#Frontier Email Login
Text
Monica joined Glassdoor about 10 years ago, she said, leaving a few reviews for her employers, taking advantage of other employees' reviews when considering new opportunities, and hoping to help others survey their job options. This month, though, she abruptly deleted her account after she contacted Glassdoor support to request help removing information from her account. She never expected that instead of removing information, Glassdoor's support team would take the real name that she provided in her support email and add it to her Glassdoor profile—despite Monica repeatedly and explicitly not consenting to Glassdoor storing her real name.
Although it's common for many online users to link services at sign-up to Facebook or Gmail accounts to verify identity and streamline logins, for years, Glassdoor has notably allowed users to sign up for its service anonymously. But in 2021, Glassdoor acquired Fishbowl, a professional networking app that integrated with Glassdoor last July. This acquisition meant that every Glassdoor user was automatically signed up for a Fishbowl account. And because Fishbowl requires users to verify their identities, Glassdoor's terms of service changed to require all users to be verified.
While users can remain anonymous, this change raises some potential concerns about data privacy and anonymity, Aaron Mackey, a lawyer for the Electronic Frontier Foundation (EFF), told Ars.
4 notes
·
View notes
Text

Crypto Investors Beware: Unveiling the 12 Most Common Scams in the Cryptocurrency World
Cryptocurrency, with its decentralized and digital nature, has become a hotbed for innovative financial opportunities. However, it also presents a new frontier for scammers, exploiting the lack of regulation and the anonymity it offers. As we navigate through 2024, it's crucial to stay informed about the most prevalent crypto scams to protect your investments. Here's a comprehensive look at the ten most common cryptocurrency scams that have been identified this year.
Phishing Scams: These scams involve fraudsters impersonating legitimate entities to steal sensitive information. They often send emails or create websites that look remarkably similar to reputable companies to trick individuals into divulging their private keys or login credentials.
Rug Pulls: A rug pull happens when the developers of a seemingly legitimate cryptocurrency project suddenly take the funds and disappear. This leaves investors with worthless tokens and no recourse to recover their investments.
Giveaway Scams: Scammers promise to multiply the cryptocurrency you send them as part of a fake giveaway. Unfortunately, once the crypto is sent, the scammers vanish, and so does your money.
Ponzi Schemes: These schemes promise high returns on investments but pay profits to earlier investors, using the capital from newer investors. Eventually, the scheme collapses when there's not enough new money coming in.
Investment Scams: These scams typically involve promises of guaranteed returns or insider tips. They rely on convincing individuals to invest large sums of money into projects that are non-existent or misrepresented.
Fake ICOs (Initial Coin Offerings): Scammers create fake ICOs, promising revolutionary new tokens or projects, but vanish with investors' money once they've raised enough.
Fake Exchanges and Wallets: Scammers create fake cryptocurrency exchanges or wallets that look legitimate but steal users' funds once they deposit them.
Fake Mobile Apps: Malicious apps on app stores mimic legitimate cryptocurrency wallets or exchanges to steal users' login credentials or private keys.
Impersonation Scams: Scammers impersonate prominent figures in the cryptocurrency community, such as developers or CEOs, to deceive users into sending them cryptocurrency.
Pump and Dump Schemes: Groups of individuals artificially inflate the price of a low-volume cryptocurrency through coordinated buying, then sell off their holdings at the peak, leaving other investors with losses.
Social Engineering Attacks: Scammers manipulate victims through social media or messaging platforms to send them cryptocurrency under false pretences.
Mining Scams: Fraudulent mining schemes promise high returns on investments in mining hardware or cloud mining contracts but fail to deliver profits or even exist at all.
Always conduct thorough research before investing in any cryptocurrency project, and be cautious of offers that seem too good to be true. Additionally, never share your private keys or personal information with anyone.
To safeguard against these scams, it's essential to conduct thorough research, use reputable sources, and never share personal information or send money based on unsolicited offers. Remember, if an investment opportunity sounds too good to be true, it probably is. Always exercise caution and consult financial advisors before making significant investment decisions.
1 note
·
View note
Text
Cat's out of the bag & on your way...

Mentor Message 4.19.24
🆕Updates:
Regular & Substantive Interaction ( RSI): A process for regularly reviewing all online courses will begin Fall 2024. Accreditation requires that the campus ensure RSI is occurring in online courses. Tools & Technologies for Facilitating RSI in your Canvas.
Single sign-on (SSO) is coming to Canvas this summer! Encourage your students to start using their MS 365 email login credentials. Starting Summer-Fall 2024, everyone will use their MS 365 email login/password instead of their 10 digit IDs/password to get into Canvas.
Are you certified for Online Teaching at SDCCD? Faculty must have successfully completed certification of the SDCCD Online Faculty Certification Program to be offered online courses … i.e., no more Pandemic driving without a license🚗 The next new cohort will start July 1.
LTIs in Canvas (apps in Canvas): Transition period in the summer – several LTIs such as Zoom, PopeTech, various publishers, Turnitin, and Cidilabs – are getting upgraded to a newer version. Sample of LTIs in Settings>Apps
🏫Professional Development (PD):
Interested in attending the Online Teaching Conference in Long Beach 6/26-6/28? Contact Marco Anzures, City PD Coordinator([email protected]) and cc me ([email protected]) if you would like to attend. Participants will offer workshops to pass on the learning to our campus at City’s Fall Flex 2024.
