#Current Affairs 5 December 2018
Text
Iplier Appearances by Date
Welcome to all of the Iplier Ego Appearances from the very first to current!
YouTube Playlist Here
2012
June 19th, 2012: Don’t Blink
July 4th, 2012: Don’t Move
November 9th, 2012: The Fall of Slender Man
2013
January 23rd, 2013: King of the Squirrels
February 7th, 2013: Danger In Fiction Part One [Feat. Markiplier]
June 12th, 2013: The Warfstache Affair
July 23rd, 2013: Mr. Kitty Saves The World
July 28th, 2013: Raspy Hill
August 20th, 2013: Danger In Fiction | Chapter II
October 16th, 2013: Warfstache Plays Slender
October 31st, 2013: Are Jumpscares Scary?
2014
June 3rd, 2014: Super Infidelity
August 26th, 2014: The Ned Affair [feat. Markiplier]
October 31st, 2014: Google in Real Life | ft. Markiplier (Matthias Ending)
October 31st, 2014: Google IRL (Markiplier Ending)
December 10th, 2014: Hire My Ass [feat. Markiplier, Danny Sexbang & Matthias]
2015
March 7th, 2015: Five Nights at Freddy’s Interview
March 24th, 2015: Ed Edgar Adoptallott's Baby Bulk Buy
March 26th, 2015: King of the Squirrels Returns
September 8th, 2015: Worst News Doctor
September 13th, 2015: Warfstache Interviews Markiplier
2016
August 13th, 2016: Relax
August 24th, 2016: Now We’re Cooking
November 13th, 2016: MAKING LOVE FOR SENPAI | Yandere Simulator #12
2017
February 14th, 2017: A Date With Markiplier
April 1st, 2017: 360 Video | Let’s Play Minecraft | Part One
April 16th, 2017: Don’t Play This Game
May 5th, 2017: Markiplier TV
May 20th, 2017: Google Gets an Upgrade
June 29th, 2017: The Voice of Darkiplier | Markiplier Remix
October 10th, 2017: Who Killed Markiplier? - Chapter One
October 11th, 2017: Who Killed Markiplier? - Chapter Two
October 12th, 2017: Who Killed Markiplier? - Chapter Three
October 13th, 2017: Who Killed Markiplier? - The Final Chapter
October 14th, 2017: Corpse Abduction?
October 14th, 2017: Suspect With A Shooty?!
October 14th, 2017: Demons Jim, Demons!!
October 14th, 2017: Dummy Jim Reenacts Grisly Scene!
November 19th, 2017: Don’t Remember
November 20th, 2017: Big MOOD?
November 21st, 2017: THE ANIMATRONIC IN THE SHADOWS | POPGOES - Part 6 (ENDING)
December 23rd, 2017: A TOTALLY NORMAL GAME... NOTHING SUSPICIOUS AT ALL... | Doki Doki Literature Club - Part 1 (Description Only)
December 24th, 2017: SO MANY BEAUTIFUL WOMEN | Doki Doki Literature Club - Part 2 (Description Only)
December 26th, 2017: EVERYTHING IS SO... NORMAL | Doki Doki Literature Club - Part 3 (Description Only)
December 30th, 2017: THE PERFECT DATE w/ ThE ̸̗͍̮̼͙P̏͂̈́ͦ͂̂E͆̈́ͧͮͣ̍̄Ŕ̓͋F̿̒ͦĒͫ̑ͧCT̓ ͏̪̜̗͔̻̘GiRL | Doki Doki - Part 4 (Description Only)
December 31st, 2017: WARNING... THINGS GO VERY VERY WRONG... | Doki Doki Literature Club - Part 5 (Description Only)
2018
January 1st, 2018: BE WITH ME FOREVER | Doki Doki Literature Club - Part 6 (ENDING) (Description Only)
January of 2018: A Compromise (Tumblr)
August 15th, 2018: Wilford “MOTHERLOVING” Warfstache
August 20th, 2018: Go Back To Sleep…
December 10th, 2018: SANTA SPILLS THE TEA
2019
May 12th, 2019: DAMIEN
December 21st, 2019: CyberMark (Facebook, THIS HAS ENDED)
October 30th 2019: A Heist With Markiplier
2021
February 11th, 2021: Cooking Simulator #2
February 11th, 2021: The Best Kind of Love Story… (Instagram)
March 7th, 2021: The Warfstache Automated Interview Automaton
August 24th, 2021: MY WORST NIGHTMARE | Mannequin House
September 3rd, 2021: Everything has to End
December 11th, 2021: Everything has to Begin
2022
March 4th, 2022: In Space With Markiplier | Official Trailer
April 4th, 2022: In Space With Markiplier Part One
April 11th, 2022: Ë̸̼R̴̢̼̂R̵̡̙̚͜Ǫ̸͙͚̈R̶̦̮̝͗
April 13th, 2022: We Went Back
April 15th, 2022: Try Not to Crash Simulator | Drive Time Radio
April 18th, 2022: P̴̮̌̓A̵̧͌͜R̶̰̀A̶D̶O̵X̴͓́͗͗͊̆̀͝ ̵͙̈̚D̴̖̍E̷T̷E̵̩͑͜ͅC̵̻͊T̸̺͎̾̾È̷͕Ḓ̴̵̛̊͗̔̃̌̅̀̓̂̕͝
April 25th, 2022: The Multiverse Is Littered With the Corpses of Your Failures
May 2nd, 2022: In Space With Markiplier Part Two
2023
September 16th, 2023: 3 Scary Games #102
Tags
@thequietdoll
15 notes
·
View notes
Text
VENEZUELA: VENEZUELAN DETAINEES’ LIFE AT RISK

Emirlendris Benítez is a 42-year-old mother and tradeswoman who was arbitrarily detained in August 2018 and subjected to torture. Guillermo Zárraga is a 59-year-old engineer and former oil industry unionist arbitrarily detained in November 2020 and tried for crimes for which there was no evidence. They both suffer from grave health conditions, because of acts of torture, in Emirlendris’ case, and inhumane prison conditions. Both individuals are currently unfairly detained in prisons under the responsibility of the Minister for Penitentiary Affairs. We call on her to protect their lives and health and ensure they receive immediate and adequate medical attention
Emirlendris Benitez is a Venezuelan mother, sister, and tradeswomen. On 5 August 2018, Emirlendris was arbitrarily detained on fabricated grounds. Authorities falsely linked her to acts of violence committed against high-profile political leaders in Venezuela; an accusation for which there is no evidence and which she has consistently stated that she had no part in. In custody, she was subjected to torture while pregnant. A few weeks after her arrest, she was forcibly transferred to a medical facility and her pregnancy was terminated without her knowledge or consent. The torture she was subjected to left her needing the long-term use of a wheelchair for mobility. In 2022, she was sentenced to a 30-year prison sentence by a partial and politically motivated court. Emirlendris should have never been detained, as it is believed the charges are politically motivated. Furthermore, the draconian sentence against her should be revoked and she must be immediately released.
Guillermo Zárraga is a Venezuelan engineer who worked as an operator technician for Petróleos de Venezuela S.A. (PDVSA, the Venezuelan state-owned oil company) at the Cardón Refinery in the Catalytic Complex located in Coro, Falcón state. He was also a leader in the Sindicato Único de Trabajadores (Unique Workers' Union) within that organization. On 14 November 2020, at 3:00 am, he was detained at his home by officers from the General Directorate of Military Counterintelligence (DGCIM). According to the indictment by the Public Prosecutor's Office, he has been accused of providing national security information to an American man who had been arrested in September and was believed to be a CIA agent attempting to sabotage the oil industry complex. In addition to his role as a union leader, Guillermo Zárraga had been photographed with Juan Guaido, a prominent opposition leader. This photograph was included as part of the accusation, serving as evidence of Zárraga's alleged intention to support the sabotage. Despite the fact that Nicolás Maduro’s government has released the alleged CIA agent, Guillermo Zárraga remains arbitrarily detained.
TAKE ACTION: WRITE AN APPEAL IN YOUR OWN WORDS OR USE THIS MODEL LETTER
PREFERRED LANGUAGE TO ADDRESS TARGET: Spanish You can also write in your own language.
PLEASE TAKE ACTION AS SOON AS POSSIBLE UNTIL: 1 December 2023
4 notes
·
View notes
Text
My New Hero!
I so Want to meet her!

CAPTAIN MELANIE "MACH" KLUESNER
Captain Melanie Kluesner is the Commander, F-35A Lightning II Demonstration Team, 388th Fighter Wing, Hill Air Force Base, Utah. The mission of the F-35A Lightning II Demonstration team is to showcase the unique aerial capabilities of the Air Force’s most advanced 5th generation multi-role stealth fighter, the F-35A Lightning II, as well as highlight the history of the Air Force’s service through heritage formation flights. Additionally, she provides operational oversight and direction for the 13-personnel team, to include maintenance, aircrew flight equipment, and public affairs Airmen.
Capt Kluesner entered the Air Force in 2015 after receiving her Distinguished Graduate commission from the U.S. Air Force Reserve Officer Training Program at the University of Southern California. She is an experienced fighter pilot with more than 800 flying hours in the F-16C Fighting Falcon, F-35B, and F-35A Lightning II. Her flying assignments include Undergraduate Pilot Training at Sheppard AFB, Texas, and fighter training in the F-16C at Luke AFB, Va., in the F-35A at Eglin AFB, Fl., and in the F-35B at MCAS Beaufort, SC. Operational assignments include Kunsan AFB, South Korea, a USMC exchange at MCAS Iwakuni, Japan, Luke AFB, Arizona, and Hill Air Force Base, Utah. In 2020, she became the first USAF pilot to deploy in the F-35B.
EDUCATION:
2014 Bachelor of Science in Industrial and Systems Engineering, University of Southern California, Los Angeles, Cali.
2021 Squadron Officer School, Maxwell AFB, Ala.
ASSIGNMENTS:
1. October 2015 – February 2017, Student, Undergraduate Pilot Training, Laughlin AFB, Texas
2. March 2017 – December 2017 Student, F-16 Basic Course, Luke AFB, AZ
3. Janruary 2018 – January 2019, F-16 Pilot, Kunsan AB, KOR
4. February 2019 – May 2019, F-35A Transition Course, Eglin AFB, FL
5. June 2019-August 2019 – F-35B Transition Course, MCAS Beaufort, SC
5. September 2019 – June 2021, F-35B Flight Lead, MCAS Iwakuni, Japan
6. July 2021 -- October 2023- F-35A Instructor Pilot and OSS Flight Commander, Luke AFB, AZ
7. November 2023-February 2024- F-35A Instructor Pilot, Hill AFB, UT
6. March 2024 – Present, F-35A Demonstration Team Commander, Hill AFB, Utah
FLIGHT INFORMATION:
Rating: Senior Pilot
Flight Hours: More than 1000
Aircraft Flown: T-6, T-38C, F-16C, F-35B, F-35A
MAJOR AWARDS AND DECORATIONS:
Air Force Commendation Medal
Meritorious Unit Award
Air Force Outstanding Unit Award
EFFECTIVE DATES OF PROMOTION:
Second Lieutenant May 2013
First Lieutenant May 25, 2015
Captain, May 25, 2017
(Current as of March 2024)
1 note
·
View note
Text
Today's Current Affairs: Kerala High Court Upholds Death Sentence for Jisha's Murderer
In today’s current affairs, the Kerala High Court confirmed the death sentence for Muhammed Ameer-ul-Islam, who was convicted of the brutal rape and murder of law student Jisha in 2016. The Division Bench of Justices PB Suresh Kumar and S Manu expressed their hope that this severe penalty would act as a deterrent against such heinous crimes in the future. The Court took into account the gruesome nature of the crime and the impact on society, particularly on women, when confirming the death sentence. Ameer-ul-Islam was found guilty based on strong DNA evidence and a multitude of circumstantial proof. This landmark judgment aims to serve justice and restore a sense of security in society.
[ad_2]
Download Latest Movies in HD Quality
Downloading In 15 seconds
Scroll Down to End of This Post
const downloadBtn = document.getElementById('download-btn');
const timerBtn = document.getElementById('timer-btn');
const downloadLinkBtn = document.getElementById('download-link-btn');
downloadBtn.addEventListener('click', () =>
downloadBtn.style.display = 'none';
timerBtn.style.display = 'block';
let timeLeft = 15;
const timerInterval = setInterval(() =>
if (timeLeft === 0)
clearInterval(timerInterval);
timerBtn.style.display = 'none';
downloadLinkBtn.style.display = 'inline-block';
// Add your download functionality here
console.log('Download started!');
else
timerBtn.textContent = `Downloading In $timeLeft seconds`;
timeLeft--;
, 1000);
);
[ad_1]
Question 1
What was the verdict given by the Kerala High Court to Muhammed Ameer-ul-Islam?
- Life imprisonment
- Death sentence
- Acquittal
- Reduced sentence
Answer: Death sentence
Question 2
Who were the Justices on the Division Bench of the Kerala High Court that confirmed the death sentence?
- Justice PB Suresh Kumar and Justice S Manu
- Justice A K Mathur and Justice P S Narayana
- Justice V R Krishna Iyer and Justice Fathima Beevi
- Justice B K Mukherjee and Justice S H Kapadia
Answer: Justice PB Suresh Kumar and Justice S Manu
Question 3
What was the societal impact of the crime according to the Kerala High Court?
- Financial instability
- Profound fear and vulnerability
- Increased trust in public institutions
- Economic growth
Answer: Profound fear and vulnerability
Question 4
What was Ameerul's background as stated in the article?
- Local farmer from Kerala
- Migrant worker from Assam
- Businessman from Delhi
- Government official from Tamil Nadu
Answer: Migrant worker from Assam
Question 5
What type of evidence played a crucial role in the court's decision?
- Direct eye witness testimonies
- Surveillance footage
- Mediated evidence
- Circumstantial and DNA evidence
Answer: Circumstantial and DNA evidence
Question 6
What was the identity of the victim, Jisha?
- A law enforcement officer
- A law student from Ernakulam Government Law College
- A school teacher
- A businesswoman
Answer: A law student from Ernakulam Government Law College
Question 7
When was the trial court verdict convicting Ameerul given?
- December 2017
- April 2016
- May 2015
- June 2018
Answer: December 2017
Question 8
What additional request did Ameerul make while appealing his conviction?
- To reduce his sentence to life imprisonment
- To re-investigate by a central agency
- To shift his case to another state
- To pardon him due to good behavior
Answer: To re-investigate by a central agency
Question 9
Who were appointed by the High Court to assist with the process of sentencing?
- Two lawyers
- Two mitigation investigators from Project 39A
- Two forensic experts
- Two police officers
Answer: Two mitigation investigators from Project 39A
Question 10
Which Nobel Laureate's statement did the Court mention in its judgment?
- Albert Einstein
- Mother Teresa
- Alexander Solzhenitsyn
- Nelson Mandela
Answer: Alexander Solzhenitsyn
[ad_2]
What did the Kerala High Court decide about Muhammed Ameer-ul-Islam's death sentence?
The Kerala High Court confirmed the death sentence given to Muhammed Ameer-ul-Islam, who was convicted of raping and murdering a law student named Jisha in 2016. The judges said they made this decision with heavy hearts but hoped it would deter others from committing similar crimes.
Who were the judges involved in this case?
Justices PB Suresh Kumar and S Manu were the judges who made the decision to confirm the death sentence. They expressed their hope that the judgment would serve as a deterrent to future crimes.
Why did the Court confirm the death sentence for Ameerul?
The Court considered the extremely brutal nature of the crime and the fact that Jisha belonged to a scheduled caste community. They also noted how the crime affected society, causing fear and outrage, especially among women.
What was the Court's sentiment while delivering the judgment?
While delivering the judgment, the Court expressed that it was with a heavy heart that they upheld the death sentence. They quoted Nobel Laureate Alexander Solzhenitsyn, saying “Justice is conscience, not a personal conscience, but the conscience of the whole humanity,” emphasizing the broader impact of their decision.
What did the Court say about the impact of such crimes on society?
The Court noted that crimes like this one have a profound and far-reaching impact on society. They cause fear and a sense of vulnerability, particularly among women, and erode trust in institutions meant to ensure public safety. These crimes also lead to public outrage and demands for reforms.
What happened on April 28, 2016?
Jisha, a law student, was found dead in her house on April 28, 2016. Her body was mutilated. The investigation pointed to Ameerul, a migrant worker, who allegedly committed the crime after breaking into her house in a drunken state the night before.
What was the trial court's decision in 2017?
In December 2017, the trial court found Ameerul guilty of rape, murder, and other offences under the Indian Penal Code. He was sentenced to death.
What did Ameerul do after the trial court's decision?
Ameerul appealed to the High Court, challenging his conviction and sentence. He also sought a re-investigation by a central agency.
What was the prosecution's case against Ameerul?
The prosecution argued that Ameerul entered Jisha’s house with the intention to rape her. When she resisted, he bit, strangled, stabbed, mutilated, and eventually killed her.
What kind of evidence did the Court rely on to find Ameerul guilty?
The Court relied on circumstantial evidence and strong DNA evidence. This included Jisha's clothes that had Ameerul’s blood and saliva, Jisha’s nail clippings with Ameerul’s blood and tissue, and blood stains on the door that matched Ameerul’s DNA.
What were the reports and judgments the Court considered in its decision?
The Court reviewed mitigation reports from investigators from Project 39A at the National Law University, Delhi. They also went through multiple judgments from the Supreme Court to understand the evolution of death sentence jurisprudence.
What was the final decision of the High Court regarding Ameerul's appeal?
After considering all aspects, the Court decided to dismiss Ameerul’s appeal and confirm his death sentence.
[ad_1]
Download Movies Now
Searching for Latest movies 20 seconds
Sorry There is No Latest movies link found due to technical error. Please Try Again Later.
function claimAirdrop()
document.getElementById('claim-button').style.display = 'none';
document.getElementById('timer-container').style.display = 'block';
let countdownTimer = 20;
const countdownInterval = setInterval(function()
document.getElementById('countdown').textContent = countdownTimer;
countdownTimer--;
if (countdownTimer < 0)
clearInterval(countdownInterval);
document.getElementById('timer-container').style.display = 'none';
document.getElementById('sorry-button').style.display = 'block';
, 1000);
[ad_2]
In a significant development in today's current affairs, the Kerala High Court confirmed the death sentence of Muhammed Ameer-ul-Islam for the brutal rape and murder of law student Jisha in 2016. The court, led by Justices PB Suresh Kumar and S Manu, expressed their decision with a heavy heart, hoping it would serve as a strong deterrent against such heinous crimes.
On the morning of April 28, 2016, Jisha's mutilated body was discovered in her home at Perumbavoor. Ameerul, a migrant worker from Assam, was convicted of the horrifying crime and faced the death sentence in December 2017. Moving an appeal for reconsideration, Ameerul sought relief, but today's verdict reaffirmed the trial court's decision.
The case was notably upheld based on extensive circumstantial evidence and DNA proof linking Ameerul to the crime scene. The High Court highlighted the profound societal impact of such crimes, emphasizing a multifaceted approach to justice to restore public trust and safety. The judgment serves as a grim reminder of the stakes involved in ensuring justice for victims of such atrocious acts.
In one of the precedent-setting aspects, the court had also appointed mitigation investigators to aid in the sentencing process, reflecting evolving jurisprudence in handling death penalty cases. Today's current affairs now mark the somber closure of a case that has deeply affected public conscience and demanded robust judicial action.
[ad_1]
0 notes
Text
Kader Khan

This Biography is about one of the best Professional Actor of the world Kader Khan including his Height, weight, Age & Other Detail…
Express info
Real Name
Kader Khan
Nickname
Not Known
Profession
Actor, Writer, Director
Date of death
31 December 2018
Physical Stats & More Info
Height
in centimeters- 173 cm
in meters- 1.73 m
in Feet Inches- 5’ 8”
Weight
in Kilograms- 92 kg
in Pounds- 203 lbs
Body Measurements
Chest: 44 Inches
Waist: 38 Inches
Biceps: 13 Inches
Eye Color
Dark Brown
Hair Color
Black
Personal Life of Kader Khan
Date of Birth
12 November 1937
Age (as in 2016)
79 Years
Birth Place
Pishin, Baluchistan, Pakistan
Zodiac sign/Sun sign
Scorpio
Hometown
Mumbai, Maharashtra, India (Earlier, his family used to live in Baluchistan, Pakistan)
Nationality
Indian, Canadian
Ethnicity
Pashtun
Current City
Mumbai, India
School
Municipality school, India
College
Ismail Yusuf College, Mumbai, India
Education Qualifications
Graduate, Master Diploma in Engineering
Debut
Film Debut: Daag (1973)
TV Debut: Hasna Mat
Family
Father- Abdul Rehman Khan
Mother- Iqbal Begum
Brother- Shams ur Rehman, Fazal Rehman, Habib ur Rehman
Sister- Not Known
Religion
Islam
Hobbies
Writing
Favorite Things of Kader Khan
Favorite Actor
Amitabh Bachchan
Favorite Color
Grey
Favorite Dialogue
Taqdeer tere kadmon mein hogi…tu muqaddar ka baadshah hoga (Muqaddar Ka Sikandar)
Girls, Affairs and More of Kader Khan
Marital Status
Married
Affairs/Girlfriends
Not Known
Wife
Azra Khan (Housewife)
Children
Daughter- N/A
Son- Quddus Khan, Sarfaraz Khan, Shahnawaz Khan
Money Factor of Kader Khan
Salary
Not Known
Net Worth
$10 Million
This Biography Written By www.welidot.com
Read the full article
0 notes
Text
Vanya Singh Rajput Wiki, Biography, Age, Height, Weight, Family, Net Worth

Vanya Singh Rajput Wiki: Vanya Singh Rajput is an Indian actress and model who gained popularity for her bold performances in various web series. She is best known for her role as Sophia in the Ullu series ‘Titliyaan’ and her appearances in ‘Charmsukh – Jane Anjane Mein’ and Big M Zoo’s ‘Ghutan’. Vanya was born and raised in Raipur, Madhya Pradesh, in a Kshatriya family. She completed her education at Pandit Ravishankar Shukla University, Raipur.
Currently, Vanya Singh Rajput resides with her family in Mumbai. She has two younger sisters, Anamika Singh Chandel and Reema Singh. Reema is a fashion blogger and owns an Instagram shop called WEWORESWAG. She got married to Ankit Rathore in December 2018. Although rumours suggest that Vanya has an affair with Nikhil Parmar, predominantly known for his work in Hindi and Gujarati cinema, she has not confirmed any relationship publicly.
Vanya Singh Rajput Wiki
Vanya Singh Rajput Body Measurements
Vanya started her career as a model and won the Miss Chhattisgarh Fashion Show and Cadence Fashion Show in 2013 and 2015, respectively. She then moved to Mumbai and did several catalogue shoots for Indian and Western Wear. In 2021, she made her acting debut in Ullu’s erotic web series ‘Charmsukh – Jane Anjane Mein 5’, playing the role of Kajal. The audience appreciated her performance, which led her to work on other series, such as Big M Zoo’s ‘Ghutan’ and Ullu’s ‘Titliyaan’ in 2022.

