#cheap antivirus
Explore tagged Tumblr posts
Text
I never know what to say when people ask me what my day job is, bc i suppose the Professional answer would be "some unholy combination of social media manager/IT support/graphic & web design" but the most accurate answer would be something more akin to Mundane Advisor. Grand Vizier for Hippies. You see, years ago, my mother used to rent out rooms to tarot readers/acupuncturists/psychics/etc, and let me tell you something about new age-y types: absolutely fucking none of them know how to make a website. As a 12 year old with a drawing tablet and a homemade Weebly site about seagulls under my belt, I was already some kind of tech expert in their eyes, and earned a fair amount of pocket money throughout high school offering dirt-cheap website & logo design services. (Child labor or entrepreneurial spirit? Who's to say.) Years later, through the powerful force of word-of-mouth-advertising and the fact that the venn-diagram intersection between "people who know what an SSL certificate is" and "people who know what an oracle card is" is razor-thin, I find myself somehow still in this field, & spending my days composing emails to the tune of "Please, sire - I know your angels guided you to make this massive blurry stolen JPEG of a unicorn your homepage background, but might i suggest... not... that?" "Yes, Mistress, verily; I am sure your issues with Microsoft Edge may very well be due to mercury being in retrograde, but ah, just in case, I would also urge you to run a scan with an antivirus program." "I--sorry? I'm sorry, Good Lady, but the premise of your new business venture is... 'The concept of love'? Spreading awareness for the concept of love? I... alright. okay. might i suggest, gently, though I know you wish not to sully your divine vision with such mundane matters as 'financial viability,' that for the sake of the kingdom, we, ah - refine our scope, somewhat--"
63 notes
·
View notes
Note
Hey ! I learnt about the first Mononoke movie through your blog a year ago ! I recommended it to a friend, who’s currently watching the series but can’t find the first bakeneko arc on YouTube anymore. Any clue where we can find it ? Thanks for your answer :)
I'm so glad you learned about the movie through this blog!
You can actually purchase DVD copies of "Bakeneko" on eBay for not that much money. If you search "ayakashi samurai horror tales dvd," quite a few listings turn up. Here are a couple:
https://www.ebay.com/itm/374740497418
https://www.ebay.com/itm/326096094288
https://www.ebay.com/itm/135396841633
These are Region 1 DVDs (there's a BluRay, but it's $50) and most, if not all, of eBay's listings ship from North America. If Region 1 doesn't work in your country, or if they don't ship there, or if you'd rather not go through eBay, then there are other (less legal) options for watching online:
Streaming:
You can find Ayakashi "Bakeneko" streaming on a few sites, like 9anime. They are currently hosting the entire Ayakashi Horror Tales anthology, including "Bakeneko" (listed as "Ghost Cat" on their site). AniWatch is another site I've seen mentioned, although I've never used it and am not sure if they have "Bakeneko."
Cons of using streaming sites:
(1) They may not be safe (my antivirus throws up a warning as soon as I open 9anime),
(2) they've got ads that also might be unsafe, so you'll need an ad blocker, and
(3) you can't download the files so you still have them if the site goes down (illegal services often do), unless you use a screen recorder, which is its own headache. 🙃
Torrents:
Probably the best way to get "Bakeneko" online is to download it via torrent. Here's a full subtitled pack that also includes the series: https://nyaa.si/view/301865.
Cons of using torrents: You need to go through a few steps and spend a little money to do it safely.
If you've never used torrents before:
(1) Make sure to use torrents only when you're logged on to a VPN (Virtual Private Network). This will keep you from being tracked via your IP address. You can set the VPN's location to a torrenting-friendly country (Switzerland is currently the best option) for maximum safety.
ExpressVPN is a good VPN option. It's not free, but it's pretty cheap: https://www.expressvpn.com. The interface is very simple and easy to use.
NordVPN also has a good rep and is a bit cheaper at the moment: https://nordvpn.com
There are free VPNs, but they're not safe and should be avoided.
(2) You'll also need a safe torrenting client to install on your computer. Fortunately, those are free. qBittorrent is currently recommended: https://www.qbittorrent.org/
The last step is to download the torrent file to your computer and then open it with qBittorent (or whichever client you're using). The client will then download the video files to your computer (should take a little while). Stay logged on to the VPN until everything is downloaded and you've exited qBittorent. 😉
Obviously, the simplest, safest, and most legal way is to purchase a DVD copy via eBay, if you can do that.
Best of luck!
12 notes
·
View notes
Text
cant believe im starting the year like this, this sucks ASS bro, rant below
tried sailing the high seas and fucked up major time by accidentally clicking on the wrong download button and letting a trojan infect my laptop. i immediately ran antivirus checks that cleared me, but apparently they got in anyways because 2 days later they started hacking into my personal accounts.
worst thing was they got into my personal instagram and posted some elon musk bitcoin fanboy thingy (which was how i found out i was being compromised). i logged out of all devices (said it was a guy in amsterdam 4 minutes before i noticed logged in) to kick em out, changed my pass, did the 2FA, all that jazz. then ran around frantically checking all my other accounts.
somehow they also got into my steam account and sold a bunch of my items that were worth pennies and bought a very cheap dota2 accessory which they can't redeem because a. i noticed it and changed my pass b. steam has a 7 day cooldown before you can re-sell it
so idk what their plan was but now i got a shitty dota2 accessory and i dont even fucken play dota, the steam part is insane cus i do have 2FA there and they still didn't notified me jack shit, and there wasn't any log ins from any other countries or devices I didn't recognize.
in any case, i changed all of my passwords from a secure device and then nuked my laptop by clean reinstalling my windows, which is obviously a hassle cus now it's back to it's shitty AI-based-one-drive-everything's-connected bull, but this was the safest thing i can do from what i can tell because it should erase any possibility of any malware hiding in my files. and since i changed my password, they shouldn't be able to get in from the old breach; im holding out hope that these type of attackers often move on to a weaker target rather than bother with one that upped their security.
really sucks cus now im paranoid as fuck despite my best efforts. this is the first (and only, i hope) time i ever experienced this kind of attack and while im lucky enough that i wasn't auto-logged into any bank accounts and i didn't lose any money and none of my friends were sent phishy texts or anything, it's still quite scary to not know for sure if im in the clear or not.
#i know its not the end of the world or anything#and i should be fine now cus i did all that i could#but still :( and i really have no one to blame than myself i guess cus i wasn't careful enough :(
14 notes
·
View notes
Text
Sav Dan's Shop (Android Zone) exploration and commentary
⚠️ The quality is just terrible
This Android Zone is called SAV SHOP in the game files. Where is it located within Detroit? No fucking clue. There's a similar destroyed Android Zone in Kara's BfD. Dunno if they're the same.
They sell new and pre-owned androids, components, repairs even some electronics and some other shit like that. Real average small tech shop.





"Kalu's Tool"? What a name. No idea wtf it is but this Uke Antivirius is kinda funny 🤪 I just can't read the text at all, bro.


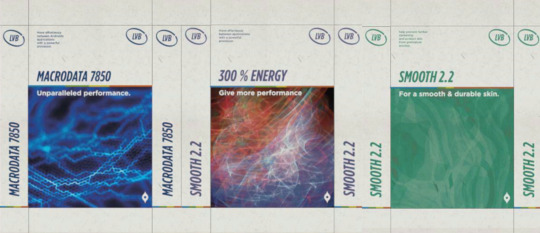
Idk what these RXL things are but ok. Reading "robot" i assume is related to those robots from the concept art. But maybe can be used in androids?
Now those LVB ones:
LVB MACRODATA 7850: Move effortlessly between Androids applications with a powerful processor.
LVB "300% ENERGY": Move effortlessly between applications with a powerful processor.
LVB SMOOTH 2.2: Help preventing further darkening and protect the skin from premature erosion
Ok, we're talking about 2 processors and one stuff for the skin? THE SKIN AIN'T A HOLOGRAM CONFIRMED.
Now, man, now look the size of that shit right there, this EYE™️ component.