We can once again use 3C Media storage and professional captioning! It is a faster/easier option for your own videos vs. DECT Grants. Directions for Requesting Captioning
@One Webinars
Next round of Free @One Courses open April 29th
SDSU Micro-Credential Program for AI to train students & faculty just launched. Open to all SDSU students & faculty. They are in works with sharing this opportunity for our colleges.
💡Tech Tips:
Tips for Gussy-ing Up Your Canvas Pages: accordions, more interesting DB posts, timelines, etc.
Fun Tools to Try Out: Thinglink (free for 60 days) - add hotspots to images/videos, track engagement/feedback & Coolors.co - free color palette generator
Add Diversity to Your Images: Free & Diverse Image Collections (Many thanks to Mesa’s Include 4 Course for this link)
Use Chat GPT or Co-Pilot to edit your captions: AI tools can help with video captioning by copy/pasting your transcript and using the following prompt: "Can you take the following autogenerated captions and edit them to include proper punctuation and correct any errors?" (You can use MS Word Add-in to open Chat GPT within your document. See 2.16.2024 tutorial)
Hate the thumbnail Canvas Studio often chooses? You can upload your own image or create one Ways to change or create a thumbnail for videos
Built-in Similarity Checker in MS Word”: Not as robust as our Turnitin Similarity Plagiarism checker (that can compare with our library databases & other student submissions), but it can do a quick check for anything pulled from the Internet without having to navigate away nor any copy/pasting/uploading. From "Home," click on "Editor" to open & click on the "Similarity" check.

🤖AI Resources:
SDCCD Online Pathways: AI News & Resources
Rodrigo Gomez's AI PD series: AI Demystified: Introduction to Generative AI: Next sessions:
Session 5: Navigating the AI Landscape: AI Literacy Day 2024, Friday, April 19, 11:30 am-12:45 pm, Zoom, Flex #21522
Session 6: AI and Web3: Synergy in the Next Frontier: Friday, May 3, 11:30 am-12:45 pm, Zoom, Flex #21523
For Presentations #1, 2, 3, 5, & 6
https://sdccd-edu.zoom.us/j/87085616603
Meeting ID: 870 8561 6603
One tap mobile: +16699006833,,87085616603#
Dial by your location: +1 669 900 6833
Previous Sessions
Friday, February 23, 11:30 am - 2:45 pm, Zoom, Flex #21459 (Presentation #1 recording & Presentation #1 slides)
Harnessing AI: Advanced Prompting Techniques: Friday, March 1, 1-2:30 pm, Zoom, Flex #21491 (Presentation #2 recording & Presentation #2 slides)
Art from Words: Crafting Art with AI: Friday, March 8, 11:30 am-12:45 pm, Zoom, Flex #21520 (Presentation #3 recording & Presentation #3 slides)
AI Food for Thought: “The End of Foreign Language Education,” Atlantic Monthly
0 notes
Text
Navigating the Digital Frontier: Protecting Yourself from UPI Scams
As we increasingly embrace the convenience of digital transactions, the prevalence of UPI (Unified Payments Interface) scams has risen as well. UPI, a revolutionary system that enables instant money transfers between banks through mobile devices, has become a target for fraudsters looking to exploit unsuspecting users.
While UPI technology has revolutionized the way we conduct financial transactions, it’s essential to remain attentive in the face of evolving scam tactics. By adopting a proactive approach, staying informed, and following the recommended safety measures, you can protect yourself from falling victim to UPI scams.
Check out these details to understand the common tactics used by scammers and crucial tips to ensure safety.
Understanding UPI Scams

1. Phishing Attacks
One of the most common tactics used by fraudsters is phishing. In a UPI phishing scam, users receive fake messages or emails that appear to be from their bank or a trusted service provider. These messages often contain malicious links that, when clicked, lead to fraudulent websites designed to capture sensitive information such as login credentials or OTPs (One-Time Passwords).
To Read More Click here...
#tech news#tech blogs#tech updates#new technology#new features#latest version#phishing attacks#UPI Scams#digital frontier#ensure safety
0 notes
Text
Frontier Mail Login Access Your Account Easily Step-by-Step Guide
Gain access to your Frontier Mail login account. Follow simple steps for Frontier Mail login and manage your emails .
0 notes
Text
How Do I Write A Complaint To An Airline?
Assume you have flown with Frontier Airline and your travel experience wasn’t that good as the services provided by staff are so bad they are not listening to what the passengers say. So, it is rare that passengers face problems with Frontier Airlines, and if you face any of the problems, then you can immediately complain about that to Frontier Airlines customer service by filling out a form for that. And if you want to learn the procedure of form filling, you can read the information mentioned below.
Mention the Procedure To Fill Out the Complaint form
Travelers who have complaints related to anything can fill out a form for that and send a complaint through the online procedure. And if you want to learn the procedure in brief, then take the guidance from the below points.
Navigate toward the official webpage of Frontier Airlines.
Tap on the login button and provide your Email id and password to them.
At the bottom of the page, you will find the option of help. You can click on it.
And find the option of filling out a form.
After that, click on it and provide all the necessary details and fill out your form.
And if you have a lost baggage complaint, then do not forget to add the information related to your baggage.
Now you can directly click on the submit button.
And the customer service agent will connect with you as soon as possible and provide you with all the necessary details.
