#government case management software
Explore tagged Tumblr posts
Text
How does Government Case Management Software Handle Data Security and Privacy for Public Sector Agencies?
https://www.speridian.com/blogs/gov-case-management-software-handle-data-security-and-privacy-for-public-sector/

#case management software for government#case management for government#government case management software#Low code Business Process Automation Suite For Government#case management platform#case management system#case management software
0 notes
Text
What is Dataflow?
This post is inspired by another post about the Crowd Strike IT disaster and a bunch of people being interested in what I mean by Dataflow. Dataflow is my absolute jam and I'm happy to answer as many questions as you like on it. I even put referential pictures in like I'm writing an article, what fun!
I'll probably split this into multiple parts because it'll be a huge post otherwise but here we go!
A Brief History

Our world is dependent on the flow of data. It exists in almost every aspect of our lives and has done so arguably for hundreds if not thousands of years.
At the end of the day, the flow of data is the flow of knowledge and information. Normally most of us refer to data in the context of computing technology (our phones, PCs, tablets etc) but, if we want to get historical about it, the invention of writing and the invention of the Printing Press were great leaps forward in how we increased the flow of information.
Modern Day IT exists for one reason - To support the flow of data.
Whether it's buying something at a shop, sitting staring at an excel sheet at work, or watching Netflix - All of the technology you interact with is to support the flow of data.
Understanding and managing the flow of data is as important to getting us to where we are right now as when we first learned to control and manage water to provide irrigation for early farming and settlement.
Engineering Rigor
When the majority of us turn on the tap to have a drink or take a shower, we expect water to come out. We trust that the water is clean, and we trust that our homes can receive a steady supply of water.
Most of us trust our central heating (insert boiler joke here) and the plugs/sockets in our homes to provide gas and electricity. The reason we trust all of these flows is because there's been rigorous engineering standards built up over decades and centuries.

For example, Scottish Water will understand every component part that makes up their water pipelines. Those pipes, valves, fitting etc will comply with a national, or in some cases international, standard. These companies have diagrams that clearly map all of this out, mostly because they have to legally but also because it also vital for disaster recovery and other compliance issues.
Modern IT
And this is where modern day IT has problems. I'm not saying that modern day tech is a pile of shit. We all have great phones, our PCs can play good games, but it's one thing to craft well-designed products and another thing entirely to think about they all work together.
Because that is what's happened over the past few decades of IT. Organisations have piled on the latest plug-and-play technology (Software or Hardware) and they've built up complex legacy systems that no one really knows how they all work together. They've lost track of how data flows across their organisation which makes the work of cybersecurity, disaster recovery, compliance and general business transformation teams a nightmare.

Some of these systems are entirely dependent on other systems to operate. But that dependency isn't documented. The vast majority of digital transformation projects fail because they get halfway through and realise they hadn't factored in a system that they thought was nothing but was vital to the organisation running.
And this isn't just for-profit organisations, this is the health services, this is national infrastructure, it's everyone.
There's not yet a single standard that says "This is how organisations should control, manage and govern their flows of data."
Why is that relevant to the companies that were affected by Crowd Strike? Would it have stopped it?
Maybe, maybe not. But considering the global impact, it doesn't look like many organisations were prepared for the possibility of a huge chunk of their IT infrastructure going down.
Understanding dataflows help with the preparation for events like this, so organisations can move to mitigate them, and also the recovery side when they do happen. Organisations need to understand which systems are a priority to get back operational and which can be left.
The problem I'm seeing from a lot of organisations at the moment is that they don't know which systems to recover first, and are losing money and reputation while they fight to get things back online. A lot of them are just winging it.
Conclusion of Part 1
Next time I can totally go into diagramming if any of you are interested in that.
How can any organisation actually map their dataflow and what things need to be considered to do so. It'll come across like common sense, but that's why an actual standard is so desperately needed!
789 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes
Text
Vittoria Elliott at Wired:
Elon Musk’s takeover of federal government infrastructure is ongoing, and at the center of things is a coterie of engineers who are barely out of—and in at least one case, purportedly still in—college. Most have connections to Musk and at least two have connections to Musk’s longtime associate Peter Thiel, a cofounder and chairman of the analytics firm and government contractor Palantir who has long expressed opposition to democracy. WIRED has identified six young men—all apparently between the ages of 19 and 24, according to public databases, their online presences, and other records—who have little to no government experience and are now playing critical roles in Musk’s so-called Department of Government Efficiency (DOGE) project, tasked by executive order with “modernizing Federal technology and software to maximize governmental efficiency and productivity.” The engineers all hold nebulous job titles within DOGE, and at least one appears to be working as a volunteer. The engineers are Akash Bobba, Edward Coristine, Luke Farritor, Gautier Cole Killian, Gavin Kliger, and Ethan Shaotran. None have responded to requests for comment from WIRED. Representatives from OPM, GSA, and DOGE did not respond to requests for comment. Already, Musk’s lackeys have taken control of the Office of Personnel Management (OPM) and General Services Administration (GSA), and have gained access to the Treasury Department’s payment system, potentially allowing him access to a vast range of sensitive information about tens of millions of citizens, businesses, and more. On Sunday, CNN reported that DOGE personnel attempted to improperly access classified information and security systems at the US Agency for International Development (USAID), and that top USAID security officials who thwarted the attempt were subsequently put on leave. The AP reported that DOGE personnel had indeed accessed classified material. “What we're seeing is unprecedented in that you have these actors who are not really public officials gaining access to the most sensitive data in government,” says Don Moynihan, a professor of public policy at the University of Michigan. “We really have very little eyes on what's going on. Congress has no ability to really intervene and monitor what's happening because these aren't really accountable public officials. So this feels like a hostile takeover of the machinery of governments by the richest man in the world.”
[...] “To the extent these individuals are exercising what would otherwise be relatively significant managerial control over two very large agencies that deal with very complex topics,” says Nick Bednar, a professor at University of Minnesota’s school of law, “it is very unlikely they have the expertise to understand either the law or the administrative needs that surround these agencies.” Sources tell WIRED that Bobba, Coristine, Farritor, and Shaotran all currently have working GSA emails and A-suite level clearance at the GSA, which means that they work out of the agency’s top floor and have access to all physical spaces and IT systems, according a source with knowledge of the GSA’s clearance protocols. The source, who spoke to WIRED on the condition of anonymity because they fear retaliation, says they worry that the new teams could bypass the regular security clearance protocols to access the agency’s sensitive compartmented information facility (SCIF), as the Trump administration has already granted temporary security clearances to unvetted people. This is in addition to Coristine and Bobba being listed as “experts” working at OPM. Bednar says that while staff can be loaned out between agencies for special projects or to work on issues that might cross agency lines, it’s not exactly common practice.
WIRED’s report on the 6 college-aged men between 19 and 24 that are shaping up DOGE in aiding and abetting in co-”President” Elon Musk’s technofascist takeover.
