#(putting quotation marks on both words 'cause it's not ai and it's not art)
Explore tagged Tumblr posts
Text
turns out we don't know why the head hurty
got curious and asked Mister Google why the head hurty. Google asked my for my location, then when I declined, told me that scientists don't actually know why the head hurty.
I think this whole "rebranding learning machines as AI" is a bit of what we call "jumping the gun." We are giving these learning machines all our knowledge and hoping it will bang out something cool, but "all our knowledge" doesn't even include why the head hurty. How is a learning machine supposed to bang out something cool if it doesn't even know why the head hurty. Why're we focusing on learning machines when we should be focusing on important things like why the head hurty. The most I can do is take some hurty go away pills. I should be able to take some head hurty go away pills, 'cept can't really do that 'cause we don't know how to stop the head hurty 'cause we don't know why the head hurty. I think we should pause our learning machine nonsense and focus on why the head hurty. We've got more pressing concerns than "can a machine eat other people's hard work and ejaculate out a jumble of pixels that vaguely looks like a watercolor painting of shrek and mario having the hottest of gay sexes." We have far more pressing concerns. Such as why the head hurty.
#in other news my head hurts and I think machine-generated images are bullshit#WOMBO was kinda cool at first 'cause you could type in a sentence and it'd bang something out#but now knowing that it's being fed people's art without their permission.... like...#damn we can't have nice things huh?#always gotta steal and hurt our way to the top#I wanna enjoy ''ai'' ''art''#(putting quotation marks on both words 'cause it's not ai and it's not art)#anyway I wanna enjoy it but. I literally cannot.#it's like trying to enjoy 4th of July but also knowing we killed Natives and oppressed sooooo many people to get here today#...sorry lmao that last part got political#anyway I think I'm a little late to the ai-art nonsense but I live under a rock when it comes to internet things
2 notes
·
View notes
Text
My litany thoughts on 1999 cult classic strategy video game Sid Meier's Alpha Centauri