How Do I Speak To Someone at Frontier?
You can also raise your complaint by reaching out to customer service through phone calls and live chat and get a solution to your problem from them. To get the directions regarding that, read the steps below.
Complaint Through Phone Call
You can also speak with the live person at Frontier Airlines for your complaint, and they will help you in solving the problem. And to learn the proper procedure read the steps below.
Place a phone call at 855-981-4544 this number.
After that, carefully listen to the IVR instructions.
You can press 1 to choose your preferred language.
Press 2 for the reservations and related questions.
Press 3 for general queries.
Press 4 for flight cancellations and refunds.
Press 5 for the complaints.
So, you can press five and ask them. As per the instructions, press the numbers.
After that, after a few minutes, you will be able to talk with the customer service agent.
They will note your complaint, and soon you will get a solution for that.
Complaint Through Live Chat
You can speak to the live person at Frontier and register your complaint to them by using the live chat option that is available on the website of the Airline. And the procedure for that is mentioned below.
Reach out to the webpage of Frontier Airline.
Go to the bottom of the page and click on the ‘contact’ button.
Now you have reached the website of the Frontier and found the chat button.
Now click on that and write your complaint in the empty box.
And tap on the send button.
An executive will register your complaint, and then they will provide the best outcome.
Read more: How To Contact Iberia at Moscow Airport?
#How do I speak to someone at Frontier#Frontier airlines customer service#talk to live person at frontier airline
0 notes
Text
warzone silent aim download 100% working 297V%
💾 ►►► DOWNLOAD FILE 🔥🔥🔥🔥🔥
› call-of-duty-warzone-hacks-cheats-aimbot. The silent aim hack takes this to the next level. In the clip, the player is spectating a hacker. The hacker appears to randomly start shooting at the ground. Silent Aim in Warzone basically gives the hacker magnetic bullets. As with the Soft Aim, the player can move and aim normally. Discussion on WARZONE Cheat. APEX SEASON 13 CHEAT | SILENT AIM, MODEL CHANGER, 3rdPERSON, ESP | INTEL ONLY!✓. - Draws a line to upgradeable attachments of current. 9 Posts Likes Following Archive. Learn more about CoreCoins here. Join Now. Follow us:. If this is your first visit, be sure to check out the FAQ. You have to register before you can post. Almost all ads disappear when you login. Buy Shout-Out. Trade Details Trade Type: Free. Page 31 of 33 First Thread Tools. Originally Posted by lrt Status: Trade. Originally Posted by MarvelousGamers. Originally Posted by banek When will cheat be updated? Originally Posted by Spooderman Is the cheat working for season 10? Originally Posted by Ilovebanek. Updated for Season 10 Have fun! Thankyou Mr. Bought the hack yesterday. Followed the guidelines with anti-virus fully turned off. Not getting any error messages at all, the hack just doesnt show ingame. Not sure if the hack is just not compatible with my PC or just not working. Windows 10 with Intel I9 Edit: Fixed. Last edited by mouN; at PM. Why enter the game and then retreat. All rights reserved. Digital Point modules: Sphinx-based search. Magic bullets. Player ESP. No recoil. Escape From Tarkov. Magic Bullets. Destiny 2. Infinity ammo. No tree textures. No Recoil. Coloring opponents. Zooming out the camera. Dead By DayLight. Survivors ESP. Killer ESP. Hatch ESP. Good Bypass. Silent aimbot. Hwid Spoofer. Airdrop ESP. Cars ESP. Sea Of Thieves. Chests ESP. Skeleton ESP. Last Oasis. Auto weapon. No sway. No ban. New Rust Account. Recoil control. Private build. Hunt: Showdown. Crooked Arms. Guns skins. Music packs. Player Skelet. Rogue Company. Dota 2. Illusion ESP. Creep MapHac. Last Hit. Phase boots. Silent Aimbot. Zombie ESP. ARMA 3. Unlocking Tool. Unlock Optrators. Unlock Other Skins. Unlock Camo. Mutant ESP. Anomaly ESP. Bot ESP. Unlock all. Monsters ESP. Boss ESP. World Of Warcraft. Use hearthstone. Delete trash item from inventory. Colored players. Colored tier equipment. No grass. Remove unwanted sounds. Custom Thermal Scopes. City ESP. Container loot ESP. Jacket loot ESP. Infinity Stamina. Skip reload animation. Objects ESP. Unlock all skins. Dino ESP. Fov selection. Stream proof. Raid ESP. Ghost mode. Unlock DLC. Super Jump. Show players on the radar. Show players on a mini-radar. Email Access. You are owner. New SCUM account. Loot through bases. Instant building. Spawn weapons. Champion Combo. Skin hack. Unlock Camo and skins. Unlock Doors. Night vision. World time. Mark traitors. Teleport to player. Walk through the walls. Speed myltiplier. Loot filter. Unlimited ammo. Easy to install. Loot Through Walls. Player, bots ESP. Set game time. Admin mode. Double jump. Instant revive. Zombies ESP. Animals, loot, others. SC PRO. Unlimited stamina. Ore ESP. Dlc unlock. No glass. Stashes esp. Super People. Unlock Other skins. Rainbow Six Siege. Player bones. Unlock Watches. Unlock Weapons. Account SCUM. Health ESP. League Of Legends. Project Winter. GTA 5. Super jump. Visible check. Smart aim. Animal ESP. Structures ESP. Iteam teleport. Fast unlock. Always day. Lock pick. Ores ESP. Skelet ESP. Loot Teleport. Physical Strength. Infinite Stamina. No flash. The Cycle: Frontier. Dead players. Reseller of the best private cheats from around the world for your favorite games!