#Elon Musk#DOGE#Department of Government Efficiency#Trump Administration II#General Services Administration#Office of Personnel Management#Scott Bessent#USAID#Akash Bobba#Edward Coristine#Luke Farritor#Gautier Cole Killian#Gavin Kliger#Ethan Shaotran#Treasury Department#Musk Coup
65 notes
·
View notes
Note
400 request! Leon x female reader. How they meet or first impressions.
(Also omg I’m so happy you write about resident evil too!)
Thank you, anon! I'm happy I write about Resident Evil too x Travel Pillow Leon Kennedy x female reader, fluff
Looking at the rain smacking against the tarmac through the plane window, you’re not convinced you will be taking off any time soon, despite the airline’s confidence when they’d opened the boarding gate 20 minutes ago. The last of the passengers are finding their seats in the small plane, only two seats either side of the aisle. You feel a knee bash against your thigh and you turn, seeing a handsome man with light brown hair framing bright blue eyes, jeans with a white tee and a semi-smart black jacket stood over the empty seat, looking apologetic.
“Sorry.” He rubs the back of his head, scolding himself for a bad first impression on the pretty girl he is going to be sitting next to for the next three hours. “I swear they make the leg room on these tin cans smaller and smaller every time.”
“No harm done. And, yeah, I agree - trying to get you to splurge for the emergency exit.”
“Mm, and my work won’t cover that expense.” He tugs off his jacket before he sits down, banging his knee against the upturned tray table on the seat in front and winces. “Yep, should’ve got some knee pads.”
You laugh at that and he smiles, sensing it’s genuine in nature. Makes a change.
“Name’s Leon.” He offers you his hand and you take it, giving it a shake and offering your name in return.
“Take it you’re traveling for business, then?” You probe – he’s easy on the eyes and much more interesting to look at than the rain out the window.
“Was.” He leans back, buckling up his seatbelt. “On the way home now. You?”
“Moving - starting a new job on Monday.”
“Oh, wow. Moving via plane?”
You shake your head. “Got a guy driving my stuff over in a few days. Only got the job offer Wednesday.”
“Huh,” Leon mulls. “They sound pretty keen for you.”
“Yeah, well-”
The PA system pings, interrupting you. There’s a crackle of static before a voice rings out. “Good evening, this is your captain speaking. I’m afraid we have a storm warning rolling in and, currently, we are unable to take off. As we are still at the gate and it will be a little while before we can depart, we are going to ask you to disembark.” Groans ring around the plane. “Please be sure to take all your hand luggage with you and be sure to pick up your complimentary drinks voucher from the cabin crew.”
“Bets on it excluding alcohol?” Leon asks, unbuckling his seat belt and getting to his feet as your fellow passengers follow suit - grumbling about the delay, grabbing their bags. “Got anything in the overhead?”
“Yeah.” You get to your feet, having to hunch over a little as the side of the plane slopes. “Black duffel bag.”
“I got it.”
“What a gentleman.” You smile, watching as he raises his arms above his head to reach for your bag, your eyes lingering on the way his biceps tense.
“I may have an ulterior motive.” He smirks, pulling the bag down and hanging it off his shoulder with ease. You hadn’t been exactly subtle while you had admired his arms.
“Oh?”
“Hoping you might partake in a non-complimentary drink with me.”
“I think I can manage that.”
--
“So, what do you do?”
You’d grabbed a cosy table for two in the corner of the airport bar, a clear view of the departures board in sight in case any news came through about your delayed flight. The complimentary drinks voucher had excluded alcohol, so you had ended up with two drinks in front of you – a soda from the airline that you’d quickly polished off, and one from your handsome seat-mate that you made sure to take your time over.
“Me?” Leon shrugs a shoulder. “I work for the government – just boring bureaucratic nonsense, wrapped up in a lot of red tape. How about you?”
“Software.”
“Guess you’re pretty skilled to be in such high demand.”
“Something like that. Just a niche area. Money was too good to say no.” It wasn’t strictly a lie. “And, if I can be so bold, no-one to leave behind?”
“Bingo.”
“Well, I feel that. No-one for me to return home to. Work keeps me too busy – can be away a few days to a few months.”
“Ah, so you don’t always flirt with women you meet on planes?”
“No,” he shakes his head, “This is just an elaborate apology for bashing your knee earlier.” “Gotcha.” You take another sip of your drink. “So, how long have you lived in DC?”
“A few years now, on and off.”
“Good, then you can tell me all of the bad coffee shops and tourist traps I need to avoid.”
Leon shakes his head, grinning all the while. “I can’t hand over that information, you’ve gotta work your way through sucky cups of coffee like every other fine resident that came before you.”
“Please?” You pout, tilting your head and he’s so tempted to give in with how adorable you look.
“Cute, but no. You’ll understand one day.”
“Not even a clue?”
“Uh-uh, I’m sorry.”
“No, you’re not.”
“Yeah,” he lifts his glass to his lips, trying to hide his smile. “I’m not.”
“Is there anything you can tell me about DC, then?”
He ponders for a moment. “They really like brunch.”
“Maybe…” you rest your hand on the table, wondering if you could reach out and touch his, “..you could take me for br-“
“Passengers for delayed flight AA4628 are asked to head towards gate 34 to commence boarding.” The PA system announces from above your heads. “That’s passengers for delayed flight AA4628 are asked to head towards gate 34 to commence boarding. Thank you.”
“Guess we better head back.” Leon downs his drink and gets to his feet, heaving your bag back over his shoulder.
“Mm,” you agree, downing the rest of your own and your question, and following him back to the gate.
--
The drink must’ve gone more to your head than you thought, especially after a frantic few days of packing, late nights from trying to get everything in order before you moved across the country because you don’t remember the plane even taking off. You wake up to your ears popping as the plane begins its descent and slowly open your eyes, wondering why the seat in front of you is at an angle. It’s then you realise you’re not upright in your own seat, instead cuddling up into someone’s chest, almost nuzzling your cheek into them, an arm draped around your shoulders.
You shoot up, the arm sliding off and you see Leon besides you, smiling sleepily, “Hey, sleepyhead.”
“I am so sorry.” You can feel your cheeks burn as you worry if you drooled, or snored or…
“What, for using me as a pillow?” He chuckles. “It’s fine. For the record, I fell asleep too so it was mutually beneficial.”
“Oh. Good.” You nod, settling back into an awkward silence as the plane continues its descent towards the tarmac and you turn your attention to the window, looking down at the place you’ll be calling home for however long.
As the plane lands and begins taxiing to the gate you wonder if you should ask Leon for his number, or give him your own. It would be nice to know someone in DC, after all. You pull your phone out your pocket, about to ask when an air stewardess appears at Leon’s side, whispers in his ear and he smiles, nods in thanks and unbuckles his seatbelt to stand, before he hesitates and turns to look at you, noting your look of confusion.
“Seems work’s been waiting for me since our delay. My boss has pulled some strings to get me off the flight first, so…” He swallows, disappointed - though he knows he shouldn’t be. He knew from the moment you started talking, despite the feeling in his stomach, that it was fantasy where he could pretend that after you’d arrived in DC, the two of you could exchange numbers and he’d take you out for the good coffee, brunch and dinner, buy you flowers, kiss you under the streetlights…
Idiot, he reprimands himself. You’re a sweet girl, too sweet for the world he’s involved in.
