#Email Encryption Market By Key Manufacturers
Text
North America Aerospace and Defense Telemetry Market: Navigating Key Drivers and Challenges (2024-2032)

The North American aerospace and defense telemetry market is poised for significant growth and innovation from 2024 to 2032. Telemetry, the transmission of data from remote sources, plays a crucial role in this sector, facilitating real-time monitoring and control of aircraft, missiles, satellites, and other critical systems.
Key Drivers:
Technological Advancements: Advancements in telemetry technology, such as miniaturization, improved data transmission rates, and enhanced encryption protocols, are driving North America Aerospace and Defense Telemetry Market growth. These innovations enable more accurate data collection and analysis, enhancing the overall performance and safety of aerospace and defense systems.
Increasing Demand for Unmanned Systems: The growing demand for unmanned aerial vehicles (UAVs) and autonomous systems is fueling the adoption of telemetry solutions. These systems require robust telemetry infrastructure to ensure reliable communication and control, driving market expansion.
Rising Security Concerns: Heightened security threats and geopolitical tensions are prompting governments to invest in advanced telemetry systems for defense applications. The need for secure data transmission and protection against cyber threats is driving market growth in the defense sector.
Request Free Sample Report - Receive a free sample report to preview the valuable insights and data we offer.
Challenges:
Regulatory Compliance: Stringent regulatory requirements, particularly in the defense sector, pose challenges for telemetry system developers and manufacturers. Compliance with industry standards and government regulations adds complexity and may impact time-to-market and cost considerations.
Integration Complexities: Integrating telemetry systems with existing aerospace and defense platforms can be complex and time-consuming. Compatibility issues, interoperability challenges, and the need for seamless integration with legacy systems present significant hurdles for market players.
Cost Pressures: Cost pressures remain a concern for stakeholders in the aerospace and defense telemetry market. Developing and deploying advanced telemetry solutions involves substantial investments in research, development, and infrastructure, which can impact profit margins and market competitiveness.
Overall, while the North American aerospace and defense telemetry market offers immense growth opportunities, addressing key challenges will be essential for stakeholders to capitalize on emerging trends and drive sustainable growth in the coming years.
About US
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services. MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions. To stay updated with technology and work process of the industry, MRFR often plans & conducts meet with the industry experts and industrial visits for its research analyst members.
Contact us:
Market Research Future (part of Wants tats Research and Media Private Limited),
99 Hudson Street,5Th Floor, New York, New York 10013, United States of America
Sales: +1 628 258 0071 (US) +44 2035 002 764 (UK)
Email: [email protected]
0 notes
Text
Global top 24 companies accounted for 48% of Network Encryption market(qyresearch, 2021)
Network encryption is the process of encrypting or encoding data and messages transmitted or communicated over a computer network.
It is a broad process that includes various tools, techniques and standards to ensure that the messages are unreadable when in transit between two or more network nodes.
Network encryption is primarily implemented on the network layer of the OSI model. Network encryption implements one or more encryption algorithms, processes and standards to encrypt the data/message/packet sent over the network. The encryption services are generally provided by encryption software or through an integrated encryption algorithm on network devices and/or in software.
On an IP-based network, network encryption is implemented through Internet Protocol Security (IPSec) -based encryption techniques and standards. Each message sent is in an encrypted form and is decrypted and converted back into plain text/original form at the recipient's end using encryption/decryption keys.
According to the new market research report “Global Network Encryption Market Report 2023-2029”, published by QYResearch, the global Network Encryption market size is projected to reach USD 7.95 billion by 2029, at a CAGR of 11.1% during the forecast period.
Figure. Global Network Encryption Market Size (US$ Mn), 2018-2029
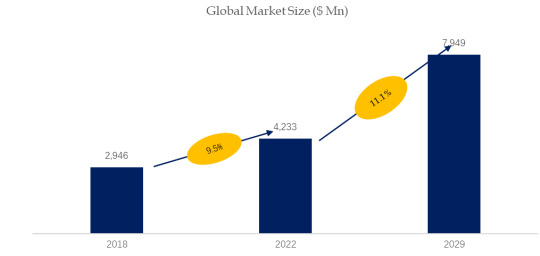
Figure. Global Network Encryption Top 24 Players Ranking and Market Share(Based on data of 2021, Continually updated)
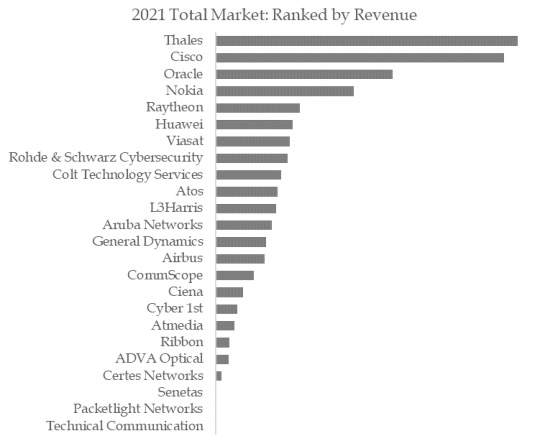
The global key manufacturers of Network Encryption include Technical Communication, Packetlight Networks, Senetas, Certes Networks, ADVA Optical, Ribbon, Atmedia, Cyber 1st, Colt Technology Services, Atos, etc. In 2021, the global top five players had a share approximately 48.0% in terms of revenue.
About QYResearch
QYResearch founded in California, USA in 2007.It is a leading global market research and consulting company. With over 16 years’ experience and professional research team in various cities over the world QY Research focuses on management consulting, database and seminar services, IPO consulting, industry chain research and customized research to help our clients in providing non-linear revenue model and make them successful. We are globally recognized for our expansive portfolio of services, good corporate citizenship, and our strong commitment to sustainability. Up to now, we have cooperated with more than 60,000 clients across five continents. Let’s work closely with you and build a bold and better future.
QYResearch is a world-renowned large-scale consulting company. The industry covers various high-tech industry chain market segments, spanning the semiconductor industry chain (semiconductor equipment and parts, semiconductor materials, ICs, Foundry, packaging and testing, discrete devices, sensors, optoelectronic devices), photovoltaic industry chain (equipment, cells, modules, auxiliary material brackets, inverters, power station terminals), new energy automobile industry chain (batteries and materials, auto parts, batteries, motors, electronic control, automotive semiconductors, etc.), communication industry chain (communication system equipment, terminal equipment, electronic components, RF front-end, optical modules, 4G/5G/6G, broadband, IoT, digital economy, AI), advanced materials industry Chain (metal materials, polymer materials, ceramic materials, nano materials, etc.), machinery manufacturing industry chain (CNC machine tools, construction machinery, electrical machinery, 3C automation, industrial robots, lasers, industrial control, drones), food, beverages and pharmaceuticals, medical equipment, agriculture, etc.
For more information, please contact the following e-mail address:
Email: [email protected]
Website: https://www.qyresearch.com
0 notes
Text
Fingerprint Sensor Market Expected to Reach $9.41 Billion, Globally, by 2027 at 14.5% CAGR: Allied Market Research
the fingerprint sensor market size is expected to witness considerable growth, owing to rise in adoption of automation and wireless connectivity in the industry. The fingerprint sensor industry is projected to witness significant growth, especially in emerging economies such as Asia-Pacific and LAMEA, owing to development of smart technologies in these regions.
Wilmington, Delaware
According to a recent report published by Allied Market Research, titled, “Fingerprint Sensor Market By Type and End Use: Opportunity Analysis and Industry Forecast, 2020–2027”, the global fingerprint sensor market size was valued at $2.93 billion in 2019, and is projected to reach $9.41 billion by 2027, registering a CAGR of 14.5% from 2020 to 2027.
Download Research Report Sample & TOC:
https://www.alliedmarketresearch.com/request-sample/6649
(We look forward to moving quickly to provide the Report Analysis needed for your Business Success)
•99 – Tables
•66 – Charts
•212 – Pages
Optical fingerprint sensor provide authenticated user with fast, secure, and easy access to personal contact details, emails, payment information, location data, and other types of encrypted data. Sensors for fingerprints allow fast record keeping and control of portals for attendance. Compared with other biometric authentication systems, they are less costly. These factors further increase growth of the fingerprint sensor market size.
