading manufacturers in the world, including sales, revenue, and market share of Software-Defined Networking percent
To illustrate the market subdivided by kind and application, complete with sales, price, revenue, market share, and growth rate broken down by type and application
To conduct an analysis of the main regions by manufacturers, categories, and applications, covering regions such as North America, Europe, Asia Pacific, the Middle East, and South America, with sales, revenue, and market share segmented by manufacturers, types, and applications.
To investigate the production costs, essential raw materials, production method, etc.
Buy Now @ https://straitsresearch.com/buy-now/software-defined-networking-market
About Us:
StraitsResearch.com is a leading research and intelligence organization, specializing in research, analytics, and advisory services along with providing business insights & research reports.
Contact Us:
Email: [email protected]
Address: 825 3rd Avenue, New York, NY, USA, 10022
Tel: +1 6464807505, +44 203 318 2846
#b2b#digitalmarketing#technology#trending#Software-Defined Networking#Software-Defined Networking Industry#Software-Defined Networking Share#Software-Defined Networking Size#Software-Defined Networking Trends#Software-Defined Networking Regional Analysis#Software-Defined Networking Growth Rate
0 notes
Text
Collaborative Whiteboard Software: Trends and Innovations to Watch in 2024

Introduction to Collaborative Whiteboard Software Market
The Collaborative Whiteboard Software Market is rapidly growing, driven by the increasing demand for remote work solutions and digital collaboration tools. This market encompasses software platforms that enable real-time, interactive brainstorming, project planning, and team communication through a virtual whiteboard interface. Businesses across various sectors, including education, IT, and corporate environments, are adopting these tools to enhance productivity and streamline workflows. The rise in hybrid work models and the need for seamless, cross-functional collaboration are key factors propelling market growth. Innovations in AI, integration with other collaboration tools, and user-friendly interfaces further boost the market’s expansion.
Market overview
The Collaborative Whiteboard Software Market is Valued USD 2.2 billion in 2024 and projected to reach USD XX billion by 2030, growing at a CAGR of 18.0% During the Forecast period of 2024–2032.This growth is driven by the increasing adoption of remote work, hybrid working models, and the rising need for digital collaboration tools across various industries.
Access Full Report : https://www.marketdigits.com/checkout/92?lic=s
Major Classifications are as follows:
By Type
Visual
List-based
By Operating System
Windows and Web
iOS
Android
By Deployment Mode
On-premise
Cloud based
By Organization Size
Large Enterprises
SMEs
By Application
Business Meetings
Team Collaborations
Others
By End-use Industry
BFSI
Healthcare
Education
IT and Telecommunications
Others
Key Region/Countries are Classified as Follows: ◘ North America (United States, Canada, and Mexico) ◘ Europe (Germany, France, UK, Russia, and Italy) ◘ Asia-Pacific (China, Japan, Korea, India, and Southeast Asia) ◘ South America (Brazil, Argentina, Colombia, etc.) ◘ The Middle East and Africa (Saudi Arabia, UAE, Egypt, Nigeria, and South Africa)
Major players in Collaborative Whiteboard Software Market include :
Cisco Systems, Inc., Hewlett Packard Enterprise (HPE), IBM Corporation, Juniper Networks, Inc., Netscout Systems, Inc., Broadcom Inc., Nokia Corporation, SolarWinds Worldwide, LLC, VIAVI Solutions Inc., Riverbed Technology, Inc., AppNeta, Gigamon, Paessler AG, Micro Focus International plc, ExtraHop Networks, and Others.
Market Drivers in Collaborative Whiteboard Software Market:
Rise in Remote and Hybrid Work Models: The shift towards remote and hybrid work environments has increased the demand for effective virtual collaboration tools, including whiteboard software.
Increased Focus on Digital Transformation: Organizations are investing in digital tools to enhance productivity, streamline workflows, and improve communication, driving the adoption of collaborative whiteboard software.
Growth in Educational Technology: Educational institutions are adopting these tools to facilitate interactive learning and virtual classrooms, contributing to market expansion.
Market challenges in Collaborative Whiteboard Software Market:
Data Security and Privacy Concerns: Ensuring the security of sensitive information shared on digital platforms is crucial, and breaches can lead to significant trust issues and regulatory scrutiny.
Integration Issues: Seamless integration with other software and systems can be challenging, particularly for organizations with complex IT environments.
Cost Constraints: The cost of advanced features and subscription models may be a barrier for smaller organizations or those with limited budgets.
Market opportunities in Collaborative Whiteboard Software Market:
Expansion in Emerging Markets: Growing adoption of digital tools in developing regions offers new opportunities for market expansion and customer acquisition.
Integration with Emerging Technologies: Incorporating AI, AR/VR, and machine learning can enhance functionality and user experience, providing a competitive edge and attracting tech-savvy users.
Customization and Industry-Specific Solutions: Developing tailored solutions for specific industries (e.g., education, healthcare, finance) can address unique needs and create niche markets.
Future trends in Collaborative Whiteboard Software Market:
AI and Machine Learning Integration: Advanced AI capabilities, such as automated content recognition, intelligent suggestions, and real-time language translation, will enhance the functionality and usability of whiteboard software.
Augmented Reality (AR) and Virtual Reality (VR) Features: AR and VR technologies will provide immersive collaboration experiences, enabling more interactive and engaging virtual meetings and brainstorming sessions.
Integration with IoT Devices: Connectivity with Internet of Things (IoT) devices will enable more dynamic and interactive collaboration experiences, such as smart whiteboards that sync with other office equipment.
Conclusion:
In conclusion, the Collaborative Whiteboard Software Market is poised for significant growth, driven by the increasing demand for remote and hybrid work solutions, advancements in technology, and the need for enhanced digital collaboration. While challenges such as data security, integration issues, and high competition exist, the market presents numerous opportunities through emerging technologies, industry-specific solutions, and expanding into new regions. Future trends will likely include advanced AI integration, immersive AR/VR features, and greater emphasis on user experience and security.
#Collaborative Whiteboard Software market demand#Collaborative Whiteboard Software market share#Collaborative Whiteboard Software market size#Collaborative Whiteboard Software market trend
0 notes
Text
Top 5 User Virtualization Software Of 2024

Their lives encompass a multicultural mix, cross-continental relationships, teenage challenges, and various parenting approaches. This rich blend results in a tapestry of humor and warmth in Modern Family – the TV show we all know and love!
Similarly, User Virtualization Software in the tech world provides a unified platform to create virtual versions of servers, storage, networks, and other physical devices. It’s like an extended family operating in different environments to host multiple virtual setups, each tailored to its own requirements.
If you’re seeking the best User Virtualization Software for your business in 2024, you’re in the right place. Continue reading to join our modern tech family!
We observe how three distinct households coexist in the diverse world of Modern Family. Likewise, User Virtualization Software separates the software components defining a user’s identity on a device from the operating system and applications. This allows for independent management, applying these settings to a desktop as needed without relying on scripting, group policies, or roaming profiles.
Virtualization enables a single piece of hardware to function as multiple machines. It’s like creating multiple “virtual machines” within a single physical computer. By virtualizing software-based applications, servers, storage, networks, desktops, and more, you can significantly reduce hardware and equipment costs. Smart, right?
Last year, we highlighted the Top 5 User Virtualization Software for 2023, and this year, we have updated the list for you.
Here are the Top 5 User Virtualization Software of 2024!
To recap, User Virtualization Software allows the separation of a user’s profile, settings, and data from underlying operating systems, enabling a consistent and personalized experience across different devices and sessions, regardless of the hardware or platform.
Here are our top 5 picks for User Virtualization Software – as randomly ordered as Phil's-Osophy!
Tool 1: VMWare Workstation Pro VMWare, established in 1998 and headquartered in Palo Alto, California, was recently acquired by Broadcom in 2022. With clients like Apple, Costco, FedEx, and PepsiCo, VMWare was awarded the Gartner Peer Insights Customers’ Choice and ranked #1 in Worldwide IT Automation and Configuration Management for the fifth consecutive year by a global analyst firm in 2023.
VMWare Workstation Pro is a leading virtualization software that allows users to run multiple operating systems on a single physical machine. It’s ideal for developers, testers, IT administrators, and power users, providing a robust and flexible environment for creating, configuring, and managing virtual machines.
Known for its advanced network configuration features, it supports hundreds of 32- and 64-bit guest operating systems, offering plenty of options for configuring virtual machines. On Windows, it also has a command line interface for developing and operating Kubernetes containers and clusters, along with robust networking and isolation features within the virtual machine.
Tool 2: Oracle VirtualBox Oracle, founded in 1977 and headquartered in Austin, Texas, serves clients like Cisco, Zoom, and Gartner. Oracle has received numerous awards for its innovative technology and leadership, including USA TODAY's America's Climate Leaders List and the Karma Award – Good Samaritan category in 2024.
VirtualBox, Oracle's open-source virtualization solution, supports host operating systems like Windows, Linux, Mac, and Solaris. It’s a cross-platform tool that enables users to run multiple operating systems simultaneously. Ideal for IT professionals and developers, Oracle VM VirtualBox is perfect for testing, developing, demonstrating, and deploying virtualized solutions across multiple platforms from one machine.