“It was nice to meet you.” He smiles. “Good luck with the new job.”
“Oh.” You can’t hide your disappointment as he finally stands, the air stewardess waiting to lead him back up the aisle. “Thanks. Nice to meet you too, Leon.”
He nods, once, and you watch him walk away.
--
You hesitate outside your new work, the building looming over you. You still don’t know how to feel about this, but how can you reject a job offer from the President of the United States? You bin the cup of coffee you’d bought from a cart in the park on the way here – mistake, curse Leon for not giving you any heads up – and walk inside, navigating through security and reception, before being told to head up to floor three where an Ingrid Hunnigan is waiting to brief you, standing by the elevator doors. She’s a smartly dressed woman, curly hair tied up in a bun and studious glasses, though she greets you with a smile and a handshake.
“Welcome to the DSO. Glad to have you – I’ve been admiring your work over the weekend.”
“Oh, thank you. I’m… It’s good to be here.” You correct.
Hunnigan doesn’t press, instead gesturing you forward. “Sorry, I promise we’ll do a whistlestop tour another time, but you’re going to be hitting the ground running this morning – we have an intel briefing at 0915.”
“We?”
“Mm – me, you and Agent Kennedy.”
You’re led to a small meeting room and told to take a seat, but Hunnigan remains standing by the door.
“Coffee? Since I haven’t had chance to give you the tour, it’s the least I could do.”
“Oh, yeah. Thank you.” You reply, taking a seat.
“Be right back.”
You fiddle with the hem of your shirt, looking around at the room – not that there’s much to take in, it’s a small, circular table with six chairs around it, a projector hanging from the ceiling and some adaptor cables poking out the middle for someone to connect a laptop.
The door opens a couple of moments later and you turn your head, eyes widening at the figure who enters.
Leon looks equally surprised for a moment before a smirk crosses his lips and he strides in, taking the seat opposite. He leans back in his chair, crosses his arms and quirks an eyebrow.
“Software, huh?”
--
You wake up to your ears popping as the plane begins its descent, your face resting on Leon’s chest, his arm wrapped around your shoulders and head resting atop your own – an all too familiar routine when you travel together by plane. You nuzzle your cheek into his warmth, feeling too content to open your eyes just yet when you feel him move and place a kiss upon your crown.
“Afraid it’s time to wake up, sweetheart”
“Mm, five more minutes. We can’t be landing already, we only just left the gate.” You protest.
His chuckle vibrates through your cheek. “You were out like a light before we even took off. I’m beginning to worry you only keep me around as your personal travel pillow.”
Sighing, you sit upright, trying to rub the crick out of your neck. “That, among other reasons.”
“What other reasons?”
“Hmm,” you pretend to muse, cupping his face in your palm and press a soft kiss to his lips before pressing your forehead against his. “Cos I love you.”
“Love you more.”
-- Comments, likes and reblogs make my whole day! x Masterlist . Requests welcome . Commissions/Ko-Fi
400 notes
·
View notes
Text
April 11, 2025
HEATHER COX RICHARDSON
APR 12
READ IN APP
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
—
15 notes
·
View notes
Text

Matt Davies
* * * *
LETTERS FROM AN AMERICAN
April 11, 2025
Heather Cox Richardson
Apr 12, 2025
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#political cartoons#Matt Davies#The Big Chill#Heather Cox Richardson#Letters from An American#personal data#the right to privacy#identity theft#mistaken identity#SCOTUS#secretary of defense#homeland security#incompetence#data mining#data weaponization
15 notes
·
View notes
Text
So this is what the Biden administration spent it's last week in office doing. It's important to know this isn't unusual activity for them. But this is all just in one week:
"Out With a Bang: Enforcers Go After John Deere, Private Equity Billionaires
https://www.thebignewsletter.com/p/out-with-a-bang-enforcers-go-after
At least for a few more days, laws are not suggestions. In the end days of strong enforcement, a flurry of litigation is met with a direct lawsuit by billionaires against Biden's Antitrust chief.
Matt Stoller
Jan 16, 2025
It’s less than a week until this era of antitrust ends. And while much of the news has been focused elsewhere, enforcers have engaged in a flurry of action, which will by legal necessity continue into the next administration. One case in particular angered some of the most powerful people on Wall Street, the partners of a $600 billion private equity firm called Kohlberg Kravis Roberts (KKR).
But before getting to that suit, here’s a partial list of some of the actions enforcers have taken in the last two weeks.
The Federal Trade Commission
Filed a monopolization claim against agricultural machine maker John Deere for generating $6 billion by prohibiting farmers from being able to repair their own equipment, a suit which Wired magazine calls a “tipping point” for the right to repair movement.
Released another report on pharmacy benefit managers, including that of UnitedHealth Group, showing that these companies inflated prices for specialty pharmaceuticals by more than $7 billion.
Sued Greystar, a large corporate landlord, for deceiving renters with falsely advertised low rents and not including mandatory junk fees in the price.
Issued a policy statement that gig workers can’t be prosecuted for antitrust violations when they try to organize, and along with the Antitrust Division, updated guidance on labor and antitrust.
Put out a series of orders prohibiting data brokers from selling sensitive location information.
Finalized changes to a rule barring third party targeted advertising to children without an explicit opt-in.
The Consumer Financial Protection Bureau
Went to court against Capital One for cheating consumers out of $2 billion by deceiving them on savings accounts and interest rates.
Fined cash app purveyor Block $175 million for fostering fraud on its platform and then refusing to offer customer support to affected consumers.
Proposed a rule to prohibit take-it-or-leave-it contracts from financial institutions that allow firms to de-bank users over how they express themselves or whether they seek redress for fraud.
Issued a report with recommendations on how states can update their laws to protect against junk fees and privacy abuses.
Sued credit reporting agency Experian for refusing to investigate consumer disputes and errors on credit reports.
Finalized a rule to remove medical debt from credit scores.
The Antitrust Division
Sued to block a merger of two leading business travel firms, American Express Global Business Travel Group and CWT Holdings.
Filed a complaint against seven giant corporate landlords for rent-fixing, using the software and consulting firm RealPage.
Got four guilty pleas in a bid-rigging conspiracy by IT vendors against the U.S. government, a guilty plea from an asphalt vendor company President, and convicted five defendants in a price-fixing scam on roofing contracts.
Issued a policy statement that non-disclosure agreements that deter individuals from reporting antitrust crimes are void, and that employers “using NDAs to obstruct or impede an investigation may also constitute separate federal criminal violations.”
Filed two amicus briefs with the FTC, one supporting Epic Games in its remedy against Google over app store monopolization, and the other supporting Elon Musk in his antitrust claims against OpenAI, Microsoft, and Reid Hoffman.
And honorary mention goes to the Department of Transportation for suing Southwest and fining Frontier for ‘chronically delayed flights.’"
It's worth reading the entire piece because the Biden people have also gone after KKR which is one of the biggest and most well-connected private equity firms. Remember when suddenly last year all the rich people who used to donate to both parties stopped giving money to Democrats? The billionaires coup against Biden was because of anti trust enforcement.