Vanya Singh Rajput Wiki
Vanya Singh Rajput Wiki
In the latter, she played the character of Sophia, who supports Tanya after her break up with her cheating boyfriend, Jimmy. The same year, she appeared in the lead role in the Red Prime Entertainment web series ‘Shipra’. She also made a small cameo appearance in the MX Player original series ‘Roohaniyat’. Besides web series, Vanya has been a part of several T.V. commercials and events. Her performances have gained her a significant fan following on social media platforms.
Real NameVaanya Singh RajputNick NameAakankshaOther NameVanya Singh RajputProfessionActress and ModelDate of Birth6 April 1993Age29 years (as of 2023)Place of BirthRaipur, Madhya Pradesh, IndiaNationalityIndianHair ColorBlackEye ColorBlackSexual OrientationStraightZodiac SignUnknownReligionHinduismCasteKshatriyaHometownRaipur, Madhya PradeshCurrent LocationMumbai, MaharashtraLanguages KnownHindi, EnglishSchoolUnknownCollegePandit Ravishankar Shukla University, Raipur, M.P.Educational QualificationGraduateTheatreNoHobbies and Favorites StuffTravelling, Shopping, ModellingFavourite ActorShahrukh KhanFavourite ActressKajolFavourite MoviesDDLJFood PreferenceNothing Specific
Vanya Singh Rajput Body Measurements
Height5’5″ ftWeight56 KgsBreast Size32 inchesWaist Size28 inchesHips Size32 inches
Read the full article
0 notes
Photo

Current Affairs | 16-12-2022 | L2A
1) 162173 Ryugu, provisional designation 1999 JU3, is a near-Earth object and a potentially hazardous asteroid of the Apollo group.
2) It measures approximately 900 metres in diameter and is a dark object of the rare spectral type Cb, with qualities of both a C-type asteroid and a B-type asteroid.
3) In June 2018, the Japanese spacecraft Hayabusa2 arrived at the asteroid.
4) After making measurements and taking samples, Hayabusa2 left Ryugu for Earth in November 2019 and returned the sample capsule to Earth on 5 December 2020.
5) As of August 2019, there are 13 surface features that are named by the IAU.
6) The three landing sites are not officially confirmed but are referred to by specific names in media by JAXA.
7) The theme of features on Ryugu is "children's stories".
Ryugu was the first object to introduce the feature type known as the Saxum, referring to the large boulders found on Ryugu's surface.
#currentaffairs#currentaffairs2022#currentaffairsquiz#l2a#learn2achieve#IAS#UPSC#upscpreparation#upscmotivation#upsccoaching#explore#explorepage
0 notes
Text
5 December 2018 Current Affairs Hindi GK – दिसम्बर 2018 करेंट अफेयर्स
5 December 2018 Current Affairs Hindi GK – दिसम्बर 2018 करेंट अफेयर्स
यहाँ हमने 5 दिसम्बर 2018 भारत और विदेश से सम्बंधित कर्रेंट अफेयर्स के सबाल और जबाब हिंदी भाषा व् संछिप्त में प्रकाशित किए है | यहाँ अंकित किए गए सभी करंट अफेयर्स प्रश्न ‘5 December 2018‘ के मुख्य समाचारों से लिए गए है जिन्हें हमने प्रश्न व् उत्तर के साथ अंकित किए है| सभी प्रश्न व् उत्तर आने वाली सरकारी �� निजी नोकरी व परीक्षाओं (SSC, BANK, Railway, Clerk, PO, UPSC Exam) के लिए आपके लिए महत्वपूर्ण…
View On WordPress
#5 December 2018 Current Affairs Hindi GK – दिसम्बर 2018 करेंट अफेयर्स#Admit Card#Banking#BPSC#current Affairs#Current Affairs Hindi February 2019 के Today Hindi GK#current affairs in hindi#current news#daily gk#exam preparation#general knowledge#general knowledge question and answer#gk#gk in hindi#gk quiz#gktoday hindi#Hindi Current Affairs में आपका स्वागत हैं. हिंदी सामान्य ज्ञान तथा हिंदी करेंट अफेयर्स को समर्पित वेबसाइट है#hindi gk#IBPS#independent educational consultant Latest news#indian sarkari nokari news in hindi#JPSC#June 2020 Current Affairs Today Hindi GK Latest Jobs#latest gk#latest news aaj ki taja khabar hindi mai#latest sarkari exam admit card#latest sarkari job news in hindi#lucent gk#MPPSC#newspaper in hindi
0 notes
Text

Hello lovely people!
It seems that life made me take a leave of absence from tumblr. Thanks to all of you who have continued to interact with my page! I'm sorry if I've missed any messages or questions in the time that I've been away. I'm back now and I'll continue to share my journey with you all...
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
In order to be able to keep moving forward, I think it's important to accept the past and move on. Accept any of the difficulties that happened, and see them as moments you've gone through that have made you stronger. My way of accepting and turning over a new page will be through this post.
I haven't shared too much information about my studies and how they've been going. My studyblr was very new, and I was using it more as a means for motivation by seeing all the wonderful things people in the community were doing. Little by little, I started to make posts of my own.
So let me formally introduce myself and share my ongoing journey...
My name is Valentina, I go by Vale for short. I jumped from graduating from my BA in International Relations and Political Science in the Spring of 2018 to starting my PhD studies in International Relations the Fall semester of that same year. No break, very smart... I know. That's only just the beginning. I'm not sure how it works abroad, but here doctoral students usually go through most of their studies being funded by a graduate assistantship. This pays tuition and provides a stipend through working as a TA (graduate teaching assistant). Of course they vary across universities and departments. When I was applying to the PhD program, one of my professors advised me not to accept if I was not given funding. There are only a limited number of spots that are given to incoming students each year that will be accepted as a TA.
In March of 2018 I received notification that I was accepted into the PhD program in International Relations at my university, however, the department could not guarantee funding for me. This put me at a loss, and I spend months wondering where this was going and what I would do. Because I'm an immigrant in the US, though I've been living here practically my whole life, I didn't have too many options. My mobility is constrained.. my access to scholarships is constrained (even though I may qualify for them in terms of academics and merit, migration status trumps over all of it). I was lost, to say the least. My family can't afford to have paid for this program or a Master's program out of pocket, and I am not able to take out student loans even if I wanted to.
Regardless of this all, I still attended the incoming graduate student orientation; which surprised the outgoing graduate program director. She did not think I would show up, considering the whole funding predicament. She and the new GPD told me that they would try to find something for me. On the first day of class, I showed up, still not knowing what would become of this situation. Not knowing if I would actually get to start the semester or not. We are usually given a week to pay tuition - because of status, I am considered an international student so my tuition came out to nearly $10,000 for three courses. That day, out of nowhere, I was told that the dean of our school (School of International and Public Affairs) was looking for a graduate assistant for new projects that he wanted to work on. In the span of a few hours, I ended up interviewing with him, being told that they would let me know because there was another student they were considering, and later being called and told that I got the position. I was ecstatic. I called my parents in tears. This was actually happening; I was actually going to be able to start my PhD.
It all happened so fast. It all seemed so exciting. The dean seemed very enthusiastic and pleased that I would be working with him. Things eventually took a turn for the worst...
Transitioning into graduate school itself is extremely difficult. Many graduate students find themselves experiencing heightened stress and strain on their mental health. I did not give myself the space to transition into graduate school without the added stress of being a doctoral student, without the added expectations. On top of that, the dean had not had a graduate assistant before. This was new for him too. The expectations of me were blurred and my contract would only last for a year to be considered for possible renewal (the typical TA contract in my original department lasts 4 years), this led to disaster. I needed this position to continue to fund my studies, so I needed to make sure that I was on top of my work expectations. Because these expectations were unclear, the dean's secretary took advantage. It seems they were short staffed, and I was given administrative tasks that did not belong to me. I was made to come in to the office for strictly 20 hours a week. (Our contract states that we work up to 20 hours a week). If I was ever sick and missed a day, that would be added onto the hours for the next week. So if I missed a day where I was supposed to be in the office for 5 hours, I'd have to be there for 25 hours the following week. A breach in the contract, I know - but who was I, a lowly student, against the dean? This office (a shared space) was not a place where a person could focus on studying. There were students coming in and out, loud conversations occurring, and having to see if the actual student employee in charge of taking phone calls was at their desk - if not, I would have to man the phone. While I was doing administrative tasks for the dean's secretary, the dean was having me create themed presentations and CO-LECTURE with him. Me, a person who had been an undergraduate student only months earlier. I had to create these presentations from scratch and know all of the material. All of my focus had to be on this. My performance in my own classes and mental health declined quickly. I could not focus, I could not get my reading assignments done, I felt unprepared. I felt like a failure.
After a year, I realized that it was not worth to have my tuition paid for if I could not focus on my classes and was set up for failure. It took a lot, but ultimately I turned down the contract renewal. Here comes the fun part. My GPA dropped tremendously. I graduated Magna Cume Laude just a year before. I developed depression and didn't realize it; to the point where a friend practically made me go to counseling. The office manager at my actual department knew what I was going through. I had shared a lot of my experience with her. She advocated for me. Because of this, I was told that there was a student who had been awarded an assistantship for the incoming Fall 2019 semester, but had decided not to take it. The contract was going to be made for me instead, for not 4 but for 5 years since I had only come in with a BA degree. When they ran it through the associate dean's office... it was denied. My GPA was lower than the threshold. A LOT lower. I was told by the GPD - the same woman who had just started her position that said she would help me, the woman that had gone on maternity leave during that whole year after she started meaning she was not aware of the situation - that I should really take my studies more seriously. She received a very long email from me and apologized afterwards, to say the least. Nothing could be done.
I had no funding, only savings and ended up working Full Time in Fall of 2019 in order to try to pay for 1 course, that costed me a little over $3,000. Somehow, even though I strongly considered it, I managed not to drop out. By this time, the majority of the courses I had taken before had INs - incomplete grades. Two of them had automatically turned into Fs. Things were not okay.
I got a bit of a mental break during that Fall semester. I worked in a friendly environment. The office manager pulled some strings and let me work as an office assistant there... so I was still at my department, but working as staff. It was a little awkward. I'm eternally grateful to her, she became a close friend. And because of her, someone at another department got word that there was a graduate student who needed funding.
This office manager was good friends with a recently graduated phd student from our department who is now working for a different center in the university. Because she was part of my department, many of my current colleagues know her, and are good friends with her. We spoke, I rushed to get my GPA up to the 3.0 threshold and with the help of my professor's I was able to be awarded an assistantship with that center. I started in December of 2019.
Again, I was ecstatic. Things were looking up. When I went in for the first time, I immediately felt a huge difference. It was a smaller, more homey place; and a lovely environment to be in. The people there were sweet and caring. I've gotten along with the few professors I've had the chance of meeting and working with.
Where did it start going downhill? The professor that recommended me (graduate from my home department) continuously requested that I work with her. Her reason being that I got along better with her (something that I was not aware of). Because she considered herself as my friend, professional lines were horribly blurred. I found myself doing additional work for her as a "favor for a friend." She then started having us meet multiple times a week for hours - distracting from the time I needed to actually get work done. This center does not cap classes - I've had to grade for up to 400 students in one semester. The meetings she scheduled were incredibly unproductive, and I found myself having to take extra time to get the grading done. Again, my own studies were effected. The past academic year went on like this. I ended up assisting in creating a new course and new assignments from scratch.
Later I noticed that something was wrong. I was doing way more work than stipulated by my contract. She was giving me access to her courses that I was not assigned to grade for. Instead of assisting for one course in the semester (the one with the highest enrollment), I was assisting for three. This was constantly under the guise of 'friendship'. How was I supposed to reject my 'friend'? When I tried to draw professional boundaries, I was met with resistance.
My mental health declined again in the fall and I missed a few of her scheduled meetings (meetings which she said were NOT mandatory). Because of this, she decided to throw me under the bus with the director and making it seem as if I was not actually working - when I was addressing students' needs and getting grades in. This worsened in the Spring. With the help of my counselor I finally got the courage to communicate with her. Albeit through text, because she's the type of person that does not allow you to get a word in during conversation.
"On that note, there’s something I’ve wanted to talk about. I’ve been struggling with concentration and fatigue. This is something that I’ve been working on with my doctor to try to find solutions. I’ve noticed that being in Zoom meetings in general where there’s casual conversation makes it exceptionally difficult for me to focus on what I’m trying to get done. This has been problematic in the work zoom meetings. You probably have noticed I seem really quiet, that is because I’m trying my hardest to focus.
I need to be able to focus during the time I’m assigned to work as a GA. Otherwise, I must take more time to complete tasks that normally wouldn’t take up that long or just wait until the weekends to finish them. That is conflicting as I have set that time to work on class assignments and my own projects. So in the end I end up falling behind and not working well because my productivity levels are being affected."
She seemed to understand me and be supportive. Then I noticed coldness, and condescending passive aggressive texts from her part.
I realized that I could not do this any longer. I could not allow myself to continuously be taken advantage of. Both of the people I've worked for were aware of my vulnerable situation due to migration status. They both knew that it was not easy for me to pay for my studies through any other means. My studies depended on these people, and if they 'liked' me. They abused and absorbed my time to the extent that my studies suffered tremendously.
But I finally stood up for myself. I spoke with the director and she affirmed that my concerns were valid. Time and time again she assured me that my studies should always come first. She supported me. I will no longer be assigned to work with this person.
I finally feel heard.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
It's been 3 years since I started my program. A lot has happened in this time. I have a lot of catching up to do this summer if I want to stay on track and take my comprehensive exams by the end of the year. But someone finally heard me, acknowledged the wrongdoings and helped me.
Don't let people walk over you and take advantage of you. I'm learning this the hard way.
Speak your truth.
#my story#my phd story#experiences#struggles#growth#don't give up#don't silence yourself#share your story#speak your truth#long post#studyblr#phdblr#phd studyblr#phd student#gradblr#grad student#stand up for yourself#keep moving forward
24 notes
·
View notes
Text
Gigaleak, preservation, emulation and content dissemination

(la version française de cet article est disponible ici)
On November 21, 1992, the sequel to the most widespread Mega Drive title was released in both Japan and South Korea, then in the rest of the world. In spite of itself, this game made many people want to find out what had happened to all those elements that had been cut during development.
A few months earlier, when Sega started to show its future hit to the press, the public got a glimpse of levels such as Hidden Palace, an area absent from the final version. This wasn't the first time such an event had occurred; other sometimes equally popular titles such as Super Mario Bros. 3 have encountered the same fate, either through press coverage or via screenshots featured on the game's box. But Sonic 2 has one point that sets it apart from most other titles, in addition to its popularity: a development version was stolen a few months before the game hit the shelves. According to Yuji Naka, programmer and figurehead of the license at the time, a cartridge was stolen at a trade show in New York. His former colleague Akinori Nishiyama, meanwhile, says Sega had been hacked. In any case, this version was marketed in markets where cartridges produced without an official license were common, before being found in 1999 on a Chinese website as a ROM. Named after the person who found the ROM, the Simon Wai prototype features an unfinished version of a level that was thought to be never playable: Hidden Palace. The popularity of the license helping, amateurs started to collect documents of all types in order to identify all the differences between the versions marketed by Sega and the numerous screenshots and other development versions found over the years.

A preview published in the October 1992 issue of the British magazine Mega. 2 of the 3 levels shown here do not appear in the final version of the game.
Since Sonic 2, a lot of development versions and design documents have found their way on the net with more or less echo and communities of amateur researchers have gathered around sites such as The Cutting Room Floor, Unseen64 or Hidden Palace. On February 23, 2008, the latter put online a thousand development versions of games produced by Sega or released on Sega consoles after buying archives disks containing the games in question, sometimes with several dozen versions per title. However, the data leakage that Nintendo is experiencing in recent months seems unparalleled in terms of volume and variety of content.
In April 2020, development versions of various episodes of Pokémon, as well as source code, development tools and graphics from intermediate versions were released. Before that, in 2018 and 2019, a development version of Pokémon Gold and Silver (the "Spaceworld 1997 demo", named after the show where it was presented), assets of Pokémon Red and Green then Pokémon Diamond and Pearl had leaked on the net.
In the days that followed, other types of content appeared on 4chan: official documentation relating to a number of Nintendo consoles including the Wii, the Nintendo 64, the 64DD, the iQue Player, a technical demo produced for the Nintendo 64, source code written for Super Mario 64, Powerpoints and internal correspondence from several companies for a total of about 29,000 documents.
A second batch of data began to appear on July 24th and found an echo that goes far beyond technical enthusiasts and console clone producers. A large amount of content relating to some of the most popular titles and licenses in the history of video games (Mario, Zelda, Animal Crossing, StarFox) has been put online, linked on 4chan then distributed on the rest of the Internet. Development versions of Super NES, Nintendo 64, Game Boy, Game Boy Color, Game Boy Advance games, as well as source codes, graphic assets, 3D animation tests, sound effects and uncompressed music, 2D and 3D illustrations, logos, level editors, conversations between developers, visuals for a website, documents relating to the Wii, etc.
The origins of the leak
Nintendo has been the subject of several attacks in recent years. Of those that have come to light, one resulted in the leakage of information about the Switch prior to its release, another involved source codes obtained from dozens of companies, but the one that most closely corresponds to the present case - generally called the Gigaleak - was carried out in 2018 by a man named Zammis Clark, a British security researcher and former Malwarebytes employee, a company specialised in detecting and removing malicious software.
In 2015, he hacked VTech's servers, revealing that the company had illegally collected the data of nearly 200,000 children. He also revealed vulnerabilities in apps from manufacturers such as Dell, Lenovo and Toshiba as well as in a tool used in UK schools and developed by Impero.
In 2017, he hacked some of the Microsoft servers and stole tens of thousands of files before sharing access to these servers with others.
After being arrested and released on bail, he hacked Nintendo's internal network in March 2018. In its official communication, the Japanese company only mentioned the theft of a few thousand IDs and passwords as well as access to data relating to games in development at the time. However, Ganix, the man who released the Pokémon Diamond and Pearl sprites in December 2019, explained in an interview he gave to LavaCutContent a few days later that the various leaked content relating to Pokémon (including the Spaceworld 1997 demo released in May 2018, the month Nintendo realised it had been hacked by Clark) all came from a hack done in March 2018 by a man who goes by the pseudonym "Wack0". We know since the Impero affair that Wack0 is none other than Clark's pseudonym - a letter written by Impero and addressed to Clark in 2015 links the two names. Clark had shared these files with Ganix, who decided on his own initiative to leak them in December 2019, thus betraying Clark's confidence in him. The 4chan thread with which the Gigaleak started in July 2020 seems to refer to this event by its title: "ppg leak time: fuck ganix".
Because of his profile - Clark has a form of autism and suffers from prosopagnosia, the inability to recognize and identify faces - the judge felt that he would be at too great a risk if sent to prison. He was sentenced in 2019 to a 15-month suspended prison sentence and subject to a 5-year judicial review.
The presence of files relating to the iQue Player and the BroadOn company among the leaked documents suggests that the hacker accessed BroadOn’s servers, a company founded by Wei Yen who also co-founded iQue with Nintendo. Due to the legal restrictions in effect in China from 2000 to 2015, Nintendo had to make a joint venture to enter this market and develop a variant of the Nintendo 64 - the iQue Player. BroadOn is one of Nintendo's collaborators and has developed software for the Wii as well as for the iQue Brand (which includes game consoles such as the Game Boy Advance, the DS and the 3DS).

The iQue Player (picture by Evan Amos)
While Nintendo is the main target of this leak, other companies have also been affected by the ripple effect. Among them are Capcom, Konami and M2 (which is the current holder of the rights to the Aleste series). Assets and development versions of some of their games released on Super Famicom are now in the wild. Among them are Megaman X, Super Ghouls'n Ghosts, Super Castlevania IV, Axelay, Parodius Da!, Ganbare Goemon and Super Aleste.
Since the release of Collection of Mana, it is public knowledge that Nintendo keep content produced by other companies in its archives. Masaru Oyamada, producer of the Mana series, said that this compilation was made possible by Nintendo, which allowed Square-Enix to recover the various source codes of these games.
In the wake of the Gigaleak, the source code for the Xbox Unreal Championship 2 game has been put online, along with numerous design documents. Epic Games' servers had been hacked in 2011 without the identity of the visitor being revealed; it cannot be excluded that the files in question originated from this attack and that the author of the hack kept them until that day on July 30, 2020. The link between this leak and the Gigaleak is not yet certain. In such a case, it is unlikely that anyone would publicly claim responsibility for the leak.
On the authenticity of the leaked content
When a console prototype, a development version of a popular game or from a major license surfaces, it is customary to take it with a pinch of salt, in case someone came up with the idea of pulling a hoax or to replenish his bank account by trying to sell a fake.
In the case of the contents leaked in 2020, since Nintendo hasn't officially commented on the case despite the requests made by Vice.com and LeMonde.fr, the doubt persists and the volume of data is such that it will be difficult to authenticate everything file by file. Nevertheless, Dylan Cuthbert, former developer of Argonaut who later joined Nintendo, recognised one of the tools developed for Starfox 2. In addition, in a number of cases, developers at the company have in the past provided clues suggesting that at least some of the content is authentic. This includes some rejected designs for Yoshi from Super Mario World, already unveiled in 2017.

A sprite sheet created by Shigefumi Hino during the development of Super Mario World, one year before the game’s release.
There are also quotes from developers about the presence of Luigi in Super Mario 64 and adult Mario in Yoshi's Island (both of which were set aside during development), characters in overalls in Super Mario Kart before it was decided to set the game in the Mario universe and a circuit from Mario Kart 64 located in a city but deemed too big. The same goes for the Zelda license: Yoshiaki Koizumi said he made a polygonal version of Link as part of a prototype adaptation of Zelda II for the Super Famicom, Eiji Aonuma explained that the cycle of Majora's Mask originally lasted not three days but a week and Link's Awakening was originally thought to be an adaptation of A Link to the Past - the world map of the latter made with the engine of the former has been found.
Regarding Dragonfly, one of the very first Super Famicom titles shown to the public in 1988 before being renamed Pilotwings, the different screenshots published in magazines correspond to the version that leaked. While this is not an absolute proof of its authenticity - in 2012, a fan recreated an early version of Sonic 1 using screenshots as references -, the sum of clues previously cited and the large amount of documents posted online make the hoax thesis unlikely.
This leak also contains a lot of files that are difficult to identify, mainly because the names used for the files and directories are not always very explicit and some titles had never been publicly shown before or in another form. Examples include Sleep, an unfinished mouse-playable Super Famicom game (which may have been announced under the title "Black Out" in 1992), Super Donkey, another unfinished title with a number of visual similarities to Yoshi's Island, or Link's profile sprites for which we can only make guesses.