VirtualBox’s open-source nature allows users to experiment and test new functions without deviating from their established workflows. With a free license for educational, personal, and evaluation purposes, getting started with VirtualBox is easy!
Tool 3: Google Compute Engine Founded in 1998, Google serves billions worldwide and is headquartered in Mountain View, California. Google’s clients include Apple, Amazon, and many others. Google received the ‘Best Global Culture’ award in 2024, along with numerous other accolades from Comparably in 2023, solidifying its status as the GOAT.
Google Compute Engine, part of the Google Cloud Platform, allows users to launch virtual machines on demand. It leverages Google’s global infrastructure, which powers services like the search engine, Gmail, and YouTube, providing reliable uptime, processing capabilities, and low latency. These features are crucial for running high-performance virtual machines, essential for user virtualization processes.
Tool 4: Red Hat Virtualization (RHV) Founded in 1993 and headquartered in Raleigh, North Carolina, Red Hat is an open-source company serving clients like MicroFocus, JPMorgan Chase, and Safe Fleet. Red Hat has been recognized for its contributions to the industry and customer support, winning the “Best Contribution to Moving the Industry Forward” and “The Ten Best Web Support Sites” for 13 consecutive years.
Red Hat Virtualization is an enterprise platform supporting key virtualization workloads, including resource-intensive and critical applications. Built on Red Hat Enterprise Linux and KVM, it’s an enterprise-grade solution fully supported by Red Hat.
Featuring an easy-to-use interface and known for its automation capabilities, Red Hat Virtualization allows users to define rules and constructs for full end-to-end automation of their virtualization deployments. This scalability is achieved through custom solutions, APIs, and open-source capabilities.
Tool 5: Azure Virtual Machines Founded in 1975 and headquartered in Redmond, Washington, Microsoft needs no introduction. Ranked fifth in the JUST 100 rankings for 2024, Microsoft serves major clients like Apple, Nvidia, and ClearBank. It also received top industry scores for environmental and social quality in 2023.
Azure Virtual Machines offer a range of networking capabilities and services such as Azure Virtual Network, VPNs, and Azure ExpressRoute, ensuring high availability and security for applications. Azure VMs provide virtualization without the need to maintain physical hardware.
Known for its cloud-based monitoring, Azure VMs track metrics for data visualizations, log queries, and dependency mapping. It also includes detailed monitoring features, robust security, and significant savings with Reserved VM Instances and on-demand capacity reservations.
To Conclude Selecting the best User Virtualization Software requires thorough research and trials to match your business's specific needs. Our list of the top User Virtualization Software of 2024 can help you get started!
User Virtualization Software offers many benefits, including reduced IT expenses and hardware costs, simplified management, and improved disaster recovery through centralized backups.
Remember, each solution has unique features and capabilities, so evaluate performance, compatibility, and scalability through hands-on testing.
0 notes
Text
Data Centre Market: Analyzing Growth Drivers and Market Trends 2024
The primary goal of Data Centre market report is to assist clients in making informed business decisions. It guides them in identifying areas that require enhancement, recognizing those that are already flourishing, and supporting new participants as they establish and navigate the competitive landscape. The report also sheds light on the prevailing challenges within the Data Centre market. The major players in the Data Centre market are evaluated based on their product and service offerings, financial statements, key developments, strategic approach to the market, position in the market, geographical penetration, and other key features. The chapter also highlights the strengths, weaknesses, opportunities, and threats (SWOT analysis), winning imperatives and current focus strategies. Furthermore, the list of companies included in the market study can also be customized as per the client’s requirements.
The global data center market is anticipated to grow from USD 292.91 Billion in 2023 to USD 536.28 Billion by 2030, at a CAGR of 10.72% during the forecast period.
Full Report of the Data Centre Market @:
Competitive Analysis:
In this section, we assess the competitive landscape of the Data Centre Market, focusing on key players.
Key Players:
Alphabet Inc., Com Inc., Digital Realty, Equinix Inc., Hewlett Packard Enterprise, IBM Corporation, Microsoft, NTT Communication Corporation, Oracle, Sap Se, Eaton Corporation Plc, Schneider Electric Se, General Electric Company, Carrier Global Corporation, Siemens Ag, LG Electronics Inc., Fujitsu Limited, Mitsubishi Electric Corporation, Cisco System Inc, Hewlett-Packard Inc
Market Segmentation:
In this section, we provide a breakdown of the Data Centre Market into segments based on different criteria, including the type of analysis, industry verticals, and geographic regions.
Data Center Market by Component
Solution
Services
Data Center Market by Type
Colocation
Hyperscale
Edge
Others
Data Center Market by Enterprise Size
Large Enterprises
Small & Medium Enterprises (SMEs)
Data Center Market by End User
BFSI
IT & Telecom
Government
Energy & Utilities
Others
Regional Analysis:
Geographically, this report is segmented into several key Regions, with production, consumption, revenue (million USD), and market share and growth rate of the Data Centre Market in these regions, from 2024 to 2030 (forecast) covering:
Europe, China, Japan, Southeast Asia, India, North America (USA, Canada, and Mexico)
Europe (Germany, France, UK, Russia, and Italy)
Asia–Pacific (China, Japan, Korea, India, and Southeast).
** Access your free sample copy of this strategic report today@:
What Information does this report contain?
Historical data coverage: Growth Projections: 2024 to 2030.
Expert analysis: industry, governing, innovation and technological trends; factors impacting development; drawbacks, SWOT.
6-year performance forecasts: major segments covering applications, top products and geographies.
Competitive landscape reporting: market leaders and important players, competencies and capacities of these companies in terms of production as well as sustainability and prospects.
Data Centre Market Size and Share Report 2023-2030 Table of Contents – Major Key Points
Introduction
Research Methodology
Market Dynamics
Impact Analysis
Value Chain Analysis
Porter’s 5 Forces Model
PEST Analysis
Data Centre Market Segmentation, By Platform Type
Data Centre Market Segmentation, By Ad Format
Data Centre Market Segmentation, By Enterprise Size
Data Centre Market Segmentation, By Industry Vertical
Regional Analysis
Company Profiles
Competitive Landscape
Conclusion
0 notes
Text
Remote Work Tools and Technologies: What Every IT Professional Should Know
In the wake of the COVID-19 pandemic, remote work has become a fundamental aspect of the modern workplace, especially in the IT industry. With this shift, IT professionals must be well-versed in the tools and technologies that enable effective remote work. For IT hiring agencies, understanding these tools is essential to identify and place the right candidates in roles that require remote capabilities. This blog will explore the key remote work tools and technologies that every IT professional should know.
1. Communication and Collaboration Tools
Why They Matter: Effective communication and collaboration are the cornerstones of successful remote work. These tools help teams stay connected, share information, and collaborate on projects in real-time.
Key Tools:
● Slack: A powerful messaging platform that facilitates team communication through channels, direct messages, and integrations with other tools.
● Microsoft Teams: A collaboration tool that combines chat, video meetings, file storage, and application integration, all in one platform.
● Zoom: Widely used for video conferencing, Zoom offers features such as screen sharing, breakout rooms, and virtual backgrounds, making it ideal for remote meetings.
Preparation Tips for IT Professionals: Familiarize yourself with these tools and their advanced features. Participate in virtual meetings, use collaborative workspaces, and explore integrations with other productivity tools to maximize their utility.
2. Project Management Software
Why They Matter: Project management tools are essential for organizing tasks, tracking progress, and ensuring timely completion of projects. They help remote teams stay aligned and focused on their goals.
Key Tools:
● Trello: A user-friendly tool that uses boards, lists, and cards to help teams organize tasks and projects visually.
● Asana: A comprehensive project management tool that allows teams to create tasks, set deadlines, assign responsibilities, and track progress.
● JIRA: Particularly popular among software development teams, JIRA provides robust tracking, bug reporting, and agile project management features.
Preparation Tips for IT Professionals: Learn how to create and manage projects, use task boards, and generate reports. Understanding how to integrate these tools with other software development and collaboration tools is also beneficial.
3. Cloud Storage and File Sharing
Why They Matter: Cloud storage solutions enable remote teams to store, access, and share files securely from anywhere. They ensure that team members can collaborate on documents in real-time.
Key Tools:
● Google Drive: Offers cloud storage and a suite of productivity apps (Docs, Sheets, Slides) that support real-time collaboration.
● Dropbox: Provides secure file storage and sharing with features like file recovery, version history, and extensive third-party app integrations.
● OneDrive: Integrated with Microsoft Office, OneDrive offers seamless storage and sharing capabilities for Office files and other documents.
Preparation Tips for IT Professionals: Get comfortable with creating, organizing, and sharing files in these platforms. Learn how to use collaboration features like real-time editing, commenting, and version control.
4. Cybersecurity Tools
Why They Matter: With remote work, cybersecurity becomes even more critical. IT professionals must ensure that data and communications are secure to protect against potential threats.
Key Tools:
● VPNs (Virtual Private Networks): Tools like NordVPN or Cisco AnyConnect provide secure, encrypted connections for remote workers.
● Antivirus and Endpoint Security: Solutions like McAfee, Norton, and CrowdStrike help protect remote devices from malware and cyber threats.
● Multi-Factor Authentication (MFA): Tools such as Google Authenticator or Duo Security add an extra layer of security to user logins.