IF YOU'RE THINKING "GOSH I NEVER HEARD ABOUT ANY OF THIS BEFORE" I HOPE YOU CAN PUT TOGETHER THAT THE NEWS AND SOCIAL MEDIA PLATFORMS ARE ALL OWNED BY BILLIONAIRES WHO ARE VERY ANGRY ABOUT ALL OF THIS AND MAYBE THAT'S WHY YOU NEVER SAW ANYONE TALK ABOUT THE HUGE RESURGENCE OF ANTI TRUST WORK DONE BY BIDEN FOR THE LAST FOUR YEARS.
And no, Trump cannot magically make this all go away. The lawsuits will have to be played out and many of them have state level components that mean the feds can't just shut them down.
X
11 notes
·
View notes
Text

NASA and Italian Space Agency test future lunar navigation technology
As the Artemis campaign leads humanity to the moon and eventually Mars, NASA is refining its state-of-the-art navigation and positioning technologies to guide a new era of lunar exploration.
A technology demonstration helping pave the way for these developments is the Lunar GNSS Receiver Experiment (LuGRE) payload, a joint effort between NASA and the Italian Space Agency to demonstrate the viability of using existing GNSS (Global Navigation Satellite System) signals for positioning, navigation, and timing on the moon.
During its voyage on an upcoming delivery to the moon as part of NASA's CLPS (Commercial Lunar Payload Services) initiative, LuGRE would demonstrate acquiring and tracking signals from both the U.S. GPS and European Union Galileo GNSS constellations during transit to the moon, during lunar orbit, and finally for up to two weeks on the lunar surface itself.
The LuGRE payload is one of the first demonstrations of GNSS signal reception and navigation on and around the lunar surface, an important milestone for how lunar missions will access navigation and positioning technology.
If successful, LuGRE would demonstrate that spacecraft can use signals from existing GNSS satellites at lunar distances, reducing their reliance on ground-based stations on the Earth for lunar navigation.
Today, GNSS constellations support essential services like navigation, banking, power grid synchronization, cellular networks, and telecommunications. Near-Earth space missions use these signals in flight to determine critical operational information like location, velocity, and time.
NASA and the Italian Space Agency want to expand the boundaries of GNSS use cases. In 2019, the Magnetospheric Multiscale (MMS) mission broke the world record for farthest GPS signal acquisition 116,300 miles from the Earth's surface—nearly half of the 238,900 miles between Earth and the moon. Now, LuGRE could double that distance.
"GPS makes our lives safer and more viable here on Earth," said Kevin Coggins, NASA deputy associate administrator and SCaN (Space Communications and Navigation) Program manager at NASA Headquarters in Washington. "As we seek to extend humanity beyond our home planet, LuGRE should confirm that this extraordinary technology can do the same for us on the moon."
Reliable space communication and navigation systems play a vital role in all NASA missions, providing crucial connections from space to Earth for crewed and uncrewed missions alike. Using a blend of government and commercial assets, NASA's Near Space and Deep Space Networks support science, technology demonstrations, and human spaceflight missions across the solar system.
"This mission is more than a technological milestone," said Joel Parker, policy lead for positioning, navigation, and timing at NASA's Goddard Space Flight Center in Greenbelt, Maryland.
"We want to enable more and better missions to the moon for the benefit of everyone, and we want to do it together with our international partners."
The data-gathering LuGRE payload combines NASA-led systems engineering and mission management with receiver software and hardware developed by the Italian Space Agency and their industry partner Qascom—the first Italian-built hardware to operate on the lunar surface.
Any data LuGRE collects is intended to open the door for use of GNSS to all lunar missions, not just those by NASA or the Italian Space Agency. Approximately six months after LuGRE completes its operations, the agencies will release its mission data to broaden public and commercial access to lunar GNSS research.
"A project like LuGRE isn't about NASA alone," said NASA Goddard navigation and mission design engineer Lauren Konitzer. "It's something we're doing for the benefit of humanity. We're working to prove that lunar GNSS can work, and we're sharing our discoveries with the world."
The LuGRE payload is one of 10 science experiments launching to the lunar surface on this delivery through NASA's CLPS initiative.
Through CLPS, NASA works with American companies to provide delivery and quantity contracts for commercial deliveries to further lunar exploration and the development of a sustainable lunar economy. As of 2024, the agency has 14 private partners on contract for current and future CLPS missions.
Demonstrations like LuGRE could lay the groundwork for GNSS-based navigation systems on the lunar surface. Bridging these existing systems with emerging lunar-specific navigation solutions has the potential to define how all spacecraft navigate lunar terrain in the Artemis era.
The payload is a collaborative effort between NASA's Goddard Space Flight Center and the Italian Space Agency.
8 notes
·
View notes
Text
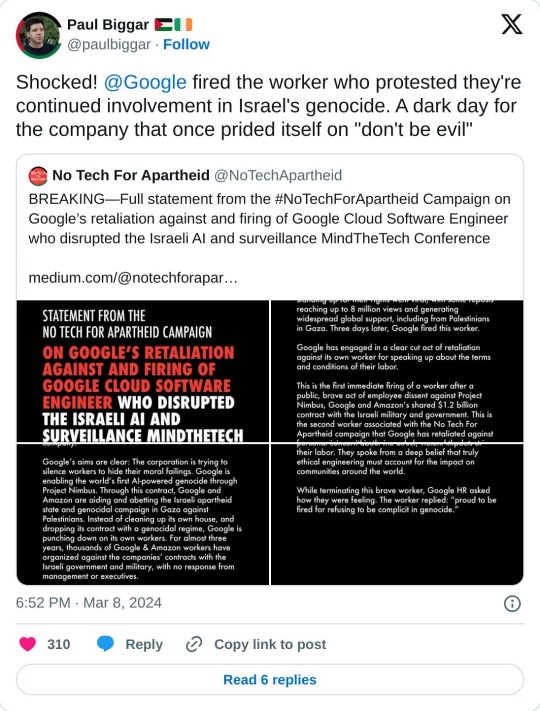
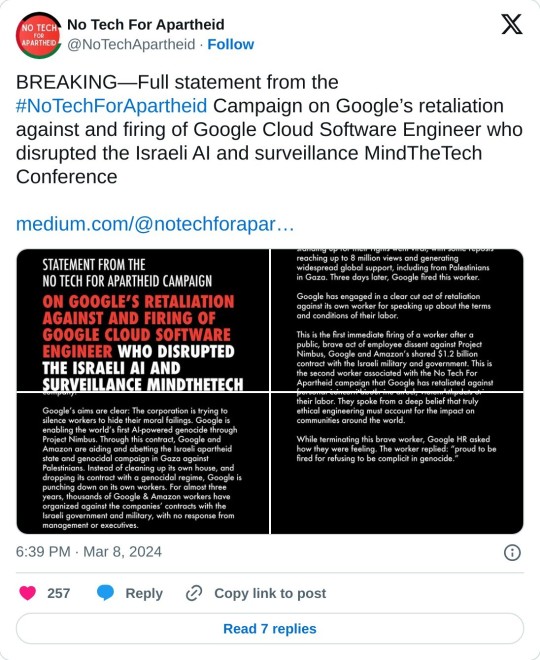
On Monday, a brave Google Cloud engineer spoke up against the corporation’s complicity in Israel’s genocide against the Palestinian people. A video of the worker standing up for their rights went viral, with some reposts reaching up to 8 million views and generating widespread global support, including from Palestinians in Gaza. Three days later, Google fired this worker.