Prime determinants of growth:
Notable factors positively affecting the fingerprint sensor market include extensive use of fingerprint sensors for biometric authentication in consumer electronics, increase in adoption of biometric authentication in government buildings, rise in number of identity threats, and emergence of touch less fingerprint technology. However, security threats pertaining to biometric database and high cost associated with biometric technologies hampers growth of the market. Furthermore, emerging trends towards IoT based biometric technology and rise in trends towards in-Display fingerprint sensors in Smartphones are expected to offer lucrative opportunities for the market growth in the coming years.
Report Coverage and Details:
Aspects
Details
By Type
FAP 10
FAP 20
FAP 30
By End Use
Banking & Finance
Government & Law Enforcement
Commercial
Others
COVID-19 Scenario:
The COVID-19 pandemic is impacting the society and overall economy across the global. The impact of this outbreak is growing day-by-day as well as affecting the supply chain. It is creating uncertainty in the stock market, falling business confidence, massive slowing of supply chain, and increasing panic among customers. European countries under lockdowns have suffered a major loss of business and revenue due to shutdown of manufacturing units in the region. Operations of production and manufacturing industries have been heavily impacted by the outbreak of the COVID-19 disease; which has led to slowdown in growth of the fingerprint sensor market in 2020.
Fingerprint sensors provide authenticated user with fast, secure, and easy access to personal contact details, emails, payment information, location data, and other types of encrypted data. Sensors for fingerprints allow fast record keeping and control of portals for attendance. Compared with other biometric authentication systems, they are less costly. Hence, such factors increase growth of the fingerprint sensor market size.
Inquiry Before Buying:
https://www.alliedmarketresearch.com/purchase-enquiry/6649
Leading Market Players:
SYNAPTICS INCORPORATED,
THALES,
HID GLOBAL CORPORATION,
APPLE INC,
3M COGENT INC,
SECUGEN CORPORATION,
PRECISE BIOMETRICS,
CROSSMATCH,
IDEMIA,
EGIS TECHNOLOGY INC
The report provides a detailed analysis of these key players of the global fingerprint sensor market. These players have adopted different strategies such as product development and product launch to increase their market share and maintain dominant shares in different regions. The report is valuable in highlighting business performance, operating segments, product portfolio, and strategic moves of market players to showcase the competitive scenario.
Key Benefits for Stakeholders:
By type, the FAP 10 segment generated the highest revenue in the fingerprint sensor market forecast in 2019.
By end use, the government & law enforcement segment generated the highest revenue in the fingerprint sensor market analysis in 2019.
By region, the Asia-Pacific segment generated the highest revenue in the fingerprint sensor market forecast in 2019.
By Region:
North America (U.S., Canada, and Mexico)
Europe (U.K., Germany, France, Italy, Spain, Russia, Netherlands, Belgium, Poland, and Rest of Europe)
Asia-Pacific (China, Japan, India, South Korea, Australia, Malaysia, Thailand, Philippines, Indonesia, and Rest of Asia-Pacific)
LAMEA (Latin America, Middle East and Africa)
Trending Reports in Semiconductor and Electronics Industry (Book Now with Up to 20% Discount + COVID-19 Scenario):
Antenna Market size is projected to reach $40.1 billion by 2032, growing at a CAGR of 9.1% from 2023 to 2032.
Image Sensor Market size is projected to reach $87.5 billion by 2032, growing at a CAGR of 12.9% from 2023 to 2032.
Superconductors Market share is projected to reach $17.4 billion by 2032, growing at a CAGR of 10% from 2023 to 2032.
Power Cable Market size is projected to reach $277.8 billion by 2031, growing at a CAGR of 6.4% from 2022 to 2031
Embedded Systems Market size is projected to reach $163.2 billion by 2031, growing at a CAGR of 6.5% from 2022 to 2031.
About Us:
Allied Market Research (AMR) is a full-service market research and business-consulting wing of Allied Analytics LLP based in Wilmington, Delaware. Allied Market Research provides global enterprises as well as medium and small businesses with unmatched quality of "Market Research Reports Insights" and "Business Intelligence Solutions." AMR has a targeted view to provide business insights and consulting to assist its clients to make strategic business decisions and achieve sustainable growth in their respective market domain.
We are in professional corporate relations with various companies and this helps us in digging out market data that helps us generate accurate research data tables and confirms utmost accuracy in our market forecasting. Allied Market Research CEO Pawan Kumar is instrumental in inspiring and encouraging everyone associated with the company to maintain high quality of data and help clients in every way possible to achieve success. Each and every data presented in the reports published by us is extracted through primary interviews with top officials from leading companies of domain concerned. Our secondary data procurement methodology includes deep online and offline research and discussion with knowledgeable professionals and analysts in the industry.
Contact:
David Correa
1209 Orange Street,
Corporation Trust Center,
Wilmington, New Castle,
Delaware 19801 USA.
Int'l: +1-503-894-6022
Toll Free: +1-800-792-5285
UK: +44-845-528-1300
India (Pune): +91-20-66346060
Fax: +1-800-792-5285
[email protected]
0 notes
Text
Unleashing Productivity: The Pivotal Role of Google Workspace

In today’s business context, when collaboration and efficiency are critical, the use of modern tools is not a choice but a strategic need. Google Workspace, a full suite of cloud-based services, has emerged as a key player in revolutionizing how businesses work, interact, and innovate. As we manage the intricacies of today’s workplace, the importance of Google Workspace in promoting productivity becomes clear.
An Integrated Ecosystem for Efficient Collaboration:
One of Google Workspace’s most notable characteristics is its ability to build a single ecosystem that smoothly integrates numerous productivity applications. The synergy among these services provides a collaborative atmosphere that exceeds the boundaries of typical office settings, from Gmail to Google Drive, Docs, Sheets, Slides, and more. This oneness allows teams to work together more effectively, breaking down boundaries and allowing for a more fluid interchange of ideas.
Collaborative Workspaces:
Gmail, a strong email platform with an intuitive layout, powerful search tools, and advanced filtering options, is included in Google Workspace. It simplifies virtual meetings, as well as asynchronous and real-time communication. Google Drive, a cloud-based storage service for documents, spreadsheets, and presentations, improves data management and eliminates version control issues. With Docs, Sheets, and Slides, Google Workspace emphasizes real-time collaboration, allowing several users to collaborate on documents at the same time, avoiding the delays and uncertainty associated with traditional file-sharing techniques. This functionality is very valuable for teams who collaborate across borders.
Efficient Project Management with Accessibility and Security:
With Google Calendar and Tasks, Google Workspace expands its capabilities into project management. Calendar keeps teams on track with schedules and deadlines, promoting a common knowledge of project schedules. Tasks, on the other hand, streamline to-do lists and progress tracking, supporting an organized and productive workflow.
Google Workspace prioritizes both security and accessibility in an era where data security is non-negotiable. Two-factor authentication, data encryption, and other advanced security features protect sensitive data. Simultaneously, the suite’s cloud-based structure ensures that users may access their work whenever and wherever they want, enabling a flexible and adaptive work environment.
Increasing Productivity in All Areas:
Google Workspace’s significance in increasing productivity extends beyond the limitations of traditional office arrangements. It is a driving force for creativity, a promoter of collaboration, and a defender of data integrity. As organizations throughout the world rethink their work paradigms, Google Workspace stands as a versatile and necessary ally, giving the tools required to prosper in today’s dynamic business landscape. Accept the power of Google Workspace and see your organization’s productivity skyrocket. The future of work has arrived, and it is fuelled by collaboration, efficiency, and Google Workspace’s seamless integration.
Conclusion:
Businesses that embrace Google Workspace are better able to boost productivity, remain ahead of the curve, and ultimately achieve their goals in today’s competitive landscape. Google Workspace is a dependable and important ally in the pursuit of better efficiency and productivity as the digital world evolves. Remember that in the business world, productivity is everything, and Google Workspace is the winning move.
So, whether you work in education, healthcare, manufacturing, marketing, retail, or another industry, think about implementing Google Workspace to empower your team and push your organization to better productivity and success. Google Workspace’s power is at your fingertips; make use of it immediately.
Read our article Google Workspace Automation: Your Key to Business Transformation to get an in-depth idea of various automation possibilities.
Are you curious about Google Workspace’s possibilities in your industry? Venturesathi provides customized automation solutions to increase productivity and efficiency. Explore our services to see how we might help you in your field.