Gotta be for those heavy work models. It says TR600 and the heavy model we know is TR400. Maybe a new gen? But, man, still too "big" xD that's what she said

As u can see, androids parts ain't "hollow". Ain't supposed to be, at least. Also u can notice how androids are made with "easy limbs detachment and replacement" in mind, the cables in the joints are basically plug/unplug. Still weird tho.

Say hi to the Roomba
Other android parts they sell are these "patellas" (the knee the joint) and legs/arms. Also those "Thirium cells"...

Kinda different from the regulator we know, huh? They also got a whole M series shit going on related to that patella thing i'll leave this link cuz these textures are ridiculous. Means some models series are named with one letter only, the second letter being variations of the same "model family".

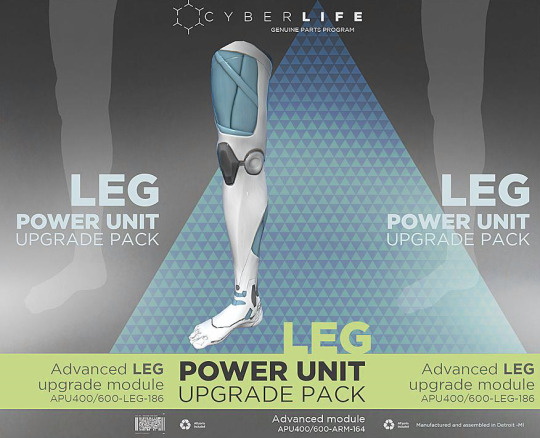
"POWER UNIT" and it's part of a UPGRADE PACK. Also a "GENUINE PARTS PROGRAM" idk what this means. Maybe pirated and cheap 3D printed components are a thing, we see these machines in Jericho.



I still don't know how these limbs works in practice, sometimes the joints just...doesn't make any sense in my head.

I ain't got no idea what those small boxes are. "Dust Cover"? What?



No idea what the triangle thing is, there's nothing on the box. Judging by being a triangle must be something related to androids (ofc).
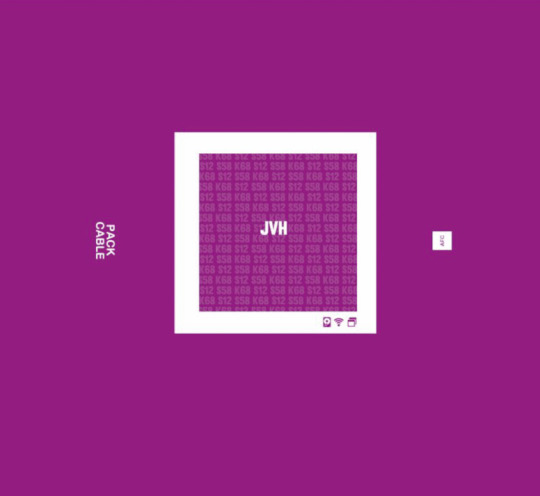
Also boxes like that purple and red ones are CABLE PACKS (from AFC?). I can notice there are some formats (one of 'em really similar to the one Zlatko uses when plugging into Kara)


U can see a Hard Disk, Wireless and "Tabs" icons there. I'm not sure what that means, maybe u can used to connect these things O.o
And ofc...CLOTHES.


They sell clothes for androids? I mean, ain't got the markings we are used to and they look pretty generic but still something.

On the table we see what looks like empty thirium bag, an opened triangle-shaped box then below the Uke Antivirus, other cable packs, dust covers, regulators, eye components, audio processing components and some other shit that looks like HDs and SSDs
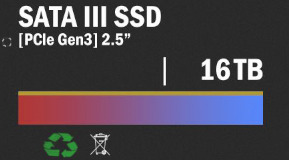
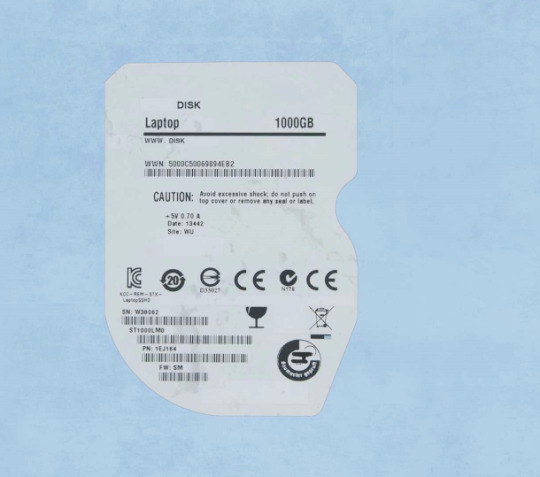
This SATA III SSD also comes in 8TB, 4TB and 2TB. Wtf xD
An honorable mention to the Android Compartments (feat Kara without a head)