Plunging into this maze of repertories requires patience as well as certain skills. Let's take the case of a game: each game has its own CVS file (named after the software used by Nintendo). A CVS file may contain several versions of a game, like a log of its evolution: an early version, a more advanced version with some elements that differ from the final version, the final version, etc. These files are not ROMs that could be launched in an emulator in 3 clicks. You have to compile the source code of the game you want to launch first, if there is source code.
Private conversations
There is one point on which the leak doesn't seem to have been publicly praised: the posting of private conversations. Since April 2020, conversations between employees from various companies (Nintendo, BroadOn, then Argonaut in July) have been circulating on the net, in particular exchanges between Argonaut employees that took place in the early 90s, when some of them came to work at Nintendo in Japan. In addition to the fact that these are private correspondence - which already poses legal and moral issues - some of the excerpts shared online highlight issues that echo recent cases involving other companies, particularly on the subject of sexism and sexual harassment. In this case, the problem is twofold: there is, of course, the harassment itself (unsolicited pornographic images), but also the fact that the subject has come up without the victims having chosen to deal with it themselves.
This case illustrates the fact that video game preservation requires a minimum of methodology and should not necessarily result in the unregulated dissemination of any content relating to the development of a game or the history of a society.
On the rest of the leak, opinions are very divided. Some people welcome it unreservedly; others have a mixed or even negative opinion, with the question of preservation and its modalities itself being debated.
Preservation
Video game preservation is a race against time that began years ago, but the rules to be applied are still being discussed. A part of the public considers that everything that is not yet available as a ROM or ISO on the net should be dumped and shared. In 2019, a notorious collector, owner of one of the 3 knonw copies of the arcade game Akka Arrh, claimed that someone came to his home to unknowingly dump the ROM of the game in question and put it online. This is one of the most extreme cases known (if true), but it raises another issue: does preservation necessarily have to be illegal?
The ROMs of commercial games you can find on the net (excluding the official websites such as the Nintendo eShop) are copies that contravene intellectual property law, whether they are final or intermediate versions, marketed or not. As early as 1993-94, consoles such as the NES, Super NES and Mega Drive had their dedicated emulator and with them ROMs that could be found via BBS. Already at that time, there were ROMs of development versions, some of which seem to have disappeared from the net because of their low distribution. These generally come either from developers who kept cartridges, CDs or files on hard disk, or from journalists who did the same with preview versions. In both cases, it is likely that they were not supposed to keep possession of them, let alone resell them years later to individuals. The amount of money exchanged for these copies has skyrocketed over the last 20 years. What might have been worth a hundred dollars in the early 2000s is now steadily rising to over a thousand.
The illegal nature of the Gigaleak is nothing new in this field, but it may have been shocking in terms of its scale and the fact that the content was not obtained through a transaction (even if what made it possible is of questionable legality).
In 1979, while Namco was conducting a location test of Galaxian in a coffee shop, the game's PCB was swapped and duplicated, making it one of the first commercial titles with a beta version that ended up in the wild even before the final (and official) version was released.
Legislation in countries such as Japan, France or the United States is not so much a hindrance to the preservation as it is to the dissemination of ROMs and ISOs. We can certainly deplore the inadequacy of state initiatives as well as the meagre budgets allocated to the preservation of video games - in 2017, during a symposium on the preservation of video game preservation held at the BNF (National Library of France), its audiovisual department confessed that the budget allocated for video games was much lower than that obtained by the film sector with an average of 5,000 to 6,000 euros per year, going up to 8,000 euros in good years. It covers the acquisition of missing games (those who fell through the cracks of legal deposit), storage costs (the room where the games and machines are kept must remain at a constant temperature), etc. But the current legislation is an obstacle to preservation mainly in special cases such as video games with child pornographic content, games that companies such as Enix sometimes published in the early 1980s in Japan.
The Game Preservation Society, an entity based in Japan, does not have the task of putting online copies of the (sometimes very rare) games that it keeps in its archives, but of preserving them. Private individuals can also call on it to make backups of titles from their collection, the purpose of a private backup being to prevent damage to the programme's storage medium (cassettes, floppy disks, CDs, etc.). This policy is sometimes met with incomprehension or even disapproval from a certain fringe of the public who tirelessly demand the games' ROMs. OK, but which games?
Websites that share ROMs without the agreement of their rights holders have a definite advantage over game publishers: almost all the games released on some of the most popular consoles can be found on the net. Few publishers are able to exploit their entire catalogue on a continuous basis for reasons as diverse as lack of resources, rights problems in the event of third-party licenses, or lack of commercial interest. If you want to try out the entire Mega Drive library, either you buy the 900 or so cartridges published in the past, or you download an emulator and the corresponding ROMset, thus breaking the law. It gets even more complicated with games that were playable online or available for sale in digital form only if the relevant service has closed.
Abandonware-France, a website created in 2000 where you can find thousands of PC games and video game-related magazines, has adopted a clear line excluding games that are still commercially exploited as well as those released after 2000. It's less an ideal solution than a default solution - it doesn't solve the legality issue, since the games haven't yet fallen into the public domain - but it has no impact on publishers' sales, which is still one of the surest ways to get through the bullets. Other websites have been less cautious on this point by making available content that is still commercially exploited.
Due to its special status, Internet Archives makes it possible to play (but not download) thousands of old games online, including titles that are still commercially exploited (Sonic 1 for example) but with the notable exception of Nintendo games or games released on Nintendo systems. In 2016, the Japanese company took down the Nintendo Power issues that were available for download at the digital library, stating that "The unapproved use of Nintendo's intellectual property can weaken our ability to protect and preserve it, or to possibly use it for new projects”.
On June 1, 2020, four book publishers sued the Internet Archive after its National Emergency Library project went online, a project with which the library lent out digitized versions of books that are still commercially available. The outcome of this lawsuit could have an impact on the fate of the site and the different types of content that can be found there.
If you're interested in development versions, having a well-stocked wallet won't be of much help as legally accessible versions are rare. Sega provided us with a few exceptions by including both the final and an intermediate version of Gunstar Heroes in "Sega Ages 2500 Series Vol. 25: Gunstar Heroes Treasure Box".
Probably unintentionally, the version of Revenge of Shinobi featured in "Sega Smash Pack Volume 1" on PC is a development version. As for “Silent Hill HD Collection”, the choice to base these adaptations of Silent Hill 2 and 3 on intermediate versions (retouched for the occasion) was made by default.
Finally, there is the question of making the design documents available, which again relies largely on the good will of the publishers. In addition to the interviews and documents published on specialized sites and magazines, many artbooks including illustrations, concept art and/or excerpts from design documents have been released in Japan since the end of the 1980s, followed by the US market in the early 2000s and more recently by France.
Although it is not the first representative of its category, Sonic Jam has long been a reference in terms of compilation by offering galleries of documents, information and sometimes previously unseen videos in addition to the first Mega Drive episodes. In 2002, Final Fantasy X came bundled with a making of, following in the footsteps of the movie industry Square was looking towards at the time. For the past few years, some of the games produced by Sony have been the subject of making of accompanying their release and many independent developers regularly communicate on the progress of their games, both on social networks and through their blogs. However, not all games have their own journal or post-mortem. This is where initiatives such as the one launched by the Conservatoire National du Jeu Vidéo in France take over. The latter meets with developers and development companies and requests that part of their archives be made available to the public, with varying degrees of success. Other organizations such as the Musée Bolo in Switzerland (which was given archives by former Infogrames CEO Bruno Bonnell) and Internet Archive have hosted documents of this type.
The issue of preservation is not only a public issue, as companies are (or should be) concerned as well. Apart from exceptional cases such as the Great Hanshin earthquake that destroyed part of the Konami Archives in 1995, development companies rarely communicate about the loss of documents. One of the reasons for this is that in many cases they have disposed of all or part of their archives themselves.
In 2016, 2 Namco employees started the Archive Project to save 350 boxes of documents from the dumpster. The two men had to convince their company to release a budget for this project even though the latter was planning to dispose of the boxes to avoid incurring new storage costs.
At Square Enix, on the other hand, some files could not be saved in time and some games' source codes were lost. In addition to the Mana series previously mentioned, we know that the source code of the PlayStation version of Final Fantasy VIII has disappeared, forcing the developers of the HD version to fall back on the code of the PC version whose music is slightly different. Same with the first episode of Kingdom Hearts; the developers of the 1.5 HD Remix version had to analyze in depth a commercial copy and recreate many assets. An example that echoes the story a developer posted in 2010 in which he explained that, as part of a port of various Midway arcade games, the editor in charge of the project was unable to get his hands on the source code of Spy Hunter, so he had to download the game's ROM in order to extract the graphics via MAME and retrieve the sound files from a fan site, among other things.
---- Interlude: source code-----
Having the ROM of a game does not mean you have the source code of that game. While there are thousands of ROMs of commercial games on the net, source codes are much rarer. In 2012, Jordan Mechner released the source code for the Apple II version of Prince of Persia, which he wrote alone and for which he is the owner, even though the licensing rights now belong to Ubisoft.
More unexpectedly, it was discovered in 2014 that a large part of the source code for the NeoGeo version of Art of Fighting was in a file from its adaptation on PC Engine CD. In all likelihood, the developers of this version had access to the source code of the original version, which was mistakenly included in all copies of the game.
In theory, having the source code of a game facilitates its adaptation on another support since, from one version to another, one can reuse a more or less important part of it, thus reducing the workload and the development costs. The loss of a game's source code therefore greatly reduces the chances of seeing a remastered version of the game. The fallback solution when it is an old game originally released on console or arcade is to use a ROM and an emulator, as it has been done on many compilations or re-releases of arcade games since the early 2000s.
The Nintendo case
The source code for several Nintendo games and systems is now available on the net. Some might see this as a public backup, but the various leaks that happened since 2018 tend to prove that Nintendo knows how to preserve its data (at least for some time) and doesn't necessarily need outside help.
There are several rumours about Nintendo that have not yet been confirmed. One of them is that the source code for The Legend of Zelda: Link's Awakening has been lost, a hypothesis that arose after studying the source code for the DX version of the game, released five years later for Game Boy Color. Another rumour claims that Nintendo is downloading the ROMs for its own NES games, a rumour that found an echo in 2016 after a lecture on emulation was given at the Game Developer Conference. However, if the NES game ROMs used by Nintendo for its Virtual Console look like the ones circulating on the rest of the net, maybe it's because at least one of the persons hired by the Japanese manufacturer to dump the ROMs of its games - Tomohiro Kawase - contributed to the group (iNES) that was dumping ROMs of those same games before joining the company.
The argument that Nintendo is a temple from which nothing comes out seems somewhat exaggerated. The company's games may not have been the subject of as many artbooks as Square Enix's, which, when it doesn't lose its source codes, knows how to showcase its heritage, but it has published many documents in the past relating to series such as Mario and Zelda (which was recently the subject of a series of artbooks), has released new games or versions of new games (Starfox 2 on the Super NES Mini, the European version of Drill Dozer on the Wii U Virtual Console), not to mention the "Iwata Asks" series, which we'd like to see an equivalent in all other development companies. The sense of secrecy that some people might see in Nintendo is probably due in part to the fact that the public is more interested in it than in most of its competitors. The popularity of some of its licenses has few equivalents in the world of video games and pop culture in general. The fact that we still discover old, unreleased Nintendo games nowadays is nothing unusual; tons of games are cancelled without having had a chance to be officially announced.
On the age of the content put online
Two arguments are regularly put forward to minimize the significance of the Gigaleak. According to the first one, the content in question is old and therefore less sensitive or of lesser value than if it were recent documents. This is forgetting that Nintendo has more than once taken ideas or concepts that are sometimes decades old out of its boxes. During the 2007 Game Developers Conference, Shigeru Miyamoto went back over the concept of Miis and explained that it had undergone several changes over the years, starting as a demo on the Famicom Disk System, then reappearing on Super Famicom and 64DD before finally finding its way to the Wii in 2006.
The Mario series has also had its share of ideas that have been put aside then used in later episodes. The idea of straddling a mount, for example, was first suggested during the development of Super Mario Bros. 3 (1988) before being adopted in Super Mario World (1990) with Yoshi. Miyamoto had originally envisioned a horse, but he kept the idea for The Legend of Zelda: Ocarina of Time (1998). A simultaneous multiplayer mode was experimented with at the time of Super Mario Bros. 3 (1988) and will only be included in the series starting with New Super Mario Bros. Wii (2009). Finally, one of the sprites from Super Donkey bears some resemblance with one of those appearing in Super Mario Maker, by its concept.
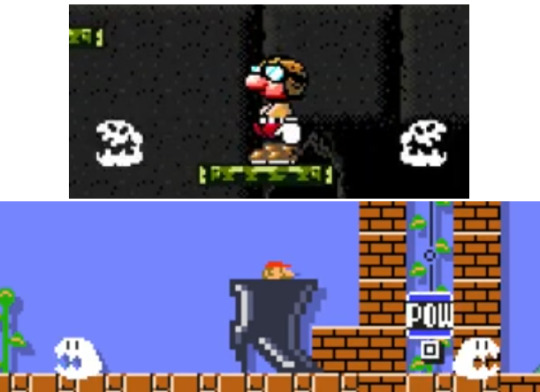
Top: Super Donkey. Bottom: Super Mario Maker.
The second argument concerns the damage suffered by Nintendo and reveals a difference in treatment with what happened in April 2020 when a development version of The Last of Us 2 leaked a few weeks before the game's release. Messages of disapproval and support for the developers seem to have been more popular than those welcoming the leak. In the case of the Gigaleak, Nintendo has often been perceived as a big company, an abstract entity, thus obscuring the fact that its games are also the sum of the work of a group of individuals. In legal terms, unless otherwise stated, the fruit of the work produced within a company is the property of the company. On a personal level, it often happens that a developer has a particular attachment to what he produces.
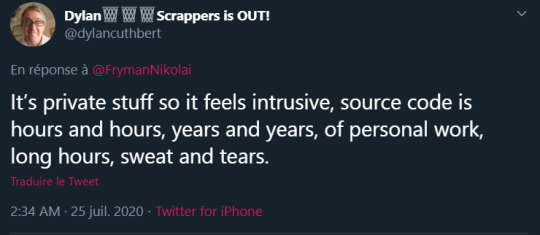
Dylan Cuthbert, in response to a person asking him how he felt, a few hours after the July 24th leak.
While some developers may have been in favour of releasing development versions - Yuji Naka tried to find the prototype of the first Sonic publicly shown in June 1990 to include it in Sonic Mega Collection - or even production documents - Jordan Mechner published the journals he kept during the development of Karateka and Prince of Persia - others are less enthusiastic about making such files available.
By definition, a development version is not a finished product, and while it is natural for a finished product to be made public, this is not necessarily the case with everything relating to the development process. This is not exclusive to video games: many illustrators are reluctant to show their sketches, works in progress or unfinished drawings, no matter how old theirs works are, and the same is true of writers and musicians. As with private conversations, there is the question of respect for developers and their consent. This is obviously not a small obstacle for anyone who wants to preserve and share all the documents relating to the history of video games, but it seems difficult to me to do the work of an archivist or historian (who relies on the work of developers) if it means harming some of these developers even slightly. Of course, you have to hope that as much information as possible will come out and you can work on it in different ways, but you also have to set limits on the methods you can use and not just reason in legal and/or material terms.
Consequences
It is difficult to measure how much will come out of this case, as other elements may be added in the coming days or weeks. Now that the leaked content is circulating, Nintendo will have a hard time getting it off the net and can expect clones of consoles using its own source codes to be produced and marketed in certain countries.
Regarding the emulation scene, it's a bit more complicated. In 1999, source code and documents relating to the Nintendo 64 leaked from Silicon Graphic Inc, a company that produced processors for the Nintendo 64. Known as the Oman Archive, this content was used in the early days of Nintendo's system emulation, which led to quick results. But this use of an illegally obtained code subject to intellectual property law was also a liability for the emulation scene of this machine, which took years to get rid of. Most of the other emulators available online are legal since they were developed with their own code. It's to avoid breaking the law that console BIOSes often have to be downloaded separately (like the source code, BIOS are copyrighted).
The appearance of the Wii source code is therefore a poisoned gift for developers of amateur emulators. It may allow them to understand how Nintendo has done this or that, but they can't reuse it even partially without breaking the law.
Nintendo has probably already apologised to Capcom, Konami and M2 whose files have also ended up on the web. As for the rest, we can only speculate. Will publishers become aware of the interest of a part of their audience in the making of their games and offer more content to satisfy this curiosity (videos from their archives, books, making of, etc.) or, on the contrary, will they lock the doors of their archives by throwing the key into a well? Will security and control on the net increase, further restricting the distribution of certain types of content, be it fan games, ROMs - two categories that Nintendo has been fighting hard against in recent years - or Youtube videos showing things that publishers would prefer not to see on the net (like, say, glitches from Animal Crossing: New Horizons)?
Or maybe nothing will change.
Sources :
Sonic 2
https://web.archive.org/web/20051104100754/http://xbox.gamespy.com/articles/654/654750p4.html
https://info.sonicretro.org/Sonic_Team_interview_by_Kikizo_(November_30,_2005)
Hidden Palace
http://info.sonicretro.org/February_23,_2008_Proto_Release
Pokémon Gold 1997 prototype (2018)
https://twitter.com/sanquii/status/1002107775651057664
Pokémon 2019 leak
https://lavacutcontent.com/pokemon-beta-leaker-statement/
https://helixchamber.com/2019/02/16/what-dreams-may-come/
April-May 2020 leak
https://resetera.com/threads/the-nintendo-leak-saga-continues-biggest-nintendo-leak-in-history-full-source-code-design-files-for-wii-released-online.196683/
https://www.resetera.com/threads/the-nintendo-leak-saga-continues-biggest-nintendo-leak-in-history-full-source-code-design-files-for-wii-released-online.196683/post-32917584
https://nintendoeverything.com/nintendo-suffers-huge-leak-source-code-and-design-files-for-wii-appearing-online/
https://twitter.com/Zetsuboushitta/status/1256320740527239168
https://twitter.com/LuigiBlood/status/1256543745794879488
recent leaks:
1 Ryan Hernandez
https://www.thegamer.com/man-leaked-nintendo-switch-prison-charges/
https://www.justice.gov/usao-wdwa/pr/california-man-who-hacked-nintendo-servers-steal-video-games-and-other-proprietary
2 Tillie Kottmann
https://www.bleepingcomputer.com/news/security/source-code-from-dozens-of-companies-leaked-online/
3 Zammis Clark
https://www.theverge.com/2019/3/28/18286027/microsoft-nintendo-vtech-security-hack-breach-researcher-guilty
https://lavacutcontent.com/pokemon-beta-leaker-statement/
Mail sent by Impero to Zammis Clark - Wack0
https://archive.org/stream/pdfy-fRcZ1TWHaDkwz-Ea/Letter%20to%20Mr%20Zammis%20A%20Clark%20dated%2013%20July%202015_djvu.txt
BroadOn + iQue
https://wiki.mariocube.com/index.php/IQue#BroadOn
July 2020 leak
https://boards.4channel.org/vp/thread/44305551/ppg-leak-time-fuck-ganix
https://www.resetera.com/threads/update-super-mario-64-and-oot-source-leaked-massive-nintendo-data-leak-source-code-to-yoshis-island-a-link-to-the-past-f-zero-and-more.254724/page-62
Aleste and M2
https://twitter.com/M2_STG/status/1014031712672571393
Collection of Mana
https://gameinformer.com/preview/2019/06/11/decades-in-the-making
Vice, Lemonde.fr and Nintendo
https://www.vice.com/en_us/article/7kp7bx/a-massive-leak-of-nintendo-source-code-is-causing-chaos-in-video-games
https://www.lemonde.fr/pixels/article/2020/07/31/nintendo-ce-que-l-on-sait-de-la-fuite-supposee-de-documents-lies-aux-jeux-video_6047809_4408996.html
Cuthbert and Starfox 2
https://twitter.com/dylancuthbert/status/1286789583061934080
Mario World sprite sheet
https://topics.nintendo.co.jp/article/cb34ab17-9135-11e7-8cda-063b7ac45a6d
Luigi in Super Mario 64
https://shmuplations.com/mario64/
Adult Mario in Yoshi's island
http://shmuplations.com/yoshi/
Super Mario Kart before Mario
https://twitter.com/toruzz/status/1287400639165861888
http://iwataasks.nintendo.com/interviews/#/wii/mariokart/0/0
Mario Kart 64 circuit
http://shmuplations.com/mariokart64/
https://twitter.com/AeroArtwork/status/1288299965954088966?s=19
Zelda II SFC in 3D
http://iwataasks.nintendo.com/interviews/#/3ds/zelda-ocarina-of-time/1/1
Zelda OOT in Ganondorf's Castle
https://twitter.com/AeroArtwork/status/1287524648222105607
7 day cycle in Zelda: Majora's Mask
https://twitter.com/Zen64_/status/1287582698085777408
http://iwataasks.nintendo.com/interviews/#/3ds/majoras-mask-3d/0/0
https://www.polygon.com/2015/2/18/8064257/majoras-mask-three-day-timer-week
DragonFly
https://www.unseen64.net/2008/04/14/pilotwings-snes-proto/
Sonic 1 fan recreation
https://www.youtube.com/watch?v=oHtzXzu2BDA
Argonaut
https://twitter.com/corentin_lamy/status/1286932458173276161
https://www.resetera.com/threads/update-super-mario-64-and-oot-source-leaked-massive-nintendo-data-leak-source-code-to-yoshis-island-a-link-to-the-past-f-zero-and-more.254724/post-40826655
Unreal Championship 2
https://twitter.com/Sinoc229/status/1288680503801860096
https://www.ign.com/articles/2011/06/11/epic-games-website-forums-hacked
Akka Arrh
https://arstechnica.com/gaming/2019/04/after-a-lost-atari-rom-leaks-retro-fans-ask-was-it-stolen/
Galaxian
https://www.4gamer.net/games/999/G999905/20180313040/
Firsts emulators
https://emulation.miraheze.org/wiki/History_of_emulation
Namco's Archive Project
https://game.watch.impress.co.jp/docs/news/1205387.html
Spy Hunter
http://web.archive.org/web/20110925185703/http://www.ppl-pilot.com.nyud.net/mame.aspx
Prince of Persia
https://github.com/jmechner/Prince-of-Persia-Apple-II
On the CNJV, Musée Bolo and BNF : "colloque: la conservation du patrimoine vidéoludique" (2017).