Alpha Centauri is a game of the early Civilization variety from the EA golden age and ranks very highly in my top ten. While you probably heard of it if you were playing video games around the turn of the century, I've found members of my age cohort to be tragically unfamiliar with this masterpiece.
Alpha Centauri is an unofficial sequel to Civilization II, a game where the only way to way to win is either completely eliminate all competitors to the last city or, rather more easily, send a spaceship loaded with colonists to the title star system. Shortly after leaving home, the ship loses contact with Earth, which would make sense to a player of Civilization II where the bonuses to science and trade from democracies evaporate when technology ends, upon which point all the AIs revolt and become militant fundamentalist theocracies and climate change rapidly destroys the planet, leaving the player with an endgame that is literally 1984. Either way, when the already strained ship arrives at the Alpha Centauri system an unknown partisan assassinates the captain of the UNS Unity and the population fractures into seven opposing factions before firing the colony pods and exploring an inconveniently hostile planet.
The player starts here, in typical Civ fashion: a scout, settler, and absolutely no technology to speak of. That isn't to say you are a bunch of primitives, all your units start out with some approximation to modern guns and judging by the amazing quotes and wonder videos your society is well beyond the 21st century--more on the story later. The gameplay is incredibly well-balanced in spite of its age and quirks (with the exception of the freight-train progression of Yang). Rapid early expansion as the bountiful Peacekeepers may leave you at serious risk to the relentlessly martial Spartans, who are in turn threatened by the uber-specialized technocratic University--but be careful to underestimate the backwards Lord's Believers, their probe teams will just as quickly rob you of your gains. The Morganites can afford to sparsely defend their home if they're willing to pay off their aggressors, but they'll struggle expand over great swaths of territory without irking civil unrest drone riots from corruption. Meanwhile the Gaian Acolytes can harness the permanently-dangerous mindworms to great effect from the beginning of the game. Yang just... builds. And keeps building, and next thing you know he's conquered the Peacekeepers and turned Miriam into nothing more than a puppet and where are all these cruise missiles are coming from?
In short, the strategic design of this game is nothing less than a work of art, but that isn't to say it doesn't have its anachronisms. The User Interface has taken its inspiration from early versions of Microsoft Word and it rapidly pays off to know the hotkeys. The wonder videos are resolution locked and can sometimes cause problems depending on your display configuration. The unit creation system is simultaneously wonderful and horrendous. It allows me to create special long-range nerve gas bombers that eradicate cities shortly before orbitally-dropping specially-trained garrisons to quash all resistance. On the other hand, if you do not accept the cumbersome slew of computer-generated options, keeping your new weapons systems up to date with your latest technology (especially when playing as Zakharov) rapidly becomes a chore.
That said, there are a variety of features in the game that I think deserve to make a reappearance in the Civ Games. The pick-your-government system is incredibly balanced and fun to roleplay. You can't get away with crimes against humanity when solar storms hit in Civilization VI, nor can you weaponise climate change to flood your rivals cities, or strategically terraform to alter weather patterns and deny your neighbors arable land. At the bare minimum, we should be given the option to nerve staple rebelling cities when our control runs out!
All that said, there is also the story to contend with. One is at first tempted to think that a 4x strategy game with a marked emphasis on replayability would necessarily have a tacked-on story, if one at all. After all, the point is for the player to create it through their actions, not have it spoonfed to them. The majority of what you learn about your world that isn't printed in numbers and small pictures on the mapscreen is through blurbs that accompany each discovered technology or new building. The aforementioned wonders even have their adorable early-CG renderings, sometimes mixed in with some experimental film footage. There are occasional interludes that describe the mindworms and machinations of Planet, but the bulk of the wordage comes from epigrams of the faction leaders and the occasional bit of Nietzsche or Plato. It's so good that I can't help but stop and listen to CEO Nbwadibuke Morgan ramble on about supply chain economics or Sister Miriam's apocalyptic warnings every single time. Take some examples.
Proper care and education for our children remains a cornerstone of our entire colonization effort. Children not only shape our future; they determine in many ways our present. Men and women work harder knowing their children are safe and close at hand, and never forget that, with children present, parents will defend their home to the death!
--Col. Corazon Santiago, "Planet: A Survivalist's Guide"
Or perhaps, a more on the nose one:
"The Academician's private residences shall remain off-limits to the Genetic Inspectors. We possess no retroviral capability, we are not researching retroviral engineering, and we shall not allow this Council to violate faction privileges in the name of this ridiculous witch hunt!
--Fedor Petrov, Vice Provost for University Affairs Accompanies the Retroviral Engineering technology
The game often doesn't directly tell you what Retroviral engineering is, nor does it labor to explain just what having someone nerve stapled means, or the precise function of the Recycling Tanks, but through its quotation it beautifully circumlocutes the world you are shaping--and being shaped by. It really never pulls any of its punches, even if its just on Organic Superlube--great stuff--and I still catch muself quoting it regularly.
Ursula LeGuin once wrote
"Science fiction is often described, and even defined, as extrapolative. The science fiction writer is supposed to take a trend or phenomenon of the here-and-now, purify and intensify it for dramatic effect, and extend it into the future. 'If this goes on, this is what will happen.' [...] This may explain why many people who read science fiction describe it as 'escapist,' but when questioned further, admit they do not read it because 'it's so depressing.'"
Alpha Centauri is absolutely extrapolative fiction and very firmly rooted in the 1990s and I love it. It was released in the Aaron Sorkin TV, pre-9/11 days where the word Internet was more often than not followed by the words, "is like an information superhighway" and it absolutely no efforts are made to cover it up. The main factions are a cross-section of the New Millenium's hopes and anxieties. A New Russia that went a very different path before Putin took over, a cheerful clan of ruthless Western capitalists hellbent on putting Morganvision on every network set, a group of vaguely Scottish free-love peaceniks hellbent on defending the most-of-the-time incredibly hostile environment. There's the Second-Amendment preaching Spartans or the optimistically-influential UN which, judging by its naming scheme for its bases, seems to dedicate entire cities to bureaucratic agencies. The All-American Christian fundamentalists don't entirely butt heads with the frighteningly powerful Human-Hive (if your country calls their cities names like "Huddling of the People" and "Paradise Swarming" you might not be the good guys). The expansion also brings in more dynamic characters like the Information Wants to be Free! data angels Brian Reynolds very clearly came up with after watching Swordfish and Hackers back to back or the Nautilus Pirates who have no right to be as fun as they are.
The visions of the future are at once both anachronistic and prophetic; while elements may come off as cheese, I see it as a sort of window to the past, a way to examine what was once (and sometimes still is) on our mind. All in all, I give Sid Meier's Alpha Centauri 4 out of 5 stars and a definite all-time favorite, warts and all. You can pick it and its expansion up for $6 on Gog.com and play it through a built-in emulator that works for most systems. If you're willing to brave a dated interface and an older-fashioned gameplay style, I would definitely recommend it.