0 notes
Text
Key Management as a Service Market is set for a Potential Growth Worldwide
Global Key Management as a Service Market Report from AMA Research highlights deep analysis on market characteristics, sizing, estimates and growth by segmentation, regional breakdowns & country along with competitive landscape, player’s market shares, and strategies that are key in the market. The exploration provides a 360° view and insights, highlighting major outcomes of the industry. These insights help the business decision-makers to formulate better business plans and make informed decisions to improved profitability. In addition, the study helps venture or private players in understanding the companies in more detail to make better informed decisions.
Major Players in This Report Include,
CipherCloud (United States), Gemalto (Netherlands), Google (United States), IBM (United States), Oracle Corporation (United States), Microsoft Corporation (United States), Thales e-Security (France), Amazon Web Services, Inc. (United States), Hewlett Packard Enterprise Development LP (United States), Box (United States).
Free Sample Report + All Related Graphs & Charts @: https://www.advancemarketanalytics.com/sample-report/67289-global--key-management-as-a-service-market
Key management as service is the process of management of cryptographic keys in cryptosystem. This service includes key generation, exchange, store and replacement. There are various applications of key management such as communication encryption database encryption, disk encryption, file/folder encryption and cloud encryption. Cryptosystem process is done by three algorithm such as key generation, encryption and decryption. Fueling demand of cloud in key management as Service will help to boost global key management service market.
Market Drivers
Fueling Demand of Cloud in Key Management as Service
Rising Dependency of Data Encryption by the Organizations
Market Trend
Increasing Availability of Encryption Keys
Organizations’ Increasing Focus on Improving Operational Efficiency
Opportunities
Rising Demand in BFSI Industries
Challenges
Lack of Skilled Professionals in Companies
Enquire for customization in Report @: https://www.advancemarketanalytics.com/enquiry-before-buy/67289-global--key-management-as-a-service-market
In this research study, the prime factors that are impelling the growth of the Global Key Management as a Service market report have been studied thoroughly in a bid to estimate the overall value and the size of this market by the end of the forecast period. The impact of the driving forces, limitations, challenges, and opportunities has been examined extensively. The key trends that manage the interest of the customers have also been interpreted accurately for the benefit of the readers.
The Key Management as a Service market study is being classified by Application (Communication Encryption (Voice Encryption, Instant Messaging Encryption, Email Encryption), Database Encryption (Database-Level Encryption, Application-Level Encryption), Disk Encryption, File/Folder Encryption, Cloud Encryption), Component (Solution, Services), End User (Healthcare & Lifesciences, Banking, Financial Services & Insurance (BFSI), Government, Aerospace & Defense, Consumer Goods & Retail, Telecom & IT, Manufacturing, Energy & Utilities, Others)
The report concludes with in-depth details on the business operations and financial structure of leading vendors in the Global Key Management as a Service market report, Overview of Key trends in the past and present are in reports that are reported to be beneficial for companies looking for venture businesses in this market. Information about the various marketing channels and well-known distributors in this market was also provided here. This study serves as a rich guide for established players and new players in this market.
Get Reasonable Discount on This Premium Report @ https://www.advancemarketanalytics.com/request-discount/67289-global--key-management-as-a-service-market
Extracts from Table of Contents
Key Management as a Service Market Research Report
Chapter 1 Key Management as a Service Market Overview
Chapter 2 Global Economic Impact on Industry
Chapter 3 Global Market Competition by Manufacturers
Chapter 4 Global Revenue (Value, Volume*) by Region
Chapter 5 Global Supplies (Production), Consumption, Export, Import by Regions
Chapter 6 Global Revenue (Value, Volume*), Price* Trend by Type
Chapter 7 Global Market Analysis by Application
………………….continued
This report also analyzes the regulatory framework of the Global Markets Key Management as a Service Market Report to inform stakeholders about the various norms, regulations, this can have an impact. It also collects in-depth information from the detailed primary and secondary research techniques analyzed using the most efficient analysis tools. Based on the statistics gained from this systematic study, market research provides estimates for market participants and readers.
Contact US :
Craig Francis (PR & Marketing Manager)
AMA Research & Media LLP
Unit No. 429, Parsonage Road Edison, NJ
New Jersey USA – 08837
Phone: +1 201 565 3262, +44 161 818 8166
[email protected]
0 notes
Text
Europe Homomorphic Encryption Market Size, Status, Demand and Growth Forecast 2019–2027
The Europe Homomorphic Encryption Market report is the most important research for those who look for all information about the market. The report covers all information about the regional markets, including historical and future trends for market dominance, size, trades, supply, competitors, and prices, as well as key vendor information across all the regions. Forecast market information, SWOT analysis, Europe Homomorphic Encryption market scenario, and feasibility study are important aspects of this report.
Get a sample copy of this report:
https://www.businessmarketinsights.com/sample/TIPRE00018163
Europe Homomorphic Encryption includes Market Analysis Report on Top Companies:
· Cosmian
· CryptoExperts SAS
· Google LLC
· IBM Corporation
· Inpher, Inc.
· Microsoft Corporation
· Netskope, Inc.
· Thales Group
· ZAMA
Europe Homomorphic Encryption Market Split by Product Type and Applications:
This report segments the Europe Homomorphic Encryption Market on the basis of Types are:
· Partially
· Somewhat
· Fully
On the basis of Application, the Europe Homomorphic Encryption Market is segmented into:
· BFSI
· Healthcare
· Government
· Other
Regional Analysis of Europe Homomorphic Encryption Market:
This section of the report identifies various key manufacturers in the market. It helps the reader understand the strategies and collaborations that players are focusing on combatting competition in the market. The comprehensive report provides a significant microscopic look at the market. The reader can identify the footprints of the manufacturers by knowing about the regional revenue of manufacturers, during the forecast period.
Directly Buy a Copy of this Europe Homomorphic Encryption Market Research Report at:
https://www.businessmarketinsights.com/buy/single/TIPRE00018163
Significant Features that are under Offering and Europe Homomorphic Encryption Market Highlights of the Reports:
– Detailed overview of the Europe Homomorphic Encryption Market
– Changes in industry market dynamics
– Detailed market segmentation by type, application, etc.
– Historical, current, and projected market size in terms of quantity and value
– Recent industry trends and developments
– Competition situation in Europe Homomorphic Encryption Market
– Key companies and product strategies
– Potential niche segment/region showing promising growth.
Finally, the Europe Homomorphic Encryption Market Report is the authoritative source for market research that can dramatically accelerate your business. The report shows economic conditions such as major locales, item values, profits, limits, generation, supply, requirements, market development rates, and numbers.
NOTE: Our team is studying Covid-19 and its impact on various industry verticals and wherever required we will be considering Covid-19 analysis of markets and industries. Cordially get in touch for more details.
About Us:
Business Market Insights is a market research platform that provides subscription services for industry and company reports. Our research team have extensive professional expertise in domains such as Electronics & Semiconductor; Aerospace & Defense; Automotive & Transportation; Energy & Power; Healthcare; Manufacturing & Construction; Food & Beverages; Chemicals & Materials; and Technology, Media, & Telecommunications.
Contact us:
If you have any questions about this report or would like further information, please contact us:
Contact person: Sameer Joshi
Phone: +16467917070
Email: [email protected]
0 notes
Text
Mobile Encryption Industry Current Trends and Challenges Analysis by 2023-2030

The Mobile Encryption Market refers to the market for products and services that offer encryption and data protection solutions for mobile devices such as smartphones, tablets, and laptops. Mobile encryption helps to secure sensitive data and prevent unauthorized access, ensuring the privacy and security of users’ data.
For Sample Report Click Here:-https://www.globmarketreports.com/request-sample/66080
The market for mobile encryption is driven by increasing concerns about data security, as well as the growing use of mobile devices for work-related tasks. The rise in cyber-attacks and data breaches has also increased the demand for mobile encryption solutions. Additionally, the increasing adoption of bring-your-own-device (BYOD) policies in enterprises is expected to drive the growth of the mobile encryption market.
Mobile encryption refers to the process of securing data and communications on mobile devices using encryption techniques. Encryption is the process of converting plain text or data into a coded format that can only be deciphered by authorized parties with the appropriate key or password.