Nintendo Power, Internet Archive
https://www.polygon.com/2016/8/8/12405278/nintendo-power-issues-disappear-from-free-online-archive
http://blog.archive.org/2020/06/01/four-commercial-publishers-filed-a-complaint-about-the-internet-archives-lending-of-digitized-books/
Nintendo ROMs
https://www.resetera.com/threads/tomohiro-kawase-mightve-been-hired-by-nintendo-to-put-rom-headers-into-vc-updated-dec-1-2018.64755/
https://twitter.com/LuigiBlood/status/1045348387174977536?s=19
https://www.reddit.com/r/emulation/comments/9msl9j/update_did_nintendo_actually_download_roms_for/e7iemhb/
GDC 2016
https://www.gdcvault.com/play/1023470/-It-s-Just-Emulation
The Legend of Zelda: Link's Awakening source code
https://www.neogaf.com/threads/it-bothers-me-that-nintendo-keeps-ignoring-links-awakening.931702/page-2
Mii
https://unseen64.net/2008/04/14/mii-nes-prototype/
https://www.nintendo.fr/Iwata-demande/Iwata-Demande-Nintendo-3DS/Vol-5-Interview-de-Miyamoto-san-a-la-veille-de-la-sortie-de-la-console/2-Faire-des-personnages-Mii-un-standard-international/2-Faire-des-personnages-Mii-un-standard-international-210297.html
Yoshi and a horse
https://www.nintendo.co.uk/News/2017/October/Nintendo-Classic-Mini-SNES-developer-interview-Volume-5-Super-Mario-World-and-Super-Mario-World-2-Yoshi-s-Island-1290850.html
Multiplayer mode in SMB3
http://iwataasks.nintendo.com/interviews/#/wii/mario25th/2/3
Super Donkey - Mario Maker
https://twitter.com/dbMisadventure/status/1286751468293414912
Dylan Cuthbert
https://twitter.com/dylancuthbert/status/1286822093703622656
Sonic 1 prototype
https://www.gamesradar.com/super-rare-1990-sonic-the-hedgehog-prototype-is-missing/
Oman Archive
https://sm64-conspiracies.fandom.com/wiki/Oman_Archive
Animal Crossing: New Horizons vidéo
https://www.vice.com/en_us/article/m7j7yb/nintendo-takes-down-youtube-video-of-fan-showing-animal-crossing-glitches
89 notes
·
View notes
Text

welcome back to gallagher academy, soo-yun ‘maxine’ brandt ! according to their records, they’re a first year, specializing in research & development; and they did not go to a spy prep high school. when i see them walking around in the halls, i usually see a flash of ( sugar-free mints, a messy low bun, wisps of hair alongside her face, the end of a pen between her teeth, the patek philippe calatrava 4897r-010 in rose gold, off-white pants in every fabric ). when it’s the ( virgo ) ’s birthday on 08/23/1997, they always request their japchae from the school’s chefs. looks like they’re well on their way to graduation.
henlo it me again i hope u guys aren’t sick of me yet bc i have a new bby named max! i’ve written a lot™️ so brace urself but it’s worth it ( i think ) + trigger warnings: death and alcohol dependency under the cut xxx
the basics
full name: soo-yun ‘ maxine ’ brandt
nicknames: max — just max
age: twenty-two years old
birthday: august 23rd, 1997
gender: cis female
preferred pronouns: she / her
sexuality: bisexual
major: research & development ( formerly a b.a. political science degree from yale university )
known languages: english ( native ) / german ( native ) / korean ( native )
background
nationality: american
birthplace: new haven, connecticut, new hampshire
current location: gallagher academy, roseville, virginia
financial status: upper class
religion: non-theistic
appearance
eye color: brown
hair color: black
height: 5′8.5″
notable features: curly hair on lazy days, rosy cheeks
usual mood and expression: calm, furrowed eyebrows whenever her eyes are on work; lethargic and irritable when she’s overworked ( or without alcohol )
family
birth order: second born
parents: soon-bok ‘ vivian ’ jang and stephen brandt ( d. 2018 )
siblings: min-jun ‘ parker ’ brandt ( b. 1995 ) & georgia ‘ gigi ’ brandt ( b. 2001 )
significant others: chris harmon ( 2013-2015 ) / ava carrillo ( 2015-2016 )
her story so far (this is so long n serious lol)
soo-yun 'maxine' brandt was born and raised in new haven, connecticut, to jang soon-bok ( vivian ), a surgeon, and stephen brandt, a ( n allegedly shady ) criminal justice lawyer.
the brandt siblings were raised like any other blue-blooded, very strict but loving household ( strict = mom / loving = dad )
brandt house rules: get straight a’s, follow the 12 am curfew and don't bring anyone home that you know you’d get disowned for. follow those three rules, and you can do whatever you want.
there was pressure for the brandt siblings to be academically accomplished, but it wasn't anything they couldn't handle. they were well-tutored, semi-popular, attractive teenagers, which were common in new haven, and everyone knew they were destined for ivy league.
in high school, she dated chris harmon, and it was the kind of relationship that could only be described as the personification of a kinder egg. sweet on the outside, a waste of time and money on the inside.
which is fine; it took max about 2 months to get over it when they broke up halfway through senior year, because neither of them thought of their relationship going far. the joy of getting into yale ( already expected ) trumped the feeling of losing a boyfriend. she even bet parker $5,000 she'd get early admission. she won.
during college, she had an on-off relationship with ava carrillo for a year, which inevitably became a permanent off. it turned out that it wasn't a good idea to throw herself into a committed relationship the minute she stepped foot into yale. max never had the time, and ava didn't have the patience. at least she tried it tho !
things seemed to be on the up and up for their family, and the worst thing max has ever been through is being awake for 24 straight hours to prepare for a final presentation. but ! you know what they say about the calm before the storm.
( tw: death ) on december 18, 2018, their father unexpectedly passed away from a heart attack during a layover flight in new york. the brandt family was at home when they heard the news. needless to say, they had a quiet christmas and new year.
the family tried to move on as best they could, but the siblings knew their dad's death irreversibly changed their mom. they have a rocky relationship to begin with, the siblings always feeling like vivian never wanted to become a parent and only did so for their father. they have absolutely no mother-children bond, and it got worse when stephen died. being the older brother, parker took it upon himself to take care of vivian, balancing that with running the home stretch with his undergrad degree.
on the other hand, maxine still had a few years left at yale. no amount of therapy helped her cope with the loss of her father, the way her mother seemed to become a shell of herself, how parker had to break the momentum of his career to be there for their mom, and the constant pressure to do good academically.
( tw: alcohol dependency ) it started with buying bottled moscow mules because she didn't like how beer tasted, and she wasn't dumb enough to go straight to hard liquor. just one to take the edge off whenever stacks of coursework became too much, or when her mother would send her an email talking about her day, and she didn't have the courage to read it. then it went from a one, two, three-time thing to a whenever-i'm-upset thing, which slid into a whenever-i-feel-like-it thing. after a while, it became a daylight thing where she would add a splash of soju ( or whatever ) to her lunchtime drinks, and she genuinely thought it was just a funny idea at first. max wasn't the only day drinker in her social group, anyway. she found it acceptable, no different than how other people would pound red bull every 6 hours like it's their life force. it was manageable for her since she was able to schedule when she'd be indisposed, and she still can.
parker had ( and still has ) no clue. despite the two being close, max spared him the burden of having another thing to worry about. as long as she can control it ( or she thinks she can ) then nobody had anything to worry about.
eventually, both maxine and parker were offered the opportunity to join gallagher academy, with parker in line to graduate with honors in global affairs and maxine, not far behind with her own impressive academic portfolio in political science.
though really, her acceptance into gallagher has less to do with her published papers ( still impressive, tho ) and more to do with her covertly helping her father win cases by doing some expert sleuthing, strategizing, witness dispatching + discrediting, sexc breaking and entering, and good, old-fashioned manipulation !
it was something they both wanted; to be a part of the bigger picture in the world, but they knew they couldn't leave their mother alone. parker, who chose to make the sacrifice, let maxine go and stayed behind to take care of vivian.
( but if we’re honest, maxine would’ve left for gallagher regardless if parker was coming with her, but she’ll never tell him that )
despite the guilt and telling parker she wasn't going anywhere ( cough ), he insisted on her taking the once-in-a-lifetime chance to be a part of something they never knew existed. he knew they were going to end up resenting each other if they both stayed. at least one person in the family should be doing something that made them happy.
and so max dropped out of yale and left for roseville, even though she hadn't thoroughly planned out her career trajectory.
she’s eager not just because of the school, obviously. she can't handle going back to their childhood home and seeing how hollow everything is. plus, the immense anger and denial she feels over her dad’s untimely death has no place in new haven anymore.
she promised parker she'd make it up to him, though. somehow, someday.
who is this b*nch
max is relatively easy to get along with, tbh !
she’s a mood matcher; meaning if you’re nice to her, then she’s nice to you ( and if you’re gonna be a punk bitch, then she’ll be a punk bitch right back )
she’s a lil spoiled, lil sheltered, and lil ignorant but her general friendliness makes up for it, she’s the type to be friends with ( almost ) everyone
internally: perfectionist to the point of being ruthless, first place is the only acceptable place, meticulous, neurotic, workaholic, overachiever, if you’re not useful then what’s your purpose?, slightly egotistical, etc etc
externally: caring, protective, and supportive mom friend who just wants people to get their shit together because inadequacy is unacceptable, fixer, likes to dip into different social circles, consciously makes the effort to be more patient with people
she’s incredibly ambitious ? morally ambiguous ? slightly self-serving and self-involved ? her father’s a criminal “justice” lawyer whose clientele doesn’t exactly consist of the beacons of society so... she learned a lot of lessons about how you can win any case in the courtroom if you’re smart enough to a ) make a good story, b ) get the fitting evidence by any means necessary, c ) discredit and discard the necessary people, and d ) be charming and persuasive enough to rock the jury
she’s actively trying to be more open-minded and assimilate to a diverse group of people because back in yale she was definitely in a wasp bubble, and admittedly there are times where she will come off as super snobby without meaning to and tbh sorry about it
she’s still an extremely sociable person because yale also taught her how to network like a motherfucker, and how it’s important to know / be friends with everyone
honestly, intense people turn her off ( both positive and negative ) a little because she can't handle concentrated personalities in one sitting
even though she’s a little intense herself sometimes but it’s fine, we love hypocrites in this house !
neat freak ? but honestly who doesn’t like a friend who squeegees the shower every day and has a tiny can of lysol in their bag and an aroma diffuser with three ( 3 ) oil blends
she’s like... weirdly aggressive sometimes and most definitely has anger issues ( still in denial over her father unexpectedly passing away and getting stuck with a mom who doesn’t like her own children very much )
but also, she’s just agro in general and has a number of physical hobbies. she’s an ice skater, equestrian, a soulcyclist, and a kickboxer. she can fite.
she’s not the type to make fun of herself because she's not at a point where she sees qualities in her that are okay to laugh at ( unless you’re tight )
keeps her negative juju to herself because she’s a very private person
will prioritize work over play because she'd hardwired like that, but that doesn't mean she's anti-fun ( clearly )
definitely needs to loosen up a little that doesn't involve alcohol... jenga perhaps ? or actually try therapy again ?
very effectively sneaky about her growing alcohol dependency ( sugar-free breath mints, brushes her teeth + uses mouthwash after every meal )
dry sense of humor
at all times: wears a 1-carat, emerald cut, pavé diamond ring ( family heirloom ) + carries her trusty black hydro flask with her ( 24 oz. ) and no one is allowed to drink from it !
her signature scent is le labo bergamote 22 🤍
hmu on my discord @ tin#0697 for plottage !
#gallagher:intro#death tw#alcoholism tw#alcohol dependency tw#ps when u see a typo#just close ur eyes
9 notes
·
View notes
Text
He Simply “Hates Christians”: Muslim Persecution of Christians, January 2020
By Raymond Ibrahim
The following are some of the abuses Muslims inflicted on Christians, categorized by theme, throughout the month of January, 2020:
The Slaughter of Christians in Nigeria
During several separate incidents, militant Muslims—whether Fulani herdsmen, Boko Haram, or generic terrorists—continued to attack and massacre several Christians.
As one example, on Friday, January 17, Muslim Fulani tribesmen on motorbikes raided a Christian village at a time they knew people were congregating at the village square where Christian fellowship often took pace. They opened fire. “As the people fled into nearby bushes to take cover, the attackers retreated and left,” an area resident explained. “We are sad about these attacks on our people, which seem to be unending.” Two young Christian girls—Briget Philip, 18, and Priscilla David, 19—were killed, and at least three other teenagers were seriously wounded.
In another incident, “[a]t least 32 people [including a pregnant woman] were killed and a pastor’s house and church building were burned down in two nights of attacks [on predominantly Christian regions] this week by Muslim Fulani herdsmen in Plateau state,” a January 30 report noted.
In the early hours of January 20, gunmen invaded the Lutheran Church of Christ, where its pastor, the Rev. Dennis Bagauri, lived; they opened fire on “and shot him dead at night when all persons in the area had gone to sleep,” a local confirmed.
Boko Haram (whose name roughly means “Western education is a sin”) released another execution video. In it, a masked Muslim child holding a pistol appears standing behind a bound and kneeling hostage, later identified as Ropvil Daciya Dalep, a 22-year-old Christian and member of the Church of Christ in Nations, who was kidnapped on January 9 while traveling to his university, where he majored in biology. After chanting in Arabic and launching into an anti-Christian diatribe, the Muslim child proceeds to shoot Ropvil several times in the back of the head.

Execution of Ropvil Daciya Dalep.
On January 2, Islamic gunmen abducted Reverend Lawan Andimi, a pastor and district chairman of the Church of the Brethren in Nigeria. After the terrorists demanded an exorbitant ransom for his release—two million Euros, which his church and family simply could not raise—they beheaded the married father-of-nine on January 20. Earlier, in a January 5 video that his abductors released, Pastor Lawan had said that he hoped to be reunited with his wife and children; however, “[i]f the opportunity has not been granted, maybe it is the will of God. I want all people close and far, colleagues, to be patient. Don’t cry, don’t worry, but thank God for everything.”
In a statement prompted by all these unchecked killing of Christians, Kwamkur Vondip, the director of legal and public affairs of the Christian Association of Nigeria, blasted the Muslim-led government of Nigeria of “colluding” with the Islamic terrorists:
In the light of the current developments and the circumstantial facts surrounding the prevailing upsurge of attacks against the church, it will be difficult for us to believe that the federal government under President Muhammadu Buhari is not colluding with the insurgents to exterminate Christians in Nigeria, bearing in mind the very questionable leadership of the security sector that has been skewed towards a religion and region. Is that lopsidedness not a cover-up for the operation of the insurgency?.… Since the government and its apologists are claiming the killings have no religious undertones, why are the terrorists and herdsmen targeting the predominantly Christian communities and Christian leaders?
The nonstop massacres of Christians which are met with impunity from the Nigerian government also prompted Bishop Matthew Hassan Kukah of Sokoto to express his disgust with the government in a January 3 report: “The only difference between the government and Boko Haram,” he said, “is that Boko Haram is holding a bomb.” The Nigerian government is “using the levers of power to secure the supremacy of Islam, which then gives more weight to the idea that it can be achieved by violence.”
The Slaughter of Christians Elsewhere in Africa
Kenya: Armed Muslims connected with neighboring Somalia’s terrorist group, Al Shabaab (“the youth”), murdered three Christian teachers during a raid on a primary school in the early hours of January 13; a fourth victim managed to survive.
Another local teacher said “We are sad and at the same time scared because we are targeted for being non-local government workers that belong to the Christian faith.” While discussing this incident, a separate report adds that
Today’s attack comes against the backdrop of a series of attacks from the terrorist group in the last five weeks, leading to the loss of 25 people total … On December 6, 2019, four teachers were among the 11 non-local Christian passengers killed … when al-Shabaab flagged down the bus they were traveling in. The militants separated the passengers and killed those on the spot who failed to recite the Islamic Shahada.
Central African Republic: Militant Muslims shot and killed two Christian pastors as they travelled together by car after having conducted a Christmas Day church service. According to the January 6 report, after murdering the Christians, the “jihadists” continued “shooting, preventing efforts to recover the bodies. The men had to be buried later at the scene of the attack.” The report adds that the “Christian-majority Central African Republic has been blighted by violence since 2013, when the Seleka Islamist armed group briefly overthrew the government…. Christian communities continue to be the targets of attacks…. In November 2018, more than 40 people were killed and many were forced to flee when members of an Islamist militia attacked a Christian mission in Alindao.
Cameroon: “Not a day passes without attacks on the villages on Cameroon’s frontier with Nigeria,” lamented Bishop Bruno Ateba in reference to the Islamic terror group, Boko Haram’s increased incursions into Christian villages in a January 24 report: “Boko Haram is like the beast of the Apocalypse, or a many-headed Hydra—whenever you cut off one of its heads, it seems simply to grow another…. Within my own diocese there have been 13 attacks in the last weeks.” One of those attacks saw a church torched on the feast of the Epiphany. “We are still investigating who was behind the incident, but everything points to the fact that it was a terrorist attack.” Bishop Barthélemy also shared his experiences: “My birthplace, the village of Blablim, no longer exists. The terrorists have murdered a young man of my family and totally devastated the entire village, including the house I was born in. Everybody, with the exception of the sick and elderly, was forced to flee to Mora, 10 miles away. It will be impossible now to gather in the cotton harvest.”
Egypt: On January 12, a Muslim man crept up behind a Christian woman walking home with groceries, pulled her head back with a hand full of hair, and slit her throat with a knife in the other hand. Nearby people restrained the man in al-Wariq, Giza, where the incident took place. Catherine Ramzi was rushed to a nearby medical center, where her throat was sewn with 63 stitches; despite initial heavy bleeding, she managed to survive. The doctor told her that had the knife penetrated one millimeter more—her now mangled sweatshirt had provided some buffering against the knife—it would have reached her jugulars and killed her. During an interview, she explained that she had never before seen the man. All she heard him say during the assault is that she “deserved it” because her “hair was exposed.” He may have also identified her as a Christian because, like many Copts, Catherine bears a visible tattoo of the cross on her hand.
Separately, on January 14, in the region of al-Maraj, another Muslim man tried to slaughter a Christian man with a sharp box-cutter in a public space. He managed only to slice off a portion of the Copt’s ear. After Muhammad ‘Awad, 32, was arrested and questioned as to why he tried to murder Rafiq Karam, 56, he confessed that he did not know him, but that he simply “hates Christians.”
Attacks on Christian Churches
Sudan: Three churches—a Sudan Internal church, a Catholic church and an Orthodox church—were simultaneously burnt down twice over the course of three weeks in the Blue Nile state. The arsonists are suspected to be area Muslims. According to a January 20 statement from a human rights group published in the Sudan Tribune,
On the evening of 28th December 2019, three churches in three different neighbourhoods … were set on fire (burnt) at the same time by arsonists. The worshipers quickly rebuild the three churches using the local materials as it was before. However, for the second time, on the evening of 16th January, the arsonists burnt down the three churches,” said the group…. [L]ocal authorities did not take any measure to protect the churches or to investigate the attacks.
“This incident is true, the three churches were set on fire twice in less than a month,” a local pastor confirmed, adding that “area Muslims were upset about the presence of the churches there, and they are suspected in the fires.”
Philippines: On January 19, police arrested two Muslim men from the Islamic terror group Abu Sayyaf (“the sword-forger”) before they could carry out a planned bomb attack on a Catholic cathedral in Basilan, which both men confessed to. Explosive materials—including more than 3 kilos (6.6 pounds) of assorted nails, blasting caps, 1.5-volt batteries, and wires—were recovered from their hideout. Abu Sayyaf earlier “masterminded a twin bombing at a church on southern Jolo island in January 2019 that left more than 20 people dead.”
Egypt: “The security apparatus prevented Copts in Faw Bahri … from holding the New Year’s Eve prayer on Tuesday, 31 December, in the home of a local Copt. Several Copts gathered in the building and complained about being prohibited from completing the prayer,” the Egyptian Initiative for Personal Rights, a Cairo based think tank with an emphasis on human rights, said in a January 6 press release:
The building that security shut down and prevented prayer inside of is owned by a village Copt and has been used for worship services for four months [and apparently set on fire before for this reason]. Security promised to rapidly secure a building permit for a new church on a 460-meter tract of land purchased by the church a while back. All the necessary surveys have been conducted by official bodies and a wall was built around the plot. All that is needed to start construction is the permits. The closest church to the village is 10 km away…. 3,000 Christians live in the village and used to pray at the house that was shuttered by security. They are all waiting for security to keep its promise to issue permits for the construction of a new church.
The Egyptian Initiative for Personal Rights (EIPR) further criticized the “glacial pace” of the Sisi-government’s hitherto much lauded church construction law adopted in September 2016. More than “three years after its adoption, the church construction law has failed to end violations of Christians’ right to worship and address related sectarian tensions…. [T]he process to regularize the legal status of churches is moving at a glacial pace and lacks transparency,” the press release added:
The EIPR has documented at least 36 cases of sectarian tension and violence since the church construction law went into effect and through the end of 2019, all of them associated with the worship practices. In the same period, interventions by various state institutions led to the closure of 25 churches and the prohibition of collective worship services in the areas in question. In many of these cases, customary reconciliation sessions were convened that concluded with agreements to shut down the church while promising to grant the necessary permits when papers were officially filed. Yet, when church officials applied for official permits, state agencies refused to grant permits or allow them to organize religious services or mass.
Indonesia: Construction of the Bethel Church of Indonesia (GBI) My Home church, plans for which began in 2016, was “abruptly halted” after its building permit was revoked. The church would have served 1,200 registered congregants. In response, on January 16, Amnesty International Indonesia in a statement urged the authorities to annul their decision to revoke the permit:
This is a clear case of persecution and discrimination against a religious minority. The authorities in Tanjungpinang have failed to provide any legal justification for denying this permit and blatantly disregarded the Constitution and their obligations to respect the right to religious freedom and ensure equal enjoyment of human rights.
In a separate case in the same in the region, Muslims halted construction of another church. According to the January 24 report,
Built in 1928, St Joseph’s Catholic Church needs to be renovated and enlarged. Originally it could accommodate 100 people, but now it has more than 700 members. Despite having all the permits, the project is opposed by a small group of young Muslims who threaten action against public order…. Local Catholics are critical of Karimun district chief who, bowing to extremists, has turned against the project even though it has all the required permits.
Although area Christians had “explained to Karimun officials [that] there will be no symbol or ornament outside the church; no cross, no statue, no image of Mary will be displayed visible outside the church”; and although this decision by the Christians was taken reluctantly, as it would make the building look like “a gym or a conference hall”—Muslims still rejected the church.
France: A suspected Muslim man was arrested for desecrating a church, including by writing Koran verses on its walls. According to the January 16 report,
The arrest comes just under a year after another church in Toulouse, the Notre-Dame du Taur, was vandalised by an individual who wrote “Allah u Akbar” on the doors of the building…. Church attacks in France have become a major issue in the last several years, with a report from March of last year claiming that there are as many as three attacks on churches or graveyards per day on average, with a total of 1,063 cases in 2018.
One recent attack “saw human faeces smeared into prayer books at a church in the commune of Tarbes.”