#pc gaming#video games#gaming#civilization#writing#ursula leguin#alpha centauri#sid meier's alpha centauri#sid meier's civilization#the drones need you#they look up to you#game retro#game recs#game review
15 notes
·
View notes
Text
PORTFOLIO IN EMPOWERMENT TECHNOLOGY
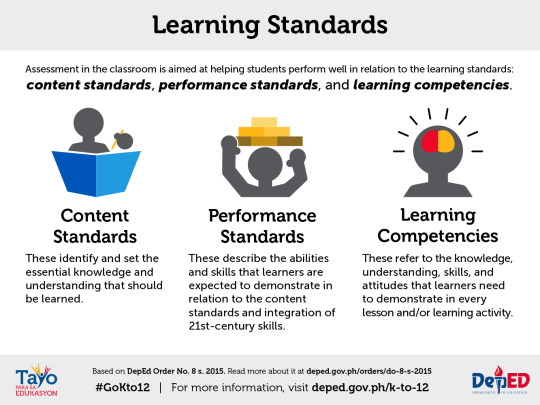
CHAPTER 1 LESSON 1: INFORMATION AND COMMUNICATIONS TECHNOLOGY - Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. CONTENT STANDARD
- The learners demonstrate an understanding of ICT in the context of global communication for specific professional track.
Performance Standards
- The learners shall be able to: at the end of the 2-week period independently compose an insightful reflection paper on the nature of ICT in the context of their lives, society, and professional tracks (Arts, Tech Vocational, Sports and Academic)
Most essential learning competencies
The learners should be able to:
1. Compare and contrast the nuances of varied online platforms, sites, and content to best achieve specific class objectives or address situational challenges.
2. Apply online safety, security, ethics, and etiquette standards and practice in the use of ICTs as it would relate to their professional tracks. 3. Use the internet as a tool for credible research and information gathering to best achieve specific class objectives or address situational.
1.1 INFORMATION AND COMMUNICATION TECHNOLOGY

- ICT is the technology required for information processing, in particular, the use of the electronic computers, communication devices and software applications to convert, store, protect, process, transmit and retrieve information from anywhere, anytime.
- Information refers to the knowledge obtained from reading, investigation, study or research. The tools to transmit information are the telephone, television and radio. Information is knowledge and helps us to fulfill our daily tasks. - Communication is an act of transmitting messages. It is a process whereby information was exchanged between individuals using symbols, signs or verbal interactions. Communication is important in order to gain knowledge. Technology is the use of scientific knowledge, experience and resources to create processes products that fulfill human needs. Technology is vital in communication.
- ICT nowadays has also widened the horizon in developing new tools or emerging technologies. Mobile devices can communicate through wireless fidelity (Wifi), Bluetooth, third generation 3g & 4g, data services and dial up services and virtual private networks. EMERGING TECHNOLOGIES

- Artificial Intelligence (AI) - is the ability of a digital computer or computer controlled robot to perform tasks commonly associated with intelligent beings. The term is frequently applied to the project of developing systems endowed with the intellectual processes characteristics of humans, such as the ability to reason, discover meaning, generalize or learn from past experience. ROBOTICS

- Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. BIOMETRICS

- Are a way to measure a person’s physical characteristics to verify their identity. These can include physiological traits, such as fingerprints and eyes, or behavioral characteristics, such as the unique way you’d complete a security-authentication puzzle. QUANTUM CRYPTOGRAPHY

- Also called quantum encryption, applies principles of quantum mechanics to encrypt messages in a way that it is never read by anyone outside of the intended recipient. COMPUTER ASSISTED TRANSLATION

- Involves the use of software programs to translate both verbal and written texts. Also known as machine-assisted or machine aided translation. 3D IMAGING AND HOLOGRAPHY

- Is defined as a 3D projection that exists freely in space and is visible to everyone without the need for 3D glasses. VIRTUAL REALITY

- Refers to the computer generated simulation in which a person can interact within an artificial 3D environment using special electronic devices that can be similar to or completely different from the real world. ONLINE SAFETY

- Is the knowledge of maximizing the user’s personal safety and security and risk to private information, and self-protection from computer crime in general. 1. Know the scams - Learn about different kinds of scams and what you can do to avoid them.

2. Think before you click - Think twice, thrice and zillion time before click any link or buttons.

3. Safety Peruse - These sites may have an Address that’s very similar to a legitimate site, but the page can have misspelling, Bad Grammar, or low resolution Images.

4. Shop Safety - Don’t shop on a site unless it has “https” and a padlock icon on the left or right in the URL.

5. Kick-butt passwords - Use an Extremely uncrackable password One like “9&4thkel965#”.
6. Protect your info’s - Keep your guard up, Back up all your data on your computer, smartphone and tablet, theft or a cash.

7. Watch your Wi-Fi Connectivity - Protect your network by changing your router’s setting and making sure that you have the connection password protected.

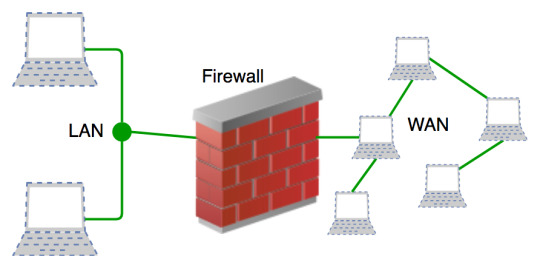
8. Install a Firewall - A firewall is a grate line of defense against cyber attracts.
9. Keep up to date - The best security updates automatically to protect your computer. - Use the manufacturer’s latest security patches to make regular updates and make that you have the software set to do routine scam.

10. Use your Noggin - Use your common sense while surfing the web.

COMMON ISSUES AND CRIMES IN THE INTERNET - CYBERBULLYING - HACKING - IDENTITY THEFT - PLAGIARISM - COPYRIGHT ISSUES CYBERBULLYING - Is a form of bullying or harassment using electronic means. Cyberbullying and Cyber Harassment are also known as online bullying. - Cyberbullying is when someone, typically teens, bully or harass others on the internet, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims’ personal information, or pejorative labels. THE ANTI-BULLYING ACT OF 2013 ( RA 10627 )
(Sec. 2, RA 10627) These acts are collectively “called cyber bullying” when committed online. (Sec. 2-D, RA 10627) This covers social bullying aiming to belittle another individual or group or gender-based bullying that humiliates another on the basis of perceived or actual sexual orientation and gender identity. (Sec. 3, B-1 RA 10627. Implementing Rules). THE REVISED PENAL CODE AND THE CYBERCRIME PREVENTION ACT. - One who publicly or maliciously imputes to another a crime, vice, defect, real or imaginary, or any act, omission, condition, status or circumstance tending to cause the dishonor, discredit or contempt of a natural or juridical person, or blacken the memory of one who is dead may be liable for libel under this Code. (Art, 353, RPC) These acts are more severely punished when done online in addition to the civil action for damages which may be brought by the offended party. (Sec. 4(c-4), RA 10175) Cyberlibel holds liable only the original author of the post (Sec. 5(3), Implementing Rules of RA 10175) Likers or shares of a post cannot be held liable under this law. - Slander may also be applicable to one who, in heat of anger, utters statements that are highly defamatory in character. (Art 358, RPC) Intriguing Against Honour may also find applicability when the principal purpose is to blemish the honour or reputation of a person. Hence, a blind ite is not as actionable as a named-post in social media. HACKING