Preparation Tips for IT Professionals: Stay updated on the latest cybersecurity threats and best practices. Implement and enforce the use of security tools and conduct regular security audits to ensure compliance.
5. Remote Desktop Software
Why They Matter: Remote desktop software allows IT professionals to access and manage another computer remotely, which is crucial for troubleshooting and maintenance.
Key Tools:
● TeamViewer: Provides remote access, desktop sharing, and file transfer capabilities.
● Remote Desktop Protocol (RDP): A proprietary protocol developed by Microsoft, allowing users to connect to another computer over a network connection.
● AnyDesk: Offers high-performance remote desktop connections and is known for its speed and low latency.
Preparation Tips for IT Professionals: Practice using these tools to support remote troubleshooting and system management. Understand how to set up secure remote access and manage permissions effectively.
6. Development and Collaboration Platforms
Why They Matter: Development and collaboration platforms enable remote IT teams to work on code, manage version control, and collaborate on software development projects.
Key Tools:
● GitHub: A web-based platform for version control and collaboration, enabling multiple developers to work on projects simultaneously.
● GitLab: Similar to GitHub, but with additional features for CI/CD (Continuous Integration/Continuous Deployment) pipelines.
● Bitbucket: Another Git repository hosting service, offering both commercial plans and free accounts with unlimited private repositories.
Preparation Tips for IT Professionals: Master version control systems like Git. Learn how to create, clone, and manage repositories, and understand the workflows for branching, merging, and pull requests.
Conclusion
The shift to remote work has underscored the importance of being adept with various tools and technologies that facilitate seamless collaboration, communication, and security. For IT professionals, mastering these tools is essential for maintaining productivity and efficiency in a remote environment. IT hiring agencies must prioritize candidates who are proficient with these technologies to ensure successful placements in remote roles.
#it staffing agency#it recruitment agency#it staffing services#it employment agency#it placement agencies#it hiring agencies#it recruiting firms#manufacturing recruiting firms#manufacturing staffing agency#manufacturing recruitment agencies
0 notes
Text
Software-Defined Anything (SDx) Market Growth Status, Analysis and Forecast 2031
The Insight Partners recently announced the release of the market research titled Software-Defined Anything (SDx) Market Outlook to 2031 | Share, Size, and Growth. The report is a stop solution for companies operating in the Software-Defined Anything (SDx) market. The report involves details on key segments, market players, precise market revenue statistics, and a roadmap that assists companies in advancing their offerings and preparing for the upcoming decade. Listing out the opportunities in the market, this report intends to prepare businesses for the market dynamics in an estimated period.
Is Investing in the Market Research Worth It?
Some businesses are just lucky to manage their performance without opting for market research, but these incidences are rare. Having information on longer sample sizes helps companies to eliminate bias and assumptions. As a result, entrepreneurs can make better decisions from the outset. Software-Defined Anything (SDx) Market report allows business to reduce their risks by offering a closer picture of consumer behavior, competition landscape, leading tactics, and risk management.
A trusted market researcher can guide you to not only avoid pitfalls but also help you devise production, marketing, and distribution tactics. With the right research methodologies, The Insight Partners is helping brands unlock revenue opportunities in the Software-Defined Anything (SDx) market.
If your business falls under any of these categories – Manufacturer, Supplier, Retailer, or Distributor, this syndicated Software-Defined Anything (SDx) market research has all that you need.
What are Key Offerings Under this Software-Defined Anything (SDx) Market Research?
Global Software-Defined Anything (SDx) market summary, current and future Software-Defined Anything (SDx) market size
Market Competition in Terms of Key Market Players, their Revenue, and their Share
Economic Impact on the Industry
Production, Revenue (value), Price Trend
Cost Investigation and Consumer Insights
Industrial Chain, Raw Material Sourcing Strategy, and Downstream Buyers
Production, Revenue (Value) by Geographical Segmentation
Marketing Strategy Comprehension, Distributors and Traders
Global Software-Defined Anything (SDx) Market Forecast
Study on Market Research Factors
Who are the Major Market Players in the Software-Defined Anything (SDx) Market?
Software-Defined Anything (SDx) market is all set to accommodate more companies and is foreseen to intensify market competition in coming years. Companies focus on consistent new launches and regional expansion can be outlined as dominant tactics. Software-Defined Anything (SDx) market giants have widespread reach which has favored them with a wide consumer base and subsequently increased their Software-Defined Anything (SDx) market share.
Report Attributes
Details
Segmental Coverage
Type
Software-Defined Networking
Software-Defined Wide Area Network
Software-Defined Data Center
End User
Service Provider
BFSI
Manufacturing
Retail
Healthcare
Government
Education
Others
Regional and Country Coverage
North America (US, Canada, Mexico)
Europe (UK, Germany, France, Russia, Italy, Rest of Europe)
Asia Pacific (China, India, Japan, Australia, Rest of APAC)
South / South & Central America (Brazil, Argentina, Rest of South/South & Central America)
Middle East & Africa (South Africa, Saudi Arabia, UAE, Rest of MEA)
Market Leaders and Key Company Profiles
Adaptiv Networks, Inc.
ARYAKA NETWORKS,INC.
Bigleaf Networks, Inc.
Cisco
Citrix Systems, Inc.
CloudGenix Inc.
FatPipe Networks Inc.
Fortinet, Inc.
Hewlett Packard Enterprise Development LP
Huawei Technologies Co., Ltd.
Other key companies
What are Perks for Buyers?
The research will guide you in decisions and technology trends to adopt in the projected period.
Take effective Software-Defined Anything (SDx) market growth decisions and stay ahead of competitors
Improve product/services and marketing strategies.
Unlock suitable market entry tactics and ways to sustain in the market
Knowing market players can help you in planning future mergers and acquisitions
Visual representation of data by our team makes it easier to interpret and present the data further to investors, and your other stakeholders.
Do We Offer Customized Insights? Yes, We Do!
The The Insight Partners offer customized insights based on the client’s requirements. The following are some customizations our clients frequently ask for:
The Software-Defined Anything (SDx) market report can be customized based on specific regions/countries as per the intention of the business
The report production was facilitated as per the need and following the expected time frame
Insights and chapters tailored as per your requirements.
Depending on the preferences we may also accommodate changes in the current scope.
Author’s Bio:
Aniruddha Dev
Senior Market Research Expert at The Insight Partners
#Software-Defined Anything (SDx) Market#Software-Defined Anything (SDx) Market Size#Software-Defined Anything (SDx) Market Share#Software-Defined Anything (SDx) Market Trends
0 notes
Text
what is a vpn in a cisco sd-wan deployment
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is a vpn in a cisco sd-wan deployment
VPN Encryption in Cisco SD-WAN
VPN encryption in Cisco SD-WAN plays a critical role in ensuring the security and privacy of data transmitted over wide area networks (WANs). Cisco SD-WAN leverages advanced encryption techniques to safeguard sensitive information from unauthorized access and cyber threats.
One of the key encryption technologies employed by Cisco SD-WAN is Transport Layer Security (TLS). TLS encrypts data during transmission between devices, preventing eavesdropping and tampering by malicious actors. By establishing secure communication channels, TLS ensures that data remains confidential and integral throughout its journey across the network.
Additionally, Cisco SD-WAN supports the use of IPsec (Internet Protocol Security) for encrypting data at the network layer. IPsec creates a secure tunnel between endpoints, encrypting each packet of information before it is transmitted over the network. This ensures end-to-end encryption, protecting data from interception and manipulation by unauthorized parties.
Moreover, Cisco SD-WAN offers robust key management mechanisms to ensure the secure generation, distribution, and rotation of encryption keys. This helps prevent unauthorized access to sensitive information and strengthens the overall security posture of the network.
Furthermore, Cisco SD-WAN provides visibility and control over encrypted traffic through advanced monitoring and analytics capabilities. This enables organizations to detect and mitigate security threats in real-time, ensuring the continuous protection of their data assets.
In conclusion, VPN encryption in Cisco SD-WAN delivers comprehensive security features to protect data transmitted over wide area networks. By leveraging technologies like TLS and IPsec, along with robust key management and monitoring capabilities, Cisco SD-WAN helps organizations maintain the confidentiality, integrity, and availability of their critical information assets.
Cisco SD-WAN VPN Configuration
Cisco SD-WAN VPN configuration is an essential aspect of optimizing network performance and security for businesses of all sizes. SD-WAN, or Software-Defined Wide Area Network, provides a flexible and cost-effective solution for connecting branch offices and remote users to a centralized network infrastructure.
To configure a VPN connection in Cisco SD-WAN, one must adhere to a structured set of steps to ensure a smooth and secure implementation. The first step is to establish connectivity between the SD-WAN routers at each end of the VPN tunnel. This is typically done by configuring the necessary interfaces and IP addresses on the devices.
Next, encryption settings must be defined to secure the data traffic passing through the VPN tunnel. Cisco SD-WAN supports various encryption protocols such as AES, 3DES, and SHA to ensure data confidentiality and integrity.
Routing configuration is another crucial aspect of setting up a VPN in Cisco SD-WAN. Dynamic routing protocols like OSPF or BGP can be configured to efficiently route traffic between different network segments and optimize network performance.
In addition to encryption and routing, access control lists (ACLs) can be implemented to restrict traffic flow based on predefined rules. This helps in preventing unauthorized access and securing the network from potential security threats.