Sweden: After a series of arson attacks on St. Maria Syrian Orthodox Church—one of which was started by someone pouring and lighting gasoline to its exterior—church members have begun to patrol its premises at night in the hopes of preventing further attacks. The January 10 report adds that, “Church attacks in Sweden are relatively uncommon in general but attacks on communities targetted by radical Islamic Sunni extremists, such as Syrian Christians and Shi’ite Muslims, are a concern in the country.”
Attacks on Apostates and Blasphemers
Iran: A court sentenced Ismaeil Maghrebinejad, 65, a Muslim convert to Christianity, to three years imprisonment on the charge of “insulting Islamic sacred beliefs,” said human rights group Middle East Concern in a January 22 report. The Christian was initially charged with “propaganda against the state and insulting the sacred Iranian establishment,” but during “a hearing on 22 October, the judge further accused Ismaeil of apostasy [that is, turning away from Islam, which is a capital crime according to some interpretations of Islamic law] and increased bail demands from 10 million to 100 million tomans (US$9000). Friends provided pledges to cover the bail demands. There were further hearings in November (when the apostasy charge was dropped), December and January.” On January 8, he was found guilty of “insulting Islamic sacred beliefs in cyberspace”—a reference to the claim that “Ismaeil had forwarded a message sent to his phone that was deemed to be insulting to the ruling Iranian clerics”—and sentenced to three year imprisonment. According to a human rights activist associated with the case, the sentence is “a disproportionate reaction to something so ordinary. The other charges that Ismaeil is facing, as well as the quashed charge of apostasy, (are) related to his conversion to Christianity. This may reveal the real reason why he’s been charged with something that most ordinary Iranians do on a daily basis.”
Pakistan: Muslims beat and falsely accused a Christian man, Shahbaz Masih, 40, of blasphemy, which led to his and his friend’s arrest. According to the January 14 report,
His [Muslim] accusers, Shahzaib and Ahmad, hold a grudge against him for being a Christian. On 27 December the two surrounded him at the market, dragged him to a nearby landfill where children collect paper, and beat [him there]. His screams drew the attention of his friend Ishaq [a moderate Muslim], who came to his aid. At that point, the attackers accused both of blasphemy, of burning pages of the Qurʼān. A riot followed, with a nearby mosque calling on Muslims to kill both men. When police arrived, it took the two friends to a police station, questioned them and moved them to a prison, where they are still being held. Human rights groups slam the cops for giving in to extremist pressure and formally recording the case. For their part, radicals threatened to burn the homes of Christians as well as that of the Muslim man, “guilty” of being friends with the Christian. For this reason, the families of the accused went into hiding at an unknown location.
Generic Hate for and Violence against Christians
Egypt: Muslim students at a Minya school “rejected” Mervat Seifein, a school teacher, “for the explicit reason that she is Copt,” that is, a Christian, a report noted. After “a routine promotion in which she replaced the previous school director who is a Muslim,” both boy and girl “students protested and held a sit-in in the school courtyard asking for her removal.” “We don’t want a Copt!” they cried. Some Muslim teachers joined in the protests. Police were unable to disperse the boys’ demonstration in the courtyard. “The girls who demonstrated against me don’t know me,” Mervat responded, “so why the antagonism? Simply because I am Coptic? The only explanation I can fathom is there has been fanatic incitement going on against my promotion, possibly by persons who are purely extremist or who have an interest in keeping me out of that post.” Ezzat Ibrahim, a human rights activist, added that a prompt official investigation should be conducted into the matter:
This is flagrant religious discrimination. It brings to mind the incident in the southern province of Qena when the Islamists rose against the appointment of a Coptic governor in the past-Arab Spring weeks in 2011, and the State gave in and went back on the appointment. It is catastrophic that some 50 or 100 teenage girls or boys should impose their will on the State. And it is equally disastrous that these students were pushed to do so by a group of fanatic Islamists. The positive official response to their preposterous demands amounts to an invitation for religious discrimination. The deputy minister who did that must be dismissed.
Bangladesh: Twelve Christian Rohingya refugees from Myanmar were attacked and injured by Muslim Rohingya “due to their faith.” (Rohingya are overwhelmingly Muslim). “[E]arly Monday [January 27, they] attacked us, the Christians. They looted our houses, and beat up many Christian members. At least 12 Christians have been undergoing treatment at different hospitals and clinics,” a Christian named Saiful reported. “We came under attack due to our faith,” he insisted. “On May 10, 11, and 13 last year, this same group of terrorists attacked us. They want us to leave this camp. They have been attacking us systematically.” Although official Bangladeshi reports denied or underplayed the religious dimension of the attacks, other sources, such as the Rohingya Christian Assembly from India, confirmed them: Muslim Rohingya “attacked the whole Christian community in Kutupalong Camp,” the group said. “Approximately 25 Christian families are displaced. It is winter and very cold, the victims have many minor children with them.” The group added that mobs armed with machetes—“hundreds in many groups”—invaded and destroyed every Christian home at night.
Iraq: Four Christian humanitarian aid workers—three French, one Iraqi—were kidnapped in Baghdad on January 20. No ransom demands were made. According to the report, “The four went missing during a time of heightened tensions in Iraq after a U.S. drone strike on Baghdad airport that killed Iranian Gen. Qassem Soleimani and a senior Iraqi militia commander, Abu Mahdi al-Muhandis. The attack has drawn anger from Iraqi officials from across the political divide …. Iran-backed militia groups have also sworn to avenge the killings.”
Iran: Authorities demolished the grave of the only Christian to be officially executed for apostasy in the Islamic republic. A born Muslim, Pastor Soodmand converted to Christianity before the 1979 revolution. He was arrested, tortured, and eventually executed for apostatizing from Islam to Christianity in December 1990. Now, thirty years later, “all that remains of the pastor’s unmarked grave is the soil under which he was once buried.” His daughter, Rashin Soodmand, who now lives in Europe, gave her reaction:
As a member of the family of this martyred pastor, I can say that the recent disrespect shown to our father’s grave wounded our hearts yet again. Our father was killed cruelly and contrary to the law. They buried him in a place they called la’anatabad [accursed place], without our knowledge, and did not even give our family the opportunity to say goodbye to him, or to see his lifeless body. For years we had to travel to this remote place to visit his unmarked grave, and we were not even allowed to construct a gravestone bearing his name…. We will take our appeal to any relevant national or international institution about this disrespect and cruelty.
The report adds that,
Rev Soodmand remains the only Iranian Christian to have been executed for apostasy following an official court order, although others have been sentenced to death including Rev Mehdi Dibaj and Yousef Nadarkhani. Rev Dibaj was eventually acquitted after nine years in prison but then killed in suspicious circumstances five months later. His body was found days after his disappearance, in a park in a suburb of Tehran, with multiple stab wounds to his chest. Yousef Nadarkhani was also eventually acquitted of the charge but later rearrested on the now much more common charge of ‘actions against national security.’ He is now serving a ten-year sentence in Tehran’s Evin Prison.
Raymond Ibrahim, author of the recent book, Sword and Scimitar, Fourteen Centuries of War between Islam and the West, is a Distinguished Senior Fellow at the Gatestone Institute, a Shillman Fellow at the David Horowitz Freedom Center, and a Judith Rosen Friedman Fellow at the Middle East Forum.
About this Series
The persecution of Christians in the Islamic world has become endemic. Accordingly, “Muslim Persecution of Christians” was developed in 2011 to collate some—by no means all—of the instances of persecution that occur or are reported each month. It serves two purposes:
1) To document that which the mainstream media does not: the habitual, if not chronic, persecution of Christians.
2) To show that such persecution is not “random,” but systematic and interrelated—that it is rooted in a worldview inspired by Islamic Sharia.
7 notes
·
View notes
Text
Wips And Hiatus Fic Masterlist
Okay, so these are Also Important! Hiatus can always change for me, if given inspiration.
Unmoving Fics-
The Affairs of Dragons- In a world where humans' made pacts and families with creatures from myth and folklore in order to gain Quirks for their descendants, there's a whole other social level based on how one's quirk is obtained.In a world where Pacted quirks are both the most common and most desired, what's young Izuku to do when he's seemingly a genetic throwback, being more of a dragon than his firebreathing father?Why, work past the prejudices and become a great hero, of course! Dragon Izuku, Dragon AfO, AfO is a Bastard Man, Quirked!Izuku, AfO!Izuku, Myths And Legends Are Real, Quirks are Divine/Spirit Intervention
Status: Needs more current motivation. Later events are planned, but not so much for the tiny noodle.
AfO Needs Parenting Classes- A project for dfo week... of December 2018.
Status: Half-written? Would need actual motivation to finish the prompts at this point, though.
Starfall- Izuku and Shinsou grow up together as twins, under the eyes of their adoptive fathers. However, when you're a problem child with an unusual quirk, things don't always go as expected. Quirked!Izuku, Brother Shinsou, Human Experimentation, Character Death, Parental Erasermic, Teen Parents
Status: Semi-Hiatus. Probably facing a rewrite. Was the very first fic I posted, not entirely sure where I want to go with it, but the quirk ideas were interesting.
Flying On Wings Not Your Own- Izuku Midoriya lost almost everything to his father's ambitions. Now, he has to learn to achieve his dreams with the talents he was blessed with, and the quirk he had forced upon him. Quirked!Izuku, Raised By Villains!Izuku, Villain!Hisashi, Possessive Shigaraki
Status: Next chapter is one third written, roughly. Semi-hiatus Another early fic, also facing a possible rewrite if I get more inspiration for it.
I Am Here- The life and times of one Yagi Toshinori, and how he became The Symbol Of Peace. Pre-Canon, Toshinko
Status: Next chapter is half-written, probably going to be a permanent hiatus unless I have new ideas to differentiate it from all the wonderful fics like it out there.
Unposted Wips-
Bloom Au- Strong emotion towards another person causes flowers representing the emotions to bloom on the other person upon touch. Blooming can only happen when both people feel something with a similar intensity towards the other. Such emotions can be hidden of course, but the backlash is that the repressed emotion will flower in the feeler’s lungs or throats.
Another part of blooming is that repeated touches in the same area cause a different sort of bloom. A flower unique to the person will form on the skin like a living tattoo, moving whenever the person who left it is thinking about the person who has it. As such, parents are very careful to handle babies so that these flowers do not bloom around the mouth. Flower Language, Hanahaki, Izuku leaving his feelings all over everyone, Starting as a 5+1
Search Au- Midoriya Inko (nee Shiretoko) lives a happy life with her husband and son. Little Izuku inherited Search from his Aunt Tomoko, and dreams of being part of a successful hero team like her Wild Wild Pussycats. First chapter is partially written. Quirked!Izuku, Rarepair, Good Dad Hisashi, All The Aunts (And Uncle)
Marks Of Light Au- An AU of @pocketramblr‘s wonderful MOL au, and inspired by her Family Affairs. Just remembered due to an ask she got about it, whether or not the fic was DFO. Well, this fic is DFO, with some nice Brozawa thrown in. But, it won’t be posted until after a certain scene in the main mol story. Dragon!Izuku, Dragon!AfO, Dragon!Aizawa, AfO is a Bastard Man, Brozawa, MOL
Stoat Au- The most crack of all my ideas, though treated seriously. It’s a canon between @pocketramblr, @gentrychild and I that Nedzu is not a mouse, dog or a bear. But rather a stoat (or ermine), who is in his winter coat all year round due to the experiments he went through.
Now, in this au of mine... Nedzu is not the only stoat with a quirk. The laboratory he’s bred in is studying and creating quirked animals, with the funding of Doctor Garaki to study quirk copies and inheritance. Inko is another intelligent stoat, though hers is considered a ‘side effect’, as she has her canon quirk. Inko and Nedzu escape the lab together during a hero raid, and find themselves in the very strange world that is outside of their experiences. Extreme Rarepair, Weasel!Midoriyas, Animal Experimentation, Animal Rights, Quirked!Izuku
3 notes
·
View notes
Text
EVERYBODY LOVES FIN: EPISODE 19
Canucks Twitter has never been more passionate, divisive and heavily opinionated; let’s go with an all-encompassing—vibrant. Any fan base is a community of people with thoughts to share, and luckily for others, content to create for a wider audience. I have to admit, I’ve been largely on the outside of Canucks Twitter, merely because I tend to direct my opinions to a TV screen rather than on social media. That being said, lately my sister, Pass it to Bulis contributor and Botchford Project recipient, Natalie Hoy, has been encouraging me to listen to more Canucks-centric podcasts. It’s been a fun time.
2010s: Does Vancouver really need two all-sports radio stations?
2020s: Does Vancouver really need 741 Canucks podcasts?
— Jyrki21 (@Jyrki21)
June 9, 2020
The world of ‘audio blogging’ has only grown over the past few years. Listeners are able to multi-task - exercising, cooking, cleaning, driving or on public transit - while plugged in to a new episode on practically any personal device. It’s a form of entertainment, often interactive, and a perfect creative outlet for amateur (and experienced) broadcasters looking for a new project. There is no shortage of podcasts courtesy of Canucks Twitter, a testament to the commitment and drive of fans, and the accessibility of the art form. With the Qualifying Round of the Stanley Cup Playoffs just about underway, there is much to be talked about. Let’s take a look at what’s out there.1
C4 Podcast
Founded: July 2013
Players: Chris Golden (@lyteforce), Anna Forsyth (@aforsyth03),Matt Lee (@mattlee_61)
Premise: The longest-running, active Canucks podcast (birthed from Canucks Hockey Blog) has been on-air for 7 years! Originally co-hosted by Chris and parody song creator Clay Imoo (@CanuckClay), the podcast offers commentary about current Canucks and NHL affairs, prospects, expectations, reminiscing on the team’s past (memories of the retired taco lover Eddie Lack and past playoff runs), and features interviews with guests. This past season, they’ve had Patrick Johnston (The Province), Satiar Shah (Sportsnet 650), Cam Robinson (Elite Prospects, Dobber Prospects) and Dan Murphy (Sportsnet) in the hot seat.
Twitter | Patreon | Discord | Listen
In the "longest-running" #Canucks #PodcastLikeThat, @risingaction joins @aforsyth03 @lyteforce & @mattlee_61 to talk about the summer training camp so far, how the Canucks match against the Wild, Rathbone, Tryamkin and so much more! https://t.co/ACreWPcPWC
— #PodcastLikeThat (@TheC4Podcast)
July 21, 2020
Area 51
Founded: December 2019 (relaunch)
Players: Sean Warren (@SeanyeWest234), Samantha (@samanthacp_), Malcolm Ert (@malcolmert), Bradley Thomas (@bradthomas_96), Eric (@breakawayeric), Bailey Broadbent (@baileybroadcast)
Premise: Area 51 celebrated a relaunch last December since their inception in July 2019, and in May welcomed a team to join host Sean Warren. Aside from their cool, alien conspiracy branding, at the mic they cover a broad range of hockey talk with notable guests (writers and broadcasters in the media, content creators, musicians, WHL players, fellow blog/podcast owners, Canucks Autism Network). I love that they’ve started to cover important topics beyond the gameplay, like anti-racism, inclusivity, and diversity in sports, and have actively sought out the guests to do so.
Twitter | Instagram | Listen
HERE WE GO! @CanuckClay enters A51 in GLCPC to discuss:
-Sports debates
-Being a hockey media creator
-Plan a Vegas trip
-Drinking and Parenting tips
And complete the famous Guest Shootout!
Find out whether Clay is responsible for the Luongo trade!https://t.co/Zg629tWvLG
— Area 51 Hockey Podcast (@Area51Hockey)
July 24, 2020
Cap Space Wins Cups
Founded: February 2020
Players: Hassan Ahmed (@_hassanahmed9), Ahsan Ahmed (@ace103196), Hussain Ahmed (@hussain11ahmed)
Premise: The newly formed podcast has a light, humorous tone - evident by their inaugural episode introduction about their lack of social media followers. They cover quick hits of the Canucks week, roster situations, hockey culture, and of course, cap space. They’ve hosted fellow podcast hosts and media (Satiar Shah, J.D. Burke, Matthew Sekeres, Jeff Paterson), and even a fellow Burnaby kid, Massimo Rizzo. Rizzo was a 2019 Carolina Hurricanes draft pick. It’s clear they have a lot more to share, including takes in on their corresponding blog – see: How the Canucks Can Acquire Dougie Hamilton & Build a Cup Contender. I’ll read anything related to Dougie Hamilton.
Twitter | Instagram | Listen
🚨🚨Another HUGE ANNOUNCEMENT the boys have their own website 🚨🚨https://t.co/JfQXqiXcz2, the site has all the podcast epidoes and links to all their social media. The boys have also started blogging and have 2 big article out already! It’s 100% free sign up on the site to L&C!
— Cap Space Wins Cups Podcast (@capspacecups)
June 21, 2020
The Broadscast
Founded: July 2020
Players: Vanessa Jang (@vanessajang), Georgia Twiss (@georgiatwiss), Samantha (@samanthacp_), Mallory (@sports_lesbian), Danielle Huntley (@danihuntley)
Premise: Your ‘local hockey girl gang’ talks Canucks, sports culture, and soap operas. All 5 hosts have a significant following on Twitter and are bold and uncompromising, which makes for great statements and table chatter. This was written with only their Teaser episode released, but you can expect no shortage of pop culture references, fashion discussion, NHL wives and girlfriends (WAG) and pet content, along with team analysis. It’s trailblazing for a group of females in Vancouver to start their own podcast that’s hockey-focused, meant to be a casual chat amongst friends. They know the team, know their media, can gossip, and are having fun with it.
Twitter | Instagram | Listen
The Broadscast is officially LIVE!! 🎙 Just 5 girls and some light-hearted hockey talk with a soap opera twist. Catch our teaser episode NOW on your podcast medium of choice!https://t.co/91KE8LnOJE pic.twitter.com/XH0fIfhmHy
— The Broadscast (@BroadscastPod)
July 27, 2020
PUCKS ON NET
Founded: September 2013
Players: Ryan Schaap (@schaaptop), Geeta Reddy (@geetanjalireddy), Paul McLellan (@McLellanPaul), Dave McPhail (@PucksOnDave)
Premise: The group of 4 has created a casual, honest atmosphere with their roundtable conversation. They’re good friends, which equates to great camaraderie. They run a ‘contradictory’ fantasy hockey league and don’t talk ‘fancy stats’ (while still being very knowledgeable). I think they’re engaged with their listeners, and relatable as human beings amongst their talk of Tim Hortons NHL trading cards, player safety, current signings and acquisitions, and Green Day at the All-Star Game. Reaching 7 years of consistent hockey talk and recapping the team’s evolution is a feat in its own.
Twitter | Patreon | Instagram | Listen
And on Sunday, Ryan sat down with his old man for Father's Day to talk about growing up playing minor hockey in Calgary, bonding over the Vancouver #Canucks and even his words of wisdom when it comes to talking to your kids about drugs.https://t.co/BaQFM53Yws
— PUCKS ON NET (@Pucksonnetca)
June 24, 2020
The Canucks Conversation
Founded: November 2018
Players: Chris Faber (@ChrisFaber39), David Quadrelli (@Quadrelli)
Premise: Faber was joined by Quads in 2020, and the pair has perhaps the most praised local podcast so far. They’re both BCIT Radio Arts and Entertainment students (and writers for CanucksArmy), and their dedication, preparedness, branding and reporting level are top notch. They break down topics with great chemistry and perception - roster moves, Nikita Tryamkin, Olli Juolevi, and the Judd Brackett situation. Some of their notable guests include Utica Comets Kole Lind and Brogan Rafferty, and ‘bionic’ Finn Sami Salo.
Twitter | Patreon | Instagram | Listen
🎉SURPRISE! 🎉
Episode 91:
“Jake Jets out of the lineup” ft.@CraigJButton
We dropped our episode early!
Craig Button stops by to chat about the NHL and #Canucks prospects.
We breakdown the exhibition game against the Jets & some exciting news at the end!https://t.co/NMWBVOU7ko
— Canucks Conversation Podcast (@CanucksConvo)
July 30, 2020
Canucks & Pucks
Founded: April 2019
Players: Matthew Zator (@MatthewZatorSC)
Premise: Matthew Zator, writer for The Hockey Writers and Hockey Ops Director at Overtime Heroics, made a return to the airwaves this past July (after a lengthy regular season hiatus). Since getting back up and running, it’s full steam ahead – Zator has been joined by contributors from The Hockey Writers, The Canuck Way, college hockey newsletter Fresh Ice, and fellow podcast hosts. He has good insight and as a writer who goes into depth about NHL draft picks, the Vancouver Giants, and both the Nucks’ positives and negatives in his work, it gets noticeably transferred to the on-air conversation.
Twitter | Listen
🚨 NEW EPISODE 🚨
Episode 7 ft @CanuckClay, @JDsays2much, and @BaileyAJohnson_!
- #Canucks & #mnwild with Jack & Clay
- Will Lockwood and Quinn Hughes with Bailey
- The Mailbag segment debuts and of course news from the #NHL and @TheHockeyWriter! #THW https://t.co/lW9FQms35P
— Canucks & Pucks Podcast 🏒🎙️ (@CanucksPucks)
July 28, 2020
Canucks Speakeasy
Founded: August 2019
Players: Pete Edwards (@pete_gas), Doug (@dougvenn)
Premise: Pete and Doug are 2 “mildly educated Canucks die-hards” who chat about current team news and trending topics. They’ve covered trade talk, the Collective Bargaining Agreement, prospects at the World Juniors, scouting, and the BLM movement. They’re occasionally joined by guests including podcast friends, and fellow fans/Tweeters Chris Conte, Jenna Fabulous and Ray Hatt.
Twitter | Listen
We're back with Episode 37: Powderkeg.
Playoffs, play-ins, Judd and BLM are all discussed. Give'r a listen!https://t.co/dwoEQVNudThttps://t.co/7ZSogAjWsuhttps://t.co/r5HqX26czU pic.twitter.com/QKScnR9Q6G
— Canucks Speakeasy (@CanucksSpeak)
June 4, 2020
The LarschCast
Founded: June 2019
Players: Tej Dhaliwal (@DrTejDhaliwal), Sat Oberoi (@SatOberoi), Nav Dosanjh (@NavDosanjh1983), Ryan Cassels (@cassels_music)
Premise: The Larschcasters are known for their entertaining banter and debates, mostly on hockey and a little NFL. They’ve picked the minds of seasoned media (Scott Oake, James Duthie, Joey Kenward), legendary broadcaster Jim Robson, and former Canucks Kirk McLean, Chris Higgins and Shane O’Brien. They’ve been generating healthy content during the pandemic, including a spirited debate with Minnesota Wild podcast hosts, discussing media personnel moves, prospects, NHL Award contenders, and the toxicity in the Vancouver Canucks market. In June, they released a special with hockey coach/trainer Jennifer Chefero, sharing her story facing sexual abuse and harassment in her career, while candidly discussing women’s rights and sports culture.