Mobile encryption can be applied to various types of data, including text messages, emails, files, and voice calls. Encryption can help protect sensitive data from unauthorized access or interception, especially when transmitting data over public networks.
There are several encryption techniques used in mobile encryption, including symmetric encryption and asymmetric encryption. In symmetric encryption, a single key is used to encrypt and decrypt data, while in asymmetric encryption, two keys (public and private) are used.
Mobile encryption solutions are offered by a range of companies, including software providers, device manufacturers, and security vendors. Some popular mobile encryption solutions include Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols for data encryption during transmission, and encryption software for data stored on the device.
The mobile encryption market is expected to continue growing in the coming years, as the use of mobile devices continues to increase and data security becomes an even more pressing concern.
0 notes
Text
Encryption Software Market Share, Competitive Landscape, Size Estimation, And Forecast 2028
Encryption Software Market research report provides comprehensive information on the market. It also includes in-depth information about Market #Drivers, Opportunities, Market Restraints, Market Growth #Challenges and Cumulative #Growth Analysis. Moreover, the report also provides an in-depth analysis of the Encryption Software Market by identifying key players. The report also examines the #competitive landscape of the #Encryption Software Market industry and analyses its impact on the growth of this market over the next few years. The segmental analysis focuses on revenue and forecast for the period 2019-2028.
Request PDF Sample Copy of Report @ https://www.axiommrc.com/request-for-sample/10572-encryption-software-market-report
Encryption software is software that uses cryptography to prevent unauthorized access to digital information. Cryptography is used to protect digital information on computers as well as the digital information that is sent to other computers over the Internet.
The competitive landscape analysis of the Encryption Software market is primarily focused on expanding the growth of the Encryption Software market with new return type innovation, business expansion, and the increasing presence of a range of manufacturers operating in the reverse logistics market has led to growing demand for the market.
Market Key Players
IBM (US)
Microsoft (US)
Symantec (US)
Thales e-Security (France)
Trend Micro (Japan)
Sophos (UK)
Check Point (Israel)
Micro Focus (UK)
McAfee (US)
Dell (US)
WinMagic (US)
ESET (US)
Cryptomathic (Denmark)
Bitdefender (Romania)
Stormshield (France)
CipherCloud
To Buy Encryption Software Market Report https://www.axiommrc.com/buy_now/10572-encryption-software-market-report
Contact Us:
Axiom Market Research & Consulting™
3 Germay Dr. Ste 4 - 4666
Wilmington DE 19804
U.S.:- + 1 (845) 875-9786
U.K.:- + 44 (0) 20 3286 9707
Email: [email protected]
Website: https://www.axiommrc.com/
Blog: https://industrywatch24.com/
Follow On
LinkedIn: https://www.linkedin.com/company/axiom-market-research-and-consulting/
Twitter: https://twitter.com/AxiommrcCom
Instagram: https://www.instagram.com/axiom_mrc
Facebook: https://www.facebook.com/axiommrc
0 notes
Text
SaaS-based IT Security Market Overview, Application, Share, Cost, Gross Margin, Status and Future Forecast 2030
SaaS-based IT Security Market 2022-2030
The SaaS-based IT Security Market report is latest report published by Fusion Market Research which provides comprehensive information, overview of the demands and describe Impact of Covid-19 on the market during the forecast period 2022–2028.
At the beginning of a recently published report on the global SaaS-based IT Security Market, extensive analysis of the industry has been done with an insightful explanation. The overview has explained the potential of the market and the role of key players that have been portrayed in the information that revealed the applications and manufacturing technology required for the growth of the global SaaS-based IT Security Market.
Request Free Sample Report @ https://www.fusionmarketresearch.com/sample_request/SaaS-based-IT-Security-Market/39277
The report offers detailed coverage of SaaS-based IT Security industry and main market trends with impact of coronavirus. The market research includes historical and forecast market data, demand, application details, price trends, and company shares of the leading SaaS-based IT Security by geography. The report splits the market size, by volume and value, on the basis of application type and geography.
At the same time, we classify SaaS-based IT Security according to the type, application by geography. More importantly, the report includes major countries market based on the type and application.
Finally, the report provides detailed profile and data information analysis of leading SaaS-based IT Security company.
Leading players of SaaS-based IT Security including:
Microsoft Corporation
IBM Corporation
Cisco Systems, Inc.
McAfee, Inc.
Symantec Corporation
Blue Coat Systems, Inc.
Citrix Systems, Inc.
Barracuda Networks, Inc.
F5 Networks, Inc.
Trend Micro
SaaS-based IT Security Market split by Type, can be divided into:
Identity and Access Management Services
Web Gateway Services
Email Gateway Services
Cloud Encryption Services
SIEM Services
SaaS-based IT Security Market split by Application, can be divided into:
Small and Medium Size Enterprises
Large Enterprises
Market segment by Region/Country including:
North America (United States, Canada and Mexico)
Europe (Germany, UK, France, Italy, Russia and Spain etc.)
Asia-Pacific (China, Japan, Korea, India, Australia and Southeast Asia etc.)
South America (Brazil, Argentina and Colombia etc.)
Middle East & Africa (South Africa, UAE and Saudi Arabia etc.)
Ask Queries @ https://www.fusionmarketresearch.com/enquiry.php/SaaS-based-IT-Security-Market/39277
Further key aspects of the report indicate that:
Chapter 1: Research Scope: Product Definition, Type, End-Use & Methodology
Chapter 2: Global Industry Summary
Chapter 3: Market Dynamics
Chapter 4: Global Market Segmentation by region, type and End-Use
Chapter 5: North America Market Segmentation by region, type and End-Use
Chapter 6: Europe Market Segmentation by region, type and End-Use
Chapter 7: Asia-Pacific Market Segmentation by region, type and End-Use
Chapter 8: South America Market Segmentation by region, type and End-Use
Chapter 9: Middle East and Africa Market Segmentation by region, type and End-Use.
Chapter 10: Market Competition by Companies
Chapter 11: Market forecast and environment forecast.
Chapter 12: Industry Summary.
What our report offers:
– Market share assessments for the regional and country-level segments
– Strategic recommendations for the new entrants
– Covers Market data for the years 2020, 2021, 2022, 2025, and 2028
– Market Trends (Drivers, Constraints, Opportunities, Threats, Challenges, Investment Opportunities, and recommendations)
– Strategic recommendations in key business segments based on the market estimations
– Competitive landscaping mapping the key common trends
– Company profiling with detailed strategies, financials, and recent developments
– Supply chain trends mapping the latest technological advancements
Free Customization Offerings:
All the customers of this report will be entitled to receive one of the following free customization options:
• Company Profiling
o Comprehensive profiling of additional market players (up to 3)
o SWOT Analysis of key players (up to 3)
• Regional Segmentation
o Market estimations, Forecasts and CAGR of any prominent country as per the client’s interest (Note: Depends on feasibility check)
• Competitive Benchmarking
o Benchmarking of key players based on product portfolio, geographical presence, and strategic alliances
Related Reports:
Secure DNS Software Market - https://www.newstrail.com/satellite-machine-to-machine-m2m-communications-market/
Security Control Room Market- https://www.newstrail.com/scuff-tester-market/
Seasoning Applicators Market
- https://www.newstrail.com/seasoning-applicators-market
0 notes
Text
Near Field Communication to Dominate India Hardware Wallet Market through FY2027 – TechSci Research
Surge in the digitization process and the growing proliferation of smart devices is expected to drive the demand for India hardware wallet market in the forecast period.
According to TechSci Research report, “India Hardware Wallet Market By Connection Type (Near Field Communication, USB and Bluetooth), By Distribution Channel (Online and Offline), By End-User (Capital Market, BFSI (Excluding Capital Market), Real Estate and Others), By Region, Competition Forecast & Opportunities, FY2027”, the India hardware wallet market is expected to witness steady growth for the next five years. A hardware wallet can be defined as a kind of cryptocurrency wallet and is made to store private keys in a secure encrypted hardware device. Hardware devices are not affected by the attack of viruses or other cyber attacking computer viruses. Hardware wallets allow the storage of multiple currencies at the same time as they take up very little storage space. Every transaction is verified with the hardware device which makes it less prone and vulnerable to cyber fraud. The hardware wallet devices use technologies such as Bluetooth and USB, near field communication, among others to make the connection with other electronic devices. There has been a rise in the adoption of cryptocurrencies by consumers as they are a convenient, fast, and secure way to pay for goods. Cryptocurrencies can be used directly without the need for a banking license and eliminate the traditional banking system which is the major reason considered for the high demand for hardware wallets. Hardware wallets provide enhanced security by minimizing data threats. The surge in the adoption of digital technology across various prominent verticals and the rising demand for online transaction is influencing the growth of the market.