Overall, Cisco SD-WAN VPN configuration requires a thorough understanding of network protocols, encryption mechanisms, and security best practices to ensure a reliable and secure connection between network endpoints. By following a structured approach and utilizing Cisco's robust SD-WAN features, businesses can optimize their network connectivity while maintaining high levels of data security.
Secure Data Transmission with Cisco SD-WAN
In today's digital landscape, ensuring secure data transmission is paramount for businesses of all sizes. With the rise of remote work and the increasing reliance on cloud-based applications, companies need robust solutions to safeguard their sensitive information while maintaining optimal network performance. Cisco Software-Defined Wide Area Networking (SD-WAN) emerges as a powerful tool in this regard, offering a comprehensive approach to secure data transmission.
One of the key features of Cisco SD-WAN is its ability to encrypt data traffic, effectively shielding it from unauthorized access or interception. By employing advanced encryption protocols such as AES (Advanced Encryption Standard), Cisco SD-WAN ensures that data remains confidential and secure, even when traversing across public networks.
Moreover, Cisco SD-WAN incorporates built-in security functionalities, including firewall capabilities and intrusion prevention systems (IPS), to fortify network defenses against cyber threats. These security measures are seamlessly integrated into the SD-WAN infrastructure, providing end-to-end protection without compromising performance.
Another advantage of Cisco SD-WAN is its centralized management and policy enforcement capabilities. Through a centralized controller, administrators can define and enforce security policies consistently across the entire network, ensuring compliance with industry regulations and organizational security standards.
Furthermore, Cisco SD-WAN offers visibility and control over network traffic, allowing administrators to identify and mitigate security risks in real-time. With granular visibility into application performance and user behavior, organizations can proactively address security threats and prevent potential breaches before they escalate.
In conclusion, Cisco SD-WAN provides a robust and scalable solution for secure data transmission in today's dynamic business environment. By combining encryption, built-in security features, centralized management, and real-time visibility, Cisco SD-WAN empowers organizations to safeguard their critical data assets while optimizing network performance. As businesses continue to embrace digital transformation, investing in secure networking solutions like Cisco SD-WAN becomes essential to mitigate risks and ensure business continuity.
Cisco SD-WAN VPN Tunneling Protocols
Title: Understanding Cisco SD-WAN VPN Tunneling Protocols
In the realm of networking, Virtual Private Networks (VPNs) play a pivotal role in securely connecting remote users and branch offices to a central network. Cisco's Software-Defined Wide Area Network (SD-WAN) offers advanced VPN solutions, leveraging various tunneling protocols to ensure secure and efficient communication across distributed networks.
One of the primary tunneling protocols employed by Cisco SD-WAN is IPsec (Internet Protocol Security). IPsec provides robust encryption and authentication mechanisms, ensuring data confidentiality and integrity over untrusted networks such as the internet. By encapsulating data packets within IPsec tunnels, Cisco SD-WAN establishes secure communication channels between different network endpoints.
Additionally, Cisco SD-WAN utilizes GRE (Generic Routing Encapsulation) tunnels to facilitate efficient routing of traffic across disparate networks. GRE encapsulates packets with a new IP header, enabling the creation of virtual point-to-point links between network devices. This flexibility in routing protocols allows for seamless integration of SD-WAN with existing network infrastructures.
Furthermore, Cisco SD-WAN incorporates MPLS (Multiprotocol Label Switching) as a tunneling protocol option, particularly in hybrid WAN deployments. MPLS offers low-latency and high-reliability connectivity, making it ideal for mission-critical applications. By integrating MPLS with SD-WAN, organizations can optimize network performance and enhance user experience across diverse network environments.
In conclusion, Cisco SD-WAN leverages a combination of tunneling protocols such as IPsec, GRE, and MPLS to deliver secure and efficient VPN solutions for modern networking requirements. By understanding the characteristics and capabilities of these protocols, organizations can effectively deploy and manage SD-WAN infrastructures to meet their evolving connectivity needs.
VPN Integration in Cisco SD-WAN Architecture
In the ever-evolving landscape of networking and data security, the integration of a VPN (Virtual Private Network) in Cisco SD-WAN architecture has become increasingly essential. Cisco SD-WAN is a cloud-delivered WAN architecture that enables digital and cloud transformation for enterprises. By integrating a VPN into this architecture, organizations can enhance their network security and ensure data privacy while maintaining high levels of performance and reliability.
One of the key benefits of integrating a VPN into Cisco SD-WAN architecture is the increased security it provides for data transmitted over the network. VPNs encrypt data as it travels between devices, ensuring that sensitive information remains protected from potential threats. This is especially important for organizations that deal with confidential data or operate in highly regulated industries where data security is of utmost importance.
Additionally, the integration of a VPN in Cisco SD-WAN architecture allows organizations to establish secure connections between remote sites and data centers, as well as provide secure access for remote workers. This not only enhances productivity but also enables organizations to leverage the benefits of cloud services without compromising on security.
Moreover, VPN integration in Cisco SD-WAN architecture simplifies network management by providing a centralized platform for monitoring and configuring VPN connections. This streamlines operations and ensures that IT teams can quickly identify and address any security vulnerabilities or performance issues that may arise.
In conclusion, integrating a VPN into Cisco SD-WAN architecture is a strategic decision for organizations looking to enhance their network security, improve data privacy, and streamline network management. By leveraging the combined power of VPN technology and Cisco SD-WAN, enterprises can create a robust and secure networking environment that meets the demands of today's digital world.
0 notes
Text
Cloud Migration Market: Forthcoming Trends and Share Analysis by 2030
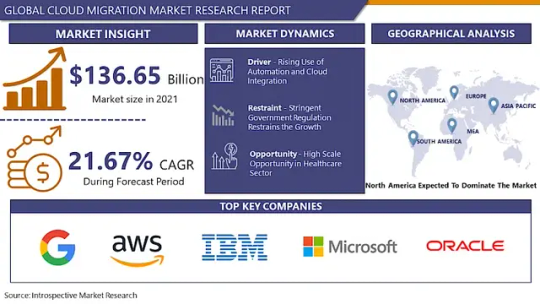
The Global Cloud Migration is expected at USD 136.65 Billion in the year 2021 and is predicted to reach USD 539.38 Billion by 2028, with a CAGR of 21.67% over the forecasted period.
The Cloud Migration Market is experiencing robust growth as businesses worldwide are increasingly shifting their operations to cloud-based platforms. This migration trend is driven by the need for scalability, cost-efficiency, and agility in today's digital landscape. Cloud migration encompasses transferring data, applications, and other business elements from on-premises infrastructure to cloud environments. Key players in the market include cloud service providers, consulting firms, and migration tool vendors.
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/14891
Updated Version 2024 is available our Sample Report May Includes the:
Scope For 2024
Brief Introduction to the research report.
Table of Contents (Scope covered as a part of the study)
Top players in the market
Research framework (structure of the report)
Research methodology adopted by Worldwide Market Reports
Moreover, the report includes significant chapters such as Patent Analysis, Regulatory Framework, Technology Roadmap, BCG Matrix, Heat Map Analysis, Price Trend Analysis, and Investment Analysis which help to understand the market direction and movement in the current and upcoming years.
Leading players involved in the Cloud Migration Market include:
Oracle Corporation, Microsoft Corporation, IBM Corporation, Amazon Web Services, Google Inc., Cisco Systems, RiverMeadow Software, Rackspace US, Informatica, OVH US LLC
If You Have Any Query Cloud Migration Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/14891
Segmentation of Cloud Migration Market:
By Service
SaaS
PaaS
IaaS
By Deployment
Private
Public
Hybrid
By End Users
Manufacturing
BFSI
IT & Telecom
Retail
Healthcare
Logistics
Education
By Regions: -
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
Highlights from the report:
Market Study: It includes key market segments, key manufacturers covered, product range offered in the years considered, Global Cloud Migration Market, and research objectives. It also covers segmentation study provided in the report based on product type and application.
Market Executive Summary: This section highlights key studies, market growth rates, competitive landscape, market drivers, trends, and issues in addition to macro indicators.
Market Production by Region: The report provides data related to imports and exports, revenue, production and key players of all the studied regional markets are covered in this section.
Cloud Migration Profiles of Top Key Competitors: Analysis of each profiled Roll Hardness Tester market player is detailed in this section. This segment also provides SWOT analysis of individual players, products, production, value, capacity, and other important factors.
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Acquire This Reports: -
https://introspectivemarketresearch.com/checkout/?user=1&_sid=14891
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assisting our clients to grow and have a successful impact on the market. Our team at IMR is ready to assist our clients to flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, that specializes in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyse extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Contact us:
Introspective Market Research
3001 S King Drive,
Chicago, Illinois
60616 USA
Ph no: +1-773-382-1049
Email: [email protected]
#Cloud Migration#Cloud Migration Market#Cloud Migration Market Size#Cloud Migration Market Share#Cloud Migration Market Growth#Cloud Migration Market Trend#Cloud Migration Market segment#Cloud Migration Market Opportunity#Cloud Migration Market Analysis 2023
0 notes
Text
does asa see vpn as outside interface
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does asa see vpn as outside interface
ASA VPN outside interface
The ASA VPN outside interface is a crucial component of any network employing VPN (Virtual Private Network) technology, particularly those utilizing Cisco's Adaptive Security Appliance (ASA). The outside interface serves as the gateway between the internal network and external networks, such as the internet.