Google has engaged in a clear cut act of retaliation against its own worker for speaking up about the terms and conditions of their labor.
This is the first immediate firing of a worker after a public, brave act of employee dissent against Project Nimbus, Google and Amazon’s shared $1.2 billion contract with the Israeli military and government. This is the second worker associated with the No Tech For Apartheid campaign that Google has retaliated against for organizing within their workplace, and the latest in a series of cases in which Google has retaliated against workers for speaking up about the corporation’s ethical malpractice in a range of business decisions.
While touting the importance of “democratic values” in the workplace, Google is shutting down free speech and silencing debate and dissent among workers within the company.
Google’s aims are clear: The corporation is trying to silence workers to hide their moral failings. Google is enabling the world’s first AI-powered genocide through Project Nimbus. Through this contract, Google and Amazon are aiding and abetting the Israeli apartheid state and genocidal campaign in Gaza against Palestinians. Instead of cleaning up its own house, and dropping its contract with a genocidal regime, Google is punching down on its own workers. For almost three years, thousands of Google & Amazon workers have organized against the companies’ contracts with the Israeli government and military, with no response from management or executives.
As a Cloud Software Engineer on critical technology that enables Project Nimbus to run on sovereign Israeli data centers, this worker spoke from a place of deep personal concern about the direct, violent impacts of their labor. They spoke from a deep belief that truly ethical engineering must account for the impact on communities around the world.
While terminating this brave worker, Google HR asked how they were feeling. The worker replied: “proud to be fired for refusing to be complicit in genocide.”
36 notes
·
View notes
Text

Mike Lynch
British tech entrepreneur who sold his Autonomy software group to Hewlett-Packard and was later cleared after a long-running US fraud case
Mike Lynch, who has died aged 59 in the wreck of his yacht, was sometimes described as “Britain’s Bill Gates”. It was a huge exaggeration, but Lynch could claim two parallels with Gates: he developed world-leading technology (in his case in machine learning or AI) and, unlike so many UK scientists, he learned how to turn it into commercial success.
Such was this success that his company, Autonomy, was valued at $11bn when he sold it to Hewlett-Packard in 2011, but the fall-out from the sale would come to overshadow his technological achievements, and lead to a national debate about the circumstances in which UK citizens may be extradited to the US.
Lynch founded Autonomy with two partners in 1996. Its software enabled a computer to search huge quantities of diverse information, including phone calls, emails and videos, and recognise words. He told the Independent in 1999: “The way our technology works is to look at words and understand the relationships because it has seen a lot of content before. When it sees the word ‘star’ in the context of film, it knows it has nothing to do with the word moon. Because it works from text, it can deal with slang and with different languages.”
Autonomy became a leading company in Cambridge’s Silicon Fen cluster and established a base in San Francisco. “We knew we had to be successful in America. It was a question of ‘Go West young man, go to San Francisco and be ignored.’ They found it hard to believe that anyone from England could have anything powerful.” Lynch found what he called the “cold-hearted schmooze” to secure funding tough.
But Autonomy’s software, enabling computers to identify and match themes and ideas, and sort mammoth amounts of data, was licensed to more than 500 customers, including the US State Department and the BBC. It was listed on Nasdaq in 1998 and on the FTSE 100 in November 2000, although its value of £5.1bn would be halved within a few months in the collapse of the technology boom and accusations of over-promotion. In 2005 it bought a major US rival, Verity, for $500m.
Lynch’s profile rose with it. In 2006 he was appointed OBE for services to enterprise and the following year joined the board of the BBC. In 2011 he became a member of the government’s Council for Science and Technology, and was named the most influential person in UK IT by Computer Weekly. In 2014 he was elected a fellow of the Royal Society.
Though quietly spoken, he had a reputation for toughness, coloured by a liking for James Bond, which led to Autonomy conference rooms being named after Bond villains, and a tank of piranha fish in reception. (Lynch claimed it belonged to one of his business partners.) Challenged about a company culture where people were “a little fanatical”, he replied: “This is not the place for you if you want to work 9 to 5 and don’t love your work.”
Born in Ilford, east London, to Michael, a firefighter, and Dolores, a nurse, and brought up in Chelmsford, Lynch won a scholarship to the independent Bancroft’s school in Woodford Green, before taking a natural sciences degree at Cambridge, where his PhD in artificial neural networks, a form of machine learning, has been widely studied since.
A saxophone player and jazz lover, he set up his first business, Lynett Systems, while still a student, to produce electronic equipment for the music industry. Later he would attribute some loss of hearing to adjusting synthesisers for bands. He quoted his own experience to highlight the difficulties of finding funding for startup businesses in Britain. He finally negotiated a £2,000 loan from one of the managers of Genesis in a Soho bar.
Lynch’s next venture came out of his research. In 1991 he founded Cambridge Neurodynamics, specialising in computer-based fingerprint recognition. Then he established Autonomy.
The pinnacle of his success appeared to come in October 2011 when Autonomy was purchased by Hewlett-Packard for $11bn and Lynch made an estimated $800m. Shortly afterwards he established a new company, Invoke Capital, for investment in tech companies, and he and his wife, Angela Bacares, whom he had married in 2001, invested about £200m in Darktrace, a cybersecurity company.
But just 13 months after the Autonomy sale, HP announced an $8.8bn writedown of the assets “due to serious accounting improprieties, disclosure failures and outright misrepresentations” which it claimed had artificially inflated the company’s value. The authorities investigated, and while the UK Serious Fraud Office found insufficient evidence, in 2018 the US authorities indicted Lynch for fraud. Soon after, Autonomy’s chief financial officer, Sushovan Hussain, was found guilty of fraud and sentenced to five years in prison.
In March 2019 HP followed up with a civil action for fraud in London. Lynch spent days in the witness box as the civil action stretched over nine months. It ended in January 2022 with the judge ruling that HP had substantially succeeded, but that damages would be much less than the $5bn they had claimed.
Meanwhile the US authorities sought Lynch’s extradition on criminal charges of conspiracy and fraud. In spite of representations by senior politicians and accusations that the US authorities were attempting to exercise “extraterritorial jurisdiction”, a district judge ruled in favour of extradition.
An application for judicial review and a further appeal failed, and in May 2023 Lynch was flown to the US to be held under house arrest in San Francisco, with the prospect of a 25-year sentence.
Charged with wire fraud, securities fraud and conspiracy, on 18 March this year Lynch pleaded not guilty, alongside his former vice-president of finance, Stephen Chamberlain. On 6 June, they were found not guilty of all charges. Chamberlain died after being hit by a car on 17 August.