I personally think it should also be a recharging point too but, well, doesn't look like one - but how tf this shit's detecting the android status then? Whatever, i hc they can recharge in there.
#[REPOST] cuz the og post was a reblog and tumblr said “idk what it is” and i couldn't find it by normal means anymore#dbh#detroit become human#dbh scenery details#dbh observation list
16 notes
·
View notes
Text
Log_50.TXT
03/02/2024, 16:05 (GMT-5)
I usually don't address this kind of stuff, but this is my fiftieth log! It's a big number so I thought it would be appropriate to address it, that's all, but let's get with the actual log now.
Yesterday, I did a delivery for some workers in my area and I hurt my ankle, it's not really something that needs to be treated by a professional or something, but it does hurt when I walk, and I've been in bed since, so I've taken this opportunity to do a little trip around the internet with my Digimon, something I haven't done since I really prefer exploring how the Digital World interacts with every nook of the real world, and not just our internet, but that's besides the point. I got my Digimon to do a little exploration of internet websites so I could have a peek at what the internet has been up to since the last time I did this, which, aside from the Mephismon X incident, was a loooong time ago, back when MegaloGrowmon was a Guilmon from what I can recall, anyways, everyone explored around a few pages that catched their interest, Canoweissmon, Siriusmon and Arcturusmon saw an astronomy related page, (this guys really like stars) Meanwhile Spinomon, Cannondramon and MegaloGrowmon were playing around a dinosaur theme park's webpage, I, however, had my eye on Kuzuhamon, Helloogarmon and Stiffilmon, who were hanging around my history to find out A Cult's Website, you see, I really like to research about cultist psychology, for no particular reason aside from the fact that I don't like predatory psychological tactics and this kind of organizations use, since a lot of people in my life could be a target to this kind of cults, but I'm going on a tangent here.
I'm guessing Kuzuhamon and Helloogarmon were attracted due to the supernatural element tied to their data and Stiffilmon was there because she really likes being near Helloogarmon, they're like a "mini" version of the not-anymore-Gammamon brothers, but, yet again, tangent, during their little exploration they ended up entering the page, and after they did that, my already deficient PC started working even worse, I initially thought it was because of the amount of Digimon I had working simultaneously, but that couldn't be it because I asked them to show in the simplest form a Digimon can adopt, a 16x16 sprite, so I had to actively check what it was, and it appears that the cult's website was to the top with Spirals. For those who don't know what Spirals are, they're a Digital Life Form (a digital being not complex enough/too complex to be considered a digimon) that was created thanks to the rifts of data that flows from the Digital World, a while ago, around 2019, the Spirals were an actual problem, however, since then a group of Tamers in Japan managed to control them, so they're more like a plague nowadays, see them as those asian hornets that were a worry about 4 years ago, they used to be feared even, but now there's plenty of ways to get rid of them, any good antivirus software should do the trick, however, some still wander around the internet since they're not allowed at the Digital World either, so they tend to hide inside unpopular websites, or some crazy people use them to infect your PC with a ton of useless data when you enter their websites. This time, it appears that they were placed on the cult's page on purpose, probably as a cheap way to store the log-in data of the members, since Spirals have a thing for Self-actualization, a thing where they basically inject random data into themselves so they can look like Digimon, anyways, seeing this vermin on my PC is the digital equivalent of having a small roach infestation in only one part of your house, so I decided to get rid of them, but it got out of hand real quick.
I asked Helloogarmon to simply burn them, however, there were way more Spirals than I expected, meaning that this cult has either an enormous amount of followers or very dedicated few ones, I quickly had to call Canoweissmon since just the heat emanating from the charge he does for the Gran Nova would be more than enough to burn them into oblivion, but this things were coming in FLOODS, much like the BEMmon that attacked us that one time at the station used to, I asked both Canoweissmon and Helloogarmon to attack together, but Stiffilmon decided to get involved too, so I might as well just got everyone there, it wasn't a particularly difficult fight, but we got rid of (I Believe) every single one of them thanks to an Atomic Blasters and Breaquasar combo. Does this harm the cult's site? Yes, on a very "small" scale, but yes, they'll have to collect that log in information again, so everyone who forgot their password will have a bad time accessing the page now, but seeing that they have predatory meanings I hold no regrets for this, anyways! In other news I finally got info on where my next tournament fight will take place, it will be this coming Thursday!, so stay tuned for another exiting narration of the next duel. Oh and regarding the DigiTama I basically stole from the police, it hasn't hatched yet, it's basically frozen, so I might have to analyze that thing, but whatever the case is, I'll keep you updated!.
ATT: ARC
#digimon#blog#blog entry#coding#larp#story#fictional world#digimon vpet#vpet#virtual pet#v pet#spiral#infection#virus#antivirus#fighting
5 notes
·
View notes
Note
Hi! This is a weird question, but I was in the notes on the VPN thing you rebloghed recently and saw you do a lot of torrenting. I used to, but didn’t have anything I needed to torrent for long enough that the current state of torrenting passed me by and I’m not sure how people torrent these days. So, if you wouldn’t mind: what’s your methodology? What do you use, sites, vpns, etc? I have utorrent, is that still the thing to use?
Basically my kid needs Land Before Time (all of it) please help
Hello! Not a weird question at all :) I'm far from an expert, but I've helped a few friends get their own setup going; I'd be happy to help! For any newbies who want to get into torrenting, check out this tutorial. It's what I used to start, and it explains a lot of the terminology and how torrenting works.
I'll put a tl;dr if you prefer to skip extra info and explanations:
VPN: AirVPN
Client: qBittorrent
Antivirus: Malwarebytes
Sites: https://knaben.info/
Playback: VLC Media Player
Step 1 is gonna be a VPN (hence why I was in the notes in that post). This will cost a bit of money, but its actually really affordable. There's a really great comprehensive ranking in r/VPNtorrents, but if you wanna skip the deep dive I use AirVPN and it gets the job done. It's on the reddit recommended list, is pretty cheap, and would be good for your situation if you just want to get Land Before Time and then drop out of torrenting again, since you can pay by the day, week, month, etc. It starts at 3 days for 2 euro, or 2.17 USD at current exchange rates. They take bitcoin or cash in the mail if you're really security-minded, as well. Whatever VPN you use make sure it has a kill switch so your ISP won't see you torrenting. Nobody wants a cease and desist in the mail.
As for clients, there's like a bajillion out there, basically all you need to do is NOT use uTorrent unless you still have a super old version and DO NOT update if you do. It's got all kinds of nasty shit baked in now and will fuck with your computer. We're talking adware, crypto mining, forcing your default search engine to yahoo for some reason, the works. Some people still use 2.2.1 but almost everybody who's made the switch prefers what the newer clients have going for them. I use qBittorrent, haven't had any issues. If qBittorrent gives you trouble, I've heard good things about Transmission.
Once you have a VPN and torrenting client, this website is an absolute lifesaver. Knaben tracks a bunch of proxies for 13 different major torrenting sites so you can see what's up and what latency looks like and all that fun stuff. It also will tell you which sites are good for what media types. IDK how easy LBT will be to find, you might need to search a couple places. Also people generally recommend against using the Pirate Bay these days because its so mainstream that it has a lot of eyes on it. I like 1337x, but that's just because I got used to its layout first.
As far as actually using your files once you have them, VLC Media Player is amazing if you don't already have it. You can even add subtitles if your videos don't come with them and you can find them online.
#torrenting#i hope this is helpful!#if you have any more questions please let me know#that goes for anybody reading this if you wanna talk torrents im always down#this is how I live out 'be gay do crimes' lol#askii
6 notes
·
View notes
Text
Ruin DLC brought me back to life
So now have my twin blorbos and an au (ish) of fnaf.
This is Lunar and Solar, plus my own design of Eclipse and how they look after Lunar and Solar repaired them.
They aren't ocs, they are self inserts
Au's name and hashtag is #Falling Stars (fnaf)
Lunar the eastern dragoness

- She/Her
- Multitask animatronic: caretaker, security, medic, cooker/baker and performer
- Wasn't created by Fazbear's Entertainment, she was created by another company of my creation called Moonshine Corporation, which even with such a name is straight up a military company.
- Older twin sister (Solar is her younger twin brother)
- 30 years old, mentally is 20
- Massive mode queen
- A magnet for baby/small animatronics, for example the mini djs
- Very maternal with younger animatronics and humans, even those who act tough or like jerks (I'm looking at you Monty)
- Isn't affected by the virus unlike Fazbear's animatronics because of the antivirus she and Solar have, which is almost completely impossible to be invaded, and even so it's very easy to take care of any virus who enters her system.
- 100% adopted c̶h̶i̶h̶u̶a̶h̶u̶a̶ ruin Monty (Monty is her dog now, at least on the au she exists lol yes, the pouch has Monty on it)
- Before ruin had an alternative mode which was the security mode, after ruin and her normal and security mode being fused, so she has another mode.
- Big 10 ft tall girl, and almost 14 ft long on ruin version
- She isn't aggressive with the player, unless the player flashlight some variations of mini djs with a moon on their chest too much times (20)
- Is DJMM and Eclipse bestie alongside Solar
Solar the eastern dragon
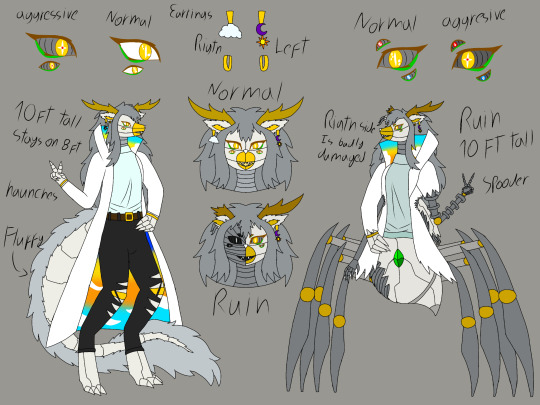
- He/Him
- Multitask animatronic: security, caretaker, cooker/baker, performer and medic
- Also wasn't created by Fazbear's Entertainment.
- Lunar's younger twin brother
- Is 30 years old, is mentally 20
- Acts very paternal with other younger animatronics and humans
- Also a magnet for baby/small animatronics, although less than his sister specially after ruin
- Likes skittering around the ceilings and walls of their area
- Big 10 ft tall boye on both versions
- The most chaotic and intense of the twins
- SPOODER
- Isn't affected by the virus like Fazbear's animatronics because of the antivirus both him and his sister have, which is almost completely impossible to be invaded, and even so it's very easy to take care of any virus who enters his system
- He's more aggressive with the player than Lunar, unlike his sister, he actively chases down the player as soon as they enter their area, he won't kill but will trap the player in a secure room
- Is DJMM and Eclipse bestie alongside Lunar
Nisshoku (They/She)