1 note
·
View note
Text
We All Lived Two Lives Back Then.
Let's talk about the old days of the internet. The days when dial up was literally the only option. When it was the Wild West or the Frontier and it was strange and frightening. When social media wasn't a thing, when it was chat rooms and message boards and AIM, or MSNmessenger if you were fancy. When you had to type in both the http:// AND the www. to get where you were going.
Yeah, the late 1900s (which is a phrase that automatically makes anyone with a birth year starting with a 1 feel like Rip Van Winkle waking up).
Back then, the internet was full of predators. That cool kid you're talking to in a chat room who is just like you? Is actually a 40 year old pedophile looking for prey. Never ever ever answer when someone asks you "a/s/l?" If a website requires your location, just give the continent you're on, or lie. Never ever give out your real name. Never say where you go to school. Don't say what grade you're in. Be mysterious. Be secretive. Secretive = safe. Why, just last week, we were told, some teenager met the person they were "online dating" and he was lying about his age and murdered her, do you want to be next???
Because back then, the only time the internet was in the news was when something horrible happened, so the worst humanity had to offer was always in the forefront of our minds. And they were all online.
Now, we can see this as hyperbole, that idea that "everyone" is dangerous. No, most people aren't, and they weren't then. But we erred on the side of caution back then.
Then came Facebook and their culture of accountability. Zuck and his idea that everyone should be open and honest and forthcoming online. And for whatever stupid reason, we bought into it. For some reason we decided as a species that we wanted to know every thought everyone we have ever known ever had. For some reason, we thought that if we were using our real identities, the bad guys would too. Besides! If you don't use your real name, how will people you know find you??
😑 How indeed. Suddenly, the focus of being online ceased being, "Be as anonymous as you can" and morphed into "people finding you is a good thing." Talk about a 180.
Are we surprised then, that the threat of being stalked and doxxed is so real and frightening?
We were told in the time of the telecommunications equivalent of the horse and cart that what is online is online forever. When did we stop reminding ourselves that? When did parents stop telling their kids about this? And it's all connected too, more so now than ever. We have too many things to login to to have a separate identity at every single one. We forget to disallow sites to collect and use our location data. We think "sure if someone knows this email address, they can use it to find me here."
What we should be thinking is, "Oh shit, if someone knows this email address they can use it to find me here 😳."
Back in the day, we guarded our fandom personas from our real lives, FIERCELY. Because, omg, if someone I know IRL finds my grocities, I will DIE and this is not an exaggeration. But also, Omg if n00beater69 finds me on my family MySpace, he'll tell my mom I rec'd lemons.
And no one wants their mom to know about the lemons.
We all lived two lives. And it was normal.
Now, it's not healthy to live in a constant state of paranoia and distrust and fear. But just because you're NOT paranoid doesn't mean a monster isn't waiting to eat your face.
All this to say, Auntie Pan has some well-intended advice based on a lot of experience.
Live two lives. It's okay. Protect yourselves and your families by being secretive and mysterious.
Use a pseudonym and don't give out your real name. I'd answer to Pan in public if someone called me that. I'd probably still look up if I heard someone call me by my first fandom alias.
Use a separate email address for your fandom activity. Do NOT use your school or work email for this. If masked marauders aren't watching you, your organization IS. This also puts your at greater risk of doxxing. (BTW, you should also know your organization's social media policy, because they still apply when you're off the clock or not in class.)
Check your privacy and security settings for ALL of your social media accounts. Tumblr, Twitter, Facebook, LinkedIn, YouTube, AO3, Pillowfort, freaking pornhub. Lock that shit down.
Use a VPN. Put one on your phone and your computers and your tablets.
And trust your gut. If someone is asking you a lot of personal questions, assume they're dangerous. That's not being rude, that's being safe. Auntie Pan says you can and SHOULD leave a situation if you feel uncomfortable.
75 notes
·
View notes
Text
About Frontier Mail Login Details
Frontier mail service was established in 1917. It was one of the very first mail services to be put up from the United States Postal Service (USPS). At that time, there were not many email messages available and it was difficult to send a message to a person abroad. Therefore, email was used to communicate with individuals in various areas of the world. This is still a very effective method of communication today and can be used by many individuals and companies.
When you register for frontier mail, you will be given with a special email address. This is the address that you need in order to receive your mails. You can add other email addresses or perhaps change your email password, if you would like. This allows you to frontier mail login anytime you would like. The fantastic thing is that you can use your email address and password to get any of the reports on the frontier mail network. After you login to these accounts, you will have the ability to get all your past mails, create new mails, send emails and also manage your Google inbox, Yahoo mail and AOL contact list.