Lynch declared that he wanted to get back to what he loved doing – innovating. But he had little opportunity to do so. He soon embarked on a voyage to celebrate his acquittal, with family, colleagues and business associates. It ended with the sinking of his yacht, Bayesian – named after the 18th-century mathematician, Thomas Bayes, whose work on probability had informed much of his thinking – in a violent storm off the coast of Sicily.
Lynch is survived by his wife and elder daughter, Esme. Their other daughter, Hannah, was also on board the Bayesian.
🔔 Michael Richard Lynch, technology entrepreneur, born 16 June 1965; died 19 August 2024
Daily inspiration. Discover more photos at Just for Books…?
7 notes
·
View notes
Text
Optimizing Case Management: Why CaseXellence is a Premier Choice Among ADAP Platforms
Choosing the right ADAP Platform can significantly enhance the efficiency and effectiveness of handling complex cases across various industries. "CaseXellence" stands out as a top choice among ADAP platforms due to its comprehensive features, user-friendly interface, and robust analytics capabilities. Here's a closer look at why CaseXellence should be considered one of the best ADAP platforms available today.
1. Intuitive Case Management: CaseXellence simplifies case management by providing an intuitive platform that organizes and streamlines crucial information. The software ensures that all case details—documents, communications, deadlines, and contacts—are stored centrally and can be accessed securely from anywhere. This centralization makes it easier for users to manage their caseloads effectively, ensuring that nothing is overlooked.
2. Customizable Workflows: One of the core strengths of CaseXellence is its highly customizable workflows. These can be tailored to fit the specific needs of any organization, regardless of the complexity or uniqueness of their cases. This flexibility ensures that the platform can adapt to the evolving demands of users, making it a robust ADAP platform for organizations seeking to enhance their case management processes. By automating repetitive tasks and routing information correctly through the workflow, CaseXellence reduces the potential for human error and increases overall efficiency.
3. Advanced Analytics and Reporting: CaseXellence offers advanced analytics and reporting tools that allow organizations to gain valuable insights into their case management operations. Users can generate detailed reports on various metrics such as case durations, success rates, and workload distributions. These insights can help identify bottlenecks and areas for improvement, enabling organizations to make data-driven decisions to enhance performance. As a leading ADAP platform, CaseXellence's commitment to leveraging data helps users stay ahead in managing their cases efficiently.
4. Seamless Integration Capabilities: Integration capabilities are essential for any ADAP platform, and CaseXellence excels in this area. It seamlessly integrates with other software tools commonly used within organizations, such as CRM systems, email clients, and document management systems. This interoperability ensures that the transition to using CaseXellence is as smooth as possible and supports a unified approach to case management.
5. Superior Support and Security: Support and security are paramount in the selection of an ADAP platform. CaseXellence provides round-the-clock customer support and boasts top-tier security features to protect sensitive information. Regular updates and maintenance ensure that the platform remains secure against potential threats and continues to function smoothly.
In conclusion, CaseXellence is an exemplary ADAP platform that offers a blend of user-friendliness, customization, advanced analytics, seamless integration, and robust security. Organizations looking to optimize their case management processes will find CaseXellence to be a superior choice, making it one of the best ADAP platforms on the market today.
#case management software#case management#government case management software#adap platform#adap platforms#adap case management platform
0 notes
Text
There's a Treasury coup going on, led by Musk. The Nazi Republicans are fine with this and the legacy (traditional) media doesn't seem to care. (It start Friday sometime. Friday Jan 31st, 2025) I'll link to the source, but I wanna include the full article from Wired in text here.
They have identified the 6 engineers (supposedly they are engineers) who are part of this coup. These people have names, they are not nameless shadows. May they never know a moment of peace in their godforsaken lives.
[Personally I have zero issue with them being young. The real problem is their lack of experience and training with confidential data, lack of security clearance, and them participating in a fucking coup.]
Vittoria Elliott Additional reporting by Zoë Schiffer and Tim Marchman Wired.com Feb 2, 2025 2:02 PM
The Young, Inexperienced Engineers Aiding Elon Musk’s Government Takeover
Engineers between 19 and 24, most linked to Musk’s companies, are playing a key role as he seizes control of federal infrastructure.
The engineers are Akash Bobba, Edward Coristine, Luke Farritor, Gautier Cole Killian (also known as Cole Killian), Gavin Kliger, and Ethan Shaotran. None have responded to requests for comment from WIRED. Representatives from OPM, GSA, and DOGE did not respond to requests for comment.
(Source: Wired.com)
Full article under the cut, including some initial details like university and internship jobs for some of the six.
Elon Musk’s takeover of federal government infrastructure is ongoing, and at the center of things is a coterie of engineers who are barely out of—and in at least one case, purportedly still in—college. Most have connections to Musk, and at least two have connections to Musk’s longtime associate Peter Thiel, a cofounder and chair of the analytics firm and government contractor Palantir who has long expressed opposition to democracy.
WIRED has identified six young men—all apparently between the ages of 19 and 24, according to public databases, their online presences, and other records—who have little to no government experience and are now playing critical roles in Musk’s so-called Department of Government Efficiency (DOGE) project, tasked by executive order with “modernizing Federal technology and software to maximize governmental efficiency and productivity.” The engineers all hold nebulous job titles within DOGE, and at least one appears to be working as a volunteer.
The engineers are Akash Bobba, Edward Coristine, Luke Farritor, Gautier Cole Killian, Gavin Kliger, and Ethan Shaotran. None have responded to requests for comment from WIRED. Representatives from OPM, GSA, and DOGE did not respond to requests for comment.
Already, Musk’s lackeys have taken control of the Office of Personnel Management (OPM) and General Services Administration (GSA), and have gained access to the Treasury Department’s payment system, potentially allowing him access to a vast range of sensitive information about tens of millions of citizens, businesses, and more. On Sunday, CNN reported that DOGE personnel attempted to improperly access classified information and security systems at the US Agency for International Development and that top USAID security officials who thwarted the attempt were subsequently put on leave. The Associated Press reported that DOGE personnel had indeed accessed classified material.
“What we're seeing is unprecedented in that you have these actors who are not really public officials gaining access to the most sensitive data in government,” says Don Moynihan, a professor of public policy at the University of Michigan. “We really have very little eyes on what's going on. Congress has no ability to really intervene and monitor what's happening because these aren't really accountable public officials. So this feels like a hostile takeover of the machinery of governments by the richest man in the world.”
Bobba has attended UC Berkeley, where he was in the prestigious Management, Entrepreneurship, and Technology program. According to a copy of his now-deleted LinkedIn obtained by WIRED, Bobba was an investment engineering intern at the Bridgewater Associates hedge fund as of last spring and was previously an intern at both Meta and Palantir. He was a featured guest on a since-deleted podcast with Aman Manazir, an engineer who interviews engineers about how they landed their dream jobs, where he talked about those experiences last June.