In the context of VPNs, the outside interface of the ASA plays a pivotal role in facilitating secure communication between remote users or sites and the organization's internal network. It is through this interface that encrypted VPN tunnels are established, allowing authorized users to access resources securely from outside the corporate network.
The ASA VPN outside interface is configured with specific settings and parameters to ensure the security and efficiency of VPN connections. This includes defining encryption protocols, authentication methods, access control policies, and other security measures to safeguard data transmission over the VPN tunnels.
Additionally, the outside interface may be configured with features such as NAT (Network Address Translation) to translate internal IP addresses to public IP addresses, providing an added layer of security and privacy for VPN traffic.
Monitoring and maintaining the ASA VPN outside interface is essential for ensuring the reliability and security of VPN connections. This involves regular monitoring of traffic, performance, and security logs to detect and address any anomalies or security threats promptly.
In summary, the ASA VPN outside interface is a critical component of VPN deployments, serving as the entry point for secure communication between remote users or sites and the organization's internal network. Proper configuration, monitoring, and maintenance are essential to ensure the security and efficiency of VPN connections.
ASA VPN interface configuration
ASA VPN interface configuration refers to the process of setting up virtual private network (VPN) connections on Cisco Adaptive Security Appliance (ASA) devices. VPNs are essential for secure communication over public networks, ensuring data privacy and integrity. Configuring VPN interfaces on ASA devices involves several steps to establish secure connections for remote users or branch offices.
To begin the configuration process, access the ASA device through the command-line interface (CLI) or graphical user interface (GUI). Define the VPN tunnel parameters, such as encryption algorithms, authentication methods, and IKE (Internet Key Exchange) settings. Create a group policy to apply specific settings and restrictions to VPN users.
Next, configure the VPN interface by assigning an IP address and enabling the VPN service. Define access control lists (ACLs) to control traffic flow between VPN peers and specify which networks can communicate securely over the VPN tunnel. Additionally, set up routing protocols or static routes to ensure proper routing of VPN traffic.
It is crucial to apply security best practices when configuring VPN interfaces on ASA devices. Use strong encryption algorithms and authentication methods to safeguard data transmission. Regularly update ASA firmware to patch vulnerabilities and enhance security. Monitor VPN traffic and logs to detect and investigate any suspicious activity.
In conclusion, ASA VPN interface configuration plays a vital role in establishing secure VPN connections on Cisco ASA devices. By following proper configuration steps and security measures, organizations can ensure safe and reliable communication over VPN tunnels.
ASA VPN tunnel setup
Setting up an ASA VPN tunnel, also known as a Virtual Private Network tunnel, on Cisco's Adaptive Security Appliance (ASA) is crucial for secure communication between remote networks or devices. This process involves configuring the ASA device to establish an encrypted connection, ensuring confidentiality and integrity of data transmission over public networks.
To initiate the ASA VPN tunnel setup, administrators typically follow these steps:
Access ASA Configuration: Log in to the ASA device through a secure connection, either via console, SSH, or ASDM (Adaptive Security Device Manager).
Configure Basic Settings: Define the VPN parameters such as tunnel endpoints, authentication methods, and encryption algorithms. This includes specifying the peer device's IP address, pre-shared key (PSK) for authentication, and encryption standards like AES or 3DES.
Create VPN Policies: Define access control policies to determine which traffic should be encrypted and allowed through the VPN tunnel. This involves configuring access lists (ACLs) to permit specific traffic flows.
Set Up IKE (Internet Key Exchange): Configure IKE parameters for negotiating security associations between VPN peers. This includes defining authentication methods, encryption protocols, and Diffie-Hellman group for key exchange.
Establish VPN Tunnel: Once configurations are in place, initiate the VPN tunnel establishment process. The ASA device will exchange IKE messages with the peer device to authenticate and establish secure communication channels.
Monitor and Troubleshoot: After the VPN tunnel is established, continuously monitor its status and performance using ASA monitoring tools or command-line interface (CLI). Troubleshoot any connectivity issues or security concerns that may arise during operation.
Implement Redundancy: For high availability and failover, consider implementing VPN redundancy options such as backup peer configurations or using multiple tunnels.
By following these steps, network administrators can effectively set up an ASA VPN tunnel, ensuring secure and seamless communication between remote networks or devices while safeguarding sensitive data from unauthorized access or interception.
ASA VPN routing table
The ASA VPN routing table, within the context of network infrastructure, refers to the specific routing table utilized by Cisco's Adaptive Security Appliance (ASA) to manage traffic flow for Virtual Private Network (VPN) connections. This routing table plays a crucial role in directing VPN traffic efficiently across networks, ensuring secure and reliable communication between remote users or sites.
In essence, when a VPN connection is established through an ASA device, the routing table is consulted to determine the optimal path for data packets to reach their destination. This involves analyzing various factors such as destination IP addresses, subnet masks, and routing metrics to make informed routing decisions.
One key aspect of the ASA VPN routing table is its ability to support dynamic routing protocols such as OSPF, EIGRP, and BGP. These protocols enable the ASA to dynamically exchange routing information with other routers in the network, allowing for automatic updates to the routing table in response to changes in network topology or routing policies.
Furthermore, the ASA VPN routing table also supports static routes, which are manually configured routes that specify the next-hop gateway for specific destination networks. This provides administrators with granular control over how VPN traffic is routed within their network environment.
Overall, the ASA VPN routing table is a critical component of Cisco's security infrastructure, facilitating secure and efficient communication for VPN connections. By leveraging dynamic routing protocols and static route configurations, organizations can optimize their VPN deployments to meet the demands of modern networking environments while maintaining robust security posture.
ASA VPN access control-list
An ASA VPN access control-list, also known as ACL, is a crucial component of Cisco's Adaptive Security Appliance (ASA) that functions to enhance network security by controlling traffic flow to and from a Virtual Private Network (VPN). These access control lists operate by defining a set of rules or policies that determine which type of traffic is permitted or denied access through the VPN gateway.
By implementing ASA VPN access control-lists, network administrators can effectively manage and secure their VPN connections by specifying the types of traffic that are authorized to pass through the ASA firewall. This allows for increased control over network resources and helps prevent unauthorized access or potentially harmful activities from occurring within the VPN.
ASA VPN access control-lists offer a granular level of control, enabling administrators to filter traffic based on various criteria such as source and destination IP addresses, protocols, ports, and application types. This level of specificity ensures that only legitimate traffic is allowed through the VPN, while potentially malicious or unauthorized traffic is blocked.
In addition, ASA VPN access control-lists can be configured to log and monitor traffic patterns, providing valuable insights into network activity and aiding in the detection of suspicious or anomalous behavior. This proactive approach to network security helps organizations maintain the integrity and confidentiality of their VPN connections while safeguarding against potential cyber threats.
Overall, ASA VPN access control-lists play a critical role in enhancing the security posture of VPN infrastructures, offering administrators a powerful tool to manage and protect their networks effectively. By leveraging the capabilities of ASA access control lists, organizations can ensure a secure and reliable VPN environment for their users.
0 notes
Text
does cisco expressway work better then vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does cisco expressway work better then vpn
Cisco Expressway architecture
Cisco Expressway Architecture: Enhancing Connectivity and Security
Cisco Expressway is a vital component of Cisco's Unified Communications (UC) and Collaboration solutions. It serves as a gateway for secure access to communication services, extending these capabilities to remote users, mobile devices, and external partners. The architecture of Cisco Expressway is designed to facilitate seamless connectivity while prioritizing security and scalability.
At its core, Cisco Expressway acts as a traversal server, enabling secure communication between internal and external endpoints. It functions as a bridge between different networks, including the internet and corporate intranets, ensuring that users can access UC services regardless of their location or network environment.
The architecture of Cisco Expressway comprises several key elements:
Core Services: Expressway provides essential services such as SIP proxy, firewall traversal, and encryption to safeguard communication traffic. It supports various protocols, including SIP, XMPP, and H.323, ensuring compatibility with a wide range of UC applications.
Mobile and Remote Access: One of the primary functions of Cisco Expressway is to enable mobile and remote access to UC services. By utilizing the Mobile and Remote Access (MRA) feature, users can securely connect their mobile devices or remote clients to the corporate network, allowing them to make voice and video calls, send messages, and access collaboration tools.
Unified Communications Integration: Expressway seamlessly integrates with Cisco Unified Communications Manager (CUCM) and Cisco Unified Communications Manager IM and Presence (CUCM IM&P), extending their capabilities beyond the corporate network. This integration enables features such as enterprise voice, instant messaging, presence, and video conferencing for remote and external users.
Security and Encryption: Security is paramount in the design of Cisco Expressway. It employs encryption protocols such as Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP) to protect communication channels from eavesdropping and tampering. Additionally, Expressway includes features like access control lists (ACLs) and authentication mechanisms to prevent unauthorized access to UC services.
In conclusion, the architecture of Cisco Expressway is built to facilitate secure and seamless communication across diverse network environments. By providing mobile and remote access, integrating with UC platforms, and prioritizing security, Expressway enables organizations to enhance productivity and collaboration while ensuring the confidentiality and integrity of their communication data.