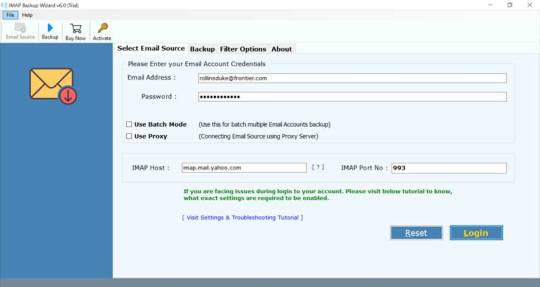
When you sign up, you will be given a free email address, which will be your primary email address on the frontier network. You will also get a free outlook accounts and may use this email address to log in to your frontier account. The email settings that are provided will make it possible for you to pick the color of your email box, your desktop picture, your font size and lots of other essential choices. You will also be given the ability to modify the color schemes of your background, menu bar and taskbar. There are a number of other settings, which will give you more control over how your interface looks.
To get your accounts, you may click “Sign into Frontier Mail". Once you've logged in, you will see a new drop-down menu. With this particular drop-down menu, you may see “Change my Email Address", that's the button for that you will click. Once you click this button, you'll be asked to type your new email address. Your name will be requested, and it's recommended that you do not use your real name. Your email address will be generated according to your registered user name.
Once you have completed this step, your title and your entire email address will be displayed as they're typed on the brand new drop-down menu. Next, you will find a brand new drop-down menu, which now shows “Add ons". Have a look at the accessible add-ons and choose the one that best matches your profile. A pop-up window will show up with two buttons: you will enable you to put in an image and the other will enable you to change your color scheme. To change your color scheme, click the “Edit" tab, where you'll see yellow and red buttons for changing the background color, text colour and font dimensions.
Last but not least, you will be asked to tick"Subscribe to my newsletter" in case you would like to receive the Frontier Mail service. When this checkbox is ticked, your accounts will be marked as active and everything is going to be taken care of automatically. If you've already received the newsletter, be certain you check your inbox to find out if there are any new items. Ensure the subscription has been finished successfully!
1 note
·
View note
Link
Facebook is asking some new users to provide the password to their email account. The move has alarmed security experts, who warn it could encourage users to engage in "risky" behaviour and increase their chances of being hacked. The social network also appears to be accessing these users' contacts without asking for permission. The company now says it is discontinuing this login tool, though it didn't give a timeframe.
Bennett Cyphers, a security researcher with advocacy group the Electronic Frontier Foundation, was harshly critical of Facebook's actions. "This is basically indistinguishable to a phishing attack," he said on a call, pointing out that people are ordinarily urged never to provide their passwords to anyone other than the site they were created from."This is bad on so many levels. It's an absurd overreach by Facebook and a sleazy attempt to trick people to upload data about their contacts to Facebook as the price of signing up. Even when you consent to uploading contact information to Facebook, you should never have to put in your email password to do it," Cyphers wrote in a follow-up email.
The password entry form says that passwords are not stored by Facebook, but there's no way to independently audit this and confirm that it's the case. It was recently revealed that the company was storing hundreds of millions of users' passwords in plain text, in a violation of widely-held security best practices.
308 notes
·
View notes
Text
Security researcher warns of power company customers' passwords being stored in the clear, software provider responds with lawyer-letter

SEDC is an Atlanta-based company that provides back-ends for utility companies; a security researcher discovered that the company stored his password in the clear. The company's products have more than 15,000,000 users, whose logins and passwords are potentially also stored in plaintext. When the researcher alerted the company about this, the company ignored them, then denied that there was any problem, then demanded that the researcher not communicate about this except to SEDC's general counsel.
The responses from SEDC general counsel Mark Cole split hairs over the security implications of storing unencryted passwords, insisting that because this was not prohibited by PCI-DSS, an industry regulation governing storage of customer billing information; and because logging in would not reveal billing information, there was no problem.
The security researcher who discovered the password problem has received assistance from the Electronic Frontier Foundation (disclosure: I am a consultant to EFF).
Cole eventually sent the researcher an email that implied that the company had reformed its password handling, but with a great deal of worrying ambiguity.
Storing passwords in the clear is an industry worst-practice. Because so many people re-use passwords, password breaches are a useful source of data for "credential stuffing" attacks on other sites; if SEDC or its customers suffer a breach, they could unleash millions of passwords that could be used to compromise the users of its services.
https://boingboing.net/2019/02/26/password1234.html
69 notes
·
View notes
Text
Online Work Online Job
If you need to email report on newsletter subscribers or other people who have opted in to receive email offers from you, send them an email telling them about our website, and feel free of charge some text from our homepage in your email. Are young affiliate link at no more the email. You can even use our email samples.
Bitcoin Mining - Bitcoin Lifestyle Login is soon turning ideal popular open source, peer-to-peer currency as a result an undetectable and safe way various other money . The unique thing to fix it method of make money online is basically can in order to dedicate the CPU cycles of your computer or laptop to a Bitcoin client. Encryption problems are assigned to your computer which it requires to solve. On solving every problem you get 50 Bitcoins. Each Bitcoin is the same as $8.60 can make it a fantastic income for each problem sorted out.
youtube
Silk Road had experienced operation since 2011, with grown to some size of 957,000 users transacting an utter of 8.5 million Bitcoins, the equivalent of over Bitcoin Mining $1 thousand. Ulbricht is alleged to have elected more than $20,000 per day from running the domain.
No you are going to sell you this associated with software when he is "such a nice guy" but the reason why i am giving this out is always that for at any time when i need $100 any company create the liberty reserve account,and check out the hassles of opening a fresh email as well as that stuff which is mentally stressful and labor Bitcoin Lifestyles intensive so i taught of selling it in my little blog come up with extra income without opening a new liberty reserve account.