Coristine, as WIRED previously reported, appears to have recently graduated from high school and to have been enrolled at Northeastern University. According to a copy of his résumé obtained by WIRED, he spent three months at Neuralink, Musk’s brain-computer interface company, last summer.e [e seems to be a typo]
Both Bobba and Coristine are listed in internal OPM records reviewed by WIRED as “experts” at OPM, reporting directly to Amanda Scales, its new chief of staff. Scales previously worked on talent for xAI, Musk’s artificial intelligence company, and as part of Uber’s talent acquisition team, per LinkedIn. Employees at GSA tell WIRED that Coristine has appeared on calls where workers were made to go over code they had written and justify their jobs. WIRED previously reported that Coristine was added to a call with GSA staff members using a nongovernment Gmail address. Employees were not given an explanation as to who he was or why he was on the calls.
Farritor, who per sources has a working GSA email address, is a former intern at SpaceX, Musk’s space company, and currently a Thiel Fellow after, according to his LinkedIn, dropping out of the University of Nebraska—Lincoln. While in school, he was part of an award-winning team that deciphered portions of an ancient Greek scroll.
Kliger, whose LinkedIn lists him as a special adviser to the director of OPM and who is listed in internal records reviewed by WIRED as a special adviser to the director for information technology, attended UC Berkeley until 2020; most recently, according to his LinkedIn, he worked for the AI company Databricks. His Substack includes a post titled “The Curious Case of Matt Gaetz: How the Deep State Destroys Its Enemies,” as well as another titled “Pete Hegseth as Secretary of Defense: The Warrior Washington Fears.”
Killian, also known as Cole Killian, has a working email associated with DOGE, where he is currently listed as a volunteer, according to internal records reviewed by WIRED. According to a copy of his now-deleted résumé obtained by WIRED, he attended McGill University through at least 2021 and graduated high school in 2019. An archived copy of his now-deleted personal website indicates that he worked as an engineer at Jump Trading, which specializes in algorithmic and high-frequency financial trades.
Shaotran told Business Insider in September that he was a senior at Harvard studying computer science and also the founder of an OpenAI-backed startup, Energize AI. Shaotran was the runner-up in a hackathon held by xAI, Musk’s AI company. In the Business Insider article, Shaotran says he received a $100,000 grant from OpenAI to build his scheduling assistant, Spark.
“To the extent these individuals are exercising what would otherwise be relatively significant managerial control over two very large agencies that deal with very complex topics,” says Nick Bednar, a professor at University of Minnesota’s school of law, “it is very unlikely they have the expertise to understand either the law or the administrative needs that surround these agencies.”
Sources tell WIRED that Bobba, Coristine, Farritor, and Shaotran all currently have working GSA emails and A-suite level clearance at the GSA, which means that they work out of the agency’s top floor and have access to all physical spaces and IT systems, according a source with knowledge of the GSA’s clearance protocols. The source, who spoke to WIRED on the condition of anonymity because they fear retaliation, says they worry that the new teams could bypass the regular security clearance protocols to access the agency’s sensitive compartmented information facility, as the Trump administration has already granted temporary security clearances to unvetted people.
This is in addition to Coristine and Bobba being listed as “experts” working at OPM. Bednar says that while staff can be loaned out between agencies for special projects or to work on issues that might cross agency lines, it’s not exactly common practice.
“This is consistent with the pattern of a lot of tech executives who have taken certain roles of the administration,” says Bednar. “This raises concerns about regulatory capture and whether these individuals may have preferences that don’t serve the American public or the federal government.”
Additional reporting by Zoë Schiffer and Tim Marchman.
#USA politics#fuck musk#the treasury coup by elon musk#aided and abetted by Trump and the Republicans and the shit ass media#name and shame#spit in their drink will ya?#you know these dudebros are eating at restaurants in DC#fuck these guys
3 notes
·
View notes
Text
If you’ve rented an apartment in the US in the past several years, you may have had the sense that the game was rigged: Prices creep up not only at your building but at others throughout the city, seemingly in lockstep. A new civil lawsuit brought by the US Department of Justice today alleges that in many cases it’s not just in your head—and that a single company’s algorithm is to blame.
That company is RealPage, a Texas-based firm that provides commercial revenue management software for landlords. In other words, it helps set the prices of apartments. But it does so, the DOJ alleges in its lawsuit, by effectively helping its clients cheat; landlords feed rental rate and lease terms into the system, and the RealPage algorithm in turn spits out a suggested price that enables coordination and hinders competition.
“By feeding sensitive data into a sophisticated algorithm powered by artificial intelligence, RealPage has found a modern way to violate a century-old law through systematic coordination of rental housing prices,” deputy attorney general Lisa Monaco said in a statement.
RealPage’s reach is broad. It controls 80 percent of the market for software of its kind, which in turn is used to set prices of around 3 million units across the country, according to the DOJ. It already faces multiple lawsuits, including one from the state of Arizona and another in Washington, DC, where RealPage software is allegedly used to price more than 90 percent of units in large apartment buildings. RealPage’s algorithmic pricing first gained broader attention when a 2022 ProPublica investigation detailed how the company’s YieldStar software works.
The DOJ civil lawsuit, which was joined by the attorneys general of eight states, is a significant escalation in legal action against the company. It’s also a first for the DOJ, according to officials speaking on background during a call to discuss the complaint. While the government had previously filed criminal charges against an Amazon seller for algorithm-enabled price-fixing, this is the first civil action in which the algorithm itself, the Justice Department official says, was effectively the means of the violation.
The complaint itself quotes RealPage executives allegedly acknowledging anticompetitive aspects of its product. “There is greater good in everybody succeeding versus essentially trying to compete against one another in a way that actually keeps the entire industry down,” one RealPage executive allegedly wrote.
RealPage has repeatedly denied any allegations of antitrust violations, going so far as to publish a six-page digital pamphlet that claims to tell “the Real Story” about its products, along with an extensive FAQ page on a dedicated public policy website. The company did not immediately respond to a request for comment. “Attacks on the industry’s revenue management are based on demonstrably false information,” one section of that site reads. “RealPage revenue management software benefits both housing providers and residents.”
“We are disappointed that, after multiple years of education and cooperation on the antitrust matters concerning RealPage, the DOJ has chosen this moment to pursue a lawsuit that seeks to scapegoat pro-competitive technology that has been used responsibly for years,” said Jennifer Bowcock, senior vice president of communications and creative at RealPage, in an emailed statement. “RealPage’s revenue management software is purposely built to be legally compliant, and we have a long history of working constructively with the DOJ to show that."
The DOJ disagrees. “Algorithms don’t exist in a law-free zone,” said Monaco in a press conference to discuss the case. “Training a machine to break the law is still breaking the law.”
In this case, the complaint alleges that those algorithms consistently drove rental prices upward. “RealPage’s software tends to maximize price increases, minimize price decreases, and maximize landlords’ pricing power,” said the DOJ in a press release. RealPage also doesn’t just recommend prices; in many cases, it actively sets them.
“RealPage actively polices landlords’ compliance with those recommendations,” said US attorney general Merrick Garland in today’s press conference. “A large number of landlords effectively agree to outsource their pricing decisions to RealPage by using an ‘auto-accept’ setting that effectively permits RealPage to determine the price a renter will pay.”