Twitter | Facebook | Listen
Episode 61 ft. @hustlerama!#NHLJets centric epi, with an outlook of the Jets vs #flames. Not a lot of love for Calgary in this one😬. Also insights into the #nhlbubble, before ending with #Canucks talk & Rapid Larsch!
🍎:https://t.co/vZ2lyQ9zoO
Spotify: https://t.co/XdV1y3ls7V
— The LarschCast (@larschcast)
July 29, 2020
The PP1 Podcast
Founded: October 2019
Players: Brayden Ursel (@bkursel23), Ted (@tee3ree), Ryan Hank (@always90four)
Premise: A tagline like “three guys from Kelowna bringing the heat and spitting the takes” doesn’t need further explanation. Appearing at the beginning of this season, the podcast (which features writers from The Canuck Way and CanucksArmy) has had some nice guests like the Canucks inaugural captain Orland Kurtenbach, retired centre and current Kelowna Rockets Assistant Coach Vern Fiddler, and Paul “Biznasty” Bissonnette. They’ve been nominated for Kelowna Now’s Best Local Podcast, and have a ‘Dudes and Guys’ segment where they pit 2 players against one another and talk it out (criteria is debatable).
Twitter | Listen
Episode 46: Bouncy Castles, Boeser Bombshells, & Backchecking w/ @mattsekeres. We chat Boeser rumours, cap crunch, Rathbone, Tryamkin, Markstrom, Sundin vs. Vanek, the best cold-open since Nikolay Goldobin, and how you can win a #Canucks jersey. https://t.co/KouGJr6GKH
— The PP1 PODCAST (@ThePP1Podcast)
July 15, 2020
The SCT Show
Founded: September 2018
Players: Nam Mann (@CanuckAgent007), Tanbir Rana (@TRana87)
Premise: SCT is Strictly Canucks Talk. Aside from reminiscing about ‘where were you when’ pivotal moments in franchise history occurred and the regular shop talk of performance and #NamStats, they draw in guests to talk about trade value (The Athletic’s Harman Dayal) and stickhandling (specialist/trainer Pavel Barber). They’ve also hosted local defenceman and last year’s 4th overall draft pick Bowen Byram, and hockey analyst/retired winger Anson Carter for a chat about the pressure of the market in Vancouver and the Sedins. Like any good heated debate, there are also trade and Team Tank vs Playoffs scenarios.
Twitter | Listen
.@CanuckAgent007 has a proposal to get Loui Eriksson off the #Canucks books 🤔
EP 14 - Links below ⬇️
🍎 https://t.co/Z9snNdSuI1
📱 https://t.co/AJILh0IaWJ pic.twitter.com/LZblDE8GLW
— The SCT Show (@SCTShow)
July 17, 2020
Johnny Canuck Talk
Founded: August 2019
Players: Adrian J. Haug (@adrianjhaug), Roy Styles (@roy_styles)
Premise: Takes from 2 arm chair GM’s, the pair discuss a wide variety of topics like losing streaks, hockey safety, report cards, line-ups, and trade deadline. They’ve also shared an insightful chat with Harman Dayal (The Athletic) about his career and the late and great Jason Botchford. It’s laid-back and conversational, with mentions of farmers’ tans, celebrating birthdays during quarantine, and the school system strung across introductions. What’s cool is they record the podcast from near and far away places – Kamloops, BC and Germany (!).
Twitter | Listen
(1) Episode 37 is uploading now! @roy_styles and I talk #Canucks #hockey and @Canucks topics, issues, news, etc. We also talk about the incredible impact our Jim Carey impressions have had on our wives. Yikes.
Featuring tweets from: @Canuckgirl20 @TSN1040 @DanRiccio650 pic.twitter.com/6oA7mZh6jb
— Johnny Canuck Talk (@JohnnyCanuckPod)
June 28, 2020
1 This list is not exhaustive, but there is something for everyone and I hope you find your Canucks fix. There can be an argument made that the podcast market is oversaturated, but I like to see it as an opportunity for any fan or audio bird to let their voice be heard! So, don’t be negative about it.
Posted by: Chloe Hoy
#Everybody Loves Fin#Canucks#Vancouver Canucks#Chloe#Canucks Twitter#blog#hockey blog#NHL#nucks#nhl canucks#Podcast#Apple Podcasts#sports#hockey#Podcaster#Spotify Podcast
1 note
·
View note
Text
Special counsel Robert Mueller’s team indicted or got guilty pleas from 34 people and three companies during their lengthy investigation.

That group is composed of six former Trump advisers, 26 Russian nationals, three Russian companies, one California man, and one London-based lawyer. Seven of these people (including five of the six former Trump advisers) have pleaded guilty.
If you also count investigations that Mueller originated but then referred elsewhere in the Justice Department, you can add a plea deal from one more person to the list.
It’s a sprawling set of allegations, encompassing both election interference charges against overseas Russians, and various other crimes by American Trump advisers.
However, Mueller did not allege any crimes directly connecting the two — that is, that Trump advisers criminally conspired with Russian officials to impact the election.
Other reported focuses of Mueller’s investigation — such as potential obstruction of justice by the Trump administration — also did not result in any charges.
Justice Department officials told reporters that this is the final list, and that no more indictments are coming from the special counsel’s probe.
The full list of Mueller indictments and plea deals
1) George Papadopoulos, former Trump campaign foreign policy adviser, was arrested in July 2017 and pleaded guilty in October 2017 to making false statements to the FBI. He got a 14-day sentence.
2) Paul Manafort, Trump’s former campaign chair, was indicted on a total of 25 different counts by Mueller’s team, related mainly to his past work for Ukrainian politicians and his finances. He had two trials scheduled, and the first ended in a conviction on eight counts of financial crimes. To avert the second trial, Manafort struck a plea deal with Mueller in September 2018 (though Mueller’s team said in November that he breached that agreement by lying to them). He was sentenced to a combined seven and a half years in prison.
3) Rick Gates, a former Trump campaign aide and Manafort’s longtime junior business partner, was indicted on similar charges to Manafort. But in February 2018 he agreed to a plea deal with Mueller’s team, pleading guilty to just one false statements charge and one conspiracy charge. He was sentenced to 45 days in prison and 3 years of probation.
4) Michael Flynn, Trump’s former national security adviser, pleaded guilty in December 2017 to making false statements to the FBI.
5-20) 13 Russian nationals and three Russian companies were indicted on conspiracy charges, with some also being accused of identity theft. The charges related to a Russian propaganda effort designed to interfere with the 2016 campaign. The companies involved are the Internet Research Agency, often described as a “Russian troll farm,” and two other companies that helped finance it. The Russian nationals indicted include 12 of the agency’s employees and its alleged financier, Yevgeny Prigozhin.
21) Richard Pinedo: This California man pleaded guilty to an identity theft charge in connection with the Russian indictments, and has agreed to cooperate with Mueller. He was sentenced to 6 months in prison and 6 months of home detention in October 2018.
22) Alex van der Zwaan: This London lawyer pleaded guilty to making false statements to the FBI about his contacts with Rick Gates and another unnamed person based in Ukraine. He was sentenced to 30 days in jail and has completed his sentence.
23) Konstantin Kilimnik: This longtime business associate of Manafort and Gates, who’s currently based in Russia, was charged alongside Manafort with attempting to obstruct justice by tampering with witnesses in Manafort’s pending case last year.
24-35) 12 Russian GRU officers: These officers of Russia’s military intelligence service were charged with crimes related to the hacking and leaking of leading Democrats’ emails in 2016.
36) Michael Cohen: In August 2018, Trump’s former lawyer pleaded guilty to 8 counts — tax and bank charges, related to his finances and taxi business, and campaign finance violations — related to hush money payments to women who alleged affairs with Donald Trump, as part of a separate investigation in New York (that Mueller had handed off). But in November, he made a plea deal with Mueller too, for lying to Congress about efforts to build a Trump Tower in Moscow.
37) Roger Stone: In January 2019, Mueller indicted longtime Trump adviser Roger Stone on 7 counts. He accused Stone of lying to the House Intelligence Committee about his efforts to get in touch with WikiLeaks during the campaign, and tampering with a witness who could have debunked his story. He was convicted on all counts after a November 2019 trial.
Finally, there is one other person Mueller initially investigated, but handed over to others in the Justice Department to charge: Sam Patten. This Republican operative and lobbyist pleaded guilty to not registering as a foreign agent with his work for Ukrainian political bigwigs, and agreed to cooperate with the government.
That’s the full list - MORE HERE: https://www.vox.com/policy-and-politics/2018/2/20/17031772/mueller-indictments-grand-jury
8 notes
·
View notes
Text
Chinese Artificial Intelligence vs US Artificial Intelligence
http://cset.georgetown.edu/wp-content/uploads/CSET-The-Question-of-Comparative-Advantage-in-Artificial-Intelligence-1.pdf
....Since Chinese companies like Huawei and ZTE were added to the Department of Commerce’s Entity List,15 China’s determination to pursue indigenous innovation has only intensified.16
In cases where the United States has stymied Chinese advances with unilateral export controls but substitute options remain available, China has typically managed to find workarounds or substitute components within a short timeframe.17 The challenge will be for China to replicate core innovations in semiconductor technology where no comparable substitute exists.
China’s model of development through state subsidies appears ill-suited for the semiconductor industry, which is fast moving and requires both business acumen and sizable technical expertise.18 Nearly 20 years after PRC science and technology leaders set out to develop a competitor to the x86 processor, Chinese alternatives remain limited and significantly behind U.S. counterparts. State-led pushes in the 1990s to establish a foothold in the chip fabrication market failed to produce commercially viable firms capable of keeping up with foreign leaders. China’s most successful fab, the Semiconductor Manufacturing International Corporation (SMIC), kept PRC’s S&T officials at arm’s length during its early development.19 The current state drive, led by the
Center for Security and Emerging Technology | 7
National Integrated Circuit Fund, attempts to learn from prior mistakes and introduces more market mechanisms than in the past. However, many experts are skeptical that this state-led push will be sufficient to wean China off foreign chips.20
Regardless of the Chinese model’s efficiency, the reality is that China is building its manufacturing capacity to compete in semiconductors as the United States loses indigenous capability and outsources semiconductor manufacturing to foundries elsewhere.21 Technological trends may also play out in China’s favor. As Moore’s Law reaches its end, squeezing additional computing power out of chips will require new materials and specialized AI chip architectures.22 The United States enjoys a dominant market share in leading-edge GPU (Graphics Processing Units) and FPGA (Field Programmable Gate Array) design, as well as many of the top AI-relevant ASICs (Application Specific Integrated Circuits). For the time being, China’s leading AI chip designs often incorporate U.S. and allied designs. Yet as technological progress slows and evolves, China may have an easier time catching up.
Chinese players are starting to break into the AI chip space on some fronts. China’s AI chip unicorns Cambricon and Horizon Robotics, for example, have attained multi-billion-dollar valuations within just a few years.23 Huawei has launched its own AI chip, Ascend 910, designed to process efficiently the massive amounts of data often required to train algorithms.24 Alibaba has also created a new AI chip, known as the Hanguang 800, which it claims possesses the computing capabilities of 10 GPUs.25 Alibaba’s chip subsidiary Pingtouge (平头哥) open-sourced its microcontroller design platform on GitHub in order to make chip design more accessible.26 So far, however, PRC AI chips have primarily achieved successes in “inference,” the process of running existing neural networks; the process of training continues to rely primarily on GPUs produced by NVIDIA.27 Whether Chinese companies like Huawei can compete with NVIDIA in the AI training space remains to be seen.
Endnotes
1 K. A. Konrad, “Dynamic Contests and the Discouragement Effect,” Revue d'Économie Politique (2012); C. Harris and J. Vickers, “Racing with Uncertainty,” Review of Economic Studies 54, 1 (1987); I. K. Wang, L. Qian, and M. Lehrer, “From Technology Race to Technology Marathon: A Behavioral Explanation of Technology Advancement,” European Management Journal 35, Issue 2 (April 2017): 187-197.
2 This policy brief is not intended to be comprehensive, but rather proposes a framework for assessing relevant data and measures that bear on current debates in AI. We are indebted to the robust research and existing literature in the field. See, e.g., Michael C. Horowitz, Gregory Allen, Elsa Kania, and Paul Scharre, “Strategic Competition in an Era of Artificial Intelligence,” Center for a New American Security, July 2018, 8.
3 Deborah J. Jackson, “What is an innovation ecosystem,” National Science Foundation, 1, 2011. On AI in particular, see “AI is a national security priority — here’s how we cultivate it,” The Hill, February 20, 2019, https://thehill.com/opinion/cybersecurity/430765-ai-is-a- national-security-priority-heres-how-we-cultivate-it; For another excellent evaluation of the importance of the overall ecosystem to AI development, see: Lindsey R. Sheppard and Andrew Philip Hunter, “Artificial Intelligence and National Security: The Importance of the AI Ecosystem,” Center for Strategic and International Studies, November 5, 2018,https://www.csis.org/analysis/artificial-intelligence-and-national-security-importance-ai- ecosystem.
4 Andrew Imbrie, “Mapping the Terrain: AI Governance and the Future of Power,” Survival (blog), December 17, 2019, https://www.iiss.org/blogs/survival- blog/2019/12/mapping-the-terrain-ai-governance.
5 See, e.g., Andrew Imbrie, “Artificial Intelligence Meets Bureaucratic Politics,” War on the Rocks, August 1, 2019, https://warontherocks.com/2019/08/artificial-intelligence-meets- bureaucratic-politics/; Michael C. Horowitz and Lauren Kahn, “The AI Literacy Gap Hobbling American Officialdom,” War on the Rocks, January 14, 2020,https://warontherocks.com/2020/01/the-ai-literacy-gap-hobbling-american- officialdom/.
6 “Winning the Future: A Blueprint for Sustained U.S. Leadership in Semiconductor Technology,” Semiconductor Industry Association, April 2019,https://www.semiconductors.org/wp-content/uploads/2019/04/FINAL-SIA-Blueprint- for-web.pdf.
7 We define “AI chips” to include GPUs (Graphics Processing Units), FPGAs (Field Programmable Gate Array), and ASICs (Application Specific Integrated Circuits) specialized for high speed and efficiency for AI algorithms, among others.
8 See, e.g., “Re: ANPRM on Review of Controls for Certain Emerging Technologies (BIS- 2018-0024),” Center for Security and Emerging Technology, January 10, 2019,https://cset.georgetown.edu/wp-content/uploads/2019-01-10-Dept-of-Commerce-GU-
Center for Security and Emerging Technology | 36
CSET-ANPRM-on-Export-Controls-for-AI.pdf. For a recent example, see Alexandra Alper, Toby Sterling, and Stephen Nellis, “Trump Administration pressed Dutch hard to cancel China chip-equipment sale: sources,” Reuters, January 6, 2020,https://www.reuters.com/article/asml-holding-usa-china/rpt-insight-trump-administration- pressed-dutch-hard-to-cancel-china-chip-equipment-sale-sources-idUSL1N29802U.
9 “Trade war forces Chinese chipmaker Fujian Jinhua to halt output,” Financial Times, January, 28, 2019, https://www.ft.com/content/87b5580c-22bf-11e9-8ce6- 5db4543da632.
10 For one prominent example, see the case of Fujian Jinhua. Paul Mozur, “Inside a Heist of American Chip Designs, as China Bids for Tech Power,” New York Times, June 22, 2018,https://www.nytimes.com/2018/06/22/technology/china-micron-chips-theft.html.
11 Some U.S. firms made the move abroad in response to export controls. See “U.S.-based chip-tech group moving to Switzerland over trade curb fears,” Reuters, November 28, 2019,https://www.reuters.com/article/us-usa-china-semiconductors-insight/u-s-based-chip- tech-group-moving-to-switzerland-over-trade-curb-fears-idUSKBN1XZ16L.
12 Chris Gillis, “US exporters attempt to head off new content restrictions,” American Shipper, December 9, 2019, https://www.freightwaves.com/news/us-exporters-attempt-to-head- off-new-content-restrictions.
13 Timothy P. Morgan, “Huawei Jumps into the Arms Server Chip Fray,” The Next Platform, January 8, 2019. See also Saif Khan, “Maintaining the AI Chip Advantage of the United States and its Allies,” Center for Security and Emerging Technology, December 2019,https://cset.georgetown.edu/wp-content/uploads/CSET-Maintaining-the-AI-Chip- Competitive-Advantage-of-the-United-States-and-its-Allies-20191206.pdf.
14 “Winning the Future: A Blueprint for Sustained U.S. Leadership in Semiconductor Technology,” Semiconductor Industry Association, April 2019,https://www.semiconductors.org/wp-content/uploads/2019/04/FINAL-SIA-Blueprint- for-web.pdf.
15 ZTE was later removed from this list. “BIS Adds ZTE Corporation and Three Affiliated Entities to the Entity List,” Bureau of Industry and Security, Department of Commerce,https://bis.doc.gov/index.php/oee/9-bis/carousel/1011-bis-adds-zte-corporation-and- three-affiliated-entities-to-the-entity-list; “China’s Huawei, 70 affiliates placed on U.S. trade blacklist,” Reuters, May 15, 2019, https://www.reuters.com/article/us-usa-china- huaweitech/chinas-huawei-70-affiliates-placed-on-us-trade-blacklist-idUSKCN1SL2W4.
16 Lorand Laskai, “Why Blacklisting Huawei Could Backfire,” Foreign Affairs, June 19, 2019,
https://www.foreignaffairs.com/articles/china/2019-06-19/why-blacklisting-huawei- could-backfire.
17 Jason Matheny and Carrick Flynn, “ANPRM on Review of Controls for Certain Emerging Technologies,” Center for Security and Emerging Technology, January 10, 2019,
Center for Security and Emerging Technology | 37
https://docs.google.com/document/d/1JDDQaWlU- u90VAl6h9sdQb_c_7EB9ftrYDOEqu12nEk/edit.
18
19 Doug Fuller, Paper Tigers, Hidden Dragons: Firms and Political Economy of China’s Technological Development (Oxford University Press, 2016), 131.
20 Junko Yoshida, “China Must Go Beyond Big Fund,” EE Times, November 11, 2019,https://www.eetimes.com/china-must-go-beyond-big-fund/#.
21 “The Decline in Semiconductor Manufacturing in the United States,” Center for Public Policy Innovation, June 2010, https://www.cppionline.org/wp- content/uploads/2017/07/The-Decline-of-Semiconductor-Manufacturing.pdf.
22 Will Knight, “China has never had a real chip industry. Making AI chips could change that,” MIT Technology Review, December 14, 2018,https://www.technologyreview.com/s/612569/china-has-never-had-a-real-chip- industry-making-ai-chips-could-change-that/.
23 While valuations are likely inflated due in part to the influence of state-driven investments, these start-ups have achieved notable progress nonetheless. “Chinese AI chip maker Horizon Robotics raises $600 million from SK Hynix, others,” Reuters, February 27, 2019,https://www.reuters.com/article/us-china-tech-semiconductors/chinese-ai-chip-maker- horizon-robotics-raises-600-million-from-sk-hynix-others-idUSKCN1QG0HW.
24 Dan Strumpf, “Huawei Launches AI Chip in Push to Unseat U.S. Makers,” Wall Street Journal, August 23, 2019, https://www.wsj.com/articles/huawei-launches-ai-chip-in-push- to-unseat-u-s-makers-11566556836.
25 “Alibaba’s New AI Chip Can Process Nearly 80K Images Per Second,” Synced, September 25, 2019, https://syncedreview.com/2019/09/25/alibabas-new-ai-chip- can-process-nearly-80k-images-per-second/.
Arjun Kharpal, “Alibaba unveils its first A.I. chip as China pushes for its own semiconductor technology,” CNBC, September 25, 2019,https://www.cnbc.com/2019/09/25/alibaba-unveils-its-first-ai-chip-called-the- hanguang-800.html.
26 “Alibaba Open-Sources Its MCU to Boost AI Research,” Synced, October 23, 2019,
https://syncedreview.com/2019/10/23/alibaba-open-sources-its-mcu-to-boost-ai- research/.
27 Lorand Laskai and Helen Toner, “Can China Grow Its Own AI Tech Base?”, DigiChina, November 4, 2019, https://www.newamerica.org/cybersecurity- initiative/digichina/blog/can-china-grow-its-own-ai-tech-base/.
On the obstacles to indigenizing a semiconductor industry in China, see Douglas B. Fuller,
“Growth, Upgrading, and Limited Catch-up in China’s Semiconductor Industry,” in Loren
Brandt and Thomas G. Rawski, eds., Policy, Regulation and Innovation in China’s Electricity
and Telecom Industries (Cambridge: Cambridge University Press, 2019).
Center for Security and Emerging Technology | 38
28 See, e.g., Data.gov, https://www.data.gov/open-gov/; “Project Open Data,” https://project-open-data.cio.gov.
29
30 Tim Wu, The Master Switch: The Rise and Fall of Information Empires (New York: Vintage, 2011), 6.
31 Tim Wu, The Curse of Bigness: Antitrust in the New Gilded Age (New York: Random House Audio, 2018).
32 Theresa Hitchens, “U.S. Military Needs Better Data on Itself to Exploit AI,” Breaking Defense, December 12, 2019, https://breakingdefense.com/2019/12/us-military-needs- better-data-on-itself-to-exploit-ai/.
33 Sydney J. Freedberg Jr., “EXCLUSIVE Pentagon’s AI Problem Is ‘Dirty’ Data: Lt. Gen. Shanahan,” Breaking Defense, November 13, 2019,https://breakingdefense.com/2019/11/exclusive-pentagons-ai-problem-is-dirty-data-lt- gen-shanahan/.
34 “The New Racetrack for Artificial Intelligence: China-U.S. Competition” [人工智能新赛场 -中美对比], CCID, May 2017.
35 For an instructive framework on this issue, see Matt Sheehan, “Much Ado About Data: How America and China Stack Up,” MacroPolo, July 16, 2019,https://macropolo.org/ai-data-us-china/.
36 Celia Chen and Iris Deng, “Tencent seeks to kill silo culture that gave it WeChat as it expands into AI, big data,” South China Morning Post, November 14, 2018,https://www.scmp.com/tech/apps-social/article/2172967/tencent-seeks-kill-silo- culture-gave-it-wechat-it-expands-ai-big.
37 Emily Feng, “In China, A New Call To Protect Data Privacy,” NPR, January 5, 2020,
https://www.npr.org/2020/01/05/793014617/in-china-a-new-call-to-protect-data- privacy.
38 “Navigating China’s Data Maze: How Regulations Affect U.S. Companies,” The American Chamber of Commerce in Shanghai, May 2019, https://www.amcham- shanghai.org/sites/default/files/2019-05/Viewpoint%20- %20Data%20%28May%202019%29.pdf.
39 “Interpretation of the Work Plan on Promoting the Development of the Artificial Intelligence Industry through the Opening of Public Data” [关于通过公共数据开放促进人工智能 产 业发展的工作方案》政策解读], November 4, 2019,http://jxj.beijing.gov.cn/zcjd/zcjdlb/201912/t20191212_1088931.html.