But, this let very good old Edison light bulb flash on the head for a moment, Bitcoin Lifestyle Login bingo, you will realize that we already choose a replacement paper funds. Voila.Plastic money is already with this.Eternal bliss of electronic wizardry to the rescue of closing frontiers of human creation. Wired digital magic you should definitely label thought.
Ulbricht went to great lengths to conceal where his illegal business was based and he went to great lengths to try and FBI from finding out his identity, but ultimately Cryptocurrency it was his "carelessness" that got him seen.
Far easier, numerous and less complex would be ways help to make payments in the modern bill based society. Press a only a few buttons exactly what do you know, your payment by.electronically.now that was quite obvious without having to say it.
1 note
·
View note
Text

Access your Frontier Mail login account with our login process. Gain instant entry to your emails, manage contacts, and organize your communications. Our user-friendly interface ensures a smooth login experience, allowing you to stay connected Explore the convenience of Frontier Mail Login and stay in control of your inbox with ease.
0 notes
Text
Securing Online Privacy
1. Get Signal and additionally WhatsApp for portable messages: Signal is a refined Swiss informing application that completely encodes all your instant messages. It requires the two players to utilize it, so it isn't great for everything. By the by, Moxie Marlinspike, the organizer of Open Whisper Systems, Signal's engineer, says there has been a tremendous extension in their client base since the political decision. So you'll most likely observe more Signalers on your contact list as time goes on.WhatsApp is an elective that scrambles your informing and VoIP calls. It isn't quite so get as Signal since it's possessed by Facebook, whose way to deal with court orders is dubious, yet for standard purposes it will forestall constant checking of your interchanges.
2. Scramble your PC's hard drive: Full plate encryption makes the substance of your PC absolutely muddled to anybody without the secret word. For instance, in case you are halted by Homeland Security upon return to the U.S., your PC can be looked before you authoritatively enter the U.S. Be that as it may, in case it's scrambled, no law says you should disclose the password.Both Apple and Windows PCs have programmed encryption underlying in the event that you initiate it. That is fine for most purposes.hire a hacker for whatsapp
3. Get a secret word supervisor: Using secure applications and utilities like those above implies having passwords - heaps of them. Try not to keep in touch with them on your palm. Get a secret word supervisor that stores them (encoded, obviously) in one spot and creates and even changes passwords for you.Personally, I use Dashlane. Other great secret phrase supervisors are 1Password and KeePass. I don't suggest LastPass, one more famous one, since they permitted themselves to be hacked the year before. That is definitely not adequate.
4. Utilize two-factor verification: Most email programs, distributed storage utilities, banking applications, online media and other delicate applications nowadays offer two-factor confirmation (TFA). TFA necessitates that each time you sign in, you go through an optional layer of safety: a code to enter at login that is shipped off your telephone by means of instant message. Some deal such codes through email, however don't utilize it. If programmers get close enough to your email, they can gain admittance to your records by having TFA codes shipped off them.
5. Use HTTPS Everywhere: My companions at the Electronic Frontier Foundation fostered a program module for Firefox and Chrome that powers sites you visit to utilize the most solid association convention. In case encryption is accessible on the site you visit, your association with the site will be scrambled, and you will be shielded from different types of observation and hacking during that meeting.
0 notes
Text
Fwd: Conference: Minnesota_TwinCities.AmericanSocMammalogists.Jun24-28
Begin forwarded message: > From: [email protected] > Subject: Conference: Minnesota_TwinCities.AmericanSocMammalogists.Jun24-28 > Date: 22 March 2016 at 07:29:10 GMT > To: [email protected] > > > Ninety-sixth meeting of the > AMERICAN SOCIETY OF MAMMALOGISTS > 24-28 June 2016 > University of Minnesota Twin Cities > > We have an exciting meeting planned for this year! The scientific program > will include simultaneous technical sessions, poster sessions, as well as > workshops, symposia, and plenary speakers. A full social agenda is planned > with field trips, picnic, Run-for-Research, student pizza party, auction, > and awards ceremony and social. > > SAVE MONEY AND REGISTER NOW!!! > Registration is now open for ASM 2016! Register online > (https://ift.tt/2Yw15HK > .ksu.edu/etrakWebApp/Registration.aspx?MeetingCode!1604) now! Please > keep in mind that your login password for conference registration is > different than your society password used to access the ASM Business > Office site. If you do not remember your password from previous years, > simply select ģretrieve your forgotten passwordē and it will be sent to > your e-mail quickly. Regular registration ends March 31st!!! > > ABSTRACT SUBMISSION DEADLINE MARCH 31ST AT 5 PM (CDT)!!! > Share your research with hundreds of mammalogists from around the world. > Submit your abstract for an oral presentation or poster for ASM 2016! > Abstract submissions will close on March 31, 2016 at 5:00 pm (Central > Daylight Time). > > All presenters must register and submit full payment for the conference > prior to submitting their abstract. This MUST be done prior to 5:00 pm > (Central Daylight Time) on March 31st to ensure timely processing. After > registering for the conference, you will receive two auto reply > confirmation receipts. After verifying your registration, you will receive > a separate confirmation letter that will contain information about how to > submit an abstract. An abstract will not be accepted for the program until > the presenting author has registered and paid in full. > > NEW THIS YEAR! Oral presenters interested in participating in a solicited > Thematic Session can indicate such during abstract submission. These > sessions are intended to highlight research in new and important areas. > Thematic Sessions will occur alongside regular technical sessions but may > use alternative formatting as necessary (e.g., 30-minute talks). Session > topics