(will be updated when reference is ready)
- Is 20 ft tall and 50 ft long
- Dragon/Arachne/Lamia mix
- Lunar and Solar fusion in a single body, is called BroodMother mode (yes that one Terrifying ARK boss)
- Has several variants of mini MMs as her children and is always with them
- Very overprotective over DJMM and Eclipse
- Unhinged asf but still very motherly if you are a child or teen
- Lunar and Solar stay a lot in this form, although they normally stay in the lower levels.
Eclipse (They/He/It)

- Lunar and Solar bestie
- In this au Eclipse is a new A.I created by fusing Sun and Moon base A.Is
- Very unsuspecting and innocent
- Completely passive with the player
- Takes a hell lot to get aggressive
- If you manage to make em get aggressive, congratulations you are the most hateable creature for them, and you are dead, because not even Niss enter their way if they get aggressive.
- Was repaired by Niss when they got out of the ruined pizzaplex, Eclipse wanting to go out or not.
- Loves sweets
About + gameplay mechanics:
Lunar and Solar have an area called Cosmic cafe, it's an cafe area themed after them after they were lend to Fazbear's Entertainment, they are very rigid with the management of their ingredients, but that's because we all know Fazbear is very cheap and they have to keep an eye to make sure nothing will result in someone sick and another lawsuit. Their cafe is mostly occupied by tired adults and teenages, who come to drop their kids/sibs off at the daycare and then go to relax in their cafe since it's pretty silent.
Lunar and Solar also help around the daycare, passing most of their free time with the daycare attendant. They also are surprisingly well loved by the kids.
- Lunar: Lunar is the most calm of the dragon twins, she's pretty much silent, chill and calm most of the time, but also can be pretty chaotic. She can be often found chilling in basically everywhere, often accompanied by tired kids and teens. A total sweet tooth.
In the base game, Lunar isn't aggressive against Gregory after all, she's not affected by the virus and she knows her friends aren't in their right mind, besides she's more busy with keeping her affected moon friend away from the gremlin to chase him.
In ruin DLC, in the start she's seen wandering senselessly around her area while singing, obviously missing someone, she's not straight up aggressive with the player, but if the player flashlight a variant of mini djs with a moon on their chest (which isn't aggressive but will still scare Cassie either way) 20 times and after Monty is shocked in the water, she becomes relatively aggressive, she won't kill cassie, but if she manages to capture her, she will bring Cassie to a secret room and trap her there, but Cassie can escape the room by making a puzzle and opening the entrance, but before Monty is shocked, she's very friendly with Cassie, sometimes even singing for her if she stays on her area for a long time, and bring treats for the kid. As Cassie turns down the security tho, she becomes very insistent in trapping Cassie in the room, after all she knows the danger below the pizzaplex.
Lunar also has a side mission, which Cassie can skip but then something very interesting won't happen and an secret area won't be open to explore, the mission is finding special plushies (not AR ones) of every animatronic on the plex and bringing it to a platform in Lunar's area, the plushies include: Sun, Moon, Fred, Monty, Roxy, Chica, Nora, and DJMM.
Lunar will be very merciful with Cassie since she's just a kid, but if an adult invades the Pizzaplex and is found by her, they will have a horrible day. On this occasion Lunar uses another mode and sends her mini djs to capture the intruder and bring them to her.
- Solar: Solar is the most chaotic, yet cheerful and happy-go-lucky of the twins, he loves making pranks and driving the plex inhabitants and workers crazy, but he's also very paternal and sweet with kids and younger animatronics. Although sometimes he's a bit too intense with people, because of it Lunar always has to keep him in line. He's a salty food person.
In the base game, Solar is completely neutral over Gregory, unless he really hurts his family, then he starts intensely chasing down the kid and trapping him in a security office, Gregory can make a puzzle and escape the room but he must be careful because Solar will keep chasing him down, becoming more active as Gregory take down the glamrocks because the next ones sure would be his family.
In ruin dlc, Solar is more active since the start, although he chases down Cassie to bring her to his sister, because it ain't safe for a kid to be around. He immediately starts becoming extremely aggressive as Cassie turns down the security, after all just like his sister he knows the danger that is to turn down the security, but he doesn't appear much since Lunar and Solar are confined to their area only since all access to other parts of the plex are blocked, not completely blocked since Cassie can easily go in and out of their area, but they can't go out since there's a big risk of a collapse.
About both:
SB:
- Both animatronics are obligatory to always be together
- They aren't Freddy Fazbear's Entertainment animatronics, they were lent for a time for the pizzaplex by Moonshine Corporation, Yami's company and creators and owners of the twins.
- They are multi-purpose animatronics, but are mainly for security and childcare.
- Afton's Virus isn't able to affect both animatronics, both because they are a completely different technology and because of their highly advanced anti-virus systems, which means that they are forced to watch their friends going crazy during the security breach without being able to help.
- They may not be affected by Afton's virus, but it doesn't mean they aren't unhinged sometimes, they have a security mode (where they change form to quadrupedal forms) and are very unhinged with those who hurt their friends.
- Both have the ability of changing their limbs to many things, the main one being changing their legs and arms into 2 big wheels, making them look like motorcycles.
- They are a freaking walking factory, if they consume metal of any kind they can transform this metal inside of them, turning the materials into animatronics parts. Both also are equipped with a auto-repair module, that makes them able to change themselves and auto-repair without the need for the assistance of any other machines or people, although this ability wasn't used much after ruin, unless to create new legs for Solar.
- Lunar and Solar also are close with the glamrocks, but are closer to DJ MM and Eclipse.
Ruin:
- Lunar and Solar pretty much remember Cassie, that's why they are so merciful with her and basically only trap her in a safe and comfortable area when they get to her.
- Both took Cassie and Roxy under their wings, so in this au when the elevator fails, it doesn't crash since spooder mom grabbed the elevator with her wires and reactivated the security against the mimic.
- Lunar and Solar aren't what they are said to be.
Notes about the AUish itself
- DJ MM besides the spooder mode also has an humanoid mode thanks to Lunar lending him a Moonshine Corporation transform module.
- Monty did attack and kill Bonnie, but only when he was completely being controlled by the virus, he regrets it, a lot, especially since Bonnie was like a big brother to him.
- Sun and Moon are dormant inside Eclipse, but can pop out any time.
- The glamrocks have a familial bond between themselves and with Lunar, Solar, DJMM and Dca.
- Roxy is Cassie's cool big sister, not mom because in my opinion she's the cool big sister that everyone wants to have.
- I cannot guarantee that I will do much about this au- maybe some doodles or random images but there's no set story or timeline yet
#fnaf sb#fnaf sb ruin#personal blorbos#Falling Stars (fnaf)#fnaf dca#fnaf djmm#fnaf glamrock animatronics#Ruin brainrot go brrrrr#my art#looong post#my sonas#fnaf security breach#fnaf sb ruin dlc
3 notes
·
View notes
Text
What free or cheap (<$100/year) antivirus are u guys using
#mine expired but I KNOW I didn’t pay $100/year for it last time it must’ve been a firstie discount :(#personal
5 notes
·
View notes
Text
Something else that tends to speed up computers is disabling Superfetch (or SysMain as it's called now, I think to scare people into not disabling it). Windows Key + R (or right click the start button and click Run), type in services.msc and hit enter or click OK, find SysMain (or Superfetch on older versions of Windows 10 and beyond), right click and go into its Properties, click Stop near the bottom and select Disable for its startup type, then click Apply > Ok.
Superfetch/SysMain takes your history of program usage and loads those applications into your RAM before you click on the program (based on how often and when you use those programs) in order to speed up load times. The impact to performance isn't very noticable on mid-range builds and higher, but business desktops and cheap work laptops bog down pretty hard the longer you use them due to bundled third-party antivirus software (that you should be uninstalling immediately), Windows Defender security updates, and Superfetch filling your RAM before you have a chance to open what you intended to.
i thought my laptop was on its last leg because it was running at six billion degrees and using 100% disk space at all times and then i turned off shadows and some other windows effects and it was immediately cured. i just did the same to my roommate's computer and its performance issues were also immediately cured. okay. i guess.
so i guess if you have creaky freezy windows 10/11 try searching "advanced system settings", go to performance settings, and uncheck "show shadows under windows" and anything else you don't want. hope that helps someone else.
220K notes
·
View notes
Text
With more and more businesses moving into the online space, the capacity for cybercrime has increased exponentially over the past few yearsIt’s become more important than ever to take cybersecurity seriously, especially as a business owner. Employing dedicated staff with cybersecurity degrees and experience to assist with data protection has become a compelling option for many business owners. Here are some things to know about cybersecurity and why it is important for any organisation.What’s the Risk?When your business is vulnerable to cyberattacks, it’s hard to know what exactly that might mean. In general, your data and money are what you most need to be worried about.Getting hacked entails that hackers might gain access to credit card information (yours and your clients) other pricing and financial details, as well as your customer’s personal info. This could put you, your company, and your clients seriously at risk. When this type of data is breached, it can lead to major financial losses due to theft as well as the costs of getting rid of the threats. On top of this, a serious breach could damage your reputation as a business and lead to a loss of clients. What Can You Do?Whether your business is big or small, there’s always a risk of a cyberattack. However, there are a few steps that you can take as a business owner to make sure that your company, staff and clients are protected.AntivirusProbably the most important step to take is investing in a good and reliable antivirus software. This is not an area in your business that you want to be cheaping out – work with a good company that will provide you with great software and be available at all times for support.TrainingTake care that your entire staff base is clued up and up to date on the cybersecurity risks we mentioned above. It’s important for them all to be in the loop, know the risks and understand how to avoid them. Invest in cybersecurity training for your employees so you can rest at ease knowing that they know the drill.Update and BackupBeing on the ball when it comes to your data, files and software is an important part of staying aware and protected. Try to keep all your software up to date, to ensure that it’s better protected against attacks. Further, it’s always a good idea to keep backups of important data that your business can’t run without. Having these important backups could make it a lot easier to get back on your feet in case your files are ever compromised in an attack.The Bottom LineAs you can tell, cybersecurity is something to be taken seriously. A cyberattack on a large enough scale could leave businesses flat on their backs and unable to recover if they’re not protected. However, there are ways to stay aware and protected and avoid any serious damage to your company.
0 notes
Text
Preventing POS System Downtime: Tips for a Smooth Checkout Experience