The DOJ also claims RealPage has created a “self-reinforcing feedback loop” with its data intake and pricing recommendations structure that also gives it an alleged monopoly in the apartment revenue management software industry. Any competitor who plays by the rules, the DOJ claims, is at a distinct disadvantage.
The Justice Department has spent the past several years staffing up with technologists and data scientists, better enabling them to “interrogate the code,” as multiple officials described the investigative process. While this is the first major algorithmic collusion case, DOJ officials suggested it would be far from the last.
161 notes
·
View notes
Text
Heather Cox Richardson
April 11, 2025 Heather Cox Richardson Apr 12 On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command. Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
(NOTE: AND MOGRHADDASI IS AN IRANIAN NAME, I BELIEVE!!!!) The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem. Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?” The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.” The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
WILL NO ONE STOP THIS FASCIST FROM MAKING OUR GOVERNMENT INTO AN AUTHORITARIAN DICTATORSHIP? I CANNOT FUCKING BELIEVE WHAT IS HAPPENING BEFORE OUR VERY EYES!!!!!
2 notes
·
View notes
Text
Top 10 Emerging Tech Trends to Watch in 2025
Technology is evolving at an unprecedented tempo, shaping industries, economies, and day by day lifestyles. As we method 2025, several contemporary technology are set to redefine how we engage with the sector. From synthetic intelligence to quantum computing, here are the important thing emerging tech developments to look at in 2025.

Top 10 Emerging Tech Trends In 2025
1. Artificial Intelligence (AI) Evolution
AI remains a dominant force in technological advancement. By 2025, we will see AI turning into greater sophisticated and deeply incorporated into corporations and personal programs. Key tendencies include:
Generative AI: AI fashions like ChatGPT and DALL·E will strengthen similarly, generating more human-like textual content, images, and even films.
AI-Powered Automation: Companies will more and more depend upon AI-pushed automation for customer support, content material advent, and even software development.
Explainable AI (XAI): Transparency in AI decision-making becomes a priority, ensuring AI is greater trustworthy and comprehensible.
AI in Healthcare: From diagnosing sicknesses to robot surgeries, AI will revolutionize healthcare, reducing errors and improving affected person results.
2. Quantum Computing Breakthroughs
Quantum computing is transitioning from theoretical studies to real-global packages. In 2025, we will expect:
More powerful quantum processors: Companies like Google, IBM, and startups like IonQ are making full-size strides in quantum hardware.
Quantum AI: Combining quantum computing with AI will enhance machine studying fashions, making them exponentially quicker.
Commercial Quantum Applications: Industries like logistics, prescribed drugs, and cryptography will begin leveraging quantum computing for fixing complex troubles that traditional computer systems can not manage successfully.
3. The Rise of Web3 and Decentralization
The evolution of the net continues with Web3, emphasizing decentralization, blockchain, and user possession. Key factors consist of:
Decentralized Finance (DeFi): More economic services will shift to decentralized platforms, putting off intermediaries.
Non-Fungible Tokens (NFTs) Beyond Art: NFTs will find utility in actual estate, gaming, and highbrow belongings.
Decentralized Autonomous Organizations (DAOs): These blockchain-powered organizations will revolutionize governance systems, making choice-making more obvious and democratic.
Metaverse Integration: Web3 will further integrate with the metaverse, allowing secure and decentralized digital environments.
4. Extended Reality (XR) and the Metaverse
Virtual Reality (VR), Augmented Reality (AR), and Mixed Reality (MR) will retain to improve, making the metaverse extra immersive. Key tendencies consist of:
Lighter, More Affordable AR/VR Devices: Companies like Apple, Meta, and Microsoft are working on more accessible and cushty wearable generation.
Enterprise Use Cases: Businesses will use AR/VR for far flung paintings, education, and collaboration, lowering the want for physical office spaces.
Metaverse Economy Growth: Digital belongings, digital real estate, and immersive studies will gain traction, driven via blockchain technology.
AI-Generated Virtual Worlds: AI will play a role in developing dynamic, interactive, and ever-evolving virtual landscapes.
5. Sustainable and Green Technology
With growing concerns over weather alternate, generation will play a vital function in sustainability. Some key innovations include:
Carbon Capture and Storage (CCS): New techniques will emerge to seize and keep carbon emissions efficaciously.
Smart Grids and Renewable Energy Integration: AI-powered clever grids will optimize power distribution and consumption.
Electric Vehicle (EV) Advancements: Battery generation upgrades will cause longer-lasting, faster-charging EVs.
Biodegradable Electronics: The upward thrust of green digital additives will assist lessen e-waste.
6. Biotechnology and Personalized Medicine
Healthcare is present process a metamorphosis with biotech improvements. By 2025, we expect:
Gene Editing and CRISPR Advances: Breakthroughs in gene modifying will enable treatments for genetic disorders.
Personalized Medicine: AI and big statistics will tailor remedies based on man or woman genetic profiles.
Lab-Grown Organs and Tissues: Scientists will make in addition progress in 3D-published organs and tissue engineering.
Wearable Health Monitors: More superior wearables will music fitness metrics in actual-time, presenting early warnings for illnesses.
7. Edge Computing and 5G Expansion
The developing call for for real-time statistics processing will push aspect computing to the vanguard. In 2025, we will see:
Faster 5G Networks: Global 5G insurance will increase, enabling excessive-velocity, low-latency verbal exchange.
Edge AI Processing: AI algorithms will system information in the direction of the source, reducing the want for centralized cloud computing.
Industrial IoT (IIoT) Growth: Factories, deliver chains, and logistics will advantage from real-time facts analytics and automation.
Eight. Cybersecurity and Privacy Enhancements
With the upward thrust of AI, quantum computing, and Web3, cybersecurity will become even more essential. Expect:
AI-Driven Cybersecurity: AI will come across and prevent cyber threats extra effectively than traditional methods.
Zero Trust Security Models: Organizations will undertake stricter get right of entry to controls, assuming no entity is inherently sincere.
Quantum-Resistant Cryptography: As quantum computer systems turn out to be greater effective, encryption techniques will evolve to counter potential threats.
Biometric Authentication: More structures will rely on facial reputation, retina scans, and behavioral biometrics.
9. Robotics and Automation
Automation will hold to disrupt numerous industries. By 2025, key trends encompass:
Humanoid Robots: Companies like Tesla and Boston Dynamics are growing robots for commercial and family use.
AI-Powered Supply Chains: Robotics will streamline logistics and warehouse operations.
Autonomous Vehicles: Self-using automobiles, trucks, and drones will become greater not unusual in transportation and shipping offerings.
10. Space Exploration and Commercialization
Space era is advancing swiftly, with governments and private groups pushing the boundaries. Trends in 2025 include:
Lunar and Mars Missions: NASA, SpaceX, and other groups will development of their missions to establish lunar bases.
Space Tourism: Companies like Blue Origin and Virgin Galactic will make industrial area travel more reachable.
Asteroid Mining: Early-level research and experiments in asteroid mining will start, aiming to extract rare materials from area.
2 notes
·
View notes