The COVID-19 outbreak across the world which has been declared as a pandemic by the World Health Organization has affected several countries adversely including India. Leading authorities of India imposed lockdown restrictions and released a set of precautionary measures to contain the spread of novel coronavirus. Due to imposition of strict regulations and policies by leading authorities, the business had to suffer huge losses. Manufacturing units were temporarily shut down and the shortage of workforce at the manufacturing plants was observed as the workers moved back to their native places. Disruption in the supply chain was observed which led to the lack of availability of raw materials, skilled workforce, and project delays.

However, the rise in concerns regarding data security and privacy of cryptocurrency may hamper the hardware wallet market growth.
Browse XX Figures spread through XX Pages and an in-depth TOC on “India Hardware Wallet Market”.
https://www.techsciresearch.com/report/india-hardware-wallet-market/7800.html
India hardware wallet market is segmented into connection type, distribution channel, end-user, regional distribution, and company. Based on connection type, the market can be bifurcated into near field communication, USB and Bluetooth. The near field communication segment is expected to account for a major market share of the hardware wallet market, FY2023F-FY2027F. The use of near field communication technology provides the storage facility which allows the flexible usage of cryptocurrency. The use of this technology enables consumers to use cryptocurrency as the normal mode of payment by connecting it with mobile applications. The transaction can take place even in the absence of the internet using near field technology which depends on the type of payment request. Based on the end-user, the market can be divided into capital market, BFSI (excluding capital market), real estate, and others. The capital market segment is expected to hold a major market share in the next five years owing to the rise in the market investments and huge revenue generation through them.
Unocoin, WazirX, Coinbase, Exodus, Guarda, Ledger, Trezor, Sugi, KeepKey LLC, BitBox Limited are the leading players operating in India hardware wallet market. Manufacturers are increasingly focusing on research and development process to fuel higher growth in the market. To meet evolving customer demand with respect to better efficiency and durability, several hardware wallet manufacturers are coming up with their technologically advanced offerings.
Download Sample Report @ https://www.techsciresearch.com/sample-report.aspx?cid=7800
Customers can also request for 10% free customization on this report.
“High-end investments by the major players for invention of new technology is expected to fuel the growth of the hardware wallet market in India in the next five years. The development of a non-custodial wallet, and wireless hardware wallet aiming to simplify the cryptocurrency transactions, coupled with the availability of a diverse variety of hardware wallets based on the consumer needs and requirements in the market is bolstering the market growth. The adoption of advanced technology by the major companies such as blockchain technology to offer higher security and ease the transactions relating to cryptocurrency is facilitating the growing demand for e-commerce platforms, which is further expected to propel the hardware wallet market growth till FY2027F,” said Mr. Karan Chechi, Research Director with TechSci Research, a research-based global management consulting firm.
According to TechSci Research “India Hardware Wallet Market By Connection Type (Near Field Communication, USB and Bluetooth), By Distribution Channel (Online and Offline), By End-User (Capital Market, BFSI (Excluding Capital Market), Real Estate and Others), By Region, Competition Forecast & Opportunities, FY2027” has evaluated the future growth potential of India hardware wallet market and provided statistics & information on market size, shares, structure and future market growth. The report intends to provide cutting-edge market intelligence and help decision makers take sound investment decisions. Besides, the report also identifies and analyzes the emerging trends along with essential drivers, challenges, and opportunities in the India hardware wallet market.
Browse Related Reports
Global Hardware Wallet Market By Connection Type (Near Field Communication, USB and Bluetooth), By Distribution Channel (Online and Offline), By End-User (Capital Market, BFSI (Excluding Capital Market), Real Estate and Others), By Region, Competition, Forecast & Opportunities, 2016-2026
https://www.techsciresearch.com/report/hardware-wallet-market/7557.html
Thailand Managed Security Services Market By Security Type (Network Security, Endpoint Security, Application Security, Cloud Security, Others), By Deployment Mode (On-Premise, Cloud), By Organization Size (Large Enterprise, SMEs), By End User Industry (BFSI, IT & Telecommunication, Energy & Utilities, Healthcare, Manufacturing, Government & Defense, Others), By Region, Competition, Forecast & Opportunities, 2016-2026
https://www.techsciresearch.com/report/thailand-managed-security-services-market/1430.html
Contact
Mr. Ken Mathews
708 Third Avenue,
Manhattan, NY,
New York – 10017
Tel: +1-646-360-1656
Email: [email protected]
#India Hardware Wallet Market#Cybersecurity Market#India Hardware Wallet Market Size#India Hardware Wallet Market Share#India Hardware Wallet Market Growth#India Hardware Wallet Market Forecast#India Hardware Wallet Market Analysis
2 notes
·
View notes
Text
Mobile Security Market: Business Opportunities, Market Challenges & Global Industry Analysis by 2027
Market Synopsis
As per the analysis by Market Research Future Reports (MRFR), the global worldwide mobile security market is estimated to grow from USD 10.50 billion in 2017 to USD 48.85 billion by 2023 at a CAGR of 29.55% during the review period.
The essential factor booming the Mobile Security Market Trends 2020 is the increasing concern of protecting data on enterprise mobile devices. The rise in the usage of mobile phones for banking and e-commerce has made it crucial for the deployment of security software in mobile devices. The need to adhere to security parameters and to increase the adoption of two-factor authentication are some other crucial factors bringing an impact on the growth of the market. The rising adoption of cloud-based technology is likely to propel the market during the review period. The increasing penetration of smartphones has motivated may regional, global, and local companies to develop mobile security software. The growing trend of Bring Your Own Device (BYOD) has propelled the market exponentially. However, increasing cyber-attacks is the biggest hurdle faced by the developers of security solutions. Moreover, pirated and free mobile security can be procured easily, which hampers the growth of the market.
Market Segmentation
The mobile security market is classified on the basis of end-user, operating system, solution, deployment, and region.
On the basis of end-user, the market is segregated into retail, individual users, and financial institutions.
On the operating system, the market is segregated into windows, iOS, android, blackberry, and others.
On the basis of the solution, the market is segregated into the firewall, multi-factor authentication, mobile data protection, data encryption, and mobile application management.
On the basis of deployment, the market is segregated into on-premises and cloud.
On the basis of region, the market is segregated into Europe, America, Asia-Pacific, and the Rest of the World (RoW).
Get a Free Sample @ https://www.marketresearchfuture.com/sample_request/1192
Regional Analysis
The geographical analysis of Europe, America, Asia-Pacific, and the Rest of the World (ROW) has been performed. North America is reigning the global worldwide mobile security market. The North American market acquires the maximum market share. The second position is attained by Europe since the developed countries like Germany, U.S, France, UK, and Canada are the quick adopters of innovative technologies. Moreover, the European region consists of significant, established mobile security software vendors and service providers. The Asia Pacific region is anticipated to be the fastest expanding region due to the establishment of consumer electronics manufacturers and I.T. hubs. Moreover, the increasing adoption of mobile security software by SMEs and enterprises in the APAC region is an additional essential factor in expanding the market. The MEA and Latin American markets are anticipated to exhibit significant growth during the review period.
Key Players
The forefront players of the global worldwide mobile security market are Honeywell International Inc. (U.S.), IBM Corporation (U.S.), ABB Ltd (Switzerland), Schneider Electric (France), Cisco Systems, Dell In, Rockwell Automation (U.S.), Bayshore Networks (U.S.), Symantec Corporation (U.S.), Kaspersky Labs (Russia), Microsoft Corporation (U.S.), IBM Corporation (U.S.), Google Inc. (U.S.), AVG Technologies (Netherlands), Kaspersky Lab (Russia), Intel security group (U.S.), Apple Inc. (U.S.), Verizon Communication Inc. (U.S.), AT&T Inc. (U.S.), and a few more.