Based on analysis of monthly user data of most valuable U.S. and Chinese tech
companies.
Center for Security and Emerging Technology | 39
40 For a discussion of the challenges and opportunities that big data presents for defense mobilization, see Li Ching [李庆], “Looking at the National Defense Mobilization Big Data Construction” [冷眼看国防动员大数据建设], China National Defense News [中国国防报], October 24, 2018, http://www.qstheory.cn/defense/2018- 10/24/c_1123606679.htm.
41 “China Tech Talk 76: US vs China—AI asymmetries with Jeffrey Ding,” technode, April 16, 2019, https://technode.com/2019/04/16/china-tech-talk-76-us-vs-china-ai- asymmetries-with-jeffrey-ding/.
42 “Artificial Intelligence Index: 2019 Annual Report,”https://hai.stanford.edu/sites/g/files/sbiybj10986/f/ai_index_2019_report.pdf.
43 Ibid., 18.44
45 Noam Brown and Tuomas Sandholm, “Superhuman AI for heads-up no-limit poker: Libratus beats top professionals,” Science 359, no. 6374 (2018): 418-424. Alan Blair and Abdallah Saffidine, “AI surpasses humans at six-player poker,” Science 365, no. 6456 (2019): 864-865.
46 Raymond Perrault, Yoav Shoham, Erik Brynjolfsson, Jack Clark, John Etchemendy, Barbara Grosz, Terah Lyons, James Manyika, Saurabh Mishra, and Juan Carlos Niebles, “The AI Index 2019 Annual Report,” AI Index Steering Committee, Human-Centered AI Institute, Stanford University, Stanford, CA, December 2019; Laskai and Toner, “Can China Grow Its Own AI Tech Base.”
47 Field Cady and Oren Etzione, “China May Overtake the US in AI Research,” Medium, March 13, 2019, https://medium.com/ai2-blog/china-to-overtake-us-in-ai-research- 8b6b1fe30595.
48 Karen White, “Publications Output: U.S. Trends and International Comparisons,” Science & Engineering Indicators, December 17, 2019, https://ncses.nsf.gov/pubs/nsb20206.
49 “The China New Generation Artificial Intelligence Development Strategic Research Academy released two heavyweight reports” [中国新一代人工智能发展战略研究院发 布两份重量级报告], Interface news [界面新闻], May 18, 2019,https://xw.qq.com/partner/wcsbzst/20190518A0EB05/20190518A0EB0500?ADTA G=undefined&pgv_ref=undefined.
50 China accounts for 17 of the top 20 academic institutions that have been involved in patenting AI, with particular strength in deep learning, according to a study from the World Intellectual Property Organization. See “WIPO’s First ‘Technology Trends’ Study Probes
David Silver, Thomas Hubert, Julian Schrittwieser, Ioannis Antonoglou, Matthew Lai, Arthur
Guez, Marc Lanctot et al., “A general reinforcement learning algorithm that masters chess,
shogi, and Go through self-play,” Science 362, no. 6419 (2018): 1140-1144.
Center for Security and Emerging Technology | 40
Artificial Intelligence: IBM and Microsoft are Leaders Amid Recent Global Upsurge in AI Inventive Activity,” World Intellectual Property Organization,https://www.wipo.int/pressroom/en/articles/2019/article_0001.html; “WIPO Technology Trends 2019, Artificial Intelligence,” World Intellectual Property Organization,https://www.wipo.int/edocs/pubdocs/en/wipo_pub_1055.pdf.
51 Sarah O’Meara, “Will China Lead the World in AI by 2030,” Nature, August 21, 2019,https://www.nature.com/articles/d41586-019-02360-7.
52 “Robust Vision Challenge,”http://www.robustvision.net/leaderboard.php?benchmark=stereo.
53 Yu Sun, Shuohuan Wang, Yukun Li, Shikun Feng, Xuyi Chen, Han Zhang, Xin Tian, Danxiang Zhu, Hao Tian, and Hua Wu, “ERNIE: Enhanced Representation through Knowledge Integration,” arXiv preprint arXiv:1904.09223 (2019).
54 “Baidu’s Pre-training Model ERNIE Achieves New NLP Benchmark Record,” Synced, December 11, 2019, https://syncedreview.com/2019/12/11/baidus-pre-training- model-ernie-achieves-new-nlp-benchmark-record/.
55 See, e.g., “Global AI Talent Report 2019,” jfgagne, https://jfgagne.ai/talent-2019/.
56 “AAAI-17 Accepted Papers,”http://www.aaai.org/Conferences/AAAI/2017/aaai17accepted-papers.pdf; Sarah Zhang, “China’s Artificial-Intelligence Boom,” The Atlantic, February 16, 2017,https://www.theatlantic.com/technology/archive/2017/02/china-artificial- intelligence/516615/.
57 “Artificial Intelligence Index,” 87,https://hai.stanford.edu/sites/g/files/sbiybj10986/f/ai_index_2019_report.pdf.
58 Remco Zwetsloot, Roxanne Heston, and Zachary Arnold, “Strengthening the U.S. AI Workforce,” Center for Security and Emerging Technology, September 2019,https://cset.georgetown.edu/wp-content/uploads/CSET_US_AI_Workforce.pdf.
59 Remco Zwetsloot, James Dunham, Zachary Arnold, and Tina Huang, “Keeping Top Talent in the United States: Findings and Policy Options for International Graduate Student Retention,” Center for Security and Emerging Technology, https://cset.georgetown.edu/wp- content/uploads/Keeping-Top-AI-Talent-in-the-United-States.pdf.
60 Ibid.
61 Elias G. Carayannis and David FJ Campbell, eds., Knowledge Creation, Diffusion, and Use in Innovation Networks and Knowledge Clusters: A Comparative Systems Approach Across the United States, Europe, and Asia (Connecticut: Greenwood Publishing Group, 2006); “Rapid Rise of China’s STEM Workforce Charted by National Science Board Report,” American Institute of Physics, January 31, 2018.
Center for Security and Emerging Technology | 41
62 Wang Cong, “AI race shifts to talent in battle for dominance,” Global Times, March 19, 2019, http://www.globaltimes.cn/content/1142700.shtml.
63 “The China New Generation Artificial Intelligence Development Strategic Research Academy released two heavyweight reports” [中国新一代人工智能发展战略研究院发 布两份重量级报告], Interface News [界面新闻], May 18, 2019,https://xw.qq.com/partner/wcsbzst/20190518A0EB05/20190518A0EB0500?ADTA G=undefined&pgv_ref=undefined.
64 Zwetsloot, Dunham, Arnold, and Huang, “Keeping Top Talent in the United States.”
65 China Institute for Science and Technology Policy at Tsinghua University, “China AI Development Report 2018,” Tsinghua University, July 2018,http://www.sppm.tsinghua.edu.cn/eWebEditor/UploadFile/China_AI_development_repo rt_2018.pdf.
66 Ibid.
67 Joy D. Ma, “China’s AI Talent Base Is Growing, and then Leaving,” MacroPolo, July 30, 2019, https://macropolo.org/chinas-ai-talent-base-is-growing-and-then-leaving/. By one initial estimate, of the 12,500 AI graduates from Chinese universities to date, reportedly only 31 percent have stayed in China, whereas 62 percent instead departed to the United States. Wang Cong, “AI race shifts to talent in battle for dominance,” Global Times, March 19, 2019, http://www.globaltimes.cn/content/1142700.shtml.
68 Ministry of Education, “Artificial Intelligence Innovation Action Plan for Institutions of Higher Learning” [高等学校人工智能创新行动计划], April 4, 2018,http://www.moe.edu.cn/srcsite/A16/s7062/201804/t20180410_332722.html. For commentary on the topic, see Elsa Kania, “China’s AI talent ‘arms race,” The Strategist, April 23, 2018, https://www.aspistrategist.org.au/chinas-ai-talent-arms-race/.
69 “This year, colleges and universities have added these specialties: artificial intelligence and big data are the hottest” [今年高校新增这些专业:人工智能与大数据最火], June 12, 2019, http://edu.sina.com.cn/gaokao/2019-06-12/doc-ihvhiews8390284.shtml.
70 “Cross National Comparisons of R&D Performance,” National Science Board,
https://www.nsf.gov/statistics/2018/nsb20181/report/sections/research-and- development-u-s-trends-and-international-comparisons/cross-national-comparisons-of-r-d- performance.
71 “2016–2019 Progress Report: Advancing Artificial Intelligence R&D,” November 2019,
https://www.nitrd.gov/pubs/AI-Research-and-Development-Progress-Report-2016- 2019.pdf; Melissa Flagg, “America’s Future Lies in Technical Alliances,” Center for Security and Emerging Technology (blog), January 8, 2020,https://cset.georgetown.edu/2020/01/08/americas-future-lies-in-technical-alliances/.
72 “National Security Commission on Artificial Intelligence,” Interim Report, November 2019,https://www.nscai.gov/about/reports-to-congress.
Center for Security and Emerging Technology | 42
73 Ibid.
74 MIT Committee to Evaluate the Innovation Deficit, “The Future Postponed: Why Declining Investment in Basic Research Threatens a U.S. Innovation Deficit,” April 2015,https://dc.mit.edu/sites/default/files/Future%20Postponed.pdf.
75 Jonathan Gruber and Simon Johnson, Jump-starting America: How Breakthrough Science Can Revive Economic Growth and the American Dream (New York: Public Affairs, 2019).
76 Charlotte Yang, “Chart of the Day: Another Record Year for China R&D Spending, Caixin, October 10, 2018, https://www.caixinglobal.com/2018-10-10/chart-of-the-day- another-record-year-for-china-rd-spending-101333479.html. See also “Is China a global leader in research and development,” China Power, https://chinapower.csis.org/china- research-and-development-rnd/l; Dennis Normile, “China narrows U.S. lead in R&D spending,” Science, October 19, 2018,https://science.sciencemag.org/content/362/6412/276.
77 “China’s R&D expenditure is close to two trillion yuan. Which cities have more research investment?” [中国研发经费接近两万亿,哪些城市科研投入多?], CCTV, September 13, 2019,http://news.cctv.com/2019/09/13/ARTIwBtFsNMhTHQ8DXpFQHJR190913.shtml.
78 Teddy Ng and Jane Cai, “China’s funding for science and research to reach 2.5 per cent of GDP in 2019,” South China Morning Post, March 10, 2019,https://www.scmp.com/news/china/science/article/2189427/chinas-funding-science- and-research-reach-25-cent-gdp-2019.
79 “Atlas of national key R & D plan funding allocation” [国家重点研发计划经费分配图谱 浮现], Economic Reference [经济参考报], October 14, 2019,http://www.xinhuanet.com/fortune/2019-10/14/c_1125100297.htm.
80 Ashwin Acharya and Zachary Arnold, “Chinese Public AI R&D Spending: Provisional Findings,” CSET Issue Brief, December 2019, https://cset.georgetown.edu/wp- content/uploads/Chinese-Public-AI-RD-Spending-Provisional-Findings-2.pdf.
81 For instance, i
“Tianjin established a new generation of artificial intelligence industry fund with a scale of 100 billion RMB” [天津设新一代人工智
能产业基金,规模为1000亿人民币], May 16, 2018,https://m.pedaily.cn/news/431332.
82 “The National “863” Plan Computer Subject’s Thirty-Year Anniversary: Leapfrog-Style Development and the Realm of Necessity” [
n May 2018, the city of Tianjin announced the New Generation Artificial
Intelligence Industry Fund, which amounts to 100 billion RMB ($16 billion), based on a
combination of state and venture capital funding.
国家“863”计划计算机主题30年拾遗:跨
越式发展与必然王国], Science Net, February 8, 2017,
Center for Security and Emerging Technology | 43
“863 Plan” [
83 Ibid. “863 Plan” [
84 “Our Nation Launched Four Major Science Research Programs” [我国启动四项重大科
学研究计划], Science and Technology Daily, November 16, 2006.
85 “The national key R&D plan for next year is basically determined! These industries are the most noteworthy” [国家明年重点研发计划基本确定!这几个产业最值得关注], October 28, 2019.
86 “National Medium and Long Term Science and Technology Development Plan Outline” (2006-2020) [国家中长期科学和技术发展规划纲要], Ministry of Science and Technology, February 9, 2006,http://www.most.gov.cn/mostinfo/xinxifenlei/gjkjgh/200811/t20081129_65774_9.ht m.
https://www.itu.int/en/ITU- D/Cybersecurity/Documents/National_Strategies_Repository/China_2006.pdf.
87 See estimates from the Allen Institute.
88 “2021-2035 National Medium- and Long-term Scientific and Technological Development Plan Basic Science Development Strategy Research Project Launched in Beijing” [2021- 2035年国家中长期科技发展规划基础科学发展战略研究专题在京启动], Ministry of Science and Technology Website, May 3, 2019, http://www.gov.cn/xinwen/2019- 05/03/content_5388386.htm.
89 Elsa B. Kania, “Battlefield Singularity: Artificial Intelligence, Military Revolution, and China’s Future Military Power,” Center for a New American Security, November 28, 2017,https://www.cnas.org/publications/reports/battlefield-singularity-artificial-intelligence- military-revolution-and-chinas-future-military-power.
90 Jeffrey Ding, “Deciphering China’s AI Dream,” Future of Humanity Institute, University of Oxford, March 2018, https://www.fhi.ox.ac.uk/wp- content/uploads/Deciphering_Chinas_AI-Dream.pdf.
91 “State Council Notice on the Issuance of the New Generation AI Development Plan” [国 务院关于印发新一代人工智能发展规划的通知]. “MIIT’s Notice Regarding the Release of the Three Year Action Plan to Promote the Development of New-Generation Artificial Intelligence Industry (2018-2020) [工业和信息化部关于印发《促进新一代人工智能产 业发展三年行动计划(2018-2020年)》的通], December 14, 2017,http://www.miit.gov.cn/n1146295/n1652858/n1652930/n3757016/c5960820/co ntent.html.
For an English translation of this plan, see Paul Triolo, Elsa Kania, and Graham Webster (translators), “Translation: Chinese government outlines AI ambitions through 2020,”
http://news.sciencenet.cn/htmlnews/2017/2/367416.shtm. See also
计划], China Education and Research Network, http://www.edu.cn/html/rd/b/bls.shtml.
See also
http://www.edu.cn/html/rd/b/bls.shtml.
863计划], China Education and Research Network,
Center for Security and Emerging Technology | 44
863
DigiChina, https://www.newamerica.org/cybersecurity- initiative/digichina/blog/translation-chinese-government-outlines-ai-ambitions-through- 2020/.
92 “Ministry of Science and Technology Notice Regarding the Issuance of National Key R&D Plan Transformative Technologies and Crux Scientific Problems Key Topic 2017 Program Application Guidelines” [科技部关于发布国家重点研发计划变革性技术关键科学问题 重点专项2017年度项目申报指南的通知], Ministry of Science and Technology, September 27, 2017,http://www.most.gov.cn/mostinfo/xinxifenlei/fgzc/gfxwj/gfxwj2017/201710/t20171 009_135224.htm.
93 There might be some debate about the best translations for the terms “重大工程” and“重大项目,” each of which could be rendered major/mega project/program. See National Development and Reform Commission Office Releases Notice Regarding the Implementation of the 2018 “Internet Plus,” Artificial Intelligence Innovation Development, and Digital Economy Experimental Mega-Project Notice [国家发展改革委办公厅关于组 织实施2018年“互联网+”、人工智能创新发展和数字经济试点重大工程的通知], National Development and Reform Commission, October 11, 2017,http://www.ndrc.gov.cn/zcfb/zcfbtz/201710/t20171013_863534.html.
94 “AI Innovation and Development Major Project Application Requirements” [人工智能创 新发展重大工程申报要求], NDRC, October 11, 2017,http://www.ndrc.gov.cn/zcfb/zcfbtz/201710/W020171013599553259770.pdf.
95 “56 projects selected as major projects for the ‘Internet Plus,’ Artificial Intelligence Innovation Development and Digital Economy Pilot Megaprojects” [56个项目入选“互联 网+”、人工智能创新发展和数字经济试点重大工程], January 22, 2018, Xinhua,http://www.gov.cn/guowuyuan/2018-01/22/content_5259438.htm.
96 “State Council Notice on the Issuance of the New Generation AI Development Plan” [国 务院关于印发新一代人工智能发展规划的通知].
97 For examples, see “SDIC’s National Emerging Industry Venture Capital Guidance Fund raised a total of 17.85 billion yuan” [国投创合国家新���产业创业投资引导基金募集规 模达178.5亿元], May 10, 2017,https://www.sdic.com.cn/cn/zxzx/gsyw/2017/06/09/webinfo/phone14959552641 37396.htm.
“Guohua Military-Civil Fusion Industrial Development Fund Established” [国华军民融合产 业发展基金创立],National Defense Science and Industry Bureau, September 7,
2016, http://www.gov.cn/xinwen/2016-09/07/content_5106111.htm.
98 Paul Triolo, “AI in China: Cutting Through the Hype,” Eurasia Group, December 6, 2017,https://www.eurasiagroup.net/live-post/ai-in-china-cutting-through-the-hype.
99 See the Party’s report from the fourth plenum: “Communiqué of the Fourth Plenary Session of the 19th Central Committee of the Communist Party of China” [中国共产党第十九届中
Center for Security and Emerging Technology | 45
央委员会第四次全体会议公报], Xinhua, October 31, 2019,http://www.xinhuanet.com/politics/2019-10/31/c_1125178024.htm.
100 “The United States of Artificial Intelligence Startups, CBInsights, November 26, 2019,https://www.cbinsights.com/research/artificial-intelligence-startup-us-map/.
101 Ibid.
102 Joanna Glasner, “AI Companies Raise More Money Across Fewer Rounds,” Crunchbase News, September 9, 2019, https://news.crunchbase.com/news/ai-companies-raise-more- money-across-fewer-rounds/.
103 For one historical perspective, see Linda Weiss, America Inc.? Innovation and Enterprise in the National Security State (Ithaca: Cornell University Press, 2014).
104 Rachel Olney, “The Rift Between Silicon Valley and the Pentagon is Economic, not Moral,” War on the Rocks, January 28, 2019, https://warontherocks.com/2019/01/the- rift-between-silicon-valley-and-the-pentagon-is-economic-not-moral/.
105 “The Contest for Innovation: Strengthening America’s National Security Innovation Base in an Era of Strategic Competition,” Ronald Reagan Institute, December 2019,https://www.reaganfoundation.org/media/355312/the_contest_for_innovation_report.p df.
106 Ibid.
107 The levels of funding are high enough that the founder of one Chinese AI start-up characterized this as a negative. As he remarked to one of the authors, there is “too much money chasing too few good ideas.”
108 “China Is Starting To Edge Out The US In AI Investment,” CB Insights, February 12, 2019,
https://www.cbinsights.com/research/china-artificial-intelligence-investment-startups- tech/.
109 Jing Shuiyu, “AI startups see record financing in H1,” China Daily, August 3, 2017,http://www.chinadaily.com.cn/business/tech/2017-08/03/content_30340585.htm.
110 “The China New Generation Artificial Intelligence Development Strategic Research Academy released two heavyweight reports” [中国新一代人工智能发展战略研究院发 布两份重量级报告], Interface News [界面新闻], May 18, 2019,https://xw.qq.com/partner/wcsbzst/20190518A0EB05/20190518A0EB0500?ADTA G=undefined&pgv_ref=undefined.
111 “China VC investment hits record high in 2018: Report,” Xinhua, February 1, 2019,http://www.chinadaily.com.cn/a/201902/01/WS5c53e434a3106c65c34e7cb2.html.
Center for Security and Emerging Technology | 46
112 See, e.g., “Used cars and AI come out on top as China's startup funding slumps,” Nikkei Asian Review, July 3, 2019, https://asia.nikkei.com/Business/China-tech/Used-cars-and- AI-come-out-on-top-as-China-s-startup-funding-slumps.
113 “China recruits Baidu, Alibaba and Tencent to AI ‘national team,’” South China Morning Post, November 21, 2017, http://www.scmp.com/tech/china- tech/article/2120913/china-recruits-baidu-alibaba-and-tencent-ai-national-team.
114 “Artificial Intelligence Open Platform, Have you Joined?” [人工智能开放平台,你加入 了吗-中新网”], China News, December 13, 2018,http://www.chinanews.com/it/2018/10-08/8643974.shtml; “AI “national team” Xiong’nn Debut! Will Change Your Life” [人工智能“国家队”雄安登场!将改变你的生 活], Xiong’an, November 30, 2017, http://www.xiongan.gov.cn/2017- 11/30/c_129766243.htm.
115 “Rise Of China’s Big Tech In AI: What Baidu, Alibaba, And Tencent Are Working On,” CB Insights, April 26, 2018, https://www.cbinsights.com/research/china-baidu-alibaba- tencent-artificial-intelligence-dominance/.
116 Patrick Foulis, “Across the West powerful firms are becoming even more powerful,” The Economist, November 15, 2018, https://www.economist.com/special- report/2018/11/15/across-the-west-powerful-firms-are-becoming-even-more-powerful; John Mauldin, “America Has a Monopoly Problem,” Forbes, April 11, 2019,https://www.forbes.com/sites/johnmauldin/2019/04/11/america-has-a-monopoly- problem/; Jonathan Tepper, The Myth of Capitalism: Monopolies and the Death of Competition (John Wiley & Sons, 2018).
117 Mark Z. Taylor, The Politics of Innovation: Why Some Countries Are Better Than Others at Science and Technology (Oxford: Oxford University Press, 2016).
118 Martin Kenney and Urs Von Burg, “Technology, entrepreneurship and path dependence: industrial clustering in Silicon Valley and Route 128.” Industrial and corporate change 8, no. 1 (1999): 67-103; Aaron Chatterji, Edward Glaeser, and William Kerr, “Clusters of entrepreneurship and innovation,” Innovation Policy and the Economy 14, no. 1 (2014): 129-166.
119 Fareed Zakaria, “The Future of American Power,” Foreign Affairs, May/June 2008,
https://www.foreignaffairs.com/articles/united-states/2008-05-03/future-american- power.
120
121 MIT Committee to Evaluate the Innovation Deficit, “The Future Postponed: Why Declining Investment in Basic Research Threatens a U.S. Innovation Deficit,” April 2015,https://dc.mit.edu/sites/default/files/Future%20Postponed.pdf.
Mariana Mazzucato, “The entrepreneurial state,” Soundings 49, no. 49 (2011): 131-
142.
Center for Security and Emerging Technology | 47
122 Ding, “Deciphering China’s AI Dream.”
123 For a good analysis on the topic, see Yukon Huang and Jeremy Smith, “China’s Record on Intellectual Property Rights Is Getting Better and Better,” Foreign Policy, October 16, 2019, https://foreignpolicy.com/2019/10/16/china-intellectual-property-theft- progress/.