In the fast-paced world of retail and hospitality, a seamless checkout experience is crucial for customer satisfaction and business efficiency. A point-of-sale (POS) system is the backbone of transactions, inventory management, and sales tracking. However, POS system downtime can result in frustrated customers, lost revenue, and operational chaos. To ensure smooth operations, businesses must take proactive steps to prevent system failures. Here are essential tips to minimize POS system downtime and maintain a seamless checkout experience.
1. Invest in Reliable POS Hardware and Software
A robust and high-quality POS system is the first step to preventing downtime. Opt for POS hardware and software that is designed for your industry, ensuring compatibility with your operational needs. Cheap or outdated systems are more prone to breakdowns and security vulnerabilities. Choose a system with a proven track record of stability and excellent customer support.
Key Considerations:
Use a cloud-based POS system to reduce reliance on a single physical server.
Ensure hardware components (e.g., receipt printers, scanners, card readers) are durable and up to date.
Select software with regular updates and support for troubleshooting.
2. Perform Regular Maintenance and Updates
Just like any technology, POS systems require routine maintenance to function efficiently. Ignoring updates can leave your system vulnerable to bugs and security threats.
Best Practices:
Schedule periodic software and firmware updates to prevent compatibility issues.
Conduct routine hardware checks to ensure devices are in working condition.
Clear cache and unwanted data from the system to improve performance.
Test updates in a controlled environment before rolling them out across multiple terminals.
3. Ensure Stable Internet Connectivity
Many modern POS systems rely on internet connectivity for payment processing, inventory updates, and cloud storage. An unstable connection can cause transaction failures and checkout delays.
Ways to Maintain a Stable Connection:
Use a high-speed internet connection with sufficient bandwidth to support multiple terminals.
Set up a failover system with a backup internet connection (e.g., a secondary broadband or LTE connection).
Implement network monitoring tools to identify and resolve connectivity issues before they affect operations.
4. Train Staff for Quick Troubleshooting
Your employees should be equipped with basic troubleshooting knowledge to handle minor POS issues without needing immediate technical support.
Training Tips:
Teach staff how to reboot the system and troubleshoot simple connectivity issues.
Create a troubleshooting guide for common POS errors.
Provide customer service training to handle frustrated customers during downtime.
5. Use Offline Mode for Transactions
In case of internet failure, an offline mode ensures that your business continues running without major disruptions.
How It Helps:
Allows card payments to be processed once connectivity is restored.
Ensures that sales data syncs automatically when the system goes back online.
Prevents unnecessary delays and lost sales during short-term outages.
6. Implement Regular Data Backups
Data loss due to system crashes or cyberattacks can be disastrous. A strong data backup strategy ensures quick recovery and continuity.
Effective Backup Strategies:
Schedule automatic cloud backups to prevent data loss.
Store backups on secure external drives as a secondary option.
Ensure encrypted backups to protect sensitive customer and sales data.
7. Protect Against Cyber Threats
POS systems are frequent targets for cyberattacks, including malware and hacking attempts. Strengthening security measures helps prevent breaches that can cause downtime.
Security Measures:
Use strong passwords and multi-factor authentication for POS access.
Install reputable antivirus and anti-malware software.
Restrict access levels so that only authorized personnel can make system changes.
Monitor POS activity logs for suspicious behavior.
8. Have a Backup Power Source
Power outages can bring operations to a halt. A backup power source ensures that your POS system remains operational during blackouts.
Solutions:
Use an uninterruptible power supply (UPS) to provide temporary power during outages.
Consider investing in a backup generator for extended power disruptions.
9. Work with a Reliable POS Provider
Choosing a POS provider with excellent customer support can make a significant difference in handling technical issues quickly.
What to Look for in a POS Provider:
24/7 technical support availability.
Quick response times for troubleshooting and repairs.
Regular system updates and security enhancements.
10. Monitor System Performance Regularly
Continuous monitoring of your POS system helps identify potential issues before they escalate into major problems.
Best Practices:
Set up alerts for system errors or connectivity issues.
Conduct periodic audits to assess system efficiency.
Track transaction speed and processing times to detect slowdowns.
Final Thoughts
POS system downtime can disrupt business operations, leading to lost revenue and customer dissatisfaction. By investing in reliable hardware and software, maintaining a stable internet connection, training employees for quick troubleshooting, and implementing security measures, businesses can significantly reduce the risk of downtime. Being proactive in monitoring and maintaining your POS system ensures a smooth and seamless checkout experience, keeping both customers and employees happy.
By following these best practices, businesses can keep their checkout processes efficient and hassle-free, ensuring a better overall shopping experience. Always stay prepared with a backup plan, and prioritize system maintenance to keep your POS system running smoothly at all times.
#retail billing software#point of sale#pointofsale#hotel pos software#retail#retailsoftware#retail software#retail business#software#hotel management software
0 notes
Text
I got out of school right before they (pretty much) ended typing classes (good riddance), filled the classrooms with chromebooks (we used Macs in Elementary school), and every kid had a phone (got my first one in middle school), which i shared with my sister.
I took a Computer & Information Technology (what a mouthful) class in middle & high school and some of our first lessons (first two days) were on basic navigation. Then we moved on to hardware & software EXTREMELY quickly. (I guess that's what happens when your teacher got hired straight out of high school by Microsoft)
My point is, if you're going to get into the advanced stuff (and by that, I mean anything more advanced than checking your email) you're going to need to learn to navigate.
Reasons to navigate folders:
Photo & Video storage
Video Games & Mods
Uninstalling Chrome so you can join the Firefox gang
Sharing memes online easily
Basic maintenance, organization, and identifying malware (If you're going to do maintenance and/or organization, I personally recommend CCleaner. Get the FREE version. if you're worrying about security or malware, get a cheap yearly subscription to an antivirus or get a VPN.)
You can look up a tutorial on navigation on YouTube or you can go exploring and check out what all the buttons do (check the LABELS before clicking, PLEASE) and where your folders are. You can click & drag, move folders to your workspace/desktop, right click, and change the arrangement/view of your folders. Feel free to experiment, but PLEASE mind the buttons that delete your shit.
If you're going to fuck around with the Command Prompt, please look up a single tutorial and make sure you know how to undo what you just did. These tools can be VERY helpful, but they can be misused.
this can't be true can it
99K notes
·
View notes
Text
The Pros and Cons of Admin RDP: Is It Worth the Investment?
Remote Desktop Protocol (RDP) answers have grow to be a fundamental a part of digital business operations. For companies seeking to streamline get admission to to sources and decorate server control, Admin RDP presents a comprehensive, high-manipulate solution. However, as with any generation investment, Admin RDP comes with its very own set of issues admin rdp buy rdp cheap rdp. This article explores the professionals and cons of Admin RDP, weighs the benefits, and assesses if it’s a worth investment.