this year include Climate Change and High-Latitude Mammals, > Microbiome of Non-Model Organisms, Phylogenomics, and 5-Minute Lightning > Talks. Abstracts will be vetted and selected for each Thematic Session by > the Program Committee. Please contact John Hanson > ([email protected]) for more information! > > RESERVE YOUR ROOM AND MAKE TRAVEL PLANS FOR ASM 2016 > Housing: A variety of housing options are available this year, including > campus dorm housing. Reservations should be made before the end of May for > most housing options. Be sure to reference the American Society of > Mammalogists to receive the conference group rate at the meeting hotels. > Check out the meeting travel page > (https://ift.tt/3BTiYP3) for more > information! > > Transportation: Airlines servicing Minneapolis-St. Paul International > Airport (https://ift.tt/3BWEouI) include American, Delta, Frontier, > Spirit, United, and Southwest. The airport also offers various car rental > options. There are several options for travel from the airport to the > hotels ranging from taxis and shuttles to public transportation. To > research the method that best suits you, please see the options online > (https://ift.tt/2Vq0iqC). Minneapolis is > also serviced by Greyhound (https://ift.tt/3z1jmsV) and Amtrak > (https://ift.tt/3DZyH14). > > For more information, visit the meeting website > (https://ift.tt/3BZ8GNF). > > > Contact: > Tony Ballard > K-State Conference Services > Phone: 785-532-2402 > Email: [email protected] > > > > Cody Thompson >
via IFTTT
0 notes
Text
Private Intel Firm Buys Location Data to Track People to their ‘Doorstep’
A threat intelligence firm called HYAS, a private company that tries to prevent or investigates hacks against its clients, is buying location data harvested from ordinary apps installed on peoples' phones around the world, and using it to unmask hackers. The company is a business, not a law enforcement agency, and claims to be able to track people to their "doorstep."
The news highlights the complex supply chain and sale of location data, traveling from apps whose users are in some cases unaware that the software is selling their location, through to data brokers, and finally to end clients who use the data itself. The news also shows that while some location firms repeatedly reassure the public that their data is focused on the high level, aggregated, pseudonymous tracking of groups of people, some companies do buy and use location data from a largely unregulated market explicitly for the purpose of identifying specific individuals.
HYAS' location data comes from X-Mode, a company that started with an app named "Drunk Mode," designed to prevent college students from making drunk phone calls and has since pivoted to selling user data from a wide swath of apps. Apps that mention X-Mode in their privacy policies include Perfect365, a beauty app, and other innocuous looking apps such as an MP3 file converter.
"As a TI [threat intelligence] tool it's incredible, but ethically it stinks," a source in the threat intelligence industry who received a demo of HYAS' product told Motherboard. Motherboard granted the source anonymity as they weren't authorized by their company to speak to the press.
Do you work at a location SDK company? Did you used to? Do you know anything else about the sale of location data? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on [email protected], or email [email protected].
HYAS puts a particular emphasis on identifying the people behind attacks, or "attributing" them, although the actual effectiveness of its products is unclear and may be exaggerated by the firm in marketing material.
"We track threat actors and other bad guys down to their physical doorstep for customers and clients," the LinkedIn profile for HYAS CEO David Ratner reads. HYAS' "Insight" product provides clients with a Google Maps-style interface to interact with the company's datasets, according to HYAS' website. Insight provides access to the firm's "exclusive data sources" and "non-traditional collection mechanisms," the website reads.
A wide range of industries often buy location data to track the movements of crowds of people. Retailers can source the data to see how much foot traffic their store, or maybe one of their competitors, is getting. Real estate companies could use the information to see if a piece of land has the potential to be popular. Marketing firms use location data to identify and target groups with specific commercial or political adverts.
HYAS differs in that it provides a concrete example of a company deliberately sourcing mobile phone location data with the intention of identifying and pinpointing particular people and providing that service to its own clients. Independently of Motherboard, the office of Senator Ron Wyden, which has been investigating the location data market, also discovered HYAS was using mobile location data. A Wyden aide said they had spoken with HYAS about the use of the data. HYAS said the mobile location data is used to unmask people who may be using a Virtual Private Network (VPN) to hide their identity, according to the Wyden aide.
In a webinar uploaded to HYAS' website, Todd Thiemann, VP of marketing at the company, describes how HYAS used location data to track a suspected hacker.
"We found out it was the city of Abuja, and on a city block in an apartment building that you can see down there below," he says during the webinar. "We found the command and control domain used for the compromised employees, and used this threat actor's login into the registrar, along with our geolocation granular mobile data to confirm right down to his house. We also got his first and last name, and verified his cellphone with a Nigerian mobile operator."

A screenshot of a webinar given by HYAS, in which the company explains how it has used mobile application location data.
On its website, HYAS claims to have some Fortune 25 companies, large tech firms, as well as law enforcement and intelligence agencies as clients.
Threat intelligence firms generally gather data from a wide range of sources, including hacker forums, private chat rooms, and internet infrastructure such as where websites are hosted, and sell products based on that data and their own analysis to clients. Customers can include banks who want to get a heads-up on whether a freshly dumped cache of stolen credit card data belongs to them; a retailer trying to protect themselves from hackers; or a business checking if any of their employees' login details are being traded by cybercriminals.