Industry News
Apple iPads and iPhones are vulnerable to hacking through the mail app because of a flaw in its email software. As per the study, two vulnerabilities were found in the mail app, which would have allowed the hackers to steal data for years. The issue came into notice while a cyber-attack was being investigated.
Browse Complete Report @ https://www.marketresearchfuture.com/reports/mobile-security-market-1192
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions.
Contact:
Market Research Future
+1 646 845 9312
Email: [email protected]
1 note
·
View note
Text
Bit by bit guidelines to Convert Bitcoins to Dollars

Exchanging bitcoins to an important money.
Bitcoins seem to have been declared by most as the money of tomorrow, yet there are only an unobtrusive bundle of objections that agree to recognize them. Luckily for us, changing bitcoins to a useful money like dollars is clear and plain. If you need to think about precisely how much bitcoin is worth, run a clear net pursuit. If you need to fundamentally change over bitcoin to dollars, move them in a web market and offer them to an interested client. The online business community may quickly and adequately convert your bitcoins to dollars and send them to a charge card, monetary equilibrium, or progressed wallet of your affirmation.
Picking a Conversion Service.
1) Compare the rates made open by grouped change benefits and choose the best one.
Also when the general bitcoin change rate improves, a couple of change organizations give you diverse change rates. For example, think one assistance accommodates convert your bitcoins at a speed of 1 to $5000 USD and one unique proposition to turn 1 bitcoin in to $5250 USD. All of additional things getting same, you ought to oblige the ensuing assistance to get the a huge part of your bitcoins. Read more bitcoin to paypal instant
2) Convert your bitcoin adding an assistance with low costs.
Change benefits routinely demand a charge. Generally speaking there is a level cost if how uncommonly you exchange, and regularly the change organization charges a part of the total you exchange. Evaluate the costs related with the different change organizations and choice one that offers you the ideal game plan. Organization costs change after some time, so try to check the organizations terms and charge routinely.
3) Confirm that the assistance you're utilizing is ensured.
Overall there are a little bundle of ways to deal with approve that a bitcoin change site page is harmless. One is to check review objections for accolades. One other procedure is to ensure the site uses https (as opposed to the less agreeable http) in their URL. At long last, complete a change organization that awards two-factor separating confirmation, checking that fundamentally you can more likely than not insist bitcoin changes.
4) Choose an assist that with lowing trade stretch of time.
A bit of destinations move bitcoins to your record not long after 2 days, anyway snappier organizations may change over your bitcoins to dollars in 2 hours or even less.
Choosing and Uploading Your Bitcoin.
1) Register for a record.
Choosing for a record comes to giving your name, date of birth, address, email address, telephone number, and other individual data. You'll furthermore need to give monetary equilibrium information, an online portion organization like PayPal, or likewise (dependent upon how you need to change over and move your bitcoins).
2) Decide on the best security decisions each time you join.
Each time you gain a record on a bitcoin business focus, you'll have the probability to let two-factor affirmation, which will achieves you would enter a mystery key and an erratically manufactured code transported off your cellphone. You may similarly wish to let a multi-signature decision, which in this way requires boundless free supports early of making a bitcoin change or withdrawal. Both of such security settings can shield you from theft and software engineers.
3) Deposit your bitcoins in the business areas.
The specific framework by which regularly you store your bitcoins should differ subject to how your bitcoins are quite taken care of. Basically, saving your bitcoins is essentially just about as basic as clicking store bitcoins, on the most elevated purpose of the business place's site. Despite your bitcoin encryption key factor is printed out, you'll be urged to go into it. Despite whether your bitcoins are in a wallet (a mixed record or code), you could be drawn closer to move the report. Make an effort not to be reluctant to contact customer help with the event you're having issue keeping your bitcoins.
Exchange Rates.
Convert your bitcoins if the change standard is marvelous. Across time-frame, exchange rates climb and tumble down. As a depiction, one day the trading scale may well allow you to trade 1 bitcoin for $4900. Following seven days, the trading scale may possibly give $5150 expected to 1 bitcoin. Hold out to exchange your bitcoins until the concurring dollar worth augmentations. Before long there is no fixed segment or worth that demonstrates an obliging change standard. A couple of individuals may maybe experience that if the estimation of a bitcoin bounces up by $100, it is an OK event to change over their cash. A couple of individuals may delay until the value they'd get hops up by 5 percent. Certify the trading scale consistently on the web or sign up expected for an assistance that invigorates you on the bitcoin-to-dollar transformation standard so you can appreciate when it improves.
Closeout your bitcoins in the business community.
Offer your bitcoins in the current market. A couple of business focuses permit you to sell your bitcoins to another person. Individuals enable you to offer them instantly to the business place, which ordinarily will after that trade them to interested buyers later on. Notwithstanding, the particular way you complete to sell your bitcoins will fluctuate imperceptibly according to the business community you use. Most of the events, you can simply tap on Sell your bitcoins or some equivalent choice to kick the connection off. The bitcoins will the be gone to dollars and moved to the record you promoted.
Save your bitcoins on a charge card.
Recognize your bitcoins on a check card. A little bundle of business focuses let you to stack your bitcoins on to a check card that favorably transforms them over to dollars. You may have the choice to acquire an online automated charge card, which by and large supplies you with a progression of figures you can get for online purchases that need to have dollars, or you can deliver a principal check card through the mail center. Moreover such a charge cards cost money, anyway they present an extra preferred position, just if you fundamentally never use cash.
Move your bitcoins to another electronic wallet.
Switch your bitcoins to one particular online wallet. A couple bitcoin change organizations make it basic for you to change over your bitcoins to dollars by transforming them to PayPal, Apple Pay, or equivalent organizations. If this is the system you need to change over your bitcoins to dollars, put your payout methodology to the online modernized wallet you need to use. By then, basically closeout or move your bitcoins to the assistance of your confirmation by using the business place menus. Changing bitcoins to dollars by moving them to an online wallet now and again has more noteworthy costs and reduce limits than moving them to your monetary equilibrium. This choice may possibly, regardless, be enormously improved anticipated customers who do online acquisitions more than once and don't wish the trouble of moving their money from a bank to an online wallet.
1 note
·
View note
Text
Sinaloa Cartel Used Encrypted Phone Network Hacked By Police, FBI Document Says
A bulletin written by the FBI for law enforcement agencies said that members of the Sinaloa drug cartel were likely using a brand of encrypted phones that was compromised by law enforcement earlier this year.
The FBI's “emerging intelligence report” is dated February 2020 and was exposed in the 270GB BlueLeaks data dump. It notes that traffickers from the Sinaloa transnational crime organization (TCO) were using Encrochat cryptophones as recently as October of last year, according to an unclassified case citation that was marked DEA sensitive and also law-enforcement sensitive by the FBI.
"As of October 2019, senior Sinaloa TCO leaders were using a highly sophisticated encrypted communications platform, Encrochat to communicate and facilitate criminal activity, according to a human source with direct access, much of whose information has been corroborated for the past year," the report says.
The report adds that another Mexican gang "with ties" to the Sinaloa cartel "was acquiring Encrochat phones from contacts in Europe to communicate with TCO members and a Canada-based trafficking associate … [the gang] was responsible for trafficking precursor chemicals from China and India and fentanyl to the United States."
Both the FBI and the DEA declined to comment for this story.
Encrochat was compromised and shut down by a multinational investigation led by European law enforcement, leading to at least hundreds of arrests across Europe, as Motherboard reported earlier this month. The apparent use of Encrochat by the Sinaloa cartel has not been previously reported.
Sim cards used in these phones were made by Dutch telecom firm KPN, according to earlier Motherboard reporting. Encrochat also stripped these handsets of their camera, microphone, GPS, and USB terminals, and installed proprietary encrypted messaging programs on them, which routed texts through their own servers, “located offshore” in their datacenter, according to an archived EncroPhone webpage.
Encrochat’s web marketing material also claimed its servers “never create, store, or decrypt keys, message conversations or user data.” Once stripped and reengineered, Encrochat sold these cryptophones for roughly EUR 1,000 each “at international scale” and offered subscriptions with worldwide coverage for EUR 3,000 a year.
It is currently unknown whether the compromise of Encrochat led to any specific arrests of Sinaloa cartel members or associates. But Dutch media outlet Het Parool connected the Encrochat takedown to the dismantling of 19 labs where MDMA producers in the Southern border region that straddles the Netherlands and Belgium collaborated with Mexicans to manufacture the “much more lucrative crystal meth.”