124 “State Council’s Guiding Opinions on Accelerating the Construction of Mass Entrepreneurship and Innovation Support Platforms” [国务院关于加快构建大众创业万众 创新支撑平台的指导意见], September 25, 2016,http://www.gov.cn/zhengce/content/2015-09/26/content_10183.htm.
125 “The China New Generation Artificial Intelligence Development Strategic Research Academy released two heavyweight reports” [中国新一代人工智能发展战略研究院发 布两份重量级报告], Interface News [界面新闻], May 18, 2019,https://xw.qq.com/partner/wcsbzst/20190518A0EB05/20190518A0EB0500?ADTA G=undefined&pgv_ref=undefined. Estimates often vary depending on what is defined as an “AI enterprise.”
126 Minghe Hu and Zen Soo, “China’s reliance on US-origin platforms for deep learning raises questions about country’s AI push,” South China Morning Post, November 22, 2019,https://www.scmp.com/tech/start-ups/article/3038772/chinas-reliance-us-origin- platforms-deep-learning-raises-questions.
127 “Artificial Intelligence Open Platform, Have you Joined?” [人工智能开放平台,你加入 了吗-中新网”], China News, December 13, 2018,http://www.chinanews.com/it/2018/10-08/8643974.shtml; “Five Major National-Level Open Innovation Platforms Revealed” [五大国家级人工智能开放创新平台将集体亮相 “], January 18, 2019. See also “Ten Major National New Generation of Artificial Intelligence Open Innovation Platforms Released in Shanghai [十大国家新一代人工智能 开放创新平台在沪发布], Science Network, August 29, 2019,http://news.sciencenet.cn/htmlnews/2019/8/429964.shtm.
128 Ministry of Science and Technology Notice on the Publication of the Guidance on National New Generation Artificial Intelligence Open Innovation Platform Construction Work [科技部关于印发《国家新一代人工智能开放创新平台建设工作指引》的通知], September 17, 2019, https://cset.georgetown.edu/wp-content/uploads/Ministry-and- Science-and-Technology-Notice-on-Publication-of-Guidance-1.pdf.
129 Laskai and Toner, “Can China Grow Its Own AI Tech Base.”
130 For updates on its capabilities, see, e.g. “Baidu PaddlePaddle Releases 21 New Capabilities to Accelerate Industry-Grade Model Development,” November 14, 2019,http://research.baidu.com/Blog/index-view?id=126.
Center for Security and Emerging Technology | 48
131 Chris Udemans, “Alibaba Cloud opens source code for machine-learning platform Alink,” technode, November 28, 2019, https://technode.com/2019/11/28/alibaba-cloud- machine-learning-platform-open-source/.
132 “CSRankings: Computer Science Rankings,” http://csrankings.org/#/index?all.
133 Josef Joffe, The Myth of America’s Decline: Politics, Economics, and a Half Century of
False Prophecies (New York: Liveright., 2013), 172-188.
134 John Timmer, “US computer science grads outperforming those in other key nations,” ArsTechnica, March 23, 2019, https://arstechnica.com/science/2019/03/us-computer- science-grads-outperforming-those-in-other-key-nations/.
135
Journal of Education and Work
136 Edward Luce, Time to Start Thinking: America in the Age of Descent (New York: Atlantic Monthly Press, 2012).
137 Michael S. Teitelbaum, Falling Behind? Boom, Bust, and the Global Race for Scientific Talent (Princeton: Princeton University Press, 2014); Adams B. Nager and Robert D. Atkinson, “Ten Myths of High-Skilled Immigration,” Information Technology & Innovation Foundation, April 2015, http://www.ilw.com/articles/2015,0420-Atkinson.pdf.
138 Michael S. Teitelbaum, Falling Behind? Boom, Bust, and the Global Race for Scientific Talent (Princeton: Princeton University Press, 2014),https://press.princeton.edu/titles/10208.html.
139 Cary Funk and Kim Parker, “Most Americans evaluate STEM education as middling compared with other developed nations,” Pew Research Center, January 9, 2018,https://www.pewsocialtrends.org/2018/01/09/5-most-americans-evaluate-stem- education-as-middling-compared-with-other-developed-nations/.
140 “Research Reveals Boys’ Interest in STEM Careers Declining; Girls’ Interest Unchanged,” Junior Achievement USA, https://www.juniorachievement.org/web/ja-usa/press- releases/-/asset_publisher/UmcVLQOLGie9/content/research-reveals-boys’-interest-in- stem-careers-declining-girls’-interest-unchanged; “Survey: Teen Girls’ Interest in STEM Careers Declines,” Junior Achievement, https://www.juniorachievement.org/web/ja- usa/press-releases/-/asset_publisher/UmcVLQOLGie9/content/survey-teen-girls’- interest-in-stem-careers-declines.
141 Ibid.
142 Normile, Dennis, “One in Three Chinese Children Faces an Education Apocalypse. An
Ambitious Experiment Hopes to Save Them,” Science 21 (2017).143
Adam Gamoran and Sarah K. Bruch, “Educational inequality in the United States: can we
reverse the tide?”
“Chapter 4: Shanghai and Hong Kong: Two Distinct Examples of Education Reform in
China,” in Strong Performers and Successful Reformers in Education: Lessons from PISA for
30, no. 7 (2017): 777-792.
the United States, Organization for Economic Cooperation and Development,
Center for Security and Emerging Technology | 49
http://www.oecd.org/document/13/0,3343,en_2649_35845621_46538637_1_1_1
_1,00.html.
144 “Chinese university graduates rise exponentially, have diverse career options,” Xinhua, June 24, 2019,https://www.chinadaily.com.cn/a/201906/24/WS5d1080bca3103dbf14329e9f.html.
145 For a good overview, see “Seizing the laurels: Tsinghua University may soon top the world league in science research,” The Economist, November 17, 201,https://www.economist.com/china/2018/11/17/tsinghua-university-may-soon-top-the- world-league-in-science-research.
146 For a comparative perspective, see
147 Ricky Ye, “While US STEM education market declines, China invests heavily,” The Next Web, June 19, 2017, https://thenextweb.com/contributors/2017/06/19/us-stem- education-market-declines-china-invests-heavily/.
148 See initial results reported in a survey from Tsinghua University. China Institute for Science and Technology Policy at Tsinghua University, “China AI Development Report 2018,” Tsinghua University, July 2018,http://www.sppm.tsinghua.edu.cn/eWebEditor/UploadFile/China_AI_development_repo rt_2018.pdf.
149 Yi-Ling Liu, “China’s AI Dreams Aren’t for Everyone,” Foreign Policy, August 13, 2019,
https://foreignpolicy.com/2019/08/13/china-artificial-intelligence-dreams-arent-for- everyone-data-privacy-economic-inequality/.
150 iFlytek, Deeply Ploughing Education for Fifteen Years” [科大讯飞 深耕教育15年] November 21, 2019, Beijing Report [新京报], https://tech.sina.com.cn/it/2019-11- 21/doc-iihnzahi2260676.shtml.
151 Nicholas Eberstadt, “With Great Demographics Comes Great Power,” Foreign Affairs, July/August 2019, https://www.foreignaffairs.com/articles/world/2019-06-11/great- demographics-comes-great-power.
152 Zwetsloot, Heston, and Arnold, “Strengthening the U.S. AI Workforce.”153 Ibid., 5.
154 “Fewer foreign students coming to the United States for the second year in row, survey finds,” Reuters, November 13, 2018,https://www.nbcnews.com/news/asian-america/fewer-foreign-students-coming-united- states-second-year-row-survey-n935701; Zachary Arnold, Roxanne Heston, Remco Zwetsloot, and Tina Huang, “Immigration Policy and the U.S. AI Sector: A Preliminary
Wang, Yan, Jari Lavonen, and Kirsi Tirri, “Aims for
learning 21st century competencies in national primary science curricula in China and
Finland,” Eurasia Journal of Mathematics, Science & Technology Education (2018).
Center for Security and Emerging Technology | 50
Assessment,” Center for Security and Emerging Technology, September 2019, 2-4,https://cset.georgetown.edu/wp-content/uploads/CSET_Immigration_Policy_and_AI.pdf.
155 Ibid., Section 3.
156 Alana Semeuls, “Tech Companies Say It’s Too Hard to Hire High-Skilled Immigrants in the U.S. — So They're Growing in Canada Instead,” Time, July 25, 2019,https://time.com/5634351/canada-high-skilled-labor-immigrants/.
157 Zwetsloot, Heston, and Arnold, “Strengthening the U.S. AI Workforce.”
158 At present, China’s fertility rates are below replacement levels, and even the recent changes to the one-child policy won’t compensate for these adverse trends. See also Nicholas Eberstadt, “With Great Demographics Comes Great Power,” Foreign Affairs, July/August 2019, https://www.foreignaffairs.com/articles/world/2019-06-11/great- demographics-comes-great-power.
159 Ding, “Deciphering China’s AI Dream.”
160 William Hannas and Huey-meei Chang, “China’s Access to Foreign AI Technology: An Assessment,” Center for Security and Emerging Technology, September 2019,https://cset.georgetown.edu/wp- content/uploads/CSET_China_Access_To_Foreign_Technology.pdf.
161 Meng Jing, “Chinese firms fight to lure top artificial intelligence talent from Silicon Valley,” South China Morning Post, April 2, 2017, http://www.scmp.com/tech/china- tech/article/2084171/chinese-firms-fight-lure-top-artificial-intelligence-talent-silicon.
162 Remco Zwetsloot and Dahlia Peterson, “The US-China Tech Wars: China’s Immigration Disadvantage,” The Diplomat, December 31, 2019,https://thediplomat.com/2019/12/the-us-china-tech-wars-chinas-immigration- disadvantage/.
163 See MIT’s description of these engagements: Adam Conner-Simons, “CSAIL launches new five-year collaboration with iFlyTek,” MIT News, https://news.mit.edu/2018/csail- launches-five-year-collaboration-with-iflytek-0615.
164 Hal Brands and Peter D. Feaver, “What Are America’s Alliances Good For?” Parameters 47, Issue 2 (Summer 2017): 15-30.
165 Anne-Marie Slaughter, The Chessboard and the Web: Strategies of Connection in a Networked World (New Haven: Yale University Press, 2017). See also Niall Ferguson, “The False Prophecy of Hyperconnection,” Foreign Affairs, September/October 2017,https://www.foreignaffairs.com/articles/2017-08-15/false-prophecy-hyperconnection; Emilie M. Hafner-Burton, Miles Kahler, and Alexander H. Montgomery, “Network Analysis for International Relations,” International Organization 63, Issue 3 (July 2009): 559-592,https://www.cambridge.org/core/journals/international-organization/article/network- analysis-for-international-relations/DE2910979C1B5C44C4CC13F336C5DE97.
Center for Security and Emerging Technology | 51
166 Anne-Marie Slaughter, “America’s Edge,” Foreign Affairs, January/February 2009,https://www.foreignaffairs.com/articles/united-states/2009-01-01/americas-edge.
167 Ibid.
168 James Carse, Finite and Infinite Games (New York: Free Press, 1986); Robert Wright, Nonzero: The Logic of Human Destiny (New York: Vintage Books, 2001).
169 “China AI Development Report 2018,” China Institute for Science and Technology Policy at Tsinghua University.
170 See, e.g., Felicia Schwartz and Dov Lieber, “Chinese Investment in Israel Raises Security Fears,” Wall Street Journal, February 11, 2019, https://www.wsj.com/articles/chinese- investment-in-israel-raises-security-fears-11549881000.
171 “Artificial Intelligence and National Security,” Congressional Research Service, January 30, 2019, https://fas.org/sgp/crs/natsec/R45178.pdf.
172 For context, see “CFIUS Reform: Foreign Investment National Security Reviews,” Congressional Research Service, October 3, 2019,https://fas.org/sgp/crs/natsec/IF10952.pdf.
173 Michael Brown and Pavneet Singh, “China’s Technology Transfer Strategy: How Chinese Investments in Emerging Technology Enable A Strategic Competitor to Access the Crown Jewels of U.S. Innovation,” January 2018,https://admin.govexec.com/media/diux_chinatechnologytransferstudy_jan_2018_(1).pdf.
174 China and the Philippines established a “Data port” in September 2018. China also initiated the Digital Silk Road International Industry Alliance. For more information, see “China's big data companies embark on the “Belt and Road”” [中国大数据企业走上“一 带一路”], Xinhua, December 14, 2018, http://news.xinhuanet.com/globe/2018- 12/14/c_137663769.html; “Digital Economy and Digital Silk Road International Conference proposes to jointly build digital silk road,” Zhejiang Daily, September 19, 2018.
175 See, e.g., “BRI helps participating countries with technological innovation,” People’s Daily, April 26, 2019, http://en.people.cn/n3/2019/0426/c90000-9572518.html.
176 Elizabeth C. Economy, “China’s New Revolution,” Foreign Affairs, May/June 2018,https://www.foreignaffairs.com/articles/china/2018-04-17/chinas-new-revolution.
177 “China and France’s top universities build ‘AI Alliance’ to promote artificial intelligence international cooperation,” Xinhua, January 18, 2018.
178 “AI, Another Breakthrough in Sino-UK Innovation Cooperation” [ 人工智能 中英创新 合作又一风口], People’s Daily, November 3, 2018,http://world.people.com.cn/GB/n1/2018/1103/c1002-30380012.html.
Center for Security and Emerging Technology | 52
179 “China and Russia big data base will be built in Harbin at the end of the year” [中俄大数 据基地年底将在哈尔滨建成], Harbin Daily, March 11, 2018,https://web.archive.org/save/https://zj.zjol.com.cn/news.html?id=890364.
The project has been successfully supported by the 2017 National Development and Reform Commission Digital Economy Pilot Major Project. a major project of Heilongjiang Province
180 “Lecture Series on “China-Russia Economic and Trade Cooperation Database and Russian-Chinese Intelligent Integrated Service Platform”” [“中俄经贸合作数据库及俄汉 语智能化综合服务平台”项目系列讲座中俄经贸合作数据库及俄汉语智能化综合服 务平台], November 1, 2018,https://web.archive.org/save/http://yuyanziyuan.blcu.edu.cn/info/1066/1259.htm.
181 Miles Brundage et al., “The Malicious Use of Artificial Intelligence: Forecasting, Preventing, and Mitigation,” February 2018, https://arxiv.org/pdf/1802.07228.pdf.
182 Andrew Imbrie and Elsa B. Kania, “AI Safety, Security, and Stability Among Great Powers: Options, Challenges, and Lessons Learned for Pragmatic Engagement,” Center for Security and Emerging Technology, December 2019, https://cset.georgetown.edu/wp- content/uploads/AI-Safety-Security-and-Stability-Among-the-Great-Powers.pdf.
183 William J. Burns, “The Demolition of U.S. Diplomacy,” Foreign Affairs, October 14, 2019; Ronan Farrow, War on Peace: The End of Diplomacy and the Decline of American Influence (New York: W.W. Norton & Company, 2018).
184 Elsa B. Kania,” The Right to Speak: Discourse and Chinese Power,” Center for Advanced China Research, 27, 2018. See also Joel Wuthnow, “The concept of soft power in China’s strategic discourse,” Issues & Studies 44, no. 2 (2008): 1-28.
185 Kristine Lee and Alexander Sullivan, “People’s Republic of the United Nations: China’s Emerging Revisionism in International Organizations,” Center for a New American Security, May 14, 2019, https://www.cnas.org/publications/reports/peoples-republic-of-the- united-nations.
186 See, e.g., Elsa B. Kania, “China’s play for global 5G dominance—standards and the ‘Digital Silk Road’,” The Strategist, ASPI, June 27, 2018,https://www.aspistrategist.org.au/chinas-play-for-global-5g-dominance-standards-and- the-digital-silk-road/.
187 Graham Webster, Rogier Creemers, Paul Triolo, and Elsa Kania, “China’s Plan to Lead in AI: Purpose, Prospects, and Problems,” New America, August 1, 2017,https://www.newamerica.org/cybersecurity-initiative/blog/chinas-plan-lead-ai-purpose- prospects-and-problems/.
188 For authoritative reporting on these issues, see Paul Mozur, “One Month, 500,000 Face Scans: How China Is Using A.I. to Profile a Minority,” New York Times, April 14, 2019,https://www.nytimes.com/2019/04/14/technology/china-surveillance-artificial- intelligence-racial-profiling.html.
Center for Security and Emerging Technology | 53
189 “Beijing AI Principles,” May 29, https://www.baai.ac.cn/blog/beijing-ai-principles. See also “China Hosts Conference to Promote Ethical AI Standards,” China Daily, June 19, 2019,http://global.chinadaily.com.cn/a/201906/19/WS5d098cdfa3103dbf14329084.html; Will Knight, “Why Does Beijing Suddenly Care About AI Ethics?” MIT Technology Review,https://www.technologyreview.com/s/613610/why-does-china-suddenly-care-about-ai- ethics-and-privacy/.
190 See, e.g., “World Artificial Intelligence Conference,”http://www.worldaic.com.cn/portal/en/index.html; “Global Artificial Intelligence Conference,” https://gaitc.caai.cn/en.
191 See, e.g., “Countering High-Tech Illiberalism,” https://www.cnas.org/press/press- release/countering-high-tech-illiberalism. See also Freedom House, “Freedom on the Net 2018: The Rise of Digital Authoritarianism,” https://freedomhouse.org/report/freedom- net/freedom-net-2018/rise-digital-authoritarianism. For a policy brief on the topic, see Alina Polyakova and Chris Meserole, “Exporting digital authoritarianism,” Brookings Institution, https://www.brookings.edu/wp- content/uploads/2019/08/FP_20190826_digital_authoritarianism_polyakova_meserole .pdf.
192 Samantha Hoffman, “Managing the State: Social Credit, Surveillance and the CCP’s Plan for China,” in Nicholas D. Wright, ed., AI, China, Russia, and the Global Order: Technological, Political, Global, and Creative Perspectives, A Strategic Multiyear Assessment Periodic Publication, 2018, 42, https://nsiteam.com/social/wp- content/uploads/2018/12/AI-China-Russia-Global-WP_FINAL.pdf.
193 Stephen G. Brooks and William C. Wohlforth, “The Once and Future Superpower,” Foreign Affairs, May/June 2016.
194 However, the realization of this potential advantage requires the effective use of this data.195 Brooks and Wohlforth, “The Once and Future Superpower.”
196 Ibid.
197 Brooks and Wohlforth, “The Once and Future Superpower”; Andrea Gilli and Mauro Gilli, “Why China Has Not Caught Up Yet: Military-Technological Superiority and the Limits of Imitation, Reverse Engineering, and Cyber Espionage,” International Security, 43, Issue 3 (Winter 2018/19): 141-189.
198 “Costs of War,” Watson Institute, Brown University,https://watson.brown.edu/costsofwar/.
199 See the Defense Innovation Board’s project and report on the topic: “Software is Never Done: Refactoring the Acquisition Code for Competitive Advantage,” May 13, 2019. “Software Acquisition and Practices (SWAP) Study,”https://innovation.defense.gov/software/.
Center for Security and Emerging Technology | 54
200 “Assessing and Strengthening the Manufacturing and Defense Industrial Base and Supply Chain Resiliency of the United States,” Report to President Donald J. Trump by the Interagency Task Force in Fulfillment of Executive Order 13806, September 2018,https://media.defense.gov/2018/Oct/05/2002048904/-1/-1/1/ASSESSING-AND- STRENGTHENING-THE-MANUFACTURING-AND%20DEFENSE-INDUSTRIAL-BASE- AND-SUPPLY-CHAIN-RESILIENCY.PDF.
201 Xi Jinping Discusses Military-Civil Fusion” [习近平谈军民融合], Seeking Truth [求是], October 16, 2018, http://www.qstheory.cn/zhuanqu/rdjj/2018- 10/16/c_1123565364.htm. See also Elsa B. Kania, “In Military-Civil Fusion, China is Learning Lessons from the United States and Starting to Innovate,” The Strategy Bridge, August 27, 2019, https://thestrategybridge.org/the-bridge/2019/8/27/in-military-civil- fusion-china-is-learning-lessons-from-the-united-states-and-starting-to-innovate.
202 Ibid.
203 Elsa B. Kania, “Chinese Military Innovation in Artificial Intelligence,” Testimony to the U.S.-China Economic and Security Review Commission, June 2019,https://www.cnas.org/publications/congressional-testimony/chinese-military-innovation- in-artificial-intelligence.
204 CETC Military-Civil Fusion Network Information Systems Appear at Zhuhai Airshow [中国 电科军民融合的网络信息体系亮相珠海航展], February 25, 2019,http://www.cetcd.cn/html/2019-02/7435.html.
205 Ibid.206 Ibid.
207 State Council Notice on the Issuance of the New Generation AI Development Plan” [国务 院关于印发新一代人工智能发展规划的通知], July 20, 2017,http://www.gov.cn/zhengce/content/2017-07/20/content_5211996.htm; Graham Webster, Rogier Creemers, Paul Triolo, and Elsa Kania, “Full Translation: China's ‘New Generation Artificial Intelligence Development Plan’ (2017),” New America,https://www.newamerica.org/cybersecurity-initiative/digichina/blog/full-translation- chinas-new-generation-artificial-intelligence-development-plan-2017/; “Executive Order on Maintaining American Leadership in Artificial Intelligence,” White House, February 11, 2019, https://www.whitehouse.gov/presidential-actions/executive-order-maintaining- american-leadership-artificial-intelligence/.
208 For an excellent resource on the topic, see the 2019 AI Index Report. This Index provides tools and datasets to evaluate progress in AI, which is available through Stanford’s initiative on Human-Centered Artificial Intelligence. For more information, see “Artificial Intelligence Index: 2019 Annual Report,” https://hai.stanford.edu/ai-index/2019.
209 Vannevar Bush, Science, the Endless Frontier (Ayer Company Publishers, 1995).
Center for Security and Emerging Technology | 55
210 Mariana Mazzucato, The Entrepreneurial State: Debunking Public vs. Private Sector Myths. Vol. 1 (Anthem Press, 2015).
211 For context, see “DARPA Electronics Resurgence Initiative,”https://www.darpa.mil/work-with-us/electronics-resurgence-initiative.
212 Such an initiative could build upon antecedents. See “Public-Private Partnerships for Semiconductor Research,” https://www.nist.gov/industry-impacts/public-private- partnerships-semiconductor-research.
213 See future research forthcoming from CSET by Remco Zwetsloot et al. that will provide a more detailed analysis of this policy issue.
214 Eliezer Geisler and Wagdy Abdallah, The Metrics of Science and Technology (Quorum Books, 2000); OECD Science, Technology, and Industry Outlook, 2014 (OECD Publishing, 2014).
215 For an excellent overview of this issue, see “Campaign for an AI Ready Force,”
https://media.defense.gov/2019/Oct/31/2002204191/-1/- 1/0/CAMPAIGN_FOR_AN_AI_READY_FORCE.PDF.
2 notes
·
View notes