- Hacking generally refers to unauthorized intrusion into a computer or a network. The person engaged in hacking activities is known as a hacker. This hacker may alter system or security features to accomplish a goal that differs from the original purpose of the system. - Hacking can also refer to non-malicious activities, usually involving unusual or improvised alterations to equipment or processes.
IDENTITY THEFT

- Also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information, such as Social Security or driver's license numbers, in order to impersonate someone else. TYPES AND EXAMPLES OF IDENTITY THEFT 1. True-name identity theft means the thief uses personal information to open new accounts. The thief might open a new credit card account, establish cellular phone service or open a new checking account in order to obtain blank checks. 2. Account-takeover identity theft means the imposter uses personal information to gain access to the person's existing accounts. PLAGIARISM

- Is an act of fraud. It involves both stealing someone else's work and lying about it afterward. The following are considered plagiarism - turning in someone else's work as your own - copying words or ideas from someone else without giving credit - failing to put a quotation in quotation marks - giving incorrect information about the source of a quotation - changing words but copying the sentence structure of a source without giving credit - copying so many words or ideas from a source that it makes up the majority of your work, whether you give credit or not (see our section on "fair use" rules) Republic Act No. 8293 [An Act Prescribing the Intellectual Property Code and Establishing the Intellectual Property Office, Providing for Its Powers and Functions, and for Other Purposes]otherwise known as the Intellectual Property Code of the Philippines. Intellectual property rights under the I. P. Code: The intellectual property rights under the Intellectual Property Code are as follows: 1. Copyright and related rights; 2. Trademarks and service marks; 3. Geographic indications; 4. Industrial designs; 5. Patents; 6. Layout designs [topographies] of integrated circuits; and 7. Protection of undisclosed information. The scheme of penalties for infringement has also been changed. From the previous fine of Php200 to Php2,000 and/or imprisonment of 1 year, the current range of penalties are as follows: - For first offenders - fine of PhP50,000 to PhP150,000 and/or imprisonment of 1 to 3 years - For second offenders - fine of PhP150,000 to PhP500,000 and/or imprisonment of 3 to 6 years - For third and subsequent offenders - fine of PhP500,000 to PhP1.5 Million and/or imprisonment of 6 to 9 years. - In case of insolvency, the offender shall furthermore suffer subsidiary imprisonment. NETIQUETTE - Is a combination of the word net and etiquette.It focuses on the acceptable behavior of a person while using the internet resource. - It focuses on the acceptable behavior of a person while using the internet resource. The Core Rules of Netiquette Rule 1. Remember the human. - Never forget that the person reading your mail or posting is, indeed, a person, with feelings that can be hurt. - Corollary 1 to Rule #1: It's not nice to hurt other people's feelings. - Corollary 2: Never mail or post anything you wouldn't say to your reader's face. - Corollary 3: Notify your readers when flaming. Rule 2. Adhere to the same standards of behavior online that you follow in real life. Corollary 1: Be Ethical Corollary Corollary 2: Breaking the law is bad Netiquette. Rule 3. Know where you are in cyberspace. Corollary 1: Netiquette varies from domain to domain. Corollary 2: Lurk before you leap. Rule 4. Respect other people's time and bandwidth. Corollary 1: It's OK to think that what you're doing at the moment is the most important thing in the universe, but don't expect anyone else to agree with you Corollary 2: Post messages to the appropriate discussion group.Corollary 3: Try not to ask stupid questions on discussion groups Corollary 4: Read the FAQ (Frequently Asked Questions) document Corollary 5: When appropriate, use private email instead of posting to the group Corollary 6: Don't post subscribe, unsubscribe, or FAQ requests Corollary 7: Don't waste expert readers' time by posting basic information Corollary 8: If you disagree with the premise of a discussion group, don't waste the time and bandwidth of the members by telling them how stupid they are.Just stay away Corollary 9: Conserve bandwidth when you retrieve information from a host or server. Rule 5. Make yourself look good online. Corollary 1: Check grammar and spelling before you post Corollary 2: Know what you're talking about and make sense Corollary 3: Don't post flame-bait Rule 6. Share expert knowledge. Corollary 1: Offer answers and help to people who ask questions on discussion groups Corollary 2: If you've received email answers to a posted question, summarize them and post the summary to the discussion group. Rule 7. Help keep flame wars under control. Corollary 1: Don't respond to flame-bait Corollary 2: Don't post spelling or grammar flames Corollary 3: If you've posted flame-bait or perpetuated a flame war, apologize Rule 8. Respect other people's privacy. - Don't read other people's private email. Rule 9. Don't abuse your power. - The more power you have, the more important it is that you use it well Rule 10. Be forgiving of other people's mistakes. CONTEXTUALIZED ONLINE SEARCH AND RESEARCH SKILLS