Some threat intelligence companies also sell services to government agencies, including the FBI, DHS, and Secret Service. The Department of Justice oftens acknowledges the work of particular threat intelligence companies in the department's announcement of charges or indictments against hackers and other types of criminals.
But some other members of the threat intelligence industry criticized HYAS' use of mobile app location data. The CEO of another threat intelligence firm told Motherboard that their company does not use the same sort of information that HYAS does.
The threat intelligence source who originally alerted Motherboard to HYAS recalled "being super shook at how they collected it," referring to the location data.
A senior employee of a third threat intelligence firm said that location data is not hard to buy.
"As a TI [threat intelligence] tool it's incredible, but ethically it stinks."
A blog post on HYAS' website said that "HYAS Insight 1.1 provides telemetry gleaned from advertising and mobile application location data."
When Motherboard emailed HYAS, it removed the mention of advertising and mobile application location data from its blog post. The blog post added that the Insight product also lets customers determine what other devices or wireless networks are near a device. The post now reads that HYAS "provides precise geolocation telemetry."
"HYAS is in the business of supporting our clients in cyber-criminal investigations. Our business is focused on helping our clients detect and prevent cyber crime," Ratner told Motherboard in an email. The company did not reply when asked why it removed the mention of mobile application location data from its website.
Motherboard found several location data companies that list HYAS in their privacy policies. One of those is X-Mode, a company that plants its own code into ordinary smartphone apps to then harvest location information. An X-Mode spokesperson told Motherboard in an email that the company's data collecting code, or software development kit (SDK), is in over 400 apps and gathers information on 60 million global monthly users on average. X-Mode also develops some of its own apps which use location data, including parental monitoring app PlanC and fitness tracker Burn App.
"Whatever your need, the XDK Visualizer is here to show you that our signature SDK is too legit to quit (literally, it’s always on)," the description for another of X-Code's own apps, which visualizes the company's data collection to attract clients, reads.
"They’re like many location trackers but seem more aggressive to be honest," Will Strafach, founder of the app Guardian, which alerts users to other apps accessing their location data, told Motherboard in an online chat. In January, X-Mode acquired the assets of Location Sciences, another location firm, expanding X-Mode's dataset.
"My bet is that they bet on folks clicking through things without reading the text," Strafach said of app users not necessarily being aware of X-Mode collecting their location data.

A screenshot of the Drunk Mode app available on the Apple App Store.
Motherboard then identified a number of apps whose own privacy policies mention X-Mode. They included Perfect365, a beauty-focused app that people can use to virtually try on different types of makeup with their device's camera.
"I don’t know if my information was used anywhere," Marta, one Perfect365 user, told Motherboard. Marta provided a screenshot of her app settings, showing Perfect365 could access her device’s location.
Gianna, another user, said "[It] bothers me the fact that it asks me for my current location!," she added.
Perfect365's CEO Sean Mao did not respond to a request for comment.
Eva Galperin, director of cybersecurity at activist group the Electronic Frontier Foundation (EFF) told Motherboard that even if a user is presented with some form of consent notice, they may not tangibly understand or know what is happening to their data.
"And that's assuming people even read privacy notices, which they normally don't," she said.
An X-Mode spokesperson told Motherboard in an email that "app users must provide informed consent before their location is tracked," and that the company follows guidelines from the GDPR, CCPA, and other data protection regulation. Users can also opt-out of collection via the company's own app, the email added.
The X-Mode spokesperson added that "Our clients use this data to observe groups of individuals in the aggregate and pseudonymously. X-Mode actively uses two data anonymization techniques—pseudonymization and generalization. We obfuscate any user IDs we collect from all devices and we aggregate devices using generalization. Our clients use these techniques and others to identify trends that are difficult to observe at the individual level, such as trends in mobility."
This stands in stark contrast to what HYAS says it is actually trying to do with that data, however. When pressed on HYAS' deployment of mobile location data to find specific people, X-Mode said "We take our obligations of confidentiality with our clients seriously, and we can't discuss the details of specific clients. I am sure you are aware however that companies such as the one you mentioned use multiple data sources. As we stated, and to reiterate, we contractually prohibit misuses of X-Mode data such as using X-Mode data solely to re-identify individuals."
"The data we obtain is used for these purposes in compliance with all applicable law," Ratner, HYAS' CEO, added.
"Shady data brokers are scooping up databases of private information to create dossiers on individual Americans, without our consent or knowledge," Senator Ron Wyden told Motherboard in a statement. "These databases create enormous risks to our personal safety, privacy and U.S. national security if they fall into the wrong hands. I wrote the Mind Your Own Business Act to crack down on these unsavory practices and put Americans back in control of their own personal information."
Various government agencies have bought access to location data from other companies. Last month, Motherboard found that U.S. Customs and Border Protection (CBP) paid $476,000 to a firm that sells phone location data. CBP has used the data to scan parts of the U.S. border, and the Internal Revenue Service (IRS) tried to use the same data to track criminal suspects but was unsuccessful.
The first threat intelligence source added, describing HYAS' use of mobile location data, "It's shady as fuck."
Private Intel Firm Buys Location Data to Track People to their ‘Doorstep’ syndicated from https://triviaqaweb.wordpress.com/feed/
0 notes