VPN vs Cisco Expressway performance
When it comes to comparing VPN (Virtual Private Network) with Cisco Expressway in terms of performance, there are several factors to consider. Both technologies aim to provide secure and efficient communication channels for users, but they function in different ways and cater to different needs.
VPN is a traditional method of creating a secure connection over the internet by encrypting data between the user's device and the target server. While VPNs are reliable and widely used, they may face performance issues such as slower connection speeds and potential latency due to data encryption and decryption processes.
On the other hand, Cisco Expressway is a collaboration gateway that enables secure access for remote users to connect to internal communication systems without the need for a VPN. Cisco Expressway offers a more seamless and optimized communication experience by providing secure real-time access to applications and data without compromising speed or performance.
In terms of performance, Cisco Expressway generally outperforms traditional VPN connections in scenarios where real-time communication and collaboration are key priorities. With Cisco Expressway, users can experience faster and more reliable connections without sacrificing security.
Ultimately, the choice between VPN and Cisco Expressway will depend on the specific needs of the organization or individual users. Organizations looking for a robust and secure solution for remote communication and collaboration may find Cisco Expressway to be a more suitable option in terms of performance and efficiency.
Security comparison: VPN vs Cisco Expressway
When considering secure communication options for businesses, two common solutions that often come up are Virtual Private Networks (VPNs) and Cisco Expressway. Both serve the purpose of ensuring secure connections, but they have distinct features and applications. Let's delve into a comparison between the two.
VPN (Virtual Private Network):
A VPN creates a secure, encrypted tunnel between the user's device and a remote server, effectively masking the user's IP address and encrypting data traffic. It's commonly used by remote workers to access company resources securely over the internet. VPNs are versatile and can be configured for various devices and operating systems. They provide anonymity and protect data from interception by encrypting it.
Cisco Expressway:
Cisco Expressway is a solution designed specifically for secure remote access for Cisco collaboration applications. It provides secure communication for voice, video, and data collaboration. Expressway ensures that communications remain private and encrypted, even for remote users outside the corporate network. It offers granular control over access permissions and integrates seamlessly with other Cisco collaboration tools.
Comparison:
While both VPNs and Cisco Expressway offer secure communication, their primary differences lie in their scope and focus. VPNs are more general-purpose, suitable for securing all types of internet traffic and access to various resources. On the other hand, Cisco Expressway is tailored specifically for Cisco collaboration applications, providing specialized security features optimized for voice, video, and data collaboration.
In conclusion, the choice between VPN and Cisco Expressway depends on the specific requirements of the organization. For general-purpose secure access to resources across different platforms, a VPN may be more suitable. However, for businesses heavily reliant on Cisco collaboration tools, Cisco Expressway offers specialized features and integration capabilities tailored to their needs.
Scalability of Cisco Expressway
Cisco Expressway is a powerful tool that allows businesses to enhance their communication capabilities. One key aspect of Cisco Expressway that sets it apart is its scalability. Scalability refers to the ability of a system to handle an increasing amount of work or its potential to accommodate growth. In the case of Cisco Expressway, scalability plays a crucial role in ensuring that the communication needs of an organization can be met both now and in the future.
Scalability is essential for businesses of all sizes, as it allows for flexibility and adaptability in the face of evolving communication requirements. With Cisco Expressway, scalability is achieved through various means. For example, the system is designed to support a large number of users, making it suitable for organizations with diverse communication needs. Additionally, Cisco Expressway can easily be expanded to accommodate growth, whether that means adding more users, devices, or applications.
Another key aspect of the scalability of Cisco Expressway is its ability to integrate with other Cisco products and third-party applications. This allows businesses to customize their communication solutions to meet their specific needs and to easily add new features as their requirements change over time.
In conclusion, the scalability of Cisco Expressway is a crucial feature that allows businesses to future-proof their communication infrastructure. By ensuring that the system can grow and adapt alongside the organization, Cisco Expressway provides a reliable and flexible solution for businesses looking to enhance their communication capabilities.
User experience with Cisco Expressway vs VPN
Cisco Expressway and VPNs (Virtual Private Networks) are both popular solutions for enabling secure remote access to networks. While both technologies offer ways for users to connect to resources from outside the office, they have distinct differences in terms of user experience.
When comparing user experience with Cisco Expressway vs VPN, there are several key factors to consider. One of the main differences is the setup process. VPNs typically require users to download and configure client software on their devices, which can sometimes be complex and time-consuming. On the other hand, Cisco Expressway offers a simpler setup process, often requiring only a web browser to access resources securely.
In terms of performance, Cisco Expressway is known for providing a more seamless user experience. With features like automatic firewall traversal and optimized bandwidth usage, Expressway can offer faster connection speeds and better call quality for users accessing voice and video services remotely. VPNs, while effective in providing secure access, can sometimes experience slower speeds and latency issues depending on network conditions.
Another aspect to consider is security. Both Cisco Expressway and VPNs provide encryption and authentication mechanisms to secure connections, but Expressway offers additional security features such as advanced threat protection and secure communication for real-time applications.
Overall, when it comes to user experience, Cisco Expressway may offer a more intuitive setup process, better performance, and enhanced security features compared to traditional VPN solutions. Organizations looking to provide seamless and secure remote access for their users may find Cisco Expressway to be a more user-friendly option.
0 notes
Text
does the cisco 2811 have vpn capabilities
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does the cisco 2811 have vpn capabilities
Cisco 2811 VPN support
The Cisco 2811 router is a powerful networking device that provides a range of features, including VPN support. Virtual Private Network (VPN) support on the Cisco 2811 router allows for secure and encrypted communication over the internet, ensuring the confidentiality and integrity of data transmission between remote locations.
Utilizing VPN technology on the Cisco 2811 router enables users to establish secure connections between different network devices, such as branch offices, remote workers, or business partners. By creating a virtual tunnel over the public internet, VPNs on the Cisco 2811 router ensure that data is protected from unauthorized access and interception.
The Cisco 2811 router supports various VPN technologies, including IPsec (Internet Protocol Security), SSL (Secure Sockets Layer), and PPTP (Point-to-Point Tunneling Protocol), offering flexibility and compatibility with different network infrastructures and security requirements. With robust encryption algorithms and authentication mechanisms, the Cisco 2811 router provides a secure platform for transmitting sensitive information over VPN connections.
Moreover, the Cisco 2811 router's VPN support allows for the implementation of advanced security policies, such as access control lists, intrusion prevention, and firewall rules, enhancing network security and protecting against potential cyber threats.
In conclusion, the Cisco 2811 router's VPN support is a valuable feature that enables organizations to establish secure and reliable communication channels over the internet, ensuring the privacy and confidentiality of data transmission. With its robust security capabilities and support for various VPN technologies, the Cisco 2811 router is an ideal choice for building secure and scalable network infrastructures.
Cisco 2811 VPN features
Cisco 2811 is a popular router model known for its robust VPN (Virtual Private Network) features that provide secure communications over the internet. The Cisco 2811 router is equipped with various VPN technologies to ensure data privacy and integrity for businesses and individuals alike.
One of the standout features of the Cisco 2811 router is its support for multiple VPN protocols, including IPsec (Internet Protocol Security) and SSL (Secure Sockets Layer). These protocols allow users to establish secure connections over the internet, enabling remote access, site-to-site connectivity, and secure data transfer.
The router's hardware-accelerated encryption capabilities enhance VPN performance without compromising security, ensuring fast and efficient data encryption and decryption processes. Additionally, the Cisco 2811 router offers advanced security features such as firewall protection, intrusion prevention, and access control, further enhancing network security.
Moreover, the Cisco 2811 router supports dynamic routing protocols like OSPF (Open Shortest Path First) and EIGRP (Enhanced Interior Gateway Routing Protocol), enabling efficient routing of VPN traffic across networks. This routing capability ensures optimal network performance and reliability, crucial for businesses with demanding network requirements.
Overall, the Cisco 2811 router's VPN features make it a reliable choice for organizations and individuals seeking secure and efficient communication over the internet. With its robust security measures, support for multiple VPN protocols, and advanced routing capabilities, the Cisco 2811 router delivers a comprehensive VPN solution for various networking needs.
VPN capabilities of Cisco 2811
The Cisco 2811 router boasts robust VPN (Virtual Private Network) capabilities, making it a top choice for businesses seeking secure network communications. With its advanced features and robust performance, the Cisco 2811 enables organizations to establish encrypted connections over public networks, ensuring the confidentiality and integrity of their data.
One of the key VPN capabilities of the Cisco 2811 is its support for multiple VPN protocols, including IPsec (Internet Protocol Security), SSL (Secure Sockets Layer), and GRE (Generic Routing Encapsulation). This versatility allows businesses to choose the most suitable protocol based on their security requirements and network infrastructure.
Additionally, the Cisco 2811 offers integrated VPN acceleration hardware, which enhances the performance of VPN connections while minimizing the impact on overall router performance. This ensures that VPN traffic can be processed efficiently, even during periods of high network activity.
Furthermore, the Cisco 2811 router provides robust encryption capabilities, including support for AES (Advanced Encryption Standard) and 3DES (Triple Data Encryption Standard) algorithms. These encryption algorithms ensure that data transmitted over VPN connections remains secure and protected from unauthorized access.