- Online search is the process of interactively searching for and retrieving requested information via a computer from databases that are online. Interactive searches became possible in the 1980s with the advent of faster databases and smart terminals. Advantages and Disadvantages Advantages: - Ability to obtain a large sample, which increases statistical power - Data is automatically coded so no data entry errors - Reduced cost of conducting research Disadvantages: Online is not totally secure and theft is one of the numerous danger it poses, researchers personal information is at risk of being access by rogue persons. - Some of the materials on the internet have not been evaluated by experts or thoroughly screened - Lack of accreditation and low quality
RESEARCH SKILLS “Research” sometimes just means finding out information about a topic.You can certainly develop advanced information retrieval skills in Working with Sources. However, in specific understandings of “research” carry a lot of weight. The classic definition is that “research” leads to an original contribution to knowledge in a particular field of inquiry by defining an important question or problem and then answering or solving it in a systematic way. - So you will need to read on to develop a relevant understanding of what research means in your subject. - Research skills can be anything from looking at competitors and seeing what they do well to producing a written report on how your department could work better. Doing research in the world of work is all about stepping back from your day-to-day work and looking at ways you can improve. Important aspects of research: - Research design covers the key issues in developing a successful research project. - Research methods takes you to resources on essential techniques for carrying out convincing research. - Working with data will provide resources on the use of statistics and other numerical skills in research. Improving Your Research Skills Online 1. Know your sources. Make sure to find the most reliable information which can be found in multiple sources or, better, to have the original source. 2. Use your web browser properly. Know the capabilities of your preferred browser to help make your search faster and easier. 3. Organize your bookmarks. It is to organize the links you have marked. 4. Learn to use advanced search engines. Practice using advanced search techniques which are available in Google. 5. Follow the web. Follow the web information in the web. Just make sure to read and be critical in every link you click. SIX STRATEGIES THAT CAN HELP ONLINE STUDENTS PRODUCE STRONGER RESEARCH. 1. Contact a librarian before getting stuck sifting through piles of online information. 2. Consider that when in doubt, it's wiser to over-cite sources than risk plagiarism. 3. Use Google and other reliable resources at the beginning of a research process, not the end. 4. Don't think that the Web is your only source of information. 5. Understand the professor's expectations for citation format. 6. Understand why professors still assign research projects. Some examples of research skills that you may have include: 1. Report writing. 2. Analyzing lots of information from different sources. 3. Finding information off the internet. 4. Critical thinking. CHAPTER 2 APPLIED PRODUCTIVITY TOOLS Productivity Tools - It is a tools that can be a freeware or shareware. Freeware - is copyrighted, which can be used for free and for an unlimited time. Shareware - is a commercial software that is copyrighted, which can be copied for trial but needs to be purchased for continued use. Advanced Techniques Using Microsoft Word Microsoft Office Word