Understanding Admin RDP: What Sets It Apart?
Admin RDP, or Administrator Remote Desktop Protocol, is a form of faraway desktop service that grants users full administrative privileges over a server. Unlike wellknown RDP get admission to, which provides constrained user rights, Admin RDP permits for entire manage over server configurations, software program installations, report management, and protection settings.
With Admin RDP, users can perform machine updates, configure software program settings, manage user money owed, or even display aid usage—all from a faraway place. This level of manipulate is why groups often purchase admin RDP for system administrators and IT teams who want robust remote control competencies.
Why Admin RDP is Popular in Today’s Remote Work Landscape.
Admin RDP has received traction as far off paintings will become more regular. As more agencies require centralized manipulate over their IT infrastructure, the demand for reasonably-priced RDP solutions with administrative skills has expanded. Admin RDP solutions can assist groups shop on infrastructure expenses, streamline IT control, and guide faraway personnel with secure get right of entry to to resources.
Why Invest in Admin RDP?
Admin RDP serves as a treasured device for businesses seeking excessive-degree manage and seamless faraway get entry to. For instance, IT directors can install, update, and troubleshoot systems remotely. Furthermore, cheap RDP solutions permit smaller organizations to get entry to RDP abilities at a decrease price with out compromising center functionalities.
The Benefits of Admin RDP
In this phase, we can discover the particular benefits of Admin RDP, diving into the flexibility, safety, and performance it brings.
Full Control and Flexibility
Admin RDP gives customers full administrative control, permitting them to manage server settings, set up programs, configure security protocols, and manage document access remotely. This degree of manipulate is specially beneficial for corporations that need to control more than one users, programs, or departments from a centralized server.
Example Use Case: A tech organization can also choose to shop for admin RDP to make sure their builders can get right of entry to steady sources remotely. Admin RDP’s flexibility allows them to customise get entry to based on unique departmental desires, whether it’s for improvement, checking out, or customer aid.
Benefits for Small Businesses: Smaller companies should buy RDP for improved flexibility, permitting them to remotely control assets and packages with out investing in on-website infrastructure. In instances in which they don’t want giant manipulate, cheap RDP alternatives are possible, in particular if server management isn’t always their number one need.
Enhanced Security Measures
Admin RDP answers come with built-in security features to ensure secure access. Companies can implement multi-issue authentication, information encryption, and strict access controls, which is vital for shielding sensitive facts.
Security Customization: For organizations that prioritize statistics security, Admin RDP’s custom protection protocols offer peace of thoughts. This consists of placing specific permissions for user get right of entry to, monitoring interest logs, and installing protection patches or antivirus software.
Risk Mitigation: Many corporations dealing with confidential facts can gain from admin RDP because it allows them to control security settings more carefully than trendy RDP solutions.
Efficient Resource Management
Admin RDP lets in customers to allocate and reveal sources together with CPU, memory, and storage consistent with their operational wishes.
Scalability: With Admin RDP, corporations can scale assets up or down, making it feasible to adjust server ability based totally on fluctuating demand. This useful resource flexibility is price-effective as it helps reduce downtime and maximizes efficiency.
Resource Optimization: Efficient useful resource allocation can also lower operational fees, as corporations can better manage using server assets across distinctive departments or packages.
Streamlined Remote Work Environment
Admin RDP is useful for businesses with distributed teams or far off employees, because it provides a seamless way to access vital assets.
Centralized Access: By buying reasonably-priced RDP alternatives, groups can centralize aid get admission to, enabling personnel to paintings from diverse places with out compromising on statistics access or speed.
Improved Productivity: A nicely-configured Admin RDP setup complements productiveness, as remote employees can get right of entry to all essential programs and files on call for.
The Drawbacks of Admin RDP.
Despite its advantages, Admin RDP isn’t with out its challenges. Here are a number of the capability drawbacks to consider.
Cost Implications
Admin RDP is usually greater steeply-priced than wellknown RDP, because of its advanced get entry to capabilities and security options. While there are reasonably-priced RDP alternatives, the fee difference can be massive while deciding on an Admin RDP plan.
Impact on Small Businesses: For smaller groups with restrained budgets, the additional cost of Admin RDP may not be possible until they require full manipulate. Instead, they may select to buy RDP with basic privileges.
Complexity and Learning Curve
Admin RDP is designed for users with technical expertise, which means that handling it can be complex.
Technical Requirements: Admin RDP regularly requires customers to have a history in server control, IT troubleshooting, and network configuration. Small groups or individuals with out technical abilties may additionally struggle to manipulate the server efficaciously.
Support Needs: Organizations that choose to shop for admin RDP may also want additional help for setup and upkeep, adding to the overall expenses and time dedication.
Security Risks from Misconfiguration
Admin RDP has sturdy protection capabilities, however improper configuration can disclose the system to vulnerabilities.
Mismanagement Risks: If security protocols are not efficaciously applied, Admin RDP get admission to could cause facts breaches. For businesses new to RDP, a cheap RDP plan with less difficult get admission to rights is probably a safer option.
Bandwidth and Latency Concerns
Using Admin RDP calls for a solid and high-velocity internet connection. Poor connectivity can disrupt get admission to to server resources, affecting productivity.
Connectivity Issues: For agencies working in regions with restricted internet infrastructure, the use of Admin RDP may additionally result in frequent delays or connectivity problems, impacting crew efficiency.
Is Admin RDP Worth the Investment?
Admin RDP gives powerful faraway management functions, mainly for businesses that require excessive-stage manipulate over their IT environments. However, whether or not it’s well worth the investment relies upon on precise factors which include organizational needs, technical functionality, and finances constraints.
Key Factors to Consider:
Operational Needs: For organizations wanting sturdy server control and full-size customization, Admin RDP is a worthwhile investment. Small teams with out complicated necessities may decide on a cheap RDP plan to deal with simple responsibilities without the cost of full admin get entry to.
Security Requirements: For agencies prioritizing information safety, Admin RDP’s protection features are important. However, misconfigurations should pose dangers, so businesses need to ensure they have IT information to be had to manipulate settings securely.
Budget Considerations: Admin RDP is generally extra high-priced, so it’s vital for companies to evaluate if they truly want the extent of control it affords.
Technical Expertise: Organizations without dedicated IT personnel may additionally locate Admin RDP difficult to manage, mainly if they’re unexpected with server administration.
How to Choose the Right RDP Solution
For companies and individuals determining between preferred and Admin RDP, numerous key elements should manual their desire.