Moreover, the Cisco 2811 router offers comprehensive VPN management features, allowing administrators to easily configure and monitor VPN connections through an intuitive web-based interface or command-line interface (CLI). This simplifies the deployment and management of VPNs, reducing the administrative overhead for IT staff.
In conclusion, the Cisco 2811 router is equipped with powerful VPN capabilities, making it an ideal choice for businesses looking to establish secure and reliable network connections. Its support for multiple VPN protocols, hardware acceleration, strong encryption, and intuitive management features make it a versatile solution for safeguarding sensitive data and ensuring secure communication across networks.
Cisco 2811 VPN compatibility
The Cisco 2811 Integrated Services Router is a robust networking solution known for its versatility and reliability. One of its key features is its compatibility with Virtual Private Networks (VPNs), which are essential for secure communication over the internet.
The Cisco 2811 supports a wide range of VPN technologies, including IPsec, SSL, and GRE, making it suitable for various network setups and security requirements. IPsec (Internet Protocol Security) is commonly used for site-to-site VPNs, allowing remote locations to securely connect to a central network. SSL (Secure Sockets Layer) VPNs, on the other hand, provide secure remote access for users connecting from outside the corporate network. Additionally, the Cisco 2811 can also handle Generic Routing Encapsulation (GRE) tunnels, which are often used to create VPNs over the internet or other untrusted networks.
With its robust hardware and flexible software capabilities, the Cisco 2811 can accommodate the encryption and decryption processes necessary for secure VPN communication without sacrificing performance. This ensures that data transmitted over the VPN remains confidential and protected from unauthorized access.
Moreover, the Cisco 2811 offers advanced features such as Quality of Service (QoS) and Traffic Management, which further enhance its suitability for VPN deployments. QoS allows administrators to prioritize certain types of traffic, ensuring that critical data receives preferential treatment over less important traffic. Traffic Management features enable efficient bandwidth utilization, optimizing the performance of VPN connections even under heavy load.
In conclusion, the Cisco 2811 Integrated Services Router is well-equipped to handle VPN deployments of various sizes and complexities, providing secure and reliable connectivity for modern network environments. Its compatibility with industry-standard VPN technologies makes it a preferred choice for businesses seeking robust network security solutions.
VPN configuration on Cisco 2811
A Virtual Private Network (VPN) offers a secure and encrypted connection over a public network such as the internet. Configuring a VPN on a Cisco 2811 router allows users to establish a secure connection between remote locations or users.
To set up a VPN on a Cisco 2811 router, you first need to access the router's command-line interface via telnet, SSH, or console cable. Once logged in, you can begin configuring the VPN parameters.
Start by creating a transform-set, which defines the encryption and hashing algorithms for the VPN tunnel. Next, configure an access control list (ACL) to determine which traffic will be encrypted and sent over the VPN tunnel.
After that, create a crypto map to bind the transform-set and ACL together. Apply the crypto map to the router interface facing the internet to establish the VPN connection. Additionally, you will need to configure authentication methods such as pre-shared keys or digital certificates to secure the VPN connection.
Finally, ensure that the VPN configuration is properly tested by initiating a connection from a remote location to verify that data is encrypted and transmitted securely over the VPN tunnel.
In conclusion, setting up a VPN on a Cisco 2811 router involves configuring transform-sets, ACLs, crypto maps, and authentication methods to establish a secure and encrypted connection between remote locations or users. By following the necessary steps outlined above, users can ensure their data remains protected while in transit over the network.
0 notes
Text
can you configure vpn on the client side
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you configure vpn on the client side
VPN client configuration process
Title: Demystifying the VPN Client Configuration Process
In today's digital age, where privacy and security concerns are paramount, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, the effectiveness of a VPN largely depends on the proper configuration of its client software. Understanding the VPN client configuration process is essential for maximizing its benefits.
The first step in configuring a VPN client is selecting the appropriate software. There are numerous options available, each with its own features and compatibility requirements. Popular choices include OpenVPN, Cisco AnyConnect, and NordVPN, among others.
Once the software is installed, users typically need to input their login credentials provided by their VPN service provider. These credentials authenticate the user and grant access to the VPN network. It's crucial to ensure the accuracy of this information to avoid connectivity issues.
Next, users must choose a VPN server to connect to. VPN servers are located in various geographical locations and offer different levels of speed and security. Selecting a server closest to the user's physical location is advisable for optimal performance.
After selecting a server, users may have the option to customize additional settings, such as encryption protocols and split tunneling. Encryption protocols like OpenVPN and IKEv2 ensure that data transmitted through the VPN remains secure from prying eyes. Split tunneling allows users to route only specific traffic through the VPN while keeping other traffic direct, optimizing bandwidth usage.
Finally, users can initiate the connection process by clicking a button or selecting a connection profile within the VPN client interface. Once connected, all internet traffic is encrypted and routed through the VPN server, providing users with anonymity and security while browsing the web.
In conclusion, configuring a VPN client involves several straightforward steps that are essential for ensuring a secure and private online experience. By understanding and following the configuration process carefully, users can harness the full potential of VPN technology to protect their digital lives.
Setting up VPN on client side
Setting up a VPN (Virtual Private Network) on the client side is a fundamental step towards ensuring online privacy and security. Whether you're using a VPN for personal or business reasons, the process involves a few straightforward steps to establish a secure connection.
Firstly, select a reputable VPN provider that aligns with your needs in terms of privacy features, server locations, and speed. There are numerous options available, ranging from free to subscription-based services. Once you've chosen a provider, proceed to sign up for an account and download their VPN client software or app compatible with your device's operating system.
Next, install the VPN client on your device and follow the on-screen instructions to set it up. This typically involves entering your login credentials provided by the VPN provider. Once logged in, you'll have access to a dashboard where you can customize settings such as server location and encryption protocol.
Choose a server location based on your preferences. Some VPN clients automatically select the optimal server for you, while others allow manual selection from a list of available locations worldwide. Keep in mind that selecting a server closer to your physical location generally results in faster connection speeds.
Additionally, configure any advanced settings according to your preferences and security requirements. These may include options such as kill switch functionality, split tunneling, or DNS leak protection, depending on the features offered by your VPN provider.
Finally, once your VPN client is configured to your satisfaction, simply toggle the connection switch to establish a secure VPN connection. You'll know you're connected when the VPN client indicates a successful connection, typically through a notification or icon change.
In conclusion, setting up a VPN on the client side is a relatively simple process that significantly enhances your online privacy and security. By following these steps and selecting a reputable VPN provider, you can enjoy a safer and more secure internet browsing experience.
VPN client software installation
VPN client software installation is a crucial step in ensuring online privacy and security. A Virtual Private Network (VPN) creates a secure and encrypted connection to the internet, allowing users to browse the web anonymously and access geo-restricted content. Installing VPN client software on your device is a simple process that can be completed in just a few steps.
First, you need to choose a reputable VPN service provider and sign up for an account. Once you have selected a plan that suits your needs, you can proceed to download the VPN client software from the provider's website. Most VPN providers offer software for various operating systems, including Windows, macOS, iOS, and Android.
After downloading the software, run the installation file and follow the on-screen instructions. You may be prompted to agree to the terms and conditions of the software, so make sure to read them carefully. Once the installation is complete, launch the VPN client software and log in using the credentials provided by the VPN service provider.
Once you are logged in, you can select a server location from the list of available options. Connecting to a server in a different country can help you bypass geo-restrictions and access content that is not available in your region. After selecting a server, simply click the connect button to establish a secure VPN connection.
In conclusion, installing VPN client software is a straightforward process that can greatly enhance your online security and privacy. By following these simple steps, you can enjoy a safe and private browsing experience while also gaining access to geo-restricted content.
Client VPN configuration steps
Title: Step-by-Step Guide: Client VPN Configuration for Secure Connectivity
In today's digital landscape, where remote work and online collaboration are increasingly prevalent, ensuring secure connectivity is paramount. One effective solution is configuring a Client VPN (Virtual Private Network), which establishes a secure connection between a user's device and a remote server. By encrypting data transmission, Client VPNs safeguard sensitive information from potential threats and unauthorized access. Below are the essential steps to configure a Client VPN for enhanced security and privacy:
Select a Reliable VPN Service Provider: Begin by researching and choosing a reputable VPN service provider that aligns with your security requirements. Evaluate factors such as encryption protocols, server locations, and user reviews to make an informed decision.
Install VPN Client Software: Download and install the VPN client software provided by your chosen service provider onto your device. Ensure compatibility with your operating system and follow the installation instructions provided.
Create User Account: Register for a user account on the VPN service provider's website. Provide necessary information and follow the account creation process. Upon successful registration, you will receive login credentials via email.
Login to VPN Client: Launch the VPN client software on your device and enter the login credentials provided during account registration. Once logged in, you will gain access to the VPN dashboard and settings.
Configure VPN Settings: Navigate to the settings menu within the VPN client interface. Here, you can customize various parameters such as connection protocol, server location, and encryption strength based on your preferences and security requirements.
Connect to VPN Server: Select a preferred server location from the available options within the VPN client software. Click on the "Connect" button to establish a secure connection to the VPN server. Upon successful connection, your device's IP address will be masked, and all data transmission will be encrypted.
Verify Connection: Once connected, verify the VPN connection status by checking the VPN client interface or using online tools to confirm your new IP address and server location.