- One of the software of Microsoft Office 2013 suite. - Offers a set of tools that is compared to its previous versions. - Along with its new features are advanced techniques including hyperlinks, macros and mail merge. Hyperlink
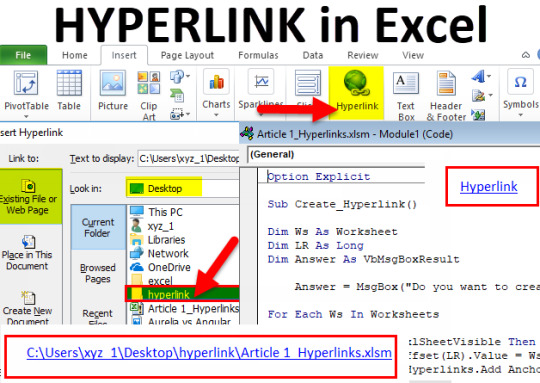
- A link that will direct you to another page or part of the same document. Creating a Hyperlink to an Existing Document - Suppose you are to link a part of your document to an existing document. - Click your mouse on the location in the document where you want to insert the hyperlink. - On the Insert Tab, click the Hyperlink button on the Links group. - On the Insert Hyperlink dialog box, click Existing File or Web Page and then select the File name where the source file is located and then hyperlink will be created on your document. - Press Ctrl+ click on the Hyperlink to open the linked file. Mail Merge
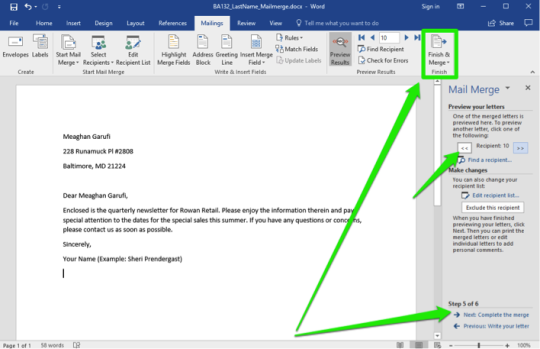
- Is a useful tool that allows you to quickly produce and send information, newsletter, resumes, or brochures to many people. Creating a Mail Merge 1. Open the word document that you want to Mail Merge. 2. On the Ribbon, click the Mailings tab, go to the Start Mail Merge group and click Start Mail Merge and select Step by Step Mail Merge Wizard. 3. The task pane will show the Mail Merge steps 1 to 6. PowerPoint

- It allows you to create slide show presentations wherein you can format the texts and images, adding also animations and other multimedia components interactively. Excel

- One of the applications created by Microsoft, used to simulate a paper worksheet.
- It is composed of cells that are represented in rows and columns design to perform basic arithmetic operations. - Widely used in accounting and financial applications, as well as statistics and engineering calculations. The following are the common Excel Functions: = SUM – Calculates the sum of the values of a range of cells = AVERAGE – Calculates the arithmetic mean of a range of cells = MAX - Gives the maximum value in a range of cells = MIN - Gives the minimum value in a range of cells = COUNT - Counts the number of cells in a range of cells BENIFITS OF ONLINE SOFTWARE Convenience - The applications should be intuitive and easy to use to ensure everyone can use them without spending a lot of time learning how. Scalability - The applications should be able to be used in all areas of your business and also work effectively no matter how much demand there is to use them or how much your business grows. Safety - All the applications should be safe to use with all existing systems and should have the ability to fully integrate with all other software and not inhibit the workers ability to do their job. Sustainability - All consumer-based software should be flexible and adaptable to have the ability to last for up to 10 years, but they must be able to expand functionally with other developments in software and operating systems. PRINCIPLES OF GRAPHICS AND DESIGN BALANCE UNITY MOVEMENT REPITITION PROXIMITY CONTRAST WHITESPACE BALANCE

- Describes the placement of elements of equal weight on the page. MOVEMENT

- Describes the flow of elements on the page.
1 note
·
View note