Assess Your Technical Needs
Understanding the level of control required is essential. If full administrative manage isn’t vital, a cheap RDP answer may be ok.
Evaluate Your Security Concerns
Organizations handling sensitive statistics have to prioritize shopping for RDP with advanced protection functions to protect towards facts breaches and unauthorized get entry to.
Calculate the Cost vs. Benefit
For companies with excessive operational desires, the investment in Admin RDP can be worth the upfront price. However, people with simple desires may also discover that the advantages of a cheap RDP plan outweigh the want for complete manage.
Understand the Role of RDP in Your Workflow
For some corporations, RDP is only a minor part of their workflow, wherein case investing in an advanced Admin RDP solution might be unnecessary.
Conclusion: Making the Right Decision on Admin RDP
Admin RDP is a effective solution for those needing unrestricted server manipulate and high-stage safety. However, the complexity, value, and capability safety dangers imply it isn’t for everyone. Businesses and people ought to determine their particular desires, budget, and technical abilities before identifying to buy admin RDP.
For people with simpler desires, admin rdp alternatives with out administrative privileges provide an affordable alternative that gives important remote get entry to features. Ultimately, the selection among Admin RDP and widespread RDP relies upon to your specific necessities and the way critical far flung computer get right of entry to is for your operations.
0 notes
Text
Navigating the Crypto Landscape: Scams, Hacks, and Protection
Cryptocurrency has taken the financial world by storm, offering new opportunities for investment, trading, and profit. However, with this digital gold rush comes an alarming rise in scams, hacks, and deceptive practices. In this article, we will explore various Airdrop Hack Techniques and Prevention to Protect Your Assets, discuss 7 New Crypto Scams in 2025, delve into Cheap Crypto Mining Software: Top 5 Options Under $100, and uncover The Dark Side of Crypto Trading: Social Media Deceptions Uncovered. This comprehensive guide aims to arm you with the knowledge needed to navigate the tumultuous waters of cryptocurrency safely.
Airdrop Hack Techniques and Prevention to Protect Your Assets
Airdrops have become a popular method for cryptocurrency projects to distribute tokens to users, but they also attract malicious actors looking to exploit unsuspecting investors. One of the most common Airdrop Hack Techniques involves phishing scams, where users receive fake airdrop notifications that lead to fraudulent websites. These sites may mimic legitimate airdrop pages, tricking users into providing sensitive information such as private keys or wallet details.
Another technique involves malicious smart contracts. Some airdrops require participants to interact with smart contracts, which can be designed to drain wallets of funds once the transaction is approved. To safeguard your assets, it’s crucial to conduct thorough research before participating in any airdrop. Always verify the legitimacy of the project and avoid clicking on suspicious links.
Additionally, using hardware wallets can significantly reduce the risk of hacks. These devices store your cryptocurrencies offline, making it difficult for hackers to access your assets. Implementing two-factor authentication and keeping your software up to date are also essential steps in protecting your digital wealth.
7 New Crypto Scams in 2025
As the crypto landscape evolves, so do the tactics used by scammers. In 2025, several new scams have emerged that every investor should be aware of. The first scam to watch out for is the fake influencer endorsements. Scammers often create fake social media profiles of popular figures, promoting dubious projects in exchange for payments. Always verify the legitimacy of endorsements before making any investment decisions.
Another emerging scam is the exit scam, where developers abandon their projects after raising significant funds. This scam typically occurs in Initial Coin Offerings (ICOs), where creators disappear once they’ve amassed a large amount of money. It’s crucial to perform due diligence and analyze the team behind any project before investing.
Additionally, pump-and-dump schemes have resurfaced, where groups artificially inflate the price of a cryptocurrency to profit from unsuspecting investors. These schemes can be particularly deceptive on social media platforms, where coordinated efforts can create a false sense of urgency.
A further concern is malware targeting crypto wallets. Cybercriminals are developing sophisticated malware designed to infiltrate wallets and steal private keys. Regularly scanning your devices for malware and using reputable antivirus software can help mitigate this risk.
Moreover, the rise of fake exchanges has made trading riskier. Scammers set up imitation exchanges that often appear legitimate, only to vanish with users' funds. Always trade on well-established platforms to avoid falling victim to these scams.
Finally, cloud mining scams have become prevalent, promising unrealistic returns on investments. These scams often lure investors with flashy advertisements and promises of high returns. If an investment sounds too good to be true, it probably is.
Cheap Crypto Mining Software: Top 5 Options Under $100
For those looking to dive into cryptocurrency mining without breaking the bank, there are several options available. Among the Cheap Crypto Mining Software: Top 5 Options Under $100, several tools stand out for their functionality and ease of use.
First on the list is software that provides a user-friendly interface and supports multiple algorithms. This type of software allows beginners to start mining with minimal technical knowledge. Additionally, some options focus on efficiency, ensuring that your mining operation consumes less power while maximizing profits.
Another valuable option is mining software that offers detailed performance analytics. Such features can help users monitor their operations and make informed decisions regarding their mining strategies.
Lastly, consider software that allows for remote management. This feature is beneficial for those who want to oversee their mining rigs from anywhere, providing flexibility and convenience.
By investing in affordable yet effective mining software, you can embark on your crypto mining journey without excessive financial strain.
The Dark Side of Crypto Trading: Social Media Deceptions Uncovered
While social media can be a powerful tool for connecting with the crypto community, it also harbors risks. The Dark Side of Crypto Trading: Social Media Deceptions Uncovered reveals how scammers use these platforms to prey on unsuspecting traders.
One common deception is the use of fake trading signals. Scammers claim to provide exclusive access to trading strategies that promise significant profits. These signals are often based on misleading information or fabricated results. It's vital to approach such claims with skepticism and conduct your own research.
Moreover, social media platforms are rife withfraudulent giveaways. Scammers often pose as legitimate projects, promising free tokens in exchange for participation in seemingly harmless activities. In reality, these giveaways are often designed to steal personal information or funds.
In addition to these scams, fake testimonials and reviews can mislead potential investors. Some individuals create false accounts to promote a particular project or product, creating an illusion of credibility. Always seek independent reviews and verify the legitimacy of claims made on social media.
Conclusion
As cryptocurrency continues to gain popularity, understanding the landscape's dangers is essential. By recognizing Airdrop Hack Techniques and Prevention to Protect Your Assets, staying informed about 7 New Crypto Scams in 2025, exploring Cheap Crypto Mining Software: Top 5 Options Under $100, and being aware of The Dark Side of Crypto Trading: Social Media Deceptions Uncovered, you can navigate this exciting yet treacherous world more safely. Knowledge is power, and equipping yourself with the right information is your best defense against scams and hacks in the ever-evolving crypto realm.