By following these steps, you can effectively configure a Client VPN for secure connectivity, ensuring privacy and protection against online threats. Remember to regularly update your VPN client software and adhere to best practices for optimal security posture.
Configuring VPN settings on client device
Configuring VPN settings on a client device is a straightforward process that can enhance security and privacy when browsing the internet. VPN, or Virtual Private Network, is a technology that creates a secure connection over the internet, encrypting the data transferred between the client device and the VPN server.
To configure VPN settings on a client device, start by selecting a reputable VPN service provider and subscribing to their service. Once you have obtained your VPN credentials, follow the steps below to set up the VPN on your device:
Open the device settings and locate the VPN options. This can usually be found under the "Network" or "Wireless & Networks" section.
Click on the option to add a new VPN connection and enter the required information provided by your VPN service provider, including the VPN server address, VPN type (such as IKEv2, L2TP/IPsec, or OpenVPN), and your login credentials.
You may also have the option to customize additional settings such as DNS servers, proxy settings, or advanced security features. Make any necessary changes according to your preferences.
Save your settings and connect to the VPN network by toggling the VPN connection switch to the 'on' position.
Once connected, your internet traffic will be securely encrypted and routed through the VPN server, protecting your data from potential eavesdroppers and ensuring your online privacy.
By following these steps, you can easily configure VPN settings on your client device and enjoy a more secure and private browsing experience.
0 notes
Text
Global Private 5G Network Market Size, In-Depth Assessment, CAGR, Demand, and Opportunity Analysis 2032 with Top Countries Data
Market Overview/Outlook (2022 to 2032)
The global Private 5G Network market is expected to grow between 2023 and 2032 due to factors like high-speed and low-latency connectivity, increased need for bandwidth, mission-critical applications, and industry 4.0 and smart manufacturing.
The Global Private 5G Network Market was valued at USD 1.68 Billion in 2022 and is projected to reach USD 6.59 Billion by 2032, registering a CAGR of 46.75% for the forecast period 2023-2032.
Global Private 5G Network Market Drivers
Increased need for Bandwidth: Private 5G networks are necessary to effectively support the increasing number of connected devices and bandwidth-intensive applications, including real-time data analytics, video streaming, and Internet of Things devices.
Get Report Sample @ https://isayresearch.com/sample/2299
Global Private 5G Network Market – Merger and Acquisitions
Huawei, Haier, and China Mobile Announced 5G Implementation Breakthroughs for Smart Manufacturing (2021)
With support from Huawei and China Mobile, Haier, China’s largest consumer electronics and home appliance producer, successfully applied innovative manufacturing solutions combining 5G and mobile edge computing in its smart factories. The three announced the breakthroughs in Qingdao, China on Friday.
Challenges Impacting the Global Private 5G Network Market
Spectrum Availability and Licensing: It can be difficult to obtain and license the necessary spectrum for private 5G networks. Obstacles to the deployment of private networks include the availability of suitable spectrum, regulatory policies, and the requirement to collaborate with current spectrum users.
List of Prominent Players:
AT&T Inc.
Broadcom Inc.
Cisco Systems, Inc.
Nokia Corporation
Qualcomm Technologies, Inc.
Samsung Electronics Co., Ltd.
Telefonaktiebolaget LM Ericsson
T-Systems International GmbH
Verizon Communications Inc.
Vodafone Group Plc
Others
Read Full Report Summary @ https://isayresearch.com/report/2299/private-5g-network-market/
Segmentation of Global Private 5G Network Market:
By Component:
Hardware
Software
By Frequency:
Sub-6-GHz
MmWave
By Spectrum:
Licensed
Unlicensed/ Shared
By Vertical:
Manufacturing
Healthcare
Transportation And Logistics
Energy And Utilities
Water Utilities
Retail
Public Sector
Oil and Gas
Others
By Region:
North America (U.S., Canada, Mexico)
Europe (Germany, France, UK, Italy, Spain, Rest of Europe)
Asia Pacific (China, Japan, India, Southeast Asia, Rest of APAC)
Latin America (Brazil, Argentina, Rest of Latin America)
Middle East & Africa (GCC Countries, UAE, Rest of MEA)
Read More @ https://www.linkedin.com/pulse/private-5g-network-market-projected-reach-usd-659-billion-vasa-1fkhf
About Us
iSay Research is the leading research company offering both tactical and strategic support to all our customers. Customer satisfaction is our goal and that is why, we have a team of skilled and experienced specialist with the ability to do data mining, information management, and revenue enhancement solutions to ensure that our clients make informed decisions when coming to investing in the market.
Contact Us
iSay Solutions LLC
166 Geary St. 15th Floor Suite #212,
San Francisco, California 94108,
United States
Tel: +14156709191
Email: [email protected]
0 notes
Text
Cloud Migration Market: Forthcoming Trends and Share Analysis by 2030

The Global Cloud Migration is expected at USD 136.65 Billion in the year 2021 and is predicted to reach USD 539.38 Billion by 2028, with a CAGR of 21.67% over the forecasted period.
The cloud migration market has been experiencing robust growth due to factors such as cost-efficiency, scalability, flexibility, and the need for digital transformation among businesses across various industries.
Several factors are driving the demand for cloud migration services, including the need to modernize legacy IT infrastructure, improve agility and scalability, enhance data security, and reduce operational costs.
Cloud migration services can encompass various types of migrations, including infrastructure migration (moving physical servers to the cloud), application migration (migrating applications to cloud platforms), data migration (transferring data to cloud storage solutions), and workload migration (moving workloads to the cloud).
Get Full PDF Sample Copy of Report: (Including Full TOC, List of Tables & Figures, Chart) @
https://introspectivemarketresearch.com/request/14891
Updated Version 2024 is available our Sample Report May Includes the:
Scope For 2024
Brief Introduction to the research report.
Table of Contents (Scope covered as a part of the study)
Top players in the market
Research framework (structure of the report)
Research methodology adopted by Worldwide Market Reports
Moreover, the report includes significant chapters such as Patent Analysis, Regulatory Framework, Technology Roadmap, BCG Matrix, Heat Map Analysis, Price Trend Analysis, and Investment Analysis which help to understand the market direction and movement in the current and upcoming years.
Leading players involved in the Cloud Migration Market include:
Oracle Corporation, Microsoft Corporation, IBM Corporation, Amazon Web Services, Google Inc., Cisco Systems, RiverMeadow Software, Rackspace US, Informatica, OVH US LLC
If You Have Any Query Cloud Migration Market Report, Visit:
https://introspectivemarketresearch.com/inquiry/14891
Segmentation of Cloud Migration Market:
By Service
SaaS
PaaS
IaaS
By Deployment
Private
Public
Hybrid
By End Users
Manufacturing
BFSI
IT & Telecom
Retail
Healthcare
Logistics
Education
By Regions: -
North America (US, Canada, Mexico)
Eastern Europe (Bulgaria, The Czech Republic, Hungary, Poland, Romania, Rest of Eastern Europe)
Western Europe (Germany, UK, France, Netherlands, Italy, Russia, Spain, Rest of Western Europe)
Asia Pacific (China, India, Japan, South Korea, Malaysia, Thailand, Vietnam, The Philippines, Australia, New Zealand, Rest of APAC)
Middle East & Africa (Turkey, Bahrain, Kuwait, Saudi Arabia, Qatar, UAE, Israel, South Africa)
South America (Brazil, Argentina, Rest of SA)
Highlights from the report:
Market Study: It includes key market segments, key manufacturers covered, product range offered in the years considered, Global Cloud Migration Market, and research objectives. It also covers segmentation study provided in the report based on product type and application.
Market Executive Summary: This section highlights key studies, market growth rates, competitive landscape, market drivers, trends, and issues in addition to macro indicators.
Market Production by Region: The report provides data related to imports and exports, revenue, production and key players of all the studied regional markets are covered in this section.
Cloud Migration Profiles of Top Key Competitors: Analysis of each profiled Roll Hardness Tester market player is detailed in this section. This segment also provides SWOT analysis of individual players, products, production, value, capacity, and other important factors.
If you require any specific information that is not covered currently within the scope of the report, we will provide the same as a part of the customization.
Acquire This Reports: -
https://introspectivemarketresearch.com/checkout/?user=1&_sid=14891
About us:
Introspective Market Research (introspectivemarketresearch.com) is a visionary research consulting firm dedicated to assisting our clients to grow and have a successful impact on the market. Our team at IMR is ready to assist our clients to flourish their business by offering strategies to gain success and monopoly in their respective fields. We are a global market research company, that specializes in using big data and advanced analytics to show the bigger picture of the market trends. We help our clients to think differently and build better tomorrow for all of us. We are a technology-driven research company, we analyse extremely large sets of data to discover deeper insights and provide conclusive consulting. We not only provide intelligence solutions, but we help our clients in how they can achieve their goals.
Contact us:
Introspective Market Research
3001 S King Drive,
Chicago, Illinois
60616 USA
Ph no: +1-773-382-1049
Email: [email protected]
#Cloud Migration#Cloud Migration Market#Cloud Migration Market Size#Cloud Migration Market Share#Cloud Migration Market Growth#Cloud Migration Market Trend#Cloud Migration Market segment#Cloud Migration Market Opportunity#Cloud Migration Market Analysis 2023
0 notes