And in an article published the day of the press conference, Dutch newspaper NRC reported, “the fact that Dutch pill makers have made a union with Mexican cartels for the production of crystal meth would not have become so clear without the hack at Encro.”
The Dutch Public Prosecutor’s Office and the Dutch National Police would not comment regarding any possible links between the recent arrests of Mexican meth trafficking suspects, Encrochat, and the Sinaloa cartel.
In the past, Sinaloa cartel members used encrypted phones made by a company called Phantom Secure. The CEO of that company. Vincent Ramos, was arrested in 2018 and was sentenced to nine years in prison last year. The cartel has also used its own, custom built encrypted network to communicate.
“Senior Sinaloa TCO leaders were using a highly sophisticated encrypted communications platform, Encrochat to communicate and facilitate criminal activity.”
The FBI report was among a cache of law enforcement documents called “BlueLeaks.” This data dump appears to stem from a security breach at law enforcement web-hosting firm Netsential, where hackers exfiltrated nearly 270 GB of unclassified records from 251 police departments and law enforcement fusion centers.
The data dump was sent to Distributed Denial of Secrets, a self-described “transparency collective” of journalists and online computer activists, which posted these records online on June 22. German authorities seized the DDoS public data server hosting the BlueLeaks data on July 2, but it has continued to circulate via BitTorrent and other websites.
Europol, Eurojust, and the public prosecutor of Lille—the interregional jurisdiction of France that has authority over the Encrochat case—all declined comment.
Beyond the 2018 case cited by DEA intelligence, the FBI identified senior Sinaloa cartel leaders using Encrochat phones “to communicate and facilitate criminal activity, according to a human source with direct access, much of whose information has been corroborated for the past year. The leaders claimed the platform operates much differently than other encrypted systems they had been using.”
The FBI report also cited two other cases where sophisticated communications were used by drug traffickers. Intelligence collected by the FBI in September 2019 revealed that a go-fast boat captain used Garmin Inreach Explorers, a handheld satellite device that allows two-way texting and email communications with any other mobile number or email address.
1 note
·
View note
Text
Blockchain Technology Market Research and Analysis in Manufacturing Industry-Forecast Report (2019-2025)
[12-Nov-2019] Meticulous Research® – leading global market research company published a research report titled “Blockchain in Manufacturing Market by Providers (Middleware Providers, Infrastructure and Protocols Providers, Application & Solution Providers), by Application (Predictive Maintenance, Business Process Optimization, Logistics and Supply Chain Management, Counterfeit Management), End-User (Automotive, Healthcare, Energy & Power, Industrial, Pharmaceuticals), and Region – Global Forecast to 2025’’.
Blockchain is a distributed chain of blocks that traces transaction and assets. It is an information which is encrypted, time-stamped, and not removable which is openly shared on a ledger by many thousands of computers at the same time. Incorporation of blockchain technology in manufacturing sector can assist in installing trust in global supply chains, reducing production expenses, and improving efficiency. Manufacturing companies are rapidly transforming their processes into digital versions and are incorporating several associated systems and applications. However, huge investment was also made by these companies in order to enhance their customer experience. In 2018, Tesla, Inc. announced to invest $5 billion in its Chinese factory. Likewise, Samsung Electronics Co., Ltd., in 2018, announced the construction of its $7 billion semiconductor line in China. Thus, rising investment in manufacturing sector is expected to boost the blockchain in manufacturing market significantly in the next few years.
Request free Sample Copy: https://www.meticulousresearch.com/request-sample-report/cp_id=5016
The blockchain in manufacturing market study presents historical market data in terms of value (2017 and 2018), estimated current data (2019), and forecasts for 2025 – by application and end-user. The study includes diverse industry competitors and analyzes the market at regional as well as country level.
Key Findings in the Global Blockchain in Manufacturing Market Study:
Energy and Power Dominated the Global Blockchain in Manufacturing Market in 2018, by End-User
Based on end-user, the global blockchain in manufacturing market is segmented into automotive, healthcare, aerospace and defense, textile and clothing, energy and power, food and beverages, pharmaceuticals, industrial, and others. Energy and power dominated the global blockchain in manufacturing market in 2018, mainly due to the rising global energy demand, which encourages companies operating in the energy and power industry to adopt blockchain solutions.
Logistics and Supply Chain Management Segment to Register Highest Growth
Based on Application, the global blockchain in manufacturing market is segmented into predictive maintenance, asset tracking and management, business process optimization, logistics and supply chain management, quality control and compliance, and counterfeit management. The logistics and supply chain management segment is expected to register highest CAGR during the forecast period.
Asia-Pacific: The Fastest Growing Regional Market
North America commanded the largest share of the global blockchain in manufacturing market in 2018, followed by Asia-Pacific, Europe, Latin America, and Middle East & Africa. This is due to the early adoption of trending technologies, such as IoT, DevOps, big data, and mobility. The manufacturers are keen to integrate blockchain technologies into their processes. However, Asia-Pacific is the fastest growing regional market due to rising investment in manufacturing sector
You will get brief idea about research and its applications at: https://www.meticulousresearch.com/product/blockchain-in-manufacturing-market-5016/
Key Players in the Blockchain in Manufacturing Market
The report includes an extensive assessment of the key strategic developments adopted by the leading market participants in the industry over the past 4 years (2016-2019). For instance, in October 2018, Infineon Technologies collaborated with Xain AG for the implementation of blockchain technology for the automotive sector.
The major players operating in the global blockchain in manufacturing market are Advanced Micro Devices, Inc. (U.S.), Amazon.Com, Inc. (U.S.), Bigchaindb GmbH (Germany), Blockchain Foundry Inc. (Canada), Chronicled, Inc. (U.S.), Factom, Inc. (U.S.), Grid Singularity GmbH (Germany), IBM Corporation (U.S.), Intel Corporation (U.S.), LO3 Energy, Inc. (U.S.), Microsoft Corporation (U.S.), NVIDIA Corporation (U.S.), Oracle Corporation (U.S.), Riddle&Code GmbH (Austria), ShipChain Inc. (U.S.), Wipro Limited (India), and XAIN AG. (Germany).
Contact Us:
MeticulousResearch®
[email protected]
Contact Sales- +1-646-781-8004
Connect with us on LinkedIn- https://in.linkedin.com/company/meticulous-research
#information & communications technology#blockchain technology#market research#research report#manufacturing industry#global research report
1 note
·
View note
Text
Database Encryption Market 2018: Global Opportunities, Growth Factors and Forecast by Regions, Types, Applications, Dynamics, Development Status and Outlook 2023
Market Highlights
Database encryption has grown in importance and demand as privacy and security has become a key concern for many business enterprises. Database encryption is vital in securing the integrity of database information and is widely being adopted. Market Research Future has conducted a detailed survey of the market and calculated various rates of growth as well as analyzed drivers, trends, and restraints of the market. Increasing data breaches in recent times have put a spotlight on database encryption and demand has exploded, driving significant growth for the global database encryption market.
Government and privacy regulations have come into effect which either endorse or mandate database encryption to reduce theft of valuable data. Increasing establishment of database security companies and the offered services are driving the growth of the market. Encryption service offerings also offer easy manageability and improved performances which have led to increased demand for database encryption services. Moreover, the increasing affordability of such services has also had a highly positive impact on market growth. The advent of the cloud and its widespread adoption has improved scalability, made deployment easy and accessible, and highly flexible which encourage database encryption adoption. Additionally, databases are increasingly being stored on the cloud which makes them more vulnerable to security threats, thus driving the need for encryption.
Notably, the high cost and complexity associated with the initial set up of database encryption are expected to challenge market growth. Moreover, there is a dire lack of awareness regarding database encryption services which is expected to restrain market growth. However, the market is flooded with opportunities as the awareness is growing gradually, and advancement of IT technology is expected to result in the rendering of highly efficient database encryption services.
Get a Free Sample @ https://www.marketresearchfuture.com/sample_request/1801
Segmentation:
Various key segments of the market have been analyzed in depth in MRFR's report. Division of the various vital market components has been performed on the basis of encryption type, deployment, vertical, and region. Encryption types implemented included column level, file system, transparent, and others.
Deployment of data encryption services can be done on-cloud and on-premise.