0 notes
Text
The thing is games from 10 years ago run amazingly well on cheap laptops these days
The latest games have the latest graphics and so need better graphics cards
The latest video, animation, and engineering software frankly run very well on $2000 to $3000 laptops when you needed a $5000 desktop before
Technology has made this better
But for operating systems and web browsers and other general purpose applications bloatware is unacceptable. A modern laptop should let people have antivirus and the ability toi watch youtube on 4GB of RAM no problem. Instead of rural internet being the test it should be that no application should require an internet connection unless needed for its core functionality. But people aren’t willing to pay for products. A windows license used to cost twice as much when accounting for inflation and now you can get it for “free”
That included bloatware and data collection PAY for your operating system and security updates. Your data is the product being sold.
My solution for bloatware is this: by law you should hire in every programming team someone who is Like, A Guy who has a crappy laptop with 4GB and an integrated graphics card, no scratch that, 2 GB of RAM, and a rural internet connection. And every time someone in your team proposes to add shit like NPCs with visible pores or ray tracing or all the bloatware that Windows, Adobe, etc. are doing now, they have to come back and try your project in the Guy's laptop and answer to him. He is allowed to insult you and humilliate you if it doesn't work in his laptop, and you should by law apologize and optimize it for him. If you try to put any kind of DRM or permanent internet connection, he is legally allowed to shoot you.
With about 5 or 10 years of that, we will fix the world.
70K notes
·
View notes
Text
Exactly How Receiving A Legitimate Windows Activation Token Can Conserve You Money?
Investing in a real Microsoft Windows activation key is actually certainly not pretty much legitimacy; it is actually a smart financial action. By picking legitimacy, you're not simply safeguarding yourself from potential legal impacts yet likewise setting on your own up for a variety of cost-saving perks. From enhanced protection measures to long-term system security, the benefits of a valid key exceed the first acquisition. Therefore, before putting away the suggestion as merely one more cost, look at the lasting effect it can have on your budget and total computer expertise.
The Ways Obtaining A Real Windows Activation Key Can Spare You Money
Lawful Conformity and Cost-Effective Solutions
To make sure legal conformity as well as find economical remedies for obtaining a legitimate Windows key cheap, it is essential to carry out extensive research and confirm the legitimacy of vendors. Start through looking into reliable online retailers or accredited resellers recommended through Microsoft. Look for reviews and comments from other consumers to determine the stability of the seller. Furthermore, think about checking the seller's internet site for main accreditations or partnerships along with Microsoft to ensure the legitimacy of the activation key.
Matching up costs from different vendors may also assist you discover an economical answer. Nonetheless, be watchful of offers that appear also really good to be true, as they might be actually selling imitation or even unwarranted keys. Bear in mind that spending in a real activation key not merely ensures legal conformity but also supplies accessibility to vital updates as well as support from Microsoft.
Boosted Protection and also System Stability
Enrich your system's protection and also stability by carrying out strong protection steps and also routine system maintenance. By utilizing a real Windows 11 keys, you ensure that your operating system gets vital protection updates and spots. These updates aid safeguard your system from malware, infections, as well as various other cyber dangers that may weaken your data as well as personal information. For a wallet-friendly solution, head to https://www.reddit.com/r/computer/comments/1c2urj7/looking_for_a_cheap_Windows_key_where_to_get_a/ website to get hold of affordable Microsoft Windows activation keys as well as boost your computing experience.
An authentic Microsoft Windows key also permits you to gain access to evolved protection features that may not be on call in pirated variations. Features like Windows Guardian Antivirus, firewall program defense, and secure shoes are crucial for protecting your system versus potential cyber strikes. With these surveillance procedures in position, you can browse the net, download documents, as well as use treatments along with better peace of thoughts.
Furthermore, normal system maintenance, like hard drive cleanup, defragmentation, as well as improving chauffeurs, can easily contribute to the general stability and efficiency of your system. Through keeping up to day with system upkeep jobs, you can protect against accidents, inaccuracies, and also various other problems that may emerge from disregarding your system's servicing. Prioritizing safety and security and system stability not merely guards your assets in your device yet additionally makes sure a smooth as well as efficient computing experience.
Long-Term Discounts as well as Software Updates
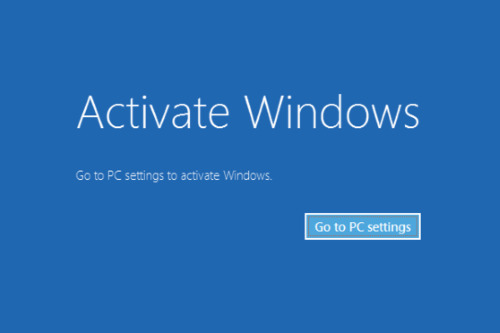
By buying an authentic Windows activation key, you get lasting discounts and also make sure access to necessary program updates for your system. Legitimate Microsoft Windows activation keys offer you along with the comfort that stems from understanding your operating system is legit as well as will definitely get regular updates directly from Microsoft. These updates certainly not simply enhance the performance of your system but additionally defend it from safety susceptibilities that may occur from making use of pirated software or unverified resources.
Regular software program updates are actually essential for keeping your system running effortlessly as well as successfully. Along with an authentic activation key, you may be actually confident that your Microsoft Windows operating system will certainly proceed to obtain the most recent attributes, bug solutions, as well as surveillance spots. This proactive technique not merely saves you money down the road by avoiding pricey system mistakes however likewise makes sure that your computer system continues to be current along with the current innovation innovations.
Technical Help and Manufacturer's Warranty Perks
Purchasing a real Microsoft Windows activation key offers you along with accessibility to beneficial technological assistance and also manufacturer's warranty perks. When you experience issues or even require assistance along with your Windows operating system, possessing access to specialized assistance could be a game-changer. Genuine Windows activation keys ensure that you may communicate to Microsoft's help crew for support, troubleshooting, and assistance, saving you time as well as frustration.
Additionally, legitimate Windows activation keys usually possess guarantee advantages that can easily guard your investment. In situation of components failures or notable issues connected to Windows activation, having an authentic key may create you qualified for manufacturer's warranty claims and assistance services. This can likely spare you money on repair services or even replacements that would typically be expensive.
Conclusion
Spending in a genuine Microsoft Windows activation key can conserve you money in the end by ensuring lawful compliance and giving affordable solutions. It enriches surveillance and also ensures system security, delivering lasting cost savings as well as accessibility to program updates. Also, it provides access to specialized assistance and manufacturer's warranty benefits. It is actually a smart option for defending your personal computer system as well as preventing potential legal concerns, pricey fines, and security breaches. Help make the sensible assets for your personal computer's safety as well as durability.
0 notes