Verticals, where database encryption is used, include manufacturing, It & telecom, BFSI, government, retail, aerospace & defense, healthcare, and others,
The global market is divided into key geographical regional markets which include Europe, Asia Pacific, North America, and the Rest of the World.
Regional Analysis:
North America has been identified and established as the leader in the global data encryption market. The strong presence of leading market players in the region such as Intel, Symantec, Win Magic, and Microsoft has put North America at the forefront of the global market. Well-developed countries such as the U.S and Canada have a high adoption rate for cloud-based services and solutions which is expected to affect the growth of the North American market positively.
Meanwhile, the Asia Pacific market is growing rapidly and is likely to register the highest CAGR among all regional markets. The increasing trend of Bring Your Own Devices (BYOD) has played a huge role in increasing the importance of database security solutions. Countries such as China and Japan are witnessing increasing adoption of scalable database encryption services in small and medium enterprises, thus driving the growth of the market.
Competitive Dashboard:
Notable market participants included in MRFR’s analysis of the competition in the global database encryption market include Win Magic Inc., PKWARE, Inc., EMC Corporation, Symantec Corporation, Microsoft Corporation, SAS Institute Inc., IBM Corporation, Sophos Ltd., Check Point Software Technologies Ltd., Intel, and Trend Micro Inc.
Latest Industry News:
Canadian based Kalepso has entered the database encryption market with its recent company launch.
Australia has established a new anti-encryption law for national security purposes.
Browse Complete Report @ https://www.marketresearchfuture.com/reports/database-encryption-market-1801
List of Tables
Table1 Global Database Encryption Market, By Country, 2018-2023
Table2 North America: Database Encryption Market, By Country, 2018–2023
Table3 Europe: Database Encryption Market, By Country, 2018–2023
Table4 Asia-Pacific: Database Encryption Market, By Country, 2018–2023
Table5 Latin America: Database Encryption Market, By Country, 2018–2023
Table6 North America: Database Encryption Market, By Country
Table7 North America: Database Encryption Market, By Application
Table8 North America: Database Encryption Market, By Type
Table9 North America: Database Encryption Market, By Service
Table10 North America: Database Encryption Market, By Vertical
Table11 Europe: Database Encryption Market, By Country
About Market Research Future:
At Market Research Future (MRFR), we enable our customers to unravel the complexity of various industries through our Cooked Research Report (CRR), Half-Cooked Research Reports (HCRR), Raw Research Reports (3R), Continuous-Feed Research (CFR), and Market Research & Consulting Services.
MRFR team have supreme objective to provide the optimum quality market research and intelligence services to our clients. Our market research studies by products, services, technologies, applications, end users, and market players for global, regional, and country level market segments, enable our clients to see more, know more, and do more, which help to answer all their most important questions.
Contact:
Market Research Future
+1 646 845 9312
Email: [email protected]
1 note
·
View note
Photo

Computex swiftly approaches, and so too does Zen 2. Why shouldn't AMD reconsider disabling the PSP and supporting Libreboot?
(the below was originally written by /u/supposedlyimsmart)
Introduction
All processors manufactured by AMD after 2013 include a small chip, known as the Platform Security Processor. It is licensed technology from ARM, their TrustZone tech. Simply put, it is a black box. It is claimed by AMD to be a security chip, responsible for memory encryption and, well, platform security. However, it is also used for remote management. Effectively, the PSP is an isolated, low-level, proprietary co-processor that cross-checks your BIOS firmware with its own. If the BIOS firmware doesn't contain AMD-PSP firmware, then your computer will not boot.
Problem
Seems fine, right? It would, if we knew how it worked. We don't. It is a black box, its code a binary blob, and it, too, is signed by cryptographic keys, held by a select few AMD employees. If this were all, this wouldn't exist. Intel has an equivalent technology, you might have heard of it, the Management Engine, the IME? It, too, boasts similar claims of remote management, security, and it, too, is a black box. More research has been done on these, though, and we have discovered that the IME also has:
Full access to memory (without the parent CPU having any knowledge) Full access to the TCP/IP stack; with a dedicated connection to the network interface Can send and receive network packets, even if the OS is protected by a firewall Can be active when the computer is hibernating or even completely turned off, allowing the Co-Processor to turn on and take control of your computer remotely via the internet.
There is no reason to believe that the PSP does not also have these capabilites. Intel doesn't advertise these, why would AMD? These chips are a massive security hole, and that's not all, either. Linus Torvalds, creator and former head developer (a whole separate drama involving a certain new age political terminology and Linus' unerring thirst for good code and brash rants as a result of bad code and a Code of Conduct) of the Linux kernel, has in the past been approached to build a backdoor into the Linux kernel, by none other than the NSA. Microsoft has sued the US government over gag orders sent to it. There is no reason to believe that these alphabet soup/3-letter agencies don't have the keys. It's a backdoor in every even somewhat aging system.
Solution
Include a manner to disable the PSP in BIOS.
No, no it's not. It may seem obvious, but there's a major problem to this approach. There is no way of verifying whether the PSP is actually disabled, as the whole heap of firmware is a massive binary blob. This is not the solution.
Well, then, don't include the PSP in the chip design at all.
While it would be ideal, it does handle memory encryption and platform security, something enterprise customers would want on their chips, and developing a better, freer alternative might not even happen until Zen 5, since Zen 4 is likely already being developed. This, too, is not the answer.
Open source the PSP!
This, this is highly ideal, however, it is unlikely. The PSP is licensed TrustZone technology, so it's not even AMD's to open source. But even then, it's useless to just open source the PSP on its own. This ain't it, chief. Close, but no.
Open sourcing the PSP is only useful if it is accompanied by support for Libreboot, or, less ideally, coreboot. What are these? These are open source firmware that when combined with a payload like SeaBIOS or Tianocore, allow a fully free boot firmware, opening up an even greater part of the computer than what was possible. The true solution is supporting the Libreboot project.
Libreboot support would allow us to verify that the PSP was getting actually disabled, there would be a trustworthy entity in possession of the signing key for the PSP, and, if it were open sourced along with Libreboot support, allow the useful parts of it to remain turned on while the dangerous elements of it are turned off.
Why?
What good reason does AMD actually have to allow disabling the PSP and to support Libreboot? For one, they used to support it, ending support in 2012, a year before the PSP got loaded onto their processors.
By doing such a move, AMD would gain the endorsement of many more circles, namely the security one and the free software ones. Many security professionals have sounded the alarms to these chips, and entities like Google are working to disable the IME, though no work seems to be done for the PSP. Google may buy even more chips for their servers from AMD, and perhaps even build more AMD-powered Chromebooks, all of which have coreboot installed on them by default.
Edward Snowden had tweeted out about the initial hubbub about AMD potentially supporting Libreboot, and such a move would certainly gain support from entities like him. The Free Software Foundation and its branches would have reason to support AMD, as would entities like the Software Freedom Conservancy, not to mention the numerous commentators that would glowingly recommend AMD with not just the expected performance of Zen 2, but also its freedom.
Here on Reddit, there is much evidence of support, with the absolutely shattering nearly 5000 upvotes, and position as the top comment, in the initial Ryzen launch AMA, found here. I highly recommend reading it, as it addresses a few things I don't here.
There was also support back at that time at /r/linux, with people ready to spring to Ryzen should this have happened. Of note, there was this post, and this one, also this post. There's also the post I wrote some 5 months ago yhat got attention, here.
Contact Information
Advanced Micro Devices
One AMD Place
Sunnyvale, CA
94085
Tel: 408-749-4000
Interestingly, no email or contact page other than the customer support one.
http://support.amd.com/en-us/contact/email-form
For those of you who own AMD Stock, this contact info might be more effective:
AMD Investor Relations
One AMD Place
M/S 112
Sunnyvale, CA 94088-3453
email: [email protected]
Tel: (408) 749-3124
Not to mention, they have their social media accounts.
@AMD, @AMDGaming, and the local variants - Twitter, Facebook, and even Instagram At Reddit, we have a few people.
/u/AMD_LisaSu (That's right, the CEO herself.) (@LisaSu for personal Twitter)
/u/AMD_Robert (Technical Marketing)
/u/AMD_James (Business Development)
As well has a few in less lofty positions, like software engineer /u/bridgmanAMD/.
1